4 Installing and Configuring the Microsoft IIS Plug-In
The following sections describe how to install and configure the Microsoft Internet Information Server Plug-In:
-
Overview of the Microsoft Internet Information Server Plug-In
-
Installing and Configuring the Microsoft Internet Information Server Plug-In
-
Installing and Configuring the Microsoft Internet Information Server Plug-In for IIs 7.0
-
Proxying Requests from Multiple Virtual Web Sites to WebLogic Server
-
Using SSL with the Microsoft Internet Information Server Plug-In
Overview of the Microsoft Internet Information Server Plug-In
The Microsoft Internet Information Server Plug-In allows requests to be proxied from a Microsoft Internet Information Server (IIS) to WebLogic Server. The plug-in enhances an IIS installation by allowing WebLogic Server to handle those requests that require the dynamic functionality of WebLogic Server.
You use the Microsoft Internet Information Server Plug-In in an environment where the Internet Information Server (IIS) serves static pages such as HTML pages, while dynamic pages such as HTTP Servlets or JavaServer Pages are served by WebLogic Server. WebLogic Server may be operating in a different process, possibly on a different host. To the end user—the browser—the HTTP requests delegated to WebLogic Server still appear to be coming from IIS. The HTTP-tunneling facility of the WebLogic client-server protocol also operates through the plug-in, providing access to all WebLogic Server services.
Connection Pooling and Keep-Alive
The Microsoft Internet Information Server Plug-In improves performance using a pool of connections from the plug-in to WebLogic Server. The plug-in implements HTTP 1.1 keep-alive connections between the plug-in and WebLogic Server by re-using the same connection for subsequent requests from the same client. If the connection is inactive for more than 30 seconds, (or a user-defined amount of time) the connection is closed. The connection with the client can be reused to connect to the same client at a later time if it has not timed out. You can disable this feature if desired. For more information, see KeepAliveEnabled in Table 7-1.
Proxying Requests
The plug-in proxies requests to WebLogic Server based on a configuration that you specify. You can proxy requests based on either the URL of the request or a portion of the URL. This is called proxying by path.
You can also proxy a request based on the MIME type of the requested file, which is called proxying by file extension.
You can also enable both methods. If you do enable both methods and a request matches both criteria, the request is proxied by path.
You can also specify additional parameters for each of these types of requests that define additional behavior of the plug-in. For more information, see Using Wildcard Application Mappings to Proxy by Path and Installing and Configuring the Microsoft Internet Information Server Plug-In.
Certifications
For the latest information on operating system and IIS version compatibility with the Microsoft Internet Information Server Plug-In, see http://www.oracle.com/technology/software/products/ias/files/fusion_certification.html.
Using Wildcard Application Mappings to Proxy by Path
As described in "Installing Wildcard Application Mappings (IIS 6.0)" (http://www.microsoft.com/technet/prodtechnol/WindowsServer2003/Library/IIS/5c5ae5e0-f4f9-44b0-a743-f4c3a5ff68ec.mspx?mfr=true), and "Add a Wildcard Script Map" for IIS 7.0 (http://technet.microsoft.com/en-us/library/cc754606(WS.10).aspx), you can configure a Web site or virtual directory to run an Internet Server API (ISAPI) application at the beginning of every request to that Web site or virtual directory, regardless of the extension of the requested file. You can use this feature to insert a mapping to iisproxy.dll and thereby proxy requests by path to WebLogic Server.
Installing Wildcard Application Mappings (IIS 6.0)
The following steps summarize the instructions available at "Installing Wildcard Application Mappings (IIS 6.0)" (http://www.microsoft.com/technet/prodtechnol/WindowsServer2003/Library/IIS/5c5ae5e0-f4f9-44b0-a743-f4c3a5ff68ec.mspx?mfr=true) for adding a wildcard application mapping to a Web server or Web site in IIS 6.0:
-
In IIS Manager, expand the local computer, expand the Web Sites folder, right-click the Web site or virtual directory that you want, and then click Properties.
-
Click the appropriate tab: Home Directory, Virtual Directory, or Directory.
-
In the Application settings area, click Configuration, and then click the Mappings tab.
-
To install a wildcard application map, do the following:
-
On the Mappings tab, click Insert.
-
Type the path to the
iisproxy.dllDLL in the Executable text box or click Browse to navigate to. -
Click OK.
-
Adding a Wildcard Script Map for IIS 7.0
The following steps summarize the instructions available at "Add a Wildcard Script Map" for IIS 7.0 (http://technet.microsoft.com/en-us/library/cc754606(WS.10).aspx) to add a wildcard script map to do proxy-by-path with ISAPI in IIS 7.0:
-
Open IIS Manager and navigate to the level you want to manage. For information about opening IIS Manager, see "Open IIS Manager" at
http://technet.microsoft.com/en-us/library/cc770472(WS.10).aspx. For information about navigating to locations in the UI, see "Navigation in IIS Manager" athttp://technet.microsoft.com/en-us/library/cc732920(WS.10).aspx. -
In Features View, on the server, site, or application Home page, double-click Handler Mappings.
-
On the Handler Mappings page, in the Actions pane, click Add Wildcard Script Map.
