Sun Open Telecommunications Platform Release Notes
These release notes contain important information available at the time of release of SunTM Open Telecommunications Platform (Sun OTP) version 2.0.
These release notes contain the following sections:
What Is Sun OTP?
Sun Open Telecommunications Platform provides an integrated solution that enable high availability services, management services, application provisioning services, and security services for development, deployment, hosting, and securing the interface for sustaining Network Equipment Provider (NEP) applications.
For Sun OTP download and installation procedures, see Sun Open Telecommunications Platform 2.0 Installation Guide.
Target Audience
OEM developers who wish to install Sun OTP in their development environment and integrate their applications with Sun OTP.
Sun OTP Documentation Set
Sun OTP guides are available as online files in PDF and HTML formats. The following table lists the tasks and concepts described in each guide.
Table 1 Sun OTP Documentation Map|
Documentation |
Purpose |
|---|---|
|
Late-breaking information about the software and documentation |
|
|
Provides the procedure for installing Sun OTP in the development environment |
The complete Sun OTP documentation is available at http://docs.sun.com/app/docs/coll/1629.4.
Supported Features in Sun OTP 2.0
Sun OTP 2.0 supports the following features:
Multiple Installation Scenarios
Sun OTP 2.0 supports multiple installation scenarios. You can install Sun OTP 2.0 in the following scenarios on:
-
Stand-alone system without zones
-
Stand-alone system with zones
-
Stand-alone system with logical domains
-
Clustered system without zones
-
Clustered system with zones
Upgrading Sun OTP Version 1.1 to Sun OTP Version 2.0
You can upgrade from Sun OTP version 1.1 to version 2.0 using the standard, quantum leap, or live upgrade method.
-
Standard Upgrade – Shuts down the cluster before upgrading the cluster nodes. Restart the cluster after all the nodes are fully upgraded.
-
Quantum Leap Upgrade – Divides the cluster into two groups of nodes. Bring down one group of nodes and upgrade them. The other group of nodes continues to provide services. After you complete upgrade of the first group of nodes, switch services to those upgraded nodes. You can then upgrade the remaining nodes and boot them back into the rest of the cluster. The cluster outage time is limited to the amount of time needed for the cluster to switch over services to the upgraded partition.
-
Live Upgrade – Retains the previous cluster configuration until you have upgraded all nodes and commit to the upgrade. If the upgraded configuration causes a problem, revert to your previous cluster configuration until you can rectify the problem.
Backing up and Restoring Sun OTP Services
Sun OTP 2.0 provides an extended feature to back up and restore the Sun OTP services. You can back up an individual service or all running services for Sun OTP with the exception of services running on the remote host. Similarly, you can restore Sun OTP services only on the same host on which they were originally backed up.
Web SSO Administration
Sun OTP 2.0 provides you the ability to administer Web Single Sign On (SSO) using the browser user interface (BUI) and the command-line interface (CLI). You can create new Web SSO users, change the password of existing users, and remove existing users.
Hardening and Unhardening the Sun OTP Host
Using Sun OTP 2.0, you can harden and unharden the Sun OTP host. Hardening is the process of modifying the SolarisTM operating system configuration to improve the network security of a system. By using the hardening process, you can close the ports and disable the services that might present a security risk to the system. You can unharden, that is, reopen the ports and enable the services that were closed by the hardening process.
Supported Services in Sun OTP 2.0
Sun OTP provides platform application and security services. Platform services are focused on operational and lifecycle management of base platform elements. Application centric services are focused on operational and lifecycle management of hosted NEP applications.
Sun OTP supports the following services:
Provisioning Service
Provisioning service consists of platform and application provisioning services.
Platform Provisioning
The platform provisioning service enables end-to-end provisioning of Sun OTP compute elements, including bare metal and firmware provisioning, operating system provisioning, and provisioning of Sun OTP software components. Operations supported by the platform provisioning service are identical to the application provisioning operations, with the exception that the operations apply to platform software instead of application software.
Application Provisioning
The application provisioning service enables end-to-end provisioning of NEP applications, including initial application deployment, application upgrade, and application patching. The application provisioning services are capable of deploying applications on a single system, or on a group of systems that follow a set of defined grouping semantics. They are also capable of deploying both single and multitier applications.
The application provisioning service supports the following operations:
-
Creating application deployment descriptions
-
Modifying application deployment descriptions
-
Deleting application deployment descriptions
-
Provisioning applications on hosts
-
Provisioning a multitier application
-
Deploying check-point software on hosts
-
Removing applications from hosts
-
Removing a multitier application
-
Rolling back to previous version of applications
-
Deploying query applications on hosts
Management Service
Management service consists of platform management and application management services.
