6 Viewing Additional Details for Investigation
OAAM provides the capability to gather detailed information about the session parameters and to allow you to drill down further into the details involved in the session. The session parameters are users, devices, locations, alerts, and fingerprints.
6.1 Details Pages Overview
The investigators are assigned to perform fraud investigation and leverages all available data, knowledge, and expertise to determine if in fact there is fraudulent activity present.
The details pages provide additional details of session parameters such as user, device, location, alerts, and fingerprints and shows their relationships so that you can cross references on data points and drill in on related data.
The following are examples of related data:
-
Administration groups to which the session parameters belong
-
Sessions in which the parameter was used
-
Success and failure login attempts for the parameters
-
Policies and rules executed during those sessions
-
Alerts generated for the session
-
Fingerprint information
Example of relationships between parameters:
You can identify what devices a single user used, which particular location was the device used, which login attempts were successful, and how many users logged in from a particular location.
6.2 Details Page Structure
Each details page provides the following items:
-
Summary of basic information such as ID, name, creation date, and other information
For an example, refer to Section 6.11.1, "User Details: Summary Tab."
-
Detail tabs for a view of the entity's relationship with other entities
The relationships are shown through the tabs.
For summaries of the tabs for each details pages, refer to:
-
Links to details pages for more information
-
Add to Group feature
6.3 Prerequisites
Prerequisites for viewing details pages are listed in this section.
6.3.1 Multitenant Access
To have access to details pages, ensure the multitenancy flag is disabled. If the user's role is a multitenant enabled role, he may not be able to access the details pages. If multitenancy is enabled, these users cannot access any of the details pages from the sessions page or sessions search. If the multitenancy flag is disabled, these users can access details pages from the sessions page or any sessions search if the link is available. CSRs do not have access to the sessions search or details pages.
6.3.2 View Transactions in Session Details
Before you can view transactions in the Session Details page, you must set the property to show transactions to true.
bharosa.trackeradmin.show.transaction.detail=true
Setting the property to false turns off the display for transactions.
Before using the details pages, check that the following properties are enabled.
oaam.admin.detail.ip.enabled=false oaam.admin.detail.user.enabled=true oaam.admin.detail.device.enabled=false oaam.admin.detail.fingerprint.enabled=false oaam.admin.detail.alert.enabled=false oaam.admin.detail.challengecount.enabled =false
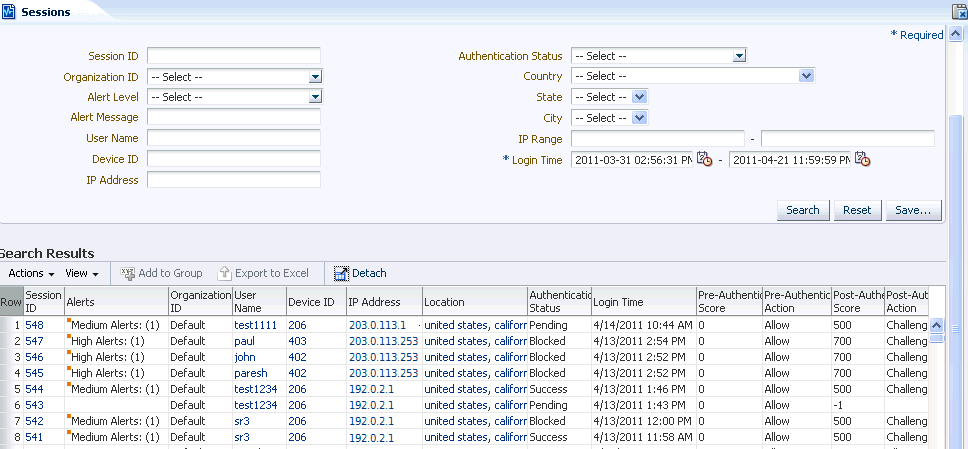
6.4 Searching for Sessions
-
Log in to OAAM Admin as an Investigator.
-
In the Navigation tree, double-click Sessions. The Sessions Search page is displayed.
Alternatively, open the Sessions Search page by:
-
Right-clicking Sessions in the Navigation tree and selecting List Sessions from the context menu.
-
Selecting Sessions in the Navigation tree and then choosing List Sessions from the Actions menu.
-
Clicking the List Sessions button in the Navigation tree toolbar.
-
-
In the Sessions search page, narrow down the number of sessions that are returned by specifying criteria in the search filters.
For example, search through sessions in the last 12 hours with High alerts and a Blocked or Locked authentication status (sessions filtered by Time, Alert Level and Action).
The filters are:
Table 6-1 Session Search Filters
Filters Description Session ID
ID for the session.
Organization ID
Identifies the organization to which the user belongs.
Alert Level
Severity of the alert whether high, medium, low.
Alert Message
Text message configured in the alert.
User Name
Login name given by user to login.
Device ID
Uniquely identifies each device and is autogenerated by the application.
IP Address
Address mapped to a location usually, although some addresses are unknown or private
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Country
Country ID
State
State ID. The State list is dynamically populated with respect to what has been selected for Country. For example, if United States is selected, whatever states are available for that country are shown under States.
City
City ID. The City list is dynamically populated with respect to what has been selected for in Country and State.
IP Range
Range of IP addresses
Login Time
The time the customer logged in to perform the transaction. For example, 5/11/09.
Click the Session ID, User Name, Device ID, IP Address, Location, and Alert Message to open the corresponding details pages to view additional information.
Note:
If the checkpoint is not run, the Pre-Authentication or Post-Authentication displays a score of -1.
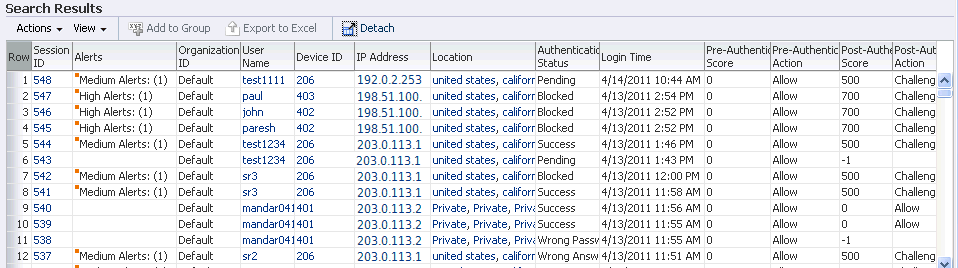
Table 6-2 Search session results
You can launch a details pages from another details page, up to a maximum of 10 tabs. The details page tabs also contain hyperlinked parameters, which can launch the details pages.
Note:
When multitenancy is enabled, investigators do not have access to details pages from anywhere in the OAAM Admin Console.
6.5 Export Sessions to Excel
An export option is available on details pages and tabs for exporting sessions information to Excel. To export sessions information for further investigation:
-
In the details page or tab, search for and select the sessions to export.
-
Click the Export to Excel button.
-
Click Save File or Open with and click OK.
The Excel sheet shows information on the Row, Session ID, Alerts, Organization ID, User name, Device ID, IP Address, Location, Authentication Status, Login Time, Pre-Authentication Score, Pre-Authentication Action, Post-Authentication Score, Post-Authentication Action, Client Type, User ID, and Internal Session ID.