-
In the Executable box, type the full path or browse to the
iisproxy.dllthat processes the request. For example, typesystemroot\system32\inetsrv\iisproxy.dll. -
In the Name box, type a friendly name for the handler mapping.
-
Click OK.
-
Optionally, on the Handler Mappings page, select a handler to lock or unlock it. When you lock a handler mapping, it cannot be overridden at lower levels in the configuration. Select a handler mapping in the list, and then in the Actions pane, click Lock or Unlock.
-
After you add a wildcard script map, you must add the executable to the ISAPI and CGI Restrictions list to enable it to run. For more information about ISAPI and CGI restrictions, see "Configuring ISAPI and CGI Restrictions in IIS 7" at
http://technet.microsoft.com/en-us/library/cc730912(WS.10).aspx.
Installing and Configuring the Microsoft Internet Information Server Plug-In
To install the Microsoft Internet Information Server Plug-In:
-
Copy the iisproxy.dll file from the
WL_HOME/server/plugin/win/32orWL_HOME/server/plugin/win/64directory of your WebLogic Server installation (whereWL_HOMEis the top-level directory for the WebLogic Platform and Server and contains the WebLogic Server installation files into a convenient directory that is accessible to IIS). This directory must also contain theiisproxy.inifile that you will create in step 4. Set the user permissions for theiisproxy.dllfile to include the name of the user who will be running IIS. One way to do this is by right clicking on theiisproxy.dllfile and selecting Permissions, then adding the username of the person who will be running IIS. -
If you want to configure proxying by file extension (MIME type) complete this step. (You can configure proxying by path in addition to or instead of configuring by MIME type. See step 3. )
-
Start the Internet Information Service Manager by selecting it from the Start menu.
-
In the left panel of the Service Manager, select your Web site (the default is “Default Web Site”).
Figure 4-1 Selecting Web Site in Service Manager
Description of "Figure 4-1 Selecting Web Site in Service Manager"
-
Click the “Play” arrow in the toolbar to start.
-
Open the properties for the selected Web site by right-clicking the Web site selection in the left panel and selecting Properties.
Figure 4-2 Selecting Properties for Selected Web Site
Description of "Figure 4-2 Selecting Properties for Selected Web Site"
-
In the Properties panel, select the Home Directory tab, and click the Configuration button in the Applications Settings section.
Figure 4-3 Home Directory Tab of the Properties Panel
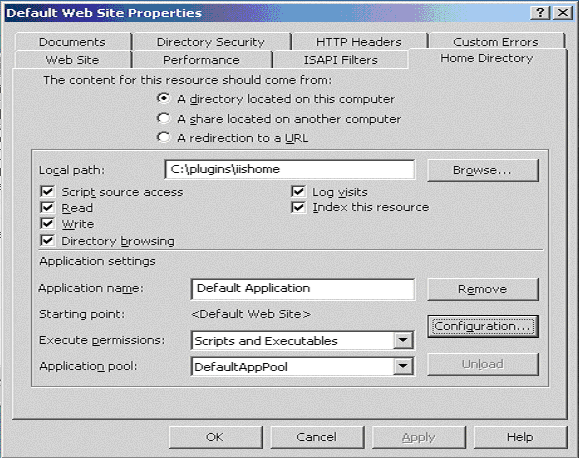
Description of "Figure 4-3 Home Directory Tab of the Properties Panel"
-
On the Mappings tab, click the Add button to add file types and configure them to be proxied to WebLogic Server.
Figure 4-4 Click the Add Button to Add File Types
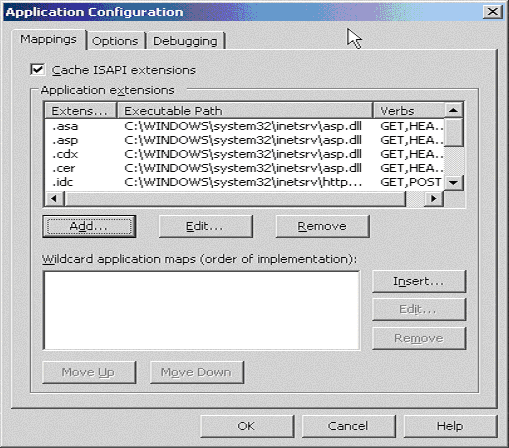
Description of "Figure 4-4 Click the Add Button to Add File Types"
-
In the Add dialog box, browse to find the
iisproxy.dllfile. -
Set the Extension to the type of file that you want to proxy to WebLogic Server.
-
If you are configuring for IIS 6.0 or later, be sure to deselect the “Check that file exists” check box. The behavior of this check has changed from earlier versions of IIS: it used to check that the iisproxy.dll file exists; now it checks that files requested from the proxy exist in the root directory of the Web server. If the check does not find the files there, the iisproxy.dll file will not be allowed to proxy requests to the WebLogic Server.
-
In the Directory Security tab, set the Method exclusions as needed to create a secure installation.
-
When you finish, click the OK button to save the configuration. Repeat this process for each file type you want to proxy to WebLogic.
-
When you finish configuring file types, click the OK button to close the Properties panel.
