1 Integrating With Oracle Identity Manager, Preferred Method
This chapter contains the following sections:
1.1 Overview
Oracle® Identity Analytics software and Oracle Identity Manager (OIM) software work together seamlessly when integrated using the Thor-API connection mechanism. When integrated, Oracle Identity Manager serves as the automated provisioning and identity synchronization solution, while Oracle Identity Analytics defines the Role-based Access Control (RBAC) framework, the attestation process, and the approach to Segregation of Duties (SoD) policy enforcement. Rather than assigning individual access entitlements, the RBAC framework allows organizations to assign and unassign roles as a means of controlling user access on various applications.
In a fully-integrated scenario, provisioning and role management works in the following manner:
-
OIM is the authoritative source for users, accounts, and entitlements. Any update made to the users or their corresponding accounts is done in OIM.
-
Oracle Identity Analytics is the authoritative source for role management and role membership. Oracle Identity Analytics is also the authoritative source for policy entitlement definitions. (Roles in Oracle Identity Analytics correspond to roles in OIM 11.x, and groups in OIM 9.x. Further, policies in Oracle Identity Analytics correspond to access policies in OIM.)
-
All roles are defined and created in Oracle Identity Analytics. All entitlements for policies and role-to-user relationships are managed from Oracle Identity Analytics.
-
Role, Policy, and Role-Membership updates should no longer be made in Oracle Identity Manager.
1.2 Introduction
This section describes how to configure Oracle Identity Analytics (OIA) and Oracle Identity Manager (OIM) so that the two products can be used together. This newer, preferred integration method uses database imports for users, accounts, and user-role memberships, which allows for incremental imports from Oracle Identity Manager.
Oracle Identity Analytics 11gR1 PS1 (11.1.1.5.0) supports the following versions of Oracle Identity Manager:
-
Oracle Identity Manager version 9.1.0.2 BP17 (and higher)
-
Oracle Identity Manager 11gR1 PS1 (11.1.1.5.0) (and higher)
The 11.1.1.5.0 release of Oracle Identity Analytics does not support Oracle Identity Manager 11gR1 (version 11.1.1.3.0).
1.3 Understanding Terminology in Oracle Identity Analytics and Oracle Identity Manager
The following table maps Oracle Identity Analytics terminology to Oracle Identity Manager terminology.
Table 1-1 Comparing Oracle Identity Analytics Terminology and Oracle Identity Manager 9.x and 11g Terminology
| Oracle Identity Analytics Terminology | Oracle Identity Manager Terminology |
|---|---|
|
Resource Type |
Resource Object |
|
Resource Type Attributes (NameSpace Attributes) |
Provisioning Attributes and Entitlements |
|
Resource |
IT Resource |
|
Global Users |
Users or Xellerate End Users |
|
Roles |
Groups (9.x) / Roles (11g) |
|
Policies |
Access Policies |
1.4 To Configure Oracle Identity Analytics and Oracle Identity Manager to Work Together (Preferred Integration Method)
Before You Begin -
-
At least Oracle Identity Manager version 9.1.0.2 BP17 or version 11.1.1.5.0 (11gR1 PS1) is required. (Oracle Identity Manager 11gR1 (version 11.1.1.3.0) is not supported.)
-
At least Oracle Identity Analytics 11.1.1.5.0 is required.
-
This integration does not support XL.UserIDReuse=true in OIM.
-
If you will be deploying Oracle Identity Analytics and Oracle Identity Manager to separate WebSphere servers, then complete the steps in Appendix A, "Preparing to Integrate Oracle Identity Manager and Oracle Identity Analytics on WebSphere," before continuing with these steps.
-
Both Oracle Identity Manager and Oracle Identity Analytics should be installed on servers running the same version of the application server software, as well as the same version of the Java® Virtual Machine (JVM).
Note:
If Oracle Identity Manager and Oracle Identity Analytics are installed on a WebLogic cluster (WebLogic versions 10.3.3 or 10.3.4, only), follow these steps to patch WebLogic before continuing. You do not need to patch WebLogic version 10.3.5.
-
Go to the My Oracle Support website (
https://support.oracle.com) and choose Patches & Updates in the menu. -
Download Patch Number 10155450 for WebLogic 10.3.3.
You can also download the patch by searching for Smart Update Patch ID JUS4.
-
Use the SmartUpdate tool to install the patch to all nodes of the cluster for both OIM and OIA.
-
Regenerate the OIM server
wlfullclient.jarfile and copy the new JAR file to all OIA server instances.
-
Copy the required Oracle Identity Manager API JAR files to Oracle Identity Analytics.
See Section 1.4.1, "Step 1: Copy the Required Files From the OIM Server."
-
In Oracle Identity Analytics, edit the required and optional configuration files.
See Section 1.4.2, "Step 2: Edit the Oracle Identity Analytics Configuration Files."
-
In Oracle Identity Manager, log on to the Design Console and edit the required forms.
See Section 1.4.3, "Step 3: Modify the Oracle Identity Manager Forms Using the Form Designer."
-
In Oracle Identity Manager, configure the data collection scheduler.
See Section 1.4.4, "Step 4: Configure the Oracle Identity Manager Data Collection Scheduler."
-
In Oracle Identity Analytics, create a connection to Oracle Identity Manager. Establish a connection by entering authentication details.
See Section 1.4.5, "Step 5: Configure Oracle Identity Analytics to Connect to Oracle Identity Manager."
-
In Oracle Identity Analytics, import data from Oracle Identity Manager.
-
To send real time changes from Oracle Identity Analytics to Oracle Identity Manager, change the Oracle Identity Analytics configuration files related to workflows.
-
In Oracle Identity Manager, review automatic role assignment and role management.
1.4.1 Step 1: Copy the Required Files From the OIM Server
-
Copy the following Oracle Identity Manager Java API JAR files located in the <OIMDesignConsole>
/libfolder to the Oracle Identity Analytics $RBACX_HOME/WEB-INF/libfolder:-
xlAPI.jar -
xlCache.jar -
xlDataObjectBeans.jar -
xlDataObjects.jar -
xlScheduler.jar -
xlUtils.jar -
xlVO.jar
-
-
Copy the following JAR files located in the <IDM-HOME>
/server/libfolder to the Oracle Identity Analytics $RBACX_HOME/WEB-INF/libfolder:-
xlCrypto.jar -
wlXLSecurityProviders.jar -
xlAuthentication.jar -
xlLogger.jar
-
-
Copy the
configfolder located at <OIMDesignConsole>/configand paste it in the Oracle Identity Analytics $RBACX_HOME/xelleratefolder. Create thexelleratefolder if it does not exist.Note:
The "config" folder must be copied from an OIM Design Console directory that has been preconfigured to communicate with Oracle Identity Manager.
