| Oracle® Fusion Applications Extensibility Guide 11g Release 1 (11.1.4) Part Number E16691-06 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Applications Extensibility Guide 11g Release 1 (11.1.4) Part Number E16691-06 |
|
|
PDF · Mobi · ePub |
This chapter describes how to use CRM Application Composer to define and edit role-based security policies on custom business objects at runtime in certain Oracle Fusion Customer Relationship Management applications, limited to the Sales, Marketing, Customer Center, Trading Community Architecture, or Order Capture applications.
This chapter includes the following sections:
Section 9.2, "Defining Security Policies for Custom Business Objects"
Section 9.3, "Enabling End User Instance-Level Security Customization"
Section 9.4, "Preventing Corrupted Security Policies in CRM Application Composer"
Security for Oracle Fusion Applications is configured to protect the data and business functions of the enterprise from unintended access. By default, new business objects and the web pages that display them are inaccessible to any user other than the user of CRM Application Composer. This means that when you create a security policy in CRM Application Composer, you specifically grant access to resources that would otherwise be protected. Additionally, security policies defined in CRM Application Composer are enforced on all the data records of the business object. Controlling access to individual data records is not supported for custom objects.
To enable access to the data records, you can use CRM Application Composer to create security policies for new business objects that they add to the following CRM applications:
Sales (Partner Center)
Marketing
Customer Center
Trading Community Architecture
Order Capture
Note:
For information about how to define security policies for custom business objects in other Oracle Fusion applications, see Chapter 15, "Customizing Security for ADF Application Artifacts."
In Oracle Fusion Applications, the business object defines the available operations that may be performed over a particular set of data. The business object also encapsulates the data as business object instances, corresponding to data records from a database table. Typical operations are business functions like viewing, editing, or creating an instance of the business object. A security policy essentially needs to specify "who can perform what operations on what specific data."
Security policies in Oracle Fusion Applications provide role-based access control to the data records encapsulated by the business object, as well as the application artifacts, like web pages that interact with those data records. Role-based security ensures that the person creating the security policy does not require information about the individuals comprised by the enterprise at any given time. Rather, a security policy is always associated with a predefined role that end users are anticipated to fill when interacting with Oracle Fusion Applications.
For example, in a sales organization, duties such as Manage_Accounts and Manage_Invoices exist for roles, such as Sales_Manager or Sales_Associate. A security policy might give end users who belong to the Sales_Associate role the ability to view and edit the data records exposed by a particular business object, such as a customer invoice, but not to delete the records. Whereas, another security policy could grant end users who belong to the Sales_Manager role, the right to view, edit, and delete the same data records.
A security administrator for the enterprise completes the security configuration task by provisioning end users of the enterprise with one or more roles, based on the variety of duties the end user is expected to perform. The security policies defined for that role, in turn, confer to its member end users specific access right, or privileges.
Note:
Security-related configuration tasks such as configuring the enterprise identity store, configuring roles, and provisioning end user identities are not supported in CRM Application Composer. For details about security configuration, see the "Securing Oracle Fusions Applications" chapter in the Oracle Fusion Applications Administrator's Guide.
In summary, a security policy for Oracle Fusion Applications considers the duties end users perform and then grants a role specific rights to:
Access the page that supports the duty
Access the specific data records, or instances of the business object, required to complete the duty
Perform only those operations on that data required by the duty.
Although CRM Application Composer does not implement the security policy directly on the business object, the user interface focuses on business objects as a convenient way to represent and manage the actual security policies of the enterprise. Specifically, CRM Application Composer security policy screens simplify the task of choosing a business object and then creating a complete security policy to grant the level of access needed by any role in Oracle Fusion Applications.
A complete security policy is one that controls access to the selected business object's operations, its instances, as well as the web pages that display the actual data records exposed by the business object. In the background, when you create a security policy for a custom business object and a role, CRM Application Composer interacts with the Oracle Fusion Applications security repositories to create or update the specific security artifacts that define the policy.
Specifically, the artifacts created in the Oracle Fusion security repositories by CRM Application Composer correspond to Oracle Fusion Data Security policies and Oracle Platform Security Service (OPSS) function security policies. A security policy that defines the level of access to the data records of the business object is known as a data security policy. A security policy that defines the level of access to the application resources that display the object is known as a function security policy. To completely specify access, both types of security policies must exist for the role.
