Part II Deploying Messaging Server
This part contains the following chapters:
Chapter 9 Introduction to Messaging Server Software
Sun Java System Messaging Server is a powerful Internet messaging server designed for high-capacity, reliable handling of the messaging needs of both enterprises and service providers. The server consists of several modular, independently configurable components that provide support for several email protocols.
Messaging Server uses a centralized LDAP database for storing information about users, groups, and domains. Some information is stored in a set of local configuration files.
The Messaging Server product suite provides tools to support user provisioning and server configuration.
This chapter contains the following sections:
What Is a Messaging System?
A good email system architecture quickly delivers email with embedded sound, graphics, video files, and HTML forms, while providing for future upgrade and scalability. At a simplistic level, the Messaging Server architecture should:
-
Accept incoming mail from external sites
-
Determine the user mailbox to deliver these messages to and route them accordingly
-
Accept incoming mail from internal hosts
-
Determine the destination system to deliver these messages to and route them accordingly
Central to an email system architecture is the messaging server itself, a collection of components used to send and deliver messages. In addition to components provided in Messaging Server, the email system also requires an LDAP server and a DNS server. The DNS server must be in place before deploying your email system.
Several factors other than efficiency and scalability influence the Messaging Server architecture. Specifically these are:
See Chapter 11, Developing a Messaging Server Architecture for more information on these topics.
Messaging Server Support for Standards and Functionality
This section describes standards supported by Messaging Server, as well as other supported functionality.
Support for Standard Protocols
Messaging Server supports most national, international, and industry standards related to electronic messaging. For a complete list, see Appendix A, Supported Standards, in Sun Java System Messaging Server 6.3 Administration Reference.
Support for Hosted Domains
Messaging Server provides full support for hosted domains—email domains that are outsourced by an ISP. That is, the ISP provides email domain hosting for an organization by operating and maintaining the email services for that organization remotely. A hosted domain can share the same Messaging Server host with other hosted domains. In earlier LDAP-based email systems, a domain was supported by one or more email server hosts. With Messaging Server, many domains can be hosted on a single server. For each hosted domain, there is an LDAP entry that points to the user and group container for the domain and provides various domain-specific default settings.
When you define a domain, there must be a corresponding domain entry in the directory; that is, you must have an LDAP entry for the domain. Attributes such as mailAlternateAddress and mailEquivalentAddress depend on the existence of domain entries in the directory. Contrast this with vanity domains, which are domain names associated with an individual user, not with a specific server or hosted domain. The vanity domain does not have an LDAP entry for the domain name.
Note –
Because of their increased operational overhead, vanity domains are not recommended.
Support for User Provisioning
Messaging Server uses a centralized LDAP database for storing information about users, groups, and domains. At this time, Messaging Server supports two schema options, Sun Java System LDAP Schema version 1 (Schema 1) and Sun Java System LDAP Schema version 2 (Schema 2). The provisioning options will depend on which schema you have chosen. See Appendix A, Messaging Server Pre-Installation Considerations and Procedures, in Sun Java Communications Suite 5 Installation Guide for more information.
Messaging Server provisioning for Schema 2 is done using Delegated Administrator, as documented in the Sun Java System Delegated Administrator 6.4 Administration Guide. Delegated Administrator provides a graphical user interface and a set of command-line utilities for managing the users, groups, domains, resources, and service packages within an organization.
Schema 1 is supported by the iPlanet Delegated Administrator for Messaging product, which provides a graphical user interface and a set of command-line utilities for managing the users, groups, and domains within an organization. You can also use the following documentation, pertaining to previous software releases, for managing users, groups, and domains in Schema 1:
-
iPlanet Messaging Server 5.2 Provisioning Guide - Describes how to create domain, user, group, or administrator entries using LDAP
-
iPlanet Messaging and Collaboration Schema Reference - Describes Schema 1 for Communications Suite
-
iPlanet Messaging Server 5.2 Reference Manual - Describes the iPlanet Delegated Administrator command-line utilities for managing users, groups, and domains
-
iPlanet Delegated Administrator online help
Note –
Access Manager console provides minimal Messaging Server and Calendar Server LDAP user entry provisioning using Access Manager Services. Because the interface provides no input validation, user entries that cannot receive email or otherwise don’t function will be created without reporting any errors. As a result, use this interface for demonstration purposes only.
Delegated Administrator, which is described in the Sun Java System Delegated Administrator 6.4 Administration Guide, is the recommended mechanism for provisioning Communications Suite users.
Support for Unified Messaging
Messaging Server provides the basis for a complete unified messaging solution: the concept of using a single message store for email, voicemail, fax, video, and other forms of communication.
Support for Webmail
Messaging Server currently ships with two native client user interfaces (UI):
-
Messenger Express
-
Communications Express
Going forward, no new features will be added to the Messenger Express user interface. It has been deprecated in favor of the Communications Express user interface. Sun Microsystems, Inc. will announce an end-of-life timeline for Messenger Express at a future date.
See the Communications Express documentation for more information:
http://docs.sun.com/app/docs/coll/1312.1
Messaging Server Security and Access Control
Messaging Server provides the following security and access control features:
-
Support for password login and certificate-based login to POP, IMAP, HTTP, or SMTP
-
Support for email encryption using S/MIME
-
Support for standard security protocols: Transport Layer Security (TLS), Secure Sockets Layer (SSL) and Simple Authentication and Security Layer (SASL)
-
Delegated administration
-
Client IP address access filters to POP, IMAP, SMTP, and HTTP
-
Filtering of unsolicited bulk email using system-wide, per-user, and server-side Sieve rules
-
Support for milter-based email filtering
Messaging Server Administration User Interfaces
Messaging Server consists of several modular, independently configurable components that provide support for email transport and access protocols.
To configure the Message Transfer Agent (MTA), Messaging Server provides a complete set of command-line utilities and configuration files stored locally on the server. To configure the Message Store and message access services, Messaging Server provides a complete set of command-line utilities.
See the Sun Java System Messaging Server 6.3 Administration Guide for more information.
Messaging Server Software Architecture
Figure 9–1 shows a simplified standalone view of Messaging Server. While this particular deployment is not recommended for large deployment because it does not scale well, it does illustrate the individual components of the server.
Figure 9–1 Standalone Messaging Server, Simplified Components View
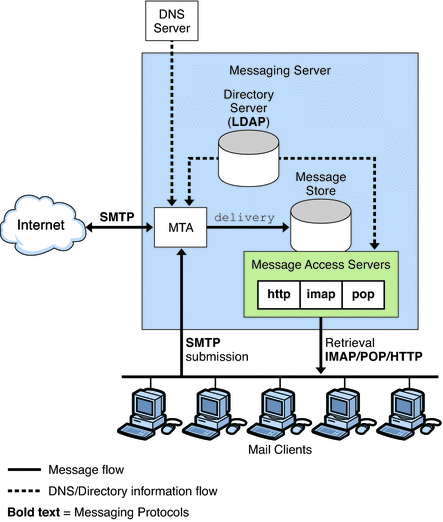
The preceding figure shows the following Messaging Server software components:
-
Message Transfer Agent or MTA. Receives, routes, transports, and delivers mail messages using the SMTP protocol. An MTA delivers messages to a local mailbox or to another MTA.
-
Message Store. Consists of a set of components that store, retrieve, and manipulate messages for mail clients. Mail can be retrieved by POP, IMAP, or HTTP clients. POP clients download messages to the client machine for reading and storage. IMAP and HTTP clients read and manipulate messages on the server.
-
LDAP directory. Stores, retrieves, and distributes mail directory information for Messaging Server. This includes user routing information, distribution lists, and other information necessary to support delivery and access of email. The LDAP directory also stores passwords, and any other information needed by the MTA or Message Store to authenticate users.
In addition to storing messages, the Message Store uses the directory server to verify user login name and passwords for mail clients accessing their mail. The directory also stores information about quota limits, default message store type, and so on.
-
DNS Server. Translates domain names into IP addresses. This component needs to be present before Messaging Server is installed.
Message Path Through the Simplified Messaging Server System
Incoming messages from the Internet or local clients are received by the MTA through the Simple Mail Transport Protocol (SMTP). If the address is internal, that is, within the Messaging Server domain, the MTA delivers the message to the Message Store. If the message is external, that is, addressed to a domain outside of Messaging Server control, the MTA relays the message to another MTA on the Internet.
Although it is possible to deliver mail to the /var/mail file system (UNIX systems only), which was the case in previous versions of the Messaging Server, local messages are usually delivered to the more optimized Messaging Server Message Store. Messages are then retrieved by IMAP4, POP3, or HTTP mail client programs.
Outgoing messages from mail clients go directly to the MTA, which sends the message to the appropriate server on the Internet. If the address is local, the MTA sends the message to the Message Store.
New users and groups are created by adding user and group entries to the directory. Entries can be created or modified by using the Delegated Administrator utility or by modifying the directory using LDAP.
Messaging Server provides a set of command-line administrative interfacs and configuration files. Some of the more common administrative tasks are adding, modifying, and removing users and groups to the mail system, and configuring the operation of the MTA, directory server, and Message Store.
The Message Transfer Agent (MTA)
The MTA routes, transfers, and delivers Internet mail messages for Messaging Server. Mail flows through interfaces known as channels. Each channel consists of one or a pair of agent programs and a set of configuration information. The agent programs are a slave program, which handles mail coming into the channel, and a master program, which handles mail as it leaves the channel. There is a message queue for storing messages that are destined to be sent to one or more of the interfaces associated with any channel. Messaging Server provides a number of default channels, including:
-
SMTP Channel. Enables TCP/IP-based message delivery and receipt. Both master and slave channels are provided.
-
LMTP Channel. Enables routing of messages directly from MTAs to the Message Store in a two-tiered configuration. These channels communicate with the Message Store on another system over LMTP instead of SMTP. Both master and slave channels are provided.
-
Pipe Channel. Used for alternative message delivery programs. Enables delivery of messages to programs such as a mail sorter rather than directly to a user’s inbox. A master channel is provided.
-
Local Channel. Delivers mail to /var/mail. Provides for compatibility with older UNIX mail clients. A master channel is provided.
-
Reprocessing Channel. Useful for messages that are resubmitted. A master channel is provided.
-
Defragmentation Channel. Reassembles partial messages into the original complete message to support the MIME message/partial content type. A master channel is provided.
-
Conversion Channel. Performs body part by body part conversion on messages. Useful for rewriting addresses or re-formatting messages. A master channel is provided.
-
Message Store Channel. Provides for local delivery to the message store.
Figure 9–2 illustrates the process. You can configure channels individually and direct mail to specific channels based on the address.
Figure 9–2 Channel Architecture
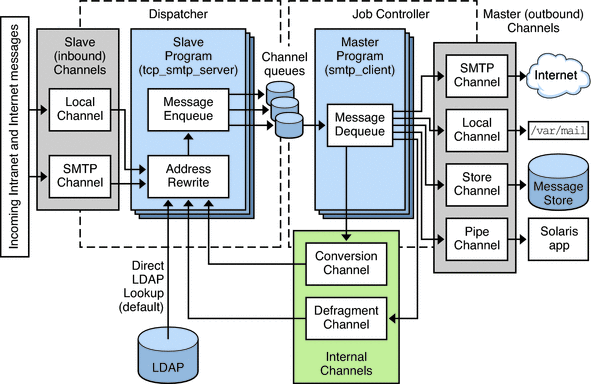
Channel programs perform one of two functions:
-
SMTP slave programs enqueue messages into message queues for further processing by the MTA, or reject the message so it is not accepted onto the system, and accept messages from other interfaces.
-
Master programs process the message from its queue area, and enqueue it on the same system for further processing by another channel, or transmit messages off system to other interfaces, deleting them from their queue after they are sent, or deliver the message to the final destination on the system, such as the Message Store.
Channels are configurable by using the imta.cnf configuration text file. Through channel configuration, you can set a variety of channel keywords to control how messages are handled. Channel keywords affect performance tuning as well as reporting aspects of the system. For example, you can define multiple channels to segment traffic by destination, define message size limits to limit traffic, and define delivery status notification rules according to the needs of your business. Diagnostic attributes are also configurable on a per-channel basis. The number of configuration parameters that can be set on a channel basis is large.
See Chapter 8, MTA Concepts, in Sun Java System Messaging Server 6.3 Administration Guide for more information on MTA concepts.
Direct LDAP Lookup
The MTA looks up the information directly from the LDAP server. The direct lookup provides a scalable, fast, and configurable relationship between the MTA and the LDAP server. The results of the LDAP queries are cached in the process, with configurable size and time, so performance is tunable. See the Sun Java System Messaging Server 6.3 Administration Guide for more information.
Rewrite Rules
Mail is routed to a channel based on the result of running the destination addresses through domain rewriting rules, or rewrite rules for short. Rewrite rules are used to convert addresses into true domain addresses and to determine their corresponding channels. These rules are used to rewrite addresses appearing in both the transport layer and the message header. The transport layer is the message’s envelope. It contains routing information and is invisible to the user, but is the actual information used to deliver the message to the appropriate recipient.
The rewrite rules and the table of channels cooperate to determine the disposition of each address. The result of the rewrite process is a rewritten address and a routing system, that is, the system (channel) to which the message is to be sent/queued. Depending upon the topology of the network, the routing system might only be the first step along the path the message takes to reach its destination, or it might be the final destination system itself.
After the rewrite process has finished, a search is made for the routing system among the channel portion of the imta.cnf file. Each channel has one or more host names associated with it. The routing system name is compared against each of these names to determine to which channel to enqueue the message. A simple rewrite rule is shown here:
example.com $U%example.com@tcp_siroe-daemon
This rule matches addresses for the domain example.com only. Such matching addresses would be rewritten using the template $U%$D, where:
- $U
-
Indicates the user portion or left-hand side of the address (before the @)
- %
-
Indicates the @ sign
- $D
-
Indicates the domain portion or right-hand side of the address (after the @)
Thus, a message of the form wallaby@thor.example.com would be rewritten to wallaby@example.com, and would be sent to the channel whose channel host name is tcp_siroe-daemon.
Rewrite rules can perform sophisticated substitutions based on mapping tables, LDAP directory lookups, and database references. While occasionally cryptic, they are useful in the fact that they operate at a low level and impose little direct overhead on the message processing cycle. For full information on these and other features available in the rewrite process, see Chapter 11, Configuring Rewrite Rules, in Sun Java System Messaging Server 6.3 Administration Guide.
The Job Controller
Master channel programs are run under the control of the job controller, a program that controls the message queues and invokes the channel programs to do the actual message delivery. The job controller is a multithreaded process and is one of the few processes that is always present in the Messaging Server system. The channel processing jobs themselves are created by the job controller but are transient and might not be present when there is no work for them to do.
Job controller configuration settings determine if there is always at least one instance of a channel processing program. In many cases, these are set so that there is always at least one instance of the service program even when there is no immediate work to do. In other cases, there will be an instance for a set period of time after it last did some work but there is nothing to do currently.
Slave channels, which accept external messages, by queueing a message, notify the job controller of a newly created message file. The job controller enters this information into its internal data structure and if necessary creates a master channel job to process the message in that queue. This job creation might not be necessary if the job controller determines that an existing channel job can process the newly queued message file. When the master channel job starts, it gets its message assignment from the job controller. When it is finished with the message, the master channel updates the job controller as to the status of its processing. The status is either that the message is successfully dequeued or the message should be rescheduled for retrying.
The job controller maintains information about message priority and previous delivery attempts that failed, allowing for advantageous scheduling of channel jobs. The job controller also keeps track of the state of each job. The state can be idle, how long the job has been idle, or whether the job is busy. Tracking state enables the job controller to keep an optimal pool of channel jobs.
Note –
There are currently only two slave channels, SMTP slave and LMTP slave. These programs are controlled by the dispatcher, which is described next.
Dispatcher
The dispatcher is another process that is always present on a Messaging Server system. It is a multithreaded traffic dispatcher, which dispatches incoming SMTP or LMTP connections to the pool of SMTP or LMTP server threads for protocol-specific processing. The SMTP and LMTP server programs provide a pool of worker threads at the disposal of the dispatcher. After it processes a message by either rejecting the message or enqueuing it into its destination channel, the worker thread is ready to accept more work from the dispatcher.
The dispatcher can block incoming traffic based on IP address and throttles it to prevent denial of service attacks. It also creates and shuts down SMTP or LMTP server processes based on load and configuration. Therefore the SMTP or LMTP slave channel programs are under the control of the dispatcher, not the job controller.
Local Mail Transfer Protocol (LMTP)
As of the Messaging Server 6.0 release, you can configure LMTP for delivery to the Message Store in a multi-tiered deployment. In these scenarios, where you are using inbound relays and back-end Message Stores, the relays become responsible for address expansion and delivery methods such as autoreply and forwarding and also for mailing list expansion.
