Part I Developing and Deploying Applications
Chapter 1 Setting Up a Development Environment
This chapter gives guidelines for setting up an application development environment in the Sun JavaTM System Application Server. Setting up an environment for creating, assembling, deploying, and debugging your code involves installing the mainstream version of the Application Server and making use of development tools. In addition, sample applications are available. These topics are covered in the following sections:
Installing and Preparing the Server for Development
For the Sun Java Enterprise System, Application Server installation is part of the system installation process. For more information, see http://www.sun.com/software/javaenterprisesystem/index.html.
For more information about stand-alone Application Server installation, see the Sun Java System Application Server Enterprise Edition 8.2 Installation Guide.
The following components are included in the full installation.
-
Application Server core, including:
-
J2EE 1.4 compliant application server
-
Administration Console
-
asadmin utility
-
deploytool
-
Other development and deployment tools
-
Sun Java System Message Queue software
-
J2SE 1.4.2
-
Java DB database, based on the Derby database from Apache
-
The High-Availability Database (HADB)
-
Load balancer plug-ins for web servers
-
-
JDK
-
Sample Applications
The NetBeans IDE bundles the Platform Edition of the Application Server, so information about this IDE is provided as well.
After you have installed Application Server, you can further optimize the server for development in these ways:
-
Locate utility classes and libraries so they can be accessed by the proper classloaders. For more information, see Using the System Classloader or Using the Common Classloader.
-
Set up debugging. For more information, see Chapter 4, Debugging Applications.
-
Configure the Java Virtual Machine (JVMTM) software. For more information, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
High Availability Features
High availability features such as load balancing and session failover are discussed in detail in the Sun Java System Application Server Enterprise Edition 8.2 High Availability Administration Guide. This Developer's Guide describes the following features in the following sections:
-
For information about HTTP session persistence, see Distributed Sessions and Persistence.
-
For information about checkpointing of the stateful session bean state, see Stateful Session Bean Failover.
-
For information about failover and load balancing for Java clients, see Chapter 8, Developing Java Clients.
-
For information about load balancing for message-driven beans, see Load-Balanced Message Inflow.
Tools
The following general tools are provided with the Application Server:
The following development tools are provided with the Application Server or downloadable from Sun:
The following third-party tools might also be useful:
The asadmin Command
The asadmin command allows you to configure a local or remote server and perform both administrative and development tasks at the command line. For general information about asadmin, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual.
The asadmin command is located in the install-dir/bin directory. Type asadmin help for a list of subcommands.
The Administration Console
The Administration Console lets you configure the server and perform both administrative and development tasks using a web browser. For general information about the Administration Console, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
To access the Administration Console, type https://host:4849 in your browser. The host is the name of the machine on which the Application Server is running.
NetBeans IDE
The NetBeansTM IDE (integrated development environment) allows you to create, assemble, and debug code from a single, easy-to-use interface. The Platform Edition of the Application Server is bundled with the NetBeans 5 IDE. For more information about using the NetBeans IDE, see http://www.netbeans.org.
The asant Utility
Apache Ant 1.6.5 is provided with the Application Server and can be launched from the bin directory using the command asant. The Application Server also provides server-specific tasks for deployment; see asant Assembly and Deployment Tool. The sample applications provided with the Application Server use Ant build.xml files; see Sample Applications.
For more information about Ant, see the Apache Software Foundation web site at http://ant.apache.org/.
deploytool
You can use the deploytool, provided with Application Server, to assemble J2EE applications and modules, configure deployment parameters, perform simple static checks, and deploy the final result. For more information about using the deploytool, see the J2EE 1.4 Tutorial at http://java.sun.com/j2ee/1.4/docs/tutorial/doc/index.html.
Verifier
The verifier tool checks a J2EE application file (EAR, JAR, WAR, RAR), including Java classes and deployment descriptors, for compliance with J2EE specifications. Use it to check whether an application has compliance bugs and to make applications portable across application servers. The verifier can be launched from the deploytool or from the command line. For more information, see The Deployment Descriptor Verifier.
Migration Tool
The Migration Tool converts and reassembles Java EE applications and modules developed on other application servers. This tool also generates a report listing how many files are successfully and unsuccessfully migrated, with reasons for migration failure. For more information and to download the Migration Tool, see http://java.sun.com/j2ee/tools/migration/index.html.
For additional information on migration, see the Sun Java System Application Server Enterprise Edition 8.2 Upgrade and Migration Guide.
Debugging Tools
You can use several debuggers with the Application Server. For more information, see Chapter 4, Debugging Applications.
Profiling Tools
You can use several profilers with the Application Server. For more information, see Profiling.
Sample Applications
Sample applications that you can examine and deploy are included with the full installation of the Application Server. You can also download these samples separately if you installed the Application Server without them initially.
If installed with the Application Server, the samples are in the install-dir/samples directory. The samples are organized in categories such as ejb, jdbc, connectors, i18n, and so on. Each sample category is further divided into subcategories. For example, under the ejb category are stateless, stateful, security, mdb, bmp, and cmp subcategories.
Most Application Server samples have the following directory structure:
-
The docs directory contains instructions for how to use the sample.
-
The build.xml file defines asant targets for the sample (see asant Assembly and Deployment Tool.
-
The build and javadocs directories are generated as a result of targets specified in the build.xml file.
-
The src/java directory under each component contains source code for the sample.
-
The src/conf directory under each component contains the deployment descriptors.
With a few exceptions, sample applications follow the standard directory structure described here: http://java.sun.com/blueprints/code/projectconventions.html.
The install-dir/samples/common-ant.xml file defines properties common to all sample applications and implements targets needed to compile, assemble, deploy and undeploy sample applications. In most sample applications, the build.xml file includes common-ant.xml.
For a detailed description of the helloworld sample and how to deploy and run it, see the associated documentation at:
install-dir/samples/ejb/stateless/apps/simple/docs/index.html
After you deploy the helloworld sample in Application Server, you can invoke it using the following URL:
http://server:port/helloworld
Chapter 2 Securing Applications
This chapter describes how to write secure J2EE applications, which contain components that perform user authentication and access authorization for servlets and EJB business logic. For information about administrative security for the server, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide. For general information about J2EE security, see the security chapter of the J2EE 1.4 Tutorial at http://java.sun.com/j2ee/1.4/docs/tutorial/doc/index.html.
This chapter contains the following sections:
Security Goals
In an enterprise computing environment, there are many security risks. The goal of the Sun Java System Application Server is to provide highly secure, interoperable, and distributed component computing based on the J2EE security model. Security goals include:
-
Full compliance with the J2EE security model (for more information, see the J2EE specification, v1.4 Chapter 3 Security).
-
Full compliance with the EJB v2.1 security model (for more information, see the Enterprise JavaBean specification v2.1 Chapter 15 Security Management). This includes EJB role-based authorization.
-
Full compliance with the Java Servlet v2.4 security model (for more information, see the Java Servlet specification, v2.4 Chapter 11 Security). This includes servlet role-based authorization.
-
Support for single sign-on across all Application Server applications within a single security domain.
-
Support for message security.
-
Security support for application clients.
-
Support for several underlying authentication realms, such as simple file and LDAP. Certificate authentication is also supported for SSL client authentication. For Solaris, OS platform authentication is supported in addition to these.
-
Support for declarative security through Application Server specific XML-based role mapping.
-
Support for JACC (Java Authorization Contract for Containers) pluggable authorization as included in the J2EE 1.4 specification and defined by JSR-115.
Application Server Specific Security Features
The Application Server supports the J2EE v1.4 security model, as well as the following features which are specific to the Application Server:
-
Message security; see Configuring Message Security
-
Single sign-on across all Application Server applications within a single security domain; see User Authentication for Single Sign-on
-
Programmatic login; see Programmatic Login
-
A GUI-based deploytool for building XML files containing the security information; see deploytool
Container Security
The component containers are responsible for providing J2EE application security. There are two security forms provided by the container:
Programmatic Security
Programmatic security involves an EJB component or servlet using method calls to the security API, as specified by the J2EE security model, to make business logic decisions based on the caller or remote user’s security role. Programmatic security should only be used when declarative security alone is insufficient to meet the application’s security model.
The J2EE specification, v1.4 defines programmatic security as consisting of two methods of the EJB EJBContext interface and two methods of the servlet HttpServletRequest interface. The Application Server supports these interfaces as specified in the specification.
For more information on programmatic security, see the following:
-
Section 3.3.6, Programmatic Security, in the J2EE Specification, v1.4
Declarative Security
Declarative security means that the security mechanism for an application is declared and handled externally to the application. Deployment descriptors describe the J2EE application’s security structure, including security roles, access control, and authentication requirements.
The Application Server supports the deployment descriptors specified by J2EE v1.4 and has additional security elements included in its own deployment descriptors; see Appendix A, Deployment Descriptor Files. Declarative security is the application deployer’s responsibility.
There are two levels of declarative security, as follows:
Application Level Security
The application XML deployment descriptor (application.xml) contains descriptors for all user roles for accessing the application’s servlets and EJB components. On the application level, all roles used by any application container must be listed in a role-name element in this file. The role names are scoped to the EJB XML deployment descriptors (ejb-jar.xml and sun-ejb-jar.xml files) and to the servlet XML deployment descriptors (web.xml and sun-web.xml files). The sun-application.xml file must also contain matching security-role-mapping elements for each role-name used by the application.
Component Level Security
Component level security encompasses web components and EJB components.
A secure web container authenticates users and authorizes access to a servlet or JSP by using the security policy laid out in the servlet XML deployment descriptors (web.xml and sun-web.xml files).
The EJB container is responsible for authorizing access to a bean method by using the security policy laid out in the EJB XML deployment descriptors (ejb-jar.xml and sun-ejb-jar.xml files).
Realm Configuration
This section covers the following topics:
Supported Realms
The following realms are supported in the Application Server:
-
file - Stores user information in a file. This is the default realm when you first install the Application Server.
-
certificate - Sets up the user identity in the Application Server security context, and populates it with user data obtained from cryptographically verified client certificates.
-
solaris - Allows authentication using Solaris username+password data. This realm is only supported on Solaris 9 and above.
For detailed information about configuring each of these realms, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
How to Configure a Realm
You can configure a realm in one of these ways:
-
In the Administration Console, open the Security component under the relevant configuration and go to the Realms page. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
-
Use the asadmin create-auth-realm command to configure realms on local servers. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual.
How to Set a Realm for an Application or Module
The following deployment descriptor elements have optional realm or realm-name data subelements or attributes that override the domain’s default realm:
-
sun-application element in sun-application.xml
-
web-app element in web.xml
-
as-context element in sun-ejb-jar.xml
-
client-container element in sun-acc.xml
-
client-credential element in sun-acc.xml
If modules within an application specify realms, these are ignored. If present, the realm defined in sun-application.xml is used, otherwise the domain’s default realm is used.
For example, a realm is specified in sun-application.xml as follows:
<sun-application>
...
<realm>ldap</realm>
</sun-application>
For more information about the deployment descriptor files and elements, see Appendix A, Deployment Descriptor Files.
Creating a Custom Realm
You can create a custom realm by providing a custom Java Authentication and Authorization Service (JAAS) login module class and a custom realm class. Note that client-side JAAS login modules are not suitable for use with the Application Server.
JAAS is a set of APIs that enable services to authenticate and enforce access controls upon users. JAAS provides a pluggable and extensible framework for programmatic user authentication and authorization. JAAS is a core API and is an underlying technology for Java EE security mechanisms. For more information about JAAS, refer to the JAAS specification for Java SDK, available at http://java.sun.com/products/jaas/.
For general information about realms and login modules, see the Security chapter of the J2EE 1.4 Tutorial.
Custom login modules must extend the com.sun.appserv.security.AppservPasswordLoginModule class. This class implements javax.security.auth.spi.LoginModule. Custom login modules must not implement LoginModule directly.
Custom login modules must provide an implementation for one abstract method defined in AppservPasswordLoginModule:
abstract protected void authenticateUser() throws LoginException
This method performs the actual authentication. The custom login module must not implement any of the other methods, such as login(), logout(), abort(), commit(), or initialize(). Default implementations are provided in AppservPasswordLoginModule which hook into the Application Server infrastructure.
The custom login module can access the following protected object fields, which it inherits from AppservPasswordLoginModule. These contain the user name and password of the user to be authenticated:
protected String _username; protected String _password;
The authenticateUser() method must end with the following sequence:
String[] grpList; // populate grpList with the set of groups to which // _username belongs in this realm, if any return commitUserAuthentication(_username, _password, _currentRealm, grpList);
Custom realms must extend the com.sun.appserv.security.AppservRealm class and implement the following methods:
public void init(Properties props) throws BadRealmException, NoSuchRealmException
This method is invoked during server startup when the realm is initially loaded. The props argument contains the properties defined for this realm in domain.xml. The realm can do any initialization it needs in this method. If the method returns without throwing an exception, the Application Server assumes the realm is ready to service authentication requests. If an exception is thrown, the realm is disabled.
public String getAuthType()
This method returns a descriptive string representing the type of authentication done by this realm.
public abstract Enumeration getGroupNames(String username) throws InvalidOperationException, NoSuchUserException
This method returns an Enumeration (of String objects) enumerating the groups (if any) to which the given username belongs in this realm.
JACC Support
JACC (Java Authorization Contract for Containers) is part of the J2EE 1.4 specification and defined by JSR-115. JACC defines an interface for pluggable authorization providers. This provides third parties with a mechanism to develop and plug in modules that are responsible for answering authorization decisions during J2EE application execution. The interfaces and rules used for developing JACC providers are defined in the JACC 1.0 specification.
The Application Server provides a simple file-based JACC-compliant authorization engine as a default JACC provider. To configure an alternate provider using the Administration Console, open the Security component under the relevant configuration, and select the JACC Providers component. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
Pluggable Audit Module Support
Audit modules collect and store information on incoming requests (servlets, EJB components) and outgoing responses. You can create a custom audit module. This section covers the following topics:
Configuring an Audit Module
To configure an audit module, you can perform one of the following tasks:
-
To specify an audit module using the Administration Console, open the Security component under the relevant configuration, and select the Audit Modules component. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
-
You can use the asadmin create-audit-module command to configure an audit module. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual.
