7 Configuring Oracle Privileged Account Manager for Integrated Solutions
This chapter explains how to configure Oracle Privileged Account Manager for integration with commonly used directory and identity management technologies and contains the following topics:
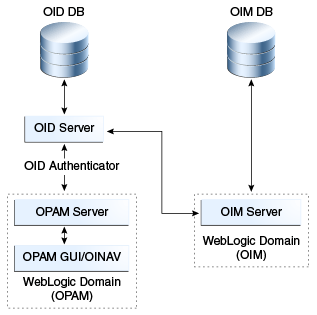
7.1 Integrating with Oracle Identity Manager
This section describes how you can use Oracle Identity Manager to manage access to the LDAP groups that are also Oracle Privileged Account Manager grantees.
Integration with Oracle Identity Manager enables Oracle Privileged Account Manager to
-
Manage the identity lifecycle from hiring to retirement
-
Provide a native ability to automate adding and removing users to the proper LDAP groups based on their HR system updates
-
Provide the ability to manually request access to accounts
-
Support the ability to get approvals for requests
-
Support reporting that you can use for attestation reporting; either to augment or in-lieu of Oracle Privileged Account Manager's own reporting.
The topics in this section include:
7.1.1 Overview
Oracle Privileged Account Manager is optimized for managing shared and privileged accounts, such as root on an UNIX system.
Oracle Privileged Account Manager determines which users can check out passwords for accounts on a target, based on the grants those users have received. Grants can be made directly or through membership in groups. The groups themselves can be static or dynamic.
Ideally, the LDAP groups should match your enterprise roles. For example, if you have a "Data Center Product UNIX Administrators" enterprise role, you should have a corresponding LDAP group. The benefit of this match is that you can use these groups to control access to other applications besides Oracle Privileged Account Manager target-accounts.
Note:
To create an LDAP group, contact your LDAP administrator.
7.1.2 Configuring Oracle Privileged Account Manager for the Integration
To configure Oracle Privileged Account Manager for integration with Oracle Identity Manager, you must be an Oracle Privileged Account Manager administrator and perform the following tasks:
7.1.3 Integrating the Oracle Identity Manager Core
Oracle Identity Manager provides the following features to support this integration:
-
Populate the resource catalog with proper enterprise roles and entitlements. Oracle Privileged Account Manager target-accounts are entitlements because Oracle Identity Manager is not actually granting direct access to the actual account only a representation of that account.
Refer to the Oracle Identity Manager documentation for more detailed information about accounts, entitlements, and roles.
7.1.4 Configuring an Oracle Identity Manager Administrator
You must configure an Oracle Identity Manager administrator who can perform the following tasks:
-
Configure an Oracle Identity Manager rule that assigns users to the proper LDAP groups based on a business rule when you add users to Oracle Identity Manager (either manually through the user screen or automatically by using an HR/text feed).
-
Use Oracle Identity Manager's native functionality to build requests for items in the Oracle Identity Manager resource catalog to ensure that the Oracle Identity Manager catalog is properly populated. Oracle Identity Manager enables users to request access to entitlements contained in the Oracle Identity Manager catalog.
-
Set approver fields to the proper values. For example, in situations where one employee requests access to the email account of another employee who will be away from the office for an extended period of time.
-
Handle "firecall" requests, where an Oracle Privileged Account Manager user must access a system that is outside the normal business process.
Firecall requests are handled based upon your business requirements and business rules. For example, if the Oracle Privileged Account Manager user is authorized for a target, but the access policy prevents that user from getting the password, then the Oracle Privileged Account Manager administrator can temporarily change the access policy for that target-account.
If the user cannot wait for Oracle Identity Manager, the Oracle Privileged Account Manager administrator can manually direct access (for example, add a specific grantee to the account) instead.
7.1.5 Managing Oracle Identity Manager Workflows
Oracle Privileged Account Manager leverages Oracle Identity Manager for workflow support. The integration points include:
-
Access to privileged accounts granted to roles in Oracle Privileged Account Manager by an Oracle Privileged Account Manager Admin
-
End users can request membership in these roles via Oracle Identity Manager
-
Standard Oracle Identity Manager workflow used to approve these requests
-
Membership in the requested role results in end user getting access to the corresponding privileged accounts in Oracle Privileged Account Manager
7.2 Integrating with Oracle Access Management Access Manager
This section explains how Oracle Access Management Access Manager (Access Manager) integrates with Oracle Privileged Account Manager. Using this integration scenario, you can protect Oracle Privileged Account Manager with Access Manager using a WebGate agent.
The topics in this section include:
7.2.1 Before You Begin
Before starting the procedure described in Section 7.2.2, "Enabling Single Sign-On," be aware of the following:
-
The instructions assume that you configured Oracle Internet Directory as the Identity Store; however, other component configurations are possible. Refer to the system requirements and certification documentation on Oracle Technology Network for more information about supported configurations.
-
In addition, the instructions describe a specific example of using Access Manager to protect URLs. Although they outline the general approach for this type of configuration, you are not limited to using the exact steps and components described here. For example, Oracle Internet Directory is one of several identity stores certified with Access Manager 11g.
-
You can use Oracle Adaptive Access Manager as an authentication option with Access Manager. Oracle Adaptive Access Manager provides strong-authentication and risk-based authorization that can be used to provide layered security for Oracle Privileged Account Manager.
To enable Oracle Adaptive Access Manager with Oracle Privileged Account Manager, select Access Manager as the authentication option for the WebGate that is protecting Oracle Privileged Account Manager.
