J2EE Agent Sample Use Case Protocol Exchange
The following are actual protocol exchanges in the two use cases. In both use cases, the configuration is as follows:
-
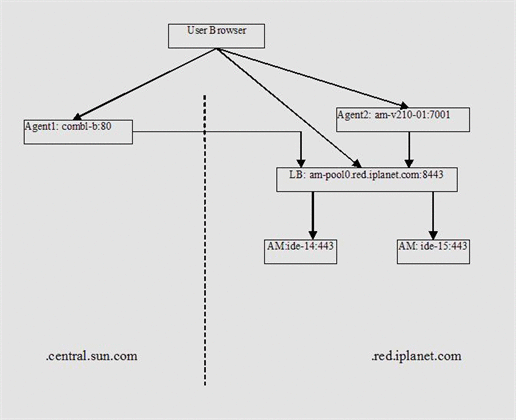
The primary domain (where Access Manager resides) is .iplanet.com. The non-primary domain is .sun.com.
-
In the primary domain, there are two Access Manager instances: ide-14.red.iplanet.com:443 and ide-15.red.iplanet.com:443. Both are behind a load balancer am-pool0.red.iplanet.com:8443.
-
In the primary domain, Agent #2 resides in am-v210-01.red.iplanet.com:7001 with CDSSO disabled because it's in the same DNS domain as the Access Manager instances.
-
In the non-primary domain, Agent #1 resides in comal-b.central.sun.com:80 with CDSSO enabled.
-
A protected resource /app1/test1.html is deployed on the servers of both agents.
In the use cases, we will demonstrate a CDSSO sequence from the primary domain to the non-primary domain, and the reverse.
J2EE Use Case 1: Accessing a Protected Resource in the Primary Domain First
In this use case, an unauthenticated user first accesses a resource under the agent #2 in the Access Manager DNS domain (the primary domain). After the authentication, the Access Manager sets an SSO token in domain .iplanet.com. Then the user accesses another resource under agent #1 in a different domain .central.sun.com. The CDSSO sequence will be invoked and access will be allowed without re-authentication.
-
An unauthenticated user attempts to access http://am-v210-01.red.iplanet.com:7001/app1/test1.html. The agent intercepts the request and receives no SSO token. The agent responds with a redirection to the Access Manager login page.
REQUEST:
GET /app1/test1.html HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us If-Modified-Since: Tue, 20 Jun 2006 11:03:04 GMT User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: am-v210-01.red.iplanet.com:7001
RESPONSE:
HTTP/1.1 302 Moved Temporarily Date: Wed, 02 Aug 2006 12:26:47 GMT Location: https://am-pool0.red.iplanet.com:8443/amserver/UI/Login?goto= http%3A%2F%2Fam-v210-01.red.iplanet.com%3A7001%2Fapp1%2Ftest1.html Content-Type: text/html Connection: Close -
The browser follows the redirection to access the Access Manager login page.
REQUEST:
GET /amserver/UI/Login?goto= http%3A%2F%2Fam-v210-01.red.iplanet.com%3A7001%2Fapp1%2Ftest1.html HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash,application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us If-Modified-Since: Tue, 20 Jun 2006 11:03:04 GMT User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: am-pool0.red.iplanet.com:8443 Connection: Keep-Alive
RESPONSE:
HTTP/1.1 200 OK Server: Sun-ONE-Web-Server/6.1 Date: Wed, 02 Aug 2006 12:26:52 GMT Content-type: text/html;charset=UTF-8 Cache-control: private Pragma: no-cache Expires: 0 X-dsameversion: 7 2005Q4 Am_client_type: genericHTML Set-cookie: JSESSIONID=54C2BEA3AB9BEE7AC172AD396F6C012A;Path=/;Secure Set-cookie: AMAuthCookie=AQIC5wM2LY4Sfcw%2F71xSeh8udj3%2FKcoBDs4FiDT7O zpFDjQ%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; ;Domain=.iplanet.com;Path=/ Set-cookie: amservercookie=0C;Domain=.iplanet.com;Path=/ <.... login in page content omitted by the author > -
The user types in his credential on the login page and clicks Submit. A login form is posted to Access Manager. If the user authenticates successfully, the Access Manager responds by setting an SSO token (iPlanetDirectoryPro) in the domain .iplanet.com. The response also redirects the browser to the original requested resource http://am-v210-01.red.iplanet.com:7001/app1/test1.html.
REQUEST:
POST /amserver/UI/Login HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Referer: https://am-pool0.red.iplanet.com:8443/amserver/UI/ Login?goto=http%3A%2F%2Fam-v210-01.red.iplanet.com%3A7001%2Fapp1%2Ftest1.html Accept-Language: en-us Content-Type: application/x-www-form-urlencoded Connection: Keep-Alive User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: am-pool0.red.iplanet.com:8443 Content-Length: 144 Cache-Control: no-cache Cookie: JSESSIONID=54C2BEA3AB9BEE7AC172AD396F6C012A; AMAuthCookie=AQIC5wM2LY4Sfcw%2F71xSeh8udj3%2FKcoBDs4FiDT7OzpF DjQ%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; amservercookie=0CRESPONSE:
HTTP/1.1 302 Moved Temporarily Server: Sun-ONE-Web-Server/6.1 Date: Wed, 02 Aug 2006 12:27:01 GMT Content-length: 0 Content-type: text/html Cache-control: private Pragma: no-cache X-dsameversion: 7 2005Q4 Am_client_type: genericHTML X-autherrorcode: 0 Location: http://am-v210-01.red.iplanet.com:7001/app1/test1.html Set-cookie: iPlanetDirectoryPro=AQIC5wM2LY4Sfcw%2F71xSeh8udj3%2 FKcoBDs4FiDT7OzpFDjQ%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; Domain=.iplanet.com;Path=/ Set-cookie: AMAuthCookie=LOGOUT;Domain=.iplanet.com;Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/ Connection: close -
The browser follows the redirection to access http://am-v210-01.red.iplanet.com:7001/app1/test.html. Note the SSO token cookie iPlanetDirectoryPro is sent in the HTTP request to the server. The agent validates the SSO token and evaluates policies by interacting with the Access Manager in the background. If the access is allowed, the server responds with the content of the protected resource.