The AuditModule Class
You can create a custom audit module by implementing a class that extends com.sun.appserv.security.AuditModule. The AuditModule class provides default “no-op” implementations for each of the following methods, which your custom class can override.
public void init(Properties props)
This method is invoked during server startup when the audit module is initially loaded. The props argument contains the properties defined for this module in domain.xml. The module can do any initialization it needs in this method. If the method returns without throwing an exception, the Application Server assumes the module realm is ready to service audit requests. If an exception is thrown the module is disabled.
public void authentication(String user, String realm, boolean success)
This method is invoked when an authentication request has been processed by a realm for the given user. The success flag indicates whether the authorization was granted or denied.
public void webInvocation(String user, HttpServletRequest req, String type, boolean success)
This method is invoked when a web container call has been processed by authorization. The success flag indicates whether the authorization was granted or denied. The req object is the standard HttpServletRequest object for this request. The type string is one of hasUserDataPermission or hasResourcePermission (see JSR-115).
public void ejbInvocation(String user, String ejb, String method, boolean success)
This method is invoked when an EJB container call has been processed by authorization. The success flag indicates whether the authorization was granted or denied. The ejb and method strings describe the EJB component and its method that is being invoked.
The server.policy File
Each Application Server domain has its own standard J2SE policy file, located in domain-dir/config. The file is named server.policy.
The Application Server is a J2EE 1.4 compliant application server. As such, it follows the requirements of the J2EE specification, including the presence of the security manager (the Java component that enforces the policy) and a limited permission set for J2EE application code.
This section covers the following topics:
Default Permissions
Internal server code is granted all permissions. These are covered by the AllPermission grant blocks to various parts of the server infrastructure code. Do not modify these entries.
Application permissions are granted in the default grant block. These permissions apply to all code not part of the internal server code listed previously. The Application Server does not distinguish between EJB and web module permissions. All code is granted the minimal set of web component permissions (which is a superset of the EJB minimal set).
A few permissions above the minimal set are also granted in the default server.policy file. These are necessary due to various internal dependencies of the server implementation. J2EE application developers must not rely on these additional permissions.
One additional permission is granted specifically for using connectors. If connectors are not used in a particular domain, you should remove this permission, because it is not otherwise necessary.
Changing Permissions for an Application
The default policy for each domain limits the permissions of J2EE deployed applications to the minimal set of permissions required for these applications to operate correctly. Do not add extra permissions to the default set (the grant block with no codebase, which applies to all code). Instead, add a new grant block with a codebase specific to the applications requiring the extra permissions, and only add the minimally necessary permissions in that block.
If you develop multiple applications that require more than this default set of permissions, you can add the custom permissions that your applications need. The com.sun.aas.instanceRoot variable refers to the domain-dir. For example:
grant "file:${com.sun.aas.instanceRoot}/applications/j2ee-apps/-" { ... }
You can add permissions to stub code with the following grant block:
grant "file:${com.sun.aas.instanceRoot}/generated/-" { ... }
In general, you should add extra permissions only to the applications or modules that require them, not to all applications deployed to a domain. For example:
grant "file:${com.sun.aas.instanceRoot}/applications/j2ee-apps/MyApp/-" { ... }
For a module:
grant "file:${com.sun.aas.instanceRoot}/applications/j2ee-modules/MyModule/-" { ... }
Do not add extra permissions to the default set (the grant block with no codebase, which applies to all code). Instead, add a new grant block with a codebase specific to the application requiring the extra permissions, and only add the minimally necessary permissions in that block.
Note –
Do not add java.security.AllPermission to the server.policy file for application code. Doing so completely defeats the purpose of the security manager, yet you still get the performance overhead associated with it.
As noted in the J2EE specification, an application should provide documentation of the additional permissions it needs. If an application requires extra permissions but does not document the set it needs, contact the application author for details.
As a last resort, you can iteratively determine the permission set an application needs by observing AccessControlException occurrences in the server log. If this is not sufficient, you can add the -Djava.security.debug=failure JVM option to the domain. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide or the Sun Java System Application Server Enterprise Edition 8.2 Administration Reference.
You can use the J2SE standard policytool or any text editor to edit the server.policy file. For more information, see:
http://java.sun.com/docs/books/tutorial/security1.2/tour2/index.html
For detailed information about the permissions you can set in the server.policy file, see:
http://java.sun.com/j2se/1.4/docs/guide/security/permissions.html
The Javadoc for the Permission class is at:
http://java.sun.com/j2se/1.4/docs/api/java/security/Permission.html
Configuring Message Security
In message security, security information is applied at the message layer and travels along with the web services message. Web Services Security (WSS) in the SOAP layer is the use of XML Encryption and XML Digital Signatures to secure SOAP messages. WSS profiles the use of various security tokens including X.509 certificates, SAML assertions, and username/password tokens to achieve this.
Message layer security differs from transport layer security in that message layer security can be used to decouple message protection from message transport so that messages remain protected after transmission, regardless of how many hops they travel on.
For more information about message security, see the following:
-
The J2EE 1.4 Tutorial chapter titled Security, which can be viewed from http://java.sun.com/j2ee/1.4/docs/tutorial/doc/index.html
-
The Sun Java System Application Server Enterprise Edition 8.2 Administration Guide chapter titled Configuring Message Security
-
The Oasis Web Services Security (WSS) specification at http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0.pdf
The following web services security topics are discussed in this section:
Message Security Responsibilities
Message security responsibilities are assigned to the following:
Application Developer
The application developer can implement message security, but is not responsible for doing so. Message security can be set up by the System Administrator so that all web services are secured, or set up by the Application Deployer when the Application Server provider configuration is insufficient.
The application developer is responsible for the following:
-
Determining if an application-specific policy is necessary for an application. If so, ensure that policy is satisfied at application assembly, or communicate the requirement for application-specific message security to the Application Deployer, or take care of implementing the application-specific policy.
-
Determining if message security is necessary at the Application Server level. If so, ensure that need is communicated to the System Administrator, or take care of implementing message security at the Application-Server level.
Application Deployer
The application deployer is responsible for:
-
Securing the application if it has not been appropriately secured by upstream roles (the developer or assembler) and only if an application-specific policy is appropriate for the application.
-
Implementing application-specific security by adding the message security binding to the web service endpoint.
-
Modifying Sun-specific deployment descriptors to add message binding information.
These security tasks are discussed in Application-Specific Message Protection. An example application using message security is discussed in Understanding and Running the Example Application.
System Administrator
The system administrator is responsible for:
-
Configuring message security providers on the Application Server.
-
Managing user databases.
-
Managing keystore and truststore files.
-
Configuring a Java Cryptography Extension (JCE) provider if using Encryption and running a version of the Java SDK prior to version 1.5.0.
-
Installing the samples server in order to work with the example message security applications.
A system administrator uses the Admin Console or the asadmin tool to manage server security settings and keytool to manage certificates. System administrator tasks are discussed in the Configuring Message Security chapter of the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
Application-Specific Message Protection
When the Application Server provided configuration is insufficient for your security needs, and you want to override the default protection, you can apply application-specific message security to a web service.
Application-specific security is implemented by adding the message security binding to the web service endpoint, whether it is an EJB or servlet web service endpoint. Modify Sun-specific XML files to add the message binding information.
For more details on message security binding for EJB web services, servlet web services, and clients, see the XML file descriptions in Appendix A, Deployment Descriptor Files.
-
For sun-ejb-jar.xml, see The sun-ejb-jar.xml File.
-
For sun-web.xml, see The sun-web.xml File.
-
For sun-application-client.xml, see The sun-application-client.xml file.
This section contains the following topics:
-
Using a Signature to Enable Message Protection for All Methods
-
Configuring Message Protection For a Specific Method Based on Digital Signatures
Using a Signature to Enable Message Protection for All Methods
To enable message protection for all methods using digital signature, update the message-security-binding element for the EJB web service endpoint in the application’s sun-ejb-jar.xml file. In this file, add request-protection and response-protection elements, which are analogous to the request-policy and response-policy elements discussed in the Configuring Message Security chapter of the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide. In order to apply the same protection mechanisms for all methods, leave the method-name element blank. Configuring Message Protection For a Specific Method Based on Digital Signatures discusses listing specific methods or using wildcard characters.
This section uses the sample application discussed in Understanding and Running the Example Application to apply application-level message security in order to show only the differences necessary for protecting web services using various mechanisms.
 To enable message protection for all methods using
digital signature
To enable message protection for all methods using
digital signature
-
In a text editor, open the application’s sun-ejb-jar.xml file.
For the xms example, this file is located in the directory install-dir /samples/webservices/security/ejb/apps/xms/xms-ejb/src/conf.
-
Modify the sun-ejb-jar.xml file by adding the message-security-binding element as shown:
<sun-ejb-jar> <enterprise-beans> <unique-id>1</unique-id> <ejb> <ejb-name>HelloWorld</ejb-name> <jndi-name>HelloWorld</jndi-name> <webservice-endpoint> <port-component-name>HelloIF</port-component-name> <endpoint-address-uri>service/HelloWorld</endpoint-address-uri> <message-security-binding auth-layer="SOAP"> <message-security> <request-protection auth-source="content" /> <response-protection auth-source="content"/> </message-security> </message-security-binding> </webservice-endpoint> </ejb> </enterprise-beans> </sun-ejb-jar> -
Compile, deploy, and run the application as described in To Run the Sample Application.
Configuring Message Protection For a Specific Method Based on Digital Signatures
To enable message protection for a specific method, or for a set of methods that can be identified using a wildcard value, follow these steps. As in the example discussed in Using a Signature to Enable Message Protection for All Methods, to enable message protection for a specific method, update the message-security-binding element for the EJB web service endpoint in the application’s sun-ejb-jar.xml file. To this file, add request-protection and response-protection elements, which are analogous to the request-policy and response-policy elements discussed in the Configuring Message Security chapter of the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide. The Administration Guide includes a table listing the set and order of security operations for different request and response policy configurations.
This section uses the sample application discussed in Understanding and Running the Example Application to apply application-level message security in order to show only the differences necessary for protecting web services using various mechanisms.
 To enable message protection for a particular method
or set of methods using digital signature
To enable message protection for a particular method
or set of methods using digital signature
-
In a text editor, open the application’s sun-ejb-jar.xml file.
For the xms example, this file is located in the directory install-dir/samples/webservices/security/ejb/apps/xms/xms-ejb/src/conf.
-
Modify the sun-ejb-jar.xml file by adding the message-security-binding element as shown:
<sun-ejb-jar> <enterprise-beans> <unique-id>1</unique-id> <ejb> <ejb-name>HelloWorld</ejb-name> <jndi-name>HelloWorld</jndi-name> <webservice-endpoint> <port-component-name>HelloIF</port-component-name> <endpoint-address-uri>service/HelloWorld</endpoint-address-uri> <message-security-binding auth-layer="SOAP"> <message-security> <message> <java-method> <method-name>ejbCreate</method-name> </java-method> </message> <message> <java-method> <method-name>sayHello</method-name> </java-method> </message> <request-protection auth-source="content" /> <response-protection auth-source="content"/> </message-security> </message-security-binding> </webservice-endpoint> </ejb> </enterprise-beans> </sun-ejb-jar> -
Compile, deploy, and run the application as described in To Run the Sample Application.
Understanding and Running the Example Application
This section discusses the WSS sample application, xms, which is located in the directory install-dir/samples/webservices/security/ejb/apps/xms/. This directory and this sample application is installed on your system only if you have selected to install the samples server when you installed the Application Server. If you have not installed the samples, see To Set Up the Sample Application.
The objective of this sample application is to demonstrate how a web service can be secured with WSS. The web service in the xms example is a simple web service implemented using a J2EE EJB endpoint and a web service endpoint implemented using a servlet. In this example, a service endpoint interface is defined with one operation, sayHello, which takes a string then sends a response with Hello prefixed to the given string. You can view the WSDL file for the service endpoint interface at install-dir/samples/webservices/security/ejb/apps/xms/xms-ejb/src/conf/HelloWorld.wsdl.
In this application, the client lookups the service using the JNDI name java:comp/env/service/HelloWorld and gets the port information using a static stub to invoke the operation using a given name. For the name Duke, the client gets the response Hello Duke!
This example shows how to use message security for web services at the Application Server level and at the application level. The WSS message security mechanisms implement message-level authentication (for example, XML digital signature and encryption) of SOAP web services invocations using the X.509 and username/password profiles of the OASIS WS-Security standard, which can be viewed from the following URL:
http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-soap-message-security-1.0.pdf
This section includes the following topics:
 To Set Up the Sample Application
To Set Up the Sample Application
Before You Begin
The example application is located in the directory install-dir/samples/webservices/security/ejb/apps/xms/. For ease of reference throughout the rest of this section, this directory is referred to as simply app-dir/xms/.
In order to have access to this sample application, you must have installed the samples server during installation of the Application Server. To check to see if the samples are installed, browse to the directory install-dir/samples/webservices/security/ejb/apps/xms/. If this directory exists, you do not need to follow the steps in the following section. If this directory does not exist, the samples server is not installed, and must be installed for access to the sample application discussed here.
-
Start the installation for the Application Server.
-
Click Next on the Welcome page.
-
Click Yes on the Software License Agreement page. Click Next.
-
Click Next to accept the installation directory, or change it to match the location where the Application Server is currently installed.
-
Select Continue to install to the same directory.
You want to do this because you want the samples/ directory to be a subdirectory of the Application Server directory, install-dir/samples/.
-
Reenter the Admin User Name and Password. Click Next.
You are on the page where you select to install just the samples.
-
Deselect everything except Create Samples Server. Click Next.
-
Click Install Now to install the samples.
-
Click Finish to complete the installation.
 To Run the Sample Application
To Run the Sample Application
-
Make sure that the Application Server is running.
Message security providers are set up when the asant targets are run, so you don’t need to configure these on the Application Server prior to running this example.
-
If you are not running HTTP on the default port of 8080, change the WSDL file for the example to reflect the change, and change the common.properties file to reflect the change as well.
The WSDL file for this example is located at install-dir/samples/webservices/security/ejb/apps/xms/xms-ejb/src/conf/HelloWorld.wsdl. The port number is in the following section:
<service name="HelloWorld"> <port name="HelloIFPort" binding="tns:HelloIFBinding"> <soap:address location="http://localhost:8080/service/HelloWorld"/> </port> </service>Verify that the properties in the install-dir/samples/common.properties file are set properly for your installation and environment. If you need more description of this file, refer to the Configuration section for the web services security applications at install-dir/samples/webservices/security/docs/common.html#Logging.
-
Change to the install-dir/samples/webservices/security/ejb/apps/xms/ directory.
-
Run the following asant targets to compile, deploy, and run the example application:
If the sample has compiled and deployed properly, you see the following response on your screen after the application has run:
run:[echo] Running the xms program:[exec] Established message level security : Hello Duke!
-
To undeploy the sample, run the following asant target:
asant undeploy
All of the web services security examples use the same web service name (HelloWorld) and web service ports in order to show only the differences necessary for protecting web services using various mechanisms. Make sure to undeploy an application when you have completed running it, or you receive an Already in Use error and deployment failures when you try to deploy another web services example application.
Programmatic Login
Programmatic login allows a deployed J2EE application to invoke a login method. If the login is successful, a SecurityContext is established as if the client had authenticated using any of the conventional J2EE mechanisms.
