11g Release 1 (11.1.4)
Part Number E20379-04
Contents
Previous
Next
|
Oracle® Fusion
Applications Workforce Deployment Implementation Guide 11g Release 1 (11.1.4) Part Number E20379-04 |
Contents |
Previous |
Next |
This chapter contains the following:
Creating Payroll Security Profiles: Examples
Payroll Flow Security and Flow Owners: Explained
Creating Payroll Flow Security Profiles: Examples
These examples illustrate different methods by which access to payrolls can be assigned to members of the Payroll department. Payroll definitions are first organized into appropriate payroll security profiles through the Manage Payroll Security Profiles task. The security profile is then included in an HCM data role or assigned directly to a job role, and that role is provisioned to a user.
This example illustrates the most common scenario, where payrolls are organized by their period type. Monthly payrolls are sorted into the same security profile; semiweekly into another; and so on. The security profile is then included in an HCM data role or assigned directly to a job role, and that role is provisioned to the payroll administrators.
This example illustrates the scenario where payrolls are organized by the regions of the target employees' work areas. For example, payrolls run against North American facilities are added to one security profile, while European facilities are added to another.
This example illustrates an ad hoc implementation where payrolls are organized according to the work responsibilities of the owning Payroll Manager. For example, payroll access may be restricted only to those administrators who created and manage their definitions.
Your HCM data role security determines which payroll flows you can submit or view on the Payroll Dashboard or payroll work areas, including flows delivered for a single report or process. When you submit a payroll flow, you become the payroll flow checklist owner.
The payroll checklist owner inherits any task within the flow, unless the payroll flow pattern specifies a different owner for a task.
A checklist or task owner can reassign a task to someone else. For example, as a checklist owner, if a task is overdue and the task owner is on leave, you might reassign the task to another team member.
HCM data roles secure the access to payroll flows through data privileges and to the payroll tasks on a payroll checklist through functional privileges.
If you cannot:
Submit or view a payroll flow, confirm that the data role assigned to you includes a security profile for the payroll flow pattern.
Perform a task such as a process or report, confirm that your data role is based on a job or abstract role whose inherited duty roles include necessary functional privilege to perform that task.
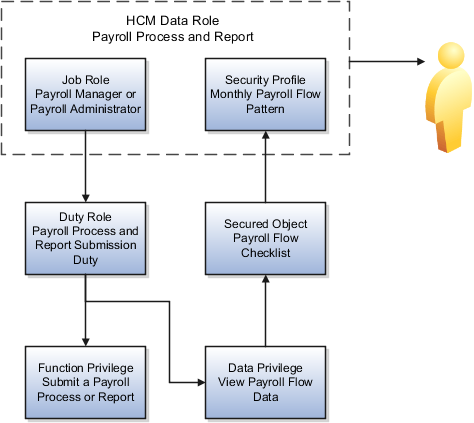
In the following figure, both the payroll administrator and the payroll manager are assigned duty roles with the functional privilege to submit a process or report and the data privilege to view the data for the monthly payroll flow pattern. Both the manager and administrator can perform the same task or have that task reassigned to them.
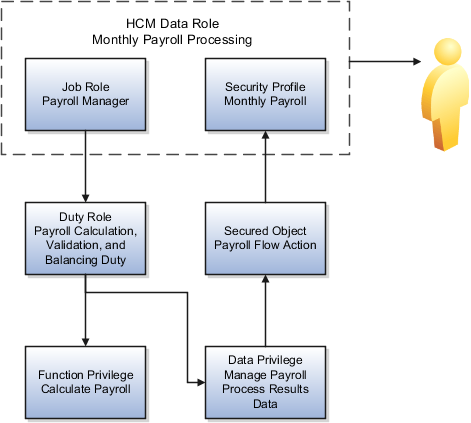
In the following figure, only the payroll manager not the payroll administrator job role inherits the functional privilege to calculate payroll. The payroll manager should not reassign a flow task to a payroll administrator, because the administrator does not have the necessary functional privilege.
The following examples illustrate different methods by which payroll flows can be organized into appropriate security profiles. Access to those profiles is granted to workers through the Assign Security Profiles to Role page. Users must also be granted access to the appropriate tasks within the flow.
Payroll administrators responsible for payroll processing would be granted permission to submit the Payroll Cycle and QuickPay flows. Therefore, their payroll flow security profiles must include the appropriate flows.
Administrators responsible for End of Year reporting would be granted permission to submit the End of Year and Archive End-of-Year Payroll Results flows. Therefore, their payroll flow security profiles must include the appropriate flows.
Administrators responsible for hiring and terminations should be granted permission to flows such as New Hire flow and Termination flow.