Note:
In the URL, any path information you add after the server and port is passed directly to WebLogic Server. For example, if you request a file from IIS with the URL:http://myiis.com/jspfiles/myfile.jsp
it is proxied to WebLogic Server with a URL such as http://mywebLogic:7001/jspfiles/myfile.jsp
Note:
To avoid out-of-process errors, do not deselect the "Cache ISAPI Applications" check box.
-
-
If you want to configure proxying by path complete this step. (In addition to proxying by file type, you can configure the Microsoft Internet Information Server Plug-In to serve files based on their path by specifying some additional parameters in the
iisproxy.inifile.) Proxying by path takes precedence over proxying by MIME type.You can also proxy multiple Web sites defined in IIS by path. For more information, see Proxying Requests from Multiple Virtual Web Sites to WebLogic Server.
To configure proxying by path:
-
Start the Internet Information Service Manager by selecting it from the Start menu.
-
Place the
iisforward.dllfile in the same directory as theiisproxy.dllfile and add theiisforward.dllfile as a filter service in IIS (WebSite Properties ->ISAPI Filters tab -> Add the iisforward dll). Set the user permissions for theiisforward.dllfile to include the name of the user who will be running IIS. One way to do this is by right clicking on theiisproxy.dllfile and selecting Permissions, then adding the username of the person who will be running IIS. -
Register .wlforward as a special file type to be handled by
iisproxy.dllin IIS. -
Define the property
WlForwardPathiniisproxy.ini.WlForwardPath defines the path that is proxied to WebLogic Server, for example:WlForwardPath=/weblogic. -
Set the
PathTrimparameter to trim off theWlForwardPathwhen necessary. For example, usingWlForwardPath=/weblogic PathTrim=/weblogic
trims a request from IIS to Weblogic Server. Therefore, /weblogic/session is changed to /session.
-
If you want requests that do not contain extra path information (in other words, requests containing only a host name), set the
DefaultFileNameparameter to the name of the welcome page of the Web Application to which the request is being proxied. The value of this parameter is appended to the URL. -
If you need to debug your application, set the Debug=ON parameter in
iisproxy.ini. Ac:\tmp\iisforward.logis generated containing a log of the plug-in's activity that you can use for debugging purposes.
-
-
In WebLogic Server, create the
iisproxy.inifile.The
iisproxy.inifile containsname=valuepairs that define configuration parameters for the plug-in. The parameters are listed in Table 7-1.Use the example
iisproxy.inifile in Sample iisproxy.ini File as a template for youriisproxy.inifile.Note:
Changes in the parameters will not go into effect until you restart the “IIS Admin Service” (under services, in the control panel).Oracle recommends that you locate the
iisproxy.inifile in the same directory that contains theiisproxy.dllfile. You can also use other locations. If you place the file elsewhere, note that WebLogic Server searches foriisproxy.iniin the following directories, in the following order:-
In the same directory where
iisproxy.dllis located. -
In the home directory of the most recent version of WebLogic Server that is referenced in the Windows Registry. (If WebLogic Server does not find the
iisproxy.inifile in the home directory, it continues looking in the Windows Registry for older versions of WebLogic Server and looks for theiisproxy.inifile in the home directories of those installations.) -
In the directory
c:\weblogic, if it exists.
-
-
Define the WebLogic Server host and port number to which the Microsoft Internet Information Server Plug-In proxies requests. Depending on your configuration, there are two ways to define the host and port:
-
If you are proxying requests to a single WebLogic Server, define the WebLogicHost and WebLogicPort parameters in the
iisproxy.inifile. For example:WebLogicHost=localhost WebLogicPort=7001
-
If you are proxying requests to a cluster of WebLogic Servers, define the WebLogicCluster parameter in the
iisproxy.inifile. For example:WebLogicCluster=myweblogic.com:7001,yourweblogic.com:7001
Where myweblogic.com and yourweblogic.com are instances of Weblogic Server running in a cluster.
-
-
Optionally, enable HTTP tunneling by following the instructions for proxying by path (see Using Wildcard Application Mappings to Proxy by Path), substituting the WebLogic Server host name and the WebLogic Server port number, or the name of a WebLogic Cluster that you wish to handle HTTP tunneling requests.
-
Set any additional parameters in the
iisproxy.inifile. A complete list of parameters is available in the appendix General Parameters for Web Server Plug-Ins. -
If you are proxying servlets from IIS to WebLogic Server and you are not proxying by path, read the section Proxying Servlets from IIS to WebLogic Server.
-
The installed version of IIS with its initial settings does not allow the
iisproxy.dll. Use the IIS Manager console to enable the Plug-In:-
Open the IIS Manager console.
-
Select Web Service Extensions.
-
Set “All Unknown ISAPI Extensions” to Allowed.
-
Installing and Configuring the Microsoft Internet Information Server Plug-In for IIs 7.0
This section describes differences in how you set up the Microsoft Internet Information Server Plug-In for IIs 7.0.
To set up the Microsoft Internet Information Server Plug-In for IIs 7.0, follow these steps:
-
Create a web application in IIS Manager by right clicking on Web Sites -> Add Web Site.
Fill in the Web Site Name with the name you want to give to your web application; for example, MyApp. Select the physical path of your web application Port (any valid port number not currently in use).