Programmatic login is useful for an application having special needs that cannot be accommodated by any of the J2EE standard authentication mechanisms.
Note –
Programmatic login is specific to the Application Server and not portable to other application servers.
This section contains the following topics:
Precautions
The Application Server is not involved in how the login information (user, password) is obtained by the deployed application. Programmatic login places the burden on the application developer with respect to assuring that the resulting system meets their security requirements. If the application code reads the authentication information across the network, it is up to the application to determine whether to trust the user.
Programmatic login allows the application developer to bypass the application server-supported authentication mechanisms and feed authentication data directly to the security service. While flexible, this capability should not be used without some understanding of security issues.
Since this mechanism bypasses the container-managed authentication process and sequence, the application developer must be very careful in making sure that authentication is established before accessing any restricted resources or methods. It is also the application developer’s responsibility to verify the status of the login attempt and to alter the behavior of the application accordingly.
The programmatic login state does not necessarily persist in sessions or participate in single sign-on.
Lazy authentication is not supported for programmatic login. If an access check is reached and the deployed application has not properly authenticated via the programmatic login method, access is denied immediately and the application might fail if not properly coded to account for this occurrence.
Granting Programmatic Login Permission
The ProgrammaticLoginPermission permission is required to invoke the programmatic login mechanism for an application. This permission is not granted by default to deployed applications because this is not a standard J2EE mechanism.
To grant the required permission to the application, add the following to the domain-dir/config/server.policy file:
grant codeBase "file:jar-file-path" {
permission com.sun.appserv.security.ProgrammaticLoginPermission
"login";
};
The jar-file-path is the path to the application’s JAR file.
For more information about the server.policy file, see The server.policy File
The ProgrammaticLogin Class
The com.sun.appserv.security.ProgrammaticLogin class enables a user to perform login programmatically. This class has four login methods, two for servlets or JSP files and two for EJB components.
The login methods for servlets or JSP files have the following signatures:
public java.lang.Boolean login(String user, String password,
javax.servlet.http.HttpServletRequest request,
javax.servlet.http.HttpServletResponse response)
public java.lang.Boolean login(String user, String password,
String realm, javax.servlet.http.HttpServletRequest request,
javax.servlet.http.HttpServletResponse response, boolean errors)
throws java.lang.Exception
The login methods for EJB components have the following signatures:
public java.lang.Boolean login(String user, String password)
public java.lang.Boolean login(String user, String password,
String realm, boolean errors) throws java.lang.Exception
All of these login methods:
-
Perform the authentication
-
Return true if login succeeded, false if login failed
The login occurs on the realm specified unless it is null, in which case the domain’s default realm is used. The methods with no realm parameter use the domain’s default realm.
If the errors flag is set to true, any exceptions encountered during the login are propagated to the caller. If set to false, exceptions are thrown.
On the client side, realm and errors parameters are ignored and the actual login does not occur until a resource requiring a login is accessed. A java.rmi.AccessException with COBRA NO_PERMISSION occurs if the actual login fails.
The logout methods for servlets or JSP files have the following signatures:
public java.lang.Boolean logout(HttpServletRequest request,
HttpServletResponse response)
public java.lang.Boolean logout(HttpServletRequest request,
HttpServletResponse response, boolean errors)
throws java.lang.Exception
The logout methods for EJB components have the following signatures:
public java.lang.Boolean logout()
public java.lang.Boolean logout(boolean errors)
throws java.lang.Exception
All of these logout methods return true if logout succeeded, false if logout failed.
If the errors flag is set to true, any exceptions encountered during the logout are propagated to the caller. If set to false, exceptions are thrown.
User Authentication for Single Sign-on
The single sign-on feature of the Application Server allows multiple web applications deployed to the same virtual server to share the user authentication state. With single sign-on enabled, users who log in to one web application become implicitly logged into other web applications on the same virtual server that require the same authentication information. Otherwise, users would have to log in separately to each web application whose protected resources they tried to access.
An example application using the single sign-on scenario could be a consolidated airline booking service that searches all airlines and provides links to different airline web sites. Once the user signs on to the consolidated booking service, the user information can be used by each individual airline site without requiring another sign-on.
Single sign-on operates according to the following rules:
-
Single sign-on applies to web applications configured for the same realm and virtual server. The realm is defined by the realm-name element in the web.xml file. For information about virtual servers, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
-
As long as users access only unprotected resources in any of the web applications on a virtual server, they are not challenged to authenticate themselves.
-
As soon as a user accesses a protected resource in any web application associated with a virtual server, the user is challenged to authenticate himself or herself, using the login method defined for the web application currently being accessed.
-
Once authenticated, the roles associated with this user are used for access control decisions across all associated web applications, without challenging the user to authenticate to each application individually.
-
When the user logs out of one web application (for example, by invalidating the corresponding session), the user’s sessions in all web applications are invalidated. Any subsequent attempt to access a protected resource in any application requires the user to authenticate again.
The single sign-on feature utilizes HTTP cookies to transmit a token that associates each request with the saved user identity, so it can only be used in client environments that support cookies.
To configure single sign-on, set the following properties in the virtual-server element of the domain.xml file:
-
sso-enabled - If false, single sign-on is disabled for this virtual server, and users must authenticate separately to every application on the virtual server. The default is true.
-
sso-max-inactive-seconds - Specifies the time after which a user’s single sign-on record becomes eligible for purging if no client activity is received. Since single sign-on applies across several applications on the same virtual server, access to any of the applications keeps the single sign-on record active. The default value is 5 minutes (300 seconds). Higher values provide longer single sign-on persistence for the users at the expense of more memory use on the server.
-
sso-reap-interval-seconds - Specifies the interval between purges of expired single sign-on records. The default value is 60.
Here is an example configuration with all default values:
<virtual-server id="server" ... >
...
<property name="sso-enabled" value="true"/>
<property name="sso-max-inactive-seconds" value="450"/>
<property name="sso-reap-interval-seconds" value="80"/>
</virtual-server>
Defining Roles
You define roles in the J2EE deployment descriptor file, web.xml, and the corresponding role mappings in the Application Server deployment descriptor file, sun-application.xml (or sun-web.xml for individually deployed web modules).
For more information regarding web.xml elements, see Chapter 13, “Deployment Descriptor,” of the Java Servlet Specification, v2.4. For more information regarding sun-web.xml and sun-application.xml elements, see Appendix A, Deployment Descriptor Files.
Each security-role-mapping element in the sun-application.xml or sun-web.xml file maps a role name permitted by the web application to principals and groups. For example, a sun-web.xml file for an individually deployed web module might contain the following:
<sun-web-app>
<security-role-mapping>
<role-name>manager</role-name>
<principal-name>jgarcia</principal-name>
<principal-name>mwebster</principal-name>
<group-name>team-leads</group-name>
</security-role-mapping>
<security-role-mapping>
<role-name>administrator</role-name>
<principal-name>dsmith</principal-name>
</security-role-mapping>
</sun-web-app>
Note that the role-name in this example must match the role-name in the security-role element of the corresponding web.xml file.
Note that for J2EE applications (EAR files), all security role mappings for the application modules must be specified in the sun-application.xml file. For individually deployed web modules, the roles are always specified in the sun-web.xml file. A role can be mapped to either specific principals or to groups (or both). The principal or group names used must be valid principals or groups in the current default realm.
Chapter 3 Assembling and Deploying Applications
This chapter describes Sun Java System Application Server modules and how these modules are assembled separately or together in an application. This chapter also describes classloaders and tools for assembly and deployment.
The Application Server modules and applications include J2EE standard features and Application Server specific features. Only Application Server specific features are described in detail in this chapter.
The following topics are presented in this chapter:
Overview of Assembly and Deployment
Application assembly (also known as packaging) is the process of combining discrete components of an application into a single unit that can be deployed to a J2EE-compliant application server. A package can be classified either as a module or as a full-fledged application. This section covers the following topics:
Modules
A J2EE module is a collection of one or more J2EE components that execute in the same container type (for example, web or EJB) with deployment descriptors of that type. One descriptor is J2EE standard, the other is Application Server specific. Types of J2EE modules are as follows:
-
Web Application Archive (WAR): A web application is a collection of servlets, HTML pages, classes, and other resources that can be bundled and deployed to several J2EE application servers. A WAR file can consist of the following items: servlets, JSP files, JSP tag libraries, utility classes, static pages, client-side applets, beans, bean classes, and deployment descriptors (web.xml and optionally sun-web.xml).
-
EJB JAR File: The EJB JAR file is the standard format for assembling enterprise beans. This file contains the bean classes (home, remote, local, and implementation), all of the utility classes, and the deployment descriptors (ejb-jar.xml and sun-ejb-jar.xml). If the EJB component is an entity bean with container managed persistence, a .dbschema file and a CMP mapping descriptor, sun-cmp-mapping.xml, must be included as well.
-
Application Client Container JAR File: An ACC client is an Application Server specific type of J2EE client. An ACC client supports the standard J2EE Application Client specifications, and in addition, supports direct access to the Application Server. Its deployment descriptors are application-client.xml and sun-application-client.xml.
-
Resource RAR File: RAR files apply to J2EE CA connectors. A connector extends the EJB container to allow access to external systems much like a device driver provides access to a peripheral device from a process hosted by an operating system. It is a portable way of allowing EJB components to access a foreign enterprise system. Each Application Server connector has a J2EE XML file, ra.xml.
Package definitions must be used in the source code of all modules so the class loader can properly locate the classes after the modules have been deployed.
Because the information in a deployment descriptor is declarative, it can be changed without requiring modifications to source code. At run time, the J2EE server reads this information and acts accordingly.
The Application Server also supports lifecycle modules. See Chapter 10, Developing Lifecycle Listeners for more information.
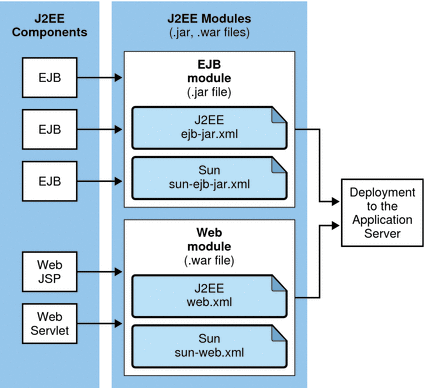
EJB JAR and Web modules can also be deployed separately, outside of any application, as in the following figure. EJB components are assembled in a JAR file with ejb-jar.xml and sun-ejb-jar.xml deployment descriptors. Web components are assembled in a WAR file with web.xml and sun-web.xml deployment descriptors. Both module types are deployed to the Application Server.
Figure 3–1 Module assembly and deployment
Applications
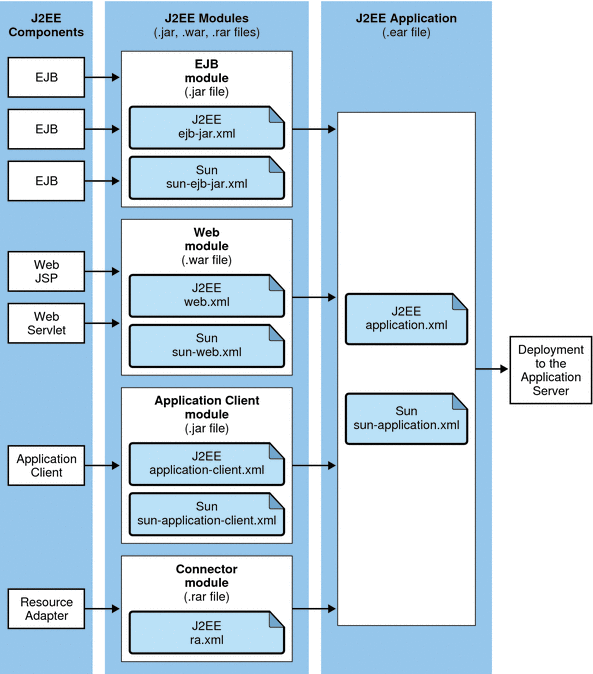
A J2EE application is a logical collection of one or more J2EE modules tied together by application deployment descriptors. Components can be assembled at either the module or the application level. Components can also be deployed at either the module or the application level.
The following diagram illustrates how components are assembled into modules and then assembled into an Application Server application and deployed. EJB components are assembled in a JAR file with ejb-jar.xml and sun-ejb-jar.xml deployment descriptors. Web components are assembled in a WAR file with web.xml and sun-web.xml deployment descriptors. An application client is assembled in a JAR file with application-client.xml and sun-application-client.xml deployment descriptors. A resource adapter is assembled in a RAR file with a ra.xml deployment descriptor. All modules are assembled in an EAR file and deployed to the Application Server.
Figure 3–2 Application assembly and deployment
Each module has an Application Server deployment descriptor and a J2EE deployment descriptor. The Application Server uses the deployment descriptors to deploy the application components and to register the resources with the Application Server.
An application consists of one or more modules, an optional Application Server deployment descriptor, and a required J2EE application deployment descriptor. All items are assembled, using the Java ARchive (.jar) file format, into one file with an extension of .ear.
J2EE Standard Descriptors
The J2EE platform provides assembly and deployment facilities. These facilities use WAR, JAR, and EAR files as standard packages for components and applications, and XML-based deployment descriptors for customizing parameters.
J2EE standard deployment descriptors are described in the J2EE specification, v1.4. You can find the specification at http://java.sun.com/products/.
To check the correctness of these deployment descriptors prior to deployment, see The Deployment Descriptor Verifier.
The following table shows where to find more information about J2EE standard deployment descriptors.
Table 3–1 J2EE Standard Descriptors|
Deployment Descriptor |
Where to Find More Information |
|---|---|
|
Java 2 Platform Enterprise Edition Specification, v1.4, Chapter 8, “Application Assembly and Deployment - J2EE:application XML DTD” |
|
|
Java Servlet Specification, v2.4 Chapter 13, “Deployment Descriptor,” and JavaServer Pages Specification, v2.0, Chapter 7, “JSP Pages as XML Documents,” and Chapter 5, “Tag Extensions” |
|
|
Enterprise JavaBeans Specification, v2.1, Chapter 16, “Deployment Descriptor” |
|
|
Java 2 Platform Enterprise Edition Specification, v1.4, Chapter 9, “Application Clients - J2EE:application-client XML DTD” |
|
|
Java 2 Enterprise Edition, J2EE Connector Architecture Specification, v1.0, Chapter 10, “Packaging and Deployment.” |
Sun Java System Application Server Descriptors
The Application Server uses additional deployment descriptors for configuring features specific to the Application Server. The sun-application.xml, sun-web.xml, and sun-cmp-mappings.xml files are optional; all the others are required.
To check the correctness of these deployment descriptors prior to deployment, see The Deployment Descriptor Verifier.