REQUEST:
GET /app1/test1.html HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Pragma: no-cache Accept-Language: en-us Cookie: amservercookie=0C; iPlanetDirectoryPro=AQIC5wM2LY4Sfcw% 2F71xSeh8udj3%2FKcoBDs4FiDT7OzpFDjQ%3D%40 AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23 User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: am-v210-01.red.iplanet.com:7001 Cache-Control: no-cache
RESPONSE:
HTTP/1.1 200 OK Date: Wed, 02 Aug 2006 12:27:02 GMT Content-Length: 88 Content-Type: text/html Last-Modified: Tue, 20 Jun 2006 11:03:04 GMT Set-Cookie: JSESSIONID=GQhWKgrXz1R8jCSpgnc1jXtzMd0M jwn1y9NXPjpZGCQn7jhX5wKd!384704559; path=/ Accept-Ranges: bytes Connection: Close <html> <head> <title>Test1 HTMOL</title> </head> TEST1 HTML </body> </html>
-
The user now attempts to access another resource http://comal-b.central.sun.com:80/app1/test1.html. Note the SSO token iPlanetDirectoryPro is not sent in the HTTP request because the server comal-b.central.sun.com does not match the cookie domain .iplanet.com. The agent, receiving no SSO token, responds by redirecting the browser to the CDC servlet URL https://am-pool0.red.iplanet.com:8443/amserver/cdcservlet.
REQUEST:
GET /app1/test1.html HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us Cookie: SUN_ID=69.196.39.237:227251153914164 If-Modified-Since: Wed, 19 Jul 2006 14:43:46 GMT If-None-Match: W/"88-1153320226000" User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: comal-b.central.sun.com
RESPONSE:
HTTP/1.1 302 Moved Temporarily Server: Sun-Java-System/Application-Server Date: Wed, 02 Aug 2006 12:27:09 GMT Content-type: text/html X-powered-by: Servlet/2.4 Location: https://am-pool0.red.iplanet.com:8443/amserver/cdcservlet?goto= http%3A%2F%2Fcomal-b.central.sun.com %3A80%2Fagentapp%2FsunwCDSSORedirectURI&refererservlet= http%3A%2F%2Fcomal-b.central.sun.com%3A80%2Fagentapp% 2FsunwCDSSORedirectURI&MajorVersion=1&MinorVersion=0&RequestID; =s8c70ff292d4b9f9fbb211003528b7ab90de41229&ProviderID;= http%3A%2F%2Fcomal-b.central.sun.com%3A80%2F%3FRealm%3D%252F&IssueInstant; =2006-08-02T12%3A27%3A09Z&ForceAuthn;=false&IsPassive;=false&Federate;=false Set-cookie: amFilterCDSSORequest=AQICAtwmVLBfMe/ PgTWWJqWPSfO2eZo6rYLpQLiSI2Uk+Es+I25/ 7Pb5lDpLfNbM1S64amLqY9RLg1gib2HzbGqM+GKp/aF/ PslJYgcOwjKzAjZCBX+fDUtjQazNCAD+XwOdOnVsdKuGHNs=; Path=/ Connection: close
A cookie amFilterCDSSORequest is set by the agent to save the user requested URL, its access type (GET/POST), etc. and AuthnRequestID (value of RequestID query parameter). This cookie is set before redirecting to the Access Manager's CDC Servlet. After getting the AuthnResponse later from the CDC Servlet, the Agent then retrieves the information from the amFilterCDSSORequest cookie to continue with the User's Original requested URL.
The redirection URL contains some parameters to be carried to the CDC servlet. Some of these parameters are:
- goto
-
The URL to which CDC servlet will forward AuthNResponse.
- MajorVersion
-
Major version is set 1. It is Liberty Federation Protocol major version.
- MinorVersion
-
The minor version is set to 1. It is Liberty Federation Protocol minor version.
- RequestID
-
Is an Authn Request ID. It is a uniquely generated id. It is of the form sfollowed-by-20-digit-hexadecimal-string. This is sent to CDC Servlet so that the its AuthnResponse later can contain this unique identifier. The RequestID is used to tie the response coming back. It is verified when the response comes back from the CDC servlet.
- ProviderID
-
It is Service Provider ID, which is the agent. The value will be of the form: http://agent-host:port/?Realm=RealmName. Where RealmName is what is configured for property com.sun.identity.agents.config.organization.name in AMAgent.properties.
- IssueInstant
-
It is the time at which the AuthnRequest was created (being sent), in UTC format.
