3 Pre-Installation Security Considerations
This chapter contains the following topics:
3.1 Recommendations for Deploying and Configuring JD Edwards EnterpriseOne in a Secure Environment
In today's environment, a properly secured computing infrastructure is critical. As companies expand, so does the complexity of their business processes. In an internet environment, the risks to valuable and sensitive data are greater than ever before. In addition, a company's computing infrastructure grows as more third-party products are integrated with its enterprise software. As a result, this type of environment can create potential security gaps.
It is critical that you secure a JD Edwards EnterpriseOne environment in alignment with your company's enterprise security policies. Those policies should be created based upon your established security model. When securing an EnterpriseOne environment, you should take a comprehensive approach that is in concert with the overall corporate security policies, guidelines, and business requirements.
It is important that EnterpriseOne and the various components involved in an EnterpriseOne setup are properly secured. This ensures that EnterpriseOne applications deliver data in a secure and reliable fashion so that data integrity, confidentiality, and availability are maintained. JD Edwards EnterpriseOne Tools must be installed and maintained in a manner that prevents unauthorized access, unauthorized use, and disruptions in service.
3.2 EnterpriseOne Upgrade Security Considerations
The JD Edwards EnterpriseOne Upgrade guides contain security-related tasks that you must perform when upgrading the production environment in EnterpriseOne. See the following sections in the Upgrade guides in the JD Edwards EnterpriseOne Installation and Upgrade Documentation Library:
-
"General Checklist and Considerations"
-
"Adding Security Overrides"
Use the following link to access the JD Edwards EnterpriseOne Upgrade guides:
3.3 Network Infrastructure Security
In an internet environment, securing the network infrastructure is the foremost priority for an organization because the risks to valuable and sensitive data are greater than in a WAN environment. To eliminate potential weak points in the network infrastructure, you may opt to pass data from protocol to protocol without the complexity of decryption and encryption. To do so securely, you must have some way to securely transfer data across network protocol boundaries. The internet enables you to connect your corporate intranet to a broad public network. Although this capability provides enormous business advantages, it also poses a risk to your data and your computer system. One way of protecting the privacy and integrity of your system is to place a firewall between the public network and your intranet.
3.4 Set Up Firewall and DMZ
A firewall is one of the most common network devices used to secure a network environment. Set up a firewall and demilitarized zone (DMZ) to block unauthorized traffic. You should place the EnterpriseOne HTTP server in a DMZ configuration for internet facing systems. Keep the web application server, database, and Enterprise Server (otherwise known as the business logic or security server) behind a firewall. Firewalls provide assurance that access to these systems is restricted to a known network route that can be monitored.
In addition, you can also place a firewall between the Web Application Server and the database or Enterprise Server to add an additional layer of protection. See Additional Network Infrastructure Security for more information.
This illustration shows the recommended firewall setup for JD Edwards EnterpriseOne:
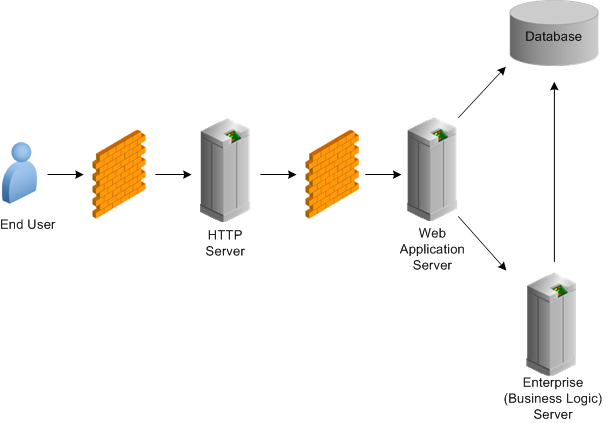
You should also install an Intrusion Detection System (IDS) and establish a policy to regularly monitor unauthorized traffic.
3.5 Additional Network Infrastructure Security
For an internet facing system, it is recommended that you place the HTTP server in a DMZ zone and keep the EnterpriseOne HTML Server (Web Application Server), database, and Enterprise Server behind a firewall. In addition, you can add an additional layer of protection by placing a firewall between the Web Application Server and the database or Enterprise Server.
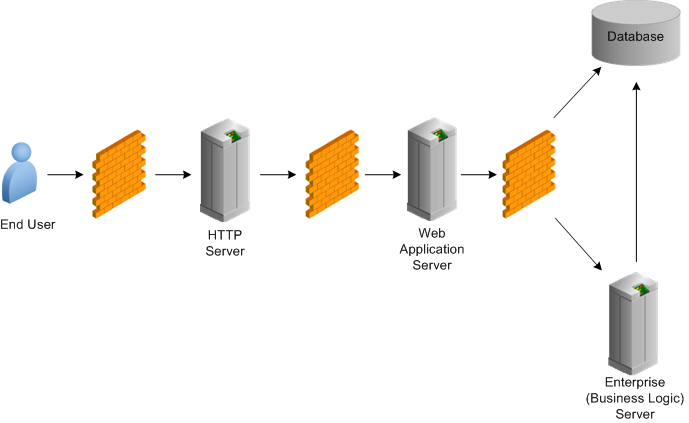
3.5.1 Enable Predefined JDENET Ports in JDE.INI
When there is a firewall between the EnterpriseOne HTML Server and the Enterprise Server, set the PredfinedJDENETPorts setting to 1 in the JDE.INI file of the Enterprise Server. This setting enables JDENET network process to use a predefined range of TCP/IP ports. This port range starts at the port number that is specified by serviceNameListen and ends at the port that is calculated by the equation serviceNameListen = maxNetProcesses - 1. You must open these ports in a firewall setup to successfully connect the EnterpriseOne HTML Server to the Enterprise Server.