Platform Management
The platform management service enables monitoring and management of the Sun OTP compute elements. This service includes monitoring and managing bare metal hardware and deployed operating system instances. The platform management service can manage both stand-alone systems and two or more systems grouped together into an administrative group.
Application Management
The application management service enables management of NEP applications. Supported operations include application health monitoring, failure recovery, and migration from one Sun OTP instance to another.
Availability Service
The availability service consists of platform availability and application availability services.
Platform Availability
The platform availability service enables availability of the Sun OTP compute elements.
Application Availability
The application availability service enables basic lifecycle and availability management of NEP applications. Supported lifecycle operations include application registration, activation, quiescence, and deactivation.
The following operations are supported by the application lifecycle and availability management services:
-
Creating application manifests
-
Modifying application manifests
-
Deleting application manifests
-
Creating application dependencies
-
Modifying application dependencies
-
Deleting application dependencies
-
Registering applications
-
Starting applications
-
Stopping applications
-
Querying application state
-
Migrating applications from host A to host B
-
Restarting applications on host X
-
Fail over applications from host A to host B
Security Service
The security service is used to secure NEP applications by authenticating Web interface through a SSO feature. Once you log in to a web-based administration interface in Sun OTP, you can access the other web-based administration interfaces without any reauthentication. Additionally, you can use the Solaris Security Toolkit (SST) driver to harden the Sun OTP application hosting environment (AHE) to improve the overall network security.
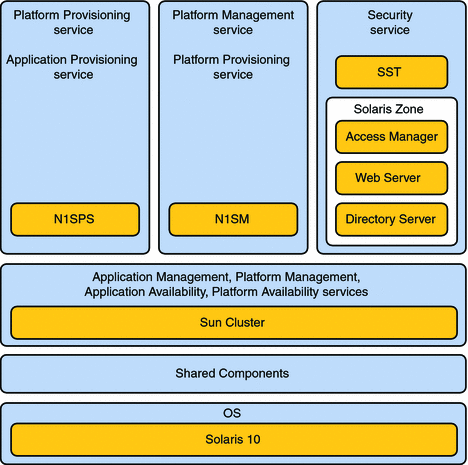
Component Product Mapping
The following figure shows the components that are a part of Sun OTP 2.0.
Figure 1 Component Product Mapping
Supported Versions
The following operating system and component versions are supported by Sun OTP 2.0.
Table 2 Supported Versions|
Operating System and Components |
Version |
|---|---|
|
SolarisOS |
10 Update 3 |
|
Sun Cluster Runtime Environment |
3.2 |
|
Sun N1TM Service Provisioning System |
5.2.4 |
|
Sun N1 System Manager |
1.3.3 |
|
Operating System Provisioning Plug-in |
3.2 |
|
Sun JavaTM System Web Server |
7.0 Update 1 |
|
Sun Java System Directory Server |
6.1 Enterprise Edition |
|
Sun Java System Access Manager |
7.1 |
|
Solaris Security Toolkit |
4.2 |
Known Issues and Bugs
This section describes the known issues in the Sun OTP 2.0 release.
Sun OTP Installation Fails When Sun OTP System Management Service Attempts to Install (6587478)
When you install the Sun OTP system management service using -installManagement of the deployOTP script or the Graphical User Interface (GUI), you might get the following error message:
postgres is already in use
Workaround:
Apply this workaround before running -installManagement in the silent installation or run Step 5 Install System Management Service in the GUI installation.
-
Open the /etc/nsswitch.conf file.
-
Remove all the entries in the file except the files entry from passwd and group lines.
-
Rerun the Install System Management plan.
# /opt/SUNWotp/cli/deploy_otp --installManagement --file /export/input_otp.dat
jesHANodeList Variable Value Should Have the Correct Syntax (6582146)
When you prepare the Sun OTP host plan worksheet, ensure that the syntax of the jesHANodeList variable is h1_hostName:h1_zoneName+h2_hostName:h2_zoneName. Otherwise, you might get the following error message during installation:
No primary node could be found for resource group
nodeType Variable Has to be Set Correctly (6588817)
While creating and configuring the non-global zone, ensure that the value of the nodeType variable is correct and the same as for the global zone of the respective cluster node. The values of the nodeType variable can be single, first, or additional.
Sun OTP Shared Filesystem /var/js Does Not Have an /etc/vfstab Entry (6616595)
The Network File System (NFS) High Availability agent logs a message to the /var/adm/messages file when the exported directory does not reside on a shared storage. This applies to a single-node deployment scenario of Sun OTP.
The following message is displayed:
WARNING: Share path /var/js may be on a root file system or any file system that does not have an /etc/vfstab entry.
This message can be safely ignored.
Invalidate Sun OTP Security Service Session in Web SSO Does Not End the Sun OTP System Management Service Session (6579392)
When you invalidate the Sun OTP security service in Web SSO, the Sun OTP application provisioning service session ends. However, the Sun OTP system management service session does not end.
