Installation and Configuration Overview
This section provides an overview of the installation and configuration tasks for meeting Global Telco’s requirements. For details on configuring Identity Manager to coexist with Identity Synchronization for Windows, see Appendix B, Configuring Identity Manager and Identity Synchronization for Windows to Coexist.
Primary and Failover Installations
To provide a high-availability solution, Identity Synchronization for Windows must be installed in two separate locations, one in the United States and another in Europe. The deployment in the United States is the primary deployment, while the one is Europe is only meant to be used during failover scenarios.
To improve performance, the Identity Synchronization for Windows components are distributed between two machines in each location. For the deployment in the United States, the Identity Synchronization for Windows Core components are installed on config-us.gt.com, and both connectors are installed on connectors-us.gt.com. For the deployment in Europe, the Identity Synchronization for Windows Core components are installed on config-eu.gt.com, and both connectors are installed on connectors-eu.gt.com.
The primary deployment and the various communication paths are shown in the following figure. For simplicity, gt.com is dropped, and only the machine names are shown.
Figure 3–3 Primary Installation of Identity Synchronization for Windows
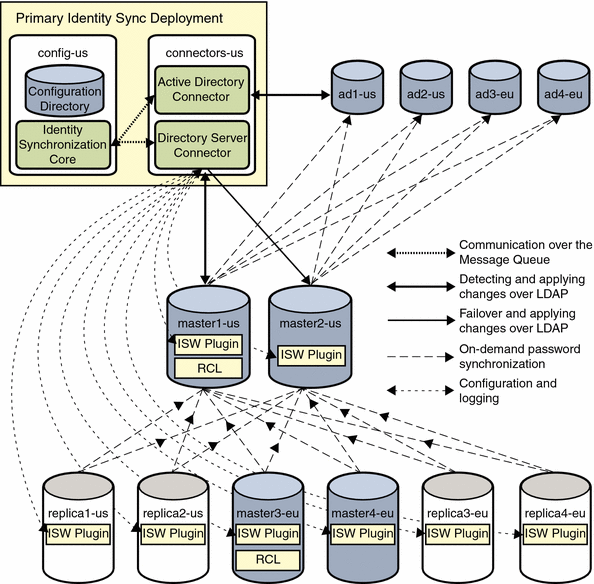
The Directory Server Connector and Active Directory Connector, installed on connectors-us.gt.com, communicate with each other and receive their configuration from the Message Queue that is installed with the Identity Synchronization for Windows Core.
The Active Directory Connector communicates exclusively with the ad1-us.gt.com domain controller, using LDAP. The Directory Server Connector communicates with two preferred Directory Servers. While primary Directory Server is available, the Directory Server Connector detects and propagates changes to master1-us.gt.com. If primary Directory Server is unavailable, it fails over to master2-us.gt.com to apply changes, but cannot detect further changes made at any other preferred Directory Server until master1-us.gt.com is available.
Note –
-
If both master1-us.gt.com and master2-us.gt.com are unavailable, changes synchronized from Active Directory are not applied to the other preferred Directory Servers, master3-eu.gt.com and master4-eu.gt.com. Identity Synchronization for Windows treats these other preferred Directory Servers like read-only replicas, except that external changes to these preferred Directory Servers are replicated to the retro change log on master1-us.gt.com and then synchronized to Active Directory.
-
The Identity Synchronization for Windows Directory Server Plug-ins running on Master1-us.gt.com and master2-us.gt.com only communicate with ad2-us, ad3-eu, and ad4-eu if ad1-us is unavailable. Similarly, the other preferred Directory Servers and replicas only communicate with master2-us.gt.com if master1-us.gt.com is unavailable.
An Identity Synchronization for Windows Directory Server Plug-in must be enabled on all eight Directory Server instances, four preferred Directory Servers and four read-only replicas.
You can enable the Directory Server Plug-in by using the following:
idsync dspluginconfig -{C/U} -D <bind DN> -w <bind pass word | -> [-h <CD hostname>] [-p <CD port no>] [-s <configuration suffix>] [-Z] [-P <cert db path>] [-m <secmod db path>] [-d <ds plugin hostname>] [-r <ds plug in port>] [-u <ds plugin user>] [-x <ds plugin user password>] [-o <database suf fix>][-q <configuration password | ->] [-W] [-B <plugin DS cert db path>] [-g <plugin DS secmod db path>]
Type idsync --help for information about the syntax.
