31 FAQ/Troubleshooting
This chapter answers common OAAM questions and describes common troubleshooting issues and tips to resolve them.
31.1 Techniques for Solving Complex Problems
This section describe a process to enable you to more easily solve a complex problem. It contains the following topics:
31.1.1 Simple Techniques
You can work your way through some simple troubleshooting techniques to try to solve a problem.
| Steps | Description |
|---|---|
| Experience | You have seen this problem before or it is simply something you know the answer to. |
| Post to the Forum | This is not the first step. Only valid once basics have been applied and a second opinion is needed. Appropriate during rigorous analysis, but not before. |
| Intuitive leap (or guess) | The problem just inspires a guess at a cause. You have a feel for the problem or rather its cause. This can be very effective and result in a quick resolution, but without proper confirmation, it often leads to the symptom being fixed and not the real cause being resolved. |
| Review basic diagnostics | Check the logs for errors and the flow. Check flow (HTTP headers, network packet trace, SQL trace, strace). Run through and document the flow. Cross check with configuration details to ensure flow is expected. |
| Read the error message | Reading the error and the flow information will give a big clue. Taken together with some knowledge of the way the component works, this can give a lot of insight. Always check knowledge (Oracle and search engine) for matches. Perform any diagnostics needed to establish if the error is key. With multiple errors, look to see which is likely the cause and which are just consequences. |
| Compare | Compare the logs and flows with a working system. Perform a test case. If it happens only at a certain site, then compare the differences. |
| Divide | Break the problem down |
31.1.2 Divide and Conquer
Steps to reduce the problem to a manageable issue are listed in this section.
| Process | Description |
|---|---|
| Simplify the problem | Make a problem as simple as possible. |
| Remove components that are not needed | Most problems involve complex components and connections between them. Most involve third party components. So where ever possible, eliminate third party components first and then as many components and custom components as possible (for example, command line not application, SQLPLUS is not an application.)? |
| Reduce complexity | Test to see if a simpler version of the problem exists with the same symptoms. (for example, remove components of a complex Select, or a search filter, check if a single request or few requests will suffice)?. |
| Like fixing an underground pipe with a leak | Imagine a complex configuration as being a underground hose pipe with a leak. You know something is wrong, there is a leak someplace, but not where it is. |
| List the components | Draw a box for each components and a line where it is connected to the next. Note the protocols used to join them. |
| Check both ends | What goes in should come out the same. If you see data in and out results in a problem then it is one of the ends that is wrong. If the flow is not as expected the problem is in between. |
| Lazy Y | Test points in the configuration to find where the deviation occurs. Once established (beyond doubt) that a piece of the configuration behaves as expected it can be ignored. |
| Repeat | Repeat this loop to close in on the problem |
| Help | When 3rd party components are involved in the issue, get help from the others and work on the issue together. |
31.1.3 Rigorous Analysis
All or part of the process should be applied if:
-
a problem is complex
-
a problem is highly escalated
-
a problem was not solved with the first attempts
-
a problem is getting out of control
-
a problem has potential for getting out of control
31.1.4 Process Flow of Analysis
The process flow of analysis is presented below:
-
State the problem.
-
Specify the problem.
Develop possible causes from:
-
Knowledge and experience
-
Distinctions and changes
-
-
Test possible causes against the specification.
-
Determine most probable cause.
-
Verify the solution.
31.1.4.1 State the Problem
Stating the problem is the most important step to solving the issue.
| Step | Description |
|---|---|
| Ensure a clear and concise problem statement | Stating the problem is the most important step. It is the most commonly ignored or at least the problem statement is assumed. It is pointless trying to solve a problem until the problem statement is stated. Otherwise what are you actually trying to fix? If you do not know what it is you are fixing how can you fix it? |
| Consider if the problem stated can be explained | If so, then it is not the problem statement --If the problem statement can be explained then back up and try and get a more correct problem statement. This is a case to start communicating if you are helping someone solve his problem. Either ask some direct questions to narrow down the issue or just pick up the telephone and talk to the person to clarify the real issue. If there are lots of issues then start noting them down as separate issues. |
| Do not settle for a vague statement | Vague problem statements, like "bad performance", "something crashes" are of no use and commonly are the cause for issues to be long running and out of control. |
| Never combine problems in a single statement | Ensure there is only one problem being dealt with. Do not accept combined problems. The combined problem is either multiple distinct problems or some of the problems are actually symptoms. |
31.1.4.2 Specify the Problem
Describe problems in detail and ask focused questions to gather pertinent information.
| Step | Description |
|---|---|
| Specify the problem | These are symptoms of the problem. |
| Start by asking questions | Ask questions such as What, Where, When, and to what Extent? |
| What? | What tends to be the obvious question and is mostly a list of facts and symptoms; what deviated from the expectation? |
| Where? | Where may or may not be relevant, but is worth asking as it is often significant and often overlooked. |
| When | When is very important as time lines helps identify patterns and establish what change triggered the problem. |
| Extent | Extent or how many is particularly useful in establishing probable causes. If it is all the systems for example then check if it affects all systems or try a testcase. How often is also important. Once a week is quite different from many times every second and tells us much about the type of issue to look for. |
| List the symptoms and facts | List the symptoms and facts and how they are significant |
| What changed? | Something changed that is certain unless the problem has always been there. This is a special case. |
| Assumptions | Verify the data provided and check for conflicts and contradictions.
