These release notes contain important information about Netscape Certificate Management System, version 4.2. Please read these notes before using the product. Use of this product is subject to the terms detailed in the license agreement accompanying it.
Note: The name of the product has been changed to iPlanet Certificate Management System and the product-download site (http://www.iplanet.com/downloads/download/) identifies the product as iPlanet Certificate Management System 4.2. The name change is not reflected in the documentation or in the software.
| Platform/OS | CMS 4.2 | CMS 4.1 |
| Sun Solaris |
|
|
| Windows NT |
|
|
| Compaq Tru64 |
|
|
| AIX |
|
|
| HP-UX |
|
|
| Other Components | CMS 4.2 | CMS 4.1 |
| CMS SDK and Samples | Are installed with the rest of the server binaries:
|
Are contained in a directory named CMS_SDK:
|
| CMS Documentation | List of documentation is available after installation at: <server_root>/manual/index.html | List of documentation is available after installation at: <server_root>/manual/index.html |
| Netscape Administration Server |
|
|
| Netscape Directory Server |
|
|
| Netscape Console |
|
|
| Netscape Personal Security Manager |
http://www.iplanet.com/downloads/download/index.html |
Includes an Alpha build of the Dual-Key Test Bed or Personal Security Manager for Communicator 4.5 in the domestic version of the Certificate Management System. |
| Network Security Services (NSS) |
|
|
| ValiCert Certificate VATM |
|
|
| Feature | CMS 4.2 | CMS 4.1 |
| Authentication methods for end users |
|
|
| Forms for certificate enrollment |
|
|
| Forms for certificate renewal |
|
|
| Forms for certificate revocation |
|
|
| Policies for governing the formulation of certificates | Constraints-specific policies:
|
Constraints-specific policies:
|
| Policies for adding certificate extensions | Extension-specific policies with ability to set the 'critical' flag (except
for the Netscape Certificate Type policy, all
other CMS 4.1 policies have been modified):
|
Extension-specific policies:
|
| Schedulable jobs |
|
|
| Event-driven notifications |
|
|
| Publishing of certificates and CRLs |
|
|
| Logging |
|
|
| Backup and recovery |
|
|
| Certificate Manager |
|
|
| Registration Manager |
|
|
| Key Recovery Manager |
|
|
| Agent Services interface |
|
After you run the setup script as described under Installation Procedure, see the file below for a complete list of the documentation installed with the product: <server_root>/manual/index.html
If you are working with files you have downloaded from the web site (http://www.iplanet.com/downloads/download/index.html), as opposed to the files on the CD, the Docs directory mentioned above will not be present. Instead, you must first run the setup script, then check this file for the documentation: <server_root>/manual/index.html
For the latest information about Certificate Management System, including current
release notes, technical notes, and deployment information, check this URL:
http://docs.iplanet.com/docs/manuals/cms.html
Operating Systems SupportedOther Required SoftwareWindows NT 4.0 with Service Pack 4, 5, or 6 Solaris 2.6, 2.7, or 8 Compaq Tru64 v4.0D AIX 4.3 HP-UX B.11.00 Platform and Hard Disk Requirements
- Netscape Administration Server 4.2 (included)
- Netscape Directory Server 4.12 (included)
Check the Directory Server 4.12 release notes at http://docs.iplanet.com/docs/manuals/directory.html for the latest information about installing this server.- Browser software that supports SSL
Note: We strongly recommend that users who will interact with Certificate Management System as agents or end entities using Netscape Communicator should use Communicator version 4.7x. Earlier versions, such as 4.5x, may not work properly. Netscape 6 has not yet been fully tested with Certificate Management System 4.2.In addition to the requirements listed below, make sure you have ample swap space or virtual memory allocated for the system on which you intend to install Certificate Management System.