In other words, even if the operating systems of the computers hosting the OIM Design Console and Oracle Identity Manager are different, the "config" folder must be copied from an OIM Design Console directory which is configured to communicate with Oracle Identity Manager.
-
If using at least Oracle Identity Manager 11.1.1.5.0 ( 11gR1 PS1), copy the following OIM files to the Oracle Identity Analytics $RBACX_HOME
/WEB-INF/libfolder:-
oimclient.jarUse the version located in the <OIMDesignConsole>
/libfolder. (Important: Do not use a copy of this JAR file located in any other directory.) -
iam-platform-utils.jarThis file is located in the <OIMDesignConsole>
/libfolder.
-
-
If Oracle Identity Manager 11.1.2.x ( 11gR2), copy the following OIM files to the Oracle Identity Analytics $RBACX_HOME/rbacx_staging
/WEB-INF/libfolder-
jrf-api.jarThis file is located at MIDDLEWARE_HOME//oracle_common/modules/oracle.jrf_11.1.1 folder.
-
-
If deploying to a WebLogic application server, and if Oracle Identity Analytics and Oracle Identity Manager are on different WebLogic domains, copy the <WLS-HOME>
/server/lib/wlfullclient.jarfile to the Oracle Identity Analytics $RBACX_HOME/WEB-INF/libfolder.Note - If the
wlfullclient.jarfile is not present, follow these steps to generate it:-
Type cd<WLS-HOME>
/server/lib, where <WLS-HOME> is the base WebLogic installation directory -
Type
java -jar wljarbuilder.jar -
Copy the
wlfullclient.jarfile to the $RBACX_HOME/WEB-INF/libfolder
-
1.4.2 Step 2: Edit the Oracle Identity Analytics Configuration Files
-
Stop Oracle Identity Analytics.
-
Enable Oracle Identity Manager as a supported provisioning server by editing
iam-context.xmlin the $RBACX_Home/WEB-INFfolder as follows:-
Uncomment the following lines at the start of
iam-context.xml:<import resource="oim-commons-context.xml"/> <import resource="oim-11g-context.xml"/> <!-- This also works with at least Oracle Identity Manager 9.1.0.2 BP17-->
-
Enable the following:
<entry key="oracle"> <ref bean="oimSolution"/> </entry>
-
Save your changes.
-
-
(Optional) To map Oracle Identity Manager extended attributes to Oracle Identity Analytics custom properties, add the following mappings to
oim-commons-context.xmlas appropriate:-
For Users, complete the mapping by updating the value attribute with the Oracle Identity Manager extended attribute name, as follows:
<util:map id="iamUserToUserCustomProperties"> <!--entry key="customProperty1" value="USR_UDF_CUSTOM1"/> <entry key="customProperty2" value="usr_udf_cust2"/> <entry key="customProperty19" value="usr_udf_cust19"/--> </util:map>
-
For Roles, complete the mapping by updating the value attribute with the Oracle Identity Manager extended attribute name, as follows:
-
For OIM 9.x use capital letters for the value:
<util:map id="iamRoleCustProperties"> <!--entry key="customProperty1" value="UGP_UDF_CUSTOM1"/--> </util:map>
-
For OIM 11.x use lowercase letters for the value:
<util:map id="iamRoleCustProperties"> <!--entry key="customProperty1" value="ugp_udf_custom1"/--> </util:map>
-
Save your changes.
-
-
Start Oracle Identity Analytics.
-
Edit $RBACX_HOME
/conf/oimjdbc.properties. This should contain the Oracle Identity Manager database information.-
Run the OIA Property Encryption Utility to encrypt the database password located in the
oimjdbc.propertiesfile.For details, see the Administrator's Guide for Oracle Identity Analytics, "Securing Oracle Identity Analytics" chapter, "Understanding the Property Encryption Utility" section.
-
Open the
oim-11g-context.xmlfile for editing and search for the word password. -
Comment out the
oim.jdbc.passwordline and uncomment theoim.jdbc.password.encryptedline.The XML should look like the following sample:
<property name="URL" value="${oim.jdbc.url}"/> <property name="user" value="${oim.jdbc.username}"/> <!--<property name="password" value="${oim.jdbc.password}"/>--> <property name="password" value="${oim.jdbc.password.encrypted}"/> -
Save your changes.
-
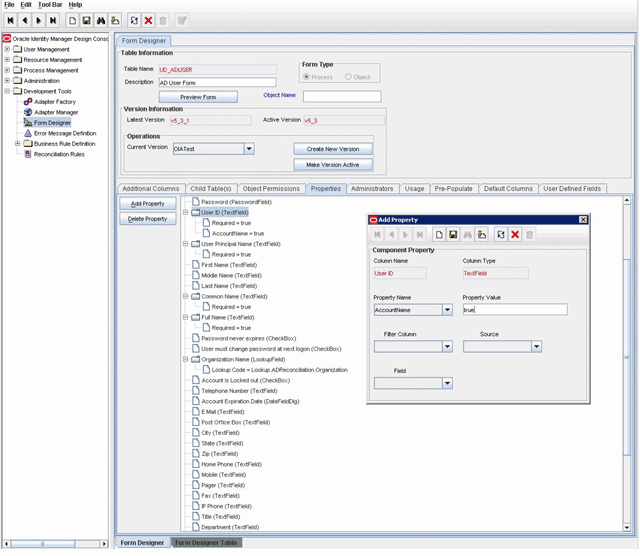
1.4.3 Step 3: Modify the Oracle Identity Manager Forms Using the Form Designer
In this step you will open Form Designer and, for each OIM resource, add the properties that OIA needs to exchange data with OIM.
-
Log in to the Oracle Identity Manager Design Console.
-
Open the Form Designer.
-
For each Resource, the following properties need to be added to some identified feed for accounts, policies, and entitlements imports:
-
AccountName - Identifies the unique account in the target system
-
ITResource - Identifies the unique IT Resource field for the target system
-
Entitlement - Identifies the account attribute designated for privileges
-
OIAParentAttribute - This property identifies the parent or mandatory entitlement attributes.
Add this property only if you have installed at least OIM 11.1.1.5.0 or at least OIM 9.1.0.2 BP17.
Complete this step as follows:
-
Locate the Process Form for the given resource.
