Configuring Administrator-Initiated Password Reset
By default, when a user password is close to expiring, Directory Server sends a warning to the user. This warning is sent based on the time configured in the password policy. The next time the user attempts to log in to a protected application, OpenSSO Enterprise redirects the user to Identity Manager where the user can change his password. If the user does not change his password, and lets his password expire, he must contact the HelpDesk administrator and request a password-reset.
When a HelpDesk administrator resets the user's password, a flag is set in the user profile. The HelpDesk administrator gives a temporary password to the user by email or over the phone. When the user logs in using the temporary password, the user is redirected to the Identity Manager user interface to reset the user password. After the user password has been reset, the flag that was set earlier is unset.
To configure OpenSSO Enterprise for administrator-initiated password reset, complete the following steps:
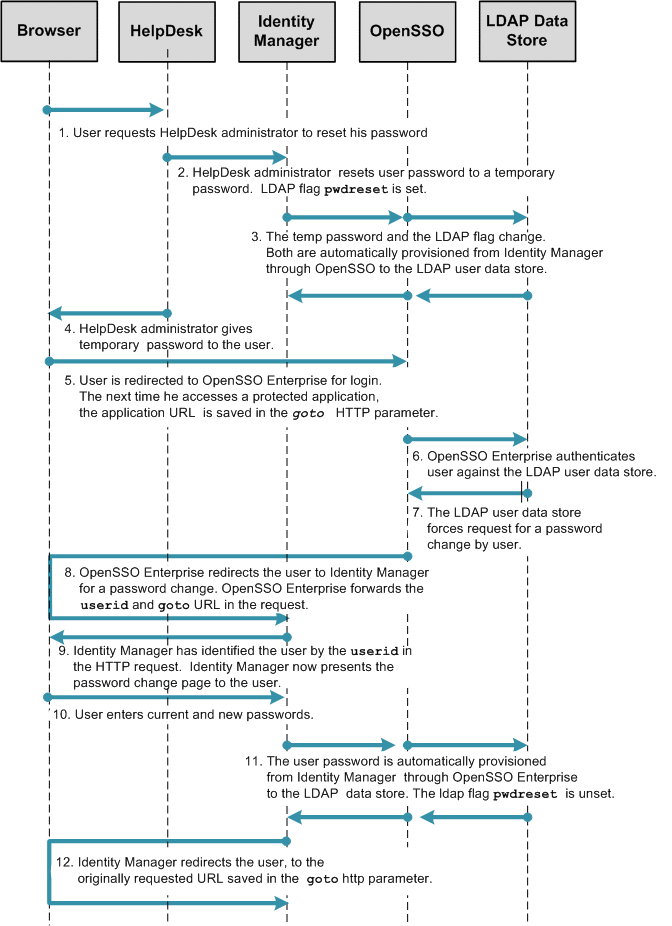
The following figure illustrates in detail the process flow for administrator-initiated password reset.
Figure 1–10 Process Flow for Administrator-Initiated Password Reset
Configuring Directory Server
Before you can configure OpenSSO Enterprise for administrator-initiated password reset, you must configure the Directory Server must to meet the following conditions:
-
A password policy is configured and assigned to the test user's LDAP profile in the directory server. The password policy should have the following controls set:
- Set Password Expiration
-
LDAP attributes: passwordexp, passwordmaxage
- Set Expiration Warning
-
LDAP attribute: passwordwarning
- Warning Duration
-
LDAP attribute: passwordExpireWithoutWarning)
-
The following controls are set to allow for administrator-driven password reset:
- Require Password Change at First Login and After Reset
-
LDAP attribute: passwordchange, passwordmustchange
- Allow Users to Change Their Passwords
-
LDAP attribute: pwdallowuserchange
-
The passwordPolicySubentry attribute in the test user's LDAP profile is set with the DN of the password policy. This indicates that the password policy has been assigned to this user. Example:
cn=idm_integration,dc=sun,dc=com
See the Sun Java System Directory Server Enterprise Edition 6.3 Administration Guide for detailed instructions on configuring these settings.