While both types of security policies are conceptually similar, the repository for storing the security artifacts, as well as the representation of the artifacts, differ. CRM Application Composer defines the data security policy in Oracle Fusion Data Security database tables and defines the OPSS function security policy as hierarchically organized objects in an LDAP directory service.
For the user of CRM Application Composer, the distinctions of the type of security policy and the specific repository used to store them are not relevant. CRM Application Composer security policy screens do not label policies as data policies and function policies. In CRM Application Composer, the security policy screens hide these distinctions and instead allow you to focus on the business object. The security policy screen lets you view the business objects by name and modify the privileges granted to the various Oracle Fusion Applications roles to access the data records exposed by the business object and to access the web page created to display those records.
To understand the implementation details of data security and function security, you can read about the tools developers use to interact directly with the security repositories, as described in Chapter 15, "Customizing Security for ADF Application Artifacts."
After you create a custom business object and then create the web page to display the data records of the business object in CRM Application Composer, these application artifacts will be secured in Oracle Fusion Applications by default. This means end users will be denied access until you grant them access through a role-based security policy that you define.
To enable access, you can use CRM Application Composer to create role-based security policies for new business objects that are added to the following CRM applications:
Sales (Partner Center)
Marketing
Customer Center
Trading Community Architecture
Order Capture
Note:
For information about how to define security policies for custom business objects in other Oracle Fusion applications, see Chapter 15, "Customizing Security for ADF Application Artifacts."
Figure 9-1 shows the Application Navigator in CRM Application Composer with the Custom Object list expanded to display the Security option for a custom business object. The Security option is displayed in the Application Navigator only for custom business objects. After you select this option, the object-centric security policy screen opens in CRM Application Composer and displays the policies for the expanded business object (as shown in Figure 9-1).
Figure 9-1 Navigator Displays Security Customization Option for Custom Objects in CRM Application Composer
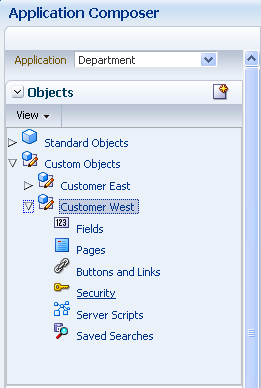
Note:
The term custom object is used in CRM Application Composer to distinguish business objects that you create from standard objects that are part of the Oracle Fusion Applications security reference implementation. Security policies for standard objects are not exposed in CRM Application Composer. For more information about configuring security for the reference implementation, see Section 15.2, "About Extending the Oracle Fusion Security Reference Implementation."
Because security policies provide role-based access, in CRM Application Composer a security policy specifies a role name, a custom business object name, and one or more privileges that specify the level of access granted to the role. As described in Section 9.1.1, "About the Implementation of Security Policies in CRM Application Composer," when you use the security policy screens in CRM Application Composer, you will not need to create the underlying security artifacts; the tool will create those for you in the appropriate Oracle Fusion security repository.The security screens in CRM Application Composer let you grant and revoke access privileges to roles in one of two formats.
Figure 9-2 shows the screen that lets you display a single custom object and view all the roles and the level of access that each one defines for that custom business object. In this example, the object-centric security screen displays the custom business object CustomerWest and shows a default security policy defined on the CRM Application Administrator Duty role (note the default role to use for testing security can be configured for the Sales, Marketing, Customer Center, Trading Community Architecture, and Order Capture applications). CRM Application Composer creates this security policy by default so that you can view and customize the custom object in CRM Application Composer. In this screen, no other policies have been defined.