-
The browser follows the redirection to access the CDC servlet. Note the SSO token iPlanetDirectoryPro is sent in the HTTP request because the server DNS domain matches the cookie domain. The CDC servlet validates the SSO token and responds with an HTML page. The page contains an HTML FORM which will be automatically posted to CDSSO Redirect URL on the agent (http://comal-b.central.sun.com:80/agentapp/sunwCDSSORedirectURI, based on the "goto" parameter earlier). The form's hidden field LARES is an encoded Liberty-like AuthnResponse that contains the existing SSO Token in the domain .iplanet.com.
REQUEST:
GET /amserver/cdcservlet?goto= http%3A%2F%2Fcomal-b.central.sun.com%3A80%2F agentapp%2FsunwCDSSORedirectURI&refererservlet;=http%3A%2F%2 Fcomal-b.central.sun.com%3A80%2Fagentapp%2FsunwCDSSORedirectURI& MajorVersion=1&MinorVersion=0&RequestID; =s8c70ff292d4b9f9fbb211003528b7ab90de41229&ProviderID; =http%3A%2F%2Fcomal-b.central.sun.com%3A80%2F%3FRealm%3D%252F&IssueInstant; =2006-08-02T12%3A27%3A09Z&ForceAuthn;=false&IsPassive; =false&Federate;=false HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash,application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us Cookie: JSESSIONID=54C2BEA3AB9BEE7AC172AD396F6C012A; amservercookie=0C; iPlanetDirectoryPro=AQIC5wM2LY4Sfcw%2F71xSeh8udj3%2FKcoBDs4FiDT7OzpF DjQ%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23 If-Modified-Since: Wed, 19 Jul 2006 14:43:46 GMT If-None-Match: W/"88-1153320226000" User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: am-pool0.red.iplanet.com:8443 Connection: Keep-AliveRESPONSE:
HTTP/1.1 200 OK Server: Sun-ONE-Web-Server/6.1 Date: Wed, 02 Aug 2006 12:27:10 GMT Content-type: text/html Pragma: no-cache Content-length: 3788 Connection: keep-alive <HTML> <BODY Onload="document.Response.submit()"> <FORM NAME="Response" METHOD="POST" ACTION= "http://comal-b.central.sun.com:80/agentapp/sunwCDSSORedirectURI"> <INPUT TYPE="HIDDEN" NAME="LARES" VALUE="PGxpYjpBdXRoblJlc3BvbnNlIHhtbG 5zOmxpYj0iaHR0cDovL3Byb2plY3RsaWJlcnR5Lm9yZy9zY2hlbWFzL2NvcmUvMjAwMi8xM IgeG1sbnM6c2FtbD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6MS4wOmFzc2VydGlvbiIge G1sbnM6c2FtbHA9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjEuMDpwcm90b2NvbCIgeG1s ... bnM6ZHM9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvMDkveG1sZHNpZyMiIHhtbG5zOnhzaT0 iaHR0cDovL3d3dy53My5vcmcvMjAwMS9YTUxTY2hlbWEtaW5zdGFuY2UiIFJlc3BvbnNlSU 0ZmIxODg2Nzc4ZTBkMzMyMmEzMzFhYTg4MzMzOTMxNjZmMmYwIiAgSW5SZXNwb25zZVRvPS JzOGM3MGZmMjkyZDRiOWY5ZmJiMjExMDAzNTI4YjdhYjkwZGU0MTIyOSIgIE1ham9yVmVyc 2lvbj0iMSIgIE1pbm9yVmVyc2lvbj0iMCIgIElzc3VlSW5zdGFudD0iMjAwNi0wOC0wMlQx g=="/> </FORM> </BODY></HTML>
The decoded AuthnResponse (line-wrapped) looks like this:
<lib:AuthnResponse xmlns:lib= "http://projectliberty.org/schemas/core/2002/12" xmlns :saml="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:samlp= "urn:oasis:names:tc:SAML:1.0:protocol" xmlns:ds= "http://www.w3.org/2000/09/xmldsig<" xmlns:xsi= "http://www.w3.org/2001/XMLSchema-instance" ResponseID="sb3f4fb1886778e0d3322a331aa8833393166f2f0" InResponseTo="s8c70ff292d4b9f9fbb211003528b7ab90de41229" MajorVersion="1" MinorVersion="0" IssueInstant="2006-08-02T12:27:10Z"> <samlp:Status> <samlp:StatusCode Value="samlp:Success"> </samlp:StatusCode> </samlp:Status> <saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:xsi= "http://www.w3.org/2001/XMLSchema-instance" xmlns:lib="http://projectliberty.org/schemas/core/2002/12" id="s16703a57e86c8163160b2a2ab3ce76111cc9ed5a01" MajorVersion="1" MinorVersion="0" AssertionID="s16703a57e86c8163160b2a2ab3ce76111cc9ed5a01" Issuer="https://ide-14.red.iplanet.com:443/amserver/cdcservlet" IssueInstant="2006-08-02T12:27:10Z" InResponseTo="s8c70ff292d4b9f9fbb211003528b7ab90de41229" xsi:type="lib:AssertionType"> <saml:Conditions NotBefore="2006-08-02T12:27:10Z" NotOnOrAfter="2006-08-02T12:28:10Z" > <saml:AudienceRestrictionCondition> <saml:Audience>http://comal-b.central.sun.com:80/?Realm=%2F</saml:Audience> </saml:AudienceRestrictionCondition> </saml:Conditions> <saml:AuthenticationStatement AuthenticationMethod="LDAP" AuthenticationInstant="2 006-08-02T12:27:01Z" ReauthenticateOnOrAfter="2006-08-02T12:28:10Z" xsi:type="lib:AuthenticationStatementType"> <saml:Subject xsi:type="lib:SubjectType"><saml:NameIdentifier