Always check for any assumptions. Be careful to identify any information that is not verified and thus is only assumed. In fact this is particularly a mistake made by analysts that have more technical experience. Though also occurs a lot when inexperienced analysts are given details from people they perceive as having more knowledge. However trivial an assumption seems, always look for proof and confirmation. |
31.1.4.3 What It Never Worked
If the component did not work before, performing these steps:
| Considerations | Description |
|---|---|
| Consider behavior and expectation if performance issue | For cases when the issue is about something that never worked correctly the first issue is to establish what correct behavior really is and if it is reasonable? This also allows us to set proper expectations from the outset. This is especially true for performance issues. |
| Confirm that there is no misunderstanding | Establish that the requirement is reasonable. |
| Do not compare Apples with Oranges | Agree on a specific goal. Focus on that issue only. |
| Consider all components involved | Consider all components involved:
|
| Consider if the solutions is just to change perception | What can you see that causes you to think there's a problem?
|
31.1.4.4 IS and IS NOT but COULD BE
Consider what the problem is, what it isn't, and what it could be.
| Step | Description |
|---|---|
| IS and IS NOT but COULD BE | For every fact or symptom ask this question: IS and IS NOT but COULD BE |
| Provide comparison | A test case often is the key to establishing something to compare the problem with.
If it reproduces the issue then it does not help the problem analysis as such, but it is extremely useful when passing the problem to the next team to work on the fix. It also allows quicker testing of potential fixes and solutions (workarounds), not to mention you would be gaining experience. |
| If there is no comparison, create a test case | If it does not reproduce then it provides something to compare the problem system with and perhaps even a possible work around. |
31.1.4.5 Develop Possible Causes
Problem solving involves developing possible causes.
| Development | Description |
|---|---|
| Knowledge and experience | You can use your knowledge and experience to recognize possible causes
|
| Distinctions and changes | You can make a list of distinctions and changes to narrow down causes:
|
| Examine each of the symptoms and comparisons | Consider each of the facts and ensure that they are relevant and that they are not conflicting |
31.1.4.6 Test Each Candidate Cause Against the Specification
Test each candidate cause against the specification:
-
Each possible cause must fit all the items in the specification
-
If you end up with no causes then go back and refine the process
-
Causes must explain both the IS and the IS not but COULD be
-
Determine the most probable cause
-
Do not discount any causes that fit
31.1.4.7 Confirm the Cause
Confirm the cause so that you can devise an action plan.
You can:
-
Devise ways to test the possible causes
-
Observe
-
Test assumptions
-
Experiment
-
Test solution and monitor
The main point here is to devise action plans to prove or disprove the theories. It is important to communicate the reason for each action plan. Especially when asking for a negative test, i.e. a test that is to prove something is not true. People might assume all action plans are attempts to solve the problem and resist any thing they think is not directed in the direction.
31.1.4.8 Failures
When one solution fails, just start back at the beginning and apply the approach once again, updated with the new results. Really complex problems will often take several iterations.
The process is not infallible.
Main causes of failure are:
-
Poor or incorrect problem statement
-
Inaccurate or vague information
-
Missing the key distinctions in IS vs. IS NOT
-
Allowing assumptions to distort judgment
-
Not involving a broader set of skills
31.2 Troubleshooting Tools
This section contains information about tools and processes you can use to investigate and troubleshoot issues with your system.
Table 31-1 lists the general and OAAM-specific tools you can use for troubleshooting problems.
Table 31-1 Troubleshooting Tools
| Category | Description |
|---|---|
|
General Tools |
|
|
OAAM Specific Tools |
|
Table 31-2 provides items to check for when troubleshooting the system.
