Configuring the Synchronization Settings
After each directory source is configured, the synchronization parameters are configured to match Example Bank’s requirements as explained in these section:
Configuring the Attributes Settings
The Attributes settings reflect Example Bank’s requirement to synchronize changes to a user’s password, full name, and login. The destinationindicator <-\> activedirectorydomainname <-\> user_nt_domain_name mapping displays because it synchronizes multiple Windows domains.
 To Configure the Attribute Settings
To Configure the Attribute Settings
-
In the Console, click the Configuration tab, then click the Attributes tab.
-
Under Synchronized Attributes, enter the attributes that Example Bank requires to synchronize with Directory Server.
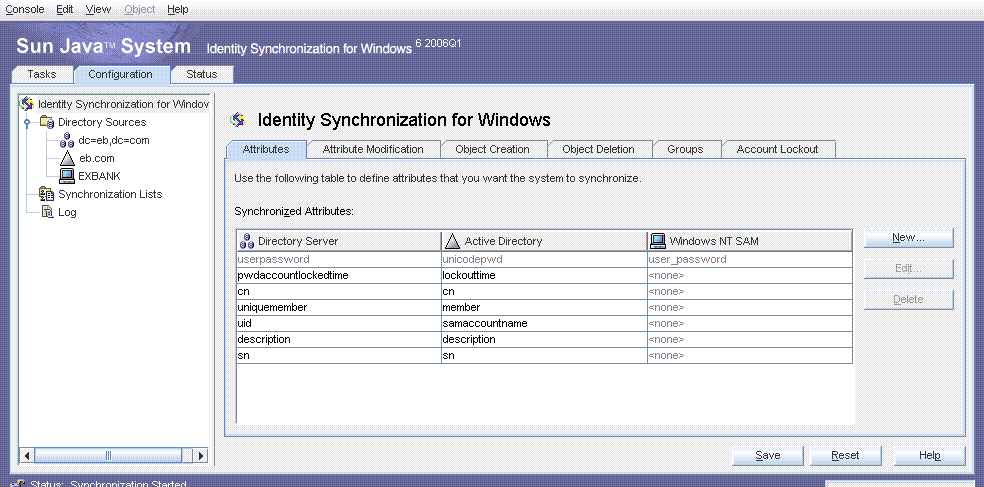
Note –Mapping an attribute to the synthetic activedirectorydomainname or user_nt_domain_name attribute is not unique to deployments that have both Active Directory and Windows NT domains. The same approach is taken in homogeneous Windows environments that have multiple Active Directory or Windows NT domains, where the destinationindicator attribute is mapped to activedirectorydomainname or user_nt_domain_name.
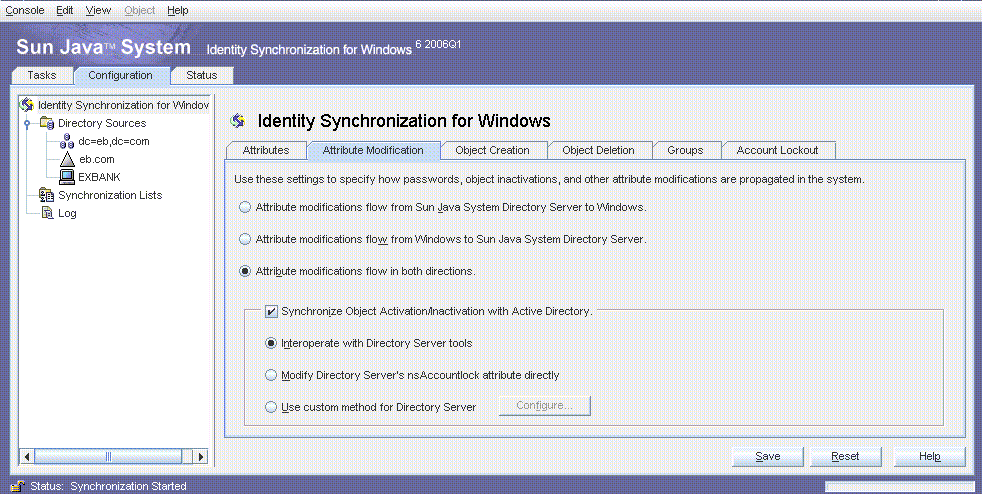
Configuring the Attribute Modification Settings
The Attribute Modification settings reflect Example Bank’s requirements to synchronize the attribute changes and account deactivations, bidirectionally, between the Active Directory and Directory Server sources.
 To Configure the Attribute Modification settings
To Configure the Attribute Modification settings
-
In the Identity Synchronization for Windows Console, click the Configuration tab, then click the Attribute Modification tab.