Note:
The
AccountNameandITResourceproperties are on the parent form, and theEntitlementandOIAParentAttributeproperties are on the child form. -
Open the child Process Form and create a new version.
-
Click the Properties tab.
-
Locate ONLY ONE entitlement field per form, click Add Property, and add the
Entitlement = trueproperty setting.If there are multiple Entitlement child forms, add one
Entitlement = trueproperty setting per Entitlement form. -
If you have installed at least OIM 11.1.1.5.0 or at least OIM 9.1.0.2 BP17, add the
OIAParentAttributeproperty.Note:
For OIM 11.1.1.5.0, first create the
OIAParentAttributeproperty as a custom property. You only need to do this once.-
In the Design Console, expand Administration and click Lookup Definition.
-
In the Code text box, type
Lookup.FormField.Custom.Propertiesand click Search.The available custom properties are displayed.
-
Click Add to add the
OIAParentAttributeproperty.
To add the
OIAParentAttributeproperty to the form, do the following:Locate ONLY ONE entitlement field per form, click Add Property, and add the
OIAParentAttribute = trueproperty setting. (If you cannot find theOIAParentAttributeproperty, create it as a custom property. See the steps in the note box.)If there are multiple Entitlement child forms, add one
OIAParentAttribute = trueproperty setting per Entitlement form. -
-
Save the child form and make it active.
Note:
If there are multiple child forms, update all of them by repeating steps d, e, and f, before going to the next step.
-
Locate the parent process form and create a new version.
-
Click the Properties tab.
-
Locate the field that uniquely identifies the account in the target system, click Add Property, and add the
AccountName = trueproperty setting. See the following screen capture for an example. -
Locate the
ITResourcefield for the target system, click Add Property, and add theITResource = trueproperty setting. -
Save the parent form and make it active.
-
-
Repeat for each Resource.
-
Restart the Oracle Identity Analytics server.
1.4.4 Step 4: Configure the Oracle Identity Manager Data Collection Scheduler
Use the following steps to register the Oracle Identity Manager scheduled task that is required to support the OIA-OIM integration.
Before You Begin - Verify that the OIM installation/upgrade script created the DataCollection Schedule Job in OIM and that the job is enabled but not scheduled for execution. Your integration will not work without this important job.
Follow these steps to register the task with OIM:
-
Enable the DataCollection Schedule task if you are using Oracle Identity Manager 9.1.0.2. (If you are using at least Oracle Identity Manager 11.1.1.5.0, the DataCollection Schedule task is already enabled so you should skip this step.)
To enable the DataCollection Schedule task, open the Design Console, search for the DataCollection Schedule task, and make it Active.
-
Enable the following system property in Oracle Identity Manager by setting the value to TRUE:
OIM.IsOIAIntegrationEnabled = TRUENote:
The OIM.IsOIAIntegrationEnabled system property needs to be enabled before role memberships are added in OIM. If the property is not turned on, incremental role memberships will not work. You will need to do a full import of role memberships at least once after this property is enabled.
1.4.5 Step 5: Configure Oracle Identity Analytics to Connect to Oracle Identity Manager
-
Log in to Oracle Identity Analytics.
-
Choose Administration > Configuration.
-
Click Provisioning Servers.
-
Click New Provisioning Server Connection.
The New Provisioning Server Connection wizard asks you to choose the type of provisioning server connection that you want to create.
-
From the Type of Provisioning Server Connection drop-down menu, select oracle and click Next.
-
Complete the form:
-
Server Name - Type the Oracle Identity Manager server name.
-
Xellerate Home - Type the path to the
xelleratefolder in OIM. (Example:C:\oracle\xellerate)If Oracle Identity Manager is on a separate machine, create a local
xelleratefolder and copy theconfigfolder from<OIMDesignConsole>in thexelleratefolder. -
Login Config - Type the path to the authentication configuration (
auth<AS>.conf) file. (Example:C:\oracle\xellerate\config\authwl.conf) -
User Name - Enter the OIM user name. (For example,
xelsysadm.) The specified OIM user needs to have system administrator privileges. -
Password - Enter the OIM password.
-
-
Click Save.
1.4.6 Step 6: Import the Oracle Identity Manager (OIM) Data Into Oracle Identity Analytics (OIA)
Complete this step if you have data in Oracle Identity Manager that you want to use to populate the Oracle Identity Analytics Identity Warehouse. Importing data about Users, Resources, Entitlements, and so on, eliminates the need to manually create this information in Oracle Identity Analytics.
WARNING:
Importing data from Oracle Identity Manager into Oracle Identity Analytics using this procedure should be a one-time event that takes place when first configuring the systems or when new objects are added in OIM.
Schedule or run the import jobs in the following order:
-
Import Resource Metadata. See Section 1.4.6.1, "To Import Resource Metadata" for details.
-
Validate that the Parent attribute is set. See Section 1.4.6.2, "To Validate That the Parent Attribute for Each Attribute Category is Set" for details
-
Import Resources. See Section 1.4.6.3, "To Import Resources" for details.
-
Import the Glossary Data. See Section 1.4.6.4, "To Import Glossary Data" for details.
-
Import Policies. See Section 1.4.6.5, "To Import Policies" for details.
-
Import Roles. See Section 1.4.6.6, "To Import Roles" for details.
-
Import Users, Accounts, User Role Memberships, and Entitlements. See Section 1.4.6.7, "To Import Users, Accounts, User Role Memberships, and Entitlements" for details.
-
Verify each import. See Section 1.4.6.8, "To Verify That Each Import Job Completed Successfully" for details.
Understanding how Resource-Attribute Value Import Methods Affect Item-Risk Settings in OIA:
You can import Resource-Attribute Values (also called Entitlements) when you import Glossary data, when you import Accounts, and when you import Policies.
When you import an Attribute Value as part of a Glossary import, and the Attribute Value does not have a specified Item-Risk level, OIA uses the default Entitlements Risk-Mapping level instead. If you later change the Entitlements Risk-Mapping setting, the Item-Risk level for the Attribute Value is not affected.
When you import an Attribute Value as part of either an Account import or a Policy import, you cannot specify an Item-Risk level. Furthermore, OIA does not assign an Item-Risk level to the Attribute Value (the Item-Risk level remains null). After import, until you directly assign an Item-Risk level to the Value, the Attribute Value inherits the default Risk-Mapping value for Entitlements. This means that if you change the Entitlements Risk-Mapping value, the Attribute Value will inherit the new risk value. To prevent an Attribute Value from continuing to inherit the default Risk-Mapping value, directly assign an Item-Risk level to the Value.