Table 31-2 Troubleshooting Tips
| Tips | Reason |
|---|---|
|
Check the operating system |
Some issues may be platform specific. For example, Java keystores created on non-IBM platforms will not work on IBM platforms |
|
Check WebLogic Server version |
Make sure OAAM is installed on a WebLogic server certified for 11g |
|
Check the JDK (Sun or JRockit) |
Make sure the JDK is certified for the Identity Management 11g Suite |
|
Change logging configuration through Enterprise Manager |
Make sure the log level is changed appropriately before tracing and debugging |
|
Search for log messages through Enterprise Manager |
Log messages record information you deem useful or important to know about how a script executes. |
|
Use the Execution Context ID to search for log messages |
The ECID is a unique identifier that can be used to correlate individual events as being part of the same request execution flow. |
|
Use the WebLogic Console to monitor database connection pool |
Check the health of the connection pool through the WebLogic Console. |
Table 31-3 summarizes problems and the checks you can perform to troubleshoot and solve the problem.
| Problem | Checks You Can Perform |
|---|---|
|
Common Troubleshooting Use Cases |
|
|
Most of the Operations are Slow |
|
|
Server is Throwing Out of Memory Exceptions |
|
|
Connection Pool Errors |
|
|
Errors While Starting the Managed Server After Upgrade |
|
|
OAAM CLI Script Issues |
|
|
SOAP Call Issues |
|
|
Native Integration Issues |
|
31.3 Case Management
Notes in log appear in English
Question/Problem: The notes in the Logs tab appear in English.
Answer/Solution: The values for the Notes column in the Logs tab for notes that are not added by the user will appear in English by default.
The notes are taken from the action enums "note" field (property).The value of that property is saved into database (as notes). After being saved, users cannot change that data.
Implementations can customize the "note" in the enum property to the localized value.
"Access case" is inside the oaam_resources.properties file:
customercare.case.actiontype.enum.accesscase.description=Access case
Case creation / access logic will use that string for the creating records after that point.
31.4 KBA
Why was I challenged with a question I did not register for
Question/Problem: A user states that he was challenged with a question he did not register for. How can this happen?
Answer/Solution: There are a few possible reasons:
-
The user may have forgotten the challenge questions since registration. Often this is because the user has not been challenged for an extended period.
-
The challenge questions may have been reset by another party in a joint account (husband, wife, significant other).
The user's questions should be reset, allowing him to register new challenge questions.
Should I increase the number of questions for user registration?
Question/Problem: How do I decide if I should increase the number of questions for registration?
Answer/Solution: Whether to increase the number of questions depends on the business use case.
If the number of questions is increased to five and the user has three questions registered:
-
If the system is using all five questions, you do not need to ask the user to re-register questions. No change is required in this case. Existing users continue to use their questions until the questions are reset.
-
If all five questions are required, you can have your users register:
-
An additional two questions, which means you must make changes in the policy and add a new rule
-
All five questions, which means you must use a batch job
-
Why is the Question Statistics in the Details Page not displaying the Percentage of Challenges for a Question.
Question/Problem: Why are the statistics not updated for "Percentage of Challenges for a Question" immediately after the user answers a question?
Answer/Solution: The thread which updates the question statistics runs every hour. Updated statistics are not available after a user answers a question. However, the statistics are updated after one hour.
Question/Problem: What is the difference between Off, Low, Medium, High?
Answer/Solution: Answer Logic is a set of advanced matching algorithms used by the system to find out whether the answers provided by the user in the challenge response process match closely to the ones provided during registration. The algorithms and the level of Answer Logic are factors in evaluating answers.
The levels of Answer Logic, the intensity or strength of algorithms, used to evaluate answers are:
-
Off – No Answer Logic is used; answers must exactly match those previously registered by the user.
-
Low – Less Answer Logic; answers provided by the user must be a match or near-match to the answers that were provided at the time of registration
-
Medium – More Answer Logic; the user is given some leeway for the answers that are provided. For example, St. might be accepted for Street.
-
High – Highest level of Answer Logic. The constraints are not strict for matching.
Refer to Section 7.9.3, "Level of Answer Logic."
Decryption of user's registered questions and answers
Question/Problem: Can a customer decrypt a user's registered questions and answers if needed?
Answer/Solution: Decryption of registered questions and answers is not supported for a number reasons. Primarily this is a security concern. If it were supported, it would be possible for an insider to discover the questions and answers for all users. Challenge questions are used to protect applications in times of high risk. These questions in the wrong hands can be used to perpetrate fraud. As well, some KBA answers could contain personally identifiable information which requires a very high level of protection. In addition to security concerns there are privacy concerns as well.
Are KBA answers case-sensitive?
Question/Problem: Are KBA answers case-sensitive?
Answer/Solution: KBA answers are not case-sensitive for usability concerns. Since a user will only be challenged with a challenge question when there is a medium level of threat, most users will not be challenged on a regular basis since most users follow regular patterns while conducting their business. If users are not challenged regularly, they may remember the answers to their challenge questions when and if they receive a challenge but may not remember the exact spelling or capitalization. Because of this, KBA includes the use of fuzzy logic to interpret use answers. Common misspellings and abbreviations, for example, can be accepted if the basic information of the answer is correct. This greatly increases the effectiveness as a solution overall since a challenge question is not useful if a user fails to answer correctly because he forgot to capitalize the name of the street he grew up on.