Solaris Platform Requirements OS Version Solaris 2.6, 2.7, or 8 Machine Ultra 1 or faster RAM 128 MB (required) Hard disk storage space requirements Total required is approximately 400 MB, as follows:
- Total transient space required during installation: 100 MB
- Hard disk storage space required for installation:
- Space required for setup, configuration, and running the server: approximately 250 MB
- Additional space to allow for database growth in pilot deployment: approximately 50 MB
- Total disk storage space for installation: approximately 300 MB
Windows NT Platform Requirements OS Version Windows NT 4.0 with Service Pack 4, 5, or 6 Machine Pentium 166 or faster File system NTFS or FAT RAM 128 MB of RAM (recommended) Hard disk storage space requirements Total required is approximately 350 MB, as follows:
- Total transient space required during installation: 100 MB
- Hard disk storage space required for installation:
- Space required for setup, configuration, and running the server: approximately 200 MB
- Additional space to allow for database growth in pilot deployment: approximately 50 MB
- Total disk storage space for installation: approximately 250 MB
Other Requirements
- On Unix systems, you must install as root in order to use well-known port numbers (such as 443) that are less than 1024. If you do not plan to use port numbers less than 1024, you do not need to install as root. If you plan to run as root, you should also install as root and specify nobody as the default run-as user and group.
- On a Windows NT system, you must install as Administrator or a user with Administrator privileges (that is, the user must be in the Administrators group).
When you run the installation program for upgrading a CMS 4.1x instance, you will be presented with the following panels (the example below lists the panels on UNIX):
- Welcome
- License
- Product Selection
- Location
- Server Products Components- Core Components- Fully qualified domain name of machine
- Directory Suite Components
- Administration Service Components
- Certificate Server Components
- User and Group- System User- Configuration Directory Server Administration Identifier
- System Group- Administrator ID- Administration Server Port for Console (You must enter the same port
- Password
number that was used for your 4.1 Console)
- Administration Server User
- Certificate Server Identifier (The CMS instance name that you enter in
this panel must exist.)
- Globally Specific: (backed up for each instance)
Step 1. Stop Certificate Management System.
Step 2. Update the basic indexes.
To do this, make sure the following indexes
are specified in the
<server_root>/slapd-<instance_id>-db/config/slapd.ldbm.conf
file:
<server_root>/bin/cert/install/42-ca-vlv.ldif for the Certificate
Manager
<server_root>/bin/cert/install/42-ra-vlv.ldif for the Registration
Manager
<server_root>/bin/cert/install/42-kra-vlv.ldif for the Data Recovery
Manager
For example, if you have a CMS instance with Certificate Manager and Data Recovery Manager, your command would look similar to this:
../shared/bin/ldapmodify -h certificate.siroe.com -p 38900 -D "cn=directory manager" -w "pwd1234" -c -a -f d:\netscape\server4\bin\cert\install\42-ca-vlv.ldif
../shared/bin/ldapmodify -h certificate.siroe.com -p 38900 -D "cn=directory manager" -w "pwd1234" -c -a -f d:\netscape\server4\bin\cert\install\42-kra-vlv.ldif
(You might see some warning messages because some of the indexes were
created in CMS 4.1 installation.)
This command will create a file in ldif sub-directory, and the timestamp is used as the filename.
Step 8. Start Certificate Management System.
If you remove the password from the adm.conf file, every time you start Netscape Console, you'll be prompted for the Administration Server administrator's password.

Once you've provided the password, if the server you're trying to connect to uses SSL, you'll be asked for the SSL token password you specified when you installed the server certificate.
To remove the clear text Administration Server password:
To configure the server to run a CGI script:
User Directory Subtree: O=Siroe
The "<space>Corporation" gets left off; that is, the words trailing the space get truncated in the UI. [# 395046]


Note that the servReq.getHeader("auth-cert") only works on Netscape
servers. Sun's Java server uses req.getAttribute("javaex.net.ssl.peer_certificates").
