JAAS and Message Queue
Figure 9–2 shows how JAAS is used by the Message Queue broker. It shows a more complex implementation of the JAAS model shown in Figure 9–1.
Figure 9–2 How Message Queue Uses JAAS
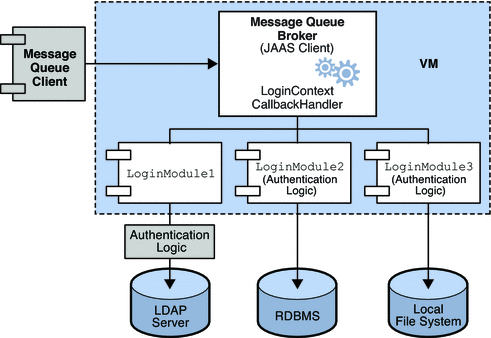
As in the simpler case, the authentication service layer is separate from the broker. The authentication service consists of one or more login modules, along with additional authentication modules if needed. The login modules run in the same Java virtual machine as the broker. The Message Queue broker is represented to the login module as a login context, and communicates with the login module by means of a callback handler that is part of the broker runtime code.
The authentication service also supplies a JAAS configuration file containing entries to the login modules. The configuration file specifies the order in which the modules are to be used and some conditions for their use. When the broker starts up, JAAS locates the configuration file by consulting either the Java system property java.security.auth.login.config or the Java security properties file. It then selects an entry in the JAAS configuration file according to the value of the broker property imq.user_repository.jaas.name. That entry specifies which login modules will be used for authentication. As the figure shows, it is possible for the broker to use more than one login module. (The relation between the configuration file, the login module, and the broker is shown in Figure 9–3.)
The fact that the broker uses a JAAS plug-in authentication service remains completely transparent to the Message Queue client. The client continues to connect to the broker as it did before, passing a user name and password. In turn, the broker uses a callback handler to pass this information to the authentication service, and the service uses the information to authenticate the user and return the results. If authentication succeeds, the broker grants the connection; if it fails, the client runtime returns a JMS security exception that the client must handle.
After the Message Queue client is authenticated, if there is further authorization to be done, the broker proceeds as it normally would, consulting the access control file to determine whether the authenticated client is authorized to perform the actions it undertakes: accessing a destination, consuming a message, browsing a queue, and so on.
- © 2010, Oracle Corporation and/or its affiliates
