6 Handling Authorization Calls and Decisions
Oracle Entitlements Server contains different application programming interfaces (API) that allow the caller to request authorization for a particular subject and handle the returned decisions. This chapter contains the following sections.
6.1 Using the PEP API
The AzAPI is a Java API developed by the OpenAZ project and designed to communicate requests for authorization decisions and responses to same. The communications are based on the authorization decision request and response standards defined in the XACML specifications and require that an authorization engine create request and response objects using these definitions. The AzAPI interfaces enable a Policy Decision Point (PDP) to supply and consume all the XACML information required when submitting an authorization resquest and receiving an authorization response.
Note:
More information on the OpenAZ project can be found at http://openliberty.org/.
The Oracle Entitlements Server PEP API are built on top of the AzAPI for protecting either Java or .NET applications. The PEP API contain utility classes for building a Policy Enforcement Point (PEP), and are designed to present a more simplified, scalable interface than the AzAPI, using native Java or .NET data objects rather than XACML data objects. Figure 6-1 illustrates the relationship between the AzAPI, the PEP API and Oracle Entitlements Server.
Figure 6-1 Relationship Between Open AZ API and PEP API
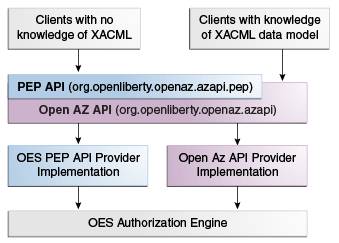
Description of "Figure 6-1 Relationship Between Open AZ API and PEP API"
The following sections contain information on how the AzAPI has been implemented by Oracle Entitlements Server.
6.1.1 Understanding the PEP API
Oracle Entitlements Server provides a Java and a .NET provider implementation of the org.openliberty.openaz.azapi.pep package. The Java PEP API provider is packaged in oracle.security.jps.openaz.pep. .NET provider interfaces are implemented under the Oes.Pep.Api name space.
Note:
The PEP API call the Web Services Security Module through its proxy implementation. This proxy layer will handle failover and caching. For information on installing the Oracle Entitlements Server Web Service Security Module, see the Oracle Fusion Middleware Installation Guide for Oracle Identity Management.
The following sections contain more information.
6.1.1.1 Working with the PEP API
For each PEP API authorization request, the provider implementation will invoke the Oracle Entitlements Server Authorization Engine and return a decision. The implementation is responsible for converting and mapping native Java or .NET objects (subjects, resources, actions and the like) to the underlying security platform. The provider implementation takes the following actions to retrieve an authorization decision. This sequence assumes policies have already been defined for the specified target. The Request and the Response provide a standard format for interacting with a PDP.
-
A request for access is received at the PEP.
A request contains a Subject, Resource, Action, and (optional) Environment attributes. It can be a call to authorize a Subject to access a protected resource, or it may query for what is allowed in terms of actions and authorization decisions.
-
The PEP calls the PEP API which passes a request for authorization (based on the type of Resource being accessed) to the Policy Decision Point (PDP).
The PEP API determines the type of authorization request based on the Resource Type.
-
The PDP requests additional subject, resource, action, environment and other attributes, if applicable.
Attributes are requested from a Policy Information Point (PIP). The PIP returns the requested attributes and the information is passed back to the PDP.
-
The PDP evaluates the request against any relevant policies.
-
The PDP returns a response (including the authorization decision) to the PEP.
A response consists of one or more results. (Multiple results can only be caused by evaluation of a hierarchical resource.) Each result contains a Decision (Permit, Deny), status information (for example, why the evaluation failed) and (optionally) one or more Obligations (the PEP is obligated to act on these before granting or denying access).
-
The PEP fulfills the obligations, if any.
-
The PEP permits access to the resource if the request is granted; otherwise, access is denied.
6.1.1.2 Using the Different PEP API Requests
The PEP API can be used to request access authorization in several ways. One or more subjects can be authorized in a single or bulk authorization call, respectively. Oracle Entitlements Server also supports queries on authorization decisions and actions. Table 6-1, "Understanding the PEP API Authorization Request Types" contains more details on these request types.
Table 6-1 Understanding the PEP API Authorization Request Types
| Authorization Request Type | Input Parameters | Returns |
|---|---|---|
|
Single Authorization Request (Only supported when using permissions) |
|
|
|
Bulk Authorization Request |
|
|
|
Query returns a list of authorization decisions for specified resource/action/subject/environment associations
|
|
|
6.1.1.3 Specifying the PEP API Subject
The Subject requesting authorization to access a protected resource can be defined by passing a string, or an object representing a currently authenticated user.
-
A String representing the value of the Name of the subject as defined in the identity store may be passed; for example, Josh Smith.
-
A Java or .NET object (representing an authenticated user) may be passed.
See Section 6.1.2.1, "Getting a Java PEP API Subject" or Section 6.1.3.1, "Getting a .NET PEP API Subject" for details.
6.1.1.4 Formatting Authorization Request Strings
The PEP API methods contain a string that defines the scope of the request. A resource string is then defined within the scope string. The following sections contain information on how to format these scope and resource strings.
6.1.1.4.1 Formatting the PEP API Scope String
The scope input string is a PDP policy-specific resource representation that encapsulates resource, actions and search scope information. It is represented as:
String scope = "resource = resourceString,actions = actionString1, actionString2, actionString3, searchscope = immediate/children";
The following is true regarding this representation.
-
resourceis required and the resource string should appear first within the scope string. See Section 6.1.1.4.2, "Formatting the PEP API Resource String." -
actionsis optional. If present, it contains a comma separated list of requested actions and they must precede scope. -
searchscopeis optional, is only used with the Query request type, and takes a value of children (the default value) or immediate.-
If the value is
children,resourceStringmay contain only the application identifier as documented in Section 6.1.1.4.2, "Formatting the PEP API Resource String." In this case, the PEP API provider will query the specified resource object and its children (if any). In the following example, Scope string defines a resource which contains a Resource string (with application identifier), no actions and no defined search scope; thus, the search scope is set tochildren, by default.String scope = "resource = PepQueryTest/resource_type_1/resource_1";
-
If the value is
immediate,resourceStringshould be fully qualified as documented in Section 6.1.1.4.2, "Formatting the PEP API Resource String." In this case, the PEP API provider will query the specified resource object. For example:String scope = "resource = PepQueryTest/resource_type_1/resource_1, actions = action1,action2, searchscope=immediate";
-
The following Scope string defines a hierarchical resource.
String scope= "resource = PepQueryTest/hierarchical_type//res1/res2/res3, searchscope= children";
6.1.1.4.2 Formatting the PEP API Resource String
The string should be in the format appId/resourceType/resourceName with the forward slash (/) acting as delimiter. The appId and resourceType cannot be empty or null; the resourceName can be empty for a query request but must be populated for all other requests.
