Similar to Oracle Fusion OLTP Function Security, somewhat beyond the scope of Oracle BI, Transactional Business Intelligence function security also secures access to Transactional Business Intelligence reporting objects by assigning BI-specific duty roles to BI-specific job roles.
The basic convention that defines these mappings is as follows: For a given subject area a single BI duty role is defined, using the naming convention “<xyz>Analysis Duty”. The association of BI duty roles to subject areas is always one-to-one. If the same job role is already defined for Oracle Fusion applications, that job role is mapped to the BI-specific duty role.
Transactional Business Intelligence function security is defined according to each of the following tables. All mapped job roles are shown in the flattened columns to the right of each table.
Note: | For guidance on how to extend security in Oracle BI Applications, see Oracle® Fusion Middleware Reference Guide for Oracle Business Intelligence Applications. |
Figure 77. Transactional Business Intelligence Supply Chain Management Pre-configured Function Security Mappings
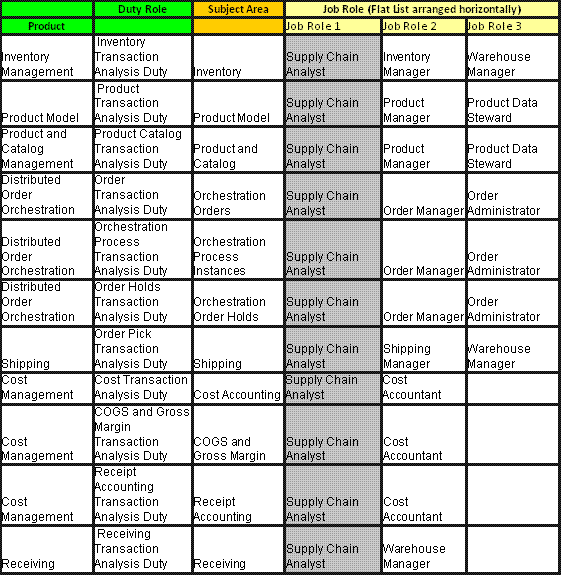
