NIS+ Authentication and Credentials—Introduction
The purpose of NIS+ credentials is to authenticate (confirm) the identity of each principal requesting an NIS+ service or access to an NIS+ object. In essence, the NIS+ credential/authorization process is an implementation of the Secure RPC system.
The credential/authentication system prevents someone from assuming some other user's identity. That is, it prevents someone with root privileges on one machine from using the su command to assume the identity of a second user who is not logged in and then accessing NIS+ objects with the second user's NIS+ access privileges.
Once a server authenticates a principal, the principal is placed in one of four authorization classes. The server then checks the NIS+ object that the principal wants to access to see what activities that class of principal is authorized to perform. (See NIS+ Authorization and Access—Introduction for further information on authorization.)
User and Machine Credentials
There are two basic types of principal, users and machines, and thus two different types of credentials:
-
User credentials. When someone is logged in to an NIS+ client as a regular user, requests for NIS+ services include that person's user credentials.
-
Machine credentials. When a user is logged in to an NIS+ client as superuser, request for services use the client machine's credentials.
DES versus LOCAL Credentials
NIS+ principals can have two types of credential: DES and LOCAL.
DES Credentials
Note –
DES credentials are only one method of achieving authentication. In the future, other methods may be available. Thus, do not equate DES credentials with NIS+ credentials.
In this document, the term DES credentials is used generically to denote a Diffie-Hellman key based authentication, regardless of key length. The system allows you to specify the key length from a pre-determined set. Use nisauthconf(1M) to set or display the Diffie-Hellman key length.
DES (Data Encryption Standard) credentials are the type of credential that provide secure authentication. When this guide refers to NIS+ checking a credential to authenticate an NIS+ principal, it is the DES credential that NIS+ is validating.
Each time a principal requests an NIS+ service or access to an NIS+ object, the software uses the credential information stored for that principal to generate a credential for that principal. DES credentials are generated from information created for each principal by an NIS+ administrator, as explained in Chapter 12, Administering NIS+ Credentials.
-
When the validity of a principal's DES credential is confirmed by NIS+, that principal is authenticated.
-
A principal must be authenticated in order to be placed in the owner, group, or world authorization classes. In other words, you must have a valid DES credential in order to be placed in one of those classes. (Principals who do not have a valid DES credential are automatically placed in the nobody class.)
-
DES credential information is always stored in the cred table of the principal's home domain, regardless of whether that principal is a client user or a client machine.
LOCAL Credentials
LOCAL credentials are simply a map between a user's User ID number and NIS+ principal name which includes their home domain name. When users log in, the system looks up their LOCAL credential, which identifies their home domain where their DES credential is stored. The system uses that information to get the user's DES credential information.
When users log in to a remote domain, those requests use their LOCAL credential which points back to their home domain; NIS+ then queries the user's home domain for that user's DES credential information. This allows a user to be authenticated in a remote domain even though the user's DES credential information is not stored in that domain.
Figure 11–3 Credentials and Domains
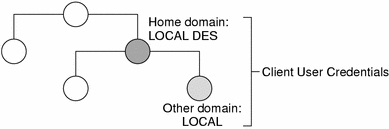
LOCAL credential information can be stored in any domain. In fact, in order to log into a remote domain and be authenticated, a client user must have a LOCAL credential in the cred table of the remote domain. If a user does not have a LOCAL credential in a remote domain the user is trying to access, NIS+ will be unable to locate the user's home domain to obtain the user's DES credential. In such a case the user would not be authenticated and would be placed in the nobody class.
User Types and Credential Types
A user can have both types of credentials, but a machine can only have DES credentials.
Root cannot have NIS+ access, as root, to other machines because the root UID of every machine is always zero. If root (UID=0) of machine A tried to access machine B as root, that would conflict with machine B's already existing root (UID=0). Thus, a LOCAL credential doesn't make sense for a client machine; so it is allowed only for a client user.
Table 11–2 Types of Credentials|
Type of Credential |
Client User |
Client machine |
|---|---|---|
|
DES |
Yes |
Yes |
|
LOCAL |
Yes |
No |
- © 2010, Oracle Corporation and/or its affiliates