NameQualifier="https://ide-14.red.iplanet.com:443/amserver/cdcservlet"> AQIC5wM2LY4Sfcw%2F71xSeh8udj3%2FKcoBDs4FiDT7OzpFDjQ%3D%40AAJTSQACMTEAAl MxAAIwMQ%3D%3D%23</saml:NameIdentifier> <saml:SubjectConfirmation> <saml:ConfirmationMethod>urn:oasis:names:tc:SAML:1.0:cm:bearer </saml:ConfirmationMe> </saml:SubjectConfirmation> <lib:IDPProvidedNameIdentifier NameQualifier="https://ide-14.red.iplanet.com:443/amserver/cdcservlet" > AQIC5wM2LY4Sfcw%2F71xSeh8udj3%2FKcoBDs4FiDT7OzpFDjQ%3D%40AAJTS QACMTEAAlMxAAIwMQ%3D%3D%23</lib:IDPProvidedNameIdentifier> </saml:Subject><saml:SubjectLocality IPAddress="192.18.72.87" DNSAddress="ide-14.red.iplanet.com" /> <lib:AuthnContext><lib:AuthnContextClassRef>http://www.projectliberty.org/ schemas/authctx/classes/Password</lib:AuthnContextClassRef> <lib:AuthnContextStatementRef>http://www.projectliberty.org/schemas/ authctx/classes/Password</lib:></lib:AuthnContext> </saml:AuthenticationStatement></saml:A> <lib:ProviderID>https://ide-14.red.iplanet.com:443/amserver/cdcservlet </lib:Provide></lib:AuthnResponse>
-
The browser automatically posts the form with LARES to http://comal-b.central.sun.com:80/agentapp/sunwCDSSORedirectURI without the user interaction. The agent responds by setting a new SSO token iPlanetDirectoryPro with an empty cookie domain. A cookie without a domain will be restricted to be sent to the originating server only in the future. Also note the cookie value is exactly the same as the one set in Step 3 response by Access Manager. The HTTP response also redirects the browser to the original requested resource http://comal-b.central.sun.com:80/app1/test1.html.
REQUEST:
POST /agentapp/sunwCDSSORedirectURI HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us Content-Type: application/x-www-form-urlencoded Pragma: no-cache User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: comal-b.central.sun.com Content-Length: 3592 Cookie: amFilterCDSSORequest=AQICAtwmVLBfMe/PgTWWJqWPSfO2eZo6rYLpQLiSI2Uk+Es+I25/ 7Pb5lDpLfNbM1S64amLqY9RLg1gib 2HzbGqM+GKp/aF/PslJYgcOwjKzAjZCBX+fDUtjQazNCAD+XwOdOnVsdKuGHNs=; SUN_ID=69.196.39.237:227251153914164
RESPONSE:
HTTP/1.1 302 Moved Temporarily Server: Sun-Java-System/Application-Server Date: Wed, 02 Aug 2006 12:27:12 GMT Content-type: text/html X-powered-by: Servlet/2.4 Location: http://comal-b.central.sun.com:80/app1/test1.html Set-cookie: iPlanetDirectoryPro=AQIC5wM2LY4Sfcw%2F71xSeh8udj3% 2FKcoBDs4FiDT7OzpFDjQ%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; Path=/ Set-cookie: amFilterCDSSORequest=reset; Expires=Thu, 01-Jan-1970 00:00:10 GMT; Path=/ Connection: close
In responding to this request, the agent goes through the following steps to validate the received AuthnResponse:
-
First the requestID (saved in the amFilterCDSSORequest cookie) is verified against the responseID of the AuthnResponse.
-
The status code of the AuthnResponse is verified to see if it is successful.
-
The assertions are extracted from the AuthnResponse. There should be only 1.
-
From the Assertion, the issuer is extracted and is verified against the policy agent list of trusted ID providers. If the issuer is not in the policy agent trusted list, then user request is blocked. These trusted ID providers are governed by property, as we discussed in the configuration section, com.sun.identity.agents.config.cdsso.trusted.id.providerx. These IDs should contain URLs of the actual Access Manager instances (not the load-balancer URL).
-
The conditions that are in the assertion are also validated. The main one is the date validity condition. The date validity attributes, not before and notOnorAfter, are verified to verify the assertion has not expired. Hence time synchronization between Access Manager and Agent is essential. Also the skew factor provided in AMAgent com.sun.identity.agents.config.cdsso.clock.skew helps to overcome any network latencies.
In the response, cookie amFilterCDSSORequest is removed by setting the expiration date in the past.
-
-
The browser follows the redirection to access the protected resoruce again at http://comal-b.central.sun.com:80/app1/test.html. Note the new SSO token is sent to the server. The agent validates the SSO token, evaluates the policies and allows the access. The server responds with the content of the protected resource.