When a directory server starts, the Directory Server Plug-in establishes a secure connection to the Directory Server Connector. After the plug-in is authenticated, the connector sends the configuration information, and the plug-in can send log messages to the central log, through the connector. The configuration includes keys for encrypting modified passwords and Active Directory information for performing on-demand password synchronization.
When a user's Active Directory password changes, Identity Synchronization for Windows sets the dspswvalidate attribute to true in the user's Directory Server entry. The user can then log in to any Directory Server, and on-demand password synchronization can originate from any server.
If the user logs in to master1-us.gt.com or master2-us.gt.com, on-demand password synchronization is performed directly to the ad1-us.gt.com Active Directory domain controller. Other domain controllers are contacted only if ad1-us.gt.com is unavailable.
If the user logs in to one of the other two preferred Directory Servers or one of the read-only replicas, on-demand password synchronization is performed against master1-us.gt.com or master2-us.gt.com. These preferred Directory Servers in turn continue the on-demand password synchronization to one of the Active Directory domain controllers.
These two actions are necessary for the following reasons:
-
A read-only replica cannot update the user's Directory Server entry with the correct password if on-demand password synchronization succeeds.
-
With the exception of the preferred and secondary Directory Servers, Identity Synchronization for Windows treats all Directory Server instances as read-only replicas.
After the primary installation is complete, the failover Identity Synchronization for Windows installation is performed on the two machines in Europe, config-eu.gt.com and connectors-eu.gt.com.
Figure 3–4 Failover Installation While the Primary Installation Is Active
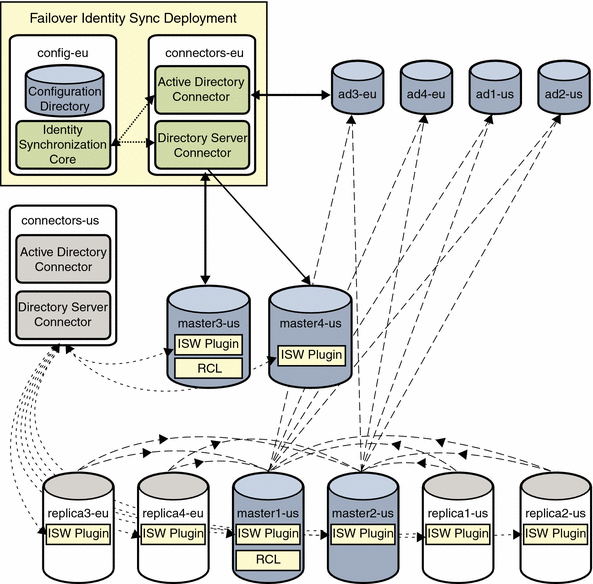
Because the Identity Synchronization for Windows Directory Server Plug-ins have not been reinstalled, so they still receive their configuration from the Directory Server Connector running on connectors-us.gt.com, while on-demand password synchronization passes through master1-us.gt.com or master2-us.gt.com before reaching the Active Directory domain controllers.
The failover installation remains in this state until Global Telco needs to fail over to it. To complete the failover process, the Identity Synchronization for Windows Plug-in is enabled on every directory server, which changes its startup configuration to communicate with the Directory Server Connector running on connectors-eu.gt.com.
Figure 3–5 Primary Installation After Reinstalling the Identity Synchronization for Windows Plug-ins

Note –
Setting up the failover installation significantly increases the amount of time required to deploy Identity Synchronization for Windows. However, this up-front cost is offset by having the ability to quickly fail over to the alternate deployment if necessary.
Periodically Linking New Users
Identity Synchronization for Windows is not used to synchronize the creation of new users. Therefore, the idsync resync command is executed periodically to establish links between newly created users. An LDAP filter is passed to this command to resynchronize only the subset of users that have been created since the command was last executed.
See Periodic idsync resync Operations for more information.
Large Deployment Considerations
Due to the large size of its deployment, Global Telco takes the following steps to increase the performance of Identity Synchronization for Windows.
-
Identity Synchronization for Windows components are distributed across two dedicated machines.
-
The log level is set to INFO except when diagnosing transient problems.
-
Message Queue Broker memory limits are increased (see the Sun Java System Directory Server Enterprise Edition 6.0 Installation Guide for more information).
-
The default number of worker threads in the connectors is increased.
-
The idsync resync command is run over batches of users to reduce the peak load on Message Queue.
Each of these actions is discussed in detail in the next section.
- © 2010, Oracle Corporation and/or its affiliates