6.6 Add to Group
An Add to Group feature is available in Search sessions, session details, and each details page. While searching results, insights can be saved and used later for rebuilding predictive models, further investigation and rules evaluation. Add a sessions parameter to a group or create a group and add the sessions parameter to it, or remove a sessions parameter from a group, using the Add to Group button from the sessions pages (sessions search results and Session Details page).
One or more data points of various types can be easily selected in search results and added to an appropriate group.
Only Security Administrators, System Administrators, and Investigators have access to the Add to Group command.
Table 6-3 Add and Remove from Group
| Feature | Description |
|---|---|
|
Select a sessions parameter group from a list of parameter groups with which the parameter is not already associated and add the parameter to it. A User Group can be either a User ID or User Name group type. A parameter cannot be added to the same parameter group multiple times with the exception of the alert. An alert can be added to an Alert Group multiple times, since whenever an alert is added to an Alert Group, a new instance of the existing alert is created and added to the group. |
|
|
Create a new sessions parameter group and add parameter to the newly created group. |
Add a new parameter group and add the parameter to it. A user group can be of either User ID or User Name group type. |
|
Remove parameter from parameter group |
Select multiple parameter groups with which the parameter is already associated and remove the parameter from the selected groups. Note: Removing users from Organization ID is not recommended. |
Instructions for adding sessions parameters is provided in the following sections.
6.6.1 Add to Group From Sessions
To add a sessions parameter from sessions to an existing group
-
Select sessions of interest from the search results.
-
Click the Add to Group button.
The Add to Group dialog is displayed.
-
Choose the type of data to add to a group and click Next. Choose only one data type at a time.
-
Device
-
User name
-
IP Address
-
Country
-
State
-
City
-
-
Search and select existing groups for adding the device to and click Next.
-
Items to be added to the group are listed below. To go back and change the items, click the Back button. To proceed with adding these items, click the Finish button.
To add a sessions parameter to a group that is being creating:
-
Click Create New group to create a new group to add the device to.
-
On Add to Group dialog, enter:
-
Group Name
-
Cache Policy
-
Description
-
-
Click Next.
-
Items to be added to the group are listed. To go back and change the items, click the Back button. To proceed with adding the items, click the Finish button.
6.6.2 Add to Group from Details Pages
To add a sessions parameter to a group:
-
Select a row containing one or more session parameters (user, Device ID, IP, and so on).
-
Click the Add to Group button in the upper right corner.
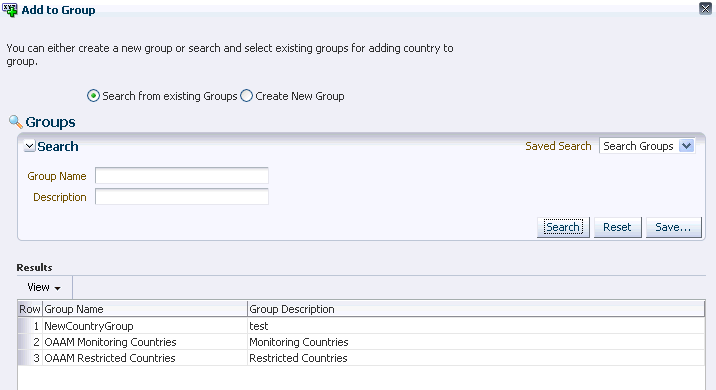
The Add to Group dialog appears with the following search filters:
Table 6-4 Add to Group Dialog Filters
Filter Description Group Name
The name of the group. Groups for which the sessions parameter is not a member of are listed.
Group Type
The type of group. Groups for which the sessions parameter is not a member of are listed.
Description
The description of the group. Groups for which the session parameter is not a member of are listed.
-
Select the group or create a new group.
Figure 6-2 shows the dialog for adding a sessions parameter to an existing group.
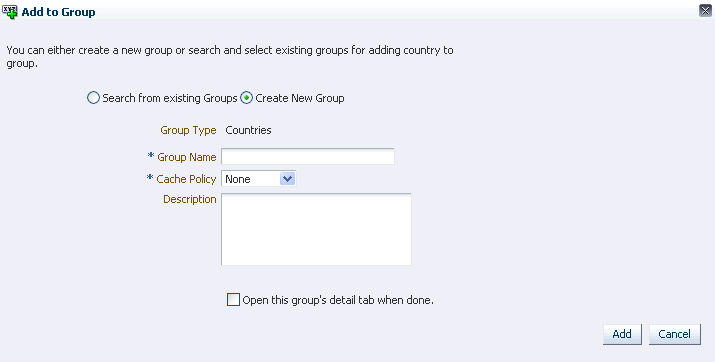
Figure 6-3 shows the dialog for creating a group to add a sessions parameter to.
Enter the following information to create a group:
Field Description Group Name
The name of the group.
Cache Policy
Groups offer two Cache Policy options: Full Cache or None.
By default, the Cache Policy should be set to "all."
For information, refer to Cache Policy.
Group Type
The type of group.
Description
Information about the group.
When adding a group to an existing group, data from selected rows of the type the group can accept are added to the group. If any data is already in the group, an informational message is displayed. When creating a group to add the entity to, do not leave any fields blank; otherwise, an error occurs.
-
Select Open this group's detail tab when done.
-
Click Add.
A confirmation dialog appears.
-
Click OK to dismiss the confirmation dialog.
6.7 Session Details Page
The Session Details page consolidates information needed for fraud analysis.
To go to the Session Details page:
-
In the Search Results table, click the Session ID of the session of interest. The Session Details page for that session is displayed.
General details and all of the actions performed during the session are captured in the Session Details page.
-
View the details of the session.
6.8 Looking at Events from a Higher Level with Session Details
A Session Details page displays an overview of the events that transpired during a particular session for fraud analysis. It contains:
-
General session data points such as user, device, location, and other details
-
A forensic record of the session, including transactions and checkpoints that were evaluated. Each checkpoint displays the policies in that checkpoint, alerts that were triggered during the session for that checkpoint, and the final action for that checkpoint.
The policy explorer view is also available to provide additional details about policies, rules, and conditions.
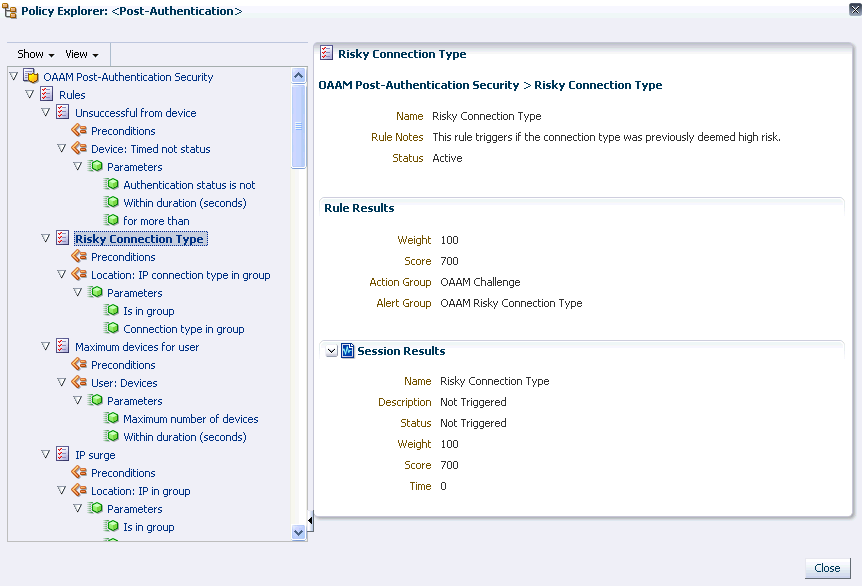
6.8.1 Policy Explorer
The Policy Explorer displays information about rules, conditions, trigger combinations, group linking, nested policies, and other items.