When formatting the string, there is no need to escape the delimiter character if it is used in the resourceName. For example, if there is a hierarchical resource with the name /res1/res2/res3, the resource string passed to the PEP API will be appId/ResType//res1/res2/res3. It is necessary to escape the delimiter character if it is used in the appId or resourceType though. In these cases, a string with more than two delimiters is considered invalid.
Note:
The Resource string myapp/computer\laptop/res1 is invalid because the character after \ is neither / nor \.
The following list of examples illustrate these rules.
-
myapp/computer\/laptop/res1signifies a Resource namedres1in themyappApplication with the Resource Typecomputer/laptop. -
myapp/computer\\laptop/res1signifies a Resource namedres1in themyappApplication with the Resource Typecomputer\laptop. -
myapp/computer/laptop/res1signifies a Resource namedlaptop/res1in themyappApplication with the Resource Typecomputer. -
myapp/computer/laptop\/res1signifies a Resource namedlaptop\/res1in themyappApplication with the Resource Typecomputer. -
myapp/hierarchialResource\\res1\res2\res3signifies a Resource named\res1\res2\res3in themyappApplication with the Resource TypehierarchicalResource.
Note:
For strings in Java, the character \ itself needs to be escaped. Thus, three of the strings previously documented, in Java, are:
-
myapp/computer\\/laptop/mybox -
myapp/computer\\\\laptop/mybox -
myapp/computer\\laptop/mybox
6.1.1.5 Retrieving Authentication Information Using a Query
A Query operation can be initiated using the PEP API. The query accepts the following objects as input parameters, returning the appropriate results.
-
Application - results are returned for all Resource instances for each Resource Type defined in the given Application.
-
Application and Resource Type - results are returned for all Resource instances for the Resource Type in the given Application. This call is valid for both hierarchical and non hierarchical Resource Types.
-
Application, Resource Type and Resource - results are returned for the given Resource instances for the Resource Type in the given Application. If the Resource Type is hierarchical, results are returned for the children of the given Resource instance as well.
There are two types of Queries as described in Table 6-2. Each type of query can operate on hierarchical and non-hierarchical Resource instances.
| Query Type | Returns | Methods |
|---|---|---|
|
Returns allowed/denied actions on a Resource and/or its children (depending on the defined scope) |
Returns a PepRequest that contains privileges of the specified subject.
|
|
|
Returns full authorization results on a Resource and its children. |
Returns full authorization results on a Resource and its children. Returns a PepRequest that can be used to get resource-actions that are allowed or denied access to current subject with given environment parameter. |
|
6.1.2 Using the PEP API for Java
The following sections contain information on how to use the PEP API for Java.
-
Section 6.1.2.2, "Making Simple Java PEP API Authorization Requests"
-
Section 6.1.2.4, "Making Java PEP API Bulk Authorization Requests"
6.1.2.1 Getting a Java PEP API Subject
This section contains sample code that illustrates how the PEP API for Java can retrieve an authenticated subject for an authorization request. It is recommended to call the newPepRequest() method with a Java Authentication and Authorization Service (JAAS) Subject.
Note:
A string subject will be converted to a JAAS subject.
See Section 6.1.1.4, "Formatting Authorization Request Strings" for information on how the scope and resource strings are specified in the following examples.
-
Example 6-1, "Using Authenticated Subject in Java PEP API Request"
-
Example 6-2, "Using WebLogic Server Subject with Java PEP API Request"
-
Example 6-3, "Using Websphere Application Server Subject with Java PEP API Request"
Example 6-1 shows how to get the authenticated user with the login service and use the authenticated subject for a single PEP API authorization request. This code returns an authorization decision based on the specified resource and action. (Bulk and query requests are created and used in a similar way.)
Example 6-1 Using Authenticated Subject in Java PEP API Request
ServiceLocator locator = JpsServiceLocator.getServiceLocator();
LoginService loginService = locator.lookup(LoginService.class);
CallbackHandler cbh = new MyCallbackHandler("name", "password".toCharArray());
LoginContext ctx = loginService.getLoginContext(new Subject(), cbh);
ctx.login();
Subject s = ctx.getSubject();
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Map<String, String> env = new HashMap<String, String>();
env.put("myAttr", "Hello");
//Alternately, a String subject like “tom” can be used.
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Map<String, String> env = new HashMap<String, String>();
env.put("myAttr", "Hello");
PepRequest pepRequest =
PepRequestFactoryImpl.getPepRequestFactory().newPepRequest
(s, action, resourceString, env);
PepResponse response = pepRequest.decide();
System.out.println("result: " + response.allowed());
Map<String, Obligation> obligations = response.getObligations();
for (String name : obligations.keySet())
{
System.out.print("obligation: name = " + name + ", values = " +
obligations.get(name).getStringValues());
}
Example 6-2 illustrates how, after Java Enterprise Edition (JEE) authentication, you can get the WebLogic Server subject to use with the PEP API.
Example 6-2 Using WebLogic Server Subject with Java PEP API Request
import weblogic.security.Security;
...
Subject s = Security.getCurrentSubject();
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Map<String, String> env = new HashMap<String, String>();
env.put("myAttr", "Hello");
PepResponse response =
PepRequestFactoryImpl.getPepRequestFactory().newPepRequest
(s, action, resourceString, env).decide();
System.out.println("result: " + response.allowed());
Map<String, Obligation> obligations = response.getObligations();
for (String name : obligations.keySet()) {
System.out.print("obligation: name = " + name + ", values = "
+ obligations.get(name).getStringValues());
}
Example 6-3 illustrates how, after Java Enterprise Edition (JEE) authentication, you can get the Websphere Application Server subject to use with the PEP API.
Example 6-3 Using Websphere Application Server Subject with Java PEP API Request
import com.ibm.websphere.security.auth.WSSubject;
...
Subject s = WSSubject.getCallerSubject();
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Map<String, String> env = new HashMap<String, String>();
env.put("myAttr", "Hello");
PepResponse response = PepRequestFactoryImpl.getPepRequestFactory().
newPepRequest(s, action, resourceString, env).decide();
System.out.println("result: " + response.allowed());
Map<String, Obligation> obligations = response.getObligations();
for (String name : obligations.keySet())
{
System.out.print("obligation: name = " + name + ", values =
" + obligations.get(name).getStringValues());
}
6.1.2.2 Making Simple Java PEP API Authorization Requests
Oracle Entitlements Server offers two types of query requests. You can request a list of all actions for a particular Resource (and its children), or you can request complete authorization results for a particular Resource (and its children). Both types of queries will retrieve results for all instantiated Resources of a given Resource Type. Example 6-4 is a query request against a particular Resource. Note that the search scope is defined as immediate. See Section 6.1.1.4, "Formatting Authorization Request Strings" for information on how the scope and resource strings are specified.