-
If you deployed Oracle Identity Navigator with Oracle Privileged Account Manager, and you are using Oracle Identity Navigator as the user interface for Oracle Privileged Account Manager, you can also protect Oracle Identity Navigator with Access Manager while enabling Oracle Single Sign-On.
Refer to "Integrating with Oracle Identity Navigator" in Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite for instructions.
-
Oracle Privileged Account Manager is protected by the domain agent out-of-the-box.
7.2.2 Enabling Single Sign-On
By default, the Access Manager 11g agent provides Single Sign On functionality for Oracle Privileged Account Manager and the following Identity Management consoles:
-
Oracle Identity Manager
-
Access Manager
-
Oracle Adaptive Access Manager
-
Oracle Authorization Policy Manager
-
Oracle Identity Navigator
The Access Manager agent can only protect consoles in a single domain. If your environment spans multiple domains, you can use Access Manager 11g WebGate for Oracle HTTP Server 11g. Configuring Oracle Privileged Account Manager for WebGate-based single sign-on is the same as configuring Oracle Identity Navigator. Refer to "Integrating with Oracle Identity Navigator" in Oracle Fusion Middleware Integration Guide for Oracle Identity Management Suite.
You can use Access Manager to enable Single Sign On for the Oracle Privileged Account Manager's user interface by using any Access Manager authentication scheme as the challenge method.
The prerequisites are as follows:
-
Oracle HTTP Server has been installed.
When installing Oracle HTTP Server, deselect Oracle WebCache and associated selected components with WebLogic domain.
-
Access Manager 11g has been installed and configured properly.
-
Oracle HTTP Server 11g has been installed and configured as a front-ending proxy web server for Oracle Privileged Account Manager.
-
Access Manager 11g WebGate for Oracle HTTP Server 11g has been installed on the Oracle HTTP Server 11g.
See Also:
Oracle Fusion Middleware Installation Guide for Oracle Identity and Access Management for details about installation of the listed components.
The high-level steps for enabling Single Sign On in Oracle Privileged Account Manager are as follows:
-
Use the Access Manager Administration Console to configure a new resource for the agent under which the Oracle Privileged Account Manager URL is to be protected. For information, see Section 7.2.2.1, "Configure a New Resource for the Agent."
-
Configure Oracle HTTP Server to point to the Access Manager domain which has the resources and policies configured. For information, see Section 7.2.2.2, "Configure Oracle HTTP Server for the Access Manager Domain."
-
Use the Administration Console to add the two new identity providers, namely the Access Manager Identity Asserter and the Oracle Internet Directory Authenticator. For information, see Section 7.2.2.3, "Add New Identity Providers.".
-
Use a WLST command to enable access to more than one application using multiple tabs in a browser session. For information, see Section 7.2.2.4, "Configure Access to Multiple Applications."
7.2.2.1 Configure a New Resource for the Agent
Perform these steps in the Access Manager administration console:
-
Select the Policy Configuration tab.
-
Under Application Domains, select the agent under which the Oracle Privileged Account Manager URL is to be protected (for example,
-OIMDomain). -
Choose Resources and click the create icon to add a new resource. Enter the type, host identifier and value, (
/oinav/…/*) and click the Apply button. -
Choose Protected Policy or the policy whose authentication schema is the LDAP schema. In the resources table, click the add icon and choose the Oracle Privileged Account Manager URL (
/oinav/…/*) from the drop-down list. -
Repeat the step for Authorization Policy.
7.2.2.2 Configure Oracle HTTP Server for the Access Manager Domain
Perform these steps to ensure that Oracle HTTP Server front ends the Oracle WebLogic Server container where Oracle Privileged Account Manager is installed.
-
Navigate to the Oracle HTTP Server server
configdirectory, for example,/scratch/mydir1/oracle/product/11.1.1/as_1/instances/instance1/config/OHS/ohs1), and find themod_wl_ohs.conffile. -
In the
<IfModule mod_weblogic.c>block, add the host and the port number of the Oracle Privileged Account Manager URL to be protected. For example:MatchExpression /oinav* WebLogicHost=host WebLogicPort=port
-
Restart the Oracle HTTP Server server in the OHS install
bindirectory, for example,/scratch/mydir1/oracle/product/11.1.1/as_1/instances/instance1/bin) by executing the following command:-./opmnctl restartproc ias=component=ohs1
7.2.2.3 Add New Identity Providers
Perform these steps to add two new identity providers:
-
Using the Administration Console, navigate to Security Realms, then myrealm, then Providers.
-
Add these two providers: Access Manager Identity Asserter and Oracle Internet Directory Authenticator.
-
Set the Control Flag of the Access Manager Identity Asserter to
Required. -
Update the following settings in the Oracle Internet Directory Authenticator:
-
Set the Control Flag to
Sufficient -
Select the Provider specific tab and make the necessary changes, supplying the host, port, and other credentials of the Oracle Internet Directory server. Configure the correct LDAP setting in the Oracle Internet Directory Authenticator.
The users and Groups in the LDAP will be reflected in the console.
-
-
Re-order the providers as follows:
-
Access Manager Identity Asserter
-
Authenticator
-
Default Authenticator
-
Default Identity Asserter
-
-
Restart Oracle WebLogic Server.
-
Enter the protected Oracle Privileged Account Manager URL, which will have the host and port from the Oracle HTTP Server install:
http://OHSHost:OHSPort/oinav/faces/idmNag.jspx