Details about the rule is shown in the Policy Explorer. The session results display the scores and results of that rule.
Pre-conditions for that rule is displayed in the details panel. The session results show the confidence factors and other values for the pre-conditions for that session.
The values for the condition parameters are displayed. The session results show if the conditions returned true for this session evaluation.
There is an option to view the triggered override combinations or view all overrides. Session results show the override information that was evaluated for this session including the nested policy information.
Group linking for the policy is displayed in the details panel.
6.8.2 Runtime Information
The Session Details page contains several panels. The main panels like checkpoints and transactions have multiple subpanels. Panel are not displayed if information is not available. Except for the Session Details panel, all other panels are displayed in the order of execution. (Looking at the Session Details page, you can see the flow of events, the sequence when the events happened within the session.)
6.8.2.1 Session Details
The Session Details panel shows all the related information regarding the login transaction. It shows the authentication status, IP address from which the user logged in, user name, User ID, cookie information, autolearning processing status, and the login time.
6.8.2.2 Policies
A list of policies in that checkpoint are displayed in the Policies panel. You can view the rules and action that triggered.
Table 6-6 Policies in a Checkpoint
| Item | Description |
|---|---|
|
Name |
The name of the policies that are under the checkpoint, rules under the policies, the conditions under the rules, and the action triggered. |
|
Status |
Executed (for policies) and Triggered (for rules). |
|
Scoring Engine |
A scoring engine is provided at the policy level and at the checkpoint level. The policy scoring engine is applied to rule scores to determine the risk for each policy. |
|
Time |
The time of the occurrence. |
|
Weight |
Percentage value used to influence the total score. |
|
Score |
Level of risk that has been calculated for specific situations or parts of a situation, expressed as a number. There are multiple policies under one checkpoint. The scores of these policies are used to determine a score for the checkpoint. |
As an investigator, you are interested in why a particular rule triggered. For example, you might look at which policy and rules triggered the alert.
Information can be gathered by looking at these details. For example, a user who successfully went through Pre-Authentication and Post-Authentication checkpoints knew the password and the questions and answers and there fore, there is a good chance that he is a valid user. On the other hand, a user who attempted to answer the questions twice and succeeded in providing a correct answer on his third attempt might be considered suspicious. This user did not know the answers right away so there is a chance that he may be a fraud trying out new answers.
To view more details about the policy, you can launch the Policy Explorer using the icon on top of the panel or from any of the icons within the table. The policy link displays the Policy Details page and the rules link displays the Rule Details page. Only active and triggered rules are displayed. Only active policies are displayed. You have the option to view all the rules in the Policy Explorer.
In the Policy Explorer, you can view the runtime values for each one of the policies and rules that were triggered. For example, if a rule triggered that showed that the user had logged in from a country that he did not usually log in from, you would want to look at the runtime details to see which country he logged in from. The Policy Explorer shows the policies that were triggered, the condition parameters, and the actual values.
6.8.2.3 Transactions
The Transactions panel displays a list of transactions that were created. You can view the actual transaction data and the entity attribute values used in the transactions. For example, a fraud investigator analyzing a session can see that a user was blocked performing a transaction and that a particular rule was triggered, and he can also see the amount that was passed in and the account number that was used in the transaction.
Transactions can be created within a checkpoint or without an associating checkpoint. If a Transaction ID is not provided (as in the case of a transaction without an associating checkpoint), OAAM processes the last transaction in the session. The Transaction data for all transaction types are displayed in the Transactions panel of the session details page whether associated to a checkpoint or not. The Transaction checkpoints and policies are displayed in the order of execution along with other checkpoints, but the order of execution of the transactions and the checkpoints at which a particular transaction occurred cannot be determined.
6.8.3 Action, Alerts, and Scores
Table 6-6 shows an example of alerts, actions, and scores displayed in a Session Details page.
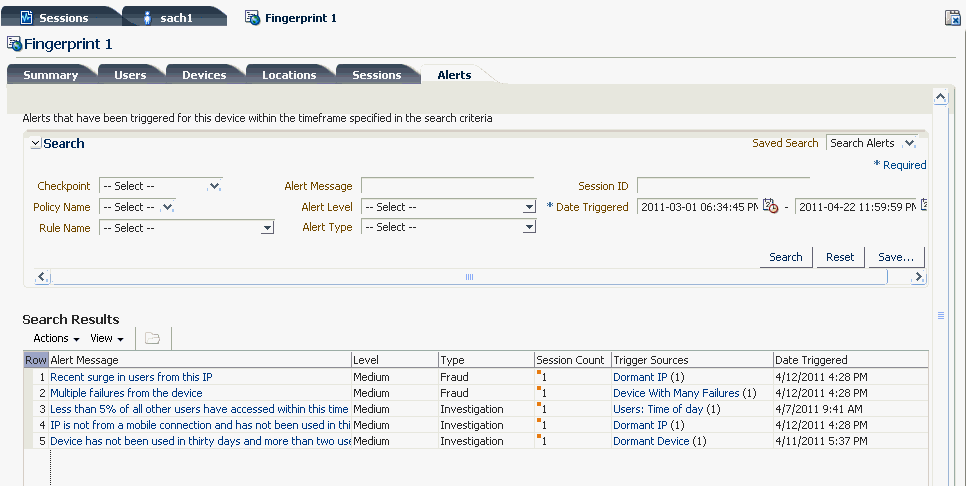
The Alerts panel shows alerts that were generated for a checkpoint during the session and details about the alerts, as shown in the table below. Each checkpoint could trigger multiple alerts. High-level alerts are displayed in bold red.
Table 6-7 Sessions Checkpoint Actions
| Item | Description |
|---|---|
|
Level |
Severity of the alert whether high, medium, low. |
|
Alert Message |
Text message configured in the alert. |
|
Type |
Type of the alert whether fraud, investigation, information, or other reason |
|
Trigger Source |
Rules that generated the particular alert |
|
Timestamp |
The time the alert was generated. |
All actions are displayed in the Actions panel with a Action Name column and a separate column indicating whether or not the action is final. The final action is also displayed in the top right section of checkpoint panel.
Scores are displayed for the policy and checkpoint. The scores are useful in detecting the probability of fraud or business scenarios and in decision making.