Important Information About Using Sun Directory Server 6.3
After you install Sun Directory Server Enterprise Edition 6.3, Directory Server uses Legacy mode for its password policy syntax, which works for both Directory Server 5.x and Directory Server 6.x. However, Directory Server 6.3 maintains two sets of password attributes for both password policies and the user's computed password attributes. This may trigger other potential issues. Unless you are planning to use Directory Server 5.x password policies, a good practice is to migrate a new Directory Server 6.3 instance to the Directory Server 6-Only mode. Doing so removes redundancies and avoids any potential problems.
Here is an example of how you can verify which mode the Directory Server is running in, and how you can enable Directory Server 6–Only mode.
# DirectoryServer-base/ds6/bin/dsconf get-server-prop -p 1389 -D "cn=directory manager" -w mypass -c -e pwd-compat-mode pwd-compat-mode : DS5-compatible-mode # DirectoryServer-base/ds6/bin>dsconf pwd-compat -p 1389 -D "cn=directory manager" -w mypass -c -e to-DS6-migration-mode ## Beginning password policy compatibility changes. ## Password policy compatibility changes finished. Task completed (slapd exit code: 0). # DirectoryServer-base/ds6/bin/dsconf pwd-compat -p 1389 -D "cn=directory manager" -w mypass -c -e to-DS6-mode ## Beginning password policy compatibility changes. ## Password policy compatibility changes finished. Task completed (slapd exit code: 0). # DirectoryServer-base/ds6/bin/dsconf get-server-prop -p 1389 -D "cn=directory manager" -w mypass -c -e pwd-compat-mode pwd-compat-mode : DS6-mod |
Configuring OpenSSO Enterprise for Administrator-Initiated Password Reset
Only the OpenSSO Enterprise LDAP authentication module supports the password change controls enforced by most directory servers.
To configure OpenSSO Enterprise for administrator-initiated password reset, complete the following steps:
 To Enable LDAP Authentication
To Enable LDAP Authentication
-
Log in to the OpenSSO Enterprise console as an administrator.
-
Click the Access Control tab.
-
Navigate to Top Level Realm > Authentication > Authentication Chaining.
-
In the Authentication Chaining section, click New.
-
Enter a name for the chain and click OK.
For this example: idmauth.
-
On the new chain's Properties page, add the LDAP module as REQUIRED, and click Save.
-
Click Back to Authentication.
-
For the Organization Authentication Configuration property value, choose the service you just created.
-
In the Module Instances section, choose LDAP.
-
Provide the following information to about the LDAP user data store:
- Primary LDAP Server:
-
Use the form server.domain:port
- DN to Start User Search:
-
Branch of the LDAP tree from which the user-search begins
- DN for Root User Bind:
-
DN to use when binding to the LDAP user data store
- Password for Root User Bind:
-
Password for the user binding to the LDAP user data store
- Password for Root User Bind (confirm):
-
Type the password again
-
Save the changes.
-
Log out of the OpenSSO Enterprise console.
Next Steps
After completing this configuration:
-
Use /opensso/console to log in to the OpenSSO Enterprise console; do not /opensso/UI/Login. This ensures that the authentication module configured for the OpenSSO Enterprise administrator is used when logging into the administration console, and that the LDAP module just configured for realm users is not used.
-
Make sure this configuration hasn't affected how you can view the objects inside the OpenSSO Enterprise resource inside Identity Manager.
Log in to the Identity Manager console and expand the OpenSSO Enterprise resource listing to view the OpenSSO Enterprise roles and groups inside it. If you receive an error, you may need to reconfigure the OpenSSO Enterprise adaptor to use a delegated administrator instead of amadmin to connect to OpenSSO Enterprise. The Identity Manager adaptor for OpenSSO Enterprise authenticates to OpenSSO Enterprise using the authentication configuration for the realm which is now different from the configuration for the OpenSSO Enterprise console. The amadmin will no longer work.
