| Oracle® Fusion Middleware Application Developer's Guide for Oracle Identity Management 11g Release 1 (11.1.1) Part Number E10186-03 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware Application Developer's Guide for Oracle Identity Management 11g Release 1 (11.1.1) Part Number E10186-03 |
|
|
PDF · Mobi · ePub |
As of Release 11g Release 1 (11.1.1), the recommended security API for Fusion Middleware application developers is Oracle Platform Security for Java, which is documented in the Fusion Middleware Security Guide. The Oracle Identity Management interfaces described in the current book are not part of Oracle Platform Security for Java.
Oracle Identity Management provides a shared infrastructure for all Oracle applications. It also provides services and interfaces that facilitate third-party enterprise application development. These interfaces are useful for application developers who need to incorporate identity management into their applications.
This chapter discusses these interfaces and recommends application development best practices in the Oracle Identity Management environment.
This chapter contains the following topics:
Section 1.1, "Oracle Identity Management Services Available for Application Integration"
Section 1.2, "Integrating Existing Applications with Oracle Identity Management"
Section 1.3, "Oracle Identity Management Programming: An Overview"
Custom applications can use Oracle Identity Management through a set of documented and supported services and APIs. For example:
Oracle Internet Directory provides LDAP APIs for C, Java, and PL/SQL, and is compatible with other LDAP SDKs.
Oracle Delegated Administration Services provides a core self-service console that can be customized to support third-party applications. In addition, they provide several services for building customized administration interfaces that manipulate directory data.
Oracle Directory Integration Services facilitate the development and deployment of custom solutions for synchronizing Oracle Internet Directory with third-party directories and other user repositories.
Oracle Provisioning Integration Services provide a mechanism for provisioning third-party applications, and a means of integrating the Oracle environment with other provisioning systems.
Oracle Single Sign-On provides APIs for developing and deploying partner applications that share a single sign-on session with other Oracle Web applications.
JAZN is the Oracle implementation of the Java Authentication and Authorization Service (JAAS) Support standard. JAZN allows applications developed for the Web using the Oracle J2EE environment to use the identity management infrastructure for authentication and authorization.
Note:
Oracle Fusion Middleware 11g Release 1 (11.1.1) does not include Oracle Single Sign-On or Oracle Delegated Administration Services. Oracle Internet Directory 11g Release 1 (11.1.1), however, is compatible with Oracle Single Sign-On and Oracle Delegated Administration Services 10g (10.1.4.3.0) or later.For new applications, use Oracle Platform Security for Java, which is documented in the Fusion Middleware Security Guide.
An enterprise may have already deployed certain applications to perform critical business functions. Oracle Identity Management provides the following services that can be leveraged by the deployment to modify existing applications:
Automated User Provisioning: The deployment can develop a custom provisioning agent that automates the provisioning of users in the existing application in response to provisioning events in the Oracle Identity Management infrastructure. This agent must be developed using the interfaces of Oracle Provisioning Integration Service.
See Also:
Oracle Fusion Middleware Administrator's Guide for Oracle Internet Directory for more information about developing automated user provisioning.User Authentication Services: If the user interface of the existing application is based on HTTP, integrating it with Oracle HTTP Server and protecting its URL using mod_osso authenticates all incoming user requests using the Oracle Single Sign-On service.
Centralized User Profile Management: If the user interface of the existing application is based on HTTP, and it is integrated with Oracle Single Sign-On for authentication, the application can use the self-service console of Oracle Delegated Administration Services to enable centralized user profile management. The self-service console can be customized by the deployment to address the specific needs of the application.
This section introduces you to the Oracle Identity Management Software Developer's Kit. It provides an overview of how an application can use the kit to integrate with the directory. You are also acquainted with the rest of the directory product suite.
The section contains these topics:
Section 1.3.1, "Programming Languages Supported by the Oracle Internet Directory SDK"
Section 1.3.3, "Application Development in the Oracle Identity Management Environment"
The SDK is for application developers who use C, C++, and PL/SQL. Java developers must use the JNDI provider to integrate with the directory.