Figure 9-2 Object-Centric Security Policy Screen: Viewing and Modifying All Security Policies for a Given Custom Business Object
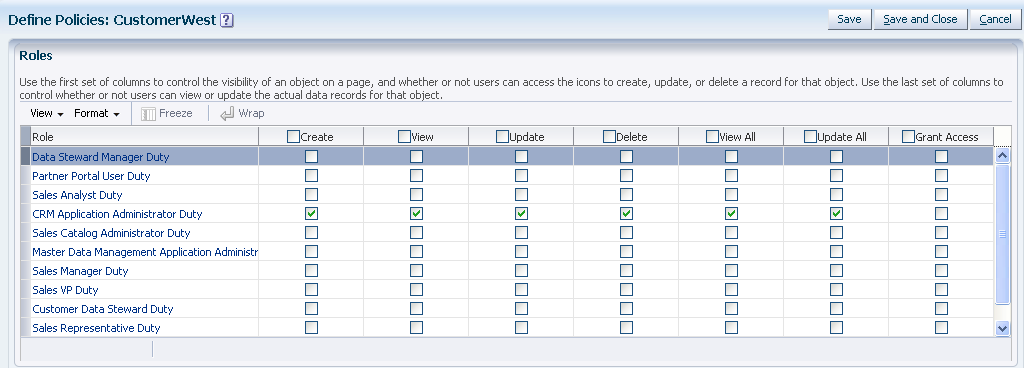
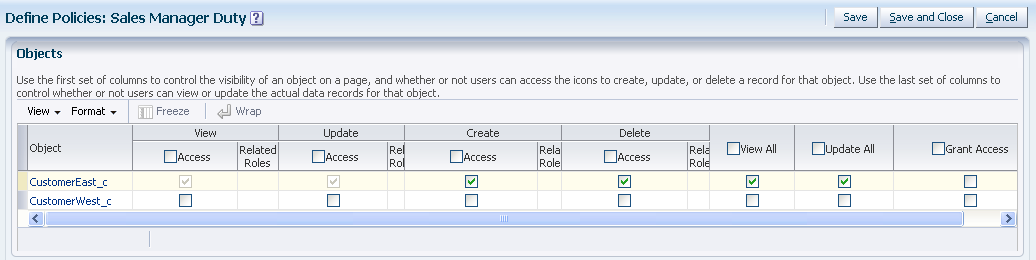
Figure 9-3 shows the alternative screen you can open to display a single role and view the level of access it grants to all the custom objects in the Sales, Marketing, Customer Center, Trading Community Architecture, or Order Capture applications. In this example, the role-centric security screen displays the Sales Manager Duty role with access granted to the CustomerEast business object.
Figure 9-3 Role-Centric Security Policy Screen: Business Viewing and Modifying All Security Policies for a Given Role
The selection choices presented by the columns of both security policies screens (the object-centric screen and the role-centric screen) have the same meaning:
The first four columns View, Update, Create, and Delete correspond to the privileges that confer rights to the web page that you create to display the data records of the custom business object.
The column selections define a function security policy in the LDAP security repository and determine whether the end user may view the web page, and then, assuming the page is displayed, whether the buttons that enable operations to edit a data record, create a new data record, or delete a data record will themselves appear enabled or disabled (grayed out) in the page.
At runtime, in the Oracle Fusion application, the end user may have the right to view the data records displayed by the web page, but unless their role also confers the right for example to edit the page, the user interface displays the page with the Edit button disabled to prevent this operation. Until View, Update, Create, and Delete columns are selected for a role, no function security policy exists in the LDAP security repository and the custom business object's web page remain protected by default, thus preventing all end users provisioned with that role from accessing the page and, consequently, also the data.
The next two columns, ViewAll and UpdateAll, confer rights to view and manipulate the data records of the custom business object in the web page.
The column selections define a data security policy in the Oracle Fusion Data Security security repository and determine whether the end user may view the data records and, assuming the records are displayed in the web page, whether the end user has the rights to edit or delete the data records exposed by the custom business object. When you select UpdateAll, as a side-effect, CRM Application Composer automatically enables the corresponding function security privileges to give the end user the right to select the Edit buttons in the web page. Until ViewAll or UpdateAll columns are selected for a role, no data security policy exists in the repository and the data records remain protected by default, thus preventing all end users provisioned with that role from accessing the data.
The last column, Grant Access, enables a runtime security configuration feature that gives end users the ability to share their security entitlements with another end user.
When you enable "sharing" of entitlements for a specific custom business object, you allow one user to confer their privileges to another end user. The Grant Access option enables the feature at the level of the business object so it will be effective in any page that displays the data records of the custom business object.
Figure 9-4 shows an alternative way to enable the entitlement sharing feature. When you use the page creation screen that you display for the custom business object, the option labeled Allow Access Grant lets you to enable the feature for the custom business object at the level of a single page.
When you use CRM Application Composer, you can optionally elect to do your work in a sandbox, and after you publish your sandbox, all business objects, pages, and the security policies you define become part of the running application. When you are ready to edit security policies, you can initiate the security sandbox setup operation. This setup operation will duplicate the schema for Oracle Fusion Data Security tables and is necessarily a lengthy one that must be allowed to complete before customization can begin. After you complete the customizations, published security policies will be merged into the Oracle Fusion security policy repository as part of the native application and they will overwrite any previous customizations.