Delivery to the back-end stores historically has been over SMTP, which requires the back-end system to look up the recipient addresses in the LDAP directory again, thereby engaging the full machinery of the MTA. For speed and efficiency, the MTA can use LMTP rather than SMTP to deliver messages to the back-end store. See Chapter 16, LMTP Delivery, in Sun Java System Messaging Server 6.3 Administration Guide for more information.
Note –
By design, LMTP is intended for use in multi-tier deployments. It is not possible to use LMTP with single-system deployments. Also, the Messaging Server’s LMTP service as implemented is not designed to work with other LMTP servers or other LMTP clients.
The Message Store
The Message Store is a dedicated data store for the delivery, retrieval, and manipulation of Internet mail messages. The Message Store works with the IMAP4 and POP3 client access servers to provide flexible and easy access to messaging. The Message Store also works through the HTTP server (mshttpd) to provide messaging capabilities to Communications Express in a web browser. In addition to this section, see Chapter 20, Managing the Message Store, in Sun Java System Messaging Server 6.3 Administration Guide for more information.
The Message Store is organized as a set of folders or user mailboxes. The folder or mailbox is a container for messages. Each user has an INBOX where new mail arrives. Each IMAP or Webmail user can also have one or more folders where mail can be stored. Folders can contain other folders arranged in a hierarchical tree. Mailboxes owned by an individual user are private folders. Private folders can be shared at the owner’s discretion with other users on the same Message Store. Messaging Server supports sharing folders across multiple stores by using the IMAP protocol.
There are two general areas in the Message Store, one for user files and another for system files. In the user area, the location of each user’s INBOX is determined by using a two-level hashing algorithm. Each user mailbox or folder is represented by another directory in its parent folder. Each message is stored as a file. When there are many messages in a folder, the system creates hash directories for that folder. Using hash directories eases the burden on the underlying file system when there are many messages in a folder. In addition to the messages themselves, the Message Store maintains an index and cache of message header information and other frequently used data to enable clients to rapidly retrieve mailbox information and do common searches without the need to access the individual message files.
A Message Store can contain many message store partitions for user files. A Message Store partition is contained by a file system volume. As the file system becomes full, you can create additional file system volumes and Message Store partitions on those file system volumes to store new users.
Note –
If the partition gets full, users on the partition will not be able to store additional messages. There are several ways to address the problem:
-
Reduce the size of user mailboxes
-
If you are using volume management software, add additional disks
-
Create additional partitions and move mailboxes to the new partitions
For more information, see Chapter 20, Managing the Message Store, in Sun Java System Messaging Server 6.3 Administration Guide.
The Message Store maintains only one copy of each message per partition. This is sometimes referred to as a single-copy message store. When the Message Store receives a message addressed to multiple users or a group or distribution list, it adds a reference to the message in each user’s INBOX. Rather than saving a copy of the message in each user’s INBOX, Message Store avoids the storage of duplicate data. The individual message status flag (seen, read, answered, deleted, and so on) is maintained per folder for each user.
The system area contains information on the entire Message Store in a database format for faster access. The information in the system area can be reconstructed from the user area. Messaging Server contains a database snapshot function. When needed, you can quickly recover the database to a known state. Messaging Server also has fast recovery, so that in case of database corruption, you can shut down the Message Store and bring it back immediately without having to wait for a lengthy database reconstruction.
The Message Store supports per-user quotas. Enforcement of quota can be turned on or off. You can configure a user quota by using number of bytes or number of messages. You can also set a threshold so that if the quota reaches the threshold, a warning message can be sent to the user. When the user is over quota, new messages can be held up for retry during a grace period. After the grace period, messages sent to the over-quota user are returned to the sender with a non-delivery notification.
For special applications where quota is used, but messages must be delivered regardless of the quota status of the users, there is a guaranteed message delivery channel. This channel can be used to deliver all messages regardless of quota status. Utilities are available for reporting quota usage and for sending over quota warnings.
Messaging Server and Directory Services
Messaging Server is bundled with Sun Java System Directory Server. Directory Server is a Lightweight Directory Access Protocol (LDAP) directory service. Directory Server provides the central repository for information critical to the operation of Messaging Server. This information includes user profiles, distribution lists, and other system resources.
Directory Information Tree
The directory stores data in the form of a tree, known as the Directory Information Tree (DIT). The DIT is a hierarchical structure, with one major branch at the top of the tree and branches and subbranches below. The DIT is flexible enough to enable you to design a deployment that fits your organization’s needs. For example, you might choose to arrange the DIT according to your actual business organizational structure, or by the geographical layout of your business. You also might want to design a DIT that follows a one-to-one mapping to your DNS layers. Use care when designing your DIT, as changing it after the fact is not an easy task.
The DIT is also flexible enough to accommodate a wide range of administration scenarios. You can administer the DIT in either a centralized or distributed manner. In centralized administration, one authority manages the entire DIT. You would use centralized administration where the entire DIT resides on one mail server. In distributed administration, multiple authorities manage the DIT. Usually you implement distributed administration when the DIT is divided into portions, or subtrees, residing on different mail servers.
When the DIT is large, or when mail servers are geographically disbursed, consider delegating management of portions of the DIT. Typically, you assign an authority to manage each subtree of the DIT. Messaging Server enables you to manage multiple subtrees from one authority. However, for security reasons, an authority can only make changes to the subtree of the DIT that the authority owns.
The default schema used by Messaging Server when Access Manager is not used is different from the one used by Access Manager. Messaging Server supports both Sun Java System LDAP Schema 1 and 2, and allows for transition and migration of the schemas.
Directory Replication
Directory Server supports replication, enabling a variety of configurations that provide redundancy and efficiency. Enabling replication of all or part of the DIT from one host to other hosts provides the following configuration capabilities:
-
The directory information is more accessible, because it is replicated on multiple servers rather than on a single server.
-
The directory information can be cached on a local directory server, reducing effort of accessing the information from a remote directory server. Caching the directory information enhances performance, especially in deployments with limited network bandwidth to the central directory.
-
Depending on the actual configuration, multiple directory servers can process mail client requests faster than a single centralized server.
For more information on directory replication, directory performance tuning, and DIT structure and design, see the Sun Java System Directory Server documentation:
http://docs.sun.com/app/docs/coll/1316.1
Provisioning Messaging Users
See Chapter 8, Understanding Schema and Provisioning Options for information on schema and provisioning options for Messaging Server users.
Message Archiving Using the AXS-One System
Messaging Server supports archiving through the AXS-One message archiving system. Whether you require archiving for regulatory, compliance or legislative purposes, or you wish to manage the growth of your message store or reduce the storage costs, the AXS-One messaging archiving system can help them to achieve both, individually, or simultaneously.
For more information on how to connect the AXS-One archiving system to Sun Java System Messaging Server, see Message Archiving Using the Sun Compliance and Content Management Solution.
Chapter 10 Planning a Messaging Server Sizing Strategy
When you design your deployment, you must decide how to configure your Messaging Server to provide optimum performance, scalability, and reliability.
Sizing is an important part of this effort. The sizing process enables you to identify what hardware and software resources are needed so that you can deliver your desired level of service or response time according to the estimated workload that your Messaging Server users generate. Sizing is an iterative effort.
This chapter introduces the basics of sizing your Messaging Server deployment to enable you to obtain the right sizing data by which you can make deployment decisions. It also provides the context and rationale for the Messaging Server sizing process.
The chapter contains the following sections:
Note –
Because each deployment has its own set of unique features, this chapter does not provide detailed sizing information for your specific site. Rather, this chapter explains what you need to consider when you architect your sizing plan. Work with your Sun technical representative for your deployment hardware and software needs.
Collecting Messaging Server Sizing Data
Use this section to identify the data you need to size your Messaging Server deployment. The following topics are covered in this section:
Determining Messaging Peak Volume
Your peak volume is the largest concentrated numbers of transactions to your messaging system within a given period in a day. The volume can vary from site to site as well as across different classes of users. For example, peak volume among a certain class of managers in a medium-sized enterprise might occur from 9 to 10 in the morning, 12 to 1 in the afternoon, and 5 to 6 in the evening.
Analyzing peak volume involves three basic operations:
-
Determining when and for how long the peaks occur
-
Sizing your deployment against peak volume load assumptions
Once patterns are analyzed, choices can be made to help the system handle the load and provide the services that users demand.
-
Making sure that your Messaging Server deployment can support the peak volume that you have determined.
Creating Your Messaging Usage Profile
Measuring your load is important for accurate sizing. Your usage profile determines the factors that programs and processes place on your Messaging Server hosts.
This section helps you create your usage profile to measure the amount of load that is placed on your deployment.
To create a usage profile, answer the following questions:
-
What is the number of users on your system?
When counting the number of users on your system, account for not only the users who have mail accounts and can log in to the mail system, but also the users with mail accounts who are currently not logged onto the system. In particular, note the difference between active and inactive users:
User
Description
Active User
A user who is logged into mail systems through mail access protocols like POP, IMAP, or HTTP. Depending on the type of access protocol, active users might or might not have connections to the mail server at any given time.
For example, POP users can have a mail client open, but the POP connection established by the mail client to the server is short in duration and periodic.
Active users in this discussion are not the same as mail attributes with active status, such as mailuserstatus or inetuserstatus. For more information on mail attributes, see Sun Java Communications Suite 5 Schema Reference.
Inactive User
A user with a mail account who currently is not using the mail system.
If you have a very small deployment (for example, under 300 users), you might not need to go through this process of planning a sizing strategy. Work with your Sun Client Services representative to determine your individual needs.
-
How many connections are on your system during your peak volume for your POP, IMAP, and Messenger Express client access services?
Specifically, note the number of concurrent, idle, and busy connections for each client access service that you support:
To determine the number of concurrent connections in your deployment, do one of the following:
-
Count the number of established TCP connections by using the netstat command on UNIX platforms.
-
Obtain the last login and logout times for Messenger Express or for IMAP users. See the Sun Java System Messaging Server 6.3 Administration Guide for more information.
-
-
If you have a large deployment, how will you organize your users?
Some options include but are not limited to:
-
Placing active users and inactive users together on separate machines from one another
If an inactive user becomes an active user, that user can be moved to the active user machines. This approach could decrease the amount of needed hardware, rather than placing inactive and active users together on a machine.
-
Separating users by Class of Service
You might separate individual contributors, managers, and executives on machines that offer different mail storage space allocation for each class of service, different privileges, and specialized services.
-
-
What is the amount of storage used on each mailbox?
When you measure the amount of storage per mailbox, you should estimate real usage per mailbox, not the specified quota. Messages in trash or wastebasket folders still take up disk space and quota.
-
How many messages enter your messaging system from the Internet?
The number of messages should be measured in messages per second during your peak volume.
-
How many messages are sent by your users to:
-
End users on your mail system?
-
The Internet?
This number of messages is also measured in messages per second during the peak volume.
-
-
What is the distribution of messages in different size ranges?
For example:
-
Less than 5 Kbytes?
-
Between 5 Kbytes - 10 Kbytes?
-
Between 10 Kbytes -100 Kbytes?
-
Between 100 Kbytes - 500 Kbytes?
-
Between 500 Kbytes -10 MB?
-
Greater than 10 MB?
If the distribution of message sizes is not available, use the average message size on your mail system, however it is not as effective as size ranges.
The size of messages is particularly important, because it affects the rate of delivery of the MTA, the rate of delivery into the Message Store, the rate of message retrieval, and processing by anti-virus or anti-spam filters.
-
-
Will you be using SSL/TLS? If yes, what percentage of users and what type of users?
For example, in a particular organization, 20 percent of IMAP connections during peak hours will enable SSL.
-
Do you plan on using any SSL crypto accelerator hardware?
-
Will you be using virus scanning or other specialized message processing and will this processing be enabled for all users?
Depending on your Messaging Server configuration, the MTA will need to scan all messages to match criteria specified in specialized processing, thus increasing load on the system.
-
For POP users, will you have a policy restricting how often they can access mail? If so, how often?
-
For IMAP users, will you enforce a standard client or allow users to choose their own?
Different IMAP clients make different numbers of concurrent connections to the server. Thus, a power user with many open folders might have many concurrent connections.
-
Will you allow users to share folders? If so, will you allow all users or only some?
Answering these questions provides a preliminary usage profile for your deployment. You can refine your usage profile as your Messaging Server needs change.
Additional Questions
While the following questions are not applicable to creating your usage profile, they are important to developing your sizing strategy. How you answer these questions might require you to consider additional hardware.
-
How much redundancy do you want in your deployment?
For example, you might consider high availability. Consider how much down time is allowed, and if you need clustering technology.
-
What backup and restore strategy do you have in place (such as disaster recovery, mailbox restores, and site failover)? What are the expected times to accomplish recovery tasks?
-
Do you need a DMZ to separate your internal and external networks? Are all users using the internal network? Or do some of them connect by using the Internet?
You might need MMP proxy servers and separate MTA layers.
-
What are your response time requirements? What are your throughput requirements?
-
What is your specific criteria for resource utilization? Can your CPUs be 80 percent busy on average? Or only at peak?
-
Will you have messaging servers at different geographic locations? Do you expect users’ mail to be located geographically?
-
Do you have archiving requirements for keeping mail messages for a certain length of time?
-
Do you have legal requirements to log all messages? Do you need to keep a copy of every message sent and received?
Defining Your Messaging User Base
Once you establish a usage profile, compare it to sample pre-defined user bases that are described in this section. A user base is made up of the types of messaging operations that your users will perform along with a range of message sizes that your users will send and receive. Messaging users fall into one of five user bases:
The sample user bases described in this section broadly generalize user behavior. Your particular usage profile might not exactly match the user bases. You will be able to adjust these differences when you run your load simulator (as described in Using a Messaging Server Load Simulator).
Lightweight POP
A lightweight POP user base typically consists of residential dial-up users with simple messaging requirements. Each concurrent client connection sends approximately four messages per hour. These users read and delete all of their messages within a single login session. In addition, these users compose and send few messages of their own with just single recipients. Approximately 80 percent of messages are 5 Kbytes or smaller in size, and about 20 percent of messages are 10 Kbytes or larger.
Heavyweight POP
A heavyweight POP user base typically consists of premium broadband users or small business accounts with more sophisticated messaging requirements than the lightweight POP user base. This group uses cable modem or DSL to access its service provider. Each concurrent client connection sends approximately six messages per hour. Messages average about two recipients per message. Sixty-five percent of messages are 5 Kbytes or smaller in size. Thirty percent of messages in this user base are between 5-10 Kbytes. Five percent of messages are larger than 1 Mbyte. Of these users, 85 percent delete all of their messages after reading them. However, 15 percent of users leave messages on the server through several logins before they delete them. Mail builds up in a small portion of those mailboxes. In some cases, the same message can be fetched several times from the server.
Lightweight IMAP
A lightweight IMAP user base represents users that enable premium broadband Internet services, including most of the advanced features of their messaging systems like message searching and client filters. This user base is similar to heavyweight POP with regard to message sizes, number of recipients, and number of messages sent and received by each concurrent connection. Lightweight IMAP users typically log in for hours at a time and delete most or all mail before log out. Consequently, mail stacks up in a mailbox during a login session, but user generally do not store more than 20 to 30 messages in their mailboxes. Most inboxes contain less than 10 messages.
Mediumweight IMAP
A mediumweight IMAP user base represents sophisticated enterprise users with login sessions lasting most of an eight hour business day. These users send, receive, and keep a large amount of mail. Furthermore, these users have unlimited or very large message quotas. Their inboxes contain a large amount of mail that grows during the day, and is fully or partially purged in large spurts. They regularly file messages into folders and search for messages multiple times per hour. Each concurrent client connection sends approximately eight messages per hour. These users send messages with an average of four recipients and have the same message size mix as the Heavyweight POP and Lightweight IMAP user bases.
Mediumweight Messenger Express/Communications Express
A mediumweight Messenger Express/Communications Express user base is similar to Mediumweight IMAP. This user base has the same message size mix as Mediumweight IMAP, Lightweight IMAP, and Heavyweight POP. And, the message delivery rates are the same as Mediumweight IMAP users.
It is likely that you will have more than one type of user base in your organization, particularly if you offer more than one client access option. Once you identify your user bases from these categories, you will test them with your usage profile and with a load simulator, described in Using a Messaging Server Load Simulator.
Using a Messaging Server Load Simulator
To measure the performance of your Messaging Server, use your messaging user bases (described in Defining Your Messaging User Base) and your messaging usage profile (described in Creating Your Messaging Usage Profile) as inputs into a load simulator.
A load simulator creates a peak volume environment and calibrates the amount of load placed on your servers. You can determine if you need to alter your hardware, throughput, or deployment architecture to meet your expected response time, without overloading your system.
 To Use a Load Simulator
To Use a Load Simulator
-
Define the user base that you want to test (for example, Lightweight IMAP).
If necessary, adjust individual parameters to best match your usage profile.
-
Define the hardware that will be tested.
-
Run the load simulator and measure the maximum number of concurrent connections on the tested hardware with the user base.
-
Publish your results and compare those results with production deployments.
-
Repeat this process using different user bases and hardware until you get the response time that is within an acceptable range for your organization under peak load conditions.
