10 Enabling LDAP Support in JD Edwards EnterpriseOne
Note:
This chapter contains updates for JD Edwards EnterpriseOne Tools Release 9.1 Update 3. All changes due to this release are noted in the text.This chapter contains the following topics:
-
Section 10.1, "Understanding LDAP Support in JD Edwards EnterpriseOne"
-
Section 10.2, "Configuring LDAP Support in JD Edwards EnterpriseOne"
-
Section 10.3, "Modifying the LDAP Default User Profile Settings"
Important:
This chapter does not provide instructions for installing and configuring an LDAP-compliant directory service, such as Microsoft Windows Active Directory or IBM Directory Server. For more information, refer to the Prerequisites section in this chapter.10.1 Understanding LDAP Support in JD Edwards EnterpriseOne
This section contains the following topics:
-
User Profile Management in LDAP-Enabled JD Edwards EnterpriseOne
-
Application Changes in LDAP-Enabled JD Edwards EnterpriseOne
10.1.1 LDAP Support Overview
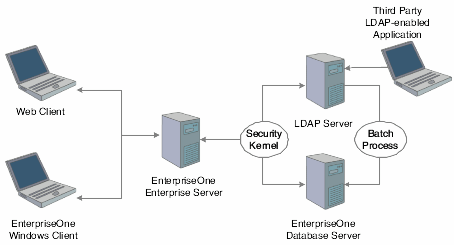
LDAP is an open industry standard protocol that directory services use to manage user profiles, such as user IDs and passwords, across multiple application systems. You can enable EnterpriseOne to use an LDAP-compliant directory service to manage EnterpriseOne user profiles and user-role relationships. After enabling EnterpriseOne for LDAP, user profiles can be administered through an LDAP version 3 compliant directory server, otherwise referred to as the LDAP server. System administrators use a third-party LDAP-enabled application to access the LDAP server.
LDAP provides these benefits:
-
Central administration and repository for user profiles.
You can easily maintain user profiles in a single location that serves multiple end user applications, including EnterpriseOne applications.
-
Reduced complexity.
You are not required to use several applications to maintain user profiles. In addition, users are not required to maintain multiple passwords across multiple systems.
Note:
LDAP support does not address single sign-on functionality that might exist through other EnterpriseOne functionality.10.1.2 User Profile Management in LDAP-Enabled JD Edwards EnterpriseOne
When EnterpriseOne is enabled for LDAP, the features used to manage user profiles in the User Profile Revisions application (P0092) are disabled. Instead, you must use a third-party, LDAP-enabled application to manage EnterpriseOne user profiles.
Note:
EnterpriseOne does not provide an application for managing LDAP user profiles.Additionally, EnterpriseOne provides a self-service version of P0092. This self-service application is used to manage only self-service user profile information for the Manufacturing Sourcing module; not EnterpriseOne user profiles. However, if you are enabling EnterpriseOne for LDAP and your company is using this self-service application, you can add parameters for it when you define the LDAP server settings. In this configuration, any self-service user profiles that are added are synchronized with the LDAP server.
Note:
Even though self-service user profiles are synchronized with the LDAP server, you cannot use this self-service application to manage EnterpriseOne or LDAP user profiles.10.1.3 LDAP and JD Edwards EnterpriseOne Relationships
The LDAP system administrator must understand the logical and database-dependent relationships between the LDAP server and EnterpriseOne. The administrator directly or indirectly controls the logical flow of events and where specific data resides based on the setting of system variables in the EnterpriseOne Enterprise Server jde.ini file and settings specified in the LDAP Server Configuration Workbench application (P95928).
The security kernel on the Enterprise Server is responsible for ensuring the integrity of the security within EnterpriseOne. If this kernel is not running correctly or cannot locate requisite data, users cannot sign in to EnterpriseOne. However, when the security kernel is properly configured, the system verifies the user credentials from data within the user profiles. In this case, the following two scenarios are possible:
-
You can configure EnterpriseOne to use LDAP to manage user profiles.
-
You can configure EnterpriseOne to use LDAP to manage user-role relationship data.
LDAP does not support certain user profile information. Such information remains in the domain of the EnterpriseOne Server and must be maintained by the EnterpriseOne system administrator. Therefore, two distinct and separate user profiles may exist:
-
LDAP user profile
This profile includes the user ID and password and can include user-role relationships.
-
JD Edwards EnterpriseOne user profile
The information contained in this profile is stored in the EnterpriseOne database. Examples of such information include the date separator, the decimal separator, and so on.
10.1.3.1 User Authentication Using the LDAP Server
When LDAP is enabled, all systems (including EnterpriseOne) are directed to perform user authentication through the LDAP server.
This diagram shows how LDAP and EnterpriseOne handle authentication:
Figure 10-1 LDAP and EnterpriseOne authentication
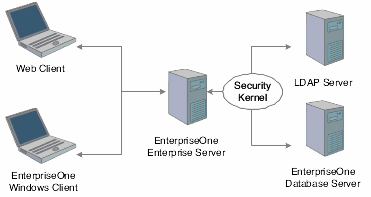
Description of ''Figure 10-1 LDAP and EnterpriseOne authentication''
In this illustration, the security kernel in the Enterprise Server performs authentication against the LDAP server when LDAP is enabled in the [SECURITY] section of the jde.ini file of the Enterprise Server. Otherwise, when LDAP is disabled, the security kernel authenticates the user against the Enterprise Server database.
10.1.3.2 JD Edwards EnterpriseOne User Data
The security kernel in EnterpriseOne requires specific attributes to be defined for all users. These attributes generally include:
-
User ID.
-
User password.
-
User-role relationship.
-
JD Edwards EnterpriseOne system user.
-
Definition of role.
-
JD Edwards EnterpriseOne user profile settings.
10.1.3.3 User Data Managed by LDAP
When you configure EnterpriseOne to use LDAP, the EnterpriseOne security kernel uses the following data stored in the LDAP server:
-
User ID
-
User password
-
User-role relationship (optional)
10.1.3.4 Data Managed by LDAP and JD Edwards EnterpriseOne
This table explains how user data is managed by LDAP and EnterpriseOne, as well as how the security kernel uses this information:
| Data Category | LDAP | EnterpriseOne | Comment |
|---|---|---|---|
| EnterpriseOne User ID | Yes | Yes
F0092 |
If you enable LDAP support in EnterpriseOne, the security kernel validates the user from the LDAP database. The security kernel synchronizes this data from LDAP to EnterpriseOne only when this data is in the LDAP server and not in EnterpriseOne. |
| EnterpriseOne User Password | Yes | Yes
F98OWSEC |
If LDAP is enabled, the user password is always stored in LDAP.