31.5 Policies, Rules, and Conditions
No results were found after policy execution
Question/Problem: I imported the policy and expected to see the results from the execution, but no results were found. How can I find out what happened?
Answer/Solution: To debug the problem:
-
Check the Session details page to verify if that policy executed in that session.
Make sure that "vcrypt.tracker.rules.trace.policySet.XXXXXX" is set to true for that checkpoint. (XXXX corresponds to that checkpoint)
-
Verify the configuration of the policy.
-
Is the policy active?
-
Is the policy linked to that user group to which this user belongs?
For a policy to execute in a session, it should either be linked to "All Users" or to one of groups the user is member of. Verify whether the policy is linked appropriately.
-
-
Verify that enough time was given for the cache to refresh.
If group linking is changed recently, make sure to wait more than 30 seconds for the cache to refresh.
Alerts and/or action did not generate for a rule
Question/Problem: The policy executed but alerts and actions were not generated.
Answer/Solution: When a rule triggers, the alerts set up in the rule will trigger. However, the action configured in a rule can be overridden in different levels, like trigger combination, policy set override. Look at these for possible override of the action triggered by the rule.
Verify the configuration of actions and alerts.
-
Verify that the alerts and actions have been set up in the rule. Then verify that the rule was indeed triggered in the session.
When a rule triggers, the alerts set up in the rule will trigger. However, the action configured in a rule can be overridden in different levels, like trigger combination, policy set override. Look at these for possible override of the action triggered by the rule.
-
Verify if there are other trigger combinations in the policy that match this specific set of conditions.
Trigger combinations are evaluated in a sequential order, as shown in the user interface, until all conditions match for a combination. After finding a matching combination, the rest of the combinations are not evaluated. It is possible that multiple combinations match for a specific set of conditions; however only the first one to match will trigger. Verify if there are other trigger combinations in the policy that match this specific set of conditions.
31.6 Groups
Action element or action member does not appear in the action group in rules
Question/Problem: An action element was added or an action member, but it does not appear in the action group in rules.
Answer/Solution: For the action to appear, you must restart the server because action members are enumerations.
Unable to delete all the groups
Question/Problem: The user is not able to delete all the groups that were selected for deletion.
Answer/Solution: If a group is used in other instances within the application, the user will not be able to delete the groups
Delete all the members in a group
Question/Problem: What happens if I delete all the members in a group?
Answer/Solution: If the group is linked to any rules or patterns, the rules or patterns will not function as expected.
Difference between a User ID and a User Name group
Question/Problem: What is the difference between a User ID and a User Name group?
Answer/Solution: The user name is set up by the user. For example: "Bob" is the login and the user is "xyz123". The User ID is the scheme a customer uses to uniquely identify users.
Question/Problem: What are groups used for?
Answer/Solution: To simplify the configuration for rule conditions and rule results, groups are created.
For example, to create a rule "Restricted IPs," you must add a condition to find out if the logged in user IP is in the list of restricted IPs configured. The restricted IPs are grouped together as RestrictedIPSGroup of type IP and the rule condition will use this group.
Add/remove group members based on a rule triggering
Question/Problem: Can I automatically add/remove members to a group based on a rule triggering? How?
Answer/Solution: To add members to a group or remove members from a group, create a new trigger action enumeration named "add member to group" or "remove member from group" and an action group for it. In the group add an action. Configure a configurable action to trigger on "add member to group" or "remove member from group" which will add or remove the member.
Question/Problem: How can I exclude some users from being affected by a rule?
Answer/Solution: Create a group which contains the users. Then specify in the Rule's Pre-Condition tab to exclude the group.
Question/Problem: What does Cache Policy do?
Answer/Solution: The Cache Policy determines if the application uses data stored in the cache or re-fetches original data from the server.
How does Cache Policy affect performance
Question/Problem: How does Cache Policy affect performance?
Answer/Solution: Performance is impacted if the application has to consult the server every time the information must be accessed. With cached data, the information is already stored for rapid access. Performance is impacted if you cache data and large changes are made since caching uses server space.
Question/Problem: In what situations should I not cache a group?
Answer/Solution: You should not cache a group if you have a long list of elements since groups are re-cached if there are any changes to the group.
Question/Problem: Can I have a group inside another group?
Answer/Solution: No, the only exception is when a city group could be in a state group which could be in a country group.
Question/Problem: How can I see if a group is linked to something else?
Answer/Solution: The Policy Tree shows the linking of User ID groups to policies.
31.7 Location Loader
Characters added during transfer of files
Question/Problem: During the transfer/ftp of files, characters such as carriage return "\r" are added.
