Virtual Private Networks
You can use IPsec to construct a virtual private network (VPN). You use IPsec by constructing an Intranet that uses the Internet infrastructure. For example, an organization that uses VPN technology to connect offices with separate networks, can deploy IPsec to secure traffic between the two offices.
The following figure illustrates how two offices use the Internet to form their VPN with IPsec deployed on their network systems.
Figure 1–3 Virtual Private Network
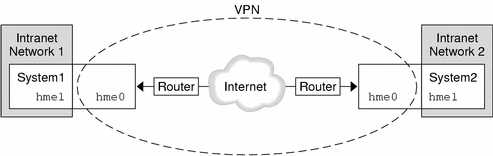
See How to Set Up a Virtual Private Network (VPN) for a description of the setup procedure.
- © 2010, Oracle Corporation and/or its affiliates