If LDAP is not enabled, the user password is stored in the F98OWSEC table in EnterpriseOne. |
| User-Role Relationship | Yes | Yes
F95921 |
If the user-role relationship is defined to execute through LDAP, the user-role relationship is synchronized from the LDAP server to EnterpriseOne.
If the user-role relationship is defined to execute through EnterpriseOne, the data is stored in the EnterpriseOne database in the F95921 table. |
| EnterpriseOne System User | No | Yes
F98OWSEC |
Not managed in the LDAP server.
EnterpriseOne requires each user to have a system user specified for access to the EnterpriseOne database. The database user is set by the EnterpriseOne system administrator in the EnterpriseOne security table, F98OWSEC. If there are no valid system user settings, the EnterpriseOne security kernel will not validate the user. |
| Definition of Role | Yes | Yes
F0092 |
The user-role relationship is synchronized from the LDAP server to the EnterpriseOne database for roles defined in the EnterpriseOne database. However, the system does not synchronize role definitions from the LDAP server to the EnterpriseOne database. Therefore, role definitions must exist in both systems. |
| EnterpriseOne User Profile Attributes | No | Yes
F00921 and F0092 |
Not managed in LDAP.
EnterpriseOne requires additional user profile attributes that are not generally defined through equivalent attributes in LDAP. Therefore, you can manually set these attributes. You can also specify these values in the default user profile settings for LDAP so that these settings are included for each user that is synchronized from LDAP to EnterpriseOne. See Modifying the LDAP Default User Profile Settings. Some of these attributes include:
|
10.1.3.5 User Data Synchronization in LDAP-Enabled JD Edwards EnterpriseOne
This diagram shows the synchronization of user data from the LDAP server to EnterpriseOne:
In this configuration, a third-party LDAP-enabled application is being used to add, modify, and delete LDAP user information. In addition, the system uses the following methods to synchronize user data from LDAP to the EnterpriseOne database:
-
At user sign-in, using the EnterpriseOne security kernel.
-
Using the LDAP Bulk Synchronization batch application (R9200040).
R9200040 enables you to perform bulk synchronization of user profile records from the LDAP server to the EnterpriseOne database.
10.1.4 Application Changes in LDAP-Enabled JD Edwards EnterpriseOne
When LDAP support is enabled in EnterpriseOne, some of the user profile tasks that you typically perform in EnterpriseOne, such as adding and deleting users, are disabled. You must use LDAP to modify these records, not EnterpriseOne. This section summarizes the following changes in EnterpriseOne menus and applications that result from using LDAP to manage user profile information:
-
User password changes.
-
User Profile Revisions application changes.
-
Security Revisions application changes.
-
Role Relationships application changes.
-
Scheduler application changes.
10.1.4.1 User Password Changes
In EnterpriseOne, users can change their passwords using the User Default Revisions application. However, when LDAP is enabled, users must contact a system administrator for password changes. If a user attempts to select the Change Password option in the User Default Revisions form, the system displays this error:
Error: LDAP authentication is enabled.
Solution: Users must contact a security administrator to have their passwords⇒ changed.
10.1.4.2 User Profile Revisions Application (P0092) Changes
The following functions for managing user information in P0092 are disabled:
-
Add
-
Copy
-
Delete
This ensures that users can only be managed through LDAP.
10.1.4.3 EnterpriseOne Security Application (P98OWSEC) Changes
When LDAP is enabled, P98OWSEC only allows you to add or change specific security settings for specified users. This section discusses the features that you can use in this application when LDAP is enabled.
When an existing single user is selected for security revisions, the User ID field contains the selected user ID.
On the Security Detail Revisions form, you can enable the User Status and Allowed Password Attempts fields by selecting these corresponding options:
-
User Status
-
Attempts
When you are updating security for all users, you click the Revise All button from the Form menu in the Work With User/Role Profiles form. The Security Detail Revisions form appears.
On the Security Detail Revisions form, you can enable the User Status and Allowed Password Attempts fields for all users by selecting these corresponding options:
-
User Status
-
Attempts
10.1.4.4 Role Relationships Application (P95921) Changes
When LDAP is enabled, P95921 has been modified to enable or disable certain functionality, depending on whether roles are managed in LDAP. When roles are managed in LDAP, you cannot use EnterpriseOne to add or delete a role for an individual user. However, you can add roles to the default user for LDAP, which is _LDAPDEFLT. Additionally, you can modify the role expiration date.
If you attempt to add a role to an individual user in EnterpriseOne, the system displays this error:
Error: Role Relationship is managed by LDAP.
Similarly, if you attempt to delegate, remove, or add a role for an individual user, the system will display the same error.
Note:
When LDAP is enabled and roles are managed in LDAP, you can use a third-party LDAP-enabled application to add, delete, or modify role relationships for any user.10.1.4.5 Schedule Jobs Application Changes
The Schedule Jobs application (P91300) displays a password column which is written to the F91300 table. The password stored in this column provides the password that P91300 uses to connect to the EnterpriseOne database. The column is only stored for program use and the actual database record contains an encrypted blob that cannot be viewed or decrypted by the system administrator. However, you can enter the password in the Scheduler Password field of the Scheduling Advance Options form.
The Scheduler kernel validates the user ID and password stored in F91300. The job cannot be launched if the validation fails. Therefore, if the user changes their password after the job is scheduled, the job cannot be launched. In such cases, the user must use P91300 to revise the job.
10.1.5 LDAP Server-Side Administration
This section assumes that EnterpriseOne is using the LDAP server for user profile administration. Using a third-party LDAP-enabled application to access the LDAP server, you can add, modify, or delete attributes of user profiles. This table lists the items that you can manage and actions that you can perform from the LDAP server:
| User Profile Attribute | Action | Description |
|---|---|---|
| User ID and Password Values | Add
Modify Delete |
The user ID and password values must be alphanumeric and cannot exceed 10 characters in length. Unicode is supported.