Note –Contact Sun Client Services for recommended load simulators and support.
Assessing Your Messaging Server System Performance
Once you evaluate your hardware and user base with a load simulator, you need to assess your system performance. The following topics address methods by which you can improve your overall system performance.
Messaging Server Memory Utilization
Make sure you have an adequate amount of physical memory on each machine in your deployment. Additional physical memory improves performance and enables the server to operate at peak volume. Without sufficient memory, Messaging Server cannot operate efficiently without excessive swapping.
At minimum, be sure to have 1 GB of memory per CPU. For most deployments, you will want 2 GB of memory per CPU with UltraSPARC® III systems.
Messaging Server Disk Throughput
Disk throughput is the amount of data that your system can transfer from memory to disk and from disk to memory. The rate at which this data can be transferred is critical to the performance of Messaging Server. To create efficiencies in your system’s disk throughput:
-
Consider your maintenance operations, and ensure you have enough bandwidth for backup. Backup can also affect network bandwidth particularly with remote backups. Private backup networks might be a more efficient alternative.
-
Carefully partition the store and separate store data items (such as tmp and db) to improve throughput efficiency.
-
Ensure the user base is distributed across RAID (Redundant Array of Independent Disks) environments in large deployments.
-
Stripe data across multiple disk spindles in order to speed up operations that retrieve data from disk.
-
Allocate enough CPU resources for RAID support, if RAID does not exist on your hardware.
You want to measure disk I/O in terms of IOPS (total I/O operations per second) not bandwidth. You need to measure the number of unique disk transactions the system can handle with a very low response time (less than 10 milliseconds).
Messaging Server Disk Capacity
When planning server system disk space, you need to be sure to include space for operating environment software, Messaging Server software, and message content and tracking. Be sure to use an external disk array if availability is a requirement. For most systems, external disks are required for performance because the internal system disks supply no more than four spindles.
For the Message Store partitions, the storage requirement is the total size of all messages plus 30 percent overhead.
In addition, user disk space needs to be allocated. Typically, this space is determined by your site’s policy.
Note –
Your deployment planning needs to include how you want to back up the Message Store for disaster recovery. Messaging Server supports Solstice Backup (Legato Networker), the imsbackup utility, and file system snapshot backup. You might want to store your backup media remotely. The more frequently you perform a backup, the better, as long as it doesn’t impact server operations.
Disk Sizing for MTA Message Queues
The behavior of the Messaging Server MTA Queue is to provide a transient store for messages waiting to be delivered. Messages are written to disk in a persistent manner to maintain guaranteed service delivery. If the MTA is unable to deliver the message, it will retry until it finally gives up and returns the message to the sender.
Message Queue Performance
Sizing the MTA Queue disks are an important step for improving MTA performance. The MTA's performance is directly tied to disk I/O first above any other system resource. This means that you should plan on disk volume that consists of multiple disk spindles, which are concatenated and stripped by using a disk RAID system.
End users are quickly affected by the MTA performance. As users press the SEND button on their email client, the MTA will not fully accept receipt of the message until the message has been committed to the Message Queue. Therefore, improved performance on the Message Queue results in better response times for the end-user experience.
Message Queue Availability
SMTP services are considered a guaranteed message delivery service. This is an assurance to end users that the messaging server will not lose messages that the service is attempting to deliver. When you architect the design of the MTA Queue system, all effort should be made to ensure that messages will not be lost. This guarantee is usually made by implementing redundant disk systems through various RAID technologies.
Message Queue Available Disk Sizing
The queue will grow excessively if one of the following conditions occurs:
-
The site has excessive network connectivity issues
-
The MTA configuration is holding on to messages too long
-
There are valid problems with those messages (not covered in this document)
The following sections address these issues.
Planning for Network Connectivity Issues
Occasionally the MTA is unable to deliver messages due to network connectivity issues. In these cases, the messages will be stored on the queue until the next time the MTA is able to attempt to deliver (as defined by the retry interval).
Planning on disk space for these outages is based on a simple rule, the “General Rule for Message Queue Sizing:”
-
Determine average number of messages/minute expected to be delivered (N).
-
Determine average size (kb) of messages (S).
-
Determine maximum duration (minutes) of typical network connectivity outages (T).
Thus, the formula for estimating the Disk Queue Size is:
Disk Queue Size (kb) = N x S x T
Tuning MTA for Reattempts of Delivery
Occasionally, the system will not be able to deliver any messages. In this state, messages will reside on the message queue while the MTA attempts to set aside the messages for a period of time (retry interval) until it reattempts the delivery. This will continue until the MTA gives up and returns the message to the sender. The reason a message is undeliverable is fairly unpredictable. A number of reasons such as network connectivity, busy destination server, network throttles, and so on, could explain why the message is undeliverable.
On a busy server, these temporarily stored messages can build up during periods of high volume activities. Such a build-up can potentially cause problems with disk space. To avoid these build-ups, tune the MTA to retry delivery at a faster rate.
The retry interval is set within the Channel Block configurations of the imta.cnf file. The structure of this file consists of two parts: rewrite rules and channel blocks. The channel blocks define the behavior of a particular disk queue and related processes. This discussion refers to the tcp_local channel. The tcp_local channel provides delivery to sites outside an enterprise's local network, in other words, to places over the Internet.
The retry interval setting of the tcp_local channel is initially set by the default channel block. The default channel block allows settings to be duplicated to avoid having repeated settings.
The following is the default channel block:
defaults notices 1 2 4 7 copywarnpost copysendpost postheadonly noswitchchannel immnonurgent maxjobs 7 defaulthost red.siroe.com red.siroe.com |
First, the structure of the channel block consists of the channel name. In the example above, this is the default channel block, which will be applied to channels without these settings. The second part is a list of channel keywords.
The notices keyword specifies the amount of time that can elapse before message delivery notices (MDNs) are sent back to the sender. This keyword starts with the notices keyword followed by a set of numbers, which set the retry period. By default, the MTA will attempt delivery and send notices back to the sender. These notices come from “postmaster” to end-user inboxes.
In this example, the MTA will retry at a period of 1 day, 2 days, and 4 days. At 7 days, the MTA will return the message and regard the message as a failed delivery.
In many cases, the default setting of the MTA provides adequate performance. In some cases, you need to tune the MTA to avoid potential resource exhaustions, such as running out disk space for message queues. This is not a product limitation, but a limitation of the total Messaging Server system, which includes hardware and network resources.
In consideration of these possible disk size issues, deployments with a large number of users may not want to attempt message deliveries for much shorter intervals. If this is the case, study the documentation listed below.
Further Readings
Refer to the following documentation for more information.
Messaging Server Network Throughput
Network throughput is the amount of data at a given time that can travel through your network between your client application and server. When a networked server is unable to respond to a client request, the client typically retransmits the request a number of times. Each retransmission introduces additional system overhead and generates more network traffic.
You can reduce the number of retransmissions by improving data integrity, system performance, and network congestion:
-
To avoid bottlenecks, ensure that the network infrastructure can handle the load.
-
Partition your network. For example, use 100 Mbps Ethernet for client access and 1 GB Ethernet for the backbone.
-
To ensure that sufficient capacity exists for future expansion, don’t use theoretical maximum values when configuring your network.
-
Separate traffic flows on different network partitions to reduce collisions and to optimize bandwidth use.
Messaging Server CPU Resources
Enable enough CPU for your Message Stores, MTAs, and on systems that are just running multiplexing services (MMP). In addition, enable enough CPU for any RAID systems that you plan to use.
Developing Messaging Server Architectural Strategies
Once you have identified your system performance needs, the next step in sizing your Messaging Server deployment is to size specific components based on your architectural decisions.
The following sections point out sizing considerations when you deploy two-tiered and one-tiered architectures.
Note –
For detailed information on planning your architecture, see Chapter 11, Developing a Messaging Server Architecture.
Two-tiered Messaging Server Architecture
A two-tiered architecture splits the Messaging Server deployment into two layers: an access layer and a data layer. In a simplified two-tiered deployment, you might add an MMP and an MTA to the access layer. The MMP acts as a proxy for POP and IMAP mail readers, and the MTA relays transmitted mail. The data layer holds the Message Store and Directory Server. Figure 10–1 shows a simplified two-tiered architecture.
Figure 10–1 Simplified Messaging Server Two-tiered Architecture
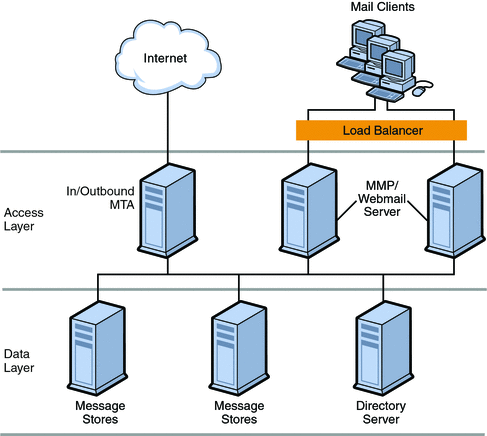
Two-tiered architectures have advantages over one-tiered architectures that might impact your sizing decisions. Two-tiered architectures permit:
-
Easier maintenance than one-tiered architectures
-
Offloading of load-intensive processes like SSL, virus scanning, message reprocessing, and denial of service
-
Easier growth management and system upgrade with limited overall downtime
The next several sections describe how to size specific components in a two-tiered deployment.
 To Size the Message Store
To Size the Message Store
The goals of sizing your Message Store are to identify the maximum number of concurrent connections your store can handle and to determine the number of messages that can be delivered to the store per second.
-
Determine the number of store machines and concurrent connections per machine based on the figures you gather by using a load simulator. For more information on sizing tools, see Using a Messaging Server Load Simulator.
-
Determine the amount of storage needed for each store machine.
-
Use multiple store partitions or store machines, if it is appropriate for your backup and restoration of file system recovery times.
Sun Client Services is often asked to specify a recommendation for the maximum number of users on a message store. Such a recommendation cannot be given without understanding:
-
Usage patterns (as described in Using a Messaging Server Load Simulator.
-
The maximum number of active users on any given piece of hardware within the deployment.
-
Backup, restore, and recovery times. These times increase as the size of a message store increases.
-
 To Size Inbound and Outbound MTAs
To Size Inbound and Outbound MTAs
In general, separate your MTA services into inbound and outbound services. You can then size each in a similar fashion. The goal of sizing your MTAs is to determine the maximum number of messages that can be relayed per second.
To size inbound MTAs, you need to know the raw performance of your inbound MTA in a real-world environment.
-
From the raw performance of the inbound MTA, add SSL, virus scanning processes, and other extraordinary message processing.
-
Account for denial of service attacks at peak volume in the day.
-
Add enough MTAs for load balancing and for redundancy as appropriate.
With redundancy, one or more of each type of machine can still handle peak load without a substantial impact to throughput or response time.
In addition, sufficient disk capacity for network problems or non-functioning remote MTAs must be calculated for transient messages.
 To Size Your MMP
To Size Your MMP
When you size your MMP, the calculation is based on your system load, particularly the number of POP and IMAP concurrent connections for the MMP.
In addition, you must:
-
Add CPU or a hardware accelerator for SSL.
-
Add more disks for an SMTP proxy.
-
Add capacity for load balancing and redundancy, if appropriate.
As with inbound MTA routers, one or more of each type of machine should still handle peak load without a substantial impact to throughput or response time when you plan for redundancy in your deployment.
Single-tiered Messaging Server Architecture
In a single-tiered architecture, there is no separation between access and data layers. The MTA, Message Store, and sometimes the Directory Server are installed in one layer. Figure 10–2 shows a single-tiered architecture.
Figure 10–2 Simplified Messaging Server Single-tiered Architecture
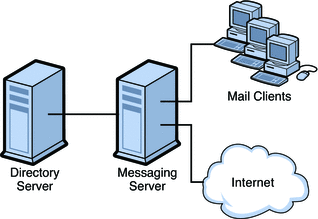
Single-tiered architectures have lower up-front hardware costs than two-tiered architectures. However, if you choose a one-tiered architecture, you need to allow for significant maintenance windows.
 To Size a Single-tiered Messaging Server Architecture
To Size a Single-tiered Messaging Server Architecture
-
Size your message stores like you size message stores in a Two-tiered Messaging Server Architecture.
-
Add CPU for SSL, if necessary.
-
Add more disks for the increased number of SMTP connections.
-
Add more disks for outbound MTA routing.
Note –For specific instructions on sizing Messaging components in single-tiered or two-tiered architectures, contact your Sun Client Services representative.
Chapter 11 Developing a Messaging Server Architecture
This chapter describes how to design the architecture of your Messaging Server, which provides for how Messaging Server components are distributed across hardware and software resources.
This chapter contains the following sections:
-
Understanding Horizontal and Vertical Scalability in Messaging Server
-
Performance Considerations for a Messaging Server Architecture
Understanding the Two-tiered Messaging Architecture
A two-tiered messaging architecture provides the optimum design for scalability and reliability. Instead of having a single host run all the components of a messaging system, a two-tiered architecture separates the components onto different machines. These separate components perform specific specialized functions. As the load for a particular functional component increases—for example, more Message Storage is required, or more outbound relaying is needed—you can add more servers to handle the larger loads.
The two-tiered architecture consists of an access layer and a data layer. The access layer is the portion of the architecture that handles delivery, message access, user login, and authentication. The data layer is the portion of the architecture that holds all the data. This includes the LDAP master servers and Messaging Server machines that are configured to store user messages.
Figure 11–1 shows an example two-tiered architecture.
Figure 11–1 Two-Tiered Messaging Server Architecture
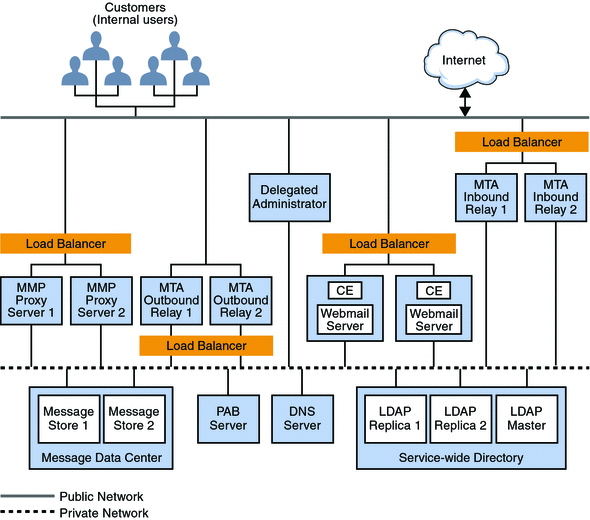
The following describes each of these functional pieces.
Public Access Network. The network connecting the Messaging Server to internal users and the Internet. Each deployment defines its own network requirements; however, the basic Messaging Server requirement is connectibility to end users and the Internet using standard protocols such as SMTP, POP, IMAP, and HTTP.
Private Data Network. This network provides secure connectivity between the public access network and Messaging Server data. It consists of a secure access layer and a data layer, which includes the service-wide directory, the message data center, and the personal address book (PAB) server.
LDAP directory server. Directory server used for storing and retrieving information about the user base. It stores user and group aliases, mailhost information, delivery preferences, and so on. Depending on your design requirements, there could be more than one identical directory for the system. Figure 11–1 shows a master directory and two replicas. An LDAP directory server is provided as part of the Messaging Server product. If desired, you can use data from an existing Sun Java System Directory Server directory. The data format of the existing directory must also be compliant with the Messaging Server schema.
Message Store. Holds and stores user mail. Sometimes referred to as a “back end.” The Message Store also refers to the Message Access Components such as the IMAP server, the POP server, and the Webmail (mshttpd) servers. Figure 11–1 shows a deployment that has two message stores. You can add more stores as needed.
Personal Address Book (PAB) Server. Stores and retrieves users’ addresses in an LDAP server, which can be the same server or a different server from the LDAP server described above.
DNS server. Maps host names to IP addresses. The DNS server determines what host to contact when routing messages to external domains. Internally, DNS maps actual services to names of machines. The DNS server is not part of the Messaging Server product. You must install an operating DNS server prior to installing Messaging Server.
Load Balancer. Balances network connections uniformly or by algorithm across multiple servers. Using load balancers, a single network address can represent a large number of servers, eliminating traffic bottlenecks, allowing management of traffic flows and guaranteeing high service levels. Figure 11–1 shows load balancers for the MMPs and the MTAs. Load balancers are not part of Sun Java Communications Suite. You cannot use load balancers on the Message Store or directory masters. You use them for connections to MMPs, Communications Express, MTAs, directory consumers, and with the MTA’s use of the Brightmail product.
MTA Inbound Relay. MTA dedicated to accepting messages from external (Internet) sites and routing those messages to internal hosts and the local Message Store server. Because this is the first point of contact from the outside, the MTA inbound relay has the added responsibility of guarding against unauthorized relaying, spam filtering, and denial of service attack. You can use MX records to balance incoming mail traffic. See Mail Exchange (MX) Records for more information.
