1 Introduction to Oracle Platform Security Services
Oracle Platform Security Services (OPSS) is a security platform that can be used to secure applications deployed in any of the supported platforms or in standalone applications. This chapter introduces the main features of this platform in the following sections:
The scope of this document does not include Oracle Web Services security. For details about that topic, see Oracle Fusion Middleware Security and Administrator's Guide for Web Services.
For an overview of Oracle Fusion Middleware security topics, see Oracle Fusion Middleware Security Overview.
1.1 What is Oracle Platform Security Services?
OPSS provides enterprise product development teams, systems integrators, and independent software vendors with a standards-based, portable, integrated, enterprise-grade security framework for Java SE and Java EE applications.
OPSS is the underlying security platform that provides security to Oracle Fusion Middleware including WebLogic Server, Server Oriented Architecture (SOA) applications, Oracle WebCenter, Oracle Application Development Framework (ADF) applications, and Oracle Entitlement Server. OPSS is designed to be portable to third-party application servers, so developers can use OPSS as the single security framework for both Oracle and third-party environments, thus decreasing application development, administration, and maintenance costs.
OPSS provides an abstraction layer in the form of application programming interfaces (APIs) that insulate developers from security and identity management implementation details. With OPSS, developers do not need to know the details of, for example, cryptographic key management, repository interfaces, or other identity management infrastructures. Using OPSS, in-house developed applications, third-party applications, and integrated applications benefit from the same, uniform security, identity management, and audit services across the enterprise.
For OPSS-related news, including FAQs, a whitepaper, and code examples, and forum discussions, see http://www.oracle.com/technology/products/id_mgmt/opss/index.html.
1.1.1 OPSS Main Features
OPSS complies with the following standards: role-based-access-control (RBAC); Java Enterprise Edition (Java EE); and Java Authorization and Authentication Services (JAAS).
Built upon these standards, OPSS provides an integrated security platform that supports:
-
Authentication
-
Identity assertion
-
Authorization, based on fine-grained JAAS permissions
-
The specification and management of application policies
-
Secure storage and access of system credentials through the Credential Store Framework
-
Secure storage and access of keys and certificates through the Keystore Service
-
Auditing
-
Role administration and role mappings
-
The User and Role API
-
Identity Virtualization
-
Security configuration and management
-
SAML and XACML
-
Oracle Security Developer Tools, including cryptography tools
-
Policy Management API
-
Java Authorization for Containers (JAAC)
Details about a given OPSS feature functionality are found in subsequent chapters of this guide.
For details about the WebLogic Auditing Provider, see section Configuring the WebLogic Auditing Provider in Oracle Fusion Middleware Securing Oracle WebLogic Server.
1.1.2 Supported Server Platforms
OPSS is supported in the following application server platforms:
-
Oracle WebLogic Server
-
IBM WebSphere Application Server - Network Deployment (ND) 7.0
-
IBM WebSphere Application Server 7.0
This guide documents OPSS features relevant to the Oracle WebLogic Server that apply uniformly to all other platforms. Those topics that apply specifically to third-party servers are found in Oracle Fusion Middleware Third-Party Application Server Guide.
1.2 OPSS Architecture Overview
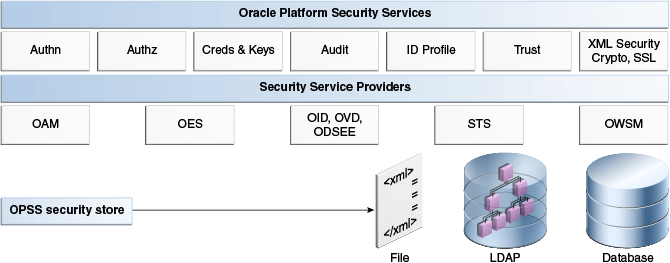
OPSS comprises the application server's security and Oracle's Fusion Middleware security. Figure 1-1 illustrates the layered architecture that combines these two security frameworks:
The top layer includes the OPSS security services; the next layer includes the service providers, and the bottom layer includes the OPSS security store with a repository of one of three kinds.
Security Services Provider Interface (SSPI) provides Java EE container security in permission-based (JACC) mode and in resource-based (non-JACC) mode, and resource-based authorization for the environment.
SSPI is a set of APIs for implementing pluggable security providers. A module implementing any of these interfaces can be plugged into SSPI to provide a particular type of security service, such as custom authentication or a particular role mapping.