Click OK to create the web application.
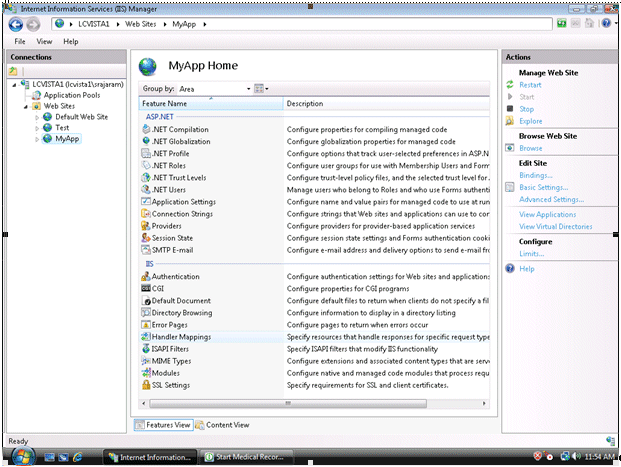
If you can see the name of your application under Web Sites it means that your application has been created and started running. Click on the MyApp node under Web Sites to see all of the settings related to the MyApp application, which you can change, as shown in Figure 4-5.
-
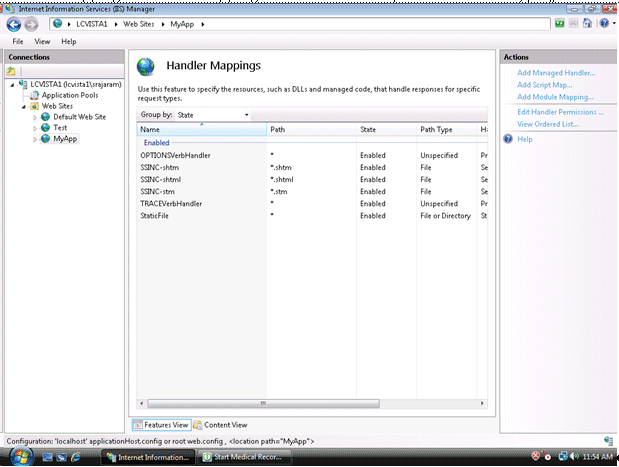
Click on "Handler Mappings" to set the mappings to the handler for a particular MIME type.
-
Click on the StaticFile and change the Request path from * to *.*. Click OK.
Figure 4-7 Editing the Request Path for Module
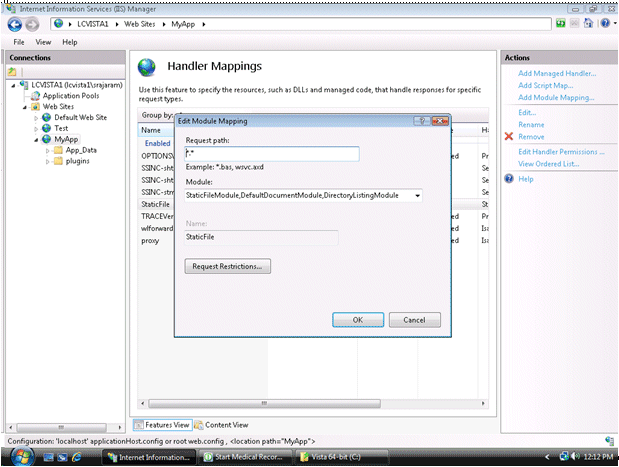
Description of "Figure 4-7 Editing the Request Path for Module"
-
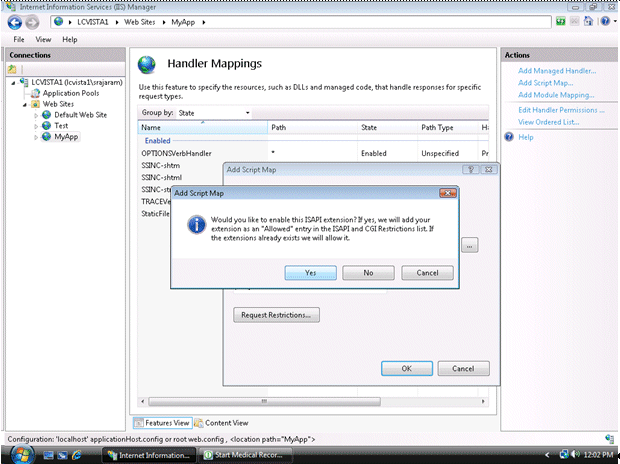
Click on MyApp and then click on "Add Script Map…" on the right-hand side menu options. Enter * for the Request path.