At sign-in, logic on the EnterpriseOne server automatically performs one-way, real-time synchronization of user IDs from the LDAP server to the EnterpriseOne database. You can run a separate batch application on the Enterprise Server to initially migrate user IDs from LDAP to the EnterpriseOne database. |
| User-Role Relationship | Add
Modify Delete |
At sign-in, logic on the EnterpriseOne server will automatically perform one-way real-time synchronization of this data from the LDAP server to the EnterpriseOne database.
You can run a separate batch application on the EnterpriseOne server to initially migrate this data from LDAP to the EnterpriseOne database. Only valid EnterpriseOne user-role relationships will be synchronized from LDAP to the EnterpriseOne database. |
| Role Definitions | Add
Modify Delete |
You must manually set up role definitions in LDAP and EnterpriseOne because there is no automated method to synchronize this data. |
10.1.6 JD Edwards EnterpriseOne Server-Side Administration
When EnterpriseOne is enabled for LDAP, there are still some user profile administrative tasks that you manage on the Enterprise Server, such as:
-
Tasks that are not supported by LDAP.
-
Tasks that are not synchronized automatically.
-
Tasks that are not synchronized through a batch process.
You can modify the following items on the Enterprise Server:
| EnterpriseOne Attributes | Action | Description |
|---|---|---|
| System User ID and Password | Add
Modify Delete |
Required to set system values not supported by LDAP.
System information is used to connect to the database. It includes database system user name, system user password, and data source name (system key). |
| User-Role Relationship | Add
Modify Delete |
Required if user-role relationships are managed in EnterpriseOne. |
| User-Role Relationship Attributes | Add
Modify Delete |
Required to set attributes not supported by LDAP, such as *ALL and Expiration Dates, when you manage user-role relationships in LDAP. |
| User Status | Modify | Allowed statuses include:
There is no automatic or batch synchronization between LDAP and EnterpriseOne for this function. |
| Allow Password Attempts for EnterpriseOne User | Modify | The number of invalid sign-on attempts a user can make before that user profile is disabled. |
| Role Definitions | Modify | You must always define the role definition in EnterpriseOne, regardless of any LDAP considerations. |
10.2 Configuring LDAP Support in JD Edwards EnterpriseOne
This section contains the following topics:
-
Overview of Steps to Enable LDAP Support in JD Edwards EnterpriseOne
-
Forms Used to Configure LDAP Support in JD Edwards EnterpriseOne
-
Configuring LDAP to EnterpriseOne Enterprise Server Mappings
Note:
If you are creating an LDAP configuration for Oracle Internet Directory, the specific settings for this configuration are listed in an appendix in this guide.See Creating a JD Edwards EnterpriseOne LDAP Configuration for OID.
10.2.1 Overview of Steps to Enable LDAP Support in JD Edwards EnterpriseOne
You must follow these high-level steps in the specified order to properly configure the Enterprise Server to support LDAP:
-
Disable LDAP authentication by ensuring that the [Security] section of the Enterprise Server jde.ini file contains this setting:
LDAPAuthentication=false
-
Use the LDAP Server Configuration Workbench application (P95928) to create an LDAP configuration, configure the LDAP server settings, and configure the LDAP to Enterprise Server mappings. The P95928 application is available on the Microsoft Windows client and the web client.
Note:
EnterpriseOne provides two versions of this application. You can use ZJDE0001 to create a template for creating an LDAP configuration. Create the template by adding specific attributes to the LDAP configuration that can be defined later. This section uses ZJDE0002 of the application to show all possible attributes that can be mapped in the LDAP configuration. -
Use the Configure LDAP Defaults form to enter the required LDAP default user profile settings.
-
Change the LDAP configuration status.
-
Enable LDAP authentication by changing the setting in the [Security] section of the Enterprise Server jde.ini file:
LDAPAuthentication=true
-
Restart the Enterprise Server.
10.2.2 How JD Edwards EnterpriseOne Uses LDAP Server Settings
Part of creating an LDAP configuration for EnterpriseOne involves configuring LDAP server settings. The LDAP server settings are in compliance with the standard syntax specified by the LDAP Data Interchange Format (LDIF). These settings, or attributes, when configured correctly, determine how EnterpriseOne searches for user profile data in the LDAP server. The attributes that you configure differ depending on whether you are:
-
Creating a standard EnterpriseOne configuration for the LDAP server.
-
Using Secure Socket Layer with the LDAP server.
-
Using the self-service version of the user profile application for the Manufacturing Sourcing module.
This diagram shows how EnterpriseOne uses the LDAP server settings to search for user profiles in the LDAP server:
Figure 10-3 User data search hierarchy in the LDAP server
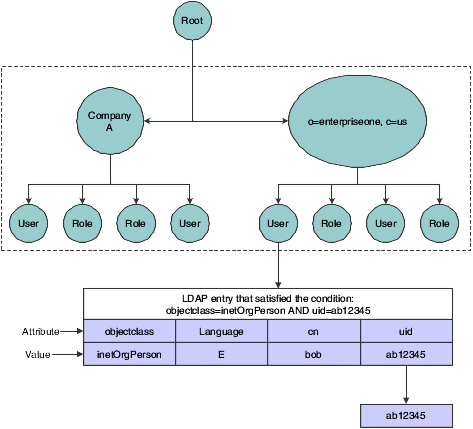
Description of ''Figure 10-3 User data search hierarchy in the LDAP server''
In this diagram, the EnterpriseOne application requests a search of the Directory Information Tree for a EnterpriseOne user in the United States with an ab12345 user ID. The user can only be found if these attributes contain valid values:
| Attribute | Value |
|---|---|
| USRSRCHBAS (User Search Base) | o=enterpriseone, c=us |
| USRSRCHSCP (User Search Scope) | subtree |
| USRSRCHFLT (User Search Filter) | objectclass=inetOrgperson |
| USRSRCHATR (User Search Attribute) | uid |
| E1USRIDATR (EnterpriseOne User ID Attribute) | uid |
-
EnterpriseOne starts the search using the criteria specified in the User Search Base attribute.
-
EnterpriseOne uses the value in the User Search Scope attribute to determine the scope of the search.
-
EnterpriseOne uses the following Search Filter parameter to search for the user in LDAP:
(&((User Search Filter value), ((User Search Attribute value)= "ab12345"))) -
EnterpriseOne retrieves the user ID from the EnterpriseOne User ID Attribute.
