This section contains an example of how to implement account security. Use this example to form an intuitive understanding of these objects. Once this intuition is obtained, you'll be ready to design the account security objects for your own company.
Securing Accounts Based On Account Type
Assume the following security requirement exists:
-
You have two broad groups of accounts:
-
Unrestricted Taxpayer accounts for the general public.
-
Restricted Taxpayer accounts for individuals whose tax information is highly sensitive (politicians, celebrities, employees of the tax authority, etc.).
-
Users can be classified as have one of the following access rights:
-
May access all accounts.
-
May only access the Unrestricted Taxpayer accounts.
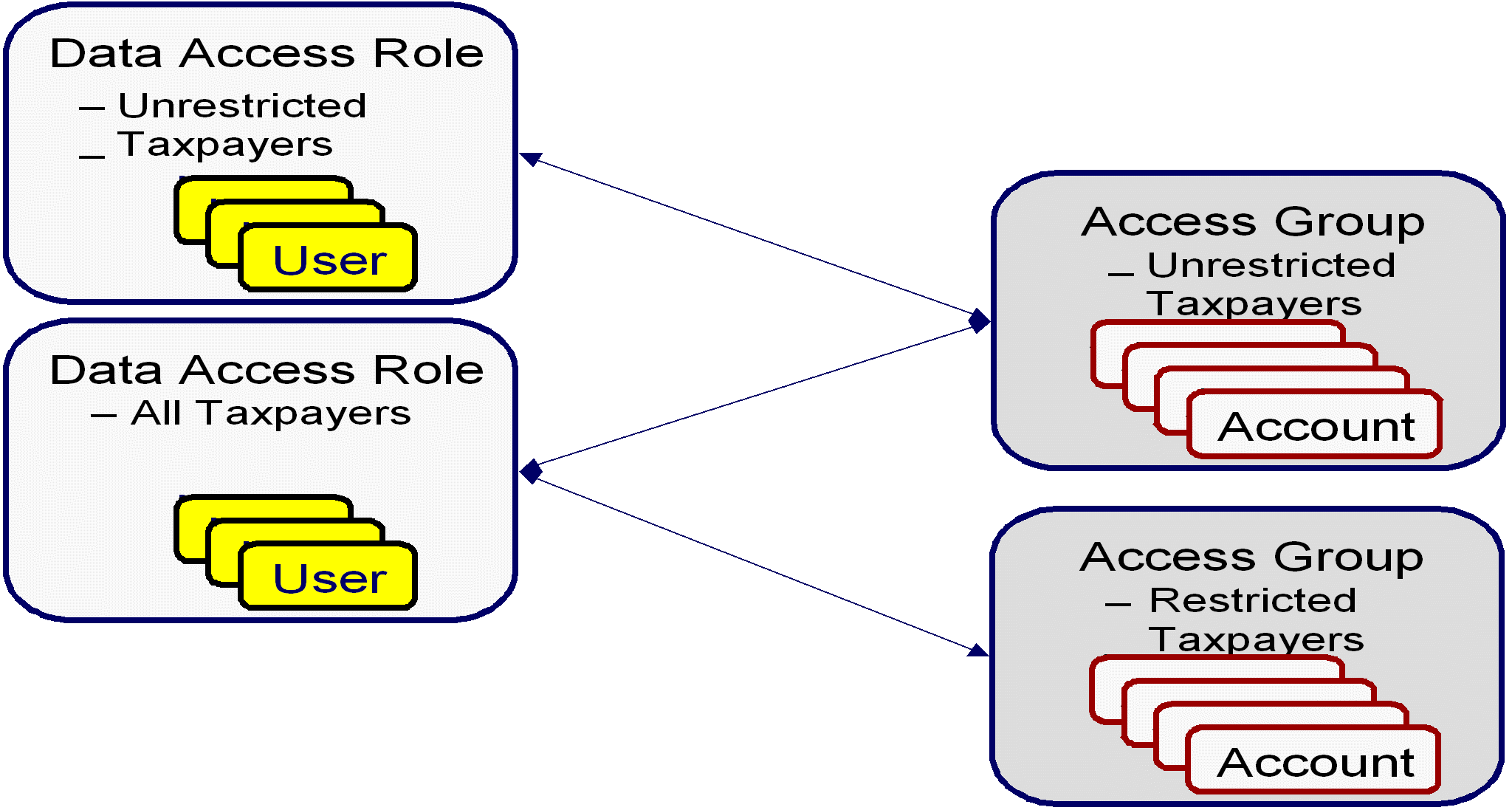
The following diagram illustrates the access groups and data access roles required to implement these requirements:
Notice the following about the above:
-
There are two access groups because access to accounts is based on whether the taxpayer's account is unrestricted or restricted.
-
The Unrestricted Taxpayers data access role is only linked to the Unrestricted Taxpayers access group.
-
The All Taxpayers data access role is linked to both the Unrestricted Taxpayers and Restricted Taxpayers access groups. Users with this role can therefore access all accounts.