6.8.4 Outcomes from Each Checkpoints
Checkpoint panels are arranged in chronological order of execution and display the checkpoints and a list of the actions and alerts that were triggered at those checkpoints. By default, checkpoint panels are collapsed. In the initial opened view, only the transactions and the final alerts are displayed in the expanded form. All other subpanels are collapsed. You can expand all the panels to view additional information for that checkpoint.
The first checkpoint panel could be one for Pre-Authentication. On top of the panel, the total amount of time taken for this checkpoint to execute, the final action, and the final risk score are shown.
6.9 Investigation and the Importance of Details Pages
OAAM provides the capability to gather detailed information about the session parameters and to allow you to drill down further into the details involved in the session. For example, you need information to investigate logins so you perform a sessions search. From the results, you can see the country, location, and other session information, as shown in Figure 6-7.
If you want to know more details about one of these, you can open a details page. These pages provide more information about the item you are interested in and allow you to filter out further and look at the related data to that particular item. In this example, if you open the location details page for the United States, you can look at the logins that only happened in the United States and all the devices used when users logged into the United States. Then, you can filter on the date created or updated if you want to look at the devices that were created during a particular time frame and used in logins from the United States. In this way, you are able to limit the data you wanted to view based on the detailed information you are looking at.
In fraud analysis an Investigator looks at sessions to find out more about what occurred. For example, to know if there was a pattern with a specific country or specific user, you would want to see more information about the user and country. For that, you would use the details pages. If you want to know if the United States belongs to a blacklist group or a monitor group, you can use the Groups tab of the Location Details page to search for those groups.
If you want to look at all the users who logged in from the United States, you can use the Users tab of the Location Details page to search on the authentication status for all the logins that were successful. You can also view the login failures from the country, the challenge success, and the challenge failure counts also.
You can also look at all the different alerts that were generated from the logins or sessions that occurred from the United States by using the Alerts tab of the Location Details page to search on the Alert ID, Alert Type, or Alert Level.
6.10 Viewing Alerts
When an alert is generated it is associated with the user, device, and location that has taken part in the authentication. The login session holds information about the alert. Any changes to the alert type or alert message are automatically reflected in the alerts page. It shows the new information. Other than the Alerts tab, the detail pages display alert instances based on the level/type at the time they were triggered. Alert instances are grouped with the alert template they belong to. For example, if there were 10 sessions with alert level High last month and then the Administrator changed the level of that template to low, then the next 10 instances are displayed with the level Low.
6.11 User Details Page
The User Details page provides general details about the user and cross reference on other data types such as device, location, alerts, browser, OS, and so on. Also shown are details related to the user such as unique ID, Organization ID, groups the user belongs to, sessions and cache data, fingerprint, browser, OS, locale, and so on. You can open a User Details page to view details regarding that user by clicking the User Name or UserID link from the Sessions search, Session Details, and other pages.
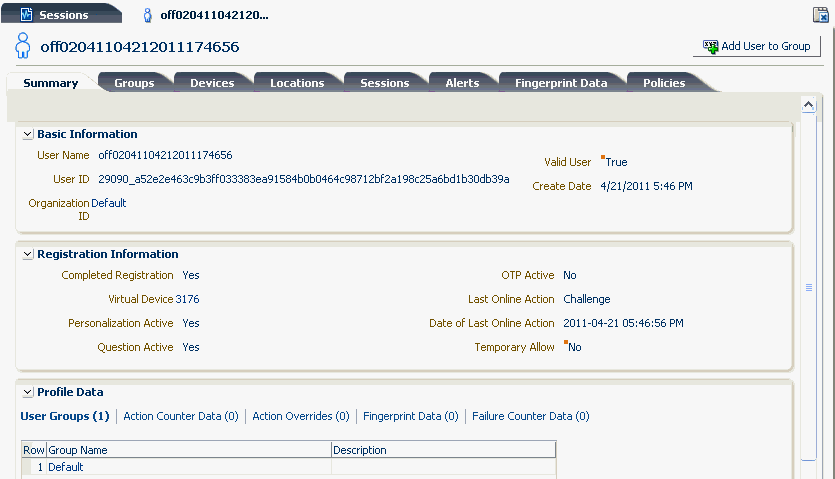
Figure 6-12 shows a User Details page.
The User Details page is divided into the following tabs:
| User Details Tab | Function |
|---|---|
|
Summary |
The Summary tab contains basic, registration, and profile information for the user. |
|
Groups |
The Groups tab shows a listing of the user groups that the user is a member of. The user can belong to User ID and User Name groups. |
|
Locations |
The Locations tab lists successful and unsuccessful login attempts from all user locations. This tab enables you to find out which locations and how many times a user logged in from a particular location. |
|
Devices |
The Devices tab lists all the devices that have been used in a session by the user during the time frame mentioned in the search criteria. It lists both successful and unsuccessful login attempts from all users' devices. This tab helps you find out which devices and how many times a device was used by the user. |
|
Alerts |
The Alerts tab lists alerts that are triggered and generated for a user by the application during the transaction process. The information shown is based on alert templates and not alert instances. Alert templates are displayed with the current details (level/type). |
|
Sessions |
The Sessions tab lists login sessions for a user for a particular period. |
|
Policies |
The Policies tab lists default and custom rules that are run for a user by the rules engine based on the checkpoints during authentication. |
|
Fingerprint Details |
The Fingerprint Details tab lists fingerprints created for the user during login. |
Detailed information about the User Details tabs follow.
6.11.1 User Details: Summary Tab
The Summary tab contains basic, registration, and profile information for the user.
Table 6-9 summarizes the basic information about a user that is provided by the User Details: Summary Tab.
Table 6-9 User Details: Basic Information about the User
| Field | Definition |
|---|---|
|
User Name |
Login name given by user to login. |
|
User ID |
Unique Identifier of that device |
|
Organization ID |
Identifies the organization to which the user belongs. |
|
Valid User |
True if the user has authenticated successfully at least once. |
|
Created Date |
Date on which the user was created. Also, this refers to the first login date of the user. |
The first time a user logs in, he must go through the registration process. Information is capture during the process. Table 6-10 summarizes the properties and attribute values that identify the status of each action performed by the user during the registration process.
Table 6-10 User Details: Registration Information
| Field | Definition |
|---|---|
|
Completed Registration |
(Yes/No) Identifies whether user has completed the registration process like registered challenge questions, image and phrase, which are unique for each user and used for identifying a user for security reasons. |
|
Virtual Device Type |
List of device IDs that the user registered as secure device during registration process. Maximum of three devices can be registered. |
|
Personalization Active |
(Yes/No) Identifies whether user registered Image and Phrase. |
|
Question Active |
(Yes/No) Identifies whether user registered Challenge Questions. |
|
OTP Active |
(Yes/No) Identifies whether user has been assigned One Time Password on SMS/Email Challenge. |
|
Last Online Action |
The last online action performed by user in his most recent transaction. |
|
Date of Last Online Action |
Date of last online action performed by user in his most recent transaction. |
|
Temporary Allow |
(Yes/No) Identifies whether the user was blocked and is allowed to access his account temporarily. |
This Profile Data section lists important statistics about the user using cached data. Aggregate values are shown for User Groups, Action Counter Data, Action Override Data, Fingerprint Data, and Policies. These values use cache data and records are always shown even if the database is purged.