Web SSO Might Not Work if Old Cookies Are Stored in the Browser (6629927)
Web SSO feature might not work correctly if old cookies are stored in the browser.
Workarounds:
Use any one of the following methods:
-
Stop and restart all the instances of the browser. This process clears all the nonpersistent cookies.
-
Log out and log in to the Web SSO.
-
Remove all the cookies stored in the web browser.
Deleted Web SSO User Cannot be Added Again (6629420)
You cannot add a new Web SSO user with the same name of a deleted Web SSO user. The following error message is displayed in the /var/OTP/SUNWotp.log file.
FATAL: Failed to execute /var/otp/spsotp/N1_Service_Provisioning_System_5.2//cli/bin/cr_cli -cmd udb.u.add -nu sso111 -np
***** -ng NM:admin exp:/var/tmp/aaakKaGo5 2>&1" - error code 1 !
FATAL: Command Output:A user with that username already exists. (015110)
Workarounds:
Use any one of the following methods:
-
Do not delete users which might be recreated in the future. Instead set such passwords of these users, which are difficult to guess.
-
Use a different user name for the new user.
N1SPS Restore Plan Does Not Enable Multiple Simultaneous Restore Operations (6610453)
Check if the security service is running on a node before attempting to run the Backup and Restore plans.
Workaround:
Using the GUI, make the following changes in the Restore plan:
-
Add options to restore N1SPS, N1SM, or the security service to make the security service consistent with the GUI of the Backup plan.
-
Provide the name of the backup directory as an input for the Restore plan. The backup directory is the directory used in the Backup plan. This directory should be consistent across all nodes. You do not need to type different file names for different nodes.
Note –
You cannot run the Restore plan in multiple nodes simultaneously as different nodes cannot stop or start the Resource Group system at the same time.
lucreate Tries to Access and Verify Nonaccessible Slices (6625672)
The operating system upgrade plan fails if an inaccessible slice is included in the /etc/vfstab file.
Workaround:
Remove or comment out the nonaccessible slices from the /etc/vfstab file.
otp-eng-s13:/opt/SUNWotp# grep c0t1d0s6 /etc/vfstab #/dev/dsk/c0t1d0s6 /dev/rdsk/c0t1d0s6 /otp1.1 ufs 3 yes - otp-eng-s13:/opt/SUNWotp#
Self-Contained Installation Server Fails (6622214)
Self-contained installation server fails after the zone installation step.
Workaround:
Due to N1 SPS limitations, you can only use the files and DNS naming service for the Sun OTP provisioning server. If your deployment depends on NIS or NIS+ for resolving names, add the logicalhostname/logicalip mapping to the /etc/hosts file.
SPS Running on a Cluster Node Cannot be Used to Change Web SSO User Password (6629114)
This configuration is not supported. If the system is installed from a Sun OTP provisioning server or from a SPS that resides on a different cluster, the SPS on the installed cluster does not contain any information about the installed components. Therefore, no Web SSO plans can be invoked from the SPS on the newly installed cluster.
Restoring the High Availability Functionality Is Not Available (6633849)
This feature is not supported. You can back up a Sun OTP cluster configuration, but cannot restore it.
During the Execution of Web SSO Install Plan, the Primary Node Fails Due to Lack of Available Swap Space on the System (6634367)
Workaround:
Do not cancel the SPS plans while deploying Sun OTP using N1SPS BUI. This feature is not supported SPS version 5.2.4
Setup Configuration Plan Does not Update the otp.reg File (6640598)
You can change the type of the node, that is, single, first, or additional, only if no other plan apart from the Setup Configuration plan is executed. Changing the node in the later stages is not supported.
Workaround:
-
Modify the following N1SPS variable:
-
hostType for a GUI installation
-
hx_hostType in the .dat file for a CLI installation
-
-
Log in to the server where you need to change the node type.
-
Remove the line starting with NODE_TYPE= from the /var/OTP/otp.reg file.
-
Rerun the Setup Configuration plan.
Deletion of the N1SPS OTP Plug-in Requires the Deletion of all Hosts (6458703)
While running the plan to configure the first node of the cluster, deletion of N1SPS OTP plug-in fails after reboot due to cluster configuration, and fails to run n1smconfig.
Workaround:
Before deleting the N1SPS OTP plug-in, delete all the hosts that use the plug-in. Otherwise, the plug-in deletion fails.
To delete a plug-in, do the following:
-
Delete all the host that used the N1SPS OTP plug-in.
-
Delete the N1SPS OTP plug-in.
Single Node Installation Fails if a Shared Volume /var/js is Created (6579762)
Workaround:
For a single node installation, do not create a shared volume /var/js for N1SM. The installation fails if you create a shared volume.