Browse to the
iisproxy.dllfile and add it as the executable. Name itproxy.Figure 4-8 Editing the Request Path for Script
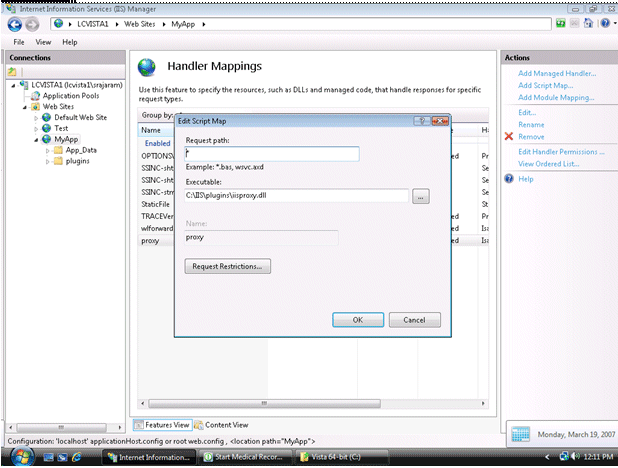
Description of "Figure 4-8 Editing the Request Path for Script"
-
Click on the "Request Restrictions…" button and uncheck the box "Invoke handler only if the request is mapped to".
Figure 4-9 Editing the Request Restrictions
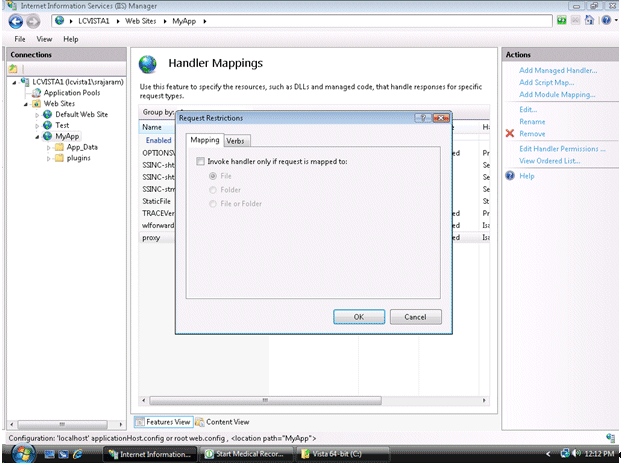
Description of "Figure 4-9 Editing the Request Restrictions"
-
Click OK to add this Handler mapping. Click Yes on the Add Script Map dialog box.
-
If you want to configure proxying by path, click on Add Script Map. Provide the Request path as
*.wlforwardand select the executable asiisproxy.dll.Click on the "Request Restrictions…" button and uncheck the box "Invoke handler only if the request is mapped to".
Click OK to add this Handler mapping. Click Yes on the Add Script Map dialog box.
Figure 4-11 Adding the Script Map for Proxying by Path
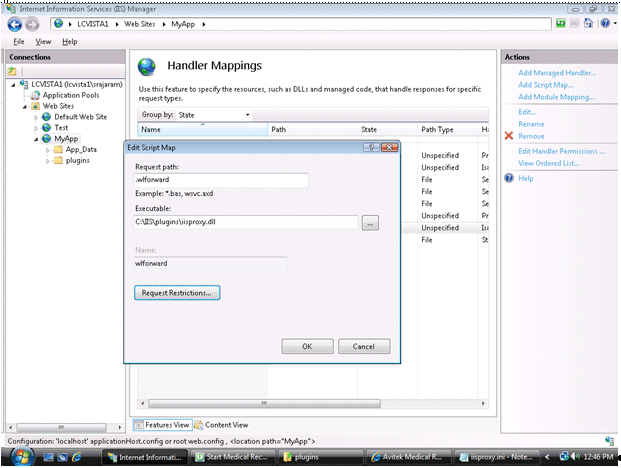
Description of "Figure 4-11 Adding the Script Map for Proxying by Path"
-
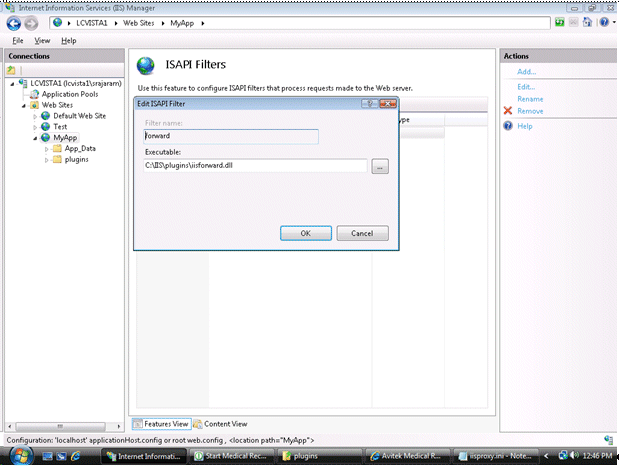
Click on the MyApp application on the left-hand side and click on ISAPI Filters. Click Add to add the ISAPI filter.
Enter the Filter name as
forwardand select the executable asiisforward.dll. Click OK. -
Click on the Root node of the IIS Manager tree and click on the ISAPI and CGI Restrictions. Make sure to check the "Allow unspecified ISAPI modules" checkbox.