MTA Outbound Relay. MTA that only receives mail from internal or authenticated users and routes those messages to other internal users or to external (Internet) domains. While a single machine can be an inbound relay as well as an outbound relay, in a large scale Internet-facing deployment, separate these functions to two separate machines. This way, internal clients sending mail do not have to compete with inbound mail from external sites.
Delegated Administrator Server. Provides a GUI management console for administrators, enabling more advanced administrative tasks, such as adding and deleting users.
Messaging Multiplexor or MMP. Enables scaling of the Message Store across multiple physical machines by decoupling the specific machine that contains a user’s mailbox from its associated DNS name. Client software does not have to know the physical machine that contains its Message Store. Thus, users do not need to change the name of their host message store every time their mailbox is moved to a new machine. When POP or IMAP clients request mailbox access, the MMP forwards the request to the Messaging Server system containing the requested mailbox by looking in the directory service for the location of the user’s mailbox. When you use multiple MMPs, they should be located behind a load balancer.
Webmail Server or mshttpd daemon. Provides email services to the Messenger Express and Communications Express clients by using HTTP. In previous versions of Messaging Server, the Webmail Server accessed the Message Store directly. Now, the Webmail Server accesses the Message Store through the IMAP server. Such an architecture enables Messenger Express and Communications Express clients to access shared folders that are located in different back-end Message Stores. Additionally, there is no longer a requirement to install the Webmail Server on each back-end server. The Webmail Server can act as a front-end server performing the multiplexing capabilities previously performed by Messenger Express Multiplexor (MEM).
Two-tiered Architecture—Messaging Data Flow
This section describes the message flow through the messaging system. How the message flow works depends upon the actual protocol and message path.
Sending Mail: Internal User to Another Internal User
Synopsis: Internal User > Load Balancer > MTA Outbound Relay 1 or 2 > MTA Inbound Relay 1 or 2 > Message Store 1 or 2
Note –
An increasingly more common scenario is to use LMTP to deliver mail directly from the outbound relay to the store. In a two-tiered deployment, you can make this choice.
Messages addressed from one internal user to another internal user (that is, users on the same email system) first go to a load balancer. The load balancer shields the email user from the underlying site architecture and helps provide a highly available email service. The load balancer sends the connection to either MTA Outbound Relay 1 or 2. The outbound relay reads the address and determines that the message is addressed to an internal user. The outbound relay sends the message to MTA Inbound Relay 1 or 2 (or directly to the appropriate message store if so configured). The MTA Inbound Relay delivers the message to the appropriate Message Store. The Message Store receives the message and delivers it to the mailbox.
Retrieving Mail: Internal User
Synopsis: Internal User > Load Balancer > MMP/Communications Express Proxy Server 1 or 2 > Message Store 1 or 2
Mail is retrieved by using either POP, HTTP, or IMAP. The user connection is received by the load balancer and forwarded to one of the MMP or Communications Express servers. The user then sends the login request to the access machine it is connected to. The access layer machine validates the login request and password, then sends the request over the same protocol designated by the user connection to the appropriate Message Store (1 or 2). The access layer machine then proxies for the rest of the connection between the client and servers.
Sending Mail: Internal User to an External (Internet) User
Synopsis: Internal User > Load Balancer > MTA Outbound Relay 1 or 2 > Internet
Messages addressed from an internal user to an external user (that is, users not on the same email system) go to a load balancer. The load balancer shields the email user from the underlying site architecture and helps provide a highly available email service. The load balancer sends the message to either MTA Outbound Relay 1 or 2. The outbound relay reads the address and determines that the message is addressed to an external user. The outbound relay sends the message to an MTA on the Internet.
Sending Mail: External (Internet) User to an Internal User
Synopsis: External User > MTA Inbound Relay 1 or 2 > Message Store 1 or 2
Messages addressed from an external user (from the Internet) to an internal user go to either MTA Inbound Relay 1 or 2 (a load balancer is not required). The inbound relay reads the address and determines that the message is addressed to an internal user. The inbound relay determines by using an LDAP lookup whether to send it to Message Store 1 or 2, and delivers accordingly. The appropriate Message Store receives the message and delivers it to the appropriate mailbox.
Understanding Horizontal and Vertical Scalability in Messaging Server
Scalability is the capacity of your deployment to accommodate growth in the use of messaging services. Scalability determines how well your system can absorb rapid growth in user population. Scalability also determines how well your system can adapt to significant changes in user behavior, for example, when a large percentage of your users want to enable SSL within a month.
This section helps you identify the features you can add to your architecture to accommodate growth on individual servers and across servers. The following topics are covered:
Planning for Horizontal Scalability
Horizontal scalability refers to the ease with which you can add more servers to your architecture. As your user population expands or as user behavior changes, you eventually overload resources of your existing deployment. Careful planning helps you to determine how to appropriately scale your deployment.
If you scale your deployment horizontally, you distribute resources across several servers. There are two methods used for horizontal scalability:
Spreading Your Messaging User Base Across Several Servers
To distribute load across servers is to divide clients’ mail evenly across several back-end Message Stores. You can divide up users alphabetically, by their Class of Service, by their department, or by their physical location and assign them to a specific back-end Message Store host.
Figure 11–2 shows a sample deployment where users are spread across multiple back-end servers and multiplexors enabled to handle incoming client connections.
Figure 11–2 Spreading Your User Base Across Multiple Servers
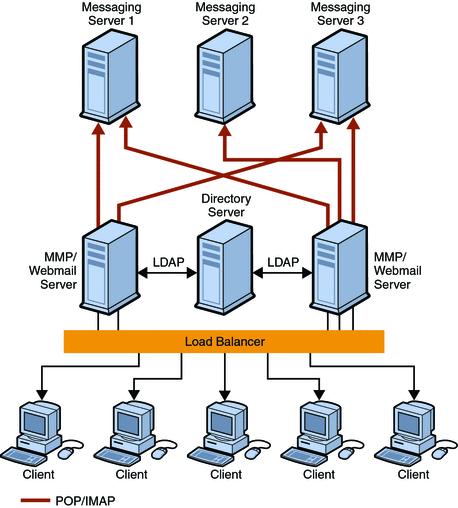
Spreading users across back-end servers provides simplified user management, as long as you use MMPs or Webmail Servers. Because users connect to one back-end server, where their mail resides, you can standardize setup across all users. This configuration also makes administration of multiple servers easier to manage. And, as the demand for more Messaging Server hosts increases, you can add more hosts seamlessly.
Spreading Your Messaging Resources Across Redundant Components
If email is a critical part of your organization’s day-to-day operations, redundant components, like load balancers, mail exchange (MX) records, and relays are necessary to ensure that the messaging system remains operational.
By using redundant MTAs, you ensure that if one component is disabled, the other is still available. Also, spreading resources across redundant MTAs enables load sharing. This redundancy also provides fault tolerance to the Messaging Server system. Each MTA relay should be able to perform the function of other MTA relays.
Installing redundant network connections to servers and MTAs also provides fault tolerance for network problems. The more critical your messaging deployment is to your organization, the more important it is for you to consider fault tolerance and redundancy.
Additional information on Mail Exchange (MX) Records, and Inbound and Outbound MTAs is described in the following sections.
Mail Exchange (MX) Records
MX records are a type of DNS record that maps one host name to another. Equal priority MX records route messages to redundant inbound MTAs. For example, the sending MTA from the Internet will find that the MX record for siroe.com corresponds to MTAA.siroe.com and MTAB.siroe.com. One of these MTAs is chosen at random, as they have equal priority, and an SMTP connection is opened. If the first MTA chosen does not respond, the mail goes to the other MTA. See the following MX record example:
siroe.com. in MX 10 MTAA.siroe.com siroe.com. in MX 10 MTAB.siroe.com |
Inbound and Outbound MTAs
When Messaging Server hosts are each supporting many users, and there is a heavy load of sending SMTP mail, offload the routing task from the Messaging Server hosts by using separate inbound and outbound MTAs. You can further share the load by designating different MTAs to handle outgoing and incoming messages.
Often, both the inbound and outbound MTAs are combined as a single In/Out SMTP host. To determine if you need one or more MTA hosts, identify the inbound and outbound message traffic characteristics of the overall architecture.
Load Balancers
Load balancing can be used to distribute the load across several servers so that no single server is overwhelmed. A load balancer takes requests from clients and redirects them to an available server by algorithms such as keeping track of each server’s CPU and memory usage. Load balancers are available as software that runs on a common server, as a pure external hardware solution, or as a combined hardware and software package.
Planning for Vertical Scalability
Vertical scalability pertains to adding resources to individual server machines, for example, adding additional CPUs. Each machine is scaled to handle a certain load. In general, you might decide upon vertical scalability in your deployment because you have resource limitations or you are unable to purchase additional hardware as your deployment grows.
To vertically scale your deployment, you need to:
-
Size each messaging component
-
Test the load of a prototype of your system
-
Monitor system performance and adjust the deployment accordingly
Planning for a Highly Available Messaging Server Deployment
High availability is a design for your deployment that operates with a small amount of planned and unplanned downtime. Typically, a highly available configuration is a cluster that is made up of two or more loosely coupled systems. Each system maintains its own processors, memory, and operating system. Storage is shared between the systems. Special software binds the systems together and allows them to provide fully automated recovery from a single point of failure. Messaging Server provides high-availability options that support both the Sun Cluster services and Veritas clustering solutions.
When you create your high availability plan, you need to weigh availability against cost. Generally, the more highly available your deployment is, the more its design and operation will cost.
High availability is an insurance against the loss of data access due to application services outages or downtime. If application services become unavailable, an organization might suffer from loss of income, customers, and other opportunities. The value of high availability to an organization is directly related to the costs of downtime. The higher the cost of downtime, the easier it is to justify the additional expense of having high availability. In addition, your organization might have service level agreements guaranteeing a certain level of availability. Not meeting availability goals can have a direct financial impact.
See Chapter 6, Designing for Service Availability for more information.
Performance Considerations for a Messaging Server Architecture
This section describes how to evaluate the performance characteristics of Messaging Server components to accurately develop your architecture.
This section contains the following topics:
Message Store Performance Considerations
Message store performance is affected by a variety of factors, including:
-
Disk I/O
-
Inbound message rate (also known as message insertion rate)
-
Message sizes
-
Use of S/MIME
-
Transaction rate for IMAP and HTTP
-
Concurrent number of connections for the various protocols
-
Network I/O
-
Use of SSL
The preceding factors list the approximate order of impact to the Message Store. Most performance issues with the Message Storage arise from insufficient disk I/O capacity. Additionally, the way in which you lay out the store on the physical disks can also have a performance impact. For smaller standalone systems, it is possible to use a simple stripe of disks to provide sufficient I/O. For most larger systems, segregate the file system and provide I/O to the various parts of store.
Messaging Server Directories
Messaging Server uses six directories that receive a significant amount of input and output activity. If you require a deployment that is scalable, responsive, and resilient to variations in load, provide each of those directories with sufficient I/O bandwidth. When you provide separate file systems for these directories, each composed of multiple drives, you can more readily diagnose I/O bottlenecks and problems. Also, you can isolate the effect of storage failures and simplify the resulting recovery operations. In addition, place a seventh directory for DB snapshots on a file system separate from the active DB to preserve it in the event of a storage failure of the active DB file system.
The following table describes these directories.
Table 11–1 High Access Messaging Server Directories|
High I/O Directory |
Description and Defining Parameter |
|---|---|
|
MTA queue directory |
In this directory, many files are created, one for each message that passes through the MTA channels. After the file is sent to the next destination, the file is then deleted. The directory location is controlled by the IMTA_QUEUE option in the imta_tailor file. Before modifying the MTA queue directory, read about this option in the Sun Java System Messaging Server 6.3 Administration Reference. Default location: /var/opt/SUNWmsgsr/queue |
|
Messaging Server log directory |
This directory contains log files which are constantly being appended with new logging information. The number of changes will depend on the logging level set. The directory location is controlled by the configutil parameter logfile.*.logdir, where * can be a log-generating component such as admin, default, http, imap, or pop. The MTA log files can be changed with the IMTA_LOG option in the imta_tailor file. Default location: /var/opt/SUNWmsgsr/log |
|
These files require constant updates as well as cache synchronization. Put this directory on your fastest disk volume. These files are always located in the /var/opt/SUNWmsgsr/store/mboxlist directory. |
|
|
Message store index files |
These files contain meta information about mailboxes, messages, and users. By default, these files are stored with the message files. The configutil parameter store.partition.*.path, where * is the name of the partition, controls the directory location. If you have the resources, put these files on your second fastest disk volume. Default location: /var/opt/SUNWmsgsr/store/partition/primary |
|
Message files |
These files contain the messages, one file per message. Files are frequently created, never modified, and eventually deleted. By default, they are stored in the same directory as the message store index files. The location can be controlled with the configutil parameter store.partition.partition_name.messagepath, where partition_name is the name of the partition. Some sites might have a single message store partition called primary specified by store.partition.primary.path. Large sites might have additional partitions that can be specified with store.partition.partition_name.messagepath, where partition_name is the name of the partition. Default location: /var/opt/SUNWmsgsr/store/partition/primary |
|
Mailbox list database temporary directory |
The directory used by the Message Store for all temporary files. To maximize performance, this directory should be located under the fastest file system. For Solaris, use the configutil command to configure the store.dbtmpdir variable to a directory under tmpfs, for example, /tmp/mboxlist. Default location: /var/opt/SUNWmsgsr/store/mboxlist |
The following sections provide more detail on Messaging Server high access directories.
MTA Queue Directories
In non-LMTP environments, the MTA queue directories in the Message Store system are also heavily used. LMTP works such that inbound messages are not put in MTA queues but directly inserted into the store. This message insertion lessens the overall I/O requirements of the Message Store machines and greatly reduces use of the MTA queue directory on Message Store machines. If the system is standalone or uses the local MTA for Webmail sends, significant I/O can still result on this directory for outbound mail traffic. In a two-tiered environment using LMTP, this directory will be lightly used, if at all. In prior releases of Messaging Server, on large systems this directory set needs to be on its own stripe or volume.
MTA queue directories should usually be on their own file systems, separate from the message files in the Message Store. The Message Store has a mechanism to stop delivery and appending of messages if the disk space drops below a defined threshold. However, if both the log and queue directories are on the same file system and keep growing, you will run out of disk space and the Message Store will stop working.
Log Files Directory
The log files directory requires varying amounts of I/O depending on the level of logging that is enabled. The I/O on the logging directory, unlike all of the other high I/O requirements of the Message Store, is asynchronous. For typical deployment scenarios, do not dedicate an entire Logical Unit Number (LUN) for logging. For very large store deployments, or environments where significant logging is required, a dedicated LUN is in order.
In almost all environments, you need to protect the Message Store from loss of data. The level of loss and continuous availability that is necessary varies from simple disk protection such as RAID5, to mirroring, to routine backup, to real time replication of data, to a remote data center. Data protection also varies from the need for Automatic System Recovery (ASR) capable machines, to local HA capabilities, to automated remote site failover. These decisions impact the amount of hardware and support staff required to provide service.
mboxlist Directory
The mboxlist directory is highly I/O intensive but not very large. The mboxlist directory contains the databases that are used by the stores and their transaction logs. Because of its high I/O activity, and due to the fact that the multiple files that constitute the database cannot be split between different file systems, you should place the mboxlist directory on its own stripe or volume in large deployments. This is also the most likely cause of a loss of vertical scalability, as many procedures of the Message Store access the databases. For highly active systems, this can be a bottleneck. Bottlenecks in the I/O performance of the mboxlist directory decrease not only the raw performance and response time of the store but also impact the vertical scalability. For systems with a requirement for fast recovery from backup, place this directory on Solid State Disks (SSD) or a high performance caching array to accept the high write rate that an ongoing restore with a live service will place on the file system.
Multiple Store Partitions
The Message Store supports multiple store partitions. Place each partition on its own stripe or volume. The number of partitions that should be put on a store is determined by a number of factors. The obvious factor is the I/O requirements of the peak load on the server. By adding additional file systems as additional store partitions, you increase the available IOPS (total IOs per second) to the server for mail delivery and retrieval. In most environments, you will get more IOPS out of a larger number of smaller stripes or LUNs than a small number of larger stripes or LUNs.
With some disk arrays, it is possible to configure a set of arrays in two different ways. You can configure each array as a LUN and mount it as a file system. Or, you can configure each array as a LUN and stripe them on the server. Both are valid configurations. However, multiple store partitions (one per small array or a number of partitions on a large array striping sets of LUNs into server volumes) are easier to optimize and administer.
Raw performance, however, is usually not the overriding factor in deciding how many store partitions you want or need. In corporate environments, it is likely that you will need more space than IOPS. Again, it is possible to software stripe across LUNs and provide a single large store partition. However, multiple smaller partitions are generally easier to manage. The overriding factor of determining the appropriate number of store partitions is usually recovery time.