For more information about Item-Risk and Risk-Mapping settings, see the Administrator's Guide for Oracle Identity Analytics, "Oracle Identity Analytics Identity Warehouse" chapter, "Understanding Item Risk and Risk-Factor Mappings."
1.4.6.1 To Import Resource Metadata
Before You Begin - You should only import resource metadata when you first configure the systems or when new resource objects are added in OIM.
-
Log in to Oracle Identity Analytics.
-
Choose Administration > Configuration.
-
Click Import/Export.
-
To start a new import job, choose Schedule Job > Import > Import Resource Metadata.
-
Under Data Selection Source, select the OIM connection that you created in "Step 5: Configure Oracle Identity Analytics to Connect to Oracle Identity Manager" and click Next.
-
Complete the form by entering the Name and Description of the Job.
-
Choose one of the following:
-
To run the job immediately, select the Run the Job Now option.
-
To schedule the job for later, clear the Run the Job Now option and enter the details of the scheduled job.
-
-
Click Finish to generate the Import Job.
The import resource metadata job runs on the scheduled date and time.
-
Set (or validate) the parent attribute for each attribute category by following the steps in Section 1.4.6.2, "To Validate That the Parent Attribute for Each Attribute Category is Set."
Complete this step as a validation step to verify that the parent attribute for each attribute category has been set appropriately.
-
Verify that the resource metadata was properly imported into Oracle Identity Analytics either by accessing the Oracle Identity Analytics Resources Types tab (choose Configuration > Resources Types), or by following the steps in Section 1.4.6.8, "To Verify That Each Import Job Completed Successfully."
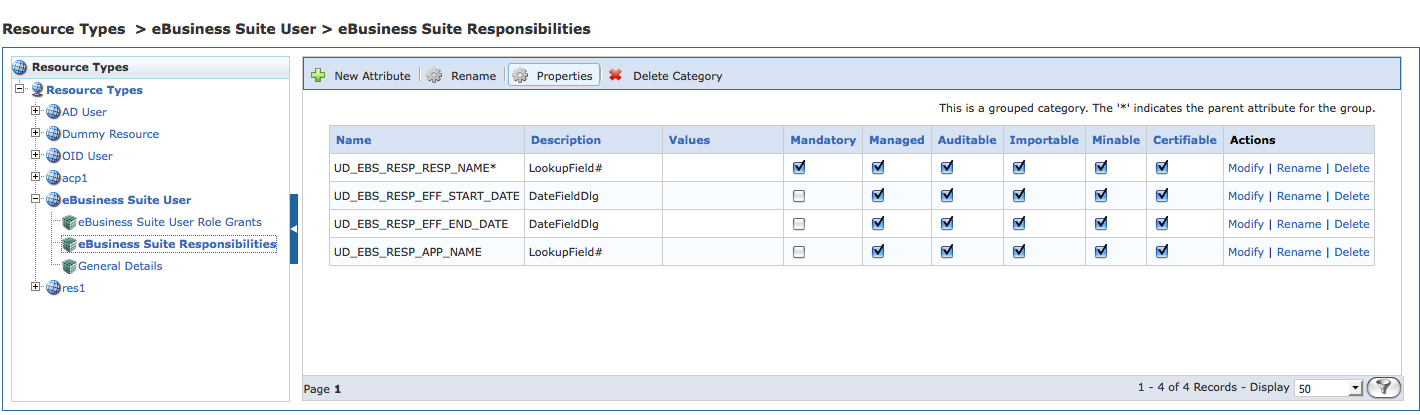
1.4.6.2 To Validate That the Parent Attribute for Each Attribute Category is Set
After Importing Resource Metadata, complete this step as a validation step to verify that the parent attribute for each attribute category has been set appropriately.
Note - This procedure is required if you are running at least OIA 11.1.1.5.0 and OIM 9.1.0.2 BP17, or if you are running at least OIA 11.1.1.5.0 and at least OIM 11.1.1.5.0. Follow these steps to manually assign the parent attribute for each attribute category.
-
Log in to Oracle Identity Analytics.
-
Choose Administration > Configuration.
-
Click Resource Types.
-
Click the + for each namespace to see the attribute categories for the selected Resource Type.
-
Click an attribute category. Attribute categories correspond to the child forms in OIM.
-
Click Properties in the menu.
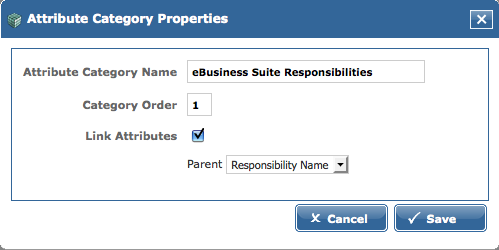
The Attribute Category Properties dialog box opens.
-
Do the following:
-
Verify that the Link Attributes option is selected and that the Parent list is set to the field that was marked as the
OIAParentAttributein OIM. -
If the correct field is not selected, choose the correct parent attribute from the Parent list and click Save.
-
1.4.6.3 To Import Resources
Before You Begin - You should only import resources when you first configure the systems or when new Resources are added in OIM.
Note:
An ITResource in OIM corresponds to a Resource in Oracle Identity Analytics.
-
If necessary, log in to Oracle Identity Analytics, choose Administration > Configuration, and click Import/Export.
-
To start the import resources job, choose Schedule Job > Import > Import Resources.
-
Under Data Selection Source, select the OIM connection that you created in "Step 5: Configure Oracle Identity Analytics to Connect to Oracle Identity Manager" and click Next.
-
Complete the form by typing a name and description for the job.
-
Choose one of the following tasks:
-
To run the job immediately, select the Run the Job Now option.
-
To schedule the job for later, clear the Run the Job Now option and enter the details of the scheduled job.
-
-
Click Finish to generate the import job.
The import resources job runs on the scheduled date and time.
-
Verify that the resources are imported into Oracle Identity Analytics from Identity Manager either by accessing the Oracle Identity Analytics Resources tab (choose Identity Warehouse > Resources), or by following the steps in Section 1.4.6.8, "To Verify That Each Import Job Completed Successfully."
1.4.6.4 To Import Glossary Data
Before You Begin - You should only import glossary data when you first configure the systems or when new entitlements are discovered in OIM through reconciliation.
Be sure that you understand how the various Resource-Attribute Value import methods affect Item-Risk settings in OIA. See the note in Section 1.4.6 for more information.