Answer/Solution: To resolve the issue, run dos2unix against the files. When you are running the .sh file, use either dos2unix <filename> or dos2unix . *.* .
TNS:no appropriate service handler found" error
Question/Problem: The following error when I load data
TNS:no appropriate service handler found
Answer/Solution: It may be that the number of processes in your database is set to a minimal value.
Use the following commands to check the number of process set in the database
SQL> show parameter process SQL> alter system set processes=100 scope=spfile;
31.8 Autolearning
Verify that autolearning is functional
Question/Problem: I enabled autolearning and configured the policies. How do I verify that autolearning is running?
Answer/Solution: To verify if autolearning is turned on and working:
-
Log in to the system.
-
Run a few logins.
-
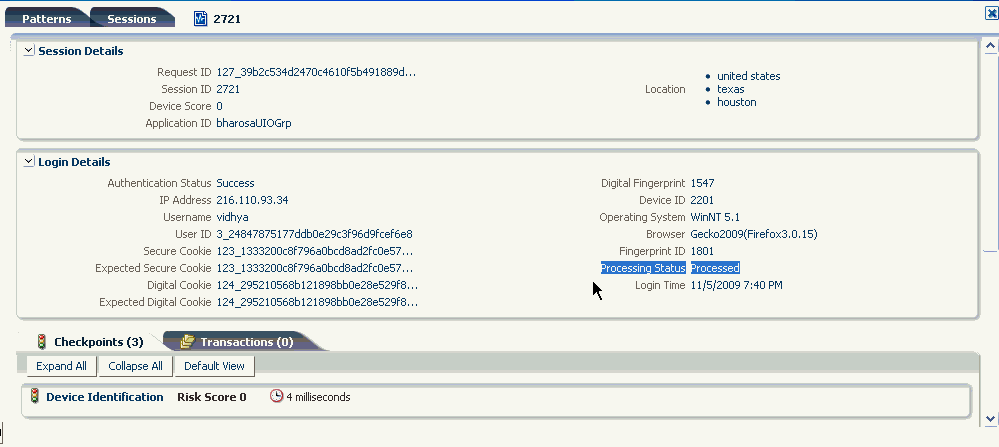
To find out whether autolearning data of a session has been processed, go to the Session Details page of that session and view the Processing Status field in the Login Details section.
If autolearning has not been set up correctly, data will not have been processed.
31.9 Configurable Actions
Question/Problem: A custom action was created, but it is not available in the user interface.
Answer/Solution: Ensure that the Java class is in the right directory and that it is in the right package.
Multiple cases were generated because of configurable action
Question/Problem: Multiple cases are generated when create cases was defined as a configurable action.
Answer/Solution: If the pre-condition is an action that can occur frequently, every time, the action occurs, a case is created. For example, actions such as "challenge" can occur more than once in a session (OTP challenge, KBA challenge, and so on).
Question/Problem: Synchronous actions are executed in the order of their priority in the ascending order. For example, if you want to create a CSR case and then send an email with the Case ID, you would choose synchronous actions. Synchronous actions will trigger/execute immediately.
What happens if the first action fails. Will the email be sent still?
Answer/Solution: The execution of configurable action is not dependent on the execution of other configurable actions. However, custom code can check data in the context that is shared across actions and perform logic based on the context data.
Question/Problem: Asynchronous actions are queued for execution and will be executed based on their priority but not in any particular sequence. For example, if you want to send an email or perform some action and do not care about executing it immediately and are not interested in any order of execution, you would choose asynchronous actions.
Are asynchronous actions guaranteed to execute? What happens if the server stops running?
Answer/Solution: If the server stops running, then any pending configurable actions will not be executed.
Question/Problem: Trigger criteria enables you to choose when you want to trigger the action in the session.
The action could be either a score or an action or both. These are compared against the values from the Rule Engine for the selected checkpoint while defining the configurable action.
What happens if both action and score are specified and only one is matched? What is the priority?
Answer/Solution: When both action and score are specified, the configurable action is executed only if both of criteria match with the outcome from the Rules Engine.
Action Priority in Asynchronous Actions
Question/Problem: How is action priority used in asynchronous actions?
Answer/Solution: Actions are aligned in different queues based on the action priority. When it is time to execute the next action from the queue, the highest-priority action is executed first.
31.10 Entities
Question/Problem: A user creates an entity, but it is not available in the Transactions Page Entities list.
Answer/Solution: The user has forgotten to activate his entity.
Refer to Section 20.9, "Activating Entities."
Data element not available for evaluation
Question/Problem: The Data element is not available for evaluation in the condition
Answer/Solution: The Data element may be encrypted.
Question/Problem: Can a user add multiple instances of the entity to a Transaction?
Answer/Solution: Yes
Entity change affects instances of the entity
Question/Problem: If a user changed the entity definition, are all the instances of the entity affected?