The following table lists the Application Server deployment descriptors and their DTD files. For complete descriptions of these files, see Appendix A, Deployment Descriptor Files.
Table 3–2 Sun Java System Application Server Descriptors|
Deployment Descriptor |
DTD File |
Description |
|---|---|---|
|
Configures an entire J2EE application (EAR file). |
||
|
Configures a web application (WAR file). |
||
|
Configures an enterprise bean (EJB JAR file). |
||
|
Configures container-managed persistence for an enterprise bean. |
||
|
Configures an Application Client Container (ACC) client (JAR file). |
||
|
Configures the Application Client Container. |
Naming Standards
Names of applications and individually deployed EJB JAR, WAR, and connector RAR modules must be unique within an Application Server domain. Modules of the same type within an application must have unique names. In addition, for entity beans that use CMP,.dbschema file names must be unique within an application.
If you do not explicitly specify a name, the default name is the first portion of the file name (without the .war or .jar extension). Modules of different types can have the same name within an application, because the directories holding the individual modules are named with _jar, _war and _rar suffixes. This is the case when you use the Administration Console, the asadmin command, or the deploytool to deploy an application or module. See Tools for Deployment.
Make sure your package and file names do not contain spaces or characters that are illegal for your operating system.
If you are writing your own JSR 88 client to deploy applications to the Application Server using the following API, the name of the application is taken from the display-name entry in the J2EE standard deployment descriptor, because there is no file name in this case. If the display-name entry is not present, the Application Server creates a temporary file name and uses that name to deploy the application.
javax.enterprise.deploy.spi.DeploymentManager.distribute(Target[], InputStream, InputStream)
Neither the Administration Console, the asadmin command, nor the deploytool uses this API.
For more information about JSR 88, see the JSR 88 page at http://jcp.org/en/jsr/detail?id=88.
Directory Structure
When you deploy an application, the application is expanded to an open directory structure, and the directories holding the individual modules are named with _jar, _war and _rar suffixes. If you use the asadmin deploydir command to deploy a directory instead of an EAR file, your directory structure must follow this same convention.
Module and application directory structures follow the structure outlined in the J2EE specification. Here is an example directory structure of a simple application containing a web module, an EJB module, and a client module.
+ converter_1/
|--- converterClient.jar
|--+ META-INF/
| |--- MANIFEST.MF
| |--- application.xml
| |--- sun-application.xml
|--+ war-ic_war/
| |--- index.jsp
| |--+ META-INF/
| | |--- MANIFEST.MF
| |--+ WEB-INF/
| |--- web.xml
| |--- sun-web.xml
|--+ ejb-jar-ic_jar/
| |--- Converter.class
| |--- ConverterBean.class
| |--- ConverterHome.class
| |--+ META-INF/
| |--- MANIFEST.MF
| |--- ejb-jar.xml
| |--- sun-ejb-jar.xml
|--+ app-client-ic_jar/
|--- ConverterClient.class
|--+ META-INF/
|--- MANIFEST.MF
|--- application-client.xml
|--- sun-application-client.xml
|
Here is an example directory structure of an individually deployed connector module.
+ MyConnector/
|--- readme.html
|--- ra.jar
|--- client.jar
|--- win.dll
|--- solaris.so
|--+ META-INF/
|--- MANIFEST.MF
|--- ra.xml
|
Runtime Environments
Whether you deploy an individual module or an application, deployment affects both the file system and the server configuration.
Module Runtime Environment
The following figure illustrates the environment for individually deployed module-based deployment.
Figure 3–3 Module runtime environment
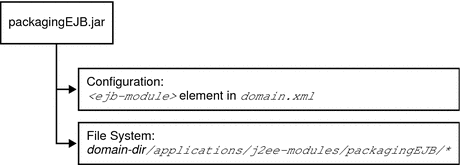
For file system entries, modules are extracted as follows:
domain-dir/applications/j2ee-modules/module-name domain-dir/generated/ejb/j2ee-modules/module-name domain-dir/generated/jsp/j2ee-modules/module-name
The applications directory contains the directory structures described in Directory Structure. The generated/ejb directory contains the stubs and ties that an ACC client needs to access the module; the generated/jsp directory contains compiled JSP files.
Lifecycle modules (see Chapter 10, Developing Lifecycle Listeners) are extracted as follows:
domain-dir/applications/lifecycle-modules/module-name
Configuration entries are added in the domain.xml file as follows:
<server>
<applications>
<type-module>
...module configuration...
</type-module>
</applications>
</server>
The type of the module in domain.xml can be lifecycle, ejb, web, or connector. For details about domain.xml, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Reference.
Application Runtime Environment
The following figure illustrates the environment for application-based deployment.
Figure 3–4 Application runtime environment

For file system entries, applications are extracted as follows:
domain-dir/applications/j2ee-apps/app-name domain-dir/generated/ejb/j2ee-apps/app-name domain-dir/generated/jsp/j2ee-apps/app-name
The applications directory contains the directory structures described in Directory Structure. The generated/ejb directory contains the stubs and ties that an ACC client needs to access the module; the generated/jsp directory contains compiled JSP files.
Configuration entries are added in the domain.xml file as follows:
<server>
<applications>
<j2ee-application>
...application configuration...
</j2ee-application>
</applications>
</server>
For details about domain.xml, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Reference.
Classloaders
Understanding Application Server classloaders can help you determine where and how you can position supporting JAR and resource files for your modules and applications.
In a Java Virtual Machine (JVM), the classloaders dynamically load a specific Java class file needed for resolving a dependency. For example, when an instance of java.util.Enumeration needs to be created, one of the classloaders loads the relevant class into the environment. This section includes the following topics:
The Classloader Hierarchy
Classloaders in the Application Server runtime follow a hierarchy that is illustrated in the following figure and fully described in Table 3–3.
Figure 3–5 Classloader runtime hierarchy
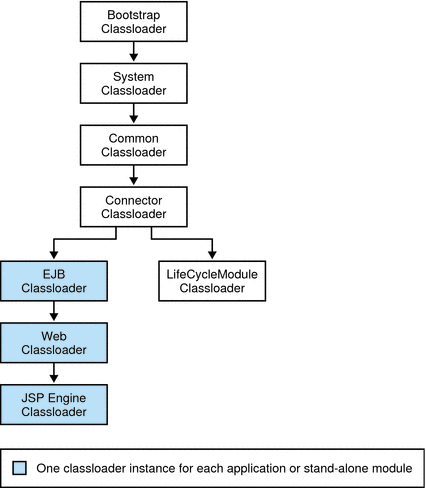 Table 3–3 Sun Java System Application Server Classloaders
Table 3–3 Sun Java System Application Server Classloaders
Note that this is not a Java inheritance hierarchy, but a delegation hierarchy. In the delegation design, a class loader delegates classloading to its parent before attempting to load a class itself. A class loader parent can be either the System Classloader or another custom class loader. If the parent class loader can’t load a class, the findClass() method is called on the class loader subclass. In effect, a class loader is responsible for loading only the classes not available to the parent.
The Servlet specification recommends that the Web Classloader look in the local class loader before delegating to its parent. You can make the Web Classloader follow the delegation model in the Servlet specification by setting delegate="false" in the class-loader element of the sun-web.xml file. It’s safe to do this only for a web module that does not interact with any other modules.
The default value is delegate="true", which causes the Web Classloader to delegate in the same manner as the other classloaders. You must use delegate="true" for a web application that accesses EJB components or that acts as a web service client or endpoint. For details about sun-web.xml, see The sun-web.xml File.
Classloader Universes
Access to components within applications and modules installed on the server occurs within the context of isolated class loader universes, each of which has its own EJB, Web, and JSP Engine classloaders.
-
Application Universe: Each J2EE application has its own class loader universe, which loads the classes in all the modules in the application.
-
Individually Deployed Module Universe: Each individually deployed EJB JAR, web WAR, or lifecycle module has its own class loader universe, which loads the classes in the module.
Note –
A resource such as a file that is accessed by a servlet, JSP, or EJB component must be in a directory pointed to by the class loader’s classpath. For example, the web class loader’s classpath includes these directories:
module-name/WEB-INF/classes module-name/WEB-INF/lib
If a servlet accesses a resource, it must be in one of these directories or it is not loaded.
Note –
In iPlanet Application Server 6.x, individually deployed modules shared the same class loader. In subsequent Application Server versions, each individually deployed module has its own class loader universe.
Circumventing Classloader Isolation
Since each application or individually deployed module class loader universe is isolated, an application or module cannot load classes from another application or module. This prevents two similarly named classes in different applications from interfering with each other.
To circumvent this limitation for libraries, utility classes, or individually deployed modules accessed by more than one application, you can include the relevant path to the required classes in one of these ways:
Using the System class loader or Common class loader requires a server restart and makes a library accessible to any other application or module across the domain.
Using the System Classloader
To use the System Classloader, do one of the following, then restart the server:
-
Use the Administration Console. Select the JVM Settings component under the relevant configuration, select the Path Settings tab, and edit the Classpath Suffix field. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
-
Edit the classpath-suffix attribute of the java-config element in the domain.xml file. For details about domain.xml, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Reference.
Using the System Classloader makes an application or module accessible to any other application or module across the domain.
Add the classes to the classpath-suffix attribute of the DAS in addition to the classpath-suffix attribute on the server instances that use the classes. The default name for the DAS configuration is server-config.
Using the Common Classloader
To use the Common Classloader, copy the JAR and ZIP files into the domain-dir/lib directory or copy the .class files into the domain-dir/lib/classes directory, then restart the server.
Using the Common Classloader makes an application or module accessible to any other application or module across the domain.
For example, this is the recommended way of adding JDBC drivers to the Application Server. For a list of the JDBC drivers currently supported by the Application Server, see the Sun Java System Application Server Enterprise Edition 8.2 Release Notes. For configurations of supported and other drivers, see Configurations for Specific JDBC Drivers.
Sharing Libraries Across a Cluster
To share libraries across a specific cluster instead of the entire domain, copy the JAR files to the domain-dir/config/cluster-config-name/lib directory. Then add the path to the JAR files to the System class loader as explained in Using the System Classloader.
Using the Java Optional Package Mechanism
To use the Java optional package mechanism, copy the JAR and ZIP files into the domain-dir/lib/ext directory, then restart the server.
Using the Java optional package mechanism makes an application or module accessible to any other application or module across the domain.
Packaging the Client JAR for One Application in Another Application
By packaging the client JAR for one application in a second application, you allow an EJB or web component in the second application to call an EJB component in the first (dependent) application, without making either of them accessible to any other application or module.
As an alternative for a production environment, you can have the Common Classloader load client JAR of the dependent application as described in Using the Common Classloader restart the server to make the dependent application accessible, and it is accessible across the domain.
 To package the client JAR for one application in another
application
To package the client JAR for one application in another
application
-
Deploy the dependent application.
-
Add the dependent application’s client JAR file to the calling application.
-
For a calling EJB component, add the client JAR file at the same level as the EJB component. Then add a Class-Path entry to the MANIFEST.MF file of the calling EJB component. The Class-Path entry has this syntax:
Class-Path: filepath1.jar filepath2.jar ...
Each filepath is relative to the directory or JAR file containing the MANIFEST.MF file. For details, see the J2EE specification, section 8.1.1.2, “Dependencies.”
-
For a calling web component, add the client JAR file under the WEB-INF/lib directory.
-
-
If you need to package the client JAR with both the EJB and web components, set delegate="true" in the class-loader element of the sun-web.xml file.
This changes the Web Classloader so it follows the standard class loader delegation model and delegates to its parent before attempting to load a class itself.
For most applications, packaging the client JAR file with the calling EJB component is sufficient. You do not need to package the client JAR file with both the EJB and web components unless the web component is directly calling the EJB component in the dependent application.
-
Deploy the calling application.
The calling EJB or web component must specify in its sun-ejb-jar.xml or sun-web.xml file the JNDI name of the EJB component in the dependent application. Using an ejb-link mapping does not work when the EJB component being called resides in another application.
Assembling Modules and Applications
Assembling (or packaging) modules and applications in Application Server conforms to all of the customary J2EE-defined specifications. The only difference is that when you assemble in Application Server, you include Application Server specific deployment descriptors that enhance the functionality of the Application Server.
For example, when you assemble an EJB JAR module, you must create two deployment descriptor files with these names: ejb-jar.xml and sun-ejb-jar.xml (both required). If the EJB component is an entity bean with container-managed persistence, you can also create a .dbschema file and a sun-cmp-mapping.xml file, but these are not required. For more information about sun-ejb-jar.xml and sun-cmp-mapping.xml, see Appendix A, Deployment Descriptor Files.
Note –
According to the J2EE specification, section 8.1.1.2, “Dependencies,” you cannot package utility classes within an individually deployed EJB module. Instead, package the EJB module and utility JAR within an application using the JAR Extension Mechanism Architecture. For other alternatives, see Circumventing Classloader Isolation.
The Application Server provides these tools for assembling and verifying a module or an application:
deploytool
You can use the deploytool, provided with the Application Server, to assemble J2EE applications and modules, configure deployment parameters, perform simple static checks, and deploy the final result. For more information about using the deploytool, see the J2EE 1.4 Tutorial at http://java.sun.com/j2ee/1.4/docs/tutorial/doc/index.html.
Apache Ant
Ant can help you assemble and deploy modules and applications. For details, see asant Assembly and Deployment Tool.
NetBeans IDE
You can use the NetBeans IDE to assemble J2EE applications and modules. For more information about using the NetBeans IDE, see http://www.netbeans.org.
The Deployment Descriptor Verifier
The verifier tool validates both J2EE and Application Server specific deployment descriptors against their corresponding DTD files and gives errors and warnings if a module or application is not J2EE and Application Server compliant. You can verify deployment descriptors in EAR, WAR, RAR, and JAR files.
The verifier tool is not simply an XML syntax verifier. Rules and interdependencies between various elements in the deployment descriptors are verified. Where needed, user application classes are introspected to apply validation rules.
The verifier is integrated into Application Server deployment, the deploytool, and the sun-appserv-deploy Ant task. You can also run it as a stand-alone utility from the command line. The verifier is located in the install-dir/bin directory.
When you run the verifier during Application Server deployment, the output of the verifier is written to the tempdir/verifier-results/ directory, where tempdir is the temporary directory defined in the operating system. Deployment fails if any failures are reported during the verification process. The verifier also logs information about verification progress to the standard output.
For details on all the assertions tested by the verifier, see the assertions documentation provided at http://java.sun.com/j2ee/avk/index.html.
Tip –
Using the verifier tool can help you avoid runtime errors that are difficult to debug.
This section covers the following topics:
Command Line Syntax
The verifier tool’s syntax is as follows:
verifier [options] file
The file can be an EAR, WAR, RAR, or JAR file.