Table 6-11 User Details; Profile Data
| Field | Definition |
|---|---|
|
User Groups |
Lists groups associated with the user. |
|
Action Counter Data |
Lists the different actions performed by the user along with the aggregate count for each one of them. The data is available only if the "incrementCacheCounter" property is set to true in the "rule.action.enum". |
|
Action Overrides |
Lists the checkpoints and the overriding actions for the user if an override is active like a temporary allow. For example, if the user was blocked earlier and is now allowed to access his account temporarily then, during Pre-authentication, instead of blocking the user, the user is allowed to proceed with the transaction (i.e. Block action is overridden to Allow). The values for overriding actions are configured in properties file. |
|
Fingerprint Data |
Lists the fingerprint information for the user if the cookies and flash are turned off. The Fingerprint Data ID numbers shown on this panel is the same as those shown in the fingerprint data tab. The difference between Fingerprint Data and the Fingerprint Data tab is that the tab shows the ID numbers and other information such as the browser, locale, and so on. |
|
Failure Counter Data |
List of Challenges faced by the user and total number of times the user failed to answer each one of them respectively. |
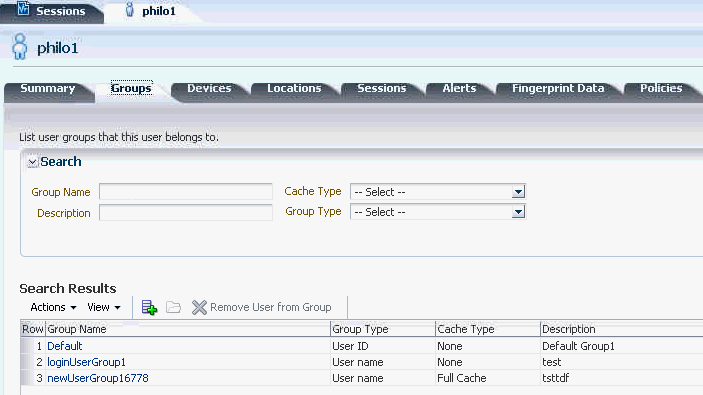
6.11.2 User Details: Groups Tab
The tab lists groups with which the user is associated. The user can belong to User ID and User Name groups.
The tab contains the following filter parameters.
Table 6-12 User Details: Group Filters
| Filters | Description |
|---|---|
|
Group Name |
Name of the group. You can enter the complete name or part of a group name. For example, if you enter new, any group with new in any part of its name is displayed. |
|
Description |
This filter maps to the User Group: description field |
|
Cache Type |
Groups offer two Cache Type options: Full Cache or None. For information, refer to Cache Policy. |
|
Group Type |
Category to which the group belongs. |
The search results show Group Name, Group Type, Cache Type, and Description columns. The default sorting is on Group Name. You can open the Group Details page by clicking the Group Name link.
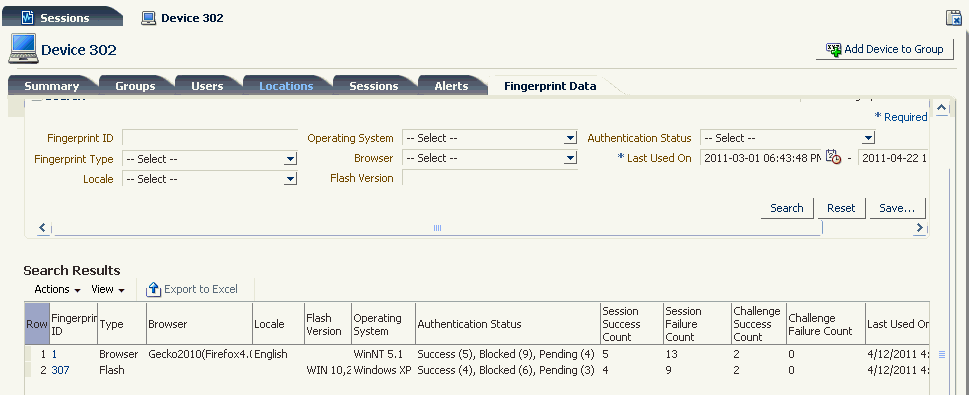
6.11.3 User Details: Devices Tab
This tab lists all the devices that have been used in a session by the user during the time frame mentioned in the search criteria.
The tab contains the following filter parameters:
Table 6-13 User Details: Device Tab
| Field | Description |
|---|---|
|
Device ID |
Uniquely identifies each device and is autogenerated by the application. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
Get all the devices which were used by the user to login during the given time duration. |
Device ID, Authentication Status, Session Success Count, Session Failure Count, Challenge Success Count, Challenge Failure Count, and Last Used On information are shown. The default sorting is on the Device ID. Device ID is unique and hence a Device ID is not repeated more than once in the results.
The login/challenge success and failure counts correspond to the aggregate counts for the time frame.
You can open the Device Details page by clicking the Device ID link.
6.11.4 User Details: Locations Tab
This tab lists all the locations from where the user had made successful and unsuccessful login attempts.
The tab contains the following filter parameters:
Table 6-14 User Details: Locations Tab
| Filters | Description |
|---|---|
|
Country |
Country ID |
|
State |
State ID. The State list is dynamically populated with respect to what has been selected for Country. For example, if United States is selected, whatever states are available for that country are shown under States. |
|
City |
City ID. The City list is dynamically populated with respect to what has been selected for in Country and State. |
|
IP Address |
Address mapped to a location usually, although some addresses are unknown or private |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
Get all the locations from which the user logged in during the given time duration |
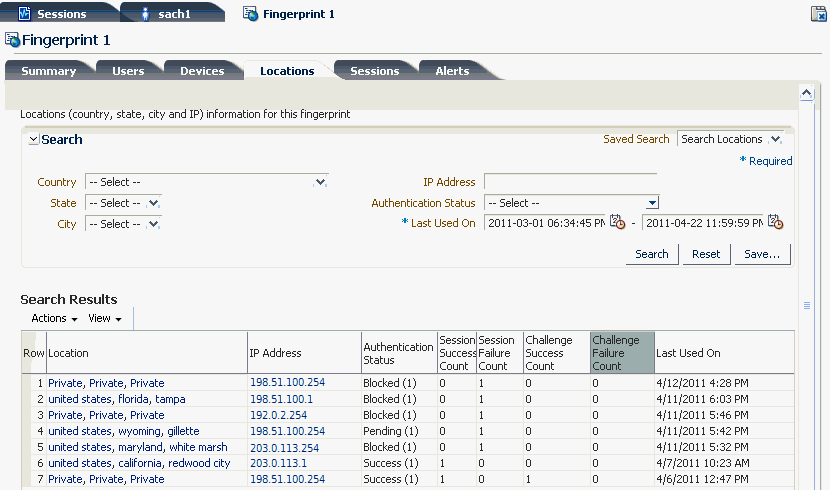
Results show the location, IP address, authentication status, session success count, session failure count, challenge success count, challenge failure count, and so on.
If a location is chosen in the search, the location may appear in the results as many times as the different IP addresses the user has used for the location. For each location there are associated success and failure counts.