Example 6-4 Requesting Java PEP API Authorization Against a Resource
... String scope = "resource = PepQueryTest/resource_type_1/resource_1, actions = action1, searchscope=immediate"; PepRequest req = PepRequestFactoryImpl.getPepRequestFactory(). newQueryPepRequest(subject, env, scope, PepRequestQueryType.RETURN_ONLY_ALLOWED_RESULTS); PepResponse resp = req.decide(); //List of RuntimeAction objects List actions = (List) resp.getAction(); RuntimeResource resource = (RuntimeResource) resp.getResource();
6.1.2.3 Processing Java PEP API Obligations
An Obligation specifies optional information that is returned to the calling application with the access decision. Each obligation in the PEP API response has a map in type Map<String, String>. (There are no double quotes around the String value.) See Section 6.1.1.4, "Formatting Authorization Request Strings" for information on how the scope and resource strings are specified in the following examples.
Example 6-5 is an authorization request that also requests any Obligations.
Example 6-5 Making PEP API Request and Parsing Response
Subject s = ...; // a Jps subject (with app roles inside)
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Map<String, String> env = new HashMap<String, String>();
env.put("myAttr", "Hello");
PepResponse response =
PepRequestFactoryImpl.getPepRequestFactory().newPepRequest
(s,action,resourceString,env).decide();
System.out.println("result: " + response.allowed());
Map<String, Obligation> obligations = response.getObligations();
for (String name : obligations.keySet())
{ System.out.print("obligation: name = " + name + ", values = " + obligations.get(name).getStringValues()); }
Example 6-6 is an example of an Obligation output. Again, there are no double quotes around the string value.
Example 6-6 Returned Obligations from Example 6-5
result: true
obligation: name = MyObligation, values =
{attr1=18, attr2=World, time=08:59:59, attr_date=12/29/2010}
6.1.2.4 Making Java PEP API Bulk Authorization Requests
Example 6-7 is sample code written to request authorization in bulk. It encapsulates two requests.
Example 6-7 Requesting Bulk Authorization with the Java PEP API
public void testBulkRequest() throws Exception {
Map<String, String> env = new HashMap<String, String>();
env.put("dynamic_attr", "dynamic_attr_value");
String resourceString =
MY_APPLICATION + "/" + MY_RESOURCE_TYPE + "/" + MY_RESOURCE;
String wrongAction = "wrong_action";
PepResponse resp = pepRequestFactory.newBulkPepRequest(
subject,
Arrays.asList(new Object[]{MY_ACTION, wrongAction}),
Arrays.asList(new Object[]{resourceString, resourceString}),
env).decide();
//
// response corresponding to first authorization decision
//
assertTrue(resp.next());
assertTrue("resp.allowed() is expected to be true!! ", resp.allowed());
assertSame(MY_ACTION, resp.getAction());
assertSame(RESOURCE_STRING, resp.getResource());
//
// response corresponding to second authorization decision
//
assertTrue(resp.next());
assertFalse("resp.allowed() is expected to be false!! ", resp.allowed());
assertSame(wrongAction, resp.getAction());
assertSame(RESOURCE_STRING, resp.getResource());
//
// call next() again..
//
assertFalse(resp.next());
}
See Section 6.1.1.4, "Formatting Authorization Request Strings" for information on how the scope and resource strings are specified in these examples.
6.1.2.5 Making Java PEP API Query Requests
The PEP API for Java contains newQueryPepRequest() methods for retrieving information regarding the scope of resources and actions covered by the authorization request. The scope is based on subject and environment objects passed to the method. (See Section 6.1.1.4, "Formatting Authorization Request Strings" for information on how the scope and resource strings are specified.) The information returned depends on how the PepRequestQueryType is defined. It takes one of the following values.
-
RETURN_ONLY_ALLOWED_RESULTS returns a list of resource action pairs that are allowed within the defined scope.
-
RETURN_ONLY_DENIED_RESULTS returns a list of resource action pairs that are denied within the defined scope.
-
VERBOSE returns all results for each resource action pairs requested within the defined scope.
Example 6-8 illustrates the signature in which you can define the query type as one of the values in the PepRequestQueryType enum.
Example 6-8 Defining the Java PEP API Query Type
public PepRequest newQueryPepRequest
(object subjectObj,
Object environmentObj
String scope
PepRequestQueryType queryType)
Example 6-9 illustrates the signature in which you can define a response type as one of the values in the new PepResponseType enum. resourceActionOnly is a Boolean indicating whether information describing just the identity of the resource and actions (to which the query applies) will be returned in the response or, if full responses (including Obligations) will be returned.
Example 6-9 Defining the New Java PEP API Response Type
public PepRequest newQueryPepRequest
(java.lang.Object subjectObj,
java.lang.Object resourceObj,
java.lang.Object actionObj,
java.lang.Object environmentObj,
org.openliberty.openaz.azapi.constants.PepResponseType responseType,
boolean resourceActionOnly)
Example 6-10 is a query requesting all allowed and denied actions against a particular Resource and its children. Note that the search scope is defined as children.
Example 6-10 Verbose Query For a Resource and Children with Java PEP API
...
String scope = "resource=PepQueryTest/Hierarchical/\\/res1";
PepRequest req = PepRequestFactoryImpl.getPepRequestFactory
(subject, env, scope, PepRequestQueryType.VERBOSE);
PepResponse resp = req.decide();
ArrayList arrayList;
List grantedActions;
List deniedActions;
int i = 0;
//there can be more than 1 result when searchscope="children"
while (resp.next()) {
RuntimeResource res = (RuntimeResource) resp.getResource();
//both granted actions and denied actions are returned for PepRequestQueryType.VERBOSE
//PepResponse.getAction() returns an ArrayList where ArrayList.get(0) returns list of granted actions;
//it returns an ArrayList where ArrayList.get(1) returns list of denied actions;
arrayList = (ArrayList) resp.getAction();
grantedActions = null;
deniedActions = null;
if (arrayList != null) {
grantedActions = (List) arrayList.get(0);
deniedActions = (List) arrayList.get(1);
}
String resourceName = res.getResourceName();
}
Example 6-11 illustrates query code that returns only allowed results in the immediate search scope.