Figure 78. Transactional Business Intelligence Projects Pre-configured Function Security Mapping (Job Roles 1-4)
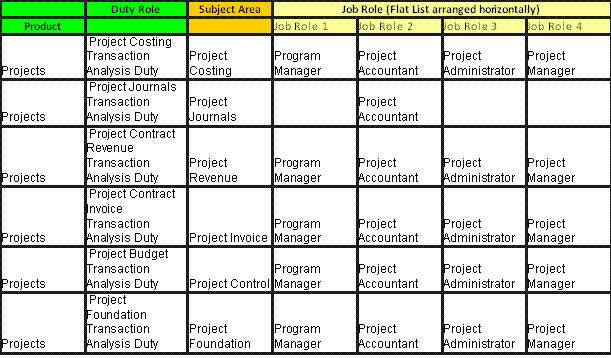
Figure 79. Transactional Business Intelligence Projects Pre-configured Function Security Mapping (Job Roles 5-9)
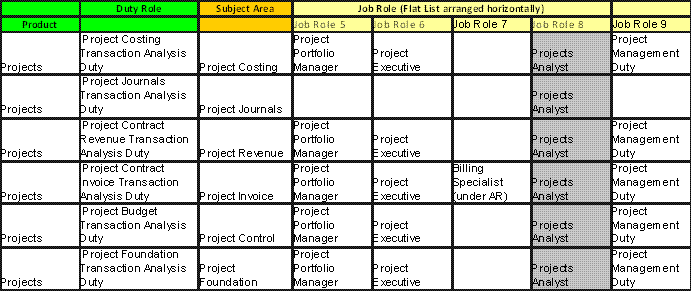
Figure 80. Transactional Business Intelligence Human Capital Management Pre-configured Function Security Mapping
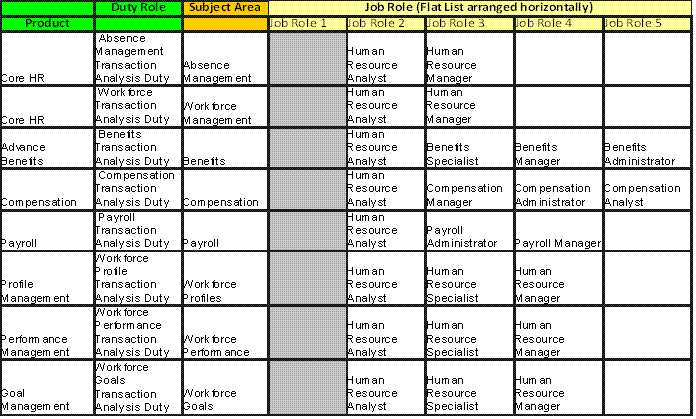
Figure 81. Transactional Business Intelligence Incentive Compensation Pre-configured Function Security Mapping
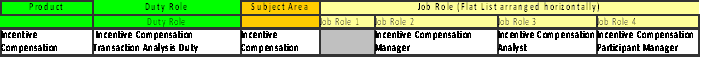
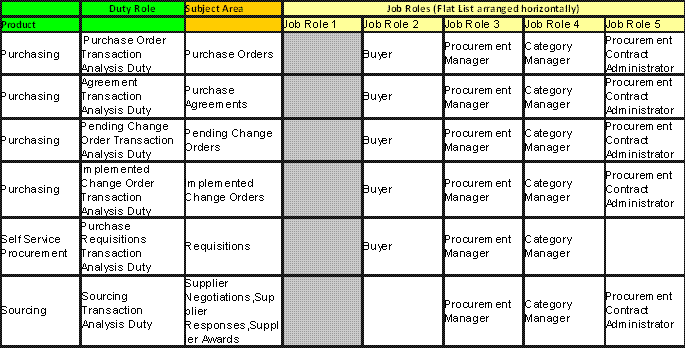
Figure 82. Transactional Business Intelligence Payables and Receivables Pre-configured Function Security Mapping (Job Roles 1-4)
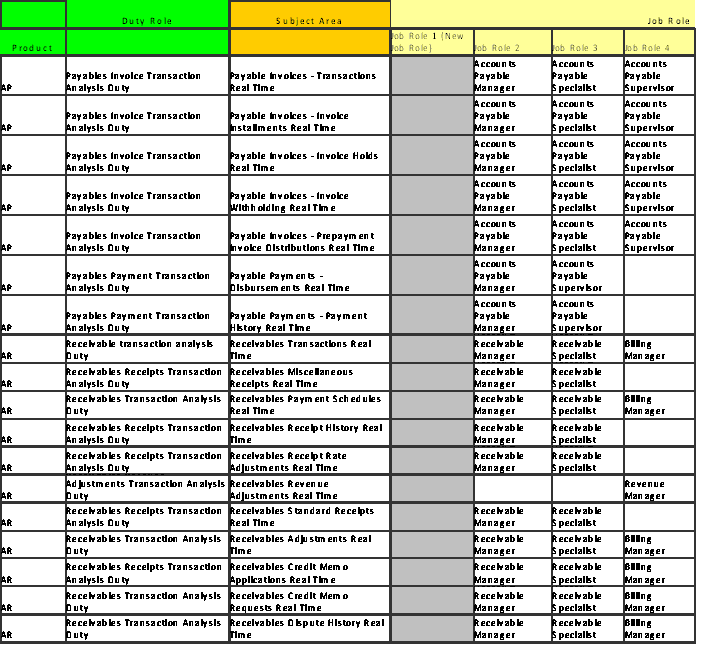
Figure 83. Transactional Business Intelligence Payables and Receivables Pre-configured Function Security Mapping (Job Roles 5-7)
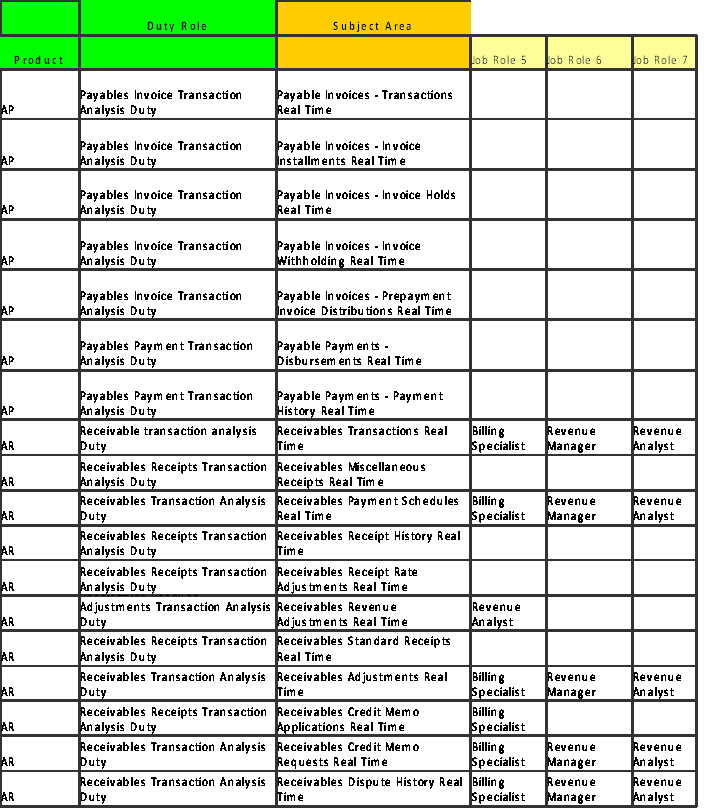
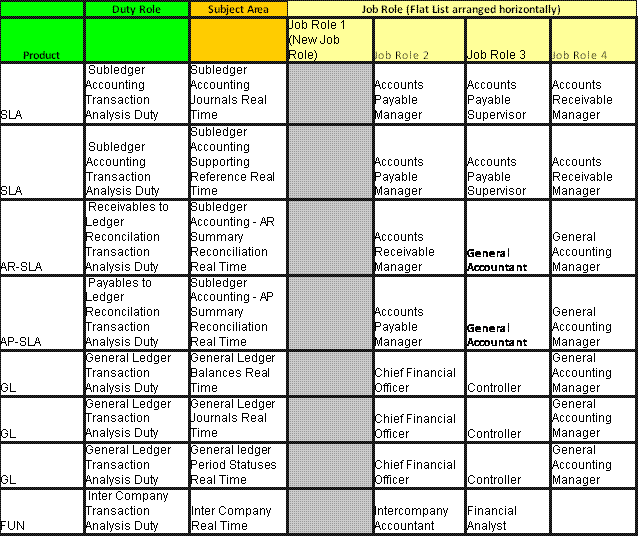
Figure 85. Subledger Accounting, Receivables, Payables, General Ledger, Financials Common Module Pre-configured Function Security Mapping (Job Roles 1-4)