-
If necessary, log in to Oracle Identity Analytics, choose Administration > Configuration, and click Import/Export.
-
To start the import glossary job, choose Schedule Job > Import > Import Glossary.
-
Under Data Selection Source, select the OIM connection that you created in "Step 5: Configure Oracle Identity Analytics to Connect to Oracle Identity Manager" and click Next.
-
Complete the form by typing a name and description for the job.
-
Choose one of the following tasks:
-
To run the job immediately, select the Run the Job Now option.
-
To schedule the job for later, clear the Run the Job Now option and enter the details of the scheduled job.
-
-
Click Finish to generate the import job.
The import glossary job runs on the scheduled date and time.
-
Verify that the glossary data imported into Oracle Identity Analytics from Identity Manager either by following the steps in Section 1.4.6.8, "To Verify That Each Import Job Completed Successfully."
1.4.6.5 To Import Policies
Before You Begin - Oracle recommends that you only import policy data when you first integrate OIM and OIA.
Be sure that you understand how the various Resource-Attribute Value import methods affect Item-Risk settings in OIA. See the note in Section 1.4.6 for more information.
Note:
A policy in OIA cannot represent more than one resource type, whereas in OIM a single access policy can represent multiple resource types. Consequently, when you import an OIM policy that represents multiple resource types, OIA creates a policy instance for each resource type, and appends the name of the resource type to the policy name (for example, policy1-AD).
Following integration, you should deprecate the old OIM policies and stop using them. Instead, use the new OIA policies, which will be used for provisioning going forward.
-
If necessary, log in to Oracle Identity Analytics, choose Administration > Configuration, and click Import/Export.
-
To start the import policies job, choose Schedule Job > Import > Import Policies.
-
Under Data Selection Source, select the OIM connection that you created in "Step 5: Configure Oracle Identity Analytics to Connect to Oracle Identity Manager" and click Next.
-
Complete the form by typing a name and description for the job.
-
Choose one of the following tasks:
-
To run the job immediately, select the Run the Job Now option.
-
To schedule the job for later, clear the Run the Job Now option and enter the details of the scheduled job.
-
-
Click Finish to generate the import job.
The import policies job runs on the scheduled date and time.
-
Verify that the policies are imported into Oracle Identity Analytics from Identity Manager either by accessing the Oracle Identity Analytics Policies tab (choose Identity Warehouse > Policies), or by following the steps in Section 1.4.6.8, "To Verify That Each Import Job Completed Successfully."
1.4.6.6 To Import Roles
Before You Begin - Oracle recommends that you only import roles when you first integrate OIM and OIA.
Note:
-
When integrating with Oracle Identity Analytics, Oracle recommends that you no longer use OIM Automatic Role Assignment and Role Management.
-
Groups defined in OIM are imported as Roles within Oracle Identity Analytics. In addition, the OIM Group-to-Access-Policy relationship is imported as a Roles-Policy relationship in Oracle Identity Analytics. For the import to work, you should have already successfully completed a Policy import.
-
In addition, the OIM Group-User relationship is imported and recreated as a Role-User relationship in Oracle Identity Analytics. To establish the Role-User relationship, verify that you have already imported Users.
-
If necessary, log in to Oracle Identity Analytics, choose Administration > Configuration, and click Import/Export.
-
To start the import roles job, choose Schedule Job > Import > Import Roles.
-
Under Data Selection Source, select the OIM connection that you created in "Step 5: Configure Oracle Identity Analytics to Connect to Oracle Identity Manager" and click Next.
-
Complete the form by typing a name and description for the job.
-
Choose one of the following tasks:
-
To run the job immediately, select the Run the Job Now option.
-
To schedule the job for later, clear the Run the Job Now option and enter the details of the scheduled job.
-
-
Click Finish to generate the import job.
The import resources job runs on the scheduled date and time.
-
Verify that the roles are imported into Oracle Identity Analytics from Identity Manager either by accessing the Oracle Identity Analytics Roles tab (choose Identity Warehouse > Resources), or by following the steps in Section 1.4.6.8, "To Verify That Each Import Job Completed Successfully."
1.4.6.7 To Import Users, Accounts, User Role Memberships, and Entitlements
Note:
Oracle Identity Analytics does not allow the same account instance to be assigned to more than one user, whereas Oracle Identity Manager does allow the same account instance to be assigned to more than one user. When importing accounts from OIM, if the same account is assigned to more than one user, OIA will only import the account for the first user.
Before you Begin - Be sure that you understand how the various Resource-Attribute Value import methods affect Item-Risk settings in OIA. See the note in Section 1.4.6 for more information.
-
If necessary, log in to Oracle Identity Analytics, choose Administration > Configuration, and click Import/Export.
-
To start a new import job, choose Schedule Job > Import > Import Users, Accounts, User Role Memberships and Entitlements.
-
Under Data Selection Source, select the OIM connection that you created in "Step 5: Configure Oracle Identity Analytics to Connect to Oracle Identity Manager" and click Next.
-
Choose one of the following:
-
Load all resources defined in the system at the time the job is run - Choose this option to import data from all resources.
-
Load only those resources selected in the table - Choose this option to import data only from select resources. If you choose this option, select one or more resources in the table.
-
-
Complete the form as follows:
-
Type a name and description for the job.
-
In the Data to Load section, select the Entitlements option if you did not perform the Glossary Import job in Section 1.4.6.4. (Selecting Entitlements here refers to the list of all available entitlements in a system, and not individual user entitlements. Individual user entitlements are imported when accounts are imported regardless of how you set the Entitlements option.)
Select the User Role Membership option to import User-Role membership data.
-
In the Import Type section, choose one of the following:
-
Full - All entities found on the OIM server will be imported.
-
Incremental - All OIM entities updated since the last successful import will be imported.
-
-
Choose one of the following:
-
To run the job immediately, select the Run the Job Now option.
-
To schedule the job for later, clear the Run the Job Now option and enter the details of the scheduled job.
-
-
-
Click Finish to generate the import job.
The import job runs on the scheduled date and time.
-
Verify that the users, accounts, user role memberships, and entitlements are imported into Oracle Identity Analytics from Identity Manager either by accessing the Users View in Oracle Identity Analytics (choose Identity Warehouse > User), or by following the steps in Section 1.4.6.8, "To Verify That Each Import Job Completed Successfully."
1.4.6.8 To Verify That Each Import Job Completed Successfully
-
Log in to Oracle Identity Analytics.
-
Choose Administration > Auditing & Events.
-
Click Import/Export Logs.