Note:
Because inconsistencies can result when multiple users edit the security policies associated with the same object in different sandboxes, users may coordinate so they avoid customizing the same object concurrently. For more information about runtime customization and the sandbox, see Section 2.2, "Using the Sandbox Manager."
In summary, using CRM Application Composer, you can perform these tasks to define security policies for a custom business object:
Grant and revoke access privileges made to specific roles (such as Sales Manager or Sale Representative). For details about this task, see Section 9.2, "Defining Security Policies for Custom Business Objects."
Enable end users to elevate the privileges of other end users by conferring their own rights to view, edit, or delete individual data records. For details about this task, see Section 9.3, "Enabling End User Instance-Level Security Customization."
CRM Application Composer does not expose the underlying implementation details of the actual security policies created in the Oracle Fusion security repositories. Other tools in the Oracle Fusion Applications environment provide the enterprise security administrator and other appropriately authorized end users with complete control over the creation and viewing of those security artifacts.
Because CRM Application Composer provides an abstracted view of the security policy implementation, it also limits your ability to edit security policies. For example, a developer may need to control access to specific records of the custom business object that they implement, and they may use other tools to interact directly with the security repository to make this type of customization. Whereas, in CRM Application Composer, when you grant access privileges to a given role for a custom business object, CRM Application Composer creates a global instance set that specifies all data records of the business object. Therefore, no capability exists currently in CRM Application Composer to stripe individual data records with specific access privileges.
While you can create role-based security policies using CRM Application Composer, the following are more advanced use cases for which you will need to use development and administration tools:
Create custom roles or modify the role inheritance hierarchy provisioned by Oracle Fusion Applications. In those cases where you will need to use a custom role, consult a system administrator. Only a system administrator may create a new role, and optionally include the role in an existing role hierarchy. For information about creating application roles, see the "Managing Policies and Policy Objects" chapter in the Oracle Fusion Middleware Oracle Authorization Policy Manager Administrator's Guide (Oracle Fusion Applications Edition).
Define or edit a security policy contained in an application that is not Sales, Marketing, Customer Center, Trading Community Architecture, or Order Capture. In those cases, you will need to use other tools instead of CRM Application Composer to define your security policies. For more information, see Chapter 15, "Customizing Security for ADF Application Artifacts."
Define or edit a data security policy for the standard business objects defined by any Oracle Fusion application. CRM Application Composer supports defining security for custom business objects only. Only an authorized an security administrator can manage the Oracle Fusion security reference implementation where they use other tools to edit policies for standard objects. For more information, see Section 15.2, "About Extending the Oracle Fusion Security Reference Implementation."
Define data security policies on individual business object instances or groups of instances. Security policies that you define in CRM Application Composer are enforced on the all the data records of the business object (referred to as a global instance set). Controlling access to individual data records is not supported on custom objects. Only customization developers and an security administrators can manage data security policies. For more information, see Section 15.3.4, "Scenarios Related to Extending and Securing Data Model Components."
Enforce column-level security. Security policies that you define in CRM Application Composer are enforced on the data records (or rows) of the business object. Controlling access to columns of data requires using Oracle JDeveloper to create a customization workspace for the application. For more information, see Section 15.3.4, "Scenarios Related to Extending and Securing Data Model Components."
Define function security policies on individual application artifacts. Security policies that you define in CRM Application Composer will automatically be enforced on the application resources that reference the custom business object based on the View, Edit, Update, and Create privileges you select. Enforcing security on specific application resources, such as a customized task flow and its web pages or components in a web page, requires using JDeveloper to create a customization workspace for the application. For more information, see Section 15.3.5, "Scenarios Related to Extending and Securing User Interface Artifacts."
Before you begin customizing security in CRM Application Composer, you should be familiar with the Oracle Fusion application architecture that enables customization, as described in Chapter 1, "Customizing and Extending Oracle Fusion Applications." You should also understand the typical workflows for working with customizations, as described in Chapter 2, "Understanding the Customization Development Lifecycle."
You will need to do the following before you can begin customizing security:
Obtain the privileges needed to define security policies in CRM Application Composer.
If you will be defining or editing security policies in Oracle Fusion Applications, you will need the correct privileges. When you have the correct privileges, CRM Application Composer will give you access to the security customization user interface. Please contact your security administrator for details.
Optionally set up a sandbox.