The above code eliminates the need for you to do LDAP queries to obtain the
certificate from the LDAP directory. [# 393043]

sslyp devel - SSLeay source code patch file
1.51.2
nfjava devel - nFast Java Generic stub
0.2.11
ldb185 user -
1.0.4
nfast devel - nFast developer software
1.52.5
nfast user - nFast software
1.52.5
nftcl user - Command line key management
1.59.2
nsapi user - Netscape Enterprise Server 3.x plug-in
1.60.6
opensl user - nftcl certificate generation utility
0.3.6
tclsrc devel - Tcl run time - Headers and Libraries
1.8.7
tclsrc user - Tcl run time
1.8.7
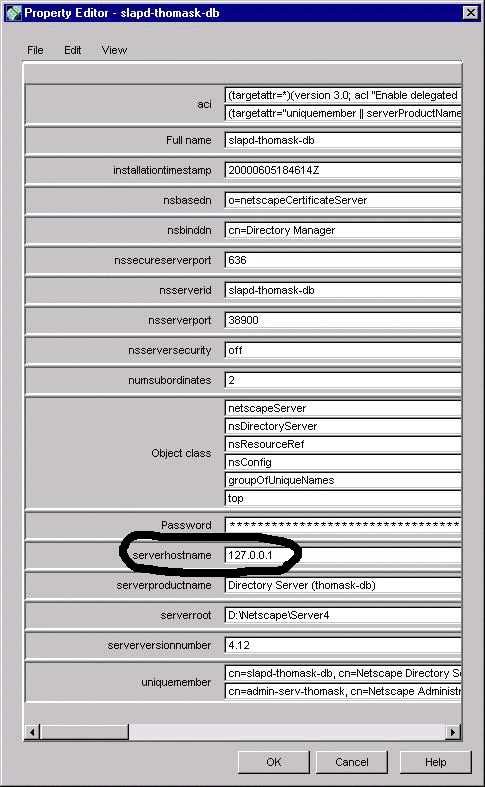
radm.https.nickName=Server-Cert cert-<instance_id>Change the nick name to include smartcard0: as follows:
radm.https.nickName=smartcard0:Server-Cert cert-<instance_id>After this change, the server will be able to start successfully.
"Public storage key: used to encrypt an end entity's private encryption key for long-term storage.
"Private storage key: used to decrypt an end entity's stored private encryption key after m of n recovery agents have authorized the recovery operation."
In fact, the opposite is true. The documentation should read:
"Public storage key: used to decrypt an end entity's stored private encryption key after m of n recovery agents have authorized the recovery operation.used to encrypt an end entity's private encryption key for long-term storage.
"Private storage key: used to encrypt an end entity's private encryption key for long-term storage."This section of the documentation will be fixed in the next version of the product.
| Parameter | Description |
| attribute | Specifies the LDAP attribute, the presence of which is to be checked
in the certificate-enrollment request. Permissible values: Valid directory attributes, separated by commas; the default value is pin. Example: pin |
| value | If this parameter is non-empty, the attribute value must match this value for the request to proceed to the next stage. |
| ldap.ldapconn.basedn | Specifies the base DN for searching the LDAP directory--the plug-in
uses the value of the uid field from the HTTP input (what a user
enters in the enrollment from) and the base DN to construct an LDAP search
filter. Permissible values: Any valid DN string of up to 255 characters. (If your user's DN is uid=jdoe, o=company, you might want to use o=company here.) Example: O=siroe.com |
| ldap.ldapconn.host | Specifies the host name of the LDAP directory to connect to. Permissible values: The name must be fully-qualified host name in the <machine_name>.<your_domain>.<domain> form. Example: corpDirectory.siroe.com |
| ldap.ldapconn.port | Specifies the TCP/IP port at which the LDAP directory listens to requests
from Certificate Management System. Permissible values: Any valid port number. The default is 389; use 636 if the directory is configured for SSL-enabled communication. Example: 389 |
| ldap.ldapconn.secureConn | Specifies the type--SSL or non-SSL--of the port at which the LDAP directory
listens to requests from Certificate Management System.
|
| ldap.ldapconn.version | Specifies the LDAP protocol version. Permissible values: 2 or 3.
|
| ldap.ldapauth.bindDN | Specifies the user entry to bind as for checking the attribute in the
LDAP directory. Permissible values: A valid bind DN. Example: CN=pinmanager |
| password | Specifies the password associated with the DN specified by the ldap.ldapauthbindDN parameter. |
| ldap.ldapauth.authtype | Specifies how to bind to the directory or the authentication type--basic
authentication or SSL client authentication--required in order to check
attributes in the LDAP directory. Permissible values: BasicAuth or SslClientAuth.