REQUEST:
GET /app1/test1.html HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us Pragma: no-cache User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: comal-b.central.sun.com Cookie: iPlanetDirectoryPro=AQIC5wM2LY4Sfcw%2F71xSeh8udj3%2FKcoB Ds4FiDT7OzpFDjQ%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; SUN_ID=69.196.39.237:227251153914164RESPONSE:
HTTP/1.1 200 OK Server: Sun-Java-System/Application-Server Date: Wed, 02 Aug 2006 12:27:13 GMT Content-length: 88 Content-type: text/html X-powered-by: Servlet/2.4 Etag: W/"88-1153320226000" Last-modified: Wed, 19 Jul 2006 14:43:46 GMT Connection: close <html> <head> <title>Test1 HTML</title> </head> body> Test1 HTML </body> </html>
J2EE Agent Use Case 2: Accessing a Protected Resource in a Non-Primary Domain First
In this use case, an unauthenticated user first accesses a protected resource in the non-primary domain (.sun.com). He then accesses a protected resource in the primary domain (.iplanet.com).
-
An unauthenticated user attempts to access http://comal-b.central.sun.com:80/app1/test1.html. The policy agent intercepts the request and receives no SSO token. Because the SSO is enabled, the agent responds with a redirection to the Access Manager CDC servlet URL https://am-pool0.red.iplanet.com:8443/amserver/cdcservlet.
REQUEST:
GET /app1/test1.html HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us Cookie: SUN_ID=69.196.39.237:227251153914164 If-Modified-Since: Wed, 19 Jul 2006 14:43:46 GMT If-None-Match: W/"88-1153320226000" User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: comal-b.central.sun.com
RESPONSE:
HTTP/1.1 302 Moved Temporarily Server: Sun-Java-System/Application-Server Date: Tue, 01 Aug 2006 17:43:58 GMT Content-type: text/html X-powered-by: Servlet/2.4 Location: https://am-pool0.red.iplanet.com:8443/amserver/cdcservlet?goto= http%3A%2F%2Fcomal-b.central.sun.com%3A80%2Fagentapp% 2FsunwCDSSORedirectURI&refererservlet; =http%3A%2F%2Fcomal-b.central.sun.com%3A80%2F agentapp%2FsunwCDSSORedirectURI&MajorVersion=1&MinorVersion=0&RequestID; =sa51a95ae420a2a8bb2d608740680c9df6e767dc3&ProviderID ; =http%3A%2F%2Fcomal-b.central.sun.com%3A80%2F%3FRealm%3D%252F&IssueInstant; =2006-08-01T17%3A43%3A58Z&ForceAuthn;=false&IsPassive;=false&Federate;=false Set-cookie: amFilterCDSSORequest=AQICAtwmVLBfMe/ PgTWWJqWPSfO2eZo6rYLpQLiSI2Uk+Es+I25/7Pb5lDpLfNbM1S64amLqY9RLg1i9nEXzWfcn BEVZS5SdG2pJtTdMzEgo/o/MARoPq//EMt766UEXFT6aOUAtME0or70=; Path=/ Connection: close
-
The browser follows the redirection to access the CDC servlet without any SSO token. The CDC servlet responds with a login page.
REQUEST:
GET /amserver/cdcservlet?goto=http%3A%2F%2 Fcomal-b.central.sun.com%3A80%2Fagentapp%2FsunCDSSORedirectURI &refererservlet;=http%3A%2F%2Fcomal-b.central.sun.com%3A80 %2Fagentapp%2FsunwCDSSORedirectURI&MajorVersion=1 &MinorVersion=0&RequestID;=sa51a95ae420a2a8bb2d608740680c9df6e767dc3& ProviderID;=http%3A%2F%2Fcomal-b.central.sun.com%3A80%2F%3FRealm%3D %252F&IssueInstant;=2006-08-01T17%3A43%3A58Z &ForceAuthn;=false&IsPassive;=false&Federate;=false HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us If-Modified-Since: Wed, 19 Jul 2006 14:43:46 GMT If-None-Match: W/"88-1153320226000" User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: am-pool0.red.iplanet.com:8443 Connection: Keep-Alive
RESPONSE:
HTTP/1.1 200 OK Server: Sun-ONE-Web-Server/6.1 Date: Tue, 01 Aug 2006 17:44:02 GMT Content-type: text/html;charset=UTF-8 Cache-control: private Pragma: no-cache Expires: 0 X-dsameversion: 7 2005Q4 Am_client_type: genericHTML Set-cookie: JSESSIONID=B38B1B717BDD9EE781995CCEC058A70D;Path=/;Secure Set-cookie: AMAuthCookie=AQIC5wM2LY4SfcwzBSR87MxpRCFm9P5Dx9csUN7EGE4o JXk%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; Domain=.iplanet.com;Path=/ Set-cookie: amservercookie=0C;Domain=.iplanet.com;Path=/ <.... login page content omitted by author ...>
-
The user types in his credential on the login page and clicks Submit. A login form is posted to Access Manager. If the user authenticates successfully, the Access Manager responds by setting an SSO token (iPlanetDirectoryPro) in the domain .iplanet.com. The response also redirects the browser back to the CDC servlet https://am-pool0.red.iplanet.com:8443/amserver/cdcservlet.
REQUEST:
POST /amserver/UI/Login HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Referer: https://am-pool0.red.iplanet.com:8443/amserver/c dcservlet?goto=http%3A%2F%2Fcomal-b.central.sun.com%3A80 %2Fagentapp%2FsunwCDSSORedirectURI&refererservlet; =http%3A%2F%2Fcomal-b.central.sun.com%3A80%2Fagentapp%2 FsunwCDSSORedirectURI&MajorVersion=1&MinorVersion=0&RequestID; =sa51a95ae420a2a8bb2d608740680c9df6e767dc3 &ProviderID;=http%3A%2F%2Fcomal-b.central.sun.com %3A80%2F%3FRealm%3D%252F&IssueInstant; =2006-08-01T17%3A43%3A58Z &ForceAuthn;=false&IsPassive;=false&Federate;=false Accept-Language: en-us Content-Type: application/x-www-form-urlencoded Connection: Keep-Alive User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: am-pool0.red.iplanet.com:8443 Content-Length: 600 Cache-Control: no-cache Cookie: JSESSIONID=B38B1B717BDD9EE781995CCEC058A70D; AMAuthCookie=AQIC5wM2LY4SfcwzBSR87MxpRCFm9P5Dx9csUN7EGE43D %40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; amservercookie=0C
RESPONSE:
HTTP/1.1 302 Moved Temporarily Server: Sun-ONE-Web-Server/6.1 Date: Tue, 01 Aug 2006 17:44:15 GMT Content-length: 0 Content-type: text/html Cache-control: private Pragma: no-cache X-dsameversion: 7 2005Q4 Am_client_type: genericHTML X-autherrorcode: 0 Location: https://am-pool0.red.iplanet.com:8443/amserver/cdcservlet? TARGET=http%3A%2F%2Fcomal-b.central.sun.com%3A80%2F agentapp%2FsunwCDSSORedirectURI&refererservlet;= http%3A%2F%2Fcomal-b.central.sun.com%3A80%2Fagentapp%2F sunwCDSSORedirectURI&MajorVersion=1&MinorVersion=0&RequestID; =sa51a95ae420a2a8bb2d608740680c9df6e767dc3 &ProviderID;=http%3A%2F%2Fcomal-b.central.sun.com %3A80%2F%3FRealm%3D%252F&IssueInstant; =2006-08-01T17%3A43%3A58Z&ForceAuthn; =false&IsPassive;=false&Federate;=false Set-cookie: iPlanetDirectoryPro=AQIC5wM2LY4SfcwzBSR87MxpRCFm9P5Dx9csUN7 EGE4oJXk%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; Domain=.iplanet.com;Path=/ Set-cookie: AMAuthCookie=LOGOUT;Domain=.iplanet.com; Expires=Thu, 01-Jan-1970 00:00:10 GMT;Path=/ Connection: close
-
The browser follows the redirection to access the CDC servlet again. This time the SSO token iPlanetDirectoryPro is sent in the HTTP request because the server DNS domain matches the cookie domain. The CDC servlet validates the SSO token and responds with an HTML page. The page contains a HTML FORM which will be automatically posted to CDSSO Redirect URL on the agent (http://comal-b.central.sun.com:80/agentapp/sunwCDSSORedirectURI). The form's hidden field LARES is an encoded Liberty-like AuthnResponse that contains the existing SSO Token in the domain .iplanet.com.
REQUEST:
GET /amserver/cdcservlet?TARGET= http%3A%2F%2Fcomal-b.central.sun.com %3A80%2Fagentapp%2FsunwCDSSORedirectURI& refererservlet;=http%3A%2F%2Fcomal-b.central.sun.com %3A80%2Fagentapp%2FsunwCDSSORedirectURI&MajorVersion=1 &MinorVersion=0&RequestID;=sa51a95ae420a2a8bb2d608740680c9df6e767dc3&ProviderID; =http%3A%2F%2Fcomal-b.central.sun.com%3A80%2F%3FRealm%3D%252F&IssueInstant; =2006-08-01T17%3A43%3A58Z&ForceAuthn;=false&IsPassive;=false&Federate; =false HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Referer: https://am-pool0.red.iplanet.com:8443/amserver/cdcservlet? goto=http%3A%2F%2Fcomal-b.central.sun.com%3A80%2Fagentapp% 2FsunwCDSSORedirectURI&refererservlet; =http%3A%2F%2Fcomal-b.central.sun.com%3A80%2Fagentapp% 2FsunwCDSSORedirectURI&MajorVersion=1&MinorVersion=0 &RequestID;=sa51a95ae420a2a8bb2d608740680c9df6e767dc3& ProviderID;=http%3A%2F%2Fcomal-b.central.sun.com%3 A80%2F%3FRealm%3D%252F&IssueInstant;=2006-08-01T17%3A43%3A58Z& ForceAuthn;=false&IsPassive;=false&Federate;=false Accept-Language: en-us Connection: Keep-Alive User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: am-pool0.red.iplanet.com:8443 Cache-Control: no-cache Cookie: JSESSIONID=B38B1B717BDD9EE781995CCEC058A70D; amservercookie=0C; iPlanetDirectoryPro=AQIC5wM2LY4SfcwzBSR87MxpRCFm9P5Dx9csUN7EGE4 oJXk%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23
RESPONSE:
HTTP/1.1 200 OK Server: Sun-ONE-Web-Server/6.1 Date: Tue, 01 Aug 2006 17:44:16 GMT Content-type: text/html Pragma: no-cache Content-length: 3776 Connection: keep-alive <HTML> <BODY Onload="document.Response.submit()"> <FORM NAME="Response" METHOD="POST" ACTION="http://comal-b.central.sun.com:80/agentapp/sunwCDSSORedirectURI"> <INPUT TYPE="HIDDEN" NAME="LARES" VALUE="PGxpYjpBdXRoblJlc3BvbnNlIHhtbG5z OmxpYj0iaHR0cDovL3Byb2plY3RsaWJlcnR5Lm9yZy9zY2hlbWFzL2NvcmUvMjAwMi8xMiIge G1sbnM6c2FtbD0idXJuOm9hc2lzOm5hbWVzOnRjOlNBTUw6MS4wOmFzc2VydGlvbiIgeG1sbn M6c2FtbHA9InVybjpvYXNpczpuYW1lczp0YzpTQU1MOjEuMDpwcm90b2NvbCIgeG1sbnM6ZHM 9Imh0dHA6Ly93d3cudzMub3JnLzIwMDAvMDkveG1sZHNpZyMiIHhtbG5zOnhzaT0iaHR0cDov L3d3dy53My5vcmcvMjAwMS9YTUxTY2hlbWEtaW5zdGFuY2UiIFJlc3BvbnNlSUQ9InM4MjMyN ... Tg3ODBhNDYwNTFkZTRlNjQzZDZhNmQ4NDQ3OWRiMTBkYmFiIiAgSW5SZXNwb25zZVRvPSJzYT xYTk1YWU0MjBhMmE4YmIyZDYwODc0MDY4MGM5ZGY2ZTc2N2RjMyIgIE1ham9yVmVyc2lvbj0i MSIgIE1pbm9yVmVyc2lvbj0iMCIgIElzc3VlSW5zdGFudD0iMjAwNi0wOC0wMVQxNzo0NDoxN loiPjxzYW1scDpTdGF0dXM+CjxzYW1scDpTdGF0dXNDb2RlIFZhbHVlPSJzYW1scDpTdWNjZX NzIj4KPC9zYW1scDpTdGF0dXNDb2RlPgo8L3NhbWxwOlN0YXR1cz4KPHNhbWw6QXNzZXJ0aW9 uICB4bWxuczpzYW1sPSJ1cm46b2FzaXM6bmFtZXM6dGM6U0FNTDoxLjA6YXNzZXJ0aW9uIiB4 bWxuczp4c2k9Imh0dHA6Ly93d3cudzMub3JnLzIwMDEvWE1MU2NoZW1hLWluc3RhbmNlIiAge G1sbnM6bGliPSJodHRwOi8vcHJvamVjkLmlwbGFuZXQuY29tOjQ0My9hbXNlcnZlci9jZGNzZ XJ2bGV0PC9saWI6UHJvdmlkZXJJRD48L2xpYjpBdXRoblJlc3BvbnNlPgo="/> </FORM> </BODY></HTML>
The corresponding decoded AuthnResponse (line-wrapped) is as follows:
<lib:AuthnResponse xmlns:lib="http://projectliberty.org/schemas/core/2002/12" xmlns:saml="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:samlp="urn:oasis:names:tc :SAML:1.0:protocol" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:xsi="htt p://www.w3.org/2001/XMLSchema-instance" ResponseID="s823258780a46051de4e643d6a6d 84479db10dbab" InResponseTo="sa51a95ae420a2a8bb2d608740680c9df6e767dc3" MajorV ersion="1" MinorVersion="0" IssueInstant="2006-08-01T17:44:16Z"><samlp:Status> <samlp:StatusCode Value="samlp:Success"> </samlp:StatusCode> </samlp:Status> <saml:Assertion xmlns:saml="urn:oasis:names:tc:SAML:1.0:assertion" xmlns:xsi="h ttp://www.w3.org/2001/XMLSchema-instance" xmlns:lib="http://projectliberty.org/ schemas/core/2002/12" id="sa3e3d3c81c45413d66bcf6baadeff0624a243e3901" MajorVer sion="1" MinorVersion="0" AssertionID="sa3e3d3c81c45413d66bcf6baadeff0624a243e39 01" Issuer="https://ide-14.red.iplanet.com:443/amserver/cdcservlet" IssueInstant ="2006-08-01T17:44:15Z" InResponseTo="sa51a95ae420a2a8bb2d608740680c9df6e767dc3" xsi:type="lib:AssertionType"> <saml:Conditions NotBefore="2006-08-01T17:44:15Z" NotOnOrAfter="2006-08-01T17:4 5:15Z" > <saml:AudienceRestrictionCondition> <saml:Audience>http://comal-b.central.sun.com:80/?Realm=%2F</saml:Audience> </saml:AudienceRestrictionCondition> </saml:Conditions> <saml:AuthenticationStatement AuthenticationMethod="LDAP" AuthenticationInstant ="2006-08-01T17:44:15Z" ReauthenticateOnOrAfter="2006-08-01T17:45:15Z" xsi:type= "lib:AuthenticationStatementType"><saml:Subject xsi:type="lib:SubjectType"><sa ml:NameIdentifier NameQualifier="https://ide-14.red.iplanet.com:443/amserver/cdc servlet">AQIC5wM2LY4SfcwzBSR87MxpRCFm9P5Dx9csUN7EGE4oJXk%3D%40AAJTSQACMTEAAlMxAA IwMQ%3D%3D%23</saml:NameIdentifier> <saml:SubjectConfirmation> <saml:ConfirmationMethod>urn:oasis:names:tc:SAML:1.0:cm:bearer</saml:Confirmatio> </saml:SubjectConfirmation> <lib:IDPProvidedNameIdentifier NameQualifier="https://ide-14.red.iplanet.com:44 3/amserver/cdcservlet" >AQIC5wM2LY4SfcwzBSR87MxpRCFm9P5Dx9csUN7EGE4oJXk%3D%40AAJ TSQACMTEAAlMxAAIwMQ%3D%3D%23</lib:IDPProvidedNameIdentifier> </saml:Subject><saml:SubjectLocality IPAddress="192.18.72.87" DNSAddress="ide-1 4.red.iplanet.com" /><lib:AuthnContext><lib:AuthnContextClassRef>http://www.proj ectliberty.org/schemas/authctx/classes/Password</lib:AuthnContextClassRef><lib:A uthnContextStatementRef>http://www.projectliberty.org/schemas/authctx/classes/Pa ssword</lib:AuthnContextStatementRef></lib:AuthnContext></saml:AuthenticationSta> </saml:Assertion> <lib:ProviderID>https://ide-14.red.iplanet.com:443/amserver/cdcservlet</lib:Prov> </lib:AuthnResponse>
-
The browser automatically posts the form with LARES to http://comal-b.central.sun.com:80/agentapp/sunwCDSSORedirectURI without the user interaction. The agent responds by setting a new SSO token iPlanetDirectoryPro with an empty cookie domain. A cookie with an empty DNS domain will have the server FQDN as the domain. Also note the cookie value is exactly the same as the one set in Step 3 response by Access Manager. The only difference is the cookie domain. The HTTP response also redirects the browser to the original requested resource http://comal-b.central.sun.com:80/app1/test1.html.