Example 6-11 Query Request for Immediate Searchscope with Java PEP API
String scope = "resource=PepQueryTest/resource_type_1/resource_1, actions=action1, searchscope=immediate"; PepRequest req = PepRequestFactoryImpl.getPepRequestFactory().newQueryPepRequest (subject, env, scope, PepRequestQueryType.RETURN_ONLY_ALLOWED_RESULTS); PepResponse resp = req.decide(); //Getting list of RuntimeAction objects List actions = (List) resp.getAction(); RuntimeResource resource = (RuntimeResource) resp.getResource();
Example 6-12 illustrates query code that returns allowed and denied results in the children search scope.
Example 6-12 Query Request for Children Searchscope with Java PEP API
String scope = "resource=PepQueryTest/Hierarchical/\\/res1";
PepRequest req = PepRequestFactoryImpl.getPepRequestFactory
(subject, env, scope, PepRequestQueryType.VERBOSE);
PepResponse resp = req.decide();
ArrayList arrayList;
List grantedActions;
List deniedActions;
int i = 0;
//there can be more than 1 result when searchscope="children"
while (resp.next()) {
RuntimeResource res = (RuntimeResource) resp.getResource();
//both granted actions and denied actions are returned for //PepRequestQueryType.VERBOSE
//PepResponse.getAction() returns an ArrayList where ArrayList.get(0)
//returns list of granted actions;
//it returns an ArrayList where ArrayList.get(1) returns list of denied actions;
arrayList = (ArrayList) resp.getAction();
grantedActions = null;
deniedActions = null;
if (arrayList != null) {
grantedActions = (List) arrayList.get(0);
deniedActions = (List) arrayList.get(1);
}
String resourceName = res.getResourceName();
}
Example 6-13 illustrates query code that returns only allowed and denied results along with any Obligations.
Example 6-13 Query Request for Allow/Deny Results & Obligations with Java PEP API
String resourceString = "MyApplication/MyResourceType/MyResource";
String action = "read";
PepRequest req = pepRequestFactory.newQueryPepRequest(subject,
resourceString, action, null, PepResponseType.ALL_RESULTS, true);
PepResponse resp = req.decide();
while (resp.next()) {
//print authorization results for each resource and action.
System.out.println(“For resource “ + resp.getResource() + “ and action” +
resp.getAction() + “ authorization allowed = “ + resp.allowed());
//check out obligations
Map<String, Obligation> obligations = resp.getObligations();
Set<String> obIds = obligations.keySet();
for (String obId : obIds) {
Obligation obligation = obligations.get(obId);
Map<String, String> strValus = obligation.getStringValues();
}
}
6.1.2.6 Configuring the Java PEP API
To use the Java PEP API, details regarding the identity store, the policy store, the Policy Distribution Service, and the user assertion login module must be defined in the jps-config.xml configuration file.
Note:
See the Oracle Fusion Middleware Security Guide for more information on this configuration file. Parameters specific to Oracle Entitlements Server are documented in the Oracle Fusion Middleware Administrator's Guide for Oracle Entitlements Server.
Example 6-14 is a snippet of jps-config.xml, copied for informational purposes.
Example 6-14 Sample jps-config.xml File
... <serviceInstance name="idstore.ldap" provider="idstore.ldap.provider"> <description>LDAP Identity Store Service Instance</description> <property name="idstore.config.provider" value="oracle.security.jps.wls.internal.idstore.WlsLdapIdStoreConfigProvider"/> <property name="CONNECTION_POOL_CLASS" value="oracle.security.idm.providers.stdldap.JNDIPool"/> </serviceInstance> <serviceInstance name="idstore.loginmodule" provider="jaas.login.provider"> <description>Identity Store Login Module</description> <property name="loginModuleClassName" value="oracle.security.jps.internal.jaas.module.idstore.IdStoreLoginModule"/> <property name="jaas.login.controlFlag" value="REQUIRED"/> </serviceInstance> <serviceInstance name="pdp.service" provider="pdp.service.provider"> <description>Runtime PDP service instance</description> <property name="oracle.security.jps.runtime.pd.client.sm_name" value="mixedsm"/> <property name="oracle.security.jps.runtime.pd.client.localpolicy.work_folder" value="/ade/diazhao_entsec_ 2/oracle/work/utp/buildout/functional/platsec/tempdir/mixedpd-work"/> <property name="oracle.security.jps.pdp.AuthorizationDecisionCacheEnabled" value="true"/> <property name="oracle.security.jps.pdp.AuthorizationDecisionCacheEvictionCapacity" value="500"/> <property name="oracle.security.jps.pdp.AuthorizationDecisionCacheEvictionPercentage" value="10"/> <property name="oracle.security.jps.pdp.AuthorizationDecisionCacheTTL" value="60"/> <property name="oracle.security.jps.pd.client.PollingTimerEnabled" value="true"/> <property name="oracle.security.jps.pd.client.PollingTimerInterval" value="10"/> <property name="oracle.security.jps.ldap.cache.refresh.interval" value="10000"/> <property name="oracle.security.jps.runtime.pd.client.policyDistributionMode" value="mixed"/> </serviceInstance> <serviceInstance name="policystore.db" provider="policystore.provider"> <property name="policystore.type" value="DB_ORACLE"/> <property name="oracle.security.jps.farm.name" value="cn=testfarm_diazhao_entsec_2"/> <property name="server.type" value="DB_ORACLE"/> <property name="oracle.security.jps.ldap.root.name" value="cn=jpsroot"/> <property name="datasource.jndi.name" value="platsec_test_ds"/> </serviceInstance> <serviceInstance name="user.assertion.loginmodule" provider="jaas.login.provider"> <description>User Assertion Login Module</description> <property name="loginModuleClassName" value="oracle. security.jps.internal.jaas.module.assertion.JpsUserAssertionLoginModule"/> <property name="jaas.login.controlFlag" value="REQUIRED"/> </serviceInstance> ... <jpsContexts default="default"> <jpsContext name="default"> <serviceInstanceRef ref="credstore.db"/> <serviceInstanceRef ref="keystore.db"/> <serviceInstanceRef ref="policystore.db"/> <serviceInstanceRef ref="audit.db"/> <serviceInstanceRef ref="trust"/> <serviceInstanceRef ref="pdp.service"/> <serviceInstanceRef ref="attribute"/> <serviceInstanceRef ref="idstore.ldap"/> </jpsContext> </jpsContexts>
6.1.3 Using the PEP API for .NET
The PEP API for .NET can be used to integrate Oracle Entitlements Server authorization into applications built using Microsoft .NET technology. The .NET application calls the PEP API for .NET to get an authorization decision. (The PEP API for .NET invokes the authorization web service exposed by the Web Services Security Module through its proxy implementation (which handles the failover and caching).
To invoke the .NET Security Module for authorization, create an IPepRequest where a list of action objects and a corresponding list of resource objects are provided to represent applicable resource-action pairs. An authorization decision for each resource-action pair will be returned when IPepRequest.decide() is invoked. The following sections contain information on how to use the PEP API for .NET applications.