Authentication Status and success and failure count values are related. For example, if there is a Success (1) value in the Authentication Status column, the Session Success Count column should show "1." If there is a Pending (1) value in the Authentication Status column, the Session Failure Count column should show "1."
Location on the result is always detailed to city level. For example, United States, California, Fremont. The default sorting is on the location name. Data cannot be edited on this page.
6.11.5 User Details: Sessions Tab
This tab lists login sessions for a user for a particular period.
The tab contains the following filter parameters:
Table 6-15 User Details: Sessions tab
| Filter | Description |
|---|---|
|
Session ID |
Unique session identifier. |
|
Alert Message |
Display name describing the alert. Partial searches can be performed on alert messages. |
|
Alert Level |
Severity of the alert whether high, medium, low. |
|
Device ID |
Uniquely identifies each device and is autogenerated by the application. |
|
Organization ID |
Identifies the organization the user belongs to |
|
Country |
Country where the login or transaction occurred. |
|
State |
State where the login or transaction occurred. |
|
City |
City where the login or transaction occurred. |
|
IP Address |
Address mapped to a location usually, although some addresses are unknown or private |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Client Type |
Virtual Authentication Devices. Device or application used for authentication or fingerprinting. For example: TextPad, KeyPad, Question Pad, login page, flash tracker. auth.client.type.enum is the enum used |
|
Login time |
Get all the sessions during which the device logged in for the given time duration. |
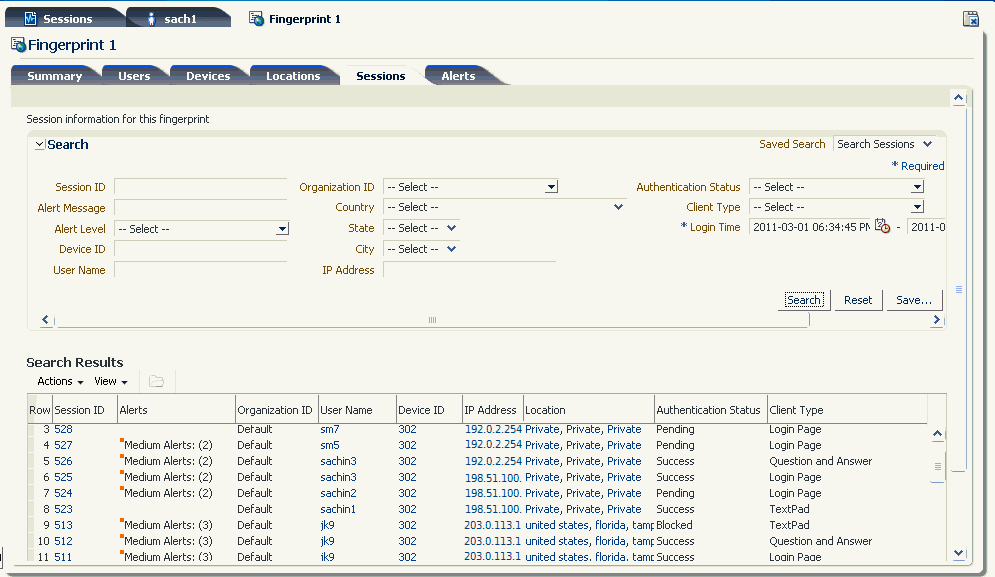
Session ID, Alerts, Organization ID, Device ID, IP Address, Location, Authentication Status, Client Type, Pre-Authentication Action, and Login Time shown.
6.11.6 User Details: Alerts Tab
This tab lists alerts that are triggered and generated for a user by OAAM Admin during transaction process. The information shown is based on alert templates and not alert instances. Alert templates are displayed with the current details (level/type).
The tab contains the following filter parameters:
Table 6-16 User Details: Alert Filters
| Filters | Description |
|---|---|
|
Checkpoint |
Decision and enforcement point when policies are call to run their rules. For information, refer to Checkpoint. |
|
Policy Name |
Name of the policy. The policy list is dynamically populated in respect to what has been selected for the checkpoint. |
|
Rule Name |
Rule that generated the alert. The rules list is dynamically populated in respect to what has been selected for the policy name. |
|
Alert ID |
ID of an alert. |
|
Alert Message |
Display name describing the alert. |
|
Alert Level |
Severity of the alert whether high, medium, low. |
|
Alert Type |
Type of the alert whether fraud, investigation, information, or other reason. |
|
Session ID |
Unique identifier for the session. |
|
Date Triggered |
Given time when the alerts triggered for the user. |
Figure 6-18 shows the Alerts tab of the User Details page.
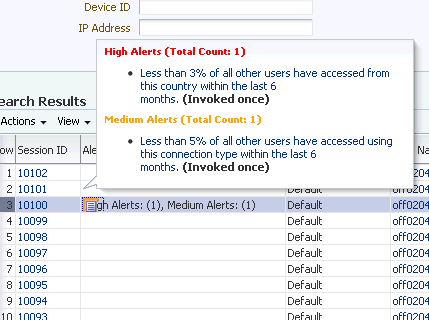
If you click an Alert Message link, details about the particular alert are shown. Details are shown for the level, alert types, and session count. In the example graphic above, the alert on the second row, "IP is not from a local mobile...," had generated in two sessions (shown in Session Count). If you click the Session Count link and then the session number, the Session Details page is displayed.
The trigger sources (name of rules) shows the rules that generated this particular alert and each one is associated with a count.