Figure 4-13 Editing ISAPI and CGI Restrictions
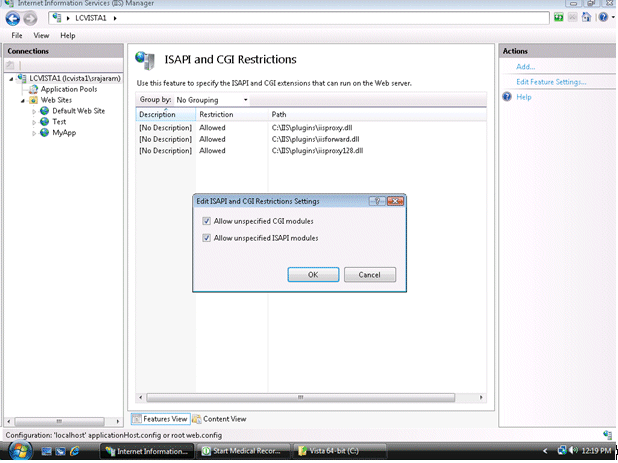
Description of "Figure 4-13 Editing ISAPI and CGI Restrictions"
-
Create a file called
iisproxy.iniwith the following contents and place it in the directory with the plug-in:WebLogicHost= @hostname@ WebLogicPort= @port@ ConnectRetrySecs=5 ConnectTimeoutSecs=25 Debug=ALL DebugConfigInfo=ON KeepAliveEnabled=true WlForwardPath=/weblogic PathTrim=/weblogic WLLogFile=@Log file name@ SecureProxy=OFF
-
Open the Internet Explorer browser and enter
http://<hostname>:<port>. You should be able to see the Medrec Sample Application from your Weblogic Server.If you want to run the plug-in in SSL mode, change the value of
WeblogicPortto the SSL port of your application, and change theSecureProxyvalue to ON.
Proxying Requests from Multiple Virtual Web Sites to WebLogic Server
To proxy requests from multiple Web sites (defined as virtual directories in IIS) to WebLogic Server:
-
Create a new directory for the virtual directories. This directory will contain dll and ini files used to define the proxy.
-
Copy
iisforward.dllto the directory you created in step1. -
Register the
iisforward.dllfor each website with IIS. -
Create a file called
iisforward.ini. Place this file in the same directory that containsiisforward.dll. This file should contain the following entry for each virtual website defined in IIS:vhostN=websiteName:port websiteName:port=dll_directory/iisproxy.ini
Where:
-
N is an integer representing the virtual website. The first virtual website you define should use the integer 1 and each subsequent website should increment this number by 1.
-
websiteNameis the name of the virtual website as registered with IIS. -
portis the port number where IIS listens for HTTP requests. -
dll_directoryis the path to the directory you created in step 1.
For example:
vhost1=strawberry.com:7001 strawberry.com:7001=c:\strawberry\iisproxy.ini vhost2=blueberry.com:7001 blueberry.com:7001=c:\blueberry\iisproxy.ini ...
-
-
Create an
iisproxy.inifile for the virtual Web sites, as described in step 4 in Proxying Requests. Copy thisiispoxy.inifile to the directory you created in step 1. -
Copy
iisproxy.dllto the directory you created in step 1. -
In IIS 5.0, set the value for the Application Protection option to high (isolated). If the Application Protection option is set to Medium(pooled), the iisproxy.dll that registered as the first website will always be invoked. In this event, all the requests will be proxied to the same WebLogic Server instances defined in the
iisproxy.iniof the first website.For IIS 6.0 and later, create a separate application pool for each virtual directory.
As described in "Creating Application Pools (IIS 6.)" (
http://www.microsoft.com/technet/prodtechnol/WindowsServer2003/Library/IIS/93275ef2-2f85-4eb1-8b92-a67545be11b4.mspx?mfr=true), you can isolate different Web applications or Web sites in pools, which are called application pools. In an application pool, process boundaries separate each worker process from other worker processes so that when an application is routed to one application pool, applications in other application pools do not affect that application.
Sample iisproxy.ini File
Here is a sample iisproxy.ini file for use with a single, non-clustered WebLogic Server. Comment lines are denoted with the “#” character.
# This file contains initialization name/value pairs # for the IIS/WebLogic plug-in. WebLogicHost=localhost WebLogicPort=7001 ConnectTimeoutSecs=20 ConnectRetrySecs=2
Here is a sample iisproxy.ini file with clustered WebLogic Servers. Comment lines are denoted with the “#” character.
# This file contains initialization name/value pairs # for the IIS/WebLogic plug-in. WebLogicCluster=myweblogic.com:7001,yourweblogic.com:7001 ConnectTimeoutSecs=20 ConnectRetrySecs=2
Note:
If you are using SSL between the plug-in and WebLogic Server, the port number should be defined as the SSL listen port.Creating ACLs Through IIS
ACLs will not work through the Microsoft Internet Information Server Plug-In if the Authorization header is not passed by IIS. Use the following information to ensure that the Authorization header is passed by IIS.
When using Basic Authentication, the user is logged on with local log-on rights. To enable the use of Basic Authentication, grant each user account the Log On Locally user right on the IIS server. Two problems may result from Basic Authentication's use of local logon:
-
If the user does not have local logon rights, Basic Authentication does not work even if the FrontPage, IIS, and Windows NT configurations appear to be correct.
-
A user who has local log-on rights and who can obtain physical access to the host computer running IIS will be permitted to start an interactive session at the console.
To enable Basic Authentication, in the Directory Security tab of the console, ensure that the Allow Anonymous option is “on” and all other options are “off”.
