| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Solaris Administration: Network Interfaces and Network Virtualization Oracle Solaris 11 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
|
Oracle Solaris Administration: Network Interfaces and Network Virtualization Oracle Solaris 11 Information Library |
1. Overview of the Networking Stack
Network Configuration in This Oracle Solaris Release
The Network Stack in Oracle Solaris
Network Devices and Datalink Names
Administration of Other Link Types
3. NWAM Configuration and Administration (Overview)
4. NWAM Profile Configuration (Tasks)
5. NWAM Profile Administration (Tasks)
6. About the NWAM Graphical User Interface
Part II Datalink and Interface Configuration
7. Using Datalink and Interface Configuration Commands on Profiles
8. Datalink Configuration and Administration
9. Configuring an IP Interface
10. Configuring Wireless Interface Communications on Oracle Solaris
12. Administering Link Aggregations
16. Exchanging Network Connectivity Information With LLDP
Part III Network Virtualization and Resource Management
17. Introducing Network Virtualization and Resource Control (Overview)
Network Virtualization and Virtual Networks
Parts of the Internal Virtual Network
How Bandwidth Management and Flow Control Works
Allocating Resource Control and Bandwidth Management on a Network
Who Should Implement Resource Control Features
Observability Features for Network Virtualization and Resource Control
18. Planning for Network Virtualization and Resource Control
19. Configuring Virtual Networks (Tasks)
20. Using Link Protection in Virtualized Environments
21. Managing Network Resources
Network virtualization is the process of combining hardware network resources and software network resources into a single administrative unit. The goal of network virtualization is to provide systems and users with efficient, controlled, and secure sharing of the networking resources.
The end product of network virtualization is the virtual network. Virtual networks are classified into two broad types, external and internal. External virtual networks consist of several local networks that are administered by software as a single entity. The building blocks of classic external virtual networks are switch hardware and VLAN software technology. Examples of external virtual networks include large corporate networks and data centers.
An internal virtual network consists of one system using virtual machines or zones that are configured over at least one pseudo-network interface. These containers can communicate with each other as though on the same local network, providing a virtual network on a single host. The building blocks of the virtual network are virtual network interface cards or virtual NICs (VNICs) and virtual switches. Oracle Solaris network virtualization provides the internal virtual network solution.
You can combine networking resources to configure both internal and external virtual networks. For example, you can configure individual systems with internal virtual networks onto LANs that are part of a large, external virtual network. The network configurations that are described in this part include examples of combined internal and external virtual networks.
An internal virtual network built on Oracle Solaris contains the following parts:
At least one network interface card, or NIC.
A virtual NIC, or VNIC, which is configured on top of the network interface
A virtual switch, which is configured at the same time as the first VNIC on the interface.
A container, such as a zone or virtual machine , which is configured on top of the VNIC.
The next figure shows these parts and how they fit together on a single system.
Figure 17-1 VNIC Configuration for a Single Interface
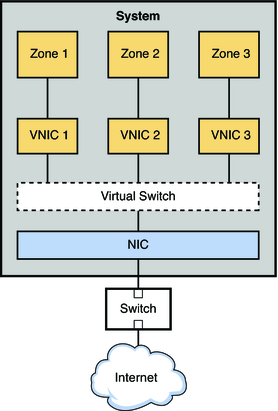
The figure shows a single system with one NIC. The NIC is configured with three VNICs. Each VNIC supports a single zone. Therefore, Zone 1, Zone 2, and Zone 3 are configured over VNIC 1, VNIC 2, and VNIC 3, respectfully. The three VNICs are virtually connected to one virtual switch. This switch provides the connection between the VNICs and the physical NIC upon which the VNICs are built. The physical interface provides the system with its external network connection.
Alternatively, you can create a virtual network based on the etherstub. Etherstubs are purely software and do not require a network interface as the basis for the virtual network.
A VNIC is a virtual network device with the same datalink interface as a physical interface. You configure VNICs on top of a physical interface. For the current list of physical interfaces that support VNICs, refer to the Network Virtualization and Resource Control FAQ. You can configure up to 900 VNICs on a single physical interface. When VNICs are configured, they behave like physical NICs. In addition, the system's resources treat VNICs as if they were physical NICs.
Each VNIC is implicitly connected to a virtual switch that corresponds to the physical interface. The virtual switch provides the same connectivity between VNICs on a virtual network that switch hardware provides for the systems connected to a switch's ports.
In accordance with Ethernet design, if a switch port receives an outgoing packet from the host connected to that port, that packet cannot go to a destination on the same port. This design is a drawback for systems that are configured with zones or virtual machines. Without network virtualization, outgoing packets from a virtual machine or a zone with an exclusive stack cannot be passed to another virtual machine or zone on the same system. The outgoing packets go through a switch port out onto the external network. The incoming packets cannot reach their destination zone or virtual machine because the packets cannot return through the same port as they were sent. Therefore, when virtual machines and zones on the same system need to communicate, a data path between the containers must open on the local machine. Virtual switches provide these containers with the method to pass packets.
Figure 17-1 illustrates a simple VNIC configuration for a virtual network on a single system.
When the virtual network is configured, a zone sends traffic to an external host in the same fashion as a system without a virtual network. Traffic flows from the zone, through the VNIC to the virtual switch, and then to the physical interface, which sends the data out onto the network.
But what happens if one zone on a virtual network wants to send packets to another zone on the virtual network, given the previously mentioned Ethernet restrictions? As shown in Figure 17-1, suppose Zone 1 needs to send traffic to Zone 3? In this case packets pass from Zone 1 through its dedicated VNIC 1. The traffic then flows through the virtual switch to VNIC 3. VNIC 3 then passes the traffic to Zone 3. The traffic never leaves the system, and therefore never violates the Ethernet restrictions.
If you need to consolidate resources on Oracle's Sun servers, consider implementing VNICs and virtual networks. Consolidators at ISPs, telecommunications companies, and large financial institutions can use the following network virtualization features to improve the performance of their servers and networks.
NIC hardware, including the powerful new interfaces that support hardware rings
Multiple MAC addresses for the VNICs
The large amount of bandwidth provided by newer interfaces
You can replace many systems with a single system that implements running multiple zones or virtual machines, without significantly losing separation, security, and flexibility.