Recovery times for store partitions fall into a number of categories:
-
First of all, the fsck command can operate on multiple file systems in parallel on a crash recovery caused by power, hardware, or operating system failure. If you are using a journaling file system (highly recommended and required for any HA platform), this factor is small.
-
Secondly, backup and recovery procedures can be run in parallel across multiple store partitions. This parallelization is limited by the vertical scalability of the mboxlist directory as the Message Store uses a single set of databases for all of the store partitions. Store cleanup procedures (expire and purge) run in parallel with one thread of execution per store partition.
-
Lastly, mirror or RAID re-sync procedures are faster with smaller LUNs. There are no hard and fast rules here, but the general recommendation in most cases is that a store partition should not encompass more than 10 spindles.
The size of drive to use in a storage array is a question of the IOPS requirements versus the space requirements. For most residential ISP POP environments, use “smaller drives.” Corporate deployments with large quotas should use “larger” drives. Again, every deployment is different and needs to examine its own set of requirements.
Message Store Processor Scalability
The Message Store scales well, due to its multiprocess, multithreaded nature. The Message Store actually scales more than linearly from one to four processors. This means that a four processor system will handle more load than a set of four single processor systems. The Message Store also scales fairly linearly from four to 12 processors. From 12 to 16 processors, there is increased capacity but not a linear increase. The vertical scalability of a Message Store is more limited with the use of LMTP although the number of users that can be supported on the same size store system increases dramatically.
Setting the Mailbox Database Cache Size
Messaging Server makes frequent calls to the mailbox database. For this reason, it helps if this data is returned as quickly as possible. A portion of the mailbox database is cached to improve Message Store performance. Setting the optimal cache size can make a big difference in overall Message Store performance. You set the size of the cache with the configutil parameter store.dbcachesize.
You should use the configutil parameter store.dbtmpdir to redefine the location of the mailbox database to /tmp, that is, /tmp/mboxlist.
The mailbox database is stored in data pages. When the various daemons make calls to the database (stored, imapd, popd), the system checks to see if the desired page is stored in the cache. If it is, the data is passed to the daemon. If not, the system must write one page from the cache back to disk, and read the desired page and write it in the cache. Lowering the number of disk read/writes helps performance, so setting the cache to its optimal size is important.
If the cache is too small, the desired data will have to be retrieved from disk more frequently than necessary. If the cache is too large, dynamic memory (RAM) is wasted, and it takes longer to synchronize the disk to the cache. Of these two situations, a cache that is too small will degrade performance more than a cache that is too large.
Cache efficiency is measured by hit rate. Hit rate is the percentage of times that a database call can be handled by cache. An optimally sized cache will have a 99 percent hit rate (that is, 99 percent of the desired database pages will be returned to the daemon without having to grab pages from the disk). The goal is to set the cache so that it holds a number of pages such that the cache will be able to return at least 95 percent of the requested data. If the direct cache return is less than 95 percent, then you need to increase the cache size.
 To Adjust the Mailbox Database Cache Size
To Adjust the Mailbox Database Cache Size
-
Become the mailsrv user (or whatever user you set mailsrv to).
Using root or any other user for this task can cause problems with the database.
-
Set the LD_LIBRARY_PATH to /opt/SUNWmsgsr/lib.
-
Set the size of the cache with the configutil parameter store.dbcachesize.
 To Monitor the Mailbox Database Cache Size
To Monitor the Mailbox Database Cache Size
Beginning with the Messaging Server 6.3 release, use the imcheck command to measure the cache hit rate. Prior to the Messaging Server 6.3 release, use the database command db_stat.
-
Display the cache hit rate.
Messaging Server 7.0: Run the imcheck -s mpool command.
Messaging Server 6.3: Run the imcheck -s command.
Messaging Server 6.2: Run the db_stat command as follows. In this example, the configutil parameter store.dbtmpdir has redefined the location of the mailbox database to /tmp, that is, /tmp/mboxlist.
# /opt/SUNWmsgsr/lib/db_stat -m -h /tmp/mboxlist
2MB 513KB 604B Total cache size. 1 Number of caches. 2MB 520KB Pool individual cache size. 0 Requested pages mapped into the process’ address space. 55339 Requested pages found in the cache (99%).
-
Examine the cache hit rate.
In this case, the hit rate is 99 percent. This could be optimal or, more likely, it could be that the cache is too large. To test, lower the cache size until the hit rate moves to below 99 percent. When you hit 98 percent, you have optimized the DB cache size. Conversely, if see a hit rate of less than 95 percent, then you should increase the cache size with the store.dbcachesize parameter. The maximum size is the total of all the *.db files in the store/mboxlist directory. The cache size should not exceed the total size of all of the .db files under the store/mboxlist directory.
-
As your user base changes, the hit rate can also change. Periodically check and adjust this parameter as necessary.
This parameter has an upper limit of 2 GB imposed by the database.
Setting Disk Stripe Width
When setting disk striping, the stripe width should be about the same size as the average message passing through your system. A stripe width of 128 blocks is usually too large and has a negative performance impact. Instead, use values of 8, 16, or 32 blocks (4, 8, or 16 kilobyte message respectively).
MTA Performance Considerations
MTA performance is affected by a number of factors including, but not limited to:
-
Disk performance
-
Use of SSL
-
The number of messages/connections inbound and outbound
-
The size of messages
-
The number of target destinations/messages
-
The speed and latency of connections to and from the MTA
-
The need to do spam or virus filtering
-
The use of Sieve rules and the need to do other message parsing (like use of the conversion channel)
The MTA is both CPU and I/O intensive. The MTA reads from and writes to two different directories: the queue directory and the logging directory. For a small host (four processors or less) functioning as an MTA, you do not need to separate these directories on different file systems. The queue directory is written to synchronously with fairly large writes. The logging directory is a series of smaller asynchronous and sequential writes. On systems that experience high traffic, consider separating these two directories onto two different file systems.
In most cases, you will want to plan for redundancy in the MTA in the disk subsystem to avoid permanent loss of mail in the event of a spindle failure. (A spindle failure is by far the single most likely hardware failure.) This implies that either an external disk array or a system with many internal spindles is optimal.
MTA and RAID Trade-offs
There are trade-offs between using external hardware RAID controller devices and using JBOD arrays with software mirroring. The JBOD approach is sometimes less expensive in terms of hardware purchase but always requires more rack space and power. The JBOD approach also marginally decreases server performance, because of the cost of doing the mirroring in software, and usually implies a higher maintenance cost. Software RAID5 has such an impact on performance that it is not a viable alternative. For these reasons, use RAID5 caching controller arrays if RAID5 is preferred.
MTA and Processor Scalability
The MTA does scale linearly beyond eight processors, and like the Message Store, more than linearly from one processor to four.
MTA and High Availability
It is rarely advisable to put the MTA under HA control, but there are exceptional circumstances where this is warranted. If you have a requirement that mail delivery happens in a short, specified time frame, even in the event of hardware failure, then the MTA must be put under HA software control. In most environments, simply increase the number of MTAs that are available by one or more over the peak load requirement. This ensures that proper traffic flow can occur even with a single MTA failure, or in very large environments, when multiple MTAs are offline for some reason.
In addition, with respect to placement of MTAs, you should always deploy the MTA inside your firewall.
MMP Performance Considerations
The MMP runs as a single multithreaded process and is CPU and network bound. It uses disk resources only for logging. The MMP scales most efficiently on two processor machines, scales less than linearly from two to four processors and scales poorly beyond four processors. Two processor, rack mounted machines are good candidates for MMPs.
In deployments where you choose to put other component software on the same machine as the MMP (Calendar Server front end, Communications Express web container, LDAP proxy, and so on), look at deploying a larger, four processor SPARC machine. Such a configuration reduces the total number of machines that need to be managed, patched, monitored, and so forth.
MMP sizing is affected by connection rates and transaction rates. POP sizing is fairly straight forward, as POP connections are rarely idle. POP connections connect, do some work, and disconnect. IMAP sizing is more complex, as you need to understand the login rate, the concurrency rate, and the way in which the connections are busy. The MMP is also somewhat affected by connection latency and bandwidth. Thus, in a dial up environment, the MMP will handle a smaller number of concurrent users than in a broadband environment, as the MMP acts as a buffer for data coming from the Message Store to the client.
If you use SSL in a significant percentage of connections, install a hardware accelerator.
MMP and High Availability
Never deploy the MMP under HA control. An individual MMP has no static data. In a highly available environment, add one or more additional MMP machines so that if one or more are down there is still sufficient capacity for the peak load. If you are using Sun Fire BladeTM Server hardware, take into account the possibility that an entire Blade rack unit can go down and plan for the appropriate redundancy.
MMP and Webmail Server
You can put the MMP and Webmail Server on the same set of servers. The advantage to doing so is if a small number of either MMPs or Webmail Servers is required, the amount of extra hardware for redundancy is minimized. The only possible downside to co-locating the MMP and Webmail Server on the same set of servers is that a denial of service attack on one protocol can impact the others.
Messaging Server and Directory Server Performance Consideration
For large-scale installations with Access Manager, Messaging Server, and an LDAP Schema 2 directory, you might want to consolidate the Access Control Instructions (ACIs) in your directory.
When you install Access Manager with Messaging Server, a large number of ACIs initially are installed in the directory. Many default ACIs are not needed or used by Messaging Server. You can improve the performance of Directory Server and, consequently, of Messaging Server look-ups, by consolidating and reducing the number of default ACIs in the directory.
For information about how to consolidate and discard unused ACIs, see Appendix F, Consolidating ACIs for Directory Server Performance, in Sun Java System Delegated Administrator 6.4 Administration Guide.
Chapter 12 Designing a Messaging Server Topology
This chapter describes how to design your messaging topology. A messaging topology describes the physical and logical layout of a networked messaging system. Specifically, a topology depicts the way the devices are arranged on a network and how they communicate with one another. In addition, a topology describes the way that data passes through a network. Topologies are bound to network protocols that direct the data flow.
This chapter contains the following sections:
Identifying Your Geographic Needs
The first step in designing your messaging topology is to identify your geographic needs. In particular, determine the messaging services you need to provide at each location within your organization:
-
Once you identify your deployment goals, determine the functions and features needed for each location within your deployment.
-
Understand your organization’s physical constraints, specifically:
-
Available bandwidth
-
Distance between physical locations within your organization
-
Mail transaction rate and volume of mail storage at each physical location
-
Designing a Messaging Topology
Before you develop your topology, you need a strategy to determine where you are going to put your messaging servers in your organization. Depending on your goals, there are four common topologies that you can apply to your organization:
-
Consolidates most or all major system components and messaging servers at a single location.
-
Spreads most or all system components and messaging servers across multiple sites.
-
Consolidates some system components and distributes other components across multiple locations.
-
Hosts multiple domains and handles larger customer base. Like a central topology, it consolidates most system components at a single location.
Central Topology
In a central topology, most or all major system components and messaging processes are located at one site. Clients at remote sites communicate over a Wide Area Network (WAN) to the centralized messaging servers. Figure 12–1 shows a central topology.
Figure 12–1 Central Topology
You should consider a central topology for your organization when:
-
Messaging at remote sites is not mission critical.
-
Users tend to send and receive small text messages.
-
Your organization is located in one physical location or distributed across many small user populations.
-
You do not have remote support personnel.
-
Good bandwidth exists between remote sites and the central site (at least ISDN or better).
There are advantages to implementing a central topology. In general, a central topology has lower hardware and support costs. Central topologies tend to be easier to manage because you have a simplified messaging architecture and a directory replication structure with fewer replication agreements. With a simplified architecture and no need to coordinate installation among geographically distant sites, a central topology is faster to deploy.
That said, there are an equal number of disadvantages to implementing a central topology. A centralized approach heavily relies on a WAN. If the network does not function properly, users at the same site as well as users in remote locations could not send email to one another. Depending on network bandwidth and traffic, services might be slower during peak usage times. For users who send messages within the same domain, a central topology is inefficient. For example, looking at Figure 12–1, a message sent from one user in the Tokyo site would first travel to the Central site before being sent to another user in the Tokyo site.
Distributed Topology
In a distributed topology, most or all system components and messaging processes are distributed across multiple sites, usually at each remote site. Figure 12–2 shows a distributed topology.
Figure 12–2 Distributed Topology
You should consider a distributed topology for your site when:
-
Messaging at remote sites is mission critical.
-
Users send and receive large messages.
-
You have large user populations at remote sites.
-
Support personnel exists at remote sites.
-
There is poor bandwidth to remote sites.
If bandwidth significantly impacts your topology strategy, you should consider upgrading the bandwidth. In general, bandwidth is relatively inexpensive. You might also consider a Virtual Private Networking (VPN), which uses existing high bandwidth Internet pipes rather than dedicated lines behind a firewall.
There are advantages to implementing a distributed topology. Users at regional sites have faster access to their messages because they do not have to retrieve messages over the WAN. Furthermore, messages sent within a regional location will incur less messaging traffic than in a central topology. However, satellite offices still rely on the WAN. Therefore, if lots of message traffic is generated in a satellite office, the WAN might need to be upgraded.
The disadvantages of implementing a distributed topology are that typically you will have higher hardware costs and higher support costs as you maintain more hardware at more locations. Support costs are also higher because of the complexity of the distributed topology. For example, failover in a distributed topology is more difficult to implement than in a central topology. In addition, it is much slower to initially deploy Messaging Server because there are multiple servers spread across multiple sites.
Because Messaging Server accesses the LDAP directory, the LDAP server is a critical link in the mail delivery process. If you don’t use remote LDAP replicas, and the central LDAP is down, the messaging service will not be usable.
Hybrid Topology
In a hybrid topology, central and distributed topologies are combined to meet the needs of an organization. Figure 12–3 shows a hybrid topology.
Figure 12–3 Hybrid Topology
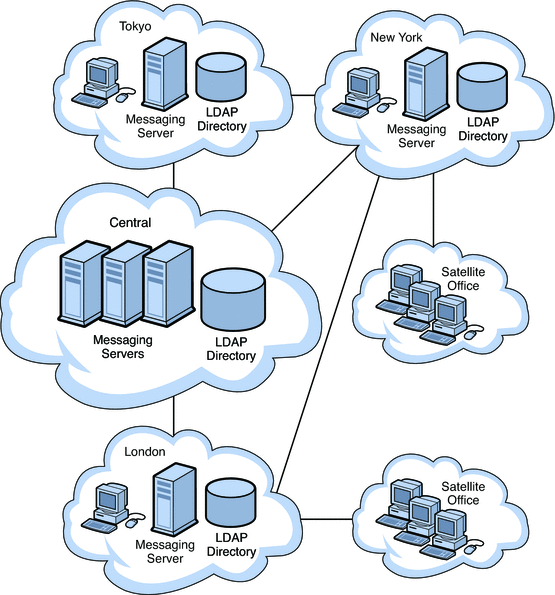
Organizations that benefit from a hybrid topology include those with many sites that have the ability to support a large user base. These sites that support them can house their own messaging servers. Some of these larger sites might have smaller satellite offices located in the general vicinity. But these satellite offices would not require their own messaging servers. Instead, the nearest major office would act as the central location for their services.
Service Provider Topology
In essence, a service provider topology is a large-scale central topology. Typically, a service provider hosts multiple domains and has a larger customer base than an enterprise. Systems are centralized and are able to support multiple users during peak hours. Figure 12–4 shows a service provider topology.
Figure 12–4 Service Provider Topology
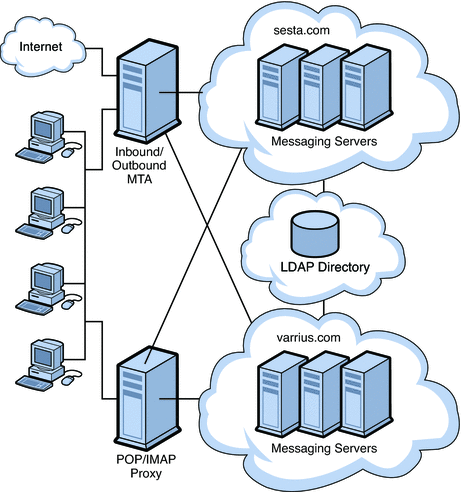
Understanding Messaging Topology Elements
This section describes the most common elements in a messaging topology. Having some familiarity with the basic elements will make it easier for you to design your own topology.
The following topics are covered:
Messaging Topology Components
In Designing a Messaging Topology, you were introduced to three components of a messaging topology: Messaging Server, Directory Server, and clients. This section will describe other components in a basic messaging topology.
Messaging Server. Houses and maintains user mailboxes; it can also be a server that contains just the MTA portion of Messaging Server as described in Internet-facing MTA and MTA Relay.
Client. Accesses messaging services from Messaging Server (often through the Messaging Multiplexor).
Directory Server. Used by Messaging Server for name and alias lookup. Direct LDAP lookup determines where messages should be routed.
Messaging Multiplexor. Connects clients to the appropriate Messaging Server for retrieving messages.
Internet-facing MTA. Routes messages from the Internet and relays them across the firewall. Typically, a Messaging Server host is set up to perform this function.