Answer/Solution: Yes, the definition is a template
Refer to Section 20.6, "Editing the Entity."
Question/Problem: The user is not able to delete an entity. The user has removed that instance from the Transaction already.
Answer/Solution: The entity is also used in other transactions, patterns, and so on.
Refer to Section 20.11, "Deleting Entities."
Not able to delete the entity even when transactions are not using them
Question/Problem: The user does not have any Transaction that uses the entity, but is still not able to delete the entity.
Answer/Solution: There might be historical Transaction data using the entity
31.11 Transactions
Group of floating point numbers
Question/Problem: I want to see if the transaction amount is one of a specific value - like $999.99. Is there a way to model this? "Generic Integer" and "Generic Long" are available, but they do not take floating point numbers.
Answer/Solution: Where decimals are needed, model by changing the unit. For example, instead of 99.99, use 9999. Care should be taken to use the unit (for example cents instead of dollars) consistently in all the rules and groups.
Question/Problem: How do you exclude certain entities - like merchants or accounts? For example, merchants and accounts are modeled as entities and Oracle Adaptive Access Manager does not have a "group of entities" option.
Answer/Solution: Group the entities using their "primary key" (like a generic strings group.
31.12 Jobs
Question/Problem: After I execute the task and view the historical data in the dashboard, will there be any difference in the user interface. Will monitor data rollup have an impact on the dashboard?
Answer/Solution: There should be no impact on dashboard. There should not be any impact with default settings for cutoff time. If you the set cutoff time to smaller than default, then you may see impact on dashboard. Example: if you perform a daily rollup and change the cutoff time from 3 to 1, then you will lose some of the hourly granularity in the hourly trending view in the bottom part of the dashboard.
31.13 Dashboard
KBA Challenge and Challenge Statistics Do Not Match in Sessions for Time Range
Question/Problem: The Summary Dashboard statistics for KBA challenges does not match the Challenge statistics on the Sessions Search page for the same time range.
Answer/Solution: The counts are two different metrics. The Challenge statistics are a count of the number of sessions that were challenged. The KBA Challenge statistics are a count of the number of times a user answered a challenge question.
For example, if a user logs in and is challenged and answers the question incorrectly once, and then answers the question correctly. There will be one session on the Sessions Search page related to this login, but the KBA Challenges on the dashboard will increase by 2.
The Count of Unsuccessful Challenges is Incorrect in the Summary Logins Report
Question/Problem: A high-risk user logs in to OAAM Server and he is challenged. He enters incorrect answers for the challenge questions. The CSR checks the Oracle Adaptive Access Manager Login Summary Report and looks at the unsuccessful challenges. The count is more than the actual.
Answer/Solution: The totals shown in Successful Challenges and Unsuccessful Challenges are the number of times a challenge question was answered successfully or unsuccessfully.
Average Processing Time for Rules and Policies Does Not Match with Reports
Question/Problem: The CSR captures the rules processing times from session details for a user and runs a SQL query to gather the statistics from the database. The report and SQL query numbers are different than those displayed by the dashboard.
-
The average processing times in sessions details and the database are different from the numbers displayed in the performance dashboard. They do not match exactly.
-
Execution counts shown in the Dashboard vary from the Security RulesBreakdown report. Additional rules are displayed in the dashboard. (Session details and the Security RulesBreakdown report show fewer rules.)
Answer/Solution: The reasons for the mismatch are listed as follows:
-
The execution count shown in the Dashboard and in the Security RulesBreakdown report vary because the dashboard displays the number of times the rule was processed, whether or not they triggered, but the Security RulesBreakdown report displays the number of times the rule returned true. The values in the dashboard and the values returned by that SQL query are different measurements, so the values should not be expected to match.
-
The average processing times in sessions details and the database are different from the numbers displayed in the performance dashboard. They do not match exactly. The monitor data calculates the processing time differently from the report and query. The report and query includes setup code and other processing times not included in the monitor data number. The monitor data contains the rules processing time and the time spent for fact assertions into the working memory.
31.14 Command-Line Interface
Question/Problem: How do I troubleshoot command-line errors?
Answer/Solution: Here are the steps to troubleshoot command-line errors:
-
Check Java Version. Make sure it is the same as recommended version. For example, like JDK 1.6.
-
Make sure the jars are in class path (jps*.jars).
-
Define credentials in the Credential Store. The Credential Store is similar to sessions.xml, but the definition is in Enterprise Management for OAAM domain instead of a file.
-
Make sure the SID is correct.
Question/Problem: Can I write a CRON job to schedule policy, group, and rule exports?
Answer/Solution: Yes.
Steps to create a scheduled job are:
-
Create a script using CLI to export the required data. Test for accuracy of data.