For details, see section The Security Service Provider Interfaces (SSPIs) in Oracle Fusion Middleware Understanding Security for Oracle WebLogic Server.
Oracle Platform Security Services
Java Authorization (JAZN) functionality includes the Credential Store Framework (CSF), the Common Audit Framework (CAF), Keystore Service, and other components, and combined with SSPI as Oracle Platform Security Services (OPSS).
1.2.1 Benefits of Using OPSS
The benefits that OPSS offers include the following:
-
Allows developers to focus on application and domain problems
-
Supports enterprise deployments
-
Supports several LDAP servers and SSO systems
-
Is certified on the Oracle WebLogic Server
-
Pre-integrates with Oracle products and technologies
-
Offers a consistent security experience for developers and administrators
-
Provides a uniform set of APIs for all types of applications
-
Optimizes development time by offering abstraction layers (declarative APIs)
-
Provides a simplified application security maintenance
-
Allows changing security rules without affecting application code
-
Eases the administrator's job
-
Integrates with identity management systems
-
Integrates with legacy and third-party security providers
OPSS combines SSPI and JPS to provide a framework where the application server and Oracle applications can seamlessly run in a single environment.
OPSS supports security for Java EE applications and for Oracle Fusion Middleware applications, such as Oracle WebCenter and Oracle SOA Suite.
Developers can use OPSS APIs to secure all types of applications and integrate them with other security artifacts, such as LDAP servers, RDBMS, and custom security components.
Administrators can use OPSS to deploy large enterprise applications with a small, uniform set of tools and administer all security in them. OPSS simplifies the maintenance of application security because it allows the modification of security configuration without changing the application code.
By default and out-of-the-box, Oracle WebLogic Server stores users and groups in its embedded LDAP repository. Domains can be configured, however, to use identity data in other kinds of LDAP repositories, such as Oracle Internet Directory, ActiveDirectory, Novell eDirectory, and OpenLDAP. In addition, Oracle WebLogic Server provides a generic, default LDAP authenticator that can be used with other LDAP servers not in the preceding list.
Out-of-the-box, policies and credentials are stored in file-based stores; these stores can be moved (or reassociated) to an LDAP repository backed by an Oracle Internet Directory.
Out-of-the-box, keys and certificates are stored in a file-based keystore, which can be reassociated with a database or an LDAP repository.
Note:
This guide does not attempt to describe in detail WebLogic security features; wherever specific information about SSPI is used or assumed, the reader is referred to the appropriate document.
1.3 Oracle ADF Security Overview
Oracle ADF is an end-to-end Java EE framework that simplifies development by providing out-of-the-box infrastructure services and a visual and declarative development experience.
Oracle ADF Security is based on the JAAS security model, and it uses OPSS. Oracle ADF Security supports LDAP- or file-based policy and credential stores, uses permission-based fine-grained authorization provided by OPSS, and simplifies the configuration of application security with the aid of visual declarative editors and the Oracle ADF Security wizard, all of them available in Oracle JDeveloper 11g (any reference to this tool in this guide stands for its 11g release).
Oracle ADF Security authorization allows protecting components (flows and pages), is integrated with Oracle JDeveloper at design time, and is available at run time when the application is deployed to the integrated server where testing of security features is typically carried out.
During the development of an Oracle ADF application, the authenticators are configured with the Oracle WebLogic Server Administration Console for the particular domain where the application is deployed, and the policy store is file-based and stored in the file jazn-data.xml. For deployment details, see Section 6.3.1, "Deploying to a Test Environment."
To summarize, Oracle ADF Security provides:
-
Control over granular declarative security
-
Visual and declarative development of security artifacts
-
Assignment of simplified permission through a role hierarchy
-
Use of EL (expression language) to access Oracle ADF resources
-
Integration with Oracle JDeveloper that allows quick development and test cycles
-
Rich Web user interfaces and simplified database access
For related information, see Scenario 2: Securing an Oracle ADF Application.
1.4 OPSS for Administrators
Depending on the application type, the guidelines to administer application security with Oracle WebLogic Administration Console, OPSS scripts, Fusion Middleware Control, or Oracle Entitlements Server are as follows:
-
For Java EE applications, security is managed with Oracle WebLogic Administration Console, Oracle Entitlements Server, or OPSS scripts.