To create the delegated administrator:
-
Create a user.
-
Assign this user to a group.
-
Assign administrator privileges to this group.
See Delegating Administrator Privileges in Sun OpenSSO Enterprise 8.0 Administration Guide for detailed information on delegating administrative privileges to a group.
-
 To Define Identity Manager URLs as Not Enforced
To Define Identity Manager URLs as Not Enforced
-
Log in to the OpenSSO Enterprise console as an administrator.
-
Click the Access Control tab.
-
Click the appropriate realm name and navigate to the Policy Agent Profile for the policy agent that protects Identity Manager.
-
Under the Policy Agent Profile, click the Application tab.
-
Add the following URIs to the Not Enforced URIs property:
-
/idm/authutil/
-
/idm/authutil/*
-
/idm/authutil/*?*
-
-
Click Save.
-
Log out of OpenSSO Enterprise.
Creating a Custom ChangePassword.jsp File
By default, the user is directed to the OpenSSO Enterprise password change page. Create a custom JSP file, ChangePassword.jsp, that redirects a user to Identity Manager for password change events. The new ChangePassword.jsp forwards the following information to Identity Manager:
-
The original URL requested by the user and defined as the value of the goto parameter
-
The user identifier defined as the value of the accountId parameter
This customized ChangePassword.jsp file is referenced in the section Modifying the LDAP Authentication Module XML Service File.
To create a custom ChangePassword.jsp file, choose only one of the following procedures:
 To Create a New ChangePassword.jsp File
To Create a New ChangePassword.jsp File
-
Create the file config/auth/default/ChangePassword.jsp in the OpenSSO Enterprise web-app directory.
Example:
<html> <%@page info="Login" language="java"%> <%@taglib uri="/WEB-INF/jato.tld" prefix="jato"%> <%@taglib uri="/WEB-INF/auth.tld" prefix="auth"%> <jato:useViewBean className="com.sun.identity.authentication.UI.LoginViewBean"> <%@ page contentType="text/html" %> <head> <title><jato:text name="htmlTitle_Login" /></title> <% String ServiceURI = (String) viewBean.getDisplayFieldValue(viewBean.SERVICE_URI); %> <link rel="stylesheet" href="<%= ServiceURI %>/css/styles.css" type="text/css" /> <script language="JavaScript" src="<%= ServiceURI %>/js/browserVersion.js"></script> <script language="JavaScript" src="<%= ServiceURI %>/js/auth.js"></script> </head> <% System.out.println("AccountId: " + request.getParameter("IDToken1")); System.out.println("goto: " + request.getParameter("goto")); System.out.println("plaingoto: " + request.getParameter("plaingoto")); String accountId = request.getParameter("IDToken1"); String gotoURL = request.getParameter("plaingoto"); String redirectURL = "http://HostName.DomainName:6480/idm/authutil/anonResetPassword.jsp"; if(accountId != null){ redirectURL = redirectURL + "?accountId=" + accountId; } if(gotoURL != null && !gotoURL.equals("null") && (gotoURL.length() > 0)){ if(accountId == null){ redirectURL = redirectURL + "?goto=" + gotoURL; }else{ redirectURL = redirectURL + "&goto=" + gotoURL; } } System.out.println("Redirect URL is:" + redirectURL); response.sendRedirect(redirectURL); %> </jato:useViewBean> </html> -
Customize the URL to the Identity Manager page that performs the password-reset functions.
The URL is highlighted in bold above. Determine this URL with help from your Identity Manager administrator, and customize the URL for your deployment.
 To Use the Sample Source Code
To Use the Sample Source Code
-
Copy the sample file opensso/integrations/idm/jsps/ChangePassword.jsp in the opensso.zip distribution to the directory web-container-deploy-base/opensso/config/auth/default.
-
Customize the URL to the Identity Manager page that performs the password-reset functions.
Determine this URL with help from your Identity Manager administrator, and customize the URL for your deployment. See step 2 of Creating a Custom ChangePassword.jsp File .