The following table shows the options for the verifier tool.
Table 3–4 Verifier Options
For example, the following command runs the verifier in verbose mode and writes all the results of static verification of the ejb.jar file to the output directory ResultsDir:
verifier -v -r a -d ResultsDir ejb.jar
The results files are ejb.jar_verifier.timestamp.txt and ejb.jar_verifier.timestamp.xml. The format of the timestamp is yyyyMMddhhmmss.
If the verifier runs successfully, a result code of 0 is returned. This does not mean that no verification errors occurred. A nonzero error code is returned if the verifier fails to run.
Ant Integration
You can integrate the verifier into an Ant build file as a target and use the Ant call feature to call the target each time an application or module is assembled. This is because the main method in com.sun.enterprise.tools.verifier.Verifier is callable from user Ant scripts. The main method accepts the arguments described in Table 3–4.
Example code for an Ant verify target is as follows:
<target name="verify">
<echo message="Verification Process for ${testfile}"/>
<java classname="com.sun.enterprise.tools.verifier.Verifier"
fork="yes">
<sysproperty key="com.sun.enterprise.home"
value="${appserv.home}"/>
<sysproperty key="verifier.xsl"
value="${appserv.home}/verifier/config" />
<!-- uncomment the following for verbose output -->
<!--<arg value="-v"/>-->
<arg value="${assemble}/${ejbjar}" />
<classpath path="${appserv.cpath}:${java.class.path}"/>
</java>
</target>
Sample Results Files
Here is a sample results XML file:
<static-verification> <ejb> <failed> <test> <test-name> tests.ejb.session.TransactionTypeNullForContainerTX </test-name> <test-assertion> Session bean with bean managed transaction demarcation test </test-assertion> <test-description> For [ TheGreeter ] Error: Session Beans [ TheGreeter ] with [ Bean ] managed transaction demarcation should not have container transactions defined. </test-description> </test> </failed> </ejb> ... </static-verification>
Here is a sample results TXT file:
--------------------------- STATIC VERIFICATION RESULTS --------------------------- ---------------------------------- NUMBER OF FAILURES/WARNINGS/ERRORS ---------------------------------- # of Failures : 3 # of Warnings : 6 # of Errors : 0 ----------------------------- RESULTS FOR EJB-RELATED TESTS ----------------------------- -------------- FAILED TESTS : -------------- Test Name : tests.ejb.session.TransactionTypeNullForContainerTX Test Assertion : Session bean with bean managed transaction demarcation test Test Description : For [ TheGreeter ] Error: Session Beans [ TheGreeter ] with [ Bean ] managed transaction demarcation should not have container transactions defined. ... --------------- PASSED TESTS : --------------- Test Name : tests.ejb.session.ejbcreatemethod.EjbCreateMethodStatic Test Assertion : Each session Bean must have at least one non-static ejbCreate method test Test Description : For [ TheGreeter ] For EJB Class [ samples.helloworld.ejb.GreeterEJB ] method [ ejbCreate ] [ samples.helloworld.ejb.GreeterEJB ] properly declares non-static ejbCreate(...) method. ... ----------- WARNINGS : ----------- Test Name : tests.ejb.businessmethod.BusinessMethodException Test Assertion : Enterprise bean business method throws RemoteException test Test Description : Test Name : tests.ejb.ias.beanpool.IASEjbBeanPool Test Assertion : Test Description : WARNING [IAS-EJB ejb] : bean-pool should be defined for Stateless Session and Message Driven Beans ... --------------------- NOTAPPLICABLE TESTS : --------------------- Test Name : tests.ejb.entity.pkmultiplefield.PrimaryKeyClassFieldsCmp Test Assertion : Ejb primary key class properly declares all class fields within subset of the names of the container-managed fields test. Test Description : For [ TheGreeter ] class com.sun.enterprise.tools. verifier.tests.ejb.entity.pkmultiplefield.PrimaryKeyClassFieldsCmp expected Entity bean, but called with Session. Test Name : tests.ejb.entity.ejbcreatemethod.EjbCreateMethodReturn Test Assertion : Each entity Bean can have zero or more ejbCreate methods which return primary key type test Test Description : For [ TheGreeter ] class com.sun.enterprise.tools. verifier.tests.ejb.entity.ejbcreatemethod.EjbCreateMethodReturn expected Entity bean, but called with Session bean. ... ----------------------------------- RESULTS FOR OTHER XML-RELATED TESTS ----------------------------------- --------------- PASSED TESTS : --------------- Test Name : tests.dd.ParseDD Test Assertion : Test parses the deployment descriptor using a SAX parser to avoid the dependency on the DOL Test Description : PASSED [EJB] : [ remote ] and [ home ] tags present. PASSED [EJB]: session-type is Stateless. PASSED [EJB]: trans-attribute is NotSupported. PASSED [EJB]: transaction-type is Bean. ...
Deploying Modules and Applications
This section describes the different ways to deploy J2EE applications and modules to the Application Server. It covers the following topics:
Deployment Errors
If an error occurs during deployment, the application or module is not deployed. If a module within an application contains an error, the entire application is not deployed. This prevents a partial deployment that could leave the server in an inconsistent state.
The Deployment Life Cycle
After an application is initially deployed, it can be modified and reloaded, redeployed, disabled, re-enabled, and finally undeployed (removed from the server). This section covers the following topics related to the deployment life cycle:
Note –
You can overwrite a previously deployed application by using the --force option of asadmin deploy or by checking the appropriate box in the Administration Console during deployment. However, you must remove a preconfigured resource before you can update it.
Dynamic Deployment
You can deploy, redeploy, and undeploy an application or module without restarting the server instances. This is called dynamic deployment. Although primarily for developers, dynamic deployment can be used in operational environments to bring new applications and modules online without requiring a server restart.
Whenever a redeployment is done, the sessions at that transit time become invalid. The client must restart the session.
Disabling a Deployed Application or Module
You can disable a deployed application or module without removing it from the server. Disabling an application makes it inaccessible to clients.
To disable an application or module using the asadmin disable command, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual.
 To disable an application or module in the Administration
Console
To disable an application or module in the Administration
Console
-
Open the Applications component.
-
Go to the page for the type of application or module.
For example, for a web application, go to the Web Applications page.
-
Click on the name of the application or module you wish to disable.
-
Uncheck the Status Enabled box.
See Also
For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
Dynamic Reloading
If dynamic reloading is enabled (it is by default), you do not have to redeploy an application or module when you change its code or deployment descriptors. All you have to do is copy the changed JSP or class files into the deployment directory for the application or module. The server checks for changes periodically and redeploys the application, automatically and dynamically, with the changes. This feature is available only on the default server instance.
This is useful in a development environment, because it allows code changes to be tested quickly. In a production environment, however, dynamic reloading might degrade performance. In addition, whenever a reload is done, the sessions at that transit time become invalid. The client must restart the session.
 To enable dynamic reloading in the Administration
Console
To enable dynamic reloading in the Administration
Console
-
Select the Stand-Alone Instances component.
-
Select the instance named server in the table.
This is the Admin Server.
-
Select the Advanced tab.
-
Check the Reload Enabled box to enable dynamic reloading.
-
Enter a number of seconds in the Reload Poll Interval field.
This sets the interval at which applications and modules are checked for code changes and dynamically reloaded. The default is 2.
See Also
For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
 To reload code or deployment descriptor changes
To reload code or deployment descriptor changes
-
Create an empty file named .reload at the root of the deployed application or module.
For an application:
domain-dir/applications/j2ee-apps/app-name/.reload
For an individually deployed module:
domain-dir/applications/j2ee-modules/module-name/.reload
-
Explicitly update the .reload file’s timestamp (touch .reload in UNIX) each time you make changes.
Automatic Deployment
Automatic deployment, also called autodeployment, involves copying an application or module file (JAR, WAR, RAR, or EAR) into a special directory, where it is automatically deployed by the Application Server. To undeploy an automatically deployed application or module, simply remove its file from the special autodeployment directory. This is useful in a development environment, because it allows new code to be tested quickly. This feature is available only on the default server instance.
Autodeployment is enabled by default.
 To enable and configure or to disable autodeployment
To enable and configure or to disable autodeployment
-
Select the Stand-Alone Instances component.
-
Select the instance named server in the table.
This is the Admin Server.
-
Select the Advanced tab.
-
Check the Auto Deploy Enabled box to enable autodeployment, or uncheck this box to disable autodeployment.
-
Enter a number of seconds in the Auto Deploy Poll Interval field.
This sets the interval at which applications and modules are checked for code changes and dynamically reloaded. The default is 2.
-
You can change the Auto Deploy Directory if you like.
You can enter an absolute or relative path. A relative path is relative to domain-dir. The default is domain-dir/autodeploy.
-
You can check the Verifier Enabled box to verify your deployment descriptor files. This is optional.
For details about the verifier, see The Deployment Descriptor Verifier.
-
Check the Precompile Enabled box to precompile any JSP files.
See Also
For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
Tools for Deployment
This section discusses the various tools that can be used to deploy modules and applications. The deployment tools include:
Apache Ant
Ant can help you assemble and deploy modules and applications. For details, see asant Assembly and Deployment Tool.
The deploytool
You can use the deploytool, provided with Application Server, to assemble J2EE applications and modules, configure deployment parameters, perform simple static checks, and deploy the final result. For more information about using the deploytool, see the J2EE 1.4 Tutorial at http://java.sun.com/j2ee/1.4/docs/tutorial/doc/index.html.
JSR 88
You can write your own JSR 88 client to deploy applications to the Application Server. For more information, see the JSR 88 page at http://jcp.org/en/jsr/detail?id=88.
See Naming Standards for application and module naming considerations.
The asadmin Command
You can use the asadmin deploy or asadmin deploydir command to deploy or undeploy applications and individually deployed modules on local servers. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual. The asadmin deploydir command is available only on the default server instance.
To deploy a lifecycle module, see Deploying a Lifecycle Module.
Note –
On Windows, if you are deploying a directory on a mapped drive, you must be running the Application Server as the same user to which the mapped drive is assigned, or the Application Server won’t see the directory.
The Administration Console
You can use the Administration Console to deploy modules and applications to both local and remote Application Server sites.
 To use the Administration Console for deployment
To use the Administration Console for deployment
-
Open the Applications component.
-
Go to the page for the type of application or module.
For example, for a web application, go to the Web Applications page.
-
Click on the Deploy button.
You can also undeploy, enable, or disable an application or module from this page.
See Also
For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
To deploy a lifecycle module, see Deploying a Lifecycle Module.
Deployment by Module or Application
You can deploy applications or individual modules that are independent of applications. The runtime and file system implications of application-based or individual module-based deployment are described in Runtime Environments.
Individual module-based deployment is preferable when components need to be accessed by:
-
Other modules
-
J2EE Applications
-
ACC clients (Module-based deployment allows shared access to a bean from an ACC client, a servlet, or an EJB component.)
Modules can be combined into an EAR file and then deployed as a single module. This is similar to deploying the modules of the EAR independently.
Deploying a WAR Module
You deploy a WAR module as described in Tools for Deployment.
You can precompile JSP files during deployment by checking the appropriate box in the Administration Console or by using the --precompilejsp option of the asadmin deploy or asadmin deploydir command. The sun-appserv-deploy and sun-appserv-jspc Ant tasks also allow you to precompile JSP files.
You can keep the generated source for JSP files by adding the -keepgenerated flag to the jsp-config element in sun-web.xml. If you include this property when you deploy the WAR module, the generated source is kept in domain-dir/generated/jsp/j2ee-apps/app-name/module-name if it is in an application or domain-dir/generated/jsp/j2ee-modules/module-name if it is in an individually deployed web module.
For more information about JSP precompilation, see Options for Compiling JSP Files jsp-config.
HTTP sessions in WAR modules can be saved in a persistent store in case a server instance fails. For more information, see Distributed Sessions and Persistence and the Sun Java System Application Server Enterprise Edition 8.2 High Availability Administration Guide.
Note –
After a web application is undeployed, its HttpSession information is not immediately removed if sessions are persistent. HttpSession information is removed in the subsequent cycle, when timed out sessions are removed. Therefore, you should disable a web application before undeploying it if sessions are persistent.
If you are setting up load balancing, web module context roots must be unique within a cluster. See the Sun Java System Application Server Enterprise Edition 8.2 High Availability Administration Guide for more information about load balancing.
Deploying an EJB JAR Module
You deploy an EJB JAR module as described in Tools for Deployment.
You can keep the generated source for stubs and ties by adding the -keepgenerated flag to the rmic-options attribute of the java-config element in domain.xml. If you include this flag when you deploy the EJB JAR module, the generated source is kept in domain-dir/generated/ejb/j2ee-apps/app-name/module-name if it is in an application or domain-dir/generated/ejb/j2ee-modules/module-name if it is in an individually deployed EJB JAR module. For more information about the -keepgenerated flag, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Reference.
Generation of stubs and ties is performed asynchronously, so unless you request their generation during deployment (for example, using the --retrieve option of the asadmin deploy command), stubs and ties are not guaranteed to be available immediately after deployment. You can use the asadmin get-client-stubs command to retrieve the stubs and ties whether or not you requested their generation during deployment. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual.
Deploying a Lifecycle Module
For general information about lifecycle modules, see Chapter 10, Developing Lifecycle Listeners.
You can deploy a lifecycle module using the following tools:
-
In the Administration Console, open the Applications component and go to the Lifecycle Modules page. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
-
Use the asadmin create-lifecycle-module command. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual.
Note –
If the is-failure-fatal setting is set to true (the default is false), lifecycle module failure prevents server initialization or startup, but not shutdown or termination.
Deploying an Application Client
Deployment is only necessary for application clients that communicate with EJB components.
 To deploy an application client
To deploy an application client
-
Assemble the necessary client files.
-
Assemble the EJB components to be accessed by the client.
-
Package the client and EJB components together in an application.
-
Deploy the application as described in Tools for Deployment.
-
Retrieve the client JAR file.
The client JAR file contains the ties and necessary classes for the ACC client.
You can use the --retrieve option to get the client JAR file.
You can also use the asadmin get-client-stubs command to retrieve the stubs and ties whether or not you requested their generation during deployment. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual.
-
Copy the client JAR file to the client machine, and set the APPCPATH environment variable on the client to point to this JAR.
Next Steps
To execute the client on the Application Server machine to test it, use the appclient script in the install-dir/bin directory. If you are using the default server instance, the only required option is -client. For example:
appclient -client converterClient.jar
The -xml parameter, which specifies the location of the sun-acc.xml file, is also required if you are not using the default instance.
See Also
For more detailed information about the appclient script, see Chapter 8, Developing Java Clients.
 To prepare another machine for executing an application
client
To prepare another machine for executing an application
client
-
You can use the package-appclient script in the install-dir/bin directory to create the ACC package JAR file. This is optional.