-
Section 6.1.3.2, "Making Simple .NET PEP API Authorization Requests"
-
Section 6.1.3.4, "Making .NET PEP API Bulk Authorization Requests"
6.1.3.1 Getting a .NET PEP API Subject
You can define a subject for the IPepRequest call by doing one of the following:
-
Pass the user name as a String.
-
Pass the
System.Security.Principal.IIdentityuser object. This object is the .NET standard and signifies authentication by the Windows operating system which Oracle Entitlements Server supports. Get theIIdentityuser object as follows:-
For a standalone application, use:
IIdentity iIdentity = WindowsIdentity.GetCurrent();
-
For a web application, use:
IIdentity iIdentity = (IIdentity)(HttpContext.Current.User.Identity);
-
-
Use the
UserPricipalclass to set the user information and pass aUserPrincipalobject if the .NET application has custom authentication.
6.1.3.2 Making Simple .NET PEP API Authorization Requests
Oracle Entitlements Server offers requests for authorization (single and bulk) and queries. You can query for a list of all actions for a particular Resource (and its children), or you can request complete authorization results for a particular Resource (and its children). Both types of queries can also be used to retrieve results for all instantiated Resources of a given Resource Type.
Authorization information that is passed includes an object corresponding to authenticated subject (for example, iIdentity), a list of objects representing the actions [for example, String (read)], a list of objects representing the Resources (for example, applicationId/resourcetype/resource), and an object representing the environment (containing information passed in the form of a hashtable). See Section 6.1.1.4, "Formatting Authorization Request Strings" for information on how the scope and resource strings are specified in Example 6-15, "Requesting .NET PEP API Authorization Against a Resource". Note the code also contains an Obligation as discussed in Section 6.1.3.3, "Processing .NET PEP API Obligations."
Example 6-15 Requesting .NET PEP API Authorization Against a Resource
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
Hashtable env = new Hashtable();
env.Add("myAttr", "Hello");
IIdentity iIdentity = WindowsIdentity.GetCurrent();
IPepResponse response =
PepRequestFactoryImpl.GetPepRequestFactory().NewPepRequest
(iIdentity, action, resourceString, env).Decide();
Console.Write ("result: " + response.Allowed());
Dictionary<String, IObligation> obligations = response.GetObligations();
foreach (KeyValuePair<String, IObligation> entry in obligations)
{Console.WriteLine
("Print the obligation" + entry.Value.GetStringValues());
}
Example 6-16 requests authorization using the .NET PEP API when the subject is specified as a string.
Example 6-16 Requesting .NET PEP API Authorization with a String Subject
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
IPepResponse response = PepRequestFactoryImpl.GetPepRequestFactory().
NewPepRequest("John", action, resourceString).Decide();
Console.WriteLine("result: " + response.Allowed());
Example 6-17 requests authorization using the .NET PEP API when the subject is specified as UserPrincipal.
Example 6-17 Requesting .NET PEP API Authorization with a UserPrincipal Subject
UserPrincipal userPrincipal = new UserPrincipal("user1");
Hashtable envTable = new Hashtable();
String action = "read";
String resourceString = "MyApplication/MyResourceType/MyResource";
IPepResponse response = PepRequestFactoryImpl.GetPepRequestFactory().
NewPepRequest
(userPrincipal, action, resourceString, envTable).Decide();
Console.WriteLine("result: " + response.Allowed());
6.1.3.3 Processing .NET PEP API Obligations
The GetObligationId() method of the IObligation interface is used to retrieve any obligation relevant to the authorization request. An Obligation specifies optional information that is returned to the calling application with the access decision. Example 6-15 (in the previous section) is an authorization request that also gets any Obligations. Example 6-18 is another example.
Example 6-18 Requesting Single Authorization and Obligations with the .NET PEP API
String appId = "test-app";
String userName = "weblogic";
String resourceType = "Electronics-MyRT";
String resource1 = ":Nelco1";
String action1 = "view";
String action2 = "off";IPepRequestFactory pepRequestFactoryImpl =
PepRequestFactoryImpl.GetPepRequestFactory();
Hashtable envTable = new Hashtable();
envTable.Add("electronicType", "entertainment");
IPepResponse pepresponse = pepRequestFactoryImpl.NewPepRequest
(userName, action1, appId + "/" + resourceType + "/" + resource1,
envTable).Decide();
Dictionary<String,IObligation> obligations=pepresponse.GetObligations();
foreach (KeyValuePair<String, IObligation> entry in obligations)
{
Console.WriteLine("Print the obligation" + entry.Value.GetStringValues());
}
6.1.3.4 Making .NET PEP API Bulk Authorization Requests
See Section 6.1.1.4, "Formatting Authorization Request Strings" for information on how the scope and resource strings are specified. Example 6-19 illustrates a call for bulk authorization.
Example 6-19 Requesting Bulk Authorization
String appId = "test-app";
String userName = "weblogic";
String authenticatedUser = "weblogic";
//String resourceType = "LibraryResourceType";
String resourceType = "Electronics-MyRT";
String resource1 = ":Nelco1";
String resource2 = ":Nelco1:TV";
String resource3 = ":Nelco1:TV:small-screen";
String action1 = "view";
String action2 = "on";
String action3 = "off";
IPepRequestFactory pepRequestFactoryImpl =
PepRequestFactoryImpl.GetPepRequestFactory();
IPepResponse pepresponse=null;
bool isNext = false;
Collection<Object> resList = new Collection<Object>();
resList.Add(appId + "/" + resourceType + "/" + resource1);
resList.Add(appId + "/" + resourceType + "/" + resource2);
Collection<Object> actList = new Collection<Object>();
actList.Add(action1);
actList.Add(action3);
Hashtable envTable = new Hashtable();
envTable.Add("electronicType", "entertainment");
pepresponse = pepRequestFactoryImpl.NewBulkPepRequest
(userName, actList, resList, envTable).Decide();
//First authorization decision
isNext = pepresponse.Next();
Debug.Assert(isNext == false, "Error in bulk operation");
Debug.Assert(pepresponse.Allowed() == false, "Error in bulk operation");
//Second authorization decision
isNext = pepresponse.Next();
Debug.Assert(isNext == false, "Error in bulk operation");
Debug.Assert(pepresponse.Allowed() == true, "Error in bulk operation");
6.1.3.5 Making .NET PEP API Query Requests
The PEP API for .NET contains a newQueryPepRequest() method for retrieving information regarding the scope of resources and actions covered by the authorization request. The scope is based on subject and environment objects passed to the method. (See Section 6.1.1.4, "Formatting Authorization Request Strings" for information on how the scope and resource strings are specified.) The information returned depends on how the PepRequestQueryType is defined. It takes one of the following values.