Refer to Chapter 29, "Oracle Adaptive Access Manager Command-Line Interface Scripts" for information on exporting policies and groups
-
Create a cron job to periodically run the script.
For information on creating a cron job, refer to
-
Ensure that you:
-
Encrypt the database password. Refer to Chapter 29, "Oracle Adaptive Access Manager Command-Line Interface Scripts."
-
Do not overwrite files - Devise a unique naming convention.
-
Monitor the backup process - Setup email and notification
-
Monitor disk space /performance - Include only required data in backup, and look for groups with many elements, and so on.
-
31.15 Import/Export
Importing large policy ZIP files
Question/Problem: I tried to import a large policy ZIP file that contains many policies (the file size is larger than 1MB), but the import failed. The log file does not shows any errors. How can I import this file?
Answer/Solution: If OAAM Admin is installed on the Windows platform, you must create a \tmp folder in the drive where you have installed WebLogic.
For example, if the WebLogic domain is on the C drive, you must create a c:\tmp folder.
This folder will be used as a temporary folder for uploading large files into OAAM Admin.
OAAM Admin failed to import policy, rule condition, and challenge questions ZIP files.
Question/Problem: OAAM Admin failed to import policy, rule condition, and challenge questions ZIP files.
Answer/Solution: This is an issue with Mozilla Firefox MIME type mapping. If the environment does not have any application mapped to the ZIP extension, Mozilla maps the incorrect content type. One workaround is to add a file type mapping in Firefox Preferences.
Browser does not recognize the files which are being uploaded
Question/Problem: When I try to import my Oracle Adaptive Access Manager files, my browser does not recognize them.
Answer/Solution: When the MIME entry for Foxfire is not present in the operating system on which it is installed, the browser fails to recognize correct file types.
A MIME entry must be added for all the types of files, viz, doc, txt, zip, and others under the /etc/mime.types file of any operating system to enable browsers to recognize the files which are being uploaded. Once this entry is there, the browser recognize the files successfully.
There is no issue if the MIME entry is already present in operating system.
31.16 Database
RCU schema load for Oracle Adaptive Access Manager partition does not create tablespace with prefix
Question/Problem: Loading the Oracle Adaptive Access Manager partition schema through RCU does not create tablespaces for the partition using the prefix used in RCU.
Answer/Solution: There is a limitation in RCU for only 5 additional tablespace support and 30+ tablespaces are needed for the Oracle Adaptive Access Manager partitioned based schema. Prefixes cannot be used for tablespace names.
Database Queries to Determine the Space Used
Question/Problem: What are the database queries to use to determine the space used?
Answer/Solution: Use the following databases queries:
The following query can be used to determine average size of row in tables:
.
select table_name,
avg_row_len
from user_tables
.
The following query can be used to determine size of indexes of the tables:
.
select inds.table_name,
inds.index_name,
sum( inds.sizes ) as index_bytes_per_row
from (
select i.index_name,
i.table_name,
i.column_name,
decode(data_type, 'DATE' , 7,
'CHAR' , data_length,
'VARCHAR2', decode(
sign(data_length)-250, -1, .7*data_length+3, .7*data_length+1),
'NUMBER' ,
floor(nvl(data_precision,38)/2)+2 ) as sizes
from user_ind_columns i,
user_tab_columns t
where t.TABLE_NAME = i.table_name AND
t.COLUMN_NAME = i.COLUMN_NAME
order by i.table_name, i.column_name
) inds
group by inds.table_name, inds.index_name;
31.17 Monitoring Performance
Monitoring Performance through Fusion Middleware Control
You can use Fusion Middleware Control to monitor Oracle Adaptive Access Manager performance and activity.
-
Select OAAM under Identity and Access to go to the home page.
On the home page, you can view a performance overview for Oracle Adaptive Access Manager.
-
Select Performance Summary from the Oracle Adaptive Access Manager menu in the upper left hand side of the home page to view performance metrics.
For information on monitoring status and performance with Fusion Middleware Control, see "Monitoring Oracle Fusion Middleware" in the Oracle Fusion Middleware Administrator's Guide.
Monitoring the Security Effectiveness of Oracle Adaptive Access Manager
The effectiveness of Oracle Adaptive Access Manager can be viewed in multiple ways:
-
Oracle Adaptive Access Manager contains a real-time dashboard of metrics including security actions taken
For information, see Chapter 24, "Using the Dashboard."
-
OAAM Admin also allows visibility into activity down to the object level details and relationships
For information, see Chapter 3, "Oracle Adaptive Access Manager Navigation."
-
Oracle Adaptive Access Manager ships with an extensive package of reporting templates for Oracle Business Intelligence Publisher.
For information, see Appendix D, "Oracle Adaptive Access Manager Reports Reference."