|
| ldap.ldapauth.clientCertNickname | Specifies the nickname or the friendly name of the certificate to be
used for SSL client authentication to the LDAP directory in order to check
attributes. Make sure that the certificate is valid and has been signed
by a CA that is trusted in the directory's certificate database, and that
the directory's certmap.conf file has been configured to correctly
map the certificate to a DN in the directory. (This is needed for PIN
removal only.) Permissible values: Enter the name of a currently valid CMS certificate, for example, its SSL server certificate. Example: Server-Cert |
| ldap.ldapconn.minConns | Specifies the minimum number of connections permitted (or to keep open)
to the LDAP directory. Permissible values: 1 to 3; the default value is1. Example: 3 |
| ldap.ldapconn.maxConns | Specifies the maximum number of connections permitted to the LDAP directory;
when needed, connection pool can grow to this many (multiplexed) connections.
Permissible values: 3 to 10; the default value is 5. Example: 9 |
This also applies to other mappers. [# 395043]
$NETSITE_ROOT/bin/cert/admin/bin/certadd
-f $NETSITE_ROOT/cert-<instance_id>/config/pwfile
net start cert-<instance_id>add
/fC:%NETSITE_ROOT%\cert-<instance_id>\config\pwfile
"Siroe, Inc."in the text field for the O component. [# 391583]
http://docs.iplanet.com/docs/manuals/cms.htmlIf you need further assistance or information about Certificate Management System, please contact technical support. For information, check this site:
http://www.iplanet.com/support/index.htmlYou may also contact us through our newsgroup for support, questions, answers, and the latest information:
snews://secnews.netscape.com/netscape.dev.certificateYou might also find it useful to subscribe to the following newsgroups, where security-related topics are discussed:
snews://secnews.netscape.com/netscape.dev.sslWhen reporting problems, please include the following:
snews://secnews.netscape.com/netscape.dev.security
| When | Where | What's been changed/added |
| 09/13/2000 | Supported Operating Systems | Changed 'OSF/1' to 'Compaq Tru64' and 'Solaris 2.8' to 'Solaris 8'. |
| -- " -- | CEP Support | Automated enrollment with CEP fails. [# 511839] |
| -- " -- | Remote Registration Manager | If either the root CA or subordinate CA certificate doesn't have an O= in the subject name, the Registration Manager setup will fail. [# 512054] |
| 10/11/2000 | -- | Details about the bugs that're addressed in the patch, cms42-sp1.zip available at http://www.iplanet.com/downloads/patches. |
| -- " -- | CA Cloning | Problem generating the SSL server certificate when cloning of a CA on another machine. [# 503641] |
| -- " -- | CEP Support | Automated enrollment with CEP fails [# 511839]; requests with no challenge password result in 'pending' response. [# 517187]; the deferOnFailure preference is not working. [# 517191]; and Invalid ContentInfo in responses [# 517057]. |
| -- " -- | Job Scheduling/Notification | Unpublishing of expired certificates from the directory doesn't work. [# 512368] |
| -- " -- | Miscellaneous | Disallow specially-formed URI for security. [# 515951] |
| -- " -- | Policies | BasicConstraintsExt plug-in doesn't recognize the isCA option when it's disabled. [# 516412] |
| -- " -- | Policies | CertificatePoliciesExt plug-in results in errors when some fields are left blank. [# 514915] |
| 10/12/2000 | Software/Hardware Requirements | Disk-space requirements. |
| 10/19/2000 | Directory Server | Directory Server Gateway bug. |
| 12/07/2000 | Installation | CMS Installation Wizard doesn't always detect which ports are in use. [# 522361] |
| 01/04/2001 | Third-Party Products | CMS documentation identifies the wrong Check Point product. |
| -- " -- | Hardware Tokens | CMS problem with Chrysalis Luna hardware token. [# 524072 ] |
| 11/01/2002 | Job Scheduling/Notification | Registration Manager cannot configure automatic renewal notifications. [# 464982] |
| 11/01/2002 | Definitions of public and private storage keys. [# 4727931] |
© Copyright © 2002 Sun Microsystems, Inc. Some preexisting portions Copyright © 2000 Netscape Communications Corp. All rights reserved.