This JAR file is created in the install-dir /lib/appclient directory.
-
Copy the ACC package JAR file to the client machine and unjar it.
-
Configure the sun-acc.xml file.
This file is located in the appclient/appserv/lib/appclient directory by default if you used the package-appclient script.
-
Configure the asenv.conf (asenv.bat on Windows) file.
This file is located in appclient/appserv/bin by default if you used the package-appclient script.
-
Copy the client JAR file to the client machine.
You are now ready to execute the client.
See Also
For more detailed information about the package-appclient script, see Chapter 8, Developing Java Clients.
Deploying a J2EE CA Resource Adapter
You deploy a connector module as described in Tools for Deployment. After deploying the module, you must configure it as described in Chapter 9, Developing Connectors.
Access to Shared Frameworks
When J2EE applications and modules use shared framework classes (such as utility classes and libraries) the classes can be put in the path for the System Classloader or the Common Classloader rather than in an application or module. If you assemble a large, shared library into every module that uses it, the result is a huge file that takes too long to register with the server. In addition, several versions of the same class could exist in different classloaders, which is a waste of resources. For more information, see Circumventing Classloader Isolation.
asant Assembly and Deployment Tool
Apache Ant 1.6.5 is provided with Application Server and can be launched from the bin directory using the command asant. The Application Server also provides server-specific tasks for deployment, which are described in this section.
Make sure you have done these things before using asant:
-
Include install-dir/bin in the PATH environment variable (/usr/sfw/bin for Sun Java Enterprise System on Solaris). The Ant script provided with the Application Server, asant, is located in this directory. For details on how to use asant, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual and the sample applications documentation in the install-dir/samples/docs/ant.html file.
-
If you are executing platform-specific applications, such as the exec or cvs task, the ANT_HOME environment variable must be set to the Ant installation directory.
-
The ANT_HOME environment variable for Sun Java Enterprise System must include the following:
-
/usr/sfw/bin - the Ant binaries (shell scripts)
-
/usr/sfw/doc/ant - HTML documentation
-
/usr/sfw/lib/ant - Java classes that implement Ant
-
-
The ANT_HOME environment variable for all other platforms is install-dir/lib.
-
-
Set up your password file. The argument for the passworfile option of each Ant task is a file. This file contains the password attribute name and its value, in the following format:
AS_ADMIN_PASSWORD=password
For more information about password files, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual.
This section covers the following asant-related topics:
For more information about Ant, see the Apache Software Foundation web site at http://ant.apache.org/.
For information about standard Ant tasks, see the Ant documentation at http://ant.apache.org/manual/.
asant Tasks for Sun Java System Application Server
Use the asant tasks provided by the Application Server for assembling, deploying, and undeploying modules and applications, and for configuring the server. The tasks are as follows:
sun-appserv-deploy
Deploys any of the following to a local or remote Application Server instance.
-
Enterprise application (EAR file)
-
Web application (WAR file)
-
Enterprise Java Bean (EJB-JAR file)
-
Enterprise connector (RAR file)
-
Application client
Subelements
The following table describes subelements for the sun-appserv-deploy task. These are objects upon which this task acts.
Table 3–5 sun-appserv-deploy Subelements|
Element |
Description |
|---|---|
|
An Application Server instance. |
|
|
A component to be deployed. |
|
|
A set of component files that match specified parameters. |
Attributes
The following table describes attributes for the sun-appserv-deploy task.
Table 3–6 sun-appserv-deploy Attributes|
Attribute |
Default |
Description |
|---|---|---|
|
none |
(optional if a component or fileset subelement is present, otherwise required) The component to deploy. If this attribute refers to a file, it must be a valid archive. If this attribute refers to a directory, it must contain a valid archive in which all components have been exploded. If upload is set to false, this must be an absolute path on the server machine. |
|
|
name |
file name without extension |
(optional) The display name for the component being deployed. |
|
determined by extension |
(optional) Deprecated. |
|
|
true |
(optional) If true, the component is overwritten if it already exists on the server. If false, sun-appserv-deploy fails if the component exists. |
|
|
client stubs not saved |
(optional) The directory where client stubs are saved. This attribute is inherited by nested component elements. |
|
|
false |
(optional) If true, all JSP files found in an enterprise application (.ear) or web application (.war) are precompiled. This attribute is ignored for other component types. This attribute is inherited by nested component elements. |
|
|
false |
(optional) If true, syntax and semantics for all deployment descriptors are automatically verified for correctness. This attribute is inherited by nested component elements. |
|
|
file name without extension |
(optional) The context root for a web module (WAR file). This attribute is ignored if the component is not a WAR file. |
|
|
sun-ejb-jar.xml entry |
(optional) The name of the database vendor for which tables can be created. Allowed values are javadb, db2, mssql, oracle, pointbase, derby (also for CloudScape), and sybase, case-insensitive. If not specified, the value of the database-vendor-name attribute in sun-ejb-jar.xml is used. If no value is specified, a connection is made to the resource specified by the jndi-name subelement of the cmp-resource element in the sun-ejb-jar.xml file, and the database vendor name is read. If the connection cannot be established, or if the value is not recognized, SQL-92 compliance is presumed. For details, see Generation Options. |
|
|
sun-ejb-jar.xml entry |
(optional) If true, causes database tables to be created for beans that need them. If false, does not create tables. If not specified, the value of the create-tables-at-deploy attribute in sun-ejb-jar.xml is used. For details, see Generation Options. |
|
|
sun-ejb-jar.xml entry |
(optional) If true, and if tables were automatically created when this application was last deployed, tables from the earlier deployment are dropped and fresh ones are created. If true, and if tables were not automatically created when this application was last deployed, no attempt is made to drop any tables. If tables with the same names as those that would have been automatically created are found, the deployment proceeds, but a warning indicates that tables could not be created. If false, settings of create-tables-at-deploy or drop-tables-at-undeploy in the sun-ejb-jar.xml file are overridden. For details, see Generation Options. |
|
|
sun-ejb-jar.xml entry |
(optional) If true, specifies that table names are unique within each application server domain. If not specified, the value of the use-unique-table-names property in sun-ejb-jar.xml is used. For details, see Generation Options. |
|
|
true |
(optional) If true, enables the component. |
|
|
none |
(optional) A deployment plan is a JAR file containing Sun-specific descriptors. Use this attribute when deploying an EAR file that lacks Sun-specific descriptors. |
|
|
false |
(optional) If true, enables high availability features, including persistence of HTTP sessions and checkpointing of the stateful session bean state. |
|
|
false |
(optional) If true, generates the static RMI-IIOP stubs and puts them in the client JAR file. |
|
|
true |
(optional) If true, the component is transferred to the server for deployment. If the component is being deployed on the local machine, set upload to false to reduce deployment time. If a directory is specified for deployment, upload must be false. |
|
|
default virtual server only |
(optional) A comma-separated list of virtual servers to be deployment targets. This attribute applies only to application (.ear) or web (.war) components and is ignored for other component types. This attribute is inherited by nested server elements. |
|
|
admin |
(optional) The user name used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
|
password |
none |
(optional) Deprecated, use passwordfile instead. The password used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
passwordfile |
none |
(optional) File containing passwords. The password from this file is retrieved for communication with the application server administration instance. This attribute is inherited by nested server elements. If both password and passwordfile are specified, passwordfile takes precedence. |
|
localhost |
(optional) Target server. When deploying to a remote server, use the fully qualified host name. This attribute is inherited by nested server elements. |
|
|
4849 |
(optional) The administration port on the target server. This attribute is inherited by nested server elements. |
|
|
name of default instance |
(optional) Target application server instance. This attribute is inherited by nested server elements. |
|
|
see description |
(optional) The installation directory for the local Application Server installation, which is used to find the administrative classes. If not specified, the command checks to see if the asinstalldir parameter has been set. Otherwise, administrative classes must be in the system classpath. |
|
|
see description |
(optional) Deprecated. Use asinstalldir instead. |
Examples
Here is a simple application deployment script with many implied attributes:
<sun-appserv-deploy
file="${assemble}/simpleapp.ear"
passwordfile="${passwordfile}" />
Here is an equivalent script showing all the implied attributes:
<sun-appserv-deploy
file="${assemble}/simpleapp.ear"
name="simpleapp"
force="true"
precompilejsp="false"
verify="false"
upload="true"
user="admin"
passwordfile="${passwordfile}"
host="localhost"
port="4849"
target="${default-instance-name}"
asinstalldir="${asinstalldir}" />
This example deploys multiple components to the same Application Server instance running on a remote server:
<sun-appserv-deploy passwordfile="${passwordfile}" host="greg.sun.com"
asinstalldir="/opt/sun" >
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"
contextroot="test"/>
<component file="${assemble}/simplebean.jar"/>
</sun-appserv-deploy>
This example deploys multiple components to two Application Server instances running on remote servers. In this example, both servers are using the same admin password. If this were not the case, each password could be specified in the server element.
<sun-appserv-deploy passwordfile="${passwordfile}" asinstalldir="/opt/sun" >
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"
contextroot="test"/>
<component file="${assemble}/simplebean.jar"/>
</sun-appserv-deploy>
This example deploys the same components as the previous example because the three components match the fileset criteria, but note that it’s not possible to set some component-specific attributes. All component-specific attributes (name and contextroot) use their default values.
<sun-appserv-deploy passwordfile="${passwordfile}" host="greg.sun.com"
asinstalldir="/opt/sun" >
<fileset dir="${assemble}" includes="**/*.?ar" />
</sun-appserv-deploy>
sun-appserv-undeploy
Undeploys any of the following from a local or remote Application Server instance.
-
Enterprise application (EAR file)
-
Web application (WAR file)
-
Enterprise Java Bean (EJB-JAR file)
-
Enterprise connector (RAR file)
-
Application client
Subelements
The following table describes subelements for the sun-appserv-undeploy task. These are objects upon which this task acts.
Table 3–7 sun-appserv-undeploy Subelements|
Element |
Description |
|---|---|
|
An Application Server instance. |
|
|
A component to be deployed. |
|
|
A set of component files that match specified parameters. |
Attributes
The following table describes attributes for the sun-appserv-undeploy task.
Table 3–8 sun-appserv-undeploy Attributes|
Attribute |
Default |
Description |
|---|---|---|
|
name |
file name without extension |
(optional if a component or fileset subelement is present or the file attribute is specified, otherwise required) The display name for the component being undeployed. |
|
none |
(optional) The component to undeploy. If this attribute refers to a file, it must be a valid archive. If this attribute refers to a directory, it must contain a valid archive in which all components have been exploded. |
|
|
determined by extension |
(optional) Deprecated. |
|
|
sun-ejb-jar.xml entry |
(optional) If true, causes database tables that were automatically created when the bean(s) were last deployed to be dropped when the bean(s) are undeployed. If false, does not drop tables. If not specified, the value of the drop-tables-at-undeploy attribute in sun-ejb-jar.xml is used. For details, see Generation Options. |
|
|
false |
(optional) If true, deletes all connection pools and connector resources associated with the resource adapter being undeployed. If false, undeployment fails if any pools or resources are still associated with the resource adapter. This attribute is applicable to connectors (resource adapters) and applications with connector modules. |
|
|
admin |
(optional) The user name used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
|
password |
none |
(optional) Deprecated, use passwordfile instead. The password used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
passwordfile |
none |
(optional) File containing passwords. The password from this file is retrieved for communication with the application server administration instance. This attribute is inherited by nested server elements. If both password and passwordfile are specified, passwordfile takes precedence. |
|
localhost |
(optional) Target server. When deploying to a remote server, use the fully qualified host name. This attribute is inherited by nested server elements. |
|
|
4849 |
(optional) The administration port on the target server. This attribute is inherited by nested server elements. |
|
|
name of default instance |
(optional) Target application server instance. This attribute is inherited by nested server elements. |
|
|
see description |
(optional) The installation directory for the local Application Server installation, which is used to find the administrative classes. If not specified, the command checks to see if the asinstalldir parameter has been set. Otherwise, administrative classes must be in the system classpath. |
|
|
see description |
(optional) Deprecated. Use asinstalldir instead. |
Examples
Here is a simple application undeployment script with many implied attributes:
<sun-appserv-undeploy name="simpleapp" passwordfile="${passwordfile}" />
Here is an equivalent script showing all the implied attributes:
<sun-appserv-undeploy
name="simpleapp"
user="admin"
passwordfile="${passwordfile}"
host="localhost"
port="4849"
target="${default-instance-name}"
asinstalldir="${asinstalldir}" />
This example demonstrates using the archive files (EAR and WAR, in this case) for the undeployment, using the component name (for undeploying the EJB component in this example), and undeploying multiple components.
<sun-appserv-undeploy passwordfile="${passwordfile}">
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-undeploy>
As with the deployment process, components can be undeployed from multiple servers in a single command. This example shows the same three components being removed from two different instances of the Application Server. In this example, the passwords for both instances are the same.
<sun-appserv-undeploy passwordfile="${passwordfile}">
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-undeploy>
sun-appserv-instance
Starts, stops, restarts, creates, or removes one or more application server instances.
Subelements
The following table describes subelements for the sun-appserv-instance task. These are objects upon which this task acts.
Table 3–9 sun-appserv-instance Subelements|
Element |
Description |
|---|---|
|
An Application Server instance. |
Attributes
The following table describes attributes for the sun-appserv-instance task.