MTA Relay. The inbound MTA routes incoming messages to valid addresses in the appropriate Messaging Server. The outgoing MTA accepts outgoing messages from clients, queries LDAP to find out where to send the message, then sends it off to the appropriate server or out across the firewall to the Internet. Typically, a Messaging Server host is set up to perform this function.
DNS Server. Resolves server names into IP addresses to allow messages to be routed to their proper address in the network.
Firewall. Restricts Internet access of your internal site. You might even have a firewall between departments in your organization.
Using MTAs to Protect Your Messaging System
You can use MTAs to protect your Messaging Server deployment, as well as to control the flow of message traffic to and from your site.
An Internet-facing MTA is a single point of contact that receives messages from sites external to your organization. An Internet-facing MTA sends the incoming messages across the firewall to the inbound MTA, typically another Messaging Server.
The inbound MTA then queries the directory to determine where to send the message within the organization. The Internet-facing MTA is located in the demilitarized zone (DMZ) of the firewall (between the external and internal walls of the firewall), and does not have access to any information about servers other than the inbound MTA.
The outbound MTA accepts outgoing messages from clients. It queries LDAP to find out where to send the message, then sends it off to the appropriate server or out across the firewall to the Internet. This offloads the MTA work from messaging servers that are used by users to retrieve messages. Figure 12–5 illustrates the idea.
Figure 12–5 MTAs in Messaging Topology
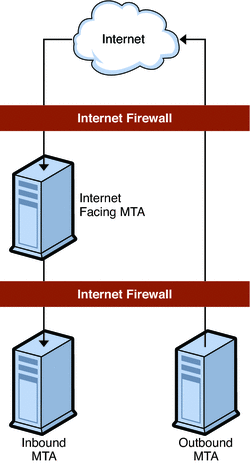
Using MMPs
The MMP enables you to mask the layout of your Messaging Server hosts from your end users. Consequently, you assign users to a generic MMP or a load balancer without having them point to the specific server where their mail boxes reside. Message access clients point to the MMP for retrieving incoming messages.
When such a client connects and authenticates, the MMP looks up the user information in the directory to determine where the user’s messages are held. The MMP then connects the client to that specific server. The following figure shows how the MMP acts as a proxy for IMAP4 and POP3 connections to Messaging servers. Figure 12–6 shows how multiplexors function in a Messaging Server environment.
Figure 12–6 MMP Overview
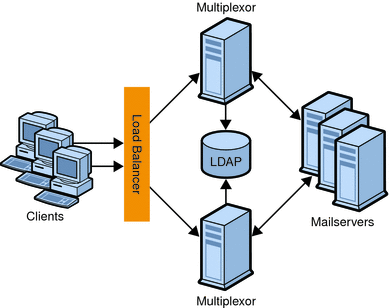
Use a load balancer in front of the multiple MMPs. It is unlikely that you would have a single MMP.
Using the MMP SMTP Proxy
The MMP contains an SMTP proxy that is designed to accept messages but not transfer messages. Because of this design, never use the MMP SMTP Proxy as the target of a DNS MX record or to otherwise receive mail incoming from arbitrary sources on the Internet. Messaging Server does not support the use of the MMP SMTP Proxy in a message transfer capacity.
Messaging Server does support the use of the MMP SMTP proxy for message submission from end-user clients. However, the multiplexing functionality of the MMP, which is necessary to distribute POP and IMAP connections to the correct back-end store, is not necessary for SMTP submission. You can balance SMTP submission by MX records for mail clients that follow the standard, or by a simple load balancer for mail clients that do not follow the standard.
Only use the MMP SMTP Proxy in the following situations:
-
If the MTA is becoming impeded with SSL/TLS processing, the MMP SMTP proxy can offload that processing for message submission while still supporting standard SMTP STARTTLS.
-
If the MMP has SSL hardware acceleration for POP/IMAP, it might make sense to also leverage that for SMTP submission.
-
If you need to use the "POP before SMTP" mechanism, then the MMP SMTP Proxy is required.
-
The MMP SMTP proxy has a desired feature not present in the back-end MTA.
-
If your deployment requires a proxy, then use the MMP SMTP proxy, which is specifically designed to preserve the security features and SMTP extensions present in the MTA and uses a custom SMTP extension (XPEHLO) to do so safely.
Note –
The MMP SMTP Proxy only works with Messaging Server's SMTP server as a back-end.
Using Gateways
Your organization might contain legacy messaging systems that use proprietary methods for messaging handling. Until you migrate your users, both messaging strategies must co-exist. To access these legacy systems, you can use an SMTP gateway, which enables SMTP connections between the new system and the other legacy systems. Usually legacy systems support SMTP connections so that the inbound MTA can route messages to it.
Creating a Messaging Topology Example
Once you have a basic understanding of your topological needs, your strategy, and the topology elements, you can create your messaging topology. To illustrate how to create a messaging topology, this section uses the example of the Siroe Corporation.
The Siroe Corporation is a multimedia organization headquartered in New York, with two smaller offices in Los Angeles and Chicago, and two satellite offices in San Diego and in Minneapolis.
Step 1: Identifying Messaging Goals
The first step in creating a topology is to understand the goals of your organization. Similar to Chapter 2, Analyzing Your Communications Suite Requirements, Siroe’s messaging goals can be categorized into business objectives, technical, and financial constraints.
Siroe’s Business Objectives
The finance, marketing, legal, IT, and engineering groups are located in New York. The creative groups are located in Los Angeles and in San Diego. The technical support groups are located in Chicago and Minneapolis. Most messages are sent between Chicago, Los Angeles, and New York.
Employees at the Siroe Corporation rely on email as their primary method of communication. On average, employees send approximately 15 messages per day with attachments in the form of spreadsheets, presentations, or animation.
The deployment planners determined that Message Server hosts would be set up in Chicago, Los Angeles, and in New York. Since the volume of email traffic in San Diego and in Minneapolis is relatively light, these satellite offices will only have mail clients connecting to servers that are located in Chicago and in Los Angeles.
Siroe’s Financial and Technical Constraints
Because of budgetary restrictions, Siroe will be using the existing infrastructure and hardware that is already in place, moving servers to locations where there is critical need. 24x7 support will be available only in the New York, Chicago, and Los Angeles offices. All offices will be connected by T3 lines to the Internet.
Step 2: Choosing a Topology Strategy
The second step in creating your messaging topology is to choose your topology strategy, described in Designing a Messaging Topology. The Siroe Corporation evaluated their business objectives as well as their financial and technical constraints. They determined that:
-
Messaging Server hosts did not need to be deployed at satellite sites, only mail clients.
-
Good bandwidth exists at satellite sites (T3 lines).
-
Regardless of location, mail users send and receive large messages throughout the corporation.
-
There are large user populations in New York, Los Angeles, and Chicago, but not in Minneapolis or San Diego.
-
Support personnel exist in New York, Los Angeles, and in Chicago.
The Siroe Corporation then mapped their objectives and constraints to a common design strategy. Figure 12–7 shows that the Siroe Corporation has chosen a hybrid topology.
Figure 12–7 Hybrid Topology for the Siroe Corporation
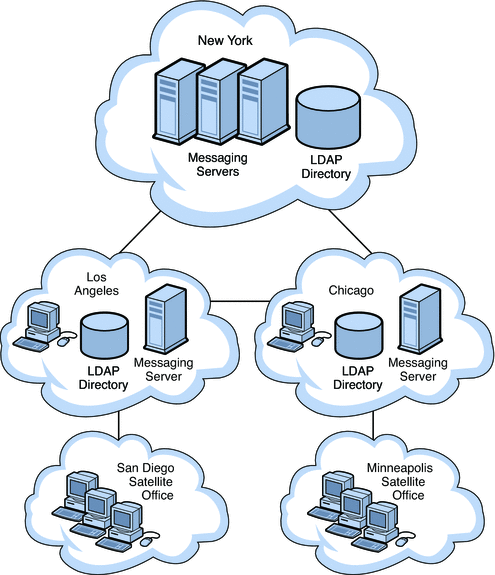
Because New York has the highest message transaction rate of messages entering and leaving the system, it has the most number of messaging servers. The smaller offices, Los Angeles and Chicago, also support San Diego and Minneapolis. However, these satellite offices do not require their own messaging servers. Instead, Chicago and Los Angeles act as the central location for their services.
Step 3: Planning the Topology Elements
The final step in creating your messaging topology is to plan your topology elements in your actual deployment, as described in Understanding Messaging Topology Elements. The following figure illustrates the topology elements in the Chicago and Minneapolis offices.
Figure 12–8 Topological Elements in the Siroe Messaging Deployment for Chicago and Minneapolis
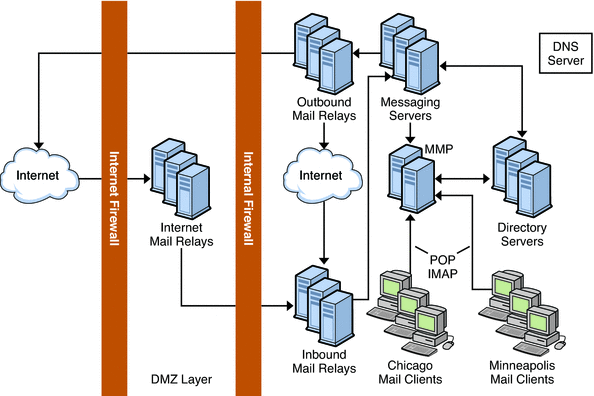
Because 30 percent of the workforce is made up of third-party vendors and contractors, internal firewalls are used in addition to the external firewalls in the topology to restrict access to locations within the company. Internet MTAs are placed in the topology to route messages from the Internet and relay them across the firewall. MTAs are added to route incoming and outgoing messages. Separating incoming and outgoing messages helps to manage the high volume of message traffic. The MMP connects employees’ POP and IMAP mail clients to their mailboxes in the Messaging Servers. By using an MMP, employees don’t have to know their specific mail host when they log in, and administrators can seamlessly move employees’ mailboxes to different mail server locations.
Creating a messaging topology enables you to account for the physical and logical placement of all the elements in your deployment. Doing so ensures minimal rework of your installation.
Chapter 13 Planning Messaging Server Security
This chapter describes how to plan for and protect the various component of your Messaging Server deployment.
This chapter contains the following sections:
Protecting Messaging Components in Your Deployment
This section describes how to secure components in your Messaging deployment:
Note –
With each component, you should use the chroot function to limit the number of available commands on each machine.
Protecting MTAs
Secure MTAs to protect processing resources and server availability. When messages are relayed from unauthorized users or large quantities of spam are delivered, response time is reduced, disk space is used up, and processing resources, which are reserved for end users, are consumed. Not only does spam waste server resources, it is also a nuisance for your end users.
Note –
Not only must you protect your deployment from external unauthorized users, but you might also have to protect your system from internal users as well.
The following table describes the most common threats to MTAs.
Table 13–1 Common MTA Security Threats
This section on MTA relays describes security options you can use in your deployment:
Access Controls
You can use access controls to reject messages from (or to) certain users at a system level. In addition, you can institute more complex restrictions of message traffic between certain users. Also, you might allow users to set up filters on their own incoming messages (including rejecting messages based on contents of the message headers).
If you want to control access with envelope-level controls, use mapping tables to filter mail. If you want to control access with header-based controls, or if users wish to implement their own personalized controls, use the more general mailbox filters approach with server-side rules.
Mapping Table Overview
You can control access to your mail services by configuring certain mapping tables. Many components of the MTA employ table lookup-oriented information. This type of table is used to transform, that is, map, an input string into an output string. Mapping tables are usually presented as two columns. The first (left-hand) column provides possible input strings against which to match (pattern), and the second (right-hand) column gives the resulting output string for which the input string is mapped (template).
The following table describes these mapping tables, which enable you to control who can or cannot send mail, receive mail, or both. See the Sun Java System Messaging Server 6.3 Administration Guide for more information.
Table 13–2 Access Control Mapping Tables|
Mapping Table |
Description |
|---|---|
|
Used to block incoming connections based on envelope From: address, envelope To: address, source and destination channels. The To: address is checked after rewriting, alias expansion, and so on, have been performed. |
|
|
Used to block incoming connections based on envelope From: address, envelope To: address, source and destination channels. The To: address is checked after rewriting but before alias expansion. |
|
|
Used to block incoming connections based on combined information found in SEND_ACCESS and PORT_ACCESS tables: that is, the channel and address information found in SEND_ACCESS combined with the IP address and port number information found in PORT_ACCESS. |
|
|
Used to block incoming connections based on combined information found in ORIG_SEND_ACCESS and PORT_ACCESS tables: that is, the channel and address information found in ORIG_SEND_ACCESS combined with the IP address and port number information found in PORT_ACCESS. |
|
|
Used to filter mail based on envelope From: addresses. Use this table if the To: address is irrelevant. |
|
|
Used to block incoming connections based on IP number. |
Figure 13–1 illustrates where mapping tables are activated in the mail acceptance process.
Figure 13–1 Mapping Tables and the Mail Acceptance Process
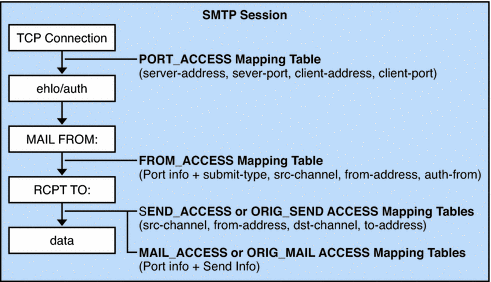
For all the network ports controlled by the MTA service dispatcher, a PORT_ACCESS rejection response, if warranted, takes place at the initial connection from a remote host. A FROM_ACCESS rejection occurs in response to the MAIL FROM: command, before the sending side can send the recipient information or the message data. A SEND_ACCESS or MAIL_ACCESS rejection occurs in response to a RCPT TO: command, before the sending side gets to send the message data. If an SMTP message is rejected, your Messaging Server never accepts or sees the message data, thus minimizing the overhead of performing such rejections. If multiple access control mapping tables exist, Messaging Server checks them all.
Note –
If the message is accepted, it can still be filtered by way of conversion channels and user defined filters.
Configuring Anti-Relaying with Mapping Tables
You can also use access control mappings to prevent people from relaying SMTP mail through your Messaging Server system. For example, someone might try to use your mail system to relay junk mail to thousands of mailboxes on your system or on other systems.
By default, Messaging Server prevents all SMTP relaying activity, including relaying by local POP and IMAP mail clients. If clients do not authenticate by using SMTP AUTH, as described in Enabling Authenticated SMTP, and attempt to submit messages to external addresses via Messaging Server’s SMTP server, their submission attempts are rejected. Thus, you will likely want to modify your configuration so that it recognizes your own internal systems and subnets from which relaying should always be accepted.
 To Prevent Relaying From Outside Hosts
To Prevent Relaying From Outside Hosts
To prevent hosts that reside outside your domain from relaying to other hosts outside your domain:
-
Split incoming mail into different channels. For example:
-
IP addresses within your domain go to the tcp_internal channel.
-
Authenticated sessions go to the tcp_auth channel.
-
All other mail is sent to the tcp_local channel.
-
-
Recognize and allow mail from your POP and IMAP clients by using an INTERNAL_IP mapping table, fully explained in the chapter on Mail Filtering and Access Control in the Sun Java System Messaging Server 6.3 Administration Guide.
Using Mailbox Filters
A filter consists of one or more conditional actions to apply to a message. Messaging Server filters are stored on the server and evaluated by the server. They are sometimes called server-side rules (SSR).
You can create channel-level filters and MTA-wide filters to prevent the delivery of unwanted mail. You can also create filter templates and make them available to end users by using Messenger Express. End users use the templates to build personal mailbox filters to prevent delivery of unwanted mail message to their mailboxes. The server applies filters in the following priority. See the Sun Java System Messaging Server 6.3 Administration Guide for more information.
-
Per-user filters
Per-user filters apply to messages destined for a particular user’s mailbox. You can create filter templates and make them available to end users by using the Messenger Express client. End users use the templates to build personal server filters to manipulate the delivery of mail messages to their mailboxes. The filers reject unwanted messages, redirect mail, filter messages into mailbox folders, and so on.
If a personal mailbox filter explicitly accepts or rejects a message, then filter processing for that message finishes.
A filter template generalizes a Sieve script by replacing “hard-coded” elements of the Sieve script with prompts and input fields. A Java servlet is used to parse the Sieve templates and generate the user interface in the browser. When an end user supplies values in the input fields, the servlet takes those values and saves them in a Sieve script in the user’s directory profile entry. The prompts and input fields are presented to the end user through the Messenger Express interface.
If the recipient user had no mailbox filter, or if the user’s mailbox filter did not explicitly apply to the message in question, Messaging Server next applies the channel-level filter.
-
Channel-level filter
Channel-level filters apply to each message enqueued to a channel. A typical use for this type of filter is to block messages going through a specific channel.