-
RETURN_ONLY_ALLOWED_RESULTS returns a list of resource action pairs that are allowed within the defined scope. See Example 6-20.
-
RETURN_ONLY_DENIED_RESULTS returns a list of resource action pairs that are denied within the defined scope. See Example 6-21.
-
VERBOSE returns all results for each resource action pairs requested within the defined scope. See Example 6-22.
Example 6-20 .NET Query for List of Allowed Resource Action Pairs
String appId = "MyApplication";
String resourceType = "resourceType";
String resource = "res";
IIdentity iIdentity = WindowsIdentity.GetCurrent();
IPepRequestFactory pepRequestFactoryImpl =
PepRequestFactoryImpl.GetPepRequestFactory();
IPepResponse pepresponse=null;
String actionStr="view,on,off";
bool isNext=false;
String scopeImmediate = "resource=" + "application" + "/" + "resource_type" +
"/" + "resource2" + ", actions=" + actionStr + ",searchscope=immediate";
Hashtable envTable = new Hashtable();
envTable.Add("electronicType", "entertainment");
pepresponse = pepRequestFactoryImpl.NewQueryPepRequest
(iIdentity, envTable,scopeImmediate,PepRequestQueryType.
RETURN_ONLY_ALLOWED_RESULTS).Decide();
isNext=pepresponse.Next();
Object act = pepresponse.GetAction();
List<String> actList = (List<String>)act;
if (actList.Contains("view") && actList.Contains("on"))
{ Debug.Assert(actList.Count == 2, "Invalid result");
}
Example 6-21 .NET Query for List of Denied Resource Action Pairs
String appId = "MyApplication";
String resourceType = "resourceType";
String resource = "res";
IIdentity iIdentity = WindowsIdentity.GetCurrent();
IPepRequestFactory pepRequestFactoryImpl =
PepRequestFactoryImpl.GetPepRequestFactory();
IPepResponse pepresponse=null;
String actionStr = "view,on,off";
bool isNext = false;
String scopeImmediate = "resource=" + "application" + "/" + "resource_type" +
"/" + "resource2" + ", actions=" + actionStr + ",searchscope=immediate";
Hashtable envTable = new Hashtable();
envTable.Add("electronicType", "entertainment");
pepresponse = pepRequestFactoryImpl.NewQueryPepRequest
(iIdentity, envTable, scopeImmediate, PepRequestQueryType.
RETURN_ONLY_DENIED_RESULTS).Decide();
isNext = pepresponse.Next();
Object act = pepresponse.GetAction();
List<String> actList = (List<String>)act;
if (actList.Count == 1 || actList[0].Equals("off"))
{
Debug.Assert(actList.Count == 1, "Invalid result");
}
Example 6-22 .NET Query for List of All Resource Action Pairs
String appId = "MyApplication";
String resourceType = "resourceType";
String resource = "res";
IIdentity iIdentity = WindowsIdentity.GetCurrent();
//for standalone
IPepRequestFactory pepRequestFactoryImpl =
PepRequestFactoryImpl.GetPepRequestFactory();
IPepResponse pepresponse=null;
String actionStr = "view,on,off";
String scopeImmediate = "resource=" + "application" + "/" + "resource_type" +
"/" + "resource2" + ", actions=" + actionStr + ", searchscope=immediate";
Hashtable envTable = new Hashtable();
envTable.Add("electronicType", "entertainment");
pepresponse = pepRequestFactoryImpl.NewQueryPepRequest
(iIdentity, envTable, scopeImmediate, PepRequestQueryType.VERBOSE).Decide();
//isNext = pepresponse.Next();
Object act = pepresponse.GetAction();
List<List<String>> actList = (List<List<String>>)act;
List<String> actListAllowed = actList[0];
List<String> actListDenied = actList[1];
if (actListAllowed.Count == 2)
{ Debug.Assert(actListAllowed.Count == 2, "Invalid result");
}
if (actListDenied.Count == 1)
{
Debug.Assert(actListDenied.Count == 1, "Invalid result");
}
Example 6-23 illustrates a query for authorization results for a specified resource and its children. Note that searchscope=children.
Example 6-23 Requesting Authorization Results for a Resource and Its Children
IPepRequestFactory pepRequestFactoryImpl =
PepRequestFactoryImpl.GetPepRequestFactory();
IPepResponse pepresponse=null;
String actionStr = "view,on,off";
String scopeImmediate = "resource=" + "application" + "/" + "resource_type" +
"/" + "resource2" + ", actions=" + actionStr + ",searchscope=children";
Hashtable envTable = new Hashtable();
envTable.Add("electronicType", "entertainment");
IIdentity iIdentity = WindowsIdentity.GetCurrent();pepresponse = pepRequestFactoryImpl.NewQueryPepRequest
(iIdentity, envTable, scopeImmediate, PepRequestQueryType.VERBOSE).Decide();
//isNext = pepresponse.Next();
Object act = pepresponse.GetAction();
List<List<String>> actList = (List<List<String>>)act;
List<String> actListAllowed = actList[0];
List<String> actListDenied = actList[1];
if (actListAllowed.Count == 2)
{ Debug.Assert(actListAllowed.Count == 2, "Invalid result");
}
if (actListDenied.Count == 1)
{
Debug.Assert(actListDenied.Count == 1, "Invalid result");
}
6.1.3.6 Configuring the .NET PEP API
The .NET PEP API are exposed to Microsoft .NET applications through Dynamic Link Libraries (DLL). The .NET application developer must incorporate OES-PEP.dll as part of the protected application. Also, as part of the configuration process:
-
Incorporate
OES-PEP.dllas part of the protected application. This is done by the .NET application developer. -
Update the following properties in the
dotnetsm_config.propertiesfile located in theOES_CLIENT_HOME/oessm/dotnetsm/configtool/directory.-
gac.utility: defines the Global Assembly utility path of the .NET framework with which the DLL have been registered. -
wssm.smurl: defines the URL of the Web Service Security Module used by the .NET application to communicate with Oracle Entitlements Server. -
application.config.file: defines the configuration file of the protected application. This parameter has two possible values. If it is a web application, the configuration file is namedweb.config; if it is a standalone application, the configuration file is namedapp.config. -
operation: defines the action for which you are preparing, this parameter has two possible values.configdenotes configuration;removewill remove all configuration that has been added to the .NET application's configuration file as well as remove the registeredOES-PEP.dllandlog4net.dllfrom the GAC utility. -
application.log4NetXmlfil: defines the path of thelog4net.xmlwhich will generate the log file for the .NET Security Module. If the .NET application has already generated the log file, use the existinglog4net.xmllocation. Otherwise, use the .NET Security Module'slog4net.xmlfile located inOES_CLIENT_HOME/dotnetsm/logging/.