31.18 Audit and Query
Question/Issue: If I want to query / audit data, it will have to be via the production instance of OAAM using OAAM Admin. This might affect the performance of OAAM Server, since query and audit activities tend to perform many sequential reads / table scans on the production index/tablespaces. How might I lessen the performance impact?
Answer/Solution: You might consider maintaining a logical standby database using DataGuard where you can have an option to query / audit / perform reporting using the logical standby database. The logical standby database would have all the data as production, except for the last one hour. The production database instance can just be used to perform its inserts, updates, and so on, and also for active monitoring and alerts.
31.19 Archive and Purge
Question/Problem: Does running the purge process remove registration of "safe" device?
Answer/Solution: There is no special treatment for safe device. Active Devices will not be purged.
Examples are:
6 Months device purge policy
-
Device is safe not used in last 6 months - candidate for purge
-
Device is not safe and not used in last 6 months - candidate for purge
-
Device is safe and used within last 6 months - not candidate for purge. It will not be purged even if device is created more than 6 months back.
-
Device is not safe and used within last 6 months - not candidate for purge. It will not be purged even if device is created more than 6 months back.
31.20 Device Registration
Question/Problem: The user has an option in the challenge questions registration page to register a device:
"Check to register the device that you are currently using as a safe device"
If he skipped during the registration flow, he does not seem to have an option later on from the user preferences page. Is there a way to turn it on?
Answer/Solution: Device registration is set up to ask the user to register the device during registration and when being challenged.
You can turn it on in the register questions page of user preferences by setting:
bharosa.uio.default.userpreferences.questions.registerdevice.enabled=true
Currently the central user preferences page only allows for unregistering devices.
The user can register the device during registration, but he is also given the option to register the device when being challenged.
31.21 Time Zones
Question/Problem: Do rules that evaluate time use one time zone for all sessions or does it use the time zone from the customer browser/OS? For example, if I set up a rule to KBA challenge if a user logs in outside of office hours (not 8:00 am - 6:00 pm) is this evaluated based on the time zone from the customer browser/OS?
Nameuser.timezoneTypeSystemValuePST8PDT user.timezone = PST8PDT oaam.adf.timezone = user.timezone
The Date and Time used for rule execution (pattern or non-pattern) comes in from "request_time." This is the same date / time that any request based rules will use.
-
For on-line it is the OAAM Admin server time.
-
For off-line: it is the time specified in the off line data for that request.
31.22 Encryption
Question/Problem: How many keystores are there? And which one is used for what?
Answer/Solution: There are 3 keystores:
-
System Keystore: Used for encrypting properties and other non database-related data
-
Database: Columns in the database. Mostly password, PIN, Transaction data (like credit card #, etc.)...
-
SOAP/WebServices: On the client side to authenticate Web Services request
What tables and columns are encrypted
Question/Problem: If the database is encrypted with these keystores which database tables, or columns, or both are encrypted?
Answer/Solution: VCryptPassword and Transaction tables.
Question/Problem: Do you need to decrypt the data? When do you need to do this?
Answer/Solution: Data is decrypted by the application as and when required. There are not external tools available to decrypt this data.
Question/Problem: Can you omit the encryption?
Answer/Solution: SOAP is optional. Database and System are mandatory
31.23 Globalization
Characterset in database for Oracle Adaptive Access Manager
Question/Problem: A client already has a database with no UTF8 support, and he wants to keep it that way as it is a shared database and ignore browser locale preferences.
Answer/Solution: Since Browser preferences cannot be controlled, the server should ignore Locale preference or always use English.
31.24 Localization
Question/Problem: How do I turn off localization?
Answer/Solution: There is no flag to turn-off localization, but there is a user-defined enum that captures the locales supported by the deployment. The enum can be used to enable only one locale.
You would change the locale.enum.XXX.adminSupported and locale.enum.XXX.enabled properties to false for each unwanted locale.
Language setting on a per user basis?
Question/Problem: Does Oracle Adaptive Access Manager support language setting on a per user basis?
Answer/Solution: Usually, Web applications take the language setting of the browser.
For example, a user registers his virtual authentication device and KBA questions using a Spanish browser. If he logs in using an English browser, his phrase will be in Spanish and answers to any KBA questions presented will be expected in Spanish. The KBA question presented to him however will be in English as is expected with most Web application content.
In Oracle Adaptive Access Manager 10.1.4.5 the end-user facing Web application used in proxy type deployments has globalization support. The end user's browser language/locale setting tells the application what language to display the screens in, including KBA questions and the personalization of the virtual authentication devices (phrase). The APIs for KBA and the virtual devices accept locale as a parameter.
However, if the deployment is using native application integration, the functionality would need to be developed in the custom end user facing Web application being built. This application would probably use resource bundles. It would also need to call the KBA and the virtual authentication device APIs while passing a supported locale as a parameter.