Table 3–10 sun-appserv-instance Attributes|
Attribute |
Default |
Description |
|---|---|---|
|
none |
The control command for the target application server. Valid values are start, stop, restart, create, and delete. A restart sends the stop command followed by the start command. The restart command is not supported on Windows. |
|
|
false |
(optional) Deprecated. If action is set to start or restart, specifies whether the server starts in debug mode. This attribute is ignored for other values of action. If true, the instance generates additional debugging output throughout its lifetime. This attribute is inherited by nested server elements. |
|
|
none |
(optional) Deprecated. |
|
|
none |
(required if action is create, otherwise ignored) The name of the node agent on which the instance is being created. |
|
|
none |
(optional, applicable only if action is create) The clustered instance to be created. The server’s configuration is inherited from the named cluster. The config and cluster attributes are mutually exclusive. If both are omitted, a stand-alone server instance is created. |
|
|
none |
(optional, applicable only if action is create) The configuration for the new stand-alone instance. The configuration must exist and must not be default-config (the cluster configuration template) or an already referenced stand-alone configuration (including the administration server configuration server-config). The config and cluster attributes are mutually exclusive. If both are omitted, a stand-alone server instance is created. |
|
|
none |
(optional, applicable only if action is create) Defines system properties for the server instance. These properties override port settings in the server instance’s configuration. The following properties are defined: http-listener-1-port, http-listener-2-port, orb-listener-1-port, SSL-port, SSL_MUTUALAUTH-port, JMX_SYSTEM_CONNECTOR_port. System properties can be changed after instance creation using the system property commands. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Reference Manual. |
|
|
admin |
(optional) The username used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
|
password |
none |
(optional) Deprecated, use passwordfile instead. The password used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
passwordfile |
none |
(optional) File containing passwords. The password from this file is retrieved for communication with the application server administration instance. This attribute is inherited by nested server elements. If both password and passwordfile are specified, passwordfile takes precedence. |
|
localhost |
(optional) Target server. If it is a remote server, use the fully qualified hostname. This attribute is inherited by nested server elements. |
|
|
4849 |
(optional) The administration port on the target server. This attribute is inherited by nested server elements. |
|
|
name of default instance |
(optional) Target application server instance. This attribute is inherited by nested server elements. |
|
|
see description |
(optional) The installation directory for the local Application Server installation, which is used to find the administrative classes. If not specified, the command checks to see if the asinstalldir parameter has been set. Otherwise, administrative classes must be in the system classpath. |
|
|
see description |
(optional) Deprecated. Use asinstalldir instead. |
Examples
This example starts the local Application Server instance:
<sun-appserv-instance action="start" passwordfile="${passwordfile}"
instance="${default-instance-name}"/>
Here is an equivalent script showing all the implied attributes:
<sun-appserv-instance
action="start"
user="admin"
passwordfile="${passwordfile}"
host="localhost"
port="4849"
instance="${default-instance-name}"
asinstalldir="${asinstalldir}" />
Multiple servers can be controlled using a single command. In this example, two servers are restarted, and in this case each server uses a different password:
<sun-appserv-instance action="restart"
instance="${default-instance-name}"/>
<server host="greg.sun.com" passwordfile="${password.greg}"/>
<server host="joe.sun.com" passwordfile="${password.joe}"/>
</sun-appserv-instance>
This example creates a new Application Server instance:
<sun-appserv-instance
action="create" instanceport="8080"
passwordfile="${passwordfile}"
instance="development" />
Here is an equivalent script showing all the implied attributes:
<sun-appserv-instance
action="create"
instanceport="8080"
user="admin"
passwordfile="${passwordfile}"
host="localhost"
port="4849"
instance="development"
asinstalldir="${asinstalldir}" />
Instances can be created on multiple servers using a single command. This example creates a new instance named qa on two different servers. In this case, both servers use the same password.
<sun-appserv-instance
action="create"
instanceport="8080"
instance="qa"
passwordfile="${passwordfile}>
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
</sun-appserv-instance>
These instances can also be removed from their respective servers:
<sun-appserv-instance
action="delete"
instance="qa"
passwordfile="${passwordfile}>
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
</sun-appserv-instance>
Different instance names and instance ports can also be specified using attributes of the server subelement:
<sun-appserv-instance action="create" passwordfile="${passwordfile}>
<server host="greg.sun.com" instanceport="8080" instance="qa"/>
<server host="joe.sun.com" instanceport="9090"
instance="integration-test"/>
</sun-appserv-instance>
sun-appserv-component
Enables or disables the following J2EE component types that have been deployed to the Application Server.
-
Enterprise application (EAR file)
-
Web application (WAR file)
-
Enterprise Java Bean (EJB-JAR file)
-
Enterprise connector (RAR file)
-
Application client
You don’t need to specify the archive to enable or disable a component: only the component name is required. You can use the component archive, however, because it implies the component name.
Subelements
The following table describes subelements for the sun-appserv-component task. These are objects upon which this task acts.
Table 3–11 sun-appserv-component Subelements|
Element |
Description |
|---|---|
|
An Application Server instance. |
|
|
A component to be deployed. |
|
|
A set of component files that match specified parameters. |
Attributes
The following table describes attributes for the sun-appserv-component task.
Table 3–12 sun-appserv-component Attributes|
Attribute |
Default |
Description |
|---|---|---|
|
none |
The control command for the target application server. Valid values are enable and disable. |
|
|
name |
file name without extension |
(optional if a component or fileset subelement is present or the file attribute is specified, otherwise required) The display name for the component being enabled or disabled. |
|
none |
(optional) The component to enable or disable. If this attribute refers to a file, it must be a valid archive. If this attribute refers to a directory, it must contain a valid archive in which all components have been exploded. |
|
|
determined by extension |
(optional) Deprecated. |
|
|
admin |
(optional) The user name used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
|
password |
none |
(optional) Deprecated, use passwordfile instead. The password used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
passwordfile |
none |
(optional) File containing passwords. The password from this file is retrieved for communication with the application server administration instance. This attribute is inherited by nested server elements. If both password and passwordfile are specified, passwordfile takes precedence. |
|
localhost |
(optional) Target server. When enabling or disabling a remote server, use the fully qualified host name. This attribute is inherited by nested server elements. |
|
|
4849 |
(optional) The administration port on the target server. This attribute is inherited by nested server elements. |
|
|
name of default instance |
(optional) Target application server instance. This attribute is inherited by nested server elements. |
|
|
see description |
(optional) The installation directory for the local Application Server installation, which is used to find the administrative classes. If not specified, the command checks to see if the asinstalldir parameter has been set. Otherwise, administrative classes must be in the system classpath. |
|
|
see description |
(optional) Deprecated. Use asinstalldir instead. |
Examples
Here is a simple example of disabling a component:
<sun-appserv-component
action="disable"
name="simpleapp"
passwordfile="${passwordfile}" />
Here is a simple example of enabling a component:
<sun-appserv-component
action="enable"
name="simpleapp"
passwordfile="${passwordfile}" />
Here is an equivalent script showing all the implied attributes:
<sun-appserv-component
action="enable"
name="simpleapp"
user="admin"
passwordfile="${passwordfile}"
host="localhost"
port="4849"
target="${default-instance-name}"
asinstalldir="${asinstalldir}" />
This example demonstrates disabling multiple components using the archive files (EAR and WAR, in this case) and using the component name (for an EJB component in this example).
<sun-appserv-component action="disable" passwordfile="${passwordfile}">
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-component>
Components can be enabled or disabled on multiple servers in a single task. This example shows the same three components being enabled on two different instances of the Application Server. In this example, the passwords for both instances are the same.
<sun-appserv-component action="enable" passwordfile="${passwordfile}">
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-component>
sun-appserv-admin
Enables arbitrary administrative commands and scripts to be executed on the Application Server. This is useful for cases where a specific Ant task hasn’t been developed or a set of related commands are in a single script.
Subelements
The following table describes subelements for the sun-appserv-admin task. These are objects upon which this task acts.
Table 3–13 sun-appserv-admin Subelements|
Element |
Description |
|---|---|
|
An Application Server instance. |
Attributes
The following table describes attributes for the sun-appserv-admin task.
Table 3–14 sun-appserv-admin Attributes|
Attribute |
Default |
Description |
|---|---|---|
|
none |
(exactly one of these is required: command, commandfile, or explicitcommand) The command to execute. If the user, passwordfile, host, port, or target attributes are also specified, they are automatically inserted into the command before execution. If any of these options are specified in the command string, the corresponding attribute values are ignored. |
|
|
none |
(exactly one of these is required: command, commandfile, or explicitcommand) Deprecated. The command script to execute. If commandfile is used, the values of all other attributes are ignored. Be sure to end the script referenced by commandfile with the exit command; if you omit exit, the Ant task might appear to hang after the command script is called. |
|
|
none |
(exactly one of these is required: command, commandfile, or explicitcommand) The exact command to execute. No command processing is done, and all other attributes are ignored. |
|
|
user |
admin |
(optional) The user name used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
password |
none |
(optional) Deprecated, use passwordfile instead. The password used when logging into the application server administration instance. This attribute is inherited by nested server elements. |
|
passwordfile |
none |
(optional) File containing passwords. The password from this file is retrieved for communication with the application server administration instance. This attribute is inherited by nested server elements. If both password and passwordfile are specified, passwordfile takes precedence. |
|
host |
localhost |
(optional) Target server. If it is a remote server, use the fully qualified host name. This attribute is inherited by nested server elements. |
|
port |
4849 |
(optional) The administration port on the target server. This attribute is inherited by nested server elements. |
|
see description |
(optional) The installation directory for the local Application Server installation, which is used to find the administrative classes. If not specified, the command checks to see if the asinstalldir parameter has been set. Otherwise, administrative classes must be in the system classpath. |
|
|
see description |
(optional) Deprecated. Use asinstalldir instead. |
Examples
Here is an example of executing the create-jms-dest command:
<sun-appserv-admin command="create-jms-dest --desttype topic">
Here is an example of using commandfile to execute the create-jms-dest command:
<sun-appserv-admin commandfile="create_jms_dest.txt" instance="development">
The create_jms_dest.txt file contains the following:
create-jms-dest --user admin --passwordfile "${passwordfile}" --host
localhost --port 4849 --desttype topic --target server1 simpleJmsDest
Here is an example of using explicitcommand to execute the create-jms-dest command:
<sun-appserv-admin command="create-jms-dest --user admin --passwordfile
"${passwordfile}" --host localhost --port 4849 --desttype topic
--target server1 simpleJmsDest">
sun-appserv-jspc
Precompiles JSP source code into Application Server compatible Java code for initial invocation by Application Server. Use this task to speed up access to JSP files or to check the syntax of JSP source code. You can feed the resulting Java code to the javac task to generate class files for the JSP files.
Subelements
none
Attributes
The following table describes attributes for the sun-appserv-jspc task.
Table 3–15 sun-appserv-jspc Attributes|
Attribute |
Default |
Description |
|---|---|---|
|
|
The destination directory for the generated Java source files. |
|
|
|
(exactly one of these is required: srcdir or webapp) The source directory where the JSP files are located. |
|
|
|
(exactly one of these is required: srcdir or webapp) The directory containing the web application. All JSP files within the directory are recursively parsed. The base directory must have a WEB-INF subdirectory beneath it. When webapp is used, sun-appserv-jspc hands off all dependency checking to the compiler. |
|
|
2 |
(optional) The verbosity integer to be passed to the compiler. |
|
|
|
(optional) The classpath for running the JSP compiler. |
|
|
|
(optional) A reference to the JSP compiler classpath. |
|
|
/ |
(optional) The URI context of relative URI references in the JSP files. If this context does not exist, it is derived from the location of the JSP file relative to the declared or derived value of uriroot. Only pages translated from an explicitly declared JSP file are affected. |
|
|
see description |
(optional) The root directory of the web application, against which URI files are resolved. If this directory is not specified, the first JSP file is used to derive it: each parent directory of the first JSP file is searched for a WEB-INF directory, and the directory closest to the JSP file that has one is used. If no WEB-INF directory is found, the directory sun-appserv-jspc was called from is used. Only pages translated from an explicitly declared JSP file (including tag libraries) are affected. |
|
|
(optional) The destination package for the generated Java classes. |
||
|
see description |
(optional) The installation directory for the local Application Server installation, which is used to find the administrative classes. If not specified, the command checks to see if the asinstalldir parameter has been set. Otherwise, administrative classes must be in the system classpath. |
|
|
see description |
(optional) Deprecated. Use asinstalldir instead. |
Example
The following example uses the webapp attribute to generate Java source files from JSP files. The sun-appserv-jspc task is immediately followed by a javac task, which compiles the generated Java files into class files. The classpath value in the javac task must be all on one line with no spaces.
<sun-appserv-jspc
destdir="${assemble.war}/generated"
webapp="${assemble.war}"
classpath="${assemble.war}/WEB-INF/classes"
asinstalldir="${asinstalldir}" />
<javac
srcdir="${assemble.war}/WEB-INF/generated"
destdir="${assemble.war}/WEB-INF/generated"
debug="on"
classpath="${assemble.war}/WEB-INF/classes:${asinstalldir}/lib/
appserv-rt.jar:${asinstalldir}/lib/appserv-ext.jar">
<include name="**/*.java"/>
</javac>
sun-appserv-update
Enables deployed applications (EAR files) and modules (EJB JAR, RAR, and WAR files) to be updated and reloaded for fast iterative development. This task copies modified class files, XML files, and other contents of the archive files to the appropriate subdirectory of the domain-dir/applications directory, then touches the .reload file to cause dynamic reloading to occur. For more information about dynamic reloading, see Dynamic Reloading.
This is a local task and must be executed on the same machine as the application server.
Subelements
none
Attributes
The following table describes attributes for the sun-appserv-update task.
Table 3–16 sun-appserv-update Attributes|
Attribute |
Default |
Description |
|---|---|---|
|
none |
The component to update, which must be a valid archive. |
|
|
domain1 |
(optional) The domain in which the application has been previously deployed. |
Example
The following example updates the J2EE application foo.ear, which is deployed to the default domain, domain1.
<sun-appserv-update file="foo.ear"/>
Reusable Subelements
Reusable subelements of the Ant tasks for the Application Server are as follows. These are objects upon which the Ant tasks act.
server
Specifies an Application Server instance. Allows a single task to act on multiple server instances. The server attributes override corresponding attributes in the parent task; therefore, the parent task attributes function as default values.
Subelements
none
Attributes
The following table describes attributes for the server element.
Table 3–17 server Attributes|
Attribute |
Default |
Description |
|---|---|---|
|
admin |
(optional) The username used when logging into the application server administration instance. |
|
|
password |
none |
(optional) Deprecated, use passwordfile instead. The password used when logging into the application server administration instance. |
|
passwordfile |
none |
(optional) File containing passwords. The password from this file is retrieved for communication with the application server administration instance. If both password and passwordfile are specified, passwordfile takes precedence. |
|
localhost |
(optional) Target server. When targeting a remote server, use the fully qualified hostname. |
|
|
4849 |
(optional) The administration port on the target server. |
|
|
name of default instance |
(optional) Target application server instance. |
|
|
(applies to sun-appserv-update only) The domain in which the application has been previously deployed. |
||
|
none |
(applies to sun-appserv-instance only) Deprecated. |
|
|
none |
(applies to sun-appserv-instance only, required if action is create, otherwise ignored) The name of the node agent on which the instance is being created. |
|
|
false |
(applies to sun-appserv-instance only, optional) Deprecated. If action is set to start, specifies whether the server starts in debug mode. This attribute is ignored for other values of action. If true, the instance generates additional debugging output throughout its lifetime. |
|
|
true |
(applies to sun-appserv-deploy only, optional) If true, the component is transferred to the server for deployment. If the component is being deployed on the local machine, set upload to false to reduce deployment time. |
|
|
default virtual server only |
(applies to sun-appserv-deploy only, optional) A comma-separated list of virtual servers to be deployment targets. This attribute applies only to application (.ear) or web (.war) components and is ignored for other component types. |
Examples
You can control multiple servers using a single task. In this example, two servers are started, each using a different password. Only the second server is started in debug mode.