-
-
Run the configuration tool on the Windows machine using the following command where
smTypedenotes the type of Security Module instantiated (in this case,dotnet) andsmConfigIddenotes the identifier defined when the Security Module was instantiated (in this case,myDotnet).config.cmd -smType dotnet -smConfigId myDotnet
This tool will register
OES-PEP.dllandlog4net.dllon the Windows machine that is hosting the protected application and update the application's configuration file (web.configorapp.config) with the locations of the Web Services Security Module and logging configuration files. Additionally, the following properties are defined:-
oracle.security.jps.pdp.proxy.RequestTimeoutMilliSecs- interval in which a request times out if the server is not responding. The default value is 10 (seconds). -
oracle.security.jps.pdp.proxy.FailureRetryCount- number of attempts to contact a server before trying an alternate failover server. The default value is 3 (attempts). -
oracle.security.jps.pdp.proxy.FailbackTimeoutMilliSecs- interval of time after which communication may be re-attempted with a primary server. The default value is 3 (minutes). -
oracle.security.jps.pdp.proxy.SynchronizationIntervalMilliSecs- defines how often the PDP Proxy polls the PDP server in order to synchronize state. For example, the interval is used to periodically check whether the authorization cache has to be flushed. The default value is 60 (seconds).
-
6.2 Making checkPermission() Calls
checkPermission() uses Java Permission objects to determine access to protected resources. A Java Permission object represents access to a resource and is constructed and assigned (access granted) based on the configured policy in effect. Oracle Entitlements Server supports the use of the checkPermission() method in the following standard classes:
-
java.lang.SecurityManager -
java.security.AccessControllerNote:
The static
AccessController.checkPermissionmethod uses the default access control context (the context inherited when the thread was created). To check permissions on some other context, call the instancecheckPermission()method on a particularAccessControlContextinstance.
Additionally, Oracle Entitlements Server supports the use of the checkPermission() method in the oracle.security.jps.util.JpsAuth class.
Tip:
Oracle recommends the use of the checkPermission() method in the oracle.security.jps.util.JpsAuth class as it provides improved debugging support, better performance, and audit support.
When invoking the checkPermission() method (in a JavaSE application), make sure:
-
The
java.security.policysystem property has been set to the location of the Oracle Platform Security Services/Oracle WebLogic Server policy file. -
Your application first calls the
setPolicy()method to explicitly set the policy provider. This is illustrated by the following sample code.java.security.Policy.setPolicy(new oracle.security.jps.internal.policystore.JavaPolicyProvider());
oracle.security.jps.util.JpsAuth.checkPermission() works exactly as the standard methods by accepting a Permission object. If the requested access is allowed, checkPermission() returns quietly; if denied, an AccessControlException is thrown. Example 6-24 illustrates how you might use checkPermission().
Example 6-24 Using the checkPermission() Method
java.security.Policy.setPolicy(new
oracle.security.jps.internal.policystore.JavaProvider()); // Java SE env only
PolicyContext.setContextID(TARGET_APP); // Java SE env only
// authorization runtime
Subject s = new Subject(); s.getPrincipals().add(new WLSUserImpl("wcai")); s.setReadOnly();
JpsSubject.invokeAs(s, new PrivilegedAction<Object>() {
public Object run() {
FilePermission perm2 = new FilePermission(“HARRY_PORTER”, "read");
psAuth.checkPermission(perm2);
return null;
}
6.3 Using the XACML Gateway
Oracle Entitlements Server allows external applications to ask authorization questions using the XACML 2.0 protocol. The Web Services Security Module contains a XACML gateway that allows it to receive XACML authorization requests and return XACML authorization responses. This capability is supported only when using the Multi-Protocol Security Module.
The Web Services Security Module XACML gateway acts as a remote PDP. It uses the standard XACML 2.0 context to convey authorization requests and responses between the PEP and the PDP. Here is the processing sequence for a XACML authorization request.
-
The PEP (application) establishes a session, authenticates a user and gets a valid token for the principal.
Example 6-25 illustrates how to establish the session and send a XACML 2.0 authorization request. Example 6-26 illustrates an alternative option.
Example 6-25 Sample Code to Establish Session For XACML Gateway
setupSession(); request = createRequest(); try { resp = xacmlSvc.authorize(request); } catch (AxisFault af) { if (isTokenExpired(af)) { resetupSession(); try { resp = xacmlSvc.authorize(request); } catch (RemoteException e) { throw new XACMLException("Error calling the XACML service.", e); } } else { throw new XACMLException(“Error calling the XACML service.”, af); } } catch (RemoteException e) { throw new XACMLException("Error calling the XACML service.", e); } private boolean isTokenExpired(AxisFault af) { String faultReason = af.getFaultReason(); if((faultReason != null) && (faultReason.indexOf ("IdentityAssertionException") != -1)) { return true; } return false; } private void setupSession() throws XACMLException { if (identity == null) { establishSession(); } } private void resetupSession() throws XACMLException { establishSession(); } private void establishSession() throws XACMLException { try { EstablishSessionType sess = new EstablishSessionType(); sess.setPrincipalsInfo(convertSubjectToPrincipalsInfo(subject)); sess.setRequestedCredentialType(OES_CREDENTIAL_TYPE); AuthenticationResultType result = atzSvc.establishSession(sess); identity = result.getIdentityAssertion(); } catch (Exception e) { throw new XACMLException("Unable to authenticate user.", e); } if (identity == null) { throw new XACMLException("Null identity received. Unable to establish session for " + subject); } System.out.println("Authentication Succeeded, Identity: "); MessageElement ele = identity.get_any()[0]; System.out.println(ele.getFirstChild()); }Example 6-26 illustrates a new mode which can pass the Subject on every request and doesn't require the
establishSessionmethod. The previous mode, Example 6-25, is still supported.Example 6-26 Sample Code To Establish Session with Principal Information
/** * Test authorize for user role in new mode which send the principal info in every request. * @throws Exception */ public void testAtzForUserRoleNewMode() throws Exception { SubjectType sbjct1 = constructSubject(OTHER_USER, new String[]{OTHER_ROLE}); SubjectType sbjct2 = constructSubject(ADMIN_USER, new String[]{ADMIN_ROLE}); printTestHeader("Deny Test: user \"" + OTHER_USER + "\" is in role \"" + OTHER_ROLE + "\""); sendRequest(new SubjectType[]{sbjct1}, new ResourceType[]{resTest1}, actionWrite, emptyEnv); printTestHeader("Permit Test: user \"" + ADMIN_USER + "\" is in role \"" + ADMIN_ROLE + "\""); sendRequest(new SubjectType[]{sbjct2}, new ResourceType[]{resTest1}, actionWrite, emptyEnv); } -
The PEP sends a XACML request containing the token to the PDP (Security Module).