To create a channel-level filter, you must write the filter using Sieve. See Chapter 18, Mail Filtering and Access Control, in Sun Java System Messaging Server 6.3 Administration Guide for specific instructions on creating filters with Sieve.
If the channel-level filter explicitly accepts or rejects a message, then filter processing for that message finishes. Otherwise, Messaging Server next applies the MTA-wide filter, if there is one.
-
MTA-wide filter
MTA-wide filters apply to all messages enqueued to the MTA. A typical use for this type of filter is to block unsolicited bulk email or other unwanted messages regardless of the messages’ destinations.
To create an MTA-wide filter, you must write the filter using Sieve. See Chapter 18, Mail Filtering and Access Control, in Sun Java System Messaging Server 6.3 Administration Guide for specific instructions on creating filters with Sieve.
By default, each user has no mailbox filter. When a user accesses Messenger Express interface to create one or more filters, then their filters are stored in the LDAP Directory.
Conversion Channels and Third Party Filtering Tools
The conversion channel performs body-part-by-body-part conversions on messages through the MTA. This processing can be done by any site-supplied programs or command procedures. The conversion channel can do such things such as convert text or images from one format to another, scan for viruses, translate languages, and so forth. Various message types of the MTA traffic are selected for conversion, and specific processes and programs can be specified for each type of message body part. If you are looking to use the conversion channel with a virus scanning program, you can either disinfect, hold, or reject messages. A special conversion channel configuration is consulted to choose an appropriate conversion for each body part. For more information, see Chapter 13, Using Predefined Channels, in Sun Java System Messaging Server 6.3 Administration Guide.
Note –
Using specialized processing like a conversion channel puts additional load on your system. Be sure to account for it when you plan your sizing strategy.
With the conversion channel, you can use third-party anti-spam and anti-virus software solutions. You can also use the MTA API to create a channel to invoke a remote scanning engine. For more information on the MTA API, see the Sun Java System Messaging Server 6.3 Administration Reference.
In general, it is best that these third-party solutions are shielded from external sites and are only used on back-end or intermediate relays.
The Brightmail solution consists of the Brightmail server and real-time anti-spam and anti-virus (for service providers only) rule updates that are downloaded to your messaging servers. When the Brightmail Logistics and Operations Center (BLOC) receives spam from email probes, operators immediately create appropriate anti-spam rules. These rules are then downloaded to Brightmail customer machines. Similarly, the Symantec Security Response real-time virus rules are also sent from Brightmail. These rules are used by customer’s Brightmail servers to catch spam and viruses.
Messaging Server also supports the use of SpamAssassin, a freeware mail filter used to identify spam. SpamAssassin calculates a score for every message. Scores are calculated by performing a series of tests on message header and body information. Each test either succeeds or fails, and the score is adjusted accordingly. Scores are real numbers and may be positive or negative. Scores that exceed a certain threshold are considered to be spam.
For more information on configuring Brightmail and SpamAssassin for Messaging Server, see Chapter 14, Integrating Spam and Virus Filtering Programs Into Messaging Server, in Sun Java System Messaging Server 6.3 Administration Guide.
RBL Checking
The Mail Abuse Protection System’s Real-time Blackhole List (MAPS RBL) is a list of host and networks that are known to be friendly or neutral to abusers who use these hosts and networks to either originate or relay spam, or to provide spam support services.
You can configure your MTAs to compare incoming connections against the MAPS RBL. You can also use DNS-based databases used to determine incoming SMTP connections that might send unsolicited bulk mail.
For more information, see Chapter 18, Mail Filtering and Access Control, in Sun Java System Messaging Server 6.3 Administration Guide.
Client Access Filters
Messaging Server supports sophisticated access control on a service-by-service basis for POP, IMAP, and HTTP. The Messaging Server access-control facility is a program that listens at the same port as the TCP daemon it serves. The access-control facility uses access filters to verify client identity, and it gives the client access to the daemon if the client passes the filtering process.
If you are managing messaging services for a large enterprise or for a service provider, these capabilities can help you to exclude spammers and DNS spoofers from your system and improve the general security of your network.
As part of its processing, the Messaging Server TCP client access-control system performs (when necessary) the following analyses of the socket end-point addresses:
-
Reverse DNS lookups of both end points (to perform name-based access control)
-
Forward DNS lookups of both end points (to detect DNS spoofing)
-
Identd callback (to check that the user on the client end is known to the client host)
The system compares this information against access-control statements called filters to decide whether to grant or deny access. For each service, separate sets of Allow filters and Deny filters control access. Allow filters explicitly grant access; Deny filters explicitly forbid access.
When a client requests access to a service, the access-control system compares the client’s address or name information to each of that service’s filters—in order—using these criteria:
-
The search stops at the first match. Because Allow filters are processed before Deny filters, Allow filters take precedence.
-
Access is granted if the client information matches an Allow filter for that service.
-
Access is denied if the client information matches a Deny filter for that service.
-
If no match with any Allow or Deny filter occurs, access is granted. The exception is the case where there are Allow filters but no Deny filters, in which case lack of a match means that access is denied.
The filter syntax described here is flexible enough that you should be able to implement many different kinds of access-control policies in a simple and straightforward manner. You can use both Allow filters and Deny filters in any combination, even though you can probably implement most policies by using almost exclusively Allows or almost exclusively Denies.
Client access filters are particularly helpful if troublesome domains are a known quantity. While UBE filters must store and process every spam message, client access filters free Messaging Server from having to process any spammed messages. Because client access filters block mail from entire domains, this feature should be used with caution.
Note the following limitations to client access filters:
-
An SMTP client is required to log in before relaying a message.
-
Client access filters do not scale well for large deployments.
For more information on client access filters, see Chapter 23, Configuring Security and Access Control, in Sun Java System Messaging Server 6.3 Administration Guide.
Monitoring Your Security Strategy
Monitoring your server is an important part of your security strategy. To identify attacks on your system, monitor message queue size, CPU utilization, disk availability, and network utilization. Unusual growth in the message queue size or reduced server response time may identify some of these attacks on MTA relays. Also, investigate unusual system load patterns and unusual connections. Review logs on a daily basis for any unusual activity.
Protecting the Message Store
The most important data in a messaging server is the user’s mail in the message store. Note that the mail messages are stored as individual files, which are not encrypted. Consequently, physical access and root access to the message store must be protected.
To secure the Message Store, restrict access to the machine where the store is installed. You can enable CRAM-MD5 or Digest-MD5 passwords instead of using unencrypted, plaintext passwords. For more information on passwords, see Planning Messaging User Authentication.
Not only should you create password authentication to the store machine, you might also use tools like VPN access, ssh, or pam, which list valid users that are allowed to login to the machine.
In addition, a two-tiered architecture is recommended over a one-tiered architecture. Because the Message Store performs the most disk intensive work of any components in a messaging system, do not have filtering, virus scanning, and other disk-intensive security processes on the same machine. In a two-tiered architecture, you don’t have to run UBE filters, anti-relay, and client access filters on the same machine as the message store, which can add load to your system. Instead, the MTAs handle that processing. In addition, user access to the store is limited to through an MMP in a two-tiered deployment, potentially adding an extra security layer to the message store.
If you deploy a one-tiered architecture, be sure to account for the additional security processing and load (like SSL and virus scanning) that you will need. For more information, see Chapter 10, Planning a Messaging Server Sizing Strategy.
For additional Message Store security processing, set disk quotas per user to limit disk usage. Also, use administrator alarms if free space thresholds are fast approaching their limits. Like the MTA, be sure to monitor the server state, disk space, and service response times. For more information, see Chapter 20, Managing the Message Store, in Sun Java System Messaging Server 6.3 Administration Guide.
Protecting MMPs
Because the MMP serves as a proxy for the Message Store, it needs to protect access to end user data and guard against unauthorized access. User IDs and passwords provide basic authentication capabilities. In addition, you can use client access filters to limit user login to specific domains or IP address ranges. SMTP Authentication, or SMTP AUTH (RFC 2554) is the preferred method of providing SMTP relay server security. SMTP AUTH allows only authenticated users to send mail through the MTA. For more information, see Enabling Authenticated SMTP.
Locate the MMP on a different machine (or under a different userID) in front of your POP or IMAP services. You can have front-end machines with just MMP and MTAs, and then have a physically secure network between those front-end machines, the mail stores, and the LDAP servers.
Special security considerations need to be given to Messenger Express access to the Message Store when your users are logging in from the Internet. In general, you want to make sure that the stores are separated from the outside world by a firewall. Like the MMP, the Webmail Server supports both unencrypted and encrypted (SSL) communication with mail clients.
Regular monitoring of log files can protect against unauthorized access.
Planning Messaging User Authentication
User authentication enables your users to log in through their mail clients to retrieve their mail messages. Methods for user authentication include:
-
Authentication with Simple Authentication and Security Layer (SASL)
-
Certificate-based Authentication with Secure Sockets Layer (SSL)
Plain Text and Encrypted Password Login
User IDs and passwords are stored in your LDAP directory. Password security criteria, such as minimum length, are determined by directory policy requirements. Password security criteria is not part of Messaging Server administration. See the Directory Server documentation to understand directory server password policies:
http://docs.sun.com/coll/1316.1
An administrator can set a messaging configuration parameter to determine if plain passwords are allowed or if passwords must be encrypted. For more information, see the service.xxx.plaintextminciper (where xxx is http, pop, or imap) parameter in the Sun Java System Messaging Server 6.3 Administration Reference. The RestrictPlainPasswords option provides the equivalent function for the MMP
Both plain text and encrypted password login can be used with POP, IMAP, and Messenger Express user access protocols.
Authentication with Simple Authentication and Security Layer (SASL)
SASL (RFC 2222) provides additional authentication mechanisms for POP, IMAP, and SMTP user access protocols. Messaging Server has SASL support for the user access protocols listed in Table 13–3:
Table 13–3 SASL Authentication User Access Protocols Support Matrix|
|
Plain |
Login |
CRAM-MD5 |
Digest-MD5 |
Certificate |
APOP |
|---|---|---|---|---|---|---|
|
SMTP AUTH |
Yes |
Yes |
Yes |
Deprecated |
Yes |
- |
|
POP |
Yes |
- |
Yes |
Deprecated |
Yes |
Yes |
|
IMAP |
Yes |
- |
Yes |
Deprecated |
Yes |
- |
|
HTTP (Messenger Express) |
Yes |
- |
- |
- |
Yes |
- |
Note –
-
When using CRAM-MD5, passwords must be stored in plain text format in the LDAP directory server.
-
Digest-MD5 was never supported by the MMP and its use is deprecated in other cases.
-
To use APOP, CRAM-MD5 or DIGEST-MD5, passwords must be stored in plain text format in the LDAP directory server.
If you use SASL, user name and passwords are not encrypted unless SSL is used for the session. (For more information on SSL, see Encryption with SSL.) The SASL mechanisms, PLAIN and LOGIN, encode authentication information, but can be easily decoded if captured. Despite this limitation, SASL is useful because it can be combined with SMTP AUTH (described in Enabling Authenticated SMTP) to allow only authenticated users to relay mail through your system. For example, legitimate users can authenticate to the SMTP server, and the SMTP server can then be configured to switch to a different channel. In this way, the message from an authenticated session can come from a different TCP channel than a user that did not authenticate. A message from a user in your internal network can also be switched to differentiate it from a message coming from other sources just based on the IP address of the incoming connection.
For more information on SASL, see Chapter 23, Configuring Security and Access Control, in Sun Java System Messaging Server 6.3 Administration Guide.
Enabling Authenticated SMTP
By default, the standard SMTP port (25) is for mail transfer only. Mail relay for submissions from external networks is disabled and authentication is disabled. By default, the standard SMTP submit port (587) is for mail submission and requires authenticated SMTP. As many mail user agents still use port 25 for submission by default it might be useful to enable SMTP authentication on port 25 for those clients.
By default, users need not submit a password when they connect to the SMTP service of Messaging Server to send a message. You can, however, enable password login to SMTP in order to enable authenticated SMTP.
Authenticated SMTP (also referred to as SMTP AUTH) is an extension to the SMTP protocol. Authenticated SMTP allows clients to authenticate to the server. The authentication accompanies the message. The primary use of authenticated SMTP is to enable local users who are not in their office to submit mail without creating an open relay that others could abuse. The AUTH command is used by the client to authenticate to the server.
Authenticated SMTP provides security in sending messages with the SMTP protocol. To use authenticated SMTP, you do not need to deploy a certificate-based infrastructure. (Certificates authentication is described in Certificate-based Authentication with Secure Sockets Layer (SSL).)
With authenticated SMTP, the client can indicate an authentication mechanism to the server and perform an authentication protocol exchange.
If you require SMTP AUTH for mail submission, turn on appropriate logging, so any mail abuse can be traced.
For more information on authenticated SMTP, see the MTA chapters of the Sun Java System Messaging Server 6.3 Administration Guide.
Certificate-based Authentication with Secure Sockets Layer (SSL)
Messaging Server uses the SSL protocol for encrypted communications and for certificate-based authentication of clients and servers. This section describes certificate-based SSL authentication. For information on SSL Encryptions, see Encryption with SSL.
SSL is based on the concepts of public-key cryptography. Although TLS (Transport Layer Security) is functionally a superset of SSL, the names are used interchangeably.
At a high-level, a server which supports SSL needs to have a certificate, a public key, a private key, certificate, key, and security databases. This helps assure message authentication, privacy, and integrity.
Table 13–4 describes the SSL authentication support with each client access protocol. This table shows whether a secure session (startTLS) could be started up over a insecure channel and whether a separate secure channel (SSL on Separate Port) is provided.
Table 13–4 SSL Authentication Support Matrix|
Protocol |
startTLS |
SSL on Separate Port |
|---|---|---|
|
SMTP |
Yes |
Yes |
|
No |
Yes |
|
|
Yes |
Yes |
|
|
POP over MMP |
No |
Yes |
|
IMAP over MMP |
Yes |
Yes |
|
SMTP over MMP |
Yes |
Yes |
|
Webmail |
No |
Yes |
The SMTP, POP, and IMAP protocols provide a way for the client and server to start communication without SSL, and then switch to it by using an equivalent startTLS command. The SMTP, POP, and IMAP servers can also be configured to use SSL on an alternate port, for clients which do not implement startTLS.
To authenticate with SSL, the mail client establishes an SSL session with the server and submits the user’s certificate to the server. The server then evaluates if the submitted certificate is genuine. If the certificate is validated, the user is considered authenticated.
If you use SSL for authentication, you need to obtain a server certificate for your Messaging Server. The certificate identifies your server to clients and to other servers. Your server can also have any number of certificates of trusted Certificate Authorities (CAs) that it uses for client authentication.
Some protocols require use of the SASL EXTERNAL mechanism in conjunction with the SSL client certificate to move from un-authenticated to authenticated state.
For more information on SSL, see Chapter 23, Configuring Security and Access Control, in Sun Java System Messaging Server 6.3 Administration Guide.
Planning Message Encryption Strategies
This section describes encryption and privacy solutions. The following topics are covered:
Encryption with SSL
SSL functions as a protocol layer beneath the application layers of IMAP, HTTP, and SMTP. If transmission of messages between a Messaging Server and its clients and between the servers and other servers is encrypted, there is little chance for eavesdropping on the communications. If connecting clients and servers are authenticated, there is little chance for intruders to spoof them.
End-to-end encryption of message transmission requires the use of S/MIME. See Requirements for Using S/MIME with Communications Express Mail in Sun Java Communications Suite 5 Installation Guide.
Note –
The extra performance overhead in setting up an SSL connection can put a burden on the server. In designing your messaging installation and in analyzing performance, you need to balance security needs against server capacity.
If you use SSL for encryption, you can improve server performance by installing a hardware encryption accelerator. An encryption accelerator typically consists of a hardware board, installed permanently in your server machine, and a software driver. Sun UltraSPARC IV computers have built-in CPU support for SSL encryption but it is not enabled by default.
The SSL connection process between client and server using HTTP/SSL (HTTPS) is as follows:
-
The client initiates contact using HTTPS. The client specifies which secret-key algorithms it can use.
-
The server sends its certificate for authentication and specifies which secret-key algorithm should be used. It will specify the strongest algorithm which it has in common with the client. If there is no match (for example, client is 40 bit only, server requires 128 bits), the connection will be refused.
-
If the server has been configured to require client authentication, it will ask the client for its certificate at this point.
-
The client checks the validity of the server certificate to make sure that it has:
-
Not expired
-
A known signed Certification Authority
-
A valid signature
-
A host name in the certificate matches the same of the server in the HTTPS request
-
SSL Ciphers
A cipher is the algorithm used to encrypt and decrypt data in the encryption process. Some ciphers are stronger than others, meaning that a message encrypted by a stronger cipher is more difficult for an unauthorized person to decrypt.
A cipher operates on data by applying a key to the data. Generally, the longer the key the cipher users during encryption, the more difficult it is to decrypt the data without the proper decryption key.