10.2.3 Prerequisites
To configure LDAP support in EnterpriseOne, you must have a system administrator who understands LDAP and understands how to use an LDAP-compliant directory service to manage user profile information.
For more information on LDAP, refer to these resources on the web:
-
The IETF LDAPv3 Working Group.
-
The LDAPv3 Working Group archived newsgroup.
-
RFC 3377, the current definition of LDAPv3.
For more information about a specific LDAP-compliant directory service, refer to that particular directory service's documentation.
If you are configuring the directory service with SSL, refer to the directory service documentation for instructions.
10.2.4 Forms Used to Configure LDAP Support in JD Edwards EnterpriseOne
| Form Name | FormID | Navigation | Usage |
|---|---|---|---|
| Available LDAP Configurations | W95928F | Enter P983051 in the Fast Path. On the Work With Interactive Versions form, enter P95928 in the Interactive Version field and click Find. Select ZJDE0002 and then select Run from the Row menu.
The P95928 application is available on the Microsoft Windows client and the web client. |
Add an LDAP configuration record. |
| LDAP Server Information | W95928A | On the Available LDAP Configurations form, click Add. | Complete the fields that are required for the LDAP configuration record. |
| LDAP Server Attribute Values | W95928E | On the Available LDAP Configurations form, select a configuration record and then select Values from the Row menu. | Enter LDAP server attribute values. |
| LDAP Server Mappings | W95928B | On the Available LDAP Configurations form, select Mappings from the Row menu. | Configure LDAP to EnterpriseOne Enterprise Server mappings. |
10.2.5 Creating an LDAP Configuration
Access the Available LDAP Configurations form.
-
Click Add to add a new configuration record.
-
On the LDAP Server Information form, complete these fields and then click OK:
| Field | Description |
|---|---|
| Server Configuration Name | Enter a unique name for the server configuration, and then tab to the next field and enter a description. |
| Enterprise Server Location | Enter the location of the Enterprise Server. |
| Enterprise Server Port | Enter the port used to connect to the Enterprise Server. |
| LDAP Server Location | Enter the location (machine name or IP address) of the LDAP server on the network. |
| LDAP Server Port | Enter the port used to connect to the LDAP server. |
| LDAP Server Type | Click the search button to select the type of LDAP server: Microsoft, IBM, or Domino.
Note: If you are configuring LDAP for Oracle Internet Directory, you must add OID to the list of options and select it here. See Creating a JD Edwards EnterpriseOne LDAP Configuration for OID. |
| LDAP Admin ID | Enter the administrator's ID for the LDAP server. |
| LDAP Admin Password | Enter the administrator's password for the LDAP server. |
| SSL Enabled LDAP Server | Select this option if you want to set up Secure Socket Layer (SSL) communication between EnterpriseOne security kernel and the LDAP server.
Note: This requires the LDAP server to be configured for SSL. See Using LDAP Over SSL. |
| Role Enabled in LDAP | Select this option if you are managing user-role relationships in LDAP. |
10.2.6 Configuring the LDAP Server Settings
Access the LDAP Server Attribute Values form. To do so, on the Available LDAP Configurations form, select a configuration record and then select Values from the Row menu.
-
Click the search button in the Enterprise Server Attribute Name column to select the attributes to include in the LDAP server settings.
After selecting the attributes, you must enter the appropriate LDAP value for the attribute in the LDAP Server Attribute Value column.
-
To configure the standard EnterpriseOne settings for LDAP server, enter values for these attributes:
Attribute Description USRSRCHBAS User search base. Specifies that the system searches for user information at the root of the directory information tree. This value specifies the "container" in which to begin the search. For example, USRSRCHBAS=o=jdedwards,c=usUSRSRCHFLT User search filter. Specifies that a search is performed at the base level for the user ID in the LDAP server using the specified criteria. For example, USRSRCHFLT=objectclass=inetOrgPersonIf you do not specify this value, no search filtering occurs.
USRSRCHSCP User search scope. Specifies the level, or scope, at which the system searches for user information. Valid values are: -
base
The query searches only the value you specified in the USRSRCHBAS setting.
-
subtree
This is the default value. The query searches the value in the Search Base field and all entries beneath it.
-
onelevel
The query searches only the entries one level down from the value in the Search Base field.
ROLSRCHBAS Role search base (use only if roles are enabled in LDAP). Specifies that a search is performed at the base level for the UserIDAttri in the LDAP database. For example, ROLSRCHBAS=o=jdedwards,c=usROLSRCHFLT Role search filter (use only if roles are enabled in LDAP). This specifies that a search is performed at the base level for the role in the LDAP database using the specified criteria. For example, ROLSRCHFLT=objectclass=groupOfNamesIf you do not specify this value, no search filtering occurs.
ROLSRCHSCP Role search scope (use only if roles are enabled in LDAP). This specifies the level, or scope, at which the system searches for role information. Valid values are: -
base
The query searches only the value you specified in the ROLSRCHBAS setting.
-
subtree
This is the default value. The query searches the value in the Search Base field and all entries beneath it.
-
onelevel
The query searches only the entries one level down from the value in the Search Base field.
-
-
When using Secure Socket Layer (SSL) with LDAP server, enter values for these attributes:
Attribute Description SSLPORT SSL Port for the LDAP server. Specifies the SSL port on the LDAP server. CERTDBPATH Dir path for cert7.db (SSL) For Windows and UNIX: This specifies the directory path to the cert7.db file (SSL). This file should generally be located in the system\bin32 directory on the Enterprise Server.
For IBM i: This specifies the directory path and file name for the cert.kdb file on the IBM i-based, Enterprise Server machine, for example
/QIBM/USERDATA/ICSS/CERT/SERVER/CERT.KDB. You should use the Digital Certificate Manager (DCM) to verify the location of the certificate for your installation.CERTDBCLBL Do not use this attribute. This is for future use only. CERTDBPSWD For IBM i only. This is the password to the key database. Specifies the password to the key database (files with a "kdb" extension). The key database is used to store a uniquely identified name, or label, associated with the client private key/certificate pair.
SSLTIMEOUT For IBM i only. This specifies the time-out value for the SSL connection.
