| Skip Navigation Links | |
| Exit Print View | |
|
Trusted Extensions Administrator's Procedures Oracle Solaris 10 1/13 Information Library |
| Skip Navigation Links | |
| Exit Print View | |
|
Trusted Extensions Administrator's Procedures Oracle Solaris 10 1/13 Information Library |
1. Trusted Extensions Administration Concepts
2. Trusted Extensions Administration Tools
Administration Tools for Trusted Extensions
Solaris Management Console Tools
Trusted Extensions Tools in the Solaris Management Console
Client-Server Communication With the Solaris Management Console
Solaris Management Console Documentation
Label Builder in Trusted Extensions
Command Line Tools in Trusted Extensions
Remote Administration in Trusted Extensions
3. Getting Started as a Trusted Extensions Administrator (Tasks)
4. Security Requirements on a Trusted Extensions System (Overview)
5. Administering Security Requirements in Trusted Extensions (Tasks)
6. Users, Rights, and Roles in Trusted Extensions (Overview)
7. Managing Users, Rights, and Roles in Trusted Extensions (Tasks)
8. Remote Administration in Trusted Extensions (Tasks)
9. Trusted Extensions and LDAP (Overview)
10. Managing Zones in Trusted Extensions (Tasks)
11. Managing and Mounting Files in Trusted Extensions (Tasks)
12. Trusted Networking (Overview)
13. Managing Networks in Trusted Extensions (Tasks)
14. Multilevel Mail in Trusted Extensions (Overview)
15. Managing Labeled Printing (Tasks)
16. Devices in Trusted Extensions (Overview)
17. Managing Devices for Trusted Extensions (Tasks)
18. Trusted Extensions Auditing (Overview)
19. Software Management in Trusted Extensions (Tasks)
A. Quick Reference to Trusted Extensions Administration
A device is either a physical peripheral that is connected to a computer or a software-simulated device called a pseudo-device. Because devices provide a means for the import and export of data to and from a system, devices must be controlled to properly protect the data. Trusted Extensions uses device allocation and device label ranges to control data flowing through devices.
Examples of devices that have label ranges are frame buffers, tape drives, diskette and CD-ROM drives, printers, and USB devices.
Users allocate devices through the Device Allocation Manager. The Device Allocation Manager mounts the device, runs a clean script to prepare the device, and performs the allocation. When finished, the user deallocates the device through the Device Allocation Manager, which runs another clean script, and unmounts and deallocates the device.
Figure 2-1 Device Allocation Manager Icon in Trusted CDE
You can manage devices by using the Device Administration tool from the Device Allocation Manager. Regular users cannot access the Device Administration tool.
Note - In Solaris Trusted Extensions (JDS), this GUI is named Device Manager, and the Device Administration button is named Administration.
Figure 2-2 Device Allocation Manager GUI
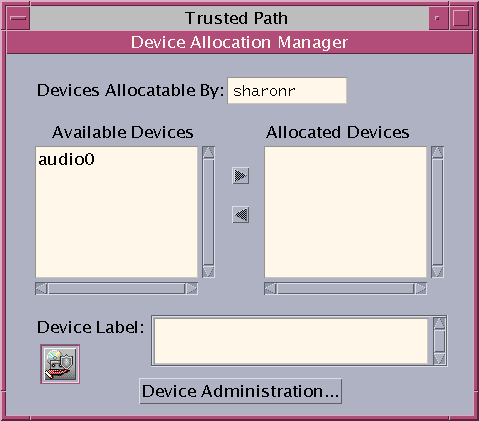
For more information about device protection in Trusted Extensions, see Chapter 17, Managing Devices for Trusted Extensions (Tasks).