The Oracle Identity Management Software Developer's Kit 11g Release 1 (11.1.1) consists of the following:
A C API compliant with LDAP Version 3
A PL/SQL API contained in a PL/SQL package called DBMS_LDAP
Oracle Identity Management Application Developer's Guide (this document)
Command-line tools
This section contains these topics:
Section 1.3.3.1, "Architecture of an Oracle Identity Management Application"
Section 1.3.3.2, "Oracle Identity Management Interactions During the Application Life Cycle"
Section 1.3.3.3, "Services and APIs for Integrating Applications with Oracle Identity Management"
Section 1.3.3.4, "Integrating Existing Applications with Oracle Identity Management"
Most Oracle Identity Management applications are back-end programs that simultaneously handle multiple requests from multiple users. Figure 1-1 shows how a directory is used by such applications.
Figure 1-1 A Directory-Enabled Application
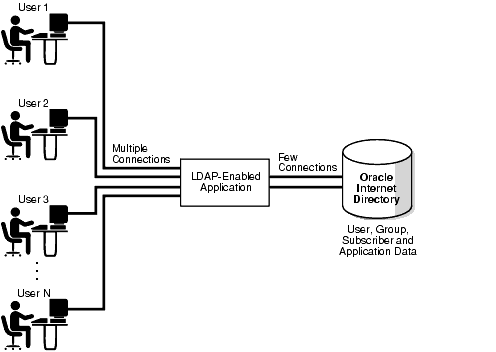
As Figure 1-1 shows, when a user request involves an LDAP-enabled operation, the application processes the request using a smaller set of pre-created directory connections.
Table 1-1 walks you through the directory operations that an application typically performs during its lifecycle.
Table 1-1 Interactions During Application Lifecycle
Application developers can integrate with Oracle Identity Management by using the services and APIs listed and described in Table 1-2.
Table 1-2 Services and APIs for Integrating with Oracle Internet Directory
| Service/API | Description | More Information |
|---|---|---|
|
These provide basic LDAP operations. The standard LDAP API used in Java is the JNDI API with the LDAP service provider. |
Chapter 2, "Developing Applications with Standard LDAP APIs" |
|
|
Oracle Extensions to Standard C, PL/SQL and Java APIs |
These APIs provide programmatic interfaces that model various concepts related to identity management. |
Chapter 4, "Developing Applications With Oracle Extensions to the Standard APIs" |
|
Oracle Delegated Administration Services |
Oracle Delegated Administration Services consists of a self-service console and administrative interfaces. You can modify the administrative interfaces to support third-party applications. |
The 10g (10.1.4.0.1) Library. |
|
Oracle Directory Provisioning Integration Service |
You can use the Oracle Provisioning Integration System to provision third-party applications and integrate other provisioning systems. |
Figure 1-2 shows an application leveraging some of the services illustrated in Table 1-2.
As Figure 1-2 shows, the application integrates with Oracle Internet Directory as follows:
Using PL/SQL, C, or Java APIs, it performs LDAP operations directly against the directory.
In some cases, it directs users to self-service features of Oracle Delegated Administration Services.
It is notified of changes to entries for users or groups in Oracle Internet Directory. The Oracle Directory Provisioning Integration Service provides this notification.
Your enterprise may already have deployed applications that you may have wanted to integrate with the Oracle identity management infrastructure. You can integrate these applications using the services presented in Table 1-3.
Table 1-3 Services for Modifying Existing Applications
| Service | Description | More Information |
|---|---|---|
|
Automated User Provisioning |
You can develop an agent that automatically provisions users when provisioning events occur in the Oracle identity management infrastructure. You use interfaces of the Oracle Directory Provisioning Integration Service to develop this agent. |
Chapter 7, "Developing Provisioning-Integrated Applications" |
|
User Authentication Services |
If your user interface is based on HTTP, you can integrate it with the Oracle HTTP Server. This enables you to use mod_osso and OracleAS Single Sign-On to protect the application URL. |
Oracle Application Server Single Sign-On Administrator's Guide |
|
Centralized User Profile Management |
If your user interface is based on HTTP and is integrated with OracleAS Single Sign-On, you can use the Oracle Internet Directory Self-Service Console to manage user profiles centrally. You can tailor the console to the needs of your application. |
|