-
If you are using the self-service version of the user profile application for the Manufacturing Sourcing module, enter values for these attributes:
Note:
You cannot use this application to manage LDAP user profiles.Attribute Description USRACNTCTL User Account Control. Specifies the authority attached when creating a user in Active Directory, for example USRACNTCTL=512creates an enabled user in Active Directory only.USRADDLOC User Add Location. Specifies the location in LDAP where users will be added, for example USRADDLOC=O=jdedwards.USRCLSHRCY User Class Hierarchy. Specifies the class hierarchy needed to create a user in LDAP, for example USRCLSHRCY=top, person, organizationalPerson, inetOrgPerson.ROLADDLOC Role Add Location (use only if roles are enabled in LDAP). Specifies the location in LDAP that contains the user-role relationship, for example ROLADDLOC=O=jdedwards.ROLCLSHRCY Do not use this attribute. This is for future use only.
10.2.7 Configuring LDAP to EnterpriseOne Enterprise Server Mappings
You can map attributes for users or for user-role relationships, depending upon your configuration. If you are entering mappings for user-role relationships, you must also ensure that the LDAP configuration record is enabled for roles.
Access the LDAP Server Mappings form. To do so, on the Available LDAP Configurations form, select Mappings from the Row menu.
-
Click the search button in the Enterprise Server Attribute Name column to select the attributes to include in the mappings.
After selecting the attributes, you must enter the appropriate LDAP value for the attribute in the LDAP Server Actual Attribute column.
-
To configure the LDAP to Enterprise Server mappings for a standard setup, enter values for these attributes:
Attribute Description E1USRIDATR EnterpriseOne User ID Attribute. Specifies the user ID attribute in LDAP that is used for EnterpriseOne users. The system uses this attribute when creating users in LDAP during EnterpriseOne sign-in, for example E1USRIDATR=cn.USRSRCHATR User ID Search Attribute. Specifies the search criteria for the sign-on user ID. This is the value that maps the sign-on user ID in LDAP to the sign-in user ID in EnterpriseOne, for example USRSRCHATR=cn.The USRSRCHATR and E1USRIDATR attributes should be mapped to the same value.
ROLNAMEATR Role Name Attribute (use only if roles are enabled in LDAP). This value maps the role in LDAP to the role in EnterpriseOne, for example ROLENAMEATR=cnROLSRCHATR Role Search Attribute (use only if roles are enabled in LDAP). Specifies the search attribute for the role in the LDAP server. The system uses this attribute to search LDAP for a list of roles for a user, for example ROLSRCHATR=member.LANGUAGATR Language Attribute. Specifies the language attribute used within LDAP, for example LANGUAGATR=preferredLanguage -
If you are using the self-service version of the user profile application for the Manufacturing Sourcing module, enter values for these attributes:
Note:
You cannot use this application to manage LDAP user profiles.Attribute Description CMNNAME Common Name. Specifies the Common Name for a user in LDAP. The system uses this attribute when creating users in LDAP, for example CMNNAME=cnGIVENNAME Specifies the Given Name for a user in LDAP. It is used when creating users in LDAP, especially in Active Directory, for example GIVENNAME=givenName.SURNAME Specifies the SUR Name for a user in LDAP. This attribute is used when creating users in LDAP, for example SURNAME=sn.PASSWORD Specifies the password associated with the account that you specify with the ConnectDN (distinguished name) of the LDAP server. OBJCLASS Object Class. Specifies the Object Class attribute for a user in LDAP it is used when creating users in LDAP, for example OBJCLASS=objectCLASS.ACNTCTLATR Account Control Attribute. Specifies the attribute used in Active Directory for user authority in Active Directory, for example ACNTCTLATR=userAccountControl. If the attributeUSRACNTCTL=512is used in conjunction withACNTCTLATR, the EnterpriseOne API will create an enabled user in Active Directory only.ACTNAMEATR Account Name Attribute. Specifies the attribute used only in Active Directory for creating a signon user account, for example ACNTCTLATR=sAMAccountName.
10.2.8 Changing the LDAP Configuration Status
After you add an LDAP configuration, by default the configuration is disabled or non-active. You must change the status to active to enable the configuration.
Note:
You can have only one active LDAP configuration per port.Access the Available LDAP Configurations form.
Select a configuration record and then select Change Status from the Row menu.
The system changes the status in the Status column to AV (active) or NA (not active).
10.3 Modifying the LDAP Default User Profile Settings
This section contains the following topics:
-
Section 10.3.1, "Understanding LDAP Default User Profile Settings"
-
Section 10.3.2, "Forms Used to Modify the LDAP Default User Profile Settings"
-
Section 10.3.3, "Reviewing the Current LDAP Default Settings"
-
Section 10.3.4, "Modifying the Default User Profile Settings for LDAP"
-
Section 10.3.5, "Modifying the Default Role Relationships for LDAP"
-
Section 10.3.6, "Modifying the Default User Security Settings for LDAP"
10.3.1 Understanding LDAP Default User Profile Settings
You must configure and review the default LDAP user profile settings that are in the EnterpriseOne database. The system requires the default settings for user profile synchronization. These values are synchronized from LDAP to EnterpriseOne by the LDAP synchronization mechanisms (security kernel and batch report). The default user profile settings are written to the F0092 table.
Note:
You must add the default LDAP user profile settings before enabling LDAP authentication in the jde.ini file of the EnterpriseOne security server.The Configuring LDAP Defaults form shows whether the following items exist for the default user:
-
User profile
-
Role relationships
-
Data source/system user
Important:
Changes made in this application can affect almost all EnterpriseOne users when synchronizing data from LDAP to the EnterpriseOne database.
10.3.2 Forms Used to Modify the LDAP Default User Profile Settings
| Form Name | FormID | Navigation | Usage |
|---|---|---|---|
| Configure LDAP Defaults | W0092M | In Solution Explorer, from the System Administration Tools menu (GH9011), select Security Maintenance, Security Maintenance Advanced and Technical Operations, Configure LDAP Defaults. | Review the current LDAP default settings. |
| User Profile Revisions | W0092A | On the Configure LDAP Defaults form, click the User Profile link. | Modify the default user profile settings for LDAP. |
| Work with Role Relationships | W95921C | On the Configure LDAP Defaults form, click the Role Relationships link. | Add roles to the default user. |
| Work With User Security | W98OWSECE | On the Configure LDAP Defaults form, click the Data Source/System User link. | Add or modify the data source or system user settings. |
| Data Source Revisions | W98OWSECH | On the Work With User Security form, select a security record and then click Select. | Assign a different system user to the data source. |
| Security Revisions | W98OWSECB | On the Work With User Security form, click Add. | Add an additional data source. |
10.3.3 Reviewing the Current LDAP Default Settings
Access the Configure LDAP Defaults form.