-
In the table, find the entries for your import jobs.
-
Click the entry in the Description column to view the Import Log Details page.
-
Verify that the number or Oracle Identity Manager export records (Number of Output Records) and the number of Oracle Identity Analytics import records (Number of Input Records) are the same.
1.4.7 Step 7: Configure the Oracle Identity Analytics (OIA) Workflows to Export Data to Oracle Identity Manager (OIM)
This section describes how to configure workflows to export data in near real-time from Oracle Identity Analytics (OIA) to Oracle Identity Manager (OIM). As noted earlier, all roles are defined and created in Oracle Identity Analytics. Hence, Oracle Identity Analytics is the authoritative source for role management, role membership, and policy entitlement definitions.
For information about closed loop compliance, see Section 1.6, "Understanding Closed Loop Compliance."
-
Log in to Oracle Identity Analytics.
-
Choose Administration > Configuration.
-
Click Workflows.
A list of workflows displays.
-
The following workflows need to be modified:
-
Role-creation
-
Role-modification
-
Role-membership
-
Policy Modification
Modify each configuration file as follows:
-
Click the workflow name.
-
In the Steps table, scroll down and click the Finish step.
The Edit Workflow Step page opens.
-
Click Add Pre-Functions
The Pre-Functions pop-up opens.
-
In the pop-up, select "Export IAM Role Function."
-
Choose the Oracle Identity Manager connection name that you created previously.
-
Click Save.
Repeat these steps until the Role-creation, Role-modification, Role-membership, and Policy Modification workflows have been modified.
-
-
The "Role-User Membership Activation" workflow needs to be modified as follows:
-
Open the following file in a text editor:
$RBACX_HOME/conf/workflows/role-user-membership-activation-workflow.xml
-
Search for
step id="5". -
Update the XML fragment to match the following and save your changes:
Note:
Replace the placeholder oimConnectionName with the provisioning server name that points to the OIM server.
<step id="5" name="Finish"> <meta name="role.status.key">1</meta> <meta name="rolestatuslabel">Active</meta> <meta name="isMandetory">true</meta> <meta name="isEditable">false</meta> <pre-functions> <function type="spring"> <arg name="bean.name">addSIMRoleMembershipFunction</arg> </function> <function type="spring"> <arg name="bean.name">updateRequestStatusFunction</arg> <arg name="requestStatus">APPROVED</arg> </function> <function name="addIAMRoleMembershipFunction" type="spring"> <arg name="bean.name">addIAMRoleMembershipFunction</arg> <arg name="iamConnectionName">oimConnectionName</arg> </function> </pre-functions>
-
-
The "Mass Modification" workflow needs to be modified as follows:
-
Open the following file in a text editor:
$RBACX_HOME/conf/workflows/mass-modification-workflow.xml
-
Locate the following section of XML:
<!--<function name="exportIAMRoleBatchFunction" type="spring"> <arg name="bean.name">exportIAMRoleBatchFunction</arg> <arg name="iamConnectionName"/> </function>--> -
Uncomment the XML section, edit it to match the following, and save your changes:
Note:
Replace the placeholder oimConnectionName with the provisioning server name that points to the OIM server.
<function name="exportIAMRoleBatchFunction" type="spring"> <arg name="bean.name">exportIAMRoleBatchFunction</arg> <arg name="iamConnectionName">oimConnectionName</arg> </function> -
Restart OIA so that changes to the "Role-User Membership Activation" workflow and the "Mass Modification" workflow take effect.
-
-
The "Mass Membership Modification" workflow needs to be modified as follows:
-
Open the following file in a text editor:
$RBACX_HOME/conf/workflows/mass-membership-modification-workflow.xml
-
Add the following section of XML to the end of the list of pre-functions within the "Finish" step of the workflow:
<function name="exportIAMRoleMembershipBatchFunction" type="spring"> <arg name="bean.name">exportIAMRoleMembershipBatchFunction</arg> <arg name="iamConnectionName"/> </function>Note:
Replace the placeholder oimConnectionName with the provisioning server name that points to the OIM server.
-
Restart OIA so that changes to the "Mass Membership Modification" workflow take effect.
-
-
If OIA is installed in a clustered configuration, repeat step 5, 6, and 7 for each additional cluster node.
1.4.8 Step 8: Review Oracle Identity Manager Automatic Role Assignment and Role Management Settings
When integrating with Oracle Identity Analytics, Oracle recommends that you no longer use OIM Automatic Role Assignment and Role Management.
1.5 To Migrate From the Deprecated OIM-OIA Integration to the Preferred OIM-OIA Integration
If you have an older integration, the following steps must be performed before using the Oracle Identity Analytics 11.1.1.5.0 release. Otherwise, your data will be corrupted and you will end up with many unusable objects in the system.
Before You Begin - Synchronize your Oracle Identity Manager data with your Oracle Identity Analytics data. This step is important!
-
In Oracle Identity Analytics, rename the namespace names from the "Resource Type" names in OIM to the "Resource Object" names in OIM.
Note:
You will need to perform the following steps for each OIA namespace that is synchronized with the OIM namespace.
-
Log in to Oracle Identity Analytics.
-
Choose Administration > Configuration.
-
Click Resource Types.
-
Select the namespace in the tree on the left side of the page, then click Rename.
-
Type the new value in the pop-up.
Refer to the
iam-context.xmlfile in your OLDER installation, and go to the section with the namespaceMap:<property name = "namespaceMap"> <map> <entry key = "AD Server"> <value>AD User</value> </entry> </map> </property>
Previously, the namespace name in Oracle Identity Analytics used to be
AD Server, which corresponds to the key value. For the new integration to work, the namespace name in OIA should beAD User, which is present in the value element. -
Repeat these steps to manually replace the key with the OIA value for each namespace specified in the older
iam-context.xmlfile.
-
-
Import your Oracle Identity Manager data into Oracle Identity Analytics. \
This step is required because some minor changes need to be imported into OIA. Going forward, the way data is represented (accounts and policies, especially) can be updated and maintained.
1.6 Understanding Closed Loop Compliance
With the integration of Oracle Identity Analytics and Oracle Identity Manager, it is possible to directly revoke roles and entitlements from Oracle Identity Analytics if the results of the certification process require it. This integration eliminates the need for manual de-provisioning of access for managed resources. In addition, roles and entitlements can still be manually revoked by leveraging the information stored in the remediation configuration module. This takes into account non-managed applications.