Example 6-27 iluustrates how to create a XACML authorization request.
Example 6-27 Creating a XACML Request
private RequestType createRequest() throws XACMLException { // create resource String res = "Library/LibraryResourceType/Book"; AttributeType attr = createAttribute(res, RESOURCE_ID, XML_STRING_TYPE); ResourceType resource = new ResourceType(null, new AttributeType[]{attr}); // create action String actionStr = "borrow"; attr = createAttribute(actionStr, ACTION_ID, XML_STRING_TYPE); ActionType action = new ActionType(new AttributeType[]{attr}); // create environment String isRegistered = input.getString("Is the user registered in the library (yes|no): "); String numberOfBorrowedBooks = input.getString("How many books has the user borrowed already:: "); EnvironmentType env; List attrs = new ArrayList(); attrs.add(createAttribute(isRegistered, XACML_NAMESPACE + "RegisteredAttribute", XML_STRING_TYPE)); attrs.add(createAttribute(numberOfBorrowedBooks, XACML_NAMESPACE + "NumberOfBorrowedBooksAttribute", XML_STRING_TYPE)); // obligations attrs.add(createAttribute(LIST_VAL1, XACML_NAMESPACE + ATTRIBUTE_NAME, XML_STRING_TYPE)); attrs.add(createAttribute(LIST_VAL2, XACML_NAMESPACE + ATTRIBUTE_NAME, XML_STRING_TYPE)); env = new EnvironmentType((AttributeType[])attrs.toArray(new AttributeType[attrs.size()])); // subject attr = createAttribute(identity.get_any(), SUBJECT_ID, XACML_NAMESPACE + OES_CREDENTIAL_TYPE); SubjectType subject = new SubjectType(new AttributeType[]{attr}, null); // now construct the request with subject, resource, action and environment. return new RequestType(new SubjectType[]{subject}, new ResourceType[]{resource}, action, env); }Example 6-28 is a sample XACML 2.0 authorization request. The
SSM-SOAPWS_xacml.wsdlfile provides the operation interface definitions.Example 6-28 XACML 2.0 Authorization Request
<Request xmlns="urn:oasis:names:tc:xacml:2.0:context:schema:os"> <Subject xsi:type="ns1:SubjectType" xmlns:ns1="urn:oasis:names:tc:xacml:2.0:context:schema:os" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <Attribute AttributeId="urn:oasis:names:tc:xacml:1.0:subject:subject-id" DataType="http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#OESIdentityAssertion" xsi:type="ns1:AttributeType"> <AttributeValue xsi:type="ns1:AttributeValueType"> <OESIdentityAssertion xmlns="http://security.bea.com/ssmws/ssm-soap-types-1.0.xsd"> SU=John;TS=1288702235781;CT=1</OESIdentityAssertion> </AttributeValue> </Attribute> </Subject> <ns2:Resource xsi:type="ns2:ResourceType" xmlns:ns2="urn:oasis:names:tc:xacml:2.0:context:schema:os" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <ns2:Attribute AttributeId="urn:oasis:names:tc:xacml:2.0:resource:resource-id" DataType="http://www.w3.org/2001/XMLSchema#string" xsi:type="ns2:AttributeType"> <ns2:AttributeValue xsi:type="ns2:AttributeValueType"> Library/LibraryResourceType/Book</ns2:AttributeValue> </ns2:Attribute> </ns2:Resource> <ns3:Action xsi:type="ns3:ActionType" xmlns:ns3="urn:oasis:names:tc:xacml:2.0:context:schema:os" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <ns3:Attribute AttributeId="urn:oasis:names:tc:xacml:1.0:action:action-id" DataType="http://www.w3.org/2001/XMLSchema#string" xsi:type="ns3:AttributeType"> <ns3:AttributeValue xsi:type="ns3:AttributeValueType">borrow</ns3:AttributeValue> </ns3:Attribute> </ns3:Action> <ns4:Environment xsi:type="ns4:EnvironmentType" xmlns:ns4="urn:oasis:names:tc:xacml:2.0:context:schema:os" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <ns4:Attribute AttributeId= "http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#RegisteredAttribute" DataType="http://www.w3.org/2001/XMLSchema#string" xsi:type="ns4:AttributeType"> <ns4:AttributeValue xsi:type="ns4:AttributeValueType">yes</ns4:AttributeValue> </ns4:Attribute> <ns4:Attribute AttributeId= "http://security.bea.com/ssmws/ssm-ws-1.0.wsdl #NumberOfBorrowedBooksAttribute" DataType="http://www.w3.org/2001/XMLSchema#string" xsi:type="ns4:AttributeType"> <ns4:AttributeValue xsi:type="ns4:AttributeValueType">2</ns4:AttributeValue> </ns4:Attribute> </ns4:Environment> </Request> -
The XACML gateway asserts the token and converts it to the applicable identity.
-
Oracle Entitlements Server reaches an authorization decision regarding the principal using any applicable policies and returns a XACML response to the PEP.
Example 6-29 is a sample XACML 2.0 authorization response. The
SSM-SOAPWS_xacml.wsdlfile provides the operation interface definitions.Example 6-29 XACML 2.0 Authorization Response
<Response xmlns="urn:oasis:names:tc:xacml:2.0:context:schema:os"> <Result ResourceId="Library/LibraryResourceType/Book"> <Decision>Permit</Decision> <Status> <StatusCode Value="urn:oasis:names:tc:xacml:1.0:status:ok"/> </Status> <ns1:Obligations xmlns:ns1="urn:oasis:names:tc:xacml:2.0:policy:schema:os"> <ns1:Obligation ObligationId= "http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#Roles" FulfillOn="Permit"> <ns1:AttributeAssignment DataType="http://www.w3.org/2001/XMLSchema#string" AttributeId="http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#role"> AuthenticatedUser</ns1:AttributeAssignment> </ns1:Obligation> <ns1:Obligation ObligationId="http://security.bea.com/ssmws/ssm-ws-1.0.wsdl# ResponseAttributes" FulfillOn="Permit"> <ns1:AttributeAssignment DataType="http://www.w3.org/2001/XMLSchema#dateTime" AttributeId="http://security.bea.com/ssmws/ssm-ws-1.0.wsdl#decisionTime"> 2010-11-02T12:50:43.685Z</ns1:AttributeAssignment> </ns1:Obligation> </ns1:Obligations> </Result> </Response>