<sun-appserv-instance action="start">
<server host="greg.sun.com" passwordfile="${password.greg}"/>
<server host="joe.sun.com" passwordfile="${password.joe}"
debug="true"/>
</sun-appserv-instance>
You can create instances on multiple servers using a single task. This example creates a new instance named qa on two different servers. Both servers use the same password.
<sun-appserv-instance action="create" instanceport="8080"
instance="qa" passwordfile="${passwordfile}>
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
</sun-appserv-instance>
These instances can also be removed from their respective servers:
<sun-appserv-instance action="delete" instance="qa"
passwordfile="${passwordfile}>
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
</sun-appserv-instance>
You can specify different instance names and instance ports using attributes of the nested server element:
<sun-appserv-instance action="create" passwordfile="${passwordfile}>
<server host="greg.sun.com" instanceport="8080" instance="qa"/>
<server host="joe.sun.com" instanceport="9090"
instance="integration-test"/>
</sun-appserv-instance>
You can deploy multiple components to multiple servers (see the component nested element. This example deploys each component to two Application Server instances running on remote servers. Both servers use the same password.
<sun-appserv-deploy passwordfile="${passwordfile}"
asinstalldir="/opt/s1as8" >
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"
contextroot="test"/>
<component file="${assemble}/simplebean.jar"/>
</sun-appserv-deploy>
You can also undeploy multiple components from multiple servers. This example shows the same three components being removed from two different instances. Both servers use the same password.
<sun-appserv-undeploy passwordfile="${passwordfile}">
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-undeploy>
You can enable or disable components on multiple servers. This example shows the same three components being enabled on two different instances. Both servers use the same password.
<sun-appserv-component action="enable" passwordfile="${passwordfile}">
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-component>
component
Specifies a J2EE component. Allows a single task to act on multiple components. The component attributes override corresponding attributes in the parent task; therefore, the parent task attributes function as default values.
Subelements
none
Attributes
The following table describes attributes for the component element.
Table 3–18 component Attributes|
Attribute |
Default |
Description |
|---|---|---|
|
none |
(optional if the parent task is sun-appserv-undeploy or sun-appserv-component) The target component. If this attribute refers to a file, it must be a valid archive. If this attribute refers to a directory, it must contain a valid archive in which all components have been exploded. If upload is set to false, this must be an absolute path on the server machine. |
|
|
name |
file name without extension |
(optional) The display name for the component. |
|
determined by extension |
(optional) Deprecated. |
|
|
true |
(applies to sun-appserv-deploy only, optional) If true, the component is overwritten if it already exists on the server. If false, the containing element’s operation fails if the component exists. |
|
|
false |
(applies to sun-appserv-deploy only, optional) If true, all JSP files found in an enterprise application (.ear) or web application (.war) are precompiled. This attribute is ignored for other component types. |
|
|
client stubs not saved |
(applies to sun-appserv-deploy only, optional) The directory where client stubs are saved. |
|
|
file name without extension |
(applies to sun-appserv-deploy only, optional) The context root for a web module (WAR file). This attribute is ignored if the component is not a WAR file. |
|
|
false |
(applies to sun-appserv-deploy only, optional) If true, syntax and semantics for all deployment descriptors is automatically verified for correctness. |
Examples
You can deploy multiple components using a single task. This example deploys each component to the same Application Server instance running on a remote server.
<sun-appserv-deploy passwordfile="${passwordfile}" host="greg.sun.com"
asinstalldir="/opt/s1as8" >
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"
contextroot="test"/>
<component file="${assemble}/simplebean.jar"/>
</sun-appserv-deploy>
You can also undeploy multiple components using a single task. This example demonstrates using the archive files (EAR and WAR, in this case) and the component name (for the EJB component).
<sun-appserv-undeploy passwordfile="${passwordfile}">
<component file="${assemble}/simpleapp.ear"/
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-undeploy>
You can deploy multiple components to multiple servers. This example deploys each component to two instances running on remote servers. Both servers use the same password.
<sun-appserv-deploy passwordfile="${passwordfile}" asinstalldir="/opt/s1as8" >
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"
contextroot="test"/>
<component file="${assemble}/simplebean.jar"/>
</sun-appserv-deploy>
You can also undeploy multiple components to multiple servers. This example shows the same three components being removed from two different instances. Both servers use the same password.
<sun-appserv-undeploy passwordfile="${passwordfile}">
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-undeploy>
You can enable or disable multiple components. This example demonstrates disabling multiple components using the archive files (EAR and WAR, in this case) and the component name (for the EJB component).
<sun-appserv-component action="disable" passwordfile="${passwordfile}">
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-component>
You can enable or disable multiple components on multiple servers. This example shows the same three components being enabled on two different instances. Both servers use the same password.
<sun-appserv-component action="enable" passwordfile="${passwordfile}">
<server host="greg.sun.com"/>
<server host="joe.sun.com"/>
<component file="${assemble}/simpleapp.ear"/>
<component file="${assemble}/simpleservlet.war"/>
<component name="simplebean" />
</sun-appserv-component>
fileset
Selects component files that match specified parameters. When fileset is included as a subelement, the name and contextroot attributes of the containing element must use their default values for each file in the fileset. For more information, see http://ant.apache.org/manual/CoreTypes/fileset.html.
Chapter 4 Debugging Applications
This chapter gives guidelines for debugging applications in the Sun Java System Application Server. It includes the following sections:
Enabling Debugging
When you enable debugging, you enable both local and remote debugging. To start the server in debug mode, use the --debug option as follows:
asadmin start-domain --debug [domain-name]
You can then attach to the server from the Java Debugger (jdb) at its default Java Platform Debugger Architecture (JPDA) port, which is 9009. For example, for UNIX® systems:
jdb -attach 9009
For Windows:
jdb -connect com.sun.jdi.SocketAttach:port=9009
For more information about the jdb debugger, see the following links:
-
Java Platform Debugger Architecture - The Java Debugger: http://java.sun.com/products/jpda/doc/soljdb.html
-
Java Platform Debugger Architecture - Connecting with JDB: http://java.sun.com/products/jpda/doc/conninv.html#JDB
Application Server debugging is based on the JPDA (Java Platform Debugger Architecture). For more information, see JPDA Options.
You can attach to the Application Server using any JPDA compliant debugger, including that of NetBeans, Sun Java Studio, JBuilder, Eclipse, and so on.
You can enable debugging even when the application server is started without the --debug option. This is useful if you start the application server from the Windows Start Menu or if you want to make sure that debugging is always turned on.
 To set the server to automatically start up in debug
mode
To set the server to automatically start up in debug
mode
-
Select the JVM Settings component under the relevant configuration in the Administration Console.
-
Check the Debug Enabled box.
-
To specify a different port (from 9009, the default) to use when attaching the JVM to a debugger, specify address= port-number in the Debug Options field.
-
If you wish to add JPDA options, add any desired JPDA debugging options in Debug Options. See JPDA Options.
See Also
For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
JPDA Options
The default JPDA options in Application Server are as follows:
-Xdebug -Xrunjdwp:transport=dt_socket,server=y,suspend=n,address=9009
For Windows, you can change dt_socket to dt_shmem.
If you substitute suspend=y, the JVM starts in suspended mode and stays suspended until a debugger attaches to it. This is helpful if you want to start debugging as soon as the JVM starts.
To specify a different port (from 9009, the default) to use when attaching the JVM to a debugger, specify address=port-number.
You can include additional options. A list of JPDA debugging options is available at http://java.sun.com/products/jpda/doc/conninv.html#Invocation.
Generating a Stack Trace for Debugging
You can generate a Java stack trace for debugging as described here if the Application Server is in verbose mode (see Enabling Verbose Mode):
http://developer.java.sun.com/developer/technicalArticles/Programming/Stacktrace/
The stack trace goes to the domain-dir/logs/server.log file and also appears on the command prompt screen.
If the -Xrs flag is set (for reduced signal usage) in the domain.xml file (under jvm-options), comment it out before generating the stack trace. If the -Xrs flag is used, the server might simply dump core and restart when you send the signal to generate the trace. For more about the domain.xml file, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Reference.
Using an IDE
You can use an IDE (integrated development environment) with the Application Server to take advantage of the IDE's debugging features.
 To use the NetBeans IDE for Debugging
To use the NetBeans IDE for Debugging
The following steps are applicable to the NetBeans 5 IDE and the Sun Java Studio 8 software, which is built on the NetBeans IDE.
-
Download the latest version of NetBeans from http://www.netbeans.org.
This site also provides documentation for the NetBeans IDE.
-
Start the NetBeans IDE.
-
If an Application Server is not already configured in the NetBeans IDE, perform the following steps:
-
Select the Runtime tab to display the Runtime window.
-
Right-click on Servers in the Runtime window.
-
Select the Add Server command from the menu.
-
On the first screen, select Sun Java System Application Server in the Server field, and type a name in the Name field. Select Next.
-
On the second screen, fill in the requested configuration information. In the Domains folder field, use the Browse button to go to the Application Server domain-root-dir directory.
-
Click Finish.
-
-
Create a project (an application or module) in the NetBeans IDE.
-
Right-click on the project in the component tree and select Debug Project from the menu.
This stops the Application Server and restarts it in debug mode.
-
Set break points in your source file in the NetBeans IDE as usual, and run the application.
Sun Java System Message Queue Debugging
Sun Java System Message Queue has a broker logger, which can be useful for debugging JMS, including message-driven bean, applications. You can adjust the logger’s verbosity, and you can send the logger output to the broker’s console using the broker’s -tty option. For more information, see the Sun Java System Message Queue 3.7 UR1 Administration Guide.
Enabling Verbose Mode
If you want to see the server logs and messages printed to System.out on your command prompt screen, you can start the server in verbose mode. This makes it easy to do simple debugging using print statements, without having to view the server.log file every time.
When the server is in verbose mode, messages are logged to the console or terminal window in addition to the log file. In addition, pressing Ctrl-C stops the server and pressing Ctrl-\ (on UNIX platforms) or Ctrl-Break (on Windows platforms) prints a thread dump. On UNIX platforms, you can also print a thread dump using the jstack command (see http://java.sun.com/j2se/1.5.0/docs/tooldocs/share/jstack.html) or the command kill -QUIT process_id.
To start the server in verbose mode, use the --verbose option as follows:
asadmin start-domain --verbose [domain-name]
You can enable verbose mode even when the application server is started without the --verbose option. This is useful if you start the application server from the Windows Start Menu or if you want to make sure that verbose mode is always turned on.
You can set the server to automatically start up in verbose mode using the Administration Console. For details, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
Logging
You can use the Application Server’s log files to help debug your applications. In the Administration Console, select the Stand-Alone Instances component, select the instance, then click on the View Log Files button in the General Information page. For details about logging, see the Sun Java System Application Server Enterprise Edition 8.2 Administration Guide.
Profiling
You can use a profiler to perform remote profiling on the Application Server to discover bottlenecks in server-side performance. This section describes how to configure these profilers for use with the Application Server:
Information about comprehensive monitoring and management support in the JavaTM 2 Platform, Standard Edition (J2SETM platform) version 5.0 is available at http://java.sun.com/j2se/1.5.0/docs/guide/management/index.html.
The HPROF Profiler
HPROF is a simple profiler agent shipped with the Java 2 SDK. It is a dynamically linked library that interacts with the JVMPI and writes out profiling information either to a file or to a socket in ASCII or binary format.
HPROF can present CPU usage, heap allocation statistics, and monitor contention profiles. In addition, it can also report complete heap dumps and states of all the monitors and threads in the Java virtual machine. For more details on the HPROF profiler, see the JDK documentation at http://java.sun.com/j2se/1.4.2/docs/guide/jvmpi/jvmpi.html#hprof.
Once HPROF is enabled using the following instructions, its libraries are loaded into the server process.
 To use HPROF profiling on UNIX
To use HPROF profiling on UNIX
-
Configure the Application Server using the Administration Console:
-
Select the JVM Settings component under the relevant configuration, then select the Profiler tab.
-
Edit the following fields:
-
Profiler Name: hprof
-
Profiler Enabled: true
-
Classpath: (leave blank)
-
JVM Option: For each of these options, select Add, type the option in the Value field, then check its box:
-Xrunhprof:file=log.txt,options
Here is an example of options you can use:
-Xrunhprof:file=log.txt,thread=y,depth=3
The file option determines where the stack dump is written in Step 2.
The syntax of HPROF options is as follows:
-Xrunhprof[:help]|[:option=value,option2=value2, ...]
Using help lists options that can be passed to HPROF. The output is as follows:
Hprof usage: -Xrunhprof[:help]|[:<option>=<value>, ...] Option Name and Value Description Default --------------------- ----------- ------- heap=dump|sites|all heap profiling all cpu=samples|old CPU usage off format=a|b ascii or binary output a file=<file> write data to file java.hprof (.txt for ascii) net=<host>:<port> send data over a socket write to file depth=<size> stack trace depth 4 cutoff=<value> output cutoff point 0.0001 lineno=y|n line number in traces? y thread=y|n thread in traces? n doe=y|n dump on exit? y
-
-
-
Restart the Application Server. This writes an HPROF stack dump to the file you specified using the file HPROF option in Step 1.
The Optimizeit Profiler
You can purchase OptimizeitTM from Borland at http://www.borland.com/optimizeit.
Once Optimizeit is enabled using the following instructions, its libraries are loaded into the server process.
 To enable remote profiling with Optimizeit
To enable remote profiling with Optimizeit
-
Configure your operating system:
-
On Solaris, add Optimizeit-dir/lib to the LD_LIBRARY_PATH environment variable.
-
On Windows, add Optimizeit-dir/lib to the PATH environment variable.
-
-
Configure the Application Server using the Administration Console:
-
Select the JVM Settings component under the relevant configuration, then select the Profiler tab.
-
Edit the following fields:
-
Profiler Name: optimizeit
-
Profiler Enabled: true
-
Classpath: Optimizeit-dir/lib/optit.jar
-
JVM Option: For each of these options, select Add, type the option in the Value field, then check its box:
-DOPTITHOME=Optimizeit-dir -Xrunpri:startAudit=t -Xbootclasspath/p:/Optimizeit-dir/lib/oibcp.jar
-
-
-
In addition, you might have to set the following in your server.policy file.
For more information about the server.policy file, see The server.policy File
grant codeBase "file:Optimizeit-dir/lib/optit.jar" { permission java.security.AllPermission; }; -
Restart the Application Server.
When the server starts up with this configuration, you can attach the profiler.
See Also
For further details, see the Optimizeit documentation.
Troubleshooting
If any of the configuration options are missing or incorrect, the profiler might experience problems that affect the performance of the Application Server.
- © 2010, Oracle Corporation and/or its affiliates