If certification remediation is enabled, changes are propagated to Oracle Identity Manager either when the certification is complete, or when the certification end-date is reached (depending on configuration). OIM revokes or re-provisions target system accounts based on the revocations and certifications that occurred during the certification process.
Note:
When creating Data Owner certifications, you should only certify parent-level attributes imported from Oracle Identity Manager (attributes with the OIAParentAttribute property), not child-level attributes. If a child attribute is certified in a Data Owner certification, closed-loop remediation with OIM will not work.
Child-level attributes that were imported in a text file can be certified provided that the attributes are marked as certifiable using the Administration > Configuration > Resource Types > Resource page.
1.6.1 To Configure Resources in Oracle Identity Analytics for Remediation
Every resource type in Oracle Identity Analytics can be separately configured for automatic or manual remediation.
-
Log in to Oracle Identity Analytics.
-
Choose Identity Warehouse> Resources.
-
Click the resource for which remediation action needs to be configured, and go to the Remediation tab.
-
Select the Select Provisioning Mode check box.
-
Choose the mode of provisioning desired for the particular resource.
-
Auto - Automatically send role/entitlement updates linked with this resource to Oracle Identity Manager.
Select the appropriate connection name of the provisioning server and save the changes.
-
Manual - Use the manual steps for revocation of roles and entitlements using a text editor. List the steps to be followed for non-managed system remediation and save the changes.
-
1.6.2 To Configure Certifications in Oracle Identity Analytics for Remediation
-
Log in to Oracle Identity Analytics.
-
Choose Administration > Settings.
-
Click Identity Certification.
-
Expand the Revoke and Remediation section, and, under the Remediation section, choose one of the following options:
-
Display Remediation Instructions - Select to display instructions about how to perform manual remediation of nonmanaged resources.
-
Perform Closed Loop Remediation on - Select to specify that the remediation be completed by either the Certification End Date or the Certification Completion Date.
-
1.7 Scheduling Incremental Updates of Users, Accounts, User-Role Memberships, and Entitlements
The OIM-OIA Preferred Integration Method allows for incremental imports of users, accounts, user-role memberships, and entitlements from Oracle Identity Manager. Scheduled imports of users, accounts, user-role memberships, and entitlements are initially configured as part of the OIM-OIA configuration process. (See Section 1.4.6.7, "To Import Users, Accounts, User Role Memberships, and Entitlements" for more information.) Use the steps in this section to schedule additional imports, or to change an existing scheduled import.
-
Log in to Oracle Identity Analytics.
-
Choose Administration > Configuration.
-
Click Import/Export.
-
To start a new import job, choose Schedule Job > Import > Import Users, Accounts, User Role Memberships and Entitlements.
-
Under Data Selection Source, select the appropriate Connection Name and click Next.
-
Choose one of the following:
-
Load all resources defined in the system at the time the job is run - Choose this option to import data from all resources.
-
Load only those resources selected in the table - Choose this option to import data only from select resources. If you choose this option, select one or more resources in the table.
-
-
Complete the form as follows:
-
Type a name and description for the job.
-
In the Data to Load section, select the Entitlements option if, in addition to accounts and users, you also want to import the users' entitlements data. Otherwise, clear the Entitlements option box and only the accounts, users, and user-role membership data will be imported.
-
In the Import Type section, choose the following option:
Incremental - All OIM entities updated since the last successful import will be imported.
-
Choose one of the following:
-
To run the job immediately, select the Run the Job Now option.
-
To schedule the job for later, clear the Run the Job Now option and enter the details of the scheduled job.
-
Note:
For help understanding cron expressions, see "Oracle Identity Analytics Scheduling" in the System Integrator's section of the Administrator's Guide for Oracle Identity Analytics.
-
-
Click Finish to generate the import job.
The import job runs on the scheduled date and time.
-
Verify that the users, accounts, user role memberships, and entitlements are imported into Oracle Identity Analytics from Identity Manager either by accessing the Users View in Oracle Identity Analytics (choose Identity Warehouse > User), or by following the steps in Section 1.4.6.8, "To Verify That Each Import Job Completed Successfully."
1.8 Troubleshooting
- Issue 1
-
When OIA tries to connect to OIM, the following error is returned:
Illegal Argument Exception thrown ( No Configuration was registered that can handle the configuration named "xellerate" )
Solution: Manually set the security property
auth.login.confthroughJAVA OPTIONSbefore starting the application server:JAVA_OPTIONS="-Djava.security.auth.login.config= /..path../config/authwl.conf
- Issue 2
-
When starting OIA, the following error is returned:
Caused By: java.lang.LinkageError: loader constraint violation: loader (instance of weblogic/utils/classloaders/ChangeAwareClassLoader) previously initiated loading for a different type with name "javax/xml/namespace/QName"
Solution: If Oracle Identity Analytics and Oracle Identity Manager are deployed to the same WebLogic domain, remove the
wlfullclient.jarfile from the Oracle Identity Analytics $RBACX_HOME/WEB-INF/libfolder. This file is only required if Oracle Identity Analytics and Oracle Identity Manager are on different WebLogic domains. Thewlfullclient.jarfile allows client applications, such as Oracle Identity Analytics, to communicate with the WebLogic Server over the T3 protocol. - Issue 3
-
The following exception is received during integrated operations:
java.lang.NoClassDefFoundError:oracle/iam/platform/OIMClient at Thor.API.tcUtilityFactory.<init>(tcUtilityFactory.java:154) at com.vaau.rbacx.iam.oracle.OIMIAMSolution.getUtilityFactory(OIMIAMSolution.java: 2595) at com.vaau.rbacx.iam.oracle.OIMIAMSolution.readUsers(OIMIAMSolution.java)
Solution: Copy the following 11g Oracle Identity Manager Java API JAR file to the
$OIA-HOME/WEB-INF/libfolder in Oracle Identity Analytics:<OIMDesignConsole>
/lib/oimclient.jar - Issue 4
-
The following error is received during integrated operations:
Caused by: java.lang.NoClassDefFoundError: com/thortech/util/logging/Logger at Thor.API.tcUtilityFactory.<clinit>(tcUtilityFactory.java:80) at com.vaau.rbacx.iam.oracle.OIMIAMSolution.getUtilityFactory(OIMIAMSolution.java: 2595) at com.vaau.rbacx.iam.oracle.OIMIAMSolution.readUsers(OIMIAMSolution. java:770) at com.vaau.rbacx.iam.service.impl.RbacxIAMServiceImpl.importUsers (RbacxIAMServiceImpl.java:119)
Solution: Copy the OIM 11g logger JAR file
xlLogger10g.jarto
$RBACX_HOME/WEB-INF/lib - Issue 5
-
Errors similar to the following are written to the OIM log file while any import job is running. OIA does not report any errors.