-
Select Attribute Modifications Flow in Both Directions.
-
Select the Synchronize Object Activation/Inactivation with Active Directory check box and select Interoperate With Directory Server Tools.
Configuring the Object Creation Settings
The Object Creation settings reflect Example Bank’s requirement to only synchronize user creations from Active Directory to Directory Server.
The Object Creation settings apply to both Active Directory and Windows NT because Example Bank has an environment with both the systems. New users in Active Directory and Windows NT are synchronized with Directory Server. Example Bank is migrating all Windows NT users to Active Directory; so no new users will be created in Windows NT.
 To Configure the Object Creation Settings
To Configure the Object Creation Settings
-
In the Console, click the Configuration tab, then click the Object Creation tab.
-
Select the Object Creations Flow From Windows to Sun Java System Directory Server check box.
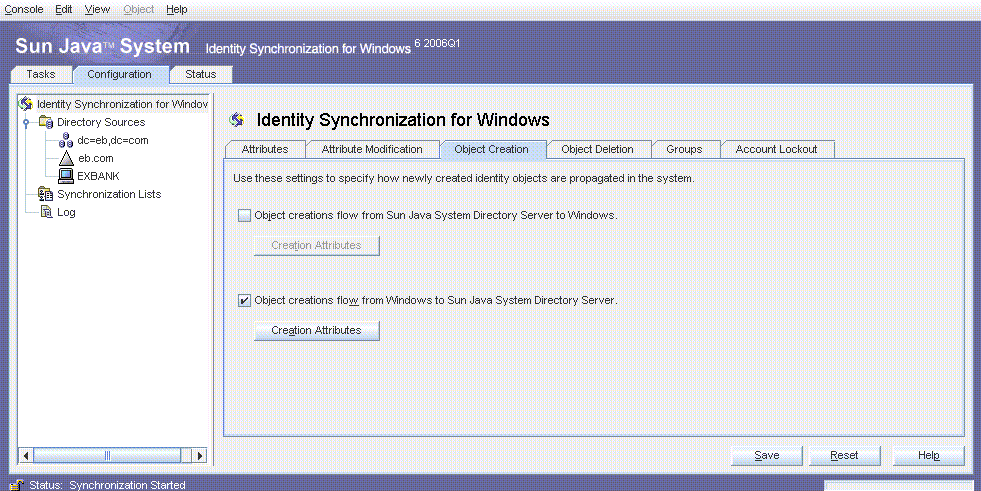
Note –To synchronize object deletions, click the Object Deletion tab and select Object Deletions Flow From Windows to Sun Java System Directory Server check box.
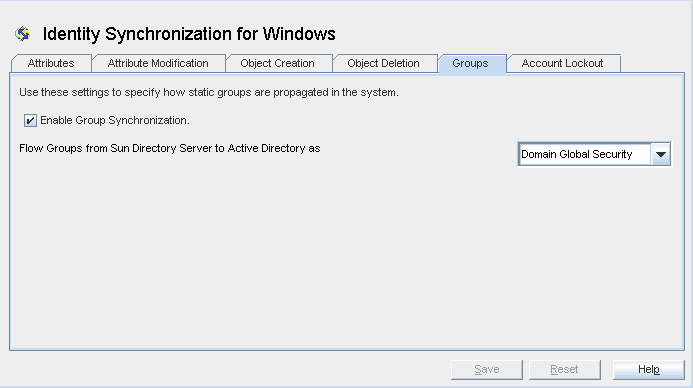
Configuring the Group Synchronization Settings
You can create or delete a group, and associate or disassociate users with that group in a directory environment. If Group Synchronization is enabled, the changes that you make in one directory environment automatically propagate to the other directory environment. All the users are synchronized across the directory servers with their group membership intact.
Note –
When Group Synchronization is enabled, the uniquemember Directory Server attribute and the member attribute Active Directory attribute are internally mapped.
 To Configure the Group synchronization Settings
To Configure the Group synchronization Settings
-
In the Console, click the Configuration tab, then click the Groups tab.
-
Select the Enable Group Synchronization check box.
-
From the drop-down menu, choose Domain Global Security or Domain Global Distribution to propagate groups from Sun Directory Server to Active Directory.