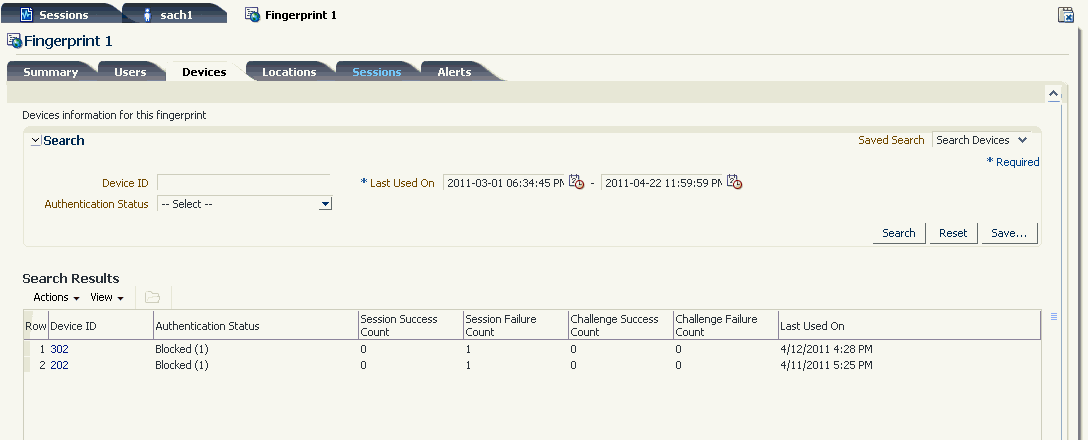
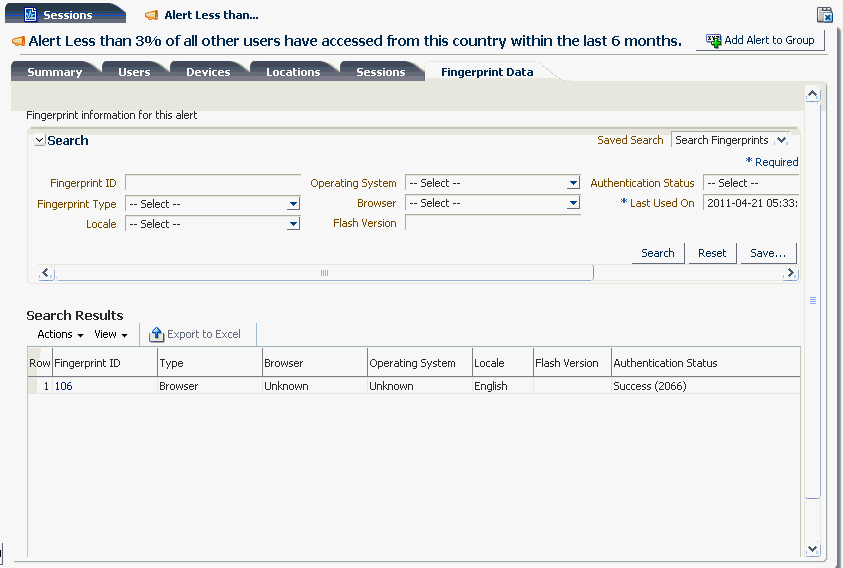
6.11.7 User Details: Fingerprint Data
This tab lists fingerprints created for the user during login. The tab contains the following filter parameters:
Table 6-17 User Details: Fingerprint Data Tab
| Filters | Description |
|---|---|
|
Fingerprint ID |
Unique ID generated for fingerprint by the application |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Browser Type |
The type of browser a user is viewing pages with |
|
OS Type |
Type of operating system |
|
Locale |
A set of parameters that defines the user's language, country and any special variant preferences that the user wants to see in their user interface |
|
Last Date Used |
Get all the fingerprints created for the given time duration |
Information is captured on the devices the user used.
The Actions menu allows you to open the particular fingerprint.
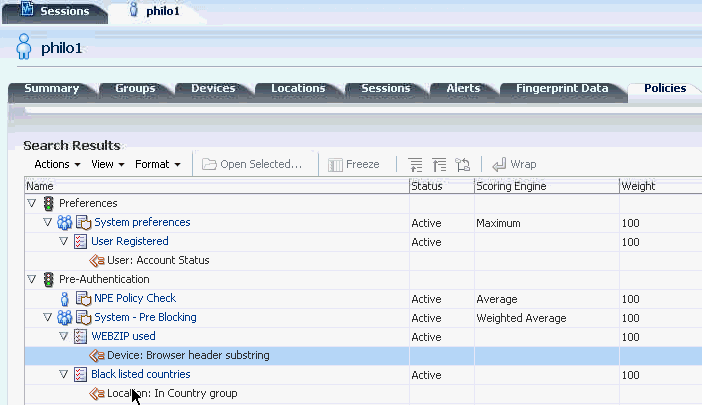
6.11.8 User Details: Policies Tab
This tab lists default and custom rules that are run for a user by the rule engine based on the checkpoints during authentication. The policies tab displays all the policies and rules that are run for the user including any nested policies in trigger combinations.
Only active policies and rules are displayed on this tab. If a policy is disabled it is not listed in this tab. Users can search for a specific checkpoint. The default sorting is on the name. The checkpoints is sorted alphabetically at the global level and the policies within each checkpoint is also sorted alphabetically.
6.11.9 User Details Tasks
This section describes how to obtain information about the user through the use of the User Details pages.
6.11.9.1 View general user information, registration information, and profile information
To view general user information, registration information, and profile information, click the User ID or User Name link from the sessions page for a valid user and view the Summary page.
6.11.9.2 View the actions performed by the user during registration
To view the actions performed by the user during registration:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
View the Registration Information section of the Summary tab for the status of each action performed by the user during the registration process.
6.11.9.3 View statistics about the user
To view statistics about the user:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
View the Profile Data / Cache Data section of the Summary tab.
6.11.9.4 Search and view the different devices used for a user to get additional information like the number of times a device is used by a user and the successful and unsuccessful login attempts from each device
To search and view the different devices used for a user to get additional information like the number of times a device is used by a user and the successful and unsuccessful login attempts from each device:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
Click the Devices tab.
-
Search for the different devices used for a user.
This tab lists all the devices that have been used in a session by the user during the time frame mentioned in the search criteria
-
In the search results, view the following information for the devices for each user:
-
Login Failures
-
Login Successes
-
Challenge Failures
-
Challenge Successes
-
6.11.9.5 Search and view the different user groups with which a user is associated
To search and view the different user groups with which a user is associated:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
Click the Groups tab.
-
Search for the different groups with which the user is associated using the following parameters:
A user can belong to User ID and User Name groups.
Filters Description Group Name
Name of the group. You can enter the complete name or part of a group name. For example, if you enter new, any group with new in any part of its name is displayed.
Group Type
Category to which the group belongs.
Cache Type
Groups offer two Cache Type options: Full Cache or None.
For information, refer to Cache Policy.
Group Description
This filter maps to the User Group: description field
6.11.9.6 Search and view the different locations used for a user to get additional information such as the number of times a location is used by a user and the successful and unsuccessful login attempts from each location
To search and view the different locations used for a user to get additional information such as the number of times a location is used by a user and the successful and unsuccessful login attempts from each location:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
Click the Locations tab.
-
Search for the different locations using the following filter parameters:
Filters Description Location
Country ID, State ID, City ID
IP Address
Address mapped to a location usually, although some addresses are unknown or private
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Last Used On
Get all the locations from which the user logged in during the given time duration
-
In the search results, view the following information for the device from each location:
-
Login Failures
-
Login Successes
-
Challenge Failures
-
Challenge Successes
-
6.11.9.7 Search and view all the alerts triggered and generated for the user
To search and view all the alerts triggered and generated for the user. The alerts are shown with different color codes to indicate the alert levels whether it is high, medium or low:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
Click the Alerts tab.
This tab lists alerts that were triggered and generated for a user during the transaction process.
-
Search for the different alerts using the following filter parameters:
Filters Description Alert Message
Display name describing the alert.
Alert ID
ID of an alert.
Alert Type
Type of this alert whether fraud, investigation, information, or other types.
Alert Level
Severity of the alert whether high, medium, low.
Rule Name
Rule that generated the alert.
Date Triggered
Given time when the alerts triggered for the user.
-
In the search results, view the alerts triggered and generated for the user:
The alerts are shown with different color codes to indicate the alert levels (whether is high, medium or low).
6.11.9.8 Search and view all the login sessions or search login sessions for a particular period for the user
To search and view all the alerts triggered and generated for the device. The alerts are shown with different color codes to indicate the alert levels whether it is high, medium or low:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
Click the Sessions tab.
This tab lists login sessions for a user for a particular period.
-
Search for the different sessions using the following filter parameters:
Filter Description Session ID
The unique identifier for a session.
