| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Identity Synchronization for Windows 6.0 Deployment Planning Guide |
| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Identity Synchronization for Windows 6.0 Deployment Planning Guide |
2. Case Study: Deploying in a Multimaster Replication Environment
Example Bank Deployment Information
Example Bank's Existing Architecture
Example Bank's Technical Requirements
Identity Synchronization for Windows Features in This Case Study
Creating a Special Active Directory User for Identity Synchronization for Windows
To Assign Administration Rights to the Special User
Configuring the Identity Synchronization for Windows Core
Configuring the Sun Java System Directory Server Source
Configuring the Active Directory Source
To Specify Information in the Global Catalog and for the Active Directory Domain
Configuring the Windows NT Source
To Specify the Windows NT Domain
Configuring the Synchronization Settings
Configuring the Attributes Settings
Configuring the Attribute Modification Settings
Configuring the Object Creation Settings
Configuring the Group Synchronization Settings
Configuring the Account Lockout Synchronization Settings
Adding the shadowAccount Object Class
Configuring the Creation Attributes
To Configure the Creation Attributes
Configuring the Synchronization User Lists
Resolving Issues With Multiple SULs
Installing the Connectors and Directory Server Plug-Ins
Running the Resynchronization Procedure When Directory Server Is Authoritative
Configuration and Installation Summary
Migrating Users From Windows NT to Active Directory
Unlinking Migrated Windows NT Entries
Linking Migrated Active Directory Entries
Moving Users Between Active Directory Organizational Units
When Contractors Become Full-Time Employees
3. Case Study: Deploying in a High-Availability Environment Over a Wide Area Network Using SSL
A. Pluggable Authentication Modules
B. Identity Manager and Identity Synchronization for Windows Cohabitation
This section describes the architecture and technical requirements of Example Bank, the company in this case study. It also lists the Identity Synchronization for Windows features that are used in this case study.
Example Bank’s infrastructure includes a Windows NT domain (EXBANK), an Active Directory domain (eb.com) with two domain controllers, and a two-way MMR Sun Java System Directory Server (dc=eb,dc=com) deployment. Example Bank has two main sites: one located in New York City and one in Los Angeles.
The following figure describes Example Bank’s deployment of its directory resources.
Figure 2-1 Example Bank Architecture
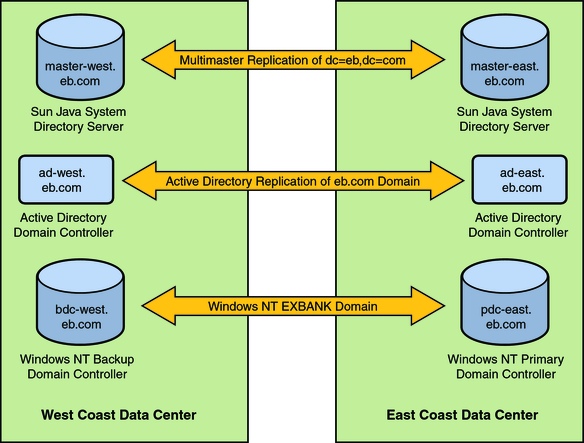
Sun Java System Directory Server is the corporate directory server that is used to control access to all web-based applications. Pluggable Authentication Module (PAM) for LDAP authenticates and manages passwords on the Solaris Operating System (Solaris OS) against Directory Server passwords. The two preferred Directory Servers manage a single root suffix, dc=eb,dc=com, and all users are stored in the ou=people,dc=eb,dc=com container with uid as the naming attribute. The directory servers, installed on Solaris systems, are running on separate machines: master-east.eb.com and master-west.eb.com.
The single Windows NT domain is called EXBANK. The Primary Domain Controller (PDC) runs on a pdc-east.eb.com machine in New York City. A backup domain controller (bdc-west.eb.com) runs on a machine located in Los Angles. All Windows NT user accounts have a Directory Server account with the exception of the built-in Windows NT accounts. The Windows NT USER_NAME attribute is the same as the Directory Server uid attribute.
The Active Directory deployment has a single domain, eb.com, with two domain controllers:
ad-east.eb.com (in New York City)
ad-west.eb.com (in Los Angeles)
In this deployment, ad-west.eb.com is the PDC Flexible Single-Master Operation (FSMO) role owner.
Users are stored in two separate organizations corresponding to the two sites:
ou=east,dc=example,dc=com
ou=west,dc=example,dc=com
Example Bank is in the process of migrating users from Windows NT to Active Directory. Each employee has a Windows NT or Active Directory account. The migration of the users is based (in phases) on the employees’ last names. Every week Example Bank moves users whose last name begins with the next letter of the alphabet. Currently, the company has migrated employees whose last names begin with letters A through F.
For users who have Directory Server accounts, the Active Directory samaccountname attribute stores the uid. When a user account is migrated from Windows NT, the user keeps the same login. That is, the Active Directory samaccountname attribute of the new user is the same as the Windows NT USER_NAME attribute.
The following table describes Example Bank’s technical requirements.
Table 2-1 Technical Requirements for Example Bank
|
The following Identity Synchronization for Windows features are used in this case study:
Synchronizing with multiple Windows domains
Synchronizing in a two-way MMR environment
Integration with PAM LDAP
Migrating users between Windows domains, (from Windows NT to Active Directory)
Synchronizing a hierarchical directory information tree (DIT) with a flat DIT
Creating attribute default values
Failover support across multiple preferred Directory Servers in a replicated environment
Account lockout synchronization
Static group synchronization