When a client initiates an SSL connection with Messaging Server, the client lets the server know what ciphers and key lengths it prefers to use for encryption. In any encrypted communication, both parties must use the same ciphers. Because there are a number of cipher-and-key combinations in common use, a server should be flexible in its support for encryption. For more information on ciphers, see Chapter 23, Configuring Security and Access Control, in Sun Java System Messaging Server 6.3 Administration Guide.
Signed and Encrypted S/MIME
Messages that are signed and encrypted are referred to as Secure/Multipurpose Internet Mail Extensions (S/MIME) messages. S/MIME is a means of securing client to client communication.
With S/MIME, senders can encrypt messages prior to sending them. The recipients can store the encrypted messages after receipt, decrypting them only to read them.
Communications Express Mail now includes the security advantages of S/MIME. Communications Express Mail users who are set up to use S/MIME can exchange signed or encrypted messages with other Communications Express Mail users, and with users of the Microsoft Outlook mail system or other mail clients that support S/MIME. See Requirements for Using S/MIME with Communications Express Mail in Sun Java Communications Suite 5 Installation Guide for more information.
For other clients that support S/MIME, see that client documentation for information on S/MIME configuration.
Chapter 14 Planning a Messaging Server Anti-Spam and Anti-Virus Strategy
Messaging Server provides many tools for dealing with unsolicited bulk email (UBE, or “spam”) and viruses. This chapter describes the various tools and strategies available for your use.
This chapter contains the following sections:
Anti-Spam and Anti-Virus Tools Overview
As more computers are connected to the Internet, and the ease of doing business online increases, the frequency of security incidents, including spam and viruses, continues to rise. You should plan your Messaging Server deployment to deal with these problems.
Mail traffic passing into, through, and out of Messaging Server can be separated into distinct channels according to various criteria. This criteria includes source and destination email addresses as well as source IP address or subnet. You can apply different processing characteristics to these different mail flows, or channels. Consequently, you can use different access controls, mail filters, processing priorities, and tools in different ways and combinations on these channels. For example, you can process mail originating from within your domain differently from mail originating from outside your deployment.
In addition to channel-based message flow classification, another useful classification is mailing list traffic. Traffic for a given mailing list can come into Messaging Server through a number of different channels and go back out through a number of different channels. When using mailing lists, you can find it helpful to think in terms of the list itself and not in terms of channels. Messaging Server recognizes this and enables many of the channel-specific spam fighting tools to also be applied in a mailing-list specific fashion.
The following summarizes the anti-spam and anti-virus tools you can use with Messaging Server:
-
Access Control. Rejects mail from known spam sources and enables control over who can send or receive email within the organization
-
Mailbox Filtering. Enables users to manage their own spam filters through a Web interface, controlling the nature of mail delivered to their mailboxes
-
Address Verification. Refuses mail with invalid originator addresses
-
Real-time Blackhole List. Refuses mail from recognized spam sources as identified by the Mail Abuse Protection System”s Real-time Blackhole List (MAPS RBL), a responsibly managed, dynamically updated list of known spam sources
-
Relay Blocking. Prevents abusers from using a mail system as a relay to send their spam to tens of thousands of recipients
-
Authentication Service. Enables password authentication in an SMTP server with the Simple Authentication and Security Layer (SASL) protocol
-
Sidelining. Silently sidelines or even deletes potential spam messages
-
Comprehensive Tracing. Uses reliable mechanisms for identifying a message’s source
-
Conversion Channel. Integrates with third-party anti-virus or anti-spam products
-
Milter. Provides a plug-in interface for third-party software to validate, modify, or block messages as they pass through the MTA.
You can use these tools individually or together. No one tool by itself will block all spam. However, taken together, these tools provide an effective means of combatting unauthorized use of your mail system. The following sections provide more details on these tools. For more information, see the Sun Java System Messaging Server 6.3 Administration Guide.
Rejecting Mail
Messaging Server has a general purpose mechanism that you can use to reject mail in accordance with a variety of criteria. This criteria includes the message source or destination email addresses, as well as source IP address. For example, you can use this mechanism to refuse mail from specific senders or entire domains (such as mail from spam@public.com). Should you have large lists of screening information, you can extend your lists with a database that stores the access criteria. While not UBE-related, this same access control mechanism is also suitable for maintaining a database of internal users who are or are not allowed to send mail out certain channels. For example, you can restrict on a per-user basis who can or cannot send or receive Internet mail.
See Access Controls for more information.
Mailbox Filtering
Messaging Server provides mail filters on a per-user, per-channel, and system-wide basis. Per-user channels can be managed from any web browser in Messenger Express. Using these filters, users can control what mail messages are delivered to their mailbox. For example, a user tired of “make money fast” UBE can specify that any message with such a subject be rejected. Mail filtering in Messaging Server is based on the Sieve filtering language (RFCs 3028 and 3685) developed by the Internet Engineering Task Force (IETF).
See Using Mailbox Filters for more information.
You can also implement content-based filtering or virus scanning through the use of third-party content filtering software, such as Brightmail and SpamAssassin. See Anti-Spam and Anti-Virus Considerations for more information.
Address Verification
UBE messages often use invalid originator addresses. The Messaging Server SMTP server can take advantage of this by reflecting messages with invalid originator addresses. If the originator's address does not correspond to a valid host name, as determined by a query to the DNS server, the message can be rejected. Note that a potential performance penalty can be incurred with such use of the DNS.
You enable address verification on a per-channel basis with the mailfromdnsverify channel keyword described in the Sun Java System Messaging Server 6.3 Administration Guide.
Real-time Blackhole List
The Mail Abuse Protection System’s Real-time Blackhole List (MAPS RBL) is a dynamically updated list of known UBE sources identified by source IP address. The Messaging Server SMTP server supports use of the MAPS RBL and can reject mail coming from sources identified by the MAPS RBL as originators of UBE. The MAPS RBL is a free service provided through the Internet DNS.
For more information, see:
Use of the RBL by the Messaging Server SMTP server is enabled with the ENABLE_RBL option of the MTA Dispatcher.
Relay Blocking
A comprehensive UBE strategy should include both ways to prevent users from receiving UBE (access controls, mailbox filtering, address verification, RBL) as well as preventing users from unauthorized relay of mail from your system to other systems. This second method is called relay blocking. In its simplest form, relay blocking is achieved by enabling local users and systems to relay mail while rejecting relay attempts from non-local systems. Using IP addresses as the differentiator easily and securely makes this differentiation between local versus non-local. By default, Messaging Server enables relay blocking upon installation. See Configuring Anti-Relaying with Mapping Tables for more information.
Authentication Services
The Messaging Server SMTP server implements the Simple Authentication and Security Layer (SASL, RFC2222) protocol. SASL can be used with POP and IMAP clients to provide password-based access to your SMTP server. A typical usage for SASL is to permit mail relaying for external authenticated users. This solves the common problem posed by local users who use ISPs from home or while traveling. Such users, when connecting to your mail system, will have non-local IP addresses. Any relay blocking that takes into account only the source IP address will not permit these users to relay mail. This difficulty is overcome through the use of SASL, which enables these users to authenticate themselves. Once authenticated, the users are permitted to relay mail.
Sidelining Messages
The access control mechanisms discussed previously can also defer the processing of suspect messages for later, manual inspection. Or, rather than sideline, the mechanisms can change the destination address, thus routing the suspect mail to a specific mailbox or simply deleting it silently. This tactic is useful when UBE is being received from a known, fixed origin and outright rejection will only cause the abuser to change the point of origin. Similar features are available for Messaging Server mailing lists. Great care should exercised when silently deleting mail to ensure that valid senders are not affected.
Comprehensive Tracing
Messaging Server’s SMTP server discovers and records crucial origination information about every incoming mail message, including, for example, source IP address and the corresponding host name. All discovered information is recorded in the message’s trace fields (for example, the Received: header line) as well as in log files, if they are so configured. Availability of such reliable information is crucial in determining the source of UBE, which often has forged headers. Sites can use their own preferred reporting tools to access this information, which is stored as plain text.
Conversion Channel
The conversion channel is a very general purpose interface where you can invoke a script or another program to perform arbitrary body part processing of an email message. The conversion program hands off each MIME body part (not the entire message) to the program or script and can replace the body part with the output of the program or script. Conversion channels can be used to convert one file format to another (for example, text to PostScript), to convert one language to another, perform content filtering for company sensitive information, scan for viruses and replace them with something else.
Integration with Third-Party Products
Content-filtering software from third-party suppliers can be hooked in to your deployment through Messaging Server’s conversion channel. Channel keywords are used to enable mail filtering using anti-spam and anti-virus products, such as Brightmail or SpamAssassin. You can configure the MTA to filter for all messages or only those going from or to certain channels, or to set the granularity at a per-user level. A user can decide to use spam or virus filtering, or both. (SpamAssassin only filters for spam.)
An extensive Sieve support enables great flexibility to set the disposition of the message determined to be spam or virus. You can take the default action of discarding the virus and spam, or filing the spam into a special folder. But using Sieve, you can forward a copy of the message to some special account, add a custom header, or use the spamtest Sieve extension to take different action based on a rating returned by SpamAssassin.
Milter
Milter refers to the Sendmail Content Management API and also to software written using this API. Milter provides a plug-in interface for third-party software to validate, modify, or block messages as they pass through the MTA. In sendmail, milter consists of support code in sendmail itself and a separate milter library. Filter authors link their filters against this library to produce a server. Sendmail is then configured to connect to these milter servers. Messaging Server provides a library that emulates the sendmail side of the milter interface. Consequently, milters written for sendmail can also be used with Messaging Server. The milter server can run in a variety of configurations. It can run on a separate system of its own, on the same system as Messaging Server, in a single system deployment, or in a two-tier deployment. Messaging Server also supports connecting to multiple milter servers.
Anti-Spam and Anti-Virus Considerations
This section describes issues to keep in mind when planning your deployment to use anti-spam or anti-virus technologies.
Architecture Issues with Anti-Spam and Anti-Virus Deployments
The Messaging Server MTA can reside on the same system as the mail filtering system, such as Brightmail or SpamAssassin, or you can use separate systems. One of the advantages of separating the MTA from the mail filtering servers is that you can add more processing power for the filtering simply by adding more hardware and cloning the servers. While the system is capable and not overloaded, you can have the mail filtering server software collocated with the MTA.
In general, consider deploying a “farm” of Brightmail severs that the MTAs utilize to filter mail. You can configure MTAs to use a list of Brightmail server names, which essentially the MTAs will load balance on. (This load balancing functionality is provided by the Brightmail SDK.) The advantage of having the Brightmail server farm is that when you need more processing power, you can simply add more Brightmail servers.
Mail filtering products tend to be CPU-intensive. Creating an architecture that separates the MTA and the mail filtering products onto their own machines provides for better overall performance of the messaging deployment.
Note –
Because mail filtering servers tend to be CPU-intensive in nature, you could end up with an architecture consisting of more mail filtering systems than the MTA hosts they are filtering for.
In larger deployments, consider also creating inbound and outbound mail filtering pools of servers that are associated with the respective inbound and outbound MTA pools. You can also create a “swing” pool that can be utilized as either an inbound or outbound pool, in response to need in either area.
As with the rest of the deployment, you need to monitor the mail filtering tier. A threshold of 50 percent CPU utilization is a good rule of thumb to follow. Once this threshold has been met, you need to consider adding more capacity to the mail filtering tier.
Security Issues with Anti-Spam and Anti-Virus Deployments
When planning to deploy anti-spam or anti-virus technology, keep in mind that an incorrect deployment can defeat your security measures. Figure 14–1 shows an incorrect deployment of an anti-spam/anti-virus filter solution.
Figure 14–1 Incorrect Deployment of Anti-Spam/Virus Solution
Figure 14–2 shows a correct deployment of an anti-spam/virus filter solution.
Figure 14–2 Correct Deployment of Anti-Spam/Virus Solution
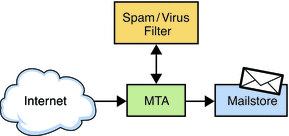
The MTA performs certain functions well, including:
-
Rejecting messages as early as possible
-
Per-user configuration and policy
-
Email security and routing policy
-
Mail queue management
The anti-spam/virus filter is good at determining if an email is spam or has a virus, but is generally not nearly as good at doing the things expected of a good MTA. Thus, do not depend on an anti-spam/virus filter to do those things. Your deployment is more “correct” when the anti-spam/virus filter is well integrated with the MTA, which is the case with Messaging Server. Messaging Server spam filter plug-in support provides all the potential reasons to reject a message early and applies all reasons at the same time.
A robust MTA, such as Messaging Server's, contains security features (SSL/TLS, traffic partitioning by IP address, early address rejection to reduce denial-of-service attacks, connection throttling by IP address/domain, and so on), which are defeated when an anti-spam/virus filter is deployed in front. Furthermore, anti-spam/virus filters that communicate by using the SMTP protocol often do not follow the robustness requirements of SMTP and thus lose email when they shouldn't. A correct deployment should have the anti-spam/virus filter working in conjunction with a robust MTA.
Implementing an RBL
In general, implementing an RBL provides the most immediate benefit to reducing spam traffic. A good RBL implemented by your MTAs immediately reduces spam by a minimum of 10 percent. In some cases, this number could approach 50 percent.
You can use your RBL and Brightmail together. If Brightmail takes care of 95 out of 100 emails for a certain IP address within some amount of time you should add that IP address to your RBL. You can adjust the RBLs for Brightmail’s false positives when you do your Brightmail analysis. That makes the RBL much more proactive in handling a specific wave of spam.
Common Anti-Spam and Anti-Virus Deployment Scenarios
This section describes common deployment scenarios for Brightmail and SpamAssassin. See the Sun Java System Messaging Server 6.3 Administration Guide for more information.
Using Symantec Brightmail
There are several common deployment scenarios for Symantec Brightmail:
-
Processing incoming messages to the local message store (ims-ms channel)
-
Processing messages going out to the Internet (tcp-local channel)
-
Processing messages coming in from the Internet (tcp-local channel)
-
Processing messages going to a specific domain (per-domain option)
-
Processing messages going to specific users (per-user option)
-
Setting up Brightmail processing as a Class-of-Service Option
If Brightmail implements both spam and virus checking, MTA message throughput can be reduced by as much 50 percent. To keep up with MTA throughput, you might need two Brightmail servers for each MTA.
Using SpamAssassin
Messaging Server supports the use of SpamAssassin, a freeware mail filter used to identify spam. SpamAssassin consists of a library written in Perl and a set of applications and utilities that can be used to integrate SpamAssassin into messaging systems.
SpamAssassin calculates a score for every message. Scores are calculated by performing a series of tests on message header and body information. Each test either succeeds or fails, and the score is adjusted accordingly. Scores are real numbers and may be positive or negative. Scores that exceed a certain threshold (typically 5.0) are considered to be spam.
SpamAssassin is highly configurable. Tests can be added or removed at any time and the scores of existing tests can be adjusted. This is all done through various configuration files. Further information on SpamAssassin can be found on the SpamAssassin Web site:
The same mechanism used for connecting to the Brightmail spam and virus scanning library can be used to connect to the SpamAssassin spamd server.
Using Symantec AntiVirus Scan Engine (SAVSE)
Messaging Server supports the use of SAVSE. SAVSE is a TCP/IP server application and communications API that provides high-performance virus scanning. It is designed to protect traffic served through, or stored on, network infrastructure devices.
Developing an Anti-Spam and Anti-Virus Site Policy
When developing a policy for preventing spam and relaying, strike a balance between providing safety from spam and providing a site where emails are delivered in a timely fashion. The best policy is therefore to initially provide a core set of measures that do not take up too much processing time but trap the majority of spam. You can then define this core set of measures after stress testing the final architecture. Start with the initial measures below. Once you have deployed your system, monitor trapped and non-trapped spam to fine tune the system and replace or add new functions if required.
Use the following set of measures as a starting point for your site’s anti-spam and anti-virus policy:
-
Anti-relay should be provided by the ORIG_SEND_ACCESS settings. This is structured to enable only subscribers and partnership users access to deliver externally bound SMTP mail.
-
Use authentication services to validate roaming users. These users verify their identity before being allowed to route externally bound SMTP mail.
-
Implement subject line checking for common spam phrases using the system-wide mailbox filters.
-
Set a maximum number of recipients using the holdlimit keyword. This will have the effect of sidelining potential spam traffic. The initial value could be set at 50 recipients and should be monitored over a period of time to determine whether a higher or lower value is required.
-
Set up dummy accounts that are then manually used by the postmasters to encourage spam to these specific accounts to identify new spam sites.
-
A message in which a virus has been detected should not be returned to the original sender and should not be forwarded to the intended recipient. There is no value in this because most viruses generate their own mail with forged sender addresses. It has become very rare that such infected messages will have any useful content.
-
Send infected messages to an engine that harvests and catalogues information about the virus. You can then use such information to create threat reports for your system administrators about new virus and worm outbreaks.
- © 2010, Oracle Corporation and/or its affiliates