Note:
All user values are assigned per user ID the first time, and the first time only, that a user signs in. During this initial sign-in, the values are synchronized from LDAP to the EnterpriseOne database. The default role relationship is synchronized only if roles are managed by EnterpriseOne.- LDAP Authentication
-
Indicates whether LDAP authentication is enabled or disabled.
- Role Management
-
Indicates whether roles are managed by LDAP. You can enable EnterpriseOne to manage roles in LDAP through the P95928 application.
- User Profile
-
Indicates whether a default user profile exists within the EnterpriseOne database. Click this link to modify the default user profile settings.
- Role Relationships
-
Indicates whether a default role relationship exists. If LDAP authentication is enabled, and if user-role relationships are set to be managed by LDAP, then this option is disabled. This means that the system does not use the default user-role relationship when synchronizing users from LDAP to the EnterpriseOne database.
To revise the default role relationship, see Modifying the Default Role Relationships for LDAP.
- Data Source/System User
-
Indicates whether a default data source or system user exists. Click this link to add or change the data source or system user.
10.3.4 Modifying the Default User Profile Settings for LDAP
Access the User Profile Revisions form. To do so, on the Configure LDAP Defaults form, click the User Profile link.
Modify the appropriate fields.
Note:
The User ID field always contains the default user ID for the LDAP system. This field is read only.10.3.5 Modifying the Default Role Relationships for LDAP
Access the Work With Role Relationships form. To do so, on the Configure LDAP Defaults form, click the Role Relationships link.
Note:
If LDAP authentication is enabled and user-role relationships are being managed by LDAP, then this option is disabled. This means that user-role relationship functionality from within EnterpriseOne is disabled.On the Work With Role Relationships form, you can highlight a role in either the Assigned Roles or Available Roles menus, and then click the appropriate directional arrow button to add or remove the role for the default user.
Note:
These values are only synchronized between EnterpriseOne and LDAP if the role is being managed by EnterpriseOne.10.3.6 Modifying the Default User Security Settings for LDAP
Access the Configure LDAP Defaults form.
-
In the Configure Defaults area, click the Data Source/System User link.
If the default data source or system user does not exist, the Security Revisions form appears.
-
On the Security Revisions form, complete the System User field to add or change the data source or system user.
If the default data source is defined, the Work With User Security form appears.
-
To assign a different system user to the data source, on the Work With User Security form, select the security record and then click Select.
-
On Data Source Revisions, click the search button in the System User field to assign a different system user.
-
To add an additional data source, on the Work With User Security form, click Add.
-
On the Security Revisions form, complete the fields as appropriate.
10.4 Using LDAP Bulk Synchronization (R9200040)
This section provides an overview of LDAP bulk synchronization and discusses how to run the LDAP Bulk Synchronization batch process (R9200040).
10.4.1 Understanding LDAP Batch Synchronization
The LDAP server contains user profile data for multiple users. This data must also exist in the EnterpriseOne database server. The LDAP Bulk Synchronization batch process (R9200040) enables you to perform bulk synchronization of user profile records from the LDAP server to the EnterpriseOne database. Therefore, this report is beneficial because it populates data that is required for EnterpriseOne functionality.
Note:
If the EnterpriseOne database contains user profile records that are not in the LDAP server, this data cannot be synchronized from EnterpriseOne to the LDAP server using the R9200040 batch process. EnterpriseOne does not provide a utility to perform this function.Running the report synchronizes user profile data obtained from the LDAP server to the following EnterpriseOne database tables:
| Table | Description |
|---|---|
| F0092 | Library List User |
| F00921 | User Display Preferences |
| F98OWSEC | Security settings |
| F95921 | Role Relationship |
| F0093 | Library List Control |
| F00922 | User Display Preferences Tag File |
| F00924 | User Install Package |
| F00926 | Anonymous User Access Table |
| F9005 | Variant Description - Control Tables |
| F9006 | Variant Detail - Control Tables |
10.4.1.1 Example: LDAP Bulk Synchronization (R9200040)
The following example shows the PDF output of the R9200040 batch process. Note that if the data on the LDAP server is already the same as the corresponding data on the EnterpriseOne database server, the report lists the affected tables and shows a zero record synchronization, which indicates the data exists, but is identical.
Figure 10-4 LDAP Bulk Synchronization output
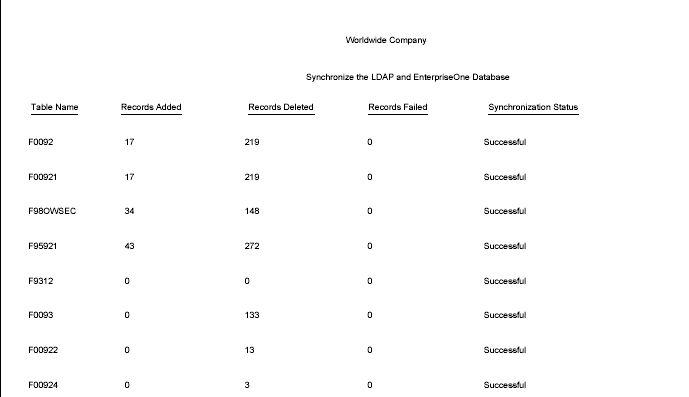
Description of ''Figure 10-4 LDAP Bulk Synchronization output''
10.4.2 Running the LDAP Bulk Synchronization Batch Process (R9200040)
Access the Batch Versions application (P98305). To do so, enter P98305 in the Fast Path.
-
On the Work With Batch Versions – Available Versions form, enter R9200040 in the Batch Application field and click Select.
-
On the Version Prompting form, click Submit.
10.5 Using LDAP Over SSL
This section provides an overview on how to enable LDAP authentication over Secure Socket Layer (SSL) and discusses how to:
-
Enable LDAP authentication over SSL for Windows and UNIX.