CRM Application Composer can use sandboxes to manage your customizations. For more information, see Section 2.2, "Using the Sandbox Manager."
Note: Because setting up the security sandbox requires duplicating the schema for Oracle Fusion Data Security tables, this will always be a lengthy operation in CRM Application Composer. Be sure to allow sufficient time for the process to complete and do not to terminate it early. You may want to defer customizing security and enabling the security sandbox until you are sure that you need to make customizations.
Create the business object, as needed.
Unless the business object appears in the Application Navigator of CRM Application Composer, you will not be able to define security policies using CRM Application Composer. You can create custom business objects for Sales, Marketing, Customer Center, Trading Community Architecture, or Order Capture applications in CRM Application Composer. For more information about creating business objects for these applications, see Task: Create Custom Objects in Section 4.4, "Creating Custom Objects." Business objects for all other applications must be created by a developer, administrator, or security manager, as described in Chapter 15, "Customizing Security for ADF Application Artifacts."
Consult the system administrator to create custom roles, as needed.
The access privileges specified by security policies you define for the custom business object are granted to application roles. Oracle Fusion Applications defines a large number of application roles based on the duties of its member end users. When an application role does not exist that adequately describe the duties pertaining to the custom business object, then a custom application role will need to be created. In those cases where you will need to use a custom role, consult a system administrator. Only a system administrator may create a new role, and optionally include the role in an existing role hierarchy.
Until you define a security policy for a custom business object, the data records exposed by that business object will be protected and end users will not have access to the data. When you want to make the custom business object accessible, you define a security policy using CRM Application Composer.
The security policy that you define in CRM Application Composer consists of the following access privileges that you select to control access to the custom business object by end users provisioned to particular roles:
Grant View, Update, Create, and Delete privileges on the web page that displays the data records. Minimally, you must grant the View privilege to allow the end user to open the web page. You can also grant Update, Create, and Delete privileges to enable the buttons in the web page that the end user clicks to initiate these operations on the data records.
Note: If an Update, Create, and Delete privilege is not granted, the corresponding button will appear grayed out (disabled) in the web page.
Grant ViewAll and UpdateAll privileges on the data records themselves. Minimally, you must grant the ViewAll privilege to populate the web page with the data records for the end user. You can also grant the UpdateAll privilege to enable the end user to modify the data contained in any data record exposed by the custom business object.
Note: When you grant the UpdateAll privilege, CRM Application Composer automatically grants the privileges for the edit operation button. You can enable or disable individual buttons (including edit, new, and delete) in the web page and thereby deny end users access to individual operations on the data record by selecting or deselecting the corresponding Update, Create, and Delete privilege.
Before you begin:
Create the business object. You can only define security policies on custom business objects that you create in CRM Application Composer. The custom business object must exist before you define the security policy. For more information, see Task: Create Custom Objects in Section 4.4, "Creating Custom Objects."
Task: Grant View and Update Access to Multiple Roles Using the Object-Centric User Interface
The data records exposed by a custom business object can be accessed by members of more than one application role. You can grant access privileges to the view, update, create, or delete operations for a particular custom business object for each application role. In the navigator for CRM Application Composer, you select the custom business object and then you click Security. In the Define Policies screen, you grant access privileges to any of the displayed application roles for the previously selected custom business object as follows:
When you want to grant view-only access, you select only the View and ViewAll privileges.
When you want to grant view and update access, you select the ViewAll and UpdateAll privileges.
After you select the UpdateAll privilege, the security policy screen automatically displays the Update privilege as selected.
When you want to allow or deny access to individual operations to edit, create, or delete data records, you can select or deselect the corresponding Update, Create, and Delete privilege and leave the UpdateAll privilege selected.
For more information, see the "Securing Custom Objects: Explained" topic in the Oracle Fusion Applications CRM Extensibility Guide.
Task: Grant View and Update Access to a Specific Role Using the Role-Centric User Interface
Members of an application role may have access to multiple custom business objects. You can grant access privileges to view, update, create, or delete operations for each of the custom business objects for a particular application role. In CRM Application Composer, you select Security Roles from the Common Setup panel. In the Security Roles screen, you select a role and then you click the Define Policies button. In the Security Policies screen, you grant access privileges to any of the displayed custom business objects for the previously selected role as follows:
When you want to grant view-only access, you select only the View and ViewAll privileges.
When you want to grant view and update access, you select the ViewAll and UpdateAll privileges.