N1SM create os and SPS import os Plans Cannot be Run Simultaneously (6531142)
You cannot run the create os and import os plans simultaneously.
Workaround:
Run these commands in a sequence.
Web SSO Installation Fails After the Successful Execution of the Install Web SSO Plan (6642359)
Workaround:
Monitor the /var/OTP/SUNWotp-debug.log file to check whether the resource group otp-system-rg has been restarted. If the resource group has not been restarted, restart the resource group manually by typing the following command on any node of the cluster:
/usr/cluster/bin/clrg online otp-system-rg
SPS Patch Installation Failure Is not Detected in Sun OTP (6611833)
Workaround:
Install the correct versions of the patches.
-
For SPARC:
Type the following command:
cd $sparc_mediapath/Products/Patches
./OTP_patch_install -R /var/js -A sparc -L /var/tmp/OTPInstaller.log n1sps
-
For x86:
Type the following command:
cd $x86_mediapath/Products/Patches
./OTP_patch_install -R /var/js -A x86 -L /var/tmp/OTPInstaller.log n1sps
Sun OTP Registry Cannot be Backed up Separately (6633845)
You can back up the Sun OTP registry as part of the Backup All plan. This module cannot be backed up separately.
Sun OTP 2.0 Ports are Not Configurable (6564838)
You cannot install Sun OTP version 2.0 if the Sun OTP ports are already being used by other applications.
You Cannot Include metadb Using lucreate (6625690)
You cannot use the lucreate command to include metadb.
Workaround:
After rebooting in to the boot environment, which has the updated operating system and Sun Cluster, apply following steps:
metadb -a -c 6 new_metadb_slice
metadb -d old_metadb_slice
Enable High Availability Service Plan Fails with Error Configuring Access Manager(6641978)
The openssl command timeout could result in potential failure of a running SPS plan during deployment
Workaround:
-
Modify the /var/OTP/otp.reg file located in the relevant zone.
Change COMP|ACCESSMANAGER|STATUS=Failed to the following:
COMP|ACCESSMANAGER|STATUS=Configured
-
Stop all the running Web Server instances by typing the following command:
/opt/SUNWotp/framework/webserver/jes_ws.pl --run stopInstance
-
Rerun the configure High Availability plan.
Access Manager CLI amadmin Throws an Authentication Error (6547158)
After the security services installation, Access Manager CLI amadmin fails with authentication login exceptions.
Workaround:
-
Log in to Access Manager at https://VIP:3224.
The user name and password are the values you specified during the Sun OTP installation. For example, user name can be otpadmin and password can be admin.
-
Select Realm—>Domain—>Authentication tab—>Advanced Properties in the Access Control tab.
-
Uncheck Agent under Identity type and click save config.
-
Disable the Access manager services on the node where changes were made for a multinode deployment.
# /usr/cluster/bin/clrg set -p RG_System=false otp-security-rg
# /usr/cluster/bin/clrs disable -n <node:zone_name> otp-ws-rs
-
Re-log in to at https://VIP:3224. Note that this time the URL will point to other Access Manager instance. Repeat steps 3 and 4.
-
Enable the Access manager services on all nodes.
# /usr/cluster/bin/clrs enable -n <node:zone_name> otp-ws-rs
# /usr/cluster/bin/clrg set -p RG_System=true otp-security-rg
SPS Plans for the Config Audit tool Does Not Work as Expected (6658672)
Before running the Config Audit tool, the Explorer should be run once. This is to get the Explorer ID as one of the parameters for running the Config Audit tool. But the requirement for Config Audit is to have the latest explorer ID after installing the config audit packages. This requires the user to run the Config Audit tool twice.
The otpadmin User for WebSSO Does Not Have All Privileges Required for Sun Cluster Administration (6660124)
After WebSSO is enabled, if a otpadmin user logs in to the Sun Cluster web console on port 6789, it is seen that the otpadmin user does not have privileges for enabling or disabling the resources and resource groups, changing properties and performing other administration tasks.
Workaround:
On the OTP system(s), do the following:
-
Open the /etc/user_attr file.
-
Replicate the entry for root in the file and replace root with otpadmin in the new entry.
-
Save the file.
-
Log out and log in using WebSSO.
The various options are now enabled on the Sun Cluster web console.
Sun Welcomes Your Comments
Sun is interested in improving its documentation and welcomes your comments and suggestions. To share your comments, go to http://docs.sun.com/ and click Send Comments. In the online form, provide the full document title and part number. The part number is located on the book's title page and in the document's URL. For example, the name of this book is Sun Open Telecommunications Platform 2.0 Release Notes and the part number of this book is 820-2325.
- © 2010, Oracle Corporation and/or its affiliates