-
Enable LDAP authentication over SSL for IBM i.
10.5.1 Understanding LDAP with SSL
You can establish a secure LDAP connection between the EnterpriseOne Server and the LDAP server.
10.5.1.1 LDAP Authentication Over SSL for Windows and UNIX
The EnterpriseOne server uses Netscape's certificate database, cert7.db. You can obtain a cert7.db using the PKCS Utilities distributed by Netscape. Refer to Netscape's documentation for more information on obtaining and using the PKCS Utilities.
For Windows and UNIX, establishing the secure connection between the EnterpriseOne application server and the LDAP server requires these items:
-
Cert7.db certificate database from Netscape.
-
A server certificate for the LDAP server.
-
The trusted root certificate from the certificate authority (CA) that issues the server certificate.
10.5.1.2 LDAP Authentication Over SSL for IBM i
The EnterpriseOne server uses IBM certificate database (.kdb) to store certificates on IBM i. You can create a certificate database on IBM i using Digital Certificate Manager.
For IBM i, establishing a secure connection between the EnterpriseOne application server and the LDAP server requires these items:
-
IBM Certificate store (.kdb) certificate database.
-
A server certificate for the LDAP server.
-
The trusted root certificate from the certificate authority (CA) that issues the server certificate.
10.5.2 Enabling LDAP Authentication Over SSL for Windows and UNIX
To enable LDAP authentication over SSL for Windows or UNIX:
-
Follow the documentation for your directory server to add the server certificate to the directory server.
-
Using Netscape's PKCS Utilities, add the CA's trusted root certificate to the cert7.db certificate database.
-
Enable SSL for the LDAP configuration using the LDAP Server Configuration Workbench application.
-
Specify the SSL parameters.
-
Restart the EnterpriseOne server.
10.5.3 Enabling LDAP Authentication Over SSL for IBM i
To enable LDAP authentication over SSL for IBM i:
-
Follow the documentation for your directory server to add the server certificate to the directory server.
-
Use Digital Certificate Manager to add and export the CA's trusted root certificate to the certificate database (.kdb file).
-
Enable the SSL for the LDAP configuration using the LDAP Server Configuration Workbench application.
-
Specify the SSL parameters.
-
Restart the EnterpriseOne server.
10.6 Exporting User Data to the LDAP Server
This section contains the following topics:
-
Section 10.6.4, "Configuring Parameters Required to Run the data4ldap Utility"
-
Section 10.6.6, "Running the data4ldap Utility on Unix or Linux"
-
Section 10.6.8, "Scenarios for Uploading Users to the LDAP Server"
10.6.1 Understanding the data4ldap Utility
The data4ldap utility automates the process of uploading EnterpriseOne user data to the LDAP server. The EnterpriseOne user data includes:
-
EnterpriseOne user ID
-
Password
Important:
Starting with EnterpriseOne Tools Release 9.1 Update 3, data4ldap can no longer export passwords. If you want to export passwords, run data4ldap in a prior release of EnterpriseOne Tools before installing or running Tools Release 9.1 Update 3. See Appendix A, "DB Password Encryption" for more information about changes to EnterpriseOne user password encryption in Tools Release 9.1 Update 3. -
Language attribute
-
User-role relationship
If you do not use this utility, you would have to populate the repository manually, which can lead to data being entered incorrectly. This illustration shows the data4ldap.exe utility uploading the EnterpriseOne user data to the LDAP server.
Figure 10-5 Uploading user data to the LDAP server with data4ldap.exe
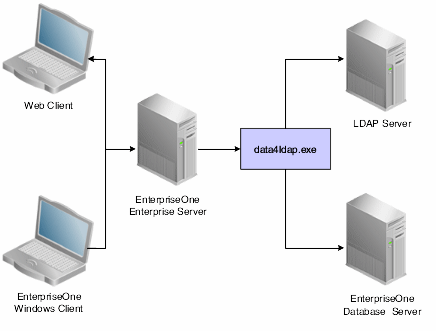
Description of ''Figure 10-5 Uploading user data to the LDAP server with data4ldap.exe''
The Language attribute is uploaded only for those EnterpriseOne users who are specifically assigned a language. By default, no language is assigned to a user when a user is added to EnterpriseOne. In such a case, no language is available for the particular user in the LDAP server. For example, if User 1 is assigned language E and User 2 is not assigned to any language, the language attribute is uploaded to the LDAP server only for User 1 and not for User 2.
Expired EnterpriseOne users and roles are also exported to the LDAP server. If an EnterpriseOne user record does not exist in the table F98OWSEC, then the particular user would not be exported to the LDAP server.
10.6.2 Prerequisites
Before you use the data4ldap utility, you must:
-
Use the LDAP Server Configuration Workbench application (P95928) to map these items:
See Enabling LDAP Support in JD Edwards EnterpriseOne.
-
User Search Attribute
-
User Search Base
-
User Class Hierarchy
-
Role Search Attribute
-
Role Name Attribute
-
Role Search Base
-
Role Class Hierarchy
-
Object Class
-
Password
If these fields are left blank, no operation is performed; the utility generates an appropriate error message and exits.
-
-
For Microsoft Active Directory, map the following attributes in addition to the above mentioned ones:
-
User Account Control
-
Account Control Attribute
-
Account Name Attribute
-
-
Use the LDAP Administrator user ID and password. If either the LDAP Administrator user ID or password field is blank in P95928, the utility cannot export EnterpriseOne user-role data to the LDAP server. It will generate an error message and exit.
-
Disable the password policies of the LDAP server. For further information, refer to the documentation of the directory server that you are using for the LDAP server or contact your LDAP Administrator.
10.6.3 Granting Access to the data4ldap Utility
The data4ldap utility involves working with secured data, so you must ensure that only authorized users are able to access and run it. Use the External Calls Security form in the Security Workbench application (P00950) to grant a user or administrator access to this utility.
10.6.4 Configuring Parameters Required to Run the data4ldap Utility
The data4ldap utility can run only on the Enterprise Server and not on the client.
To run the data4ldap utility, you must configure these parameters:
data4ldap <UserID> <Environment> <Role> <IsRoleIncluded (*YES/*NO)> <IsOverwrite⇒ Allowed (*YES/*NO)>
| Parameter | Description |
|---|---|
| UserID | Enter a valid EnterpriseOne user ID that has been granted access to the utility from External Call Security. |
| Environment | Enter a valid EnterpriseOne environment. |
| Role | Enter a valid EnterpriseOne role. |
| IsRoleIncluded | Specify whether or not EnterpriseOne role information is included in the export to the LDAP server.
