PAM (Overview)
The Pluggable Authentication Module (PAM) framework lets you “plug in” new authentication technologies without changing system entry services, such as login, ftp, telnet, and so on. You can also use PAM to integrate UNIX login with other security mechanisms like DCE or Kerberos. Mechanisms for account, session, and password management can also be “plugged in” by using this framework.
Benefits of Using PAM
The PAM framework allows you to choose any combination of system entry services (ftp, login, telnet, or rsh, for example) for user authentication. Some benefits that PAM provides are as follows:
-
Flexible configuration policy
-
Per application authentication policy
-
The ability to choose a default authentication mechanism
-
Multiple passwords on high-security systems
-
-
Ease of use for the end user
-
No retyping of passwords if the passwords are the same for different mechanisms.
-
The ability to use a single password for multiple authentication methods with the password-mapping feature. This feature works even if the passwords that are associated with each authentication method are different.
-
The ability to prompt the user for passwords for multiple authentication methods without having the user enter multiple commands.
-
-
The ability to pass optional parameters to the user authentication services
PAM Components
The PAM software consists of a library, several modules, and a configuration file. New versions of several commands or daemons that take advantage of the PAM interfaces are also included.
The following figure illustrates the relationship between the applications, the PAM library, the pam.conf file, and the PAM modules.
Figure 4–1 How PAM Works
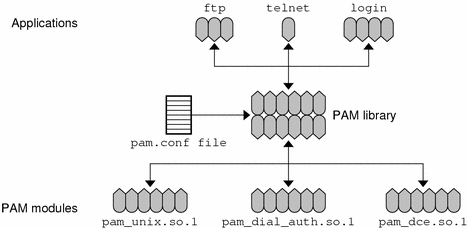
The applications, such as ftp, telnet, and login, use the PAM library to access the appropriate module. The pam.conf file defines which modules to use, and in what order the modules are to be used with each application. Responses from the modules are passed back through the library to the application.
The following sections describe the relationship between the PAM components and the applications.
PAM Library
The PAM library, /usr/lib/libpam, provides the framework to load the appropriate modules and to manage the stacking process. The PAM library provides a generic structure to which all of the modules can plug in.
Stacking Feature
The PAM framework provides a method for authenticating users with multiple services by using stacking. Depending on the configuration, the user can be prompted for passwords for each authentication method. The order in which the authentication services are used is determined through the PAM configuration file.
Password-Mapping Feature
The stacking feature can require that a user remembers several passwords. With the password-mapping feature, the primary password is used to decrypt the other passwords. The user does not need to remember or enter multiple passwords. The other option is to synchronize the passwords across each authentication mechanism. This strategy could increase the security risk, because the mechanism security is limited by the least secure password method that is used in the stack.
Changes to PAM for the Solaris 9 Release
The Solaris 9 release includes several enhancements to the PAM service. The following list highlights the most important changes:
-
To accommodate proper stacking, the pam_unix module is broken into single service modules. These modules provide the same capabilities as in the existing module. The capabilities are provided by the following modules:
-
pam_authtok_get
-
pam_authtok_check
-
pam_authtok_store
-
pam_unix_auth
-
pam_dhkeys
-
pam_passwd_auth
See PAM Modules for information about the new modules.
-
-
New PAM services are included: cron, dtsession, ppp and ssh. See Valid Service Names for PAM for information about the new services.
-
The PAM configuration file was updated to include the new modules and new services. See Generic pam.conf File for information about the configuration file.
Changes to PAM for the Solaris 9 Update 2 Release
Update 2 includes a new binding control flag. This flag provides the ability to skip additional authentication if the service module returns success and if no preceding required modules have failed. The control flag is documented in the pam.conf(4) man page and in PAM Control Flags.
- © 2010, Oracle Corporation and/or its affiliates
