| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Identity Synchronization for Windows 6.0 Deployment Planning Guide |
| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Identity Synchronization for Windows 6.0 Deployment Planning Guide |
2. Case Study: Deploying in a Multimaster Replication Environment
3. Case Study: Deploying in a High-Availability Environment Over a Wide Area Network Using SSL
A. Pluggable Authentication Modules
Configuring PAM and Identity Synchronization for Windows
Step 1: Configure an LDAP Repository for PAM
Step 2: Configuring Identity Synchronization for Windows
Step 3: Populating the LDAP Repository
Step 4: Configuring a Solaris Host to Use PAM
Installing and Configuring a Solaris Test System
Configuring the Client Machine
Specifying Rules for Authentication and Password Management
Step 5: Verifying that PAM is Interoperating with the LDAP Store
Step 6: Demonstrating that User Changes are Flowing to the Reciprocal Environment
Configuring Systems to Prevent Eavesdropping
Introducing Windows NT into the configuration
B. Identity Manager and Identity Synchronization for Windows Cohabitation
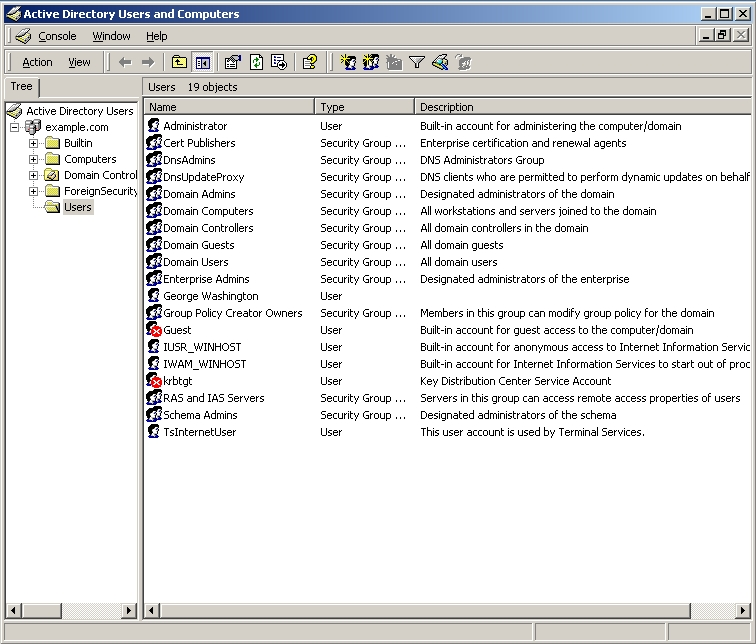
When the George Washington Properties dialog box is displayed, check the Account options section and you can see that the User must change password at next logon check box is enabled, which means George Washington will be required to change his password the next time he logs on.
This is first time the user has logged on (since being created over protocol), so supplying an old password value will cause an error message and Windows will ask you to enter the new password again.
If Windows accepts the new password, a message is displayed stating that the new password has been accepted.
At this point, George Washington's entry has moved from Case 3 (where the Windows entry is stale and the LDAP store is current) to Case 2 (where Windows is current and the LDAP store entry is stale).
George Washington's entry will maintain this condition until the next time he binds to the LDAP store. At that time, the entry will move to the Case 1 (where the entry is current on both Windows and the LDAP store).