<Warning> <RMI> <BEA-080003> <RuntimeException thrown by rmi server: weblogic.jndi.internal.AdminRoleBasedDispatchServerRef@9, implementation: 'weblogic.jndi.internal.RootNamingNode@fb777e3', oid: '9', implementationClassName: 'weblogic.jndi.internal.RootNamingNode' java.lang.SecurityException: [Security:090398]Invalid Subject: principals=[weblogic, Administrators]. java.lang.SecurityException: [Security:090398]Invalid Subject: principals=[weblogic, Administrators] at weblogic.security.service.SecurityServiceManager.seal(SecurityServiceManager.java: 835) at weblogic.security.service.SecurityServiceManager.getSealedSubjectFromWire (SecurityServiceManager.java:524) at weblogic.rjvm.MsgAbbrevInputStream.getSubject(MsgAbbrevInputStream.java:351) at weblogic.rmi.internal.BasicServerRef.acceptRequest(BasicServerRef.java:875) at weblogic.rmi.internal.BasicServerRef.dispatch(BasicServerRef.java:310) Truncated. see log file for complete stacktrace
Solution:
If Oracle Identity Manager and Oracle Identity Analytics are installed on a WebLogic cluster, follow these steps to patch WebLogic.
-
Go to the My Oracle Support website (
https://support.oracle.com) and choose Patches & Updates in the menu. -
Download Patch Number 10155450 for WebLogic 10.3.3.
You can also download the patch by searching for Smart Update Patch ID JUS4.
-
Use the SmartUpdate tool to install the patch to all nodes of the cluster for both OIM and OIA.
-
Regenerate the OIM server
wlfullclient.jarfile and copy the new JAR file to all OIA server instances.
-
- Issue 6
-
User imports from OIM will fail if the
userbatchsizeis set to a value greater than1000in theiam.propertiesfiles.Solution:
For User imports from OIM to work, Oracle recommends setting the batch size to a value of
1000or lower. - Issue 7
-
When integrating OIA with OIM 9.x the following error is logged:
ERROR [UDP] failed handling incoming message java.lang.OutOfMemoryError at java.util.ArrayList.<init>(ArrayList.java:138) at org.jgroups.protocols.TP.readMessageList(TP.java:1167) at org.jgroups.protocols.TP.access$500(TP.java:52) at org.jgroups.protocols.TP$IncomingPacket.run(TP.java:1417) at java.util.concurrent.ThreadPoolExecutor$Worker.runTask(ThreadPoolExecutor.java:665) at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:690) at java.lang.Thread.run(Thread.java:810)
There are two solutions for this issue. Solution 1 is the recommended solution.
Solution 1:
-
Stop Oracle Identity Analytics.
-
Edit the
$RBACX/WEB-INF/classes/oscache.propertiesfile by uncommenting the following two linescache.event.listeners=com.opensymphony.oscache.plugins.clustersupport.JavaGroupsBroadcastingListener,com.opensymphony.oscache.extra.CacheMapAccessEventListenerImpl
and the last
cache.cluster.properties= ....
( Uncomment the line that has the last property as
discard_incompatible_packets=true.) -
Open the
xlconfig.xmlfile on the OIA server that was copied in Step 1 and search for the following line:<MultiCastAddress>xxx.xxx.xxx.xxx</MultiCastAddress>
Comment out the line as follows:
<!-- <MultiCastAddress>xxx.xxx.xxx.xxx</MultiCastAddress> -->
-
Add the following lines, taking care to replace the
xxxwith the value of the IP address present in the XML file:<MultiCastConfiguration>UDP(mcast_addr=xxx.xx.xxx.xxx;mcast_port=45566;ip_ttl=32;mcast_send_buf_size=150000;mcast_recv_buf_size=80000):PING(timeout=2000; num_initial_members=3):MERGE2(min_interval=5000;max_interval=10000):FD_SOCK:VERIFY_SUSPECT(timeout=1500):pbcast.NAKACK(gc_lag=50;retransmit_timeout=300,600,1200,2400,4800; max_xmit_size=8192):UNICAST(timeout=300,600,1200,2400):pbcast.STABLE(desired_avg_gossip=20000):FRAG(frag_size=8096;down_thread=false;up_thread=false):pbcast.GMS(join_timeout=5000; join_retry_timeout=2000;shun=false;print_local_addr=true);discard_incompatible_packets=true</MultiCastConfiguration>
-
Restart Oracle Identity Analytics.
Solution 2:
In the rare case that Solution 1 does not solve the problem do the following:
-
Open the
$RBACX\WEB-INF\libfolder and get the filejgroups-all.jar. -
Unjar the file.
-
Recompile the
TP.javafile with the variabledrop_incompatible_packets = TRUE(the default isFALSE). -
Recompile the
jgroups-all.jarfile and put it back in the$RBACX\WEB-INF\libfolder.
You can also contact Support and request a copy of the
jgroups-all.jarfile that has thedrop_incompatible_packetsvariable set toTRUE. -
1.9 User Attribute Mappings Between OIM and OIA
The following table shows how OIM user attributes are mapped to OIA global user attributes during an OIM user import. The OIA columns are located in the oia_staging_users table.
Table 1-2 User Attribute Mappings Between OIM and OIA
| OIA Column Name | Type | OIM 9.1 Column | OIM 11g Column | Comments |
|---|---|---|---|---|
|
|
|
- |
- |
Primary key. |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
- |
|
|
|
|
|
- |
- |
|
|
|
|
- |
|
|
|
|
|
- |
|
|
|
|
|
- |
|
|
|
|
|
- |
|
|
|
|
|
- |
|
|
|
|
|
- |
- |
|
|
|
|
- |
|
|
|
|
|
- |
|
|
|
|
|
- |
|
|
|
|
|
|
|
|
|
|
|
- |
- |
|
|
|
|
- |
- |
|
|
|
|
- |
- |
|
|
|
|
- |
- |
|
|
|
|
|
|
|
|
|
|
- |
- |
|
|
|
|
- |
- |
|
|
|
|
- |
- |
|
|
through
|
|
- |
- |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
- |
- |
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
- |
- |
|
|
|
|
- |
- |
|
|
|
|
- |
- |
|
|
|
|
- |
|
|
|
|
|
- |
- |
The following table shows the database columns that map extended properties in OIM to custom properties in OIA.