-
For Oracle SOA, Oracle WebCenter, MDS, and Oracle ADF applications, authentication is managed with Oracle WebLogic Administration Console and authorization is managed with Fusion Middleware Control and Oracle Entitlements Server.
-
For Java EE applications integrating with OPSS, authentication is managed using Oracle WebLogic Administration Console, and authorization is managed with Fusion Middleware Control and Oracle Entitlements Server.
For details about security administration, see Chapter 5, "Security Administration."
1.5 OPSS for Developers
This section summarizes the main OPSS features typically used when securing applications, in the following scenarios:
For other use cases, see Section 19.2, "Security Integration Use Cases."
1.5.1 Scenario 1: Enhancing Security in a Java EE Application
A Java EE application can be enhanced to use OPSS APIs such as the CSF, User and Role, or Policy Management: user attributes, such as a user's email, phone, or address, can be retrieved using the Identity Governance Framework API or the User and Role API; external system credentials (stored in a wallet or in a LDAP-based store) can be retrieved using the CSF API; authorization policy data can be managed with the policy management APIs; and application keys and certificates can be managed with Keystore Service APIs.
Java EE applications, such as servlets, JSPs, and EJBs, deployed on Oracle WebLogic Server can be configured to use authentication and authorization declaratively, with specifications in the file web.xml, or programmatically, with calls to isUserInRole and isCallerInRole.
Custom authenticators include the standard basic, form, and client certification methods. Authentication between servlets and EJBs is controlled using user roles and enterprise groups, typically stored in an LDAP repository, a database, or a custom authenticators.
1.5.2 Scenario 2: Securing an Oracle ADF Application
Oracle Application Development Framework (ADF) is a Java EE development framework available in Oracle JDeveloper that simplifies the development of Java EE applications by minimizing the need to write code that implements the application's infrastructure, thus allowing developers to focus on the application features. Oracle ADF provides these infrastructure implementations as part of the Oracle JDeveloper framework, therefore enhancing the development experience with visual and declarative approaches to Java EE development.
Oracle ADF implicitly uses OPSS, and, for most part, the developer does not have to code directly to OPSS APIs; of course, the developer can nevertheless use direct calls to OPSS APIs.
Oracle ADF leverages container authentication and subsequently uses JAAS based authorization to control access to Oracle ADF resources. These authorization policies may include application-specific roles and JAAS authorization permissions. Oracle ADF connection credentials are stored securely in the credential store.
Oracle ADF and Oracle WebCenter applications deployed on Oracle WebLogic Server include WebLogic authenticators, such as the default WebLogic authenticator, and may include a single sign-on solution (Oracle Access Manager or Oracle Application Server Single Sign-On).
Usually, applications also use one or several of the following OPSS features: anonymous and authenticated role support, policy management APIs, and the Credential Store Framework.
For details about these topics, see the following sections:
For details on how to develop and secure Oracle ADF applications, see chapter 29 in Oracle Fusion Middleware Fusion Developer's Guide for Oracle Application Development Framework.
1.5.3 Scenario 3: Securing a Java SE Application
Most of the OPSS features that work in Java EE applications work in Java SE applications, but there are some differences, which are noted in this section.
All OPSS-related configuration and data files are located under configuration directory in the domain home. For example, the configuration file for a Java SE environment is defined in the file jps-config-jse.xml by default installed in the following location:
$DOMAIN_HOME/config/fmwconfig/jps-config-jse.xml
To specify a different location, use the following switch:
-Doracle.security.jps.config=pathToConfigFile
The syntax of this file is identical to that of the file jps-config.xml. This file is used by code running in WebLogic containers. For details, see Appendix A, "OPSS Configuration File Reference."
For details about security configuration for Java SE applications, see Section 22.2, "Authentication for Java SE Applications," and Section 23.1, "Configuring Policy and Credential Stores in Java SE Applications."
To make OPSS services available to a Java SE application, ensure that the following JAR file is added to your class path, located in the modules area of the Oracle installation home:
$ORACLE_HOME/oracle_common/modules/oracle.jps_11.1.1/jps-manifest.jar
Java SE applications can use standard JAAS login modules. However, to use the same login module on WLS, implement a custom authentication provider that invokes the login module. The SSPI interfaces allow integrating custom authentication providers in WLS.
The login module recommended for Java SE applications is the IdentityStore login module.
For details, see section Authentication Providers in Oracle Fusion Middleware Developing Security Providers for Oracle WebLogic Server.