Setting Up Perimeter Authentication
Use perimeter authentication to secure your WebLogic Server applications that are accessed via the Microsoft Internet Information Server Plug-In.
A WebLogic Identity Assertion Provider authenticates tokens from outside systems that access your WebLogic Server application, including users who access your WebLogic Server application through the Microsoft Internet Information Server Plug-In. Create an Identity Assertion Provider that will safely secure your Plug-In as follows:
-
Create a custom Identity Assertion Provider on your WebLogic Server application. See "How to Develop a Custom Identity Assertion Provider" in Developing Security Providers for Oracle WebLogic Server.
-
Configure the custom Identity Assertion Provider to support the "Cert" token type and make it the active token type. See "How to Create New Token Types" in Developing Security Providers for Oracle WebLogic Server.
-
Set the
clientCertProxyattribute to True in the web.xml deployment descriptor file for the Web application (or, if using a cluster, optionally set theClient Cert Proxy Enabledattribute to true for the whole cluster on the Administration Console Cluster-->Configuration-->General tab). See "context-param" in Developing Web Applications, Servlets, and JSPs for Oracle WebLogic Server. -
Once you have set
clientCertProxy, be sure to use a connection filter to ensure that WebLogic Server accepts connections only from the machine on which the Microsoft Internet Information Server Plug-In is running. See "Using Network Connection Filters" in Programming Security for Oracle WebLogic Server. -
Web server plug-ins require a trusted Certificate Authority file in order to use SSL between the plug-in and WebLogic Server. Use Sun Microsystems' keytool utility to export a trusted Certificate Authority file from the
DemoTrust.jkskeystore file that resides inWL_HOME/server/lib.-
To extract the wlsdemoca file, for example, use the command:
keytool -export -file trustedcafile.der -keystore DemoTrust.jks -alias wlsdemoca
Change the alias name to obtain a different trusted CA file from the keystore.
To look at all of the keystore's trusted CA files, use:
keytool -list -keystore DemoTrust.jks.Press enter if prompted for password.
-
To convert the Certificate Authority file to pem format:
java utils.der2pem trustedcafile.der.
See "Identity Assertion Providers" in Developing Security Providers for Oracle WebLogic Server for more information about Identity Assertion Providers.
-
Using SSL with the Microsoft Internet Information Server Plug-In
You can use the Secure Sockets Layer (SSL) protocol to protect the connection between WebLogic Server and the Microsoft Internet Information Server Plug-In. The SSL protocol provides confidentiality and integrity to the data passed between the Microsoft Internet Information Server Plug-In and WebLogic Server.
The Microsoft Internet Information Server Plug-In does not use the transport protocol (http or https) to determine whether the SSL protocol will be used to protect the connection between the proxy plug-in and the Microsoft Internet Information Server. In order to use the SSL protocol with the Microsoft Internet Information Server Plug-In, configure the WebLogic Server instance receiving the proxied requests to use the SSL protocol. The port on the WebLogic Server that is configured for secure SSL communication is used by the Microsoft Internet Information Server Plug-In to communicate with the Microsoft Internet Information Server.
To use the SSL protocol between Microsoft Internet Information Server Plug-In and WebLogic Server:
-
Configure WebLogic Server for SSL. For more information, see Configuring SSL.
-
Configure the WebLogic Server SSL listen port. For more information, see Configuring SSL.
-
Set the WebLogicPort parameter in the
iisproxy.inifile to the listen port configured in step 2. -
Set the SecureProxy parameter in the
iisproxy.inifile to ON. -
Set additional parameters in the
iisproxy.inifile that define the SSL connection. For a complete list of parameters, see SSL Parameters for Web Server Plug-Ins.
For example:
WebLogicHost=myweblogic.com WebLogicPort=7002 SecureProxy=ON
Proxying Servlets from IIS to WebLogic Server
You can proxy servlets by path if the iisforward.dll is registered as a filter. You would then invoke your servlet with a URL similar to the following:
http://IISserver/weblogic/myServlet
To proxy servlets if iisforward.dll is not registered as a filter, you must configure servlet proxying by file type.To proxy servlets by file type:
-
Register an arbitrary file type (extension) with IIS to proxy the request to the WebLogic Server, as described in step 2 under Installing and Configuring the Microsoft Internet Information Server Plug-In.
-
Register your servlet in the appropriate Web Application. For more information on registering servlets, see Creating and Configuring Servlets.
-
Invoke your servlet with a URL formed according to this pattern:
http://www.myserver.com/virtualName/anyfile.ext
where virtualName is the URL pattern defined in the
<servlet-mapping>element of the Web Application deployment descriptor (web.xml) for this servlet and ext is a file type (extension) registered with IIS for proxying to WebLogic Server. The anyfile part of the URL is ignored in this context.Note:
If the image links called from the servlet are part of the Web Application, you must also proxy the requests for the images to WebLogic Server by registering the appropriate file types (probably .gif and .jpg) with IIS. You can, however, choose to serve these images directly from IIS if desired.If the servlet being proxied has links that call other servlets, then these links must also be proxied to WebLogic Server, conforming to the pattern described in step 3.