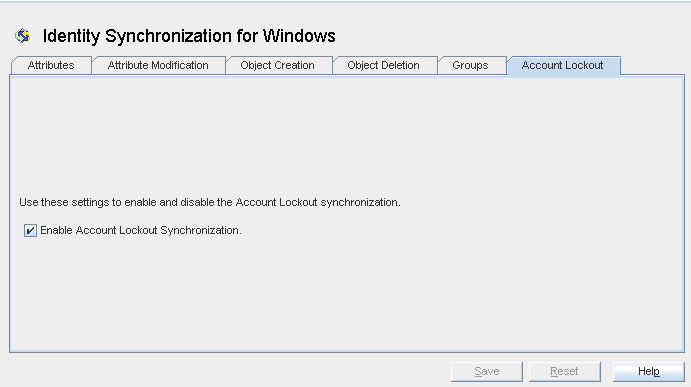
Configuring the Account Lockout Synchronization Settings
In Identity Synchronization for Windows, account lockout and unlockout are synchronized between the Directory Server and Active Directory sources.
 To Configure the Account Lockout Synchronization Settings
To Configure the Account Lockout Synchronization Settings
-
In the Console, click the Configuration tab, then click the Account Lockout tab.
-
Select the Enable Account Lockout Synchronization check box.
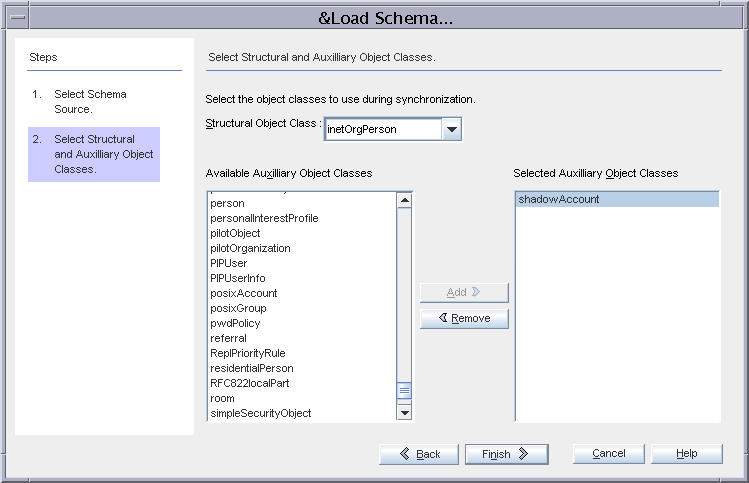
Adding the shadowAccount Object Class
When configuring Identity Synchronization for Windows to interoperate with PAM LDAP on Solaris systems, select and then add the shadowAccount object class as an auxiliary object class for synchronization. When a new user is created in Active Directory, and that user is synchronized to Directory Server, the user entry includes the shadowAccount object class, which is required by PAM LDAP.
Figure 2–2 shadowAccount Object Class
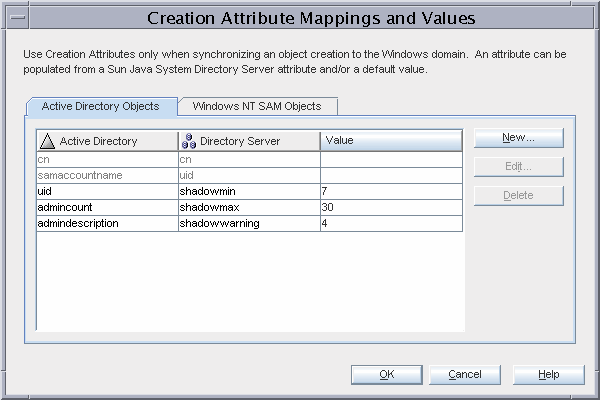
Configuring the Creation Attributes
Use the Creation Attribute Mappings and Values dialog box to configure additional attributes to be synchronized when an entry is created.
 To Configure the Creation Attributes
To Configure the Creation Attributes
-
Click Creation Attributes under the Object Creation tab.
-
Provide a mapping or default value for sn, a mandatory attribute for the inetOrgPerson object class.
Active Directory has a corresponding attribute sn. However, Windows NT does not have an equivalent attribute, so the special ** NO VALUE ** value is provided. Because Example Bank’s requirements do not include creating users in Windows NT, this value does not appear in any of the user entries. This value is only provided to conform to the Console’s validations.
Configure the shadowmin, shadowmax, and shadowwarning attributes, which are used for PAM LDAP.
-
A shadowmin value of 7 implies that a user must wait seven days from the time the password has changed before changing it again.
-
A shadowmax value of 30 implies that the user must change the password at least every 30 days.
-
A shadowwarning value of 4 implies that the user is warned that the password must be changed four days before the password expires.
Directory Server attributes that are grayed-out are mandatory creation attributes. The inetOrgPerson object class has cn and sn as mandatory attributes, and the shadowAccount object class has uid as a mandatory attribute.
-
- © 2010, Oracle Corporation and/or its affiliates