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Client Type
Virtual Authentication Devices. Device or application used for authentication or fingerprinting. For example: TextPad, KeyPad, Question Pad, login page, flash tracker. auth.client.type.enum is the enum used
Alert Level
Severity of the alert whether high, medium, low.
User Name
Login name given by user to login.
Organization ID
Identifies the organization to which the user belongs.
IP Address
Address mapped to a location usually, although some addresses are unknown or private
Location
The place where the login or transaction occurred
Session Date
Get all the sessions during which the device logged in for the given time duration.
6.11.9.9 View the rules run on the user
To view the rules run on the user:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
Click the Policies tab.
This tab lists default and custom rules that are run for a user.
6.11.9.10 Search and view the fingerprints created for the user
To search and view the fingerprints created for the user:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
Click the Fingerprints tab.
This tab lists fingerprints created for the user during login.
6.11.9.11 Add user to user group
You could add users to groups and create groups, using the Add User to Group button from search and details pages.
If you are viewing the details of a specific user, and based on the analysis, you identified this user as a fraudster, you could add this user to a blacklisted group from the dialog. You do not have to navigate away to the details page to add the user.
To add a user to a user group:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
Click Add User To Group at the upper right corner.
The Add User to Group dialog is displayed.
-
Search for the group you want to add the user to by the group name.
Only those groups that the user is not a member of are displayed.
-
Select the group to add the user to and click the Add button.
6.11.9.12 Create a new user group and add user to the newly created group
The Add User to Group and Add to Group dialogs allow you to search and view the details of a user group, before adding the user to that group. If you do not find the group to which this user belongs, a new group can be created.
If you perform a fraud analysis, and you identify that this particular user belongs to a certain group, but you do not have that group available, you can create that group. Then, you can add that particular user to that group.
To create a new user group and add user to the newly created group:
-
Click the User ID or User Name link from the Sessions page for a valid user.
The User Details page is displayed.
-
Click the Add User to Group button at the upper right corner.
The Add to User dialog is displayed.
-
Click Create New Group button and specify the details for the new group.
-
Select the Open this Group's details tab when done option.
-
Click the Add button.
The group's details tab is displayed with the user added.
6.11.9.13 Remove user from user group
You can remove a user from the group from detail pages. For example, if you added a user to a monitor user group, and you have been monitoring the user for three months, and you realize that he or she is a valid user, you can remove that user from that group.
To remove a user from the user groups:
-
Click the User ID or User Name link from Sessions page for a valid user.
The User Details page is displayed.
-
View the Groups tab.
The Groups tab shows a listing of the groups.
-
Remove the user from a group by selecting a specific row and clicking the Remove from group button.
You can select multiple rows to remove multiple users.
-
Click Remove from Group.
The user is removed from the group selected.
Note:
You should not be able to remove a user from the Organization ID of the primary user group.
6.11.9.14 Navigate to other details pages for groups, alerts, devices, locations, sessions, policy, rules and fingerprints
You can click a link from a tab to open the corresponding details pages.
-
From the Users tab: click the User Name link to open the User Details page.
-
From the Groups tab: click the Group Name link to open the Group Details page.
-
From the Locations tab, click the Location or IP link to open the Location Details page.
-
From the Alerts tab, click the Alert Message link to open the Alert Details page.
-
From the Devices tab: click the Device ID link to open the Device Details page.
-
From the Fingerprint tab: click the Fingerprint ID to open the corresponding fingerprint details page.
Links for User Name, IP address, session, and location are available on the Sessions tab.
6.12 IP or Locations (Country, State, or City) Details Page
IP, Country, State, or City Details pages provide details for an IP Address, country, state, or city, including mapping of city, state, country, cross reference on other data types such as device, user, alerts, sessions, browser, OS, locales, fingerprints, and so on.
You can drill down to the respective Location Details page by selecting either the IP Address, Country Name, State Name, or City Name shown in the Sessions search result or Case's sessions tab.
The Location Details page is divided into the following tabs:
Table 6-22 Location Details Tabs
| Location Details Tabs | Description |
|---|---|
|
Summary |
The Summary tab provides general location information. |
|
Groups |
The Groups tab lists groups which the location is associated to. |
|
Users |
The Users tab lists successful and unsuccessful login attempts by all users from the location. |
|
Devices |
The Devices tab lists successful and unsuccessful login attempts by all devices from the location. |
|
Alerts |
The Alerts tab lists alerts that are generated for the location by the application during transaction process. The information shown is based on alert templates and not alert instances. Alert templates are displayed with the current details (level/type). |
|
Sessions |
The Sessions tab lists login sessions for a location for a particular period. |
|
Fingerprints |
The Fingerprints tab lists fingerprints created for the location during login. |
6.12.1 Location Details: Summary Tab
The Summary tab provides general location information. Information is displayed about country and state depending on the item selected. For example, if the user selected a city called "San Jose", the Summary tab displays the state and country name for that city. If the user selected the state called "California," only the country information is listed.
If you want to view IP Address details, you can click the IP Address link.
Table 6-23, "Country Details" lists the general country details that are displayed in the Summary tab of a Country Details page.
| Country Details | Description |
|---|---|
|
Country ID |
The ID of a country which is unique |
|
Country Code |
Geographical code (geocode) representing the country. |
|
Country Name |
Geographic name of country. |
Table 6-24, "State Details" lists the general state details that are displayed in the Summary tab of a State Details page.
| State Details | Description |
|---|---|
|
State ID |
The ID of a state. |
|
State Code |
Geographical code (geocode) representing the state. |
|
State Name |
Geographic name of state |
|
Country Name |
Geographic name of country the state belongs to. |
Table 6-25, "City Details" lists the general city details that are displayed in the Summary tab of a City Details page.
| City Details | Description |
|---|---|
|
City ID |
The ID of the city. |
|
City Code |
Geographical code (geocode) representing the city. |
|
City Name |
Geographic name of the city. |
|
State Name |
Geographic name of the state the city belongs to. |
|
Country Name |
Geographic name of the country the city belongs to. |
Table 6-26, "IP Details" lists the general IP information that are displayed in the Summary tab of the IP Details page.
| IP Details | Description |
|---|---|
|
IP Address |
Address mapped to a location usually, although some addresses are unknown or private |
|
City Name |
Geographic name of the city. |
|
State Name |
Geographic name of the state. |
|
Country Name |
Geographic name of the country. |
|
Connection Speed |
Internet connection speeds or bandwidths (high, medium, low). |
|
Connection Type |
Describes the data connection between the device or LAN and the internet. See the Connection Type mapping. |
|
Routing Type |
Tells how the user is routed to the internet. |
|
Carrier |
The name of the entity that manages the ASN entry. |
|
ASN |
Globally unique number assigned to a network or group of networks that is managed by a single entity. |
|
Top-level Domain |
The top-level domain of the URL. For example, .com in www.company.example.com. This is mapped through the Quova reference file. |
|
Second-level Domain |
The second-level domain of the URL. For example, Name in www.oracle.com. This is mapped through the Quova reference file. |
|
City Confidence Factor |
The confidence factor (1-