After you select the UpdateAll privilege, the security policy screen automatically displays the Edit privilege as selected.
When you want to allow or deny access to individual operations to edit, create, or delete data records, you can select or deselect the corresponding Update, Create, and Delete privilege and leave the UpdateAll privilege selected.
For more information, see the "Securing Custom Objects: Explained" topic in the Oracle Fusion Applications CRM Extensibility Guide.
In certain situations one end user may require temporary access to the data records of another end user. In this scenario, Oracle Fusion Applications supports a runtime security customization feature that lets end users elevate the privileges of another end user by conferring their own rights to view, edit, or delete individual data records. Because each data record corresponds to a business object instance, this type of runtime customization is known as instance-level security.
In CRM Application Composer, this end user security configuration feature is enabled on the custom business object during page customization. At runtime, the page that displays the data records of the enabled custom business object will display a Manage Permissions button that opens a dialog that displays the list of end users to whom additional privileges may be granted. The privileges the dialog displays will be limited to the privileges available to the conferring end user, as defined in CRM Application Composer for the user's provisioned roles and the currently the displayed custom business object.
Additionally, to complete the configuration of this runtime security customization feature in CRM Application Composer, you must grant sufficient privileges to the roles which may be conferred a higher level of access by another end user in order to enable the Edit and Delete buttons in the user interface so that the user with elevated privileges can invoke edit or delete operations on the data record.
Before you begin:
Create the appropriate security policy on the custom business object for the conferring end user. The end user can only confer the access privileges to a data record that they already possess. This requirement means that the conferring end user's role must have the ViewAll or UpdateAll privileges granted in CRM Application Composer to be able to confer the right to view, edit, and delete a particular data record.
Create the appropriate security policy on the custom business object to be accessed by the target end user. At runtime, in Oracle Fusion application, the end user to whom the rights are granted must also have the privileges needed to select the buttons the web page displays to invoke the create, edit, or delete operations on the data records of the custom business object. This requirement means at least one role of the target end user must have the View, Update, and Delete privileges granted for the specific custom business object in CRM Application Composer. Otherwise, without these privileges, the Oracle Fusion application will display the web page with the Edit and Delete buttons grayed out (disabled) for the business object.
Task: Enabling End Users to Elevate the Access Privileges of Other End Users for a Business Object in a Specific Page
The data records of a custom business object represent instances of the object. You can enable a runtime security configuration feature that allows one end user to elevate the rights of another end user to access individual business object instances displayed in a specific page. Instance-level security lets one end user confer their own access privileges to other end users of the Oracle Fusion application in the enterprise. In the navigator for CRM Application Composer, to enable this runtime security configuration feature, you select the custom business object and then you click Page. In either of the Pages panels, you click through the page creation workflow until you reach the Configure Landing and Creation Pages task, and you then select Allow Access Grant. For more information, see the "Securing Custom Objects: Explained" topic in the Oracle Fusion Applications CRM Extensibility Guide.
Task: Enabling End Users to Elevate the Access Privileges of Other End Users for a Business Object on Any Page
The data records of a custom business object represent instances of the object. You can enable a runtime security configuration feature that allows one end user to elevate the rights of another end user to access individual business object instances when they appear in any page. Instance-level security lets one end user confer their own access privileges to other end users of the Oracle Fusion application in the enterprise. In the navigator for CRM Application Composer, to enable this runtime security configuration feature, you select the custom business object and then you click Security. In the object-centric Define Policies screen, you select Grant Access for the desired application role. Alternatively, you can use the role-centric Define Policies screen to enable the same runtime security configuration feature. For more information, see the "Securing Custom Objects: Explained" topic in the Oracle Fusion Applications CRM Extensibility Guide.
CRM Application Composer creates a variety of security artifacts, which together provide security for the CRM application. After you define or edit a security policy in CRM Application Composer, authorized developers or security managers may be able to access the security repository and view the security policy. However, in the current release of Oracle Fusion Applications, even browsing the security policies for custom objects in tools such as Oracle Authorization Policy Manager or Oracle Fusion Functional Setup Manager may corrupt the security artifacts created in CRM Application Composer.
Important:
Security managers must not use Oracle Authorization Policy Manager or Oracle Fusion Functional Setup Manager to browse or edit the security policies that you create in CRM Application Composer. Security policies created for custom objects, must therefore only be edited within CRM Application Composer.