Enter *YES to export role information. Enter *NO to not export role information. |
| IsOverwriteAllowed | Determine whether you want to override the LDAP server entries with the EnterpriseOne user-role data: Enter *YES to overwrite the LDAP server entries with the EnterpriseOne user-role data. Enter *NO if you do not want to overwrite the LDAP server entries with the EnterpriseOne user-role data. |
Note:
The IsOverwriteAllowed parameter is used in case the LDAP server already contains user data that is identical to EnterpriseOne user data. In this case, you have the option to overwrite the existing LDAP server user IDs with the current EnterpriseOne user IDs. The value of IsOverwriteAllowed parameter is valid only for user data (common name, language, password, and given name whichever is configured through the application P95928) and not for user-role relationship data. However, starting with EnterpriseOne Tools Release 9.1 Update 3, password information is not included in the exported user data.10.6.5 Running the data4ldap Utility on Windows
In the command prompt, navigate to Enterprise Server System\bin32.
-
Enter the valid parameters. For example:
data4ldap JDE DV812 *ALL *YES *YES
-
Press Enter.
The utility prompts for User – Password.
-
Enter the password for the EnterpriseOne account.
10.6.6 Running the data4ldap Utility on Unix or Linux
In the command prompt, navigate to Enterprise Server System\bin32.
-
Enter the valid parameters. For example:
data4ldap JDE DV812 *ALL *YES *YES
-
Press Enter.
The utility prompts for User – Password.
-
Enter the password for the EnterpriseOne account.
10.6.7 Running the data4ldap utility on IBM i
Access the IBM i command prompt.
-
Under "Selection or command," type data4ldap and press F4.
Some default values that are editable appear on the screen.
-
Enter the valid parameters, for example:
data4ldap JDE Password DV812 *ALL *YES *YES
-
Press Enter.
10.6.8 Scenarios for Uploading Users to the LDAP Server
This section discusses the following scenarios for uploading users to the LDAP server:
-
data4ldap JDE DV812 *ALL *NO *YES
-
data4ldap JDE DV812 *ALL *YES *YES
-
data4ldap JDE DV812 *ALL *YES *NO
-
data4ldap JDE DV812 *ALL *NO *NO
10.6.8.1 data4ldap JDE DV812 *ALL *NO *YES
All EnterpriseOne users are uploaded to the LDAP server and existing LDAP user data is overwritten. However, EnterpriseOne user-role relationship data is neither uploaded nor overwritten in the LDAP server.
10.6.8.2 data4ldap JDE DV812 *ALL *YES *YES
All EnterpriseOne user and user-role relationship data is uploaded to the LDAP server. The existing LDAP user data and LDAP role-relationship data is overwritten.
10.6.8.3 data4ldap JDE DV812 *ALL *YES *NO
All EnterpriseOne users who do not exist in the LDAP server are uploaded to the LDAP server. The existing LDAP users are not be overwritten.
All EnterpriseOne user-role relationship data is uploaded to the LDAP server and the existing LDAP role-relationship data is overwritten.
10.6.8.4 data4ldap JDE DV812 *ALL *NO *NO
All EnterpriseOne users who do not exist in the LDAP server are uploaded to the LDAP server, and the existing LDAP users are not overwritten.
However, EnterpriseOne user-role relationship data would neither be uploaded nor overwritten in the LDAP Server.
10.6.9 LDAP Server Behavior
This section provides information about LDAP server and:
-
Tree Delete control
-
Microsoft Active Directory
10.6.9.1 Tree Delete Control
IBM Directory Server (IDS) and Microsoft Active Directory support Tree Delete Control. The Tree Delete Control extends the delete operation and allows the removal of sub trees within a directory using a single delete request.
It is always recommended that if the Role data are managed by the LDAP server, include the Role data (isRoleIncluded = *YES) while choosing the Overwrite option (isOverwriteAllowed = *YES).
For more details on Tree Delete Control, see:
http://publib.boulder.ibm.com/infocenter/iseries/v5r3/index.jsp?topic=/rzahy/rzahycontrols.htm
Note:
Oracle Internet Directory (OID) does not support Tree Delete Control.10.6.9.2 Microsoft Active Directory
Microsoft Active Directory uses "inetOrgPerson" and a user password can be stored in the Active Directory attribute called "userPassword". However, Microsoft Active Directory must be configured to store a user password in the "userPassword" attribute. It can be configured by setting the 9th bit of dsHeuristics value. It is located in CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=domain. object. The value should look like this: 000000001. For more information, refer to Microsoft documentation.
http://msdn.microsoft.com/en-us/library/cc223249.aspx
http://msdn.microsoft.com/en-us/library/cc223560.aspx
Consider the following items when using Microsoft Active Directory:
-
EnterpriseOne application P95928 should be configured accordingly for "InetOrgPerson" and "userPassword".
-
For Microsoft Active Directory, the EnterpriseOne data can be dynamically uploaded only over a SSL connection. This is due to the Microsoft Active Directory restriction.
-
Microsoft Active Directory user-password authentication is case sensitive, but the requirements for password authentication vary depending on the EnterpriseOne Tools release:
-
With EnterpriseOne Tools Releases 9.1 and 9.1 Update 2, the uploaded user passwords are stored in uppercase in LDAP servers. During sign-in, other LDAP servers ignore the case of the supplied password, whereas Microsoft Active Directory fails to authenticate a user if the supplied password is not in uppercase.
-
With EnterpriseOne Tools Release 9.1 Update 3 and above, the user information uploaded from EnterpriseOne does not include user passwords. Therefore, passwords must be entered by an administrator or end users using the applicable LDAP tool. The passwords are stored in the case in which they are entered. During sign-in, other LDAP servers ignore the case of the supplied password, whereas Microsoft Active Directory fails to authenticate a user if the supplied password is not in the correct case.
-
-
In case a user does not get uploaded to Microsoft Active Directory, all of the roles assigned to the particular user would also not be uploaded to Microsoft Active Directory. This restriction is valid only for Microsoft Active Directory and not for OID / IDS.