REQUEST:
POST /agentapp/sunwCDSSORedirectURI HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us Content-Type: application/x-www-form-urlencoded Pragma: no-cache User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: comal-b.central.sun.com Content-Length: 3584 Cookie: amFilterCDSSORequest=AQICAtwmVLBfMe/PgTWWJqWPSfO2eZo6rYLpQLiSI2Uk+Es+I25/ 7Pb5lDpLfNbM1S64amLqY9RLg1i9nEXzWfcnBEVZS5SdG2pJtTdMzEgo/o/ MARoPq//EMt766UEXFT6aOUAtME0or70=; SUN_ID=69.196.39.237:227251153914164
RESPONSE:
HTTP/1.1 302 Moved Temporarily Server: Sun-Java-System/Application-Server Date: Tue, 01 Aug 2006 17:44:18 GMT Content-type: text/html X-powered-by: Servlet/2.4 Location: http://comal-b.central.sun.com:80/app1/test1.html Set-cookie: iPlanetDirectoryPro=AQIC5wM2LY4SfcwzBSR87MxpRCFm 9P5Dx9csUN7EGE4oJXk%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; Path=/ Set-cookie: amFilterCDSSORequest=reset; Expires=Thu, 01-Jan-1970 00:00:10 GMT; Path=/ Connection: close
-
The browser follows the redirection to access the protected resoruce again at http://comal-b.central.sun.com:80/app1/test.html. Note the new SSO token is sent to the server. The agent validates the SSO token, evaluates the policies and allows the access. The server responds with the content of the protected resource.
REQUEST:
GET /app1/test1.html HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us Pragma: no-cache User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: comal-b.central.sun.com Cookie: iPlanetDirectoryPro=AQIC5wM2LY4SfcwzBSR87MxpRCFm9P5Dx9cs UN7EGE4oJXk%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23; SUN_ID=69.196.39.237:227251153914164
RESPONSE:
HTTP/1.1 200 OK Server: Sun-Java-System/Application-Server Date: Tue, 01 Aug 2006 17:44:19 GMT Content-length: 88 Content-type: text/html X-powered-by: Servlet/2.4 Etag: W/"88-1153320226000" Last-modified: Wed, 19 Jul 2006 14:43:46 GMT Connection: close <html> <head> <title>Test1 HTML</title> </head> <body> Test1 HTML </body> </html>
-
The user now attempts to access http://am-v210-01.red.iplanet.com:7001/app1/test1.html. A SSO token is sent with the HTTP request. The browser currently has two SSO Tokens, one for each domain. The token sent was obtained in Step 3. The agent intercepts the request and receives the SSO token. The agent validates the token and permits the server to serve the content of the protected page.
REQUEST:
GET /app1/test1.html HTTP/1.0 Accept: image/gif, image/x-xbitmap, image/jpeg, image/pjpeg, application/x-shockwave-flash, application/vnd.ms-excel, application/vnd.ms-powerpoint, application/msword, */* Accept-Language: en-us If-Modified-Since: Tue, 20 Jun 2006 11:03:04 GMT User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; .NET CLR 1.1.4322) Host: am-v210-01.red.iplanet.com:7001 Cookie: amservercookie=0C; iPlanetDirectoryPro=AQIC5wM2LY4Sfcwz BSR87MxpRCFm9P5Dx9csUN7EGE4oJX k%3D%40AAJTSQACMTEAAlMxAAIwMQ%3D%3D%23
RESPONSE:
HTTP/1.1 304 Not Modified Date: Tue, 01 Aug 2006 17:44:32 GMT Content-Length: 0 Set-Cookie: JSESSIONID=GPTQKHJWTyvJVSGm31rV59LCzxGTmhqVFfc4GbLY4 L98vBRCYnKT!384704559; path=/ Connection: Close
- © 2010, Oracle Corporation and/or its affiliates