Modifying the LDAP Authentication Module XML Service File
By default, upon receiving a directory-server request for the user to change his password, OpenSSO Enterprise directs the user to its own password-change page. Configure OpenSSO Enterprise to use a custom JSP for password-change events. Modify the LDAP.xmlfile to use ChangePassword.jsp that you created in Creating a Custom ChangePassword.jsp File .
You can manually change the deployed LDAP.xml file, or you can use the sample LDAP.xml included with the opensso.zip download. Choose only one of the following procedures:
 To Manually Modify a Deployed LDAP.xml File
To Manually Modify a Deployed LDAP.xml File
-
Use a text editor to open the /web-container-deploy-base/opensso/config/auth/default/LDAP.xml file, and add the section of code highlighted in bold in the following example:
PasswordCallback echoPassword="false" > <Prompt> Password: </Prompt> </PasswordCallback> </Callbacks> <Callbacks length="4" order="2" timeout="120" template="ChangePassword.jsp" header="Change Password<BR></BR>#REPLACE#<BR></BR>" > <PasswordCallback echoPassword="false" > <Prompt>Old Password </Prompt> </PasswordCallback>
-
Use a text editor to open the /web-container-deploy-base/opensso/config/auth/default_en/LDAP.xml file, and make the same change as in step 1.
 To Use the Sample LDAP.xml
To Use the Sample LDAP.xml
-
Change to the opensso/integrations/idm/xml/ directory in the decompressed opensso.zip to access the sample LDAP.xml.
-
Replace your deployed /web-container-deploy-base/opensso/config/auth/default/LDAP.xml with the a customLDAP.xml.
Choose only one of the following options:
-
Replace your existing LDAP.xml file with the sample LDAP.xml file. If you choose this option, you will lose any custom changes you may have made to this file earlier.
-
Run the diff command to compare the files, then manually make the necessary changes.
-
Modifying the OpenSSO Login Page
Embed code into the OpenSSO Enterprise Login.jsp file that will save the URL in the HTTP request parameter goto. This URL is required by the ChangePassword.jsp that you created in the section To Create a New ChangePassword.jsp File. Once saved, the URL can be passed onto Identity Manager. Identity Manager later redirects the user to that URL.
The URL in the HTTP request parameter goto is the original URL requested by the user, before he was redirected to OpenSSO Enterprise for login.
You can manually change the deployed Login.jsp file, or you can use the sample Login.jsp included with the opensso.zip download. Choose only one of the following procedures:
 To Modify a Deployed Login.jsp File
To Modify a Deployed Login.jsp File
-
Use a text editor to open the file web-container-deploy-base/opensso/config/auth/default/Login.jsp and add the sections of code displayed in bold the following example:
... <% String ServiceURI = (String) viewBean.getDisplayFieldValue(viewBean.SERVICE_URI); String encoded = "false"; String gotoURL = (String) viewBean.getValidatedInputURL( request.getParameter("goto"), request.getParameter("encoded"), request); String encodedQueryParams = (String) viewBean.getEncodedQueryParams(request); if ((gotoURL != null) && (gotoURL.length() != 0)) { encoded = "true"; } String replaygotoURL = ""; String goToURL = request.getParameter("goto"); if(gotoURL != null && !gotoURL.equals("null") && (gotoURL.length() > 0)){ replaygotoURL = "&goto=" + goToURL; } System.out.println("replaygotoURL: " + replaygotoURL); %> <link rel="stylesheet" href="<%= ServiceURI %>/css/styles.css" type="text/css" /> <script language="JavaScript" src="<%= ServiceURI %>/js/browserVersion.js"></script> <script language="JavaScript" src="<%= ServiceURI %>/js/auth.js"></script> ... <input type="hidden" name="goto" value="<%= gotoURL %>"> <input type="hidden" name="SunQueryParamsString" value="<%= encodedQueryParams %>"> <input type="hidden" name="encoded" value="<%= encoded %>"> <input type="hidden" name="plaingoto" value="<%= request.getParameter("goto") %>"> </auth:form> </jato:content> ... -
Remove the web container's temporary, compiled JSP to ensure that the changes made are picked up.
For example, if you are using GlassFish, the temporary, compiled classes are in the glassfish-home/domains/your-domain/generated/ directory.
-
Restart the OpenSSO Enterprise web container after making the changes.
 To Use the Sample Login.jsp
To Use the Sample Login.jsp
-
Locate the file opensso/integrations/idm/jsps/Login.jsp in the decompressed opensso.zip distribution.
-
Replace the deployed web-container-deploy-base/opensso/config/auth/default/Login.jsp file.
Choose only one of the following two options:
You can replace your existing Login.jsp with the sample Login.jsp. If you choose this option, the following will occur:
-
You will lose any custom changes made to the existing Login.jsp.
-
You will inherit changes that might have been previously made to the sample Login.jsp to incorporate requirements for other use cases related to the OpenSSO integration with Identity Manager.
-
You must change the Identity Manager URL embedded in the sample Login.jsp to reflect the Identity Manager system URL of your architecture.
You can search for the string /idm to locate the URLs.
Alternatively, you can make the changes manually. If you choose this option, first run the diff command to view the differences between the deployed Login.jsp and the sample Login.jsp, and then make the changes manually.
-
-
Remove the web containers temporary, compiled JSP to ensure that the changes made are picked up.
For example, if you are using GlassFish, the temporary, compiled classes is in the glassfish-home/domains/your-domain/generated/ directory.
-
Restart the OpenSSO web container after making the changes.
Configuring the Identity Manager Password Controls
When the Identity Manager password controls are configured for administrator-initiated password reset, the following occur:
-
The Identity Manager Open SSO Resource Adaptor requires the old password.
-
Identity Manager uses the basic change password form.
-
Identity Manager self-change is enabled.
 To Configure the Identity Manager Password
Controls
To Configure the Identity Manager Password
Controls
-
Log in to Identity Manager as an administrator.
-
Navigate to the Configure tab.
-
Click on the link "Form and Process Mappings.”
-
Search for the entry "endUserChangePassword. "
In the text field, replace "End User Change Password Form" with "Basic Change Password Form.”
-
Save the changes.
 To Test the Identity Manager Password Control
Configuration
To Test the Identity Manager Password Control
Configuration
-
Login to Identity Manager as a regular user .
-
Under the "Profile" tab, go to the "Change password" page.
You should see that SunAccessManagerRealm requires the old password.
-
Enter the user's the old password, the new password, and confirmation of the new password,
The user's password should be set in the Directory Server user data store as a "self-change” instead of am "admin-change.” This is especially important if the pwdMustChange or passwordMustChange attributes had been earlier set on the user's profile on the Directory Server. If the self-change configuration is not implemented, when the user logs back into OpenSSO Enterprise, the user will be asked to change his password again
Testing Administrator-Initiated Password Reset Configurations
To verify the behavior for each stage of this use case, perform the following validation tests in this exact order:
 To Test the Password Expiration Warning
To Test the Password Expiration Warning
Complete the following steps after the time for the password expiration warning, as defined in the password policy, would take effect.
-
Access a URL protected by OpenSSO Enterprise .
The OpenSSO login page is displayed.
-
Enter the test user name and password.
You are redirected to Identity Manager to change your password. Note the following about the Identity Manager URL:
-
The URL is the one configured in ChangePassword.jsp.
-
The user will be forwarded to the value of the goto parameter after the password has been successfully changed.
-
The value of the accountId parameter determines the account for which the password needs to be changed. Identity Manager will make the changes to the password on both Identity Manager and OpenSSO Enterprise .
-
 To Test the Password Expiration
To Test the Password Expiration
Complete the following steps after the time the password should have expired, as defined in the password policy.
-
Access a URL protected by OpenSSO Enterprise.
The OpenSSO Enterprise login page is displayed.
-
Enter the test user name and password.
An error page is displayed indicating the test user that the password has expired. The user is then instructed to ask the administrator to reset the password.
 To Test Administrator-Initiated Password Reset
To Test Administrator-Initiated Password Reset
Before You Begin
The Directory Server must have logging and auditing features enabled. Use these features to monitor the Directory Server audit log as you complete the test. See the Sun Java System Directory Server Enterprise Edition 6.3 Administration Guide .
-
Log in as the Directory Administrator, and change the password for a test user.
This simulates the password reset by a HelpDesk administrator.
-
Verify that the user's userPassword attribute was modified, and that the pwdreset attribute was set to TRUE using the audit log.
The pwdreset attribute will force the user to change the password at the next login. The audit log might resemble this sample:
time: 20090713074720 dn: uid=idmuser1,dc=sun,dc=com changetype: modify replace: userPassword userPassword: {SSHA}4Bgy/HF9SGN9nnS4Ii6/KJj9ktFdAxQUIDvwVQ== - replace: modifiersname modifiersname: cn=admin,cn=administrators,cn=dscc - replace: modifytimestamp modifytimestamp: 20090713144720Z - replace: passwordexpirationtime passwordexpirationtime: 19700101000000Z - replace: pwdreset pwdreset: TRUE -
Access the Identity Manager user URL.
You are redirected to OpenSSO Enterprise for login.
-
Enter the test user name and password.
You are redirected to Identity Manager to change your password. Note the following about the Identity Manager URL:
-
The URL is the one configured in ChangePassword.jsp.
-
The user is forwarded to the value of the goto parameter after the password has been successfully changed.
-
The value of the accountId parameter determines the account for which the password needs to be changed. Identity Manager will make the changes to the password on both Identity Manager and OpenSSO Enterprise.
-
Troubleshooting Administrator-Initiated Account Unlock
If you cannot log in to OpenSSO Enterprise, verify that you are using the correct userid and password. The Directory Administrator who reset your password should have communicated to you the temporary password for the user account.
Monitor the Directory Server's access log, during login. You should see successful SRCH and BIND operations, for the user. Example:
[15/Jul/2009:09:32:12 -0700] conn=158 op=9 msgId=269 - SRCH base="dc=sun,dc=com" scope=2 filter="(uid=idmuser1)" attrs="dn uid" [15/Jul/2009:09:32:12 -0700] conn=158 op=9 msgId=269 - RESULT err=0 tag=101 nentries=1 etime=0 [15/Jul/2009:09:32:12 -0700] conn=160 op=5 msgId=270 - BIND dn="uid=idmuser1,dc=sun,dc=com" method=128 version=3 [15/Jul/2009:09:32:12 -0700] conn=160 op=5 msgId=270 - RESULT err=0 tag=97 nentries=0 etime=0 dn="uid=idmuser1,dc=sun,dc=com" |
The string err=0 in the entries above indicates success for that operation.
After you log in to OpenSSO Enterprise , if you are not redirected to the Identity Manager page, check the following :
-
Be sure that your OpenSSO Enterprise web-container is using the changed or new files, that you configured above. The web-container may be using an old pre-compiled version of the default JSP files.
-
Be sure the IDM URLs that you embedded in the JSP files are accurate and don't contain typographic errors.
-
Browse through the OpenSSO Enterprise web-container logs and look for any reported errors.
-
Browse through the OpenSSO Enterprise debug logs, especially the Authentication and IdRepo logs, to check for any reported errors or exceptions.
-
Browse through the OpenSSO Enterprise Authentication debug log to determine which LDAP.xml file is being looked up, and be sure that specific file was actually modified by you. Depending upon your browser configuration for localization, OpenSSO Enterprise might be looking for LDAP.xml in a different directory. For example, you may have modified just the config/auth/default/LDAP.xml file, but OpenSSO Enterprise might be using the /config/auth/default_en/LDAP.xml file.
- © 2010, Oracle Corporation and/or its affiliates