Testing the Installation
After you install and configure the Microsoft Internet Information Server Plug-In, follow these steps for deployment and testing:
-
Make sure WebLogic Server and IIS are running.
-
Save a JSP file into the document root of the default Web Application.
-
Open a browser and set the URL to the IIS plus filename.jsp, as shown in this example:
http://myii.server.com/filename.jsp
If filename.jsp is displayed in your browser, the plug-in is functioning.
Connection Errors and Clustering Failover
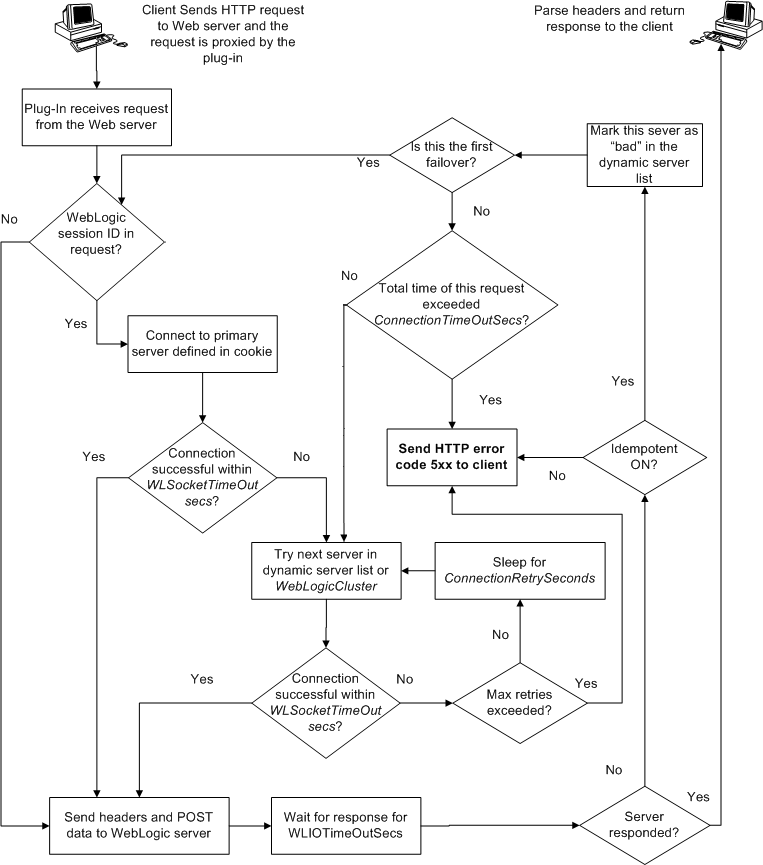
When the Microsoft Internet Information Server Plug-In attempts to connect to WebLogic Server, the plug-in uses several configuration parameters to determine how long to wait for connections to the WebLogic Server host, and, after a connection is established, how long the plug-in waits for a response. If the plug-in cannot connect or does not receive a response, the plug-in attempts to connect and sends the request to other WebLogic Servers in the cluster. If the connection fails or there is no response from any WebLogic Server instance in the cluster, an error message is sent.
Figure 4-15 demonstrates how the plug-in handles failover.
Possible Causes of Connection Failures
Failure of the WebLogic Server host to respond to a connection request could indicate problems with the host machine, networking problems, or other server failures.
Failure of any WebLogic Server instance in the cluster to respond, could indicate that WebLogic Server is not running or is unavailable, a hung server, a database problem, or other application failure.
Failover with a Single, Non-Clustered WebLogic Server
If you are running only a single WebLogic Server, the plug-in only attempts to connect to the server defined with the WebLogicHost parameter. If the attempt fails, an HTTP 503 error message is returned. The plug-in continues trying to connect to WebLogic Server as determined by the ConnectTimeoutSecs and ConnectRetrySecs parameters.
The Dynamic Server List
The WebLogicCluster parameter is required to proxy to a list of back-end servers that are clustered, or to perform load balancing among non-clustered managed server instances.
In the case of proxying to clustered managed servers, when you use the WebLogicCluster parameter in your httpd.conf or weblogic.conf file to specify a list of WebLogic Servers, the plug-in uses that list as a starting point for load balancing among the members of the cluster. After the first request is routed to one of these servers, a dynamic server list is returned containing an updated list of servers in the cluster. The updated list adds any new servers in the cluster and deletes any that are no longer part of the cluster or that have failed to respond to requests. This list is updated automatically with the HTTP response when a change in the cluster occurs.
Failover, Cookies, and HTTP Sessions
When a request contains session information stored in a cookie or in the POST data, or encoded in a URL, the session ID contains a reference to the specific server instance in which the session was originally established (called the primary server). A request containing a cookie attempts to connect to the primary server. If that attempt fails, the plug-in attempts to make a connection to the next available server in the list in a round-robin fashion. That server retrieves the session from the original secondary server and makes itself the new primary server for that same session. For more information see Figure 4-15.
Note:
If the POST data is larger than 64K, the plug-in will not parse the POST data to obtain the session ID. Therefore, if you store the session ID in the POST data, the plug-in cannot route the request to the correct primary or secondary server, resulting in possible loss of session data.