Solaris RBAC Elements
In the RBAC model in the Solaris operating environment, users log in as themselves and assume roles that enable them to run restricted administration graphical tools and commands. The RBAC model introduces these elements to the Solaris operating environment:
-
Privileged Application – An application that can override system controls and check for specific user IDs (UIDs), group IDs (GIDs), or authorizations (see Privileged Applications).
-
Role – A special identity for running privileged applications that can be assumed by assigned users only.
-
Authorization – A permission that can be assigned to a role or user (or embedded in a rights profile) for performing a class of actions that are otherwise prohibited by security policy.
-
Rights Profile – A collection of overrides that can be assigned to a role or user. A rights profile can consist of authorizations, commands with setuid or setgid permissions (referred to as security attributes), and other rights profiles.
The following figure shows how the RBAC elements work together.
Figure 5–1 Solaris RBAC Element Relationships
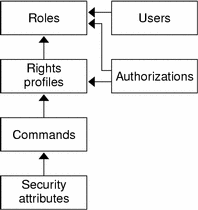
In RBAC, users are assigned to roles. Roles get their capabilities from rights profiles and authorizations. Authorizations are generally assigned to the rights profiles with which they are logically associated but can be assigned directly to roles.
Note –
Rights profiles and authorizations can also be assigned directly to users. This practice is discouraged because it enables users to make mistakes through inadvertent use of their privileges.
Commands with security attributes, that is, real or effective UIDs or GIDs, can be assigned to rights profiles.
The following figure uses the Operator role and the Printer Management rights profiles as examples to demonstrate RBAC relationships.
Figure 5–2 How Solaris RBAC Elements Relate
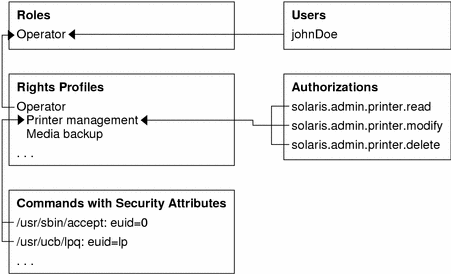
The Operator role is used to maintain printers and perform media backup. The user johnDoe is assigned to the Operator role and can assume it by supplying the Operator password.
The Operator rights profile has been assigned to the Operator role. The Operator rights profile has two supplementary profiles assigned to it, Printer Management and Media Backup, which reflect the Operator role's primary tasks.
The Printer Management rights profile is for managing printers, print daemons, and spoolers. Three authorizations are assigned to the Printer Management rights profile: solaris.admin.printer.read, solaris.admin.printer.delete, and solaris.admin.printer.modify. These authorizations allows users to manipulate information in the printer queue. The Printer Management profile also has a number of commands with security attributes that are assigned to it, such as /usr/sbin/accept with euid=0 and /usr/ucb/lpq with euid=lp.
- © 2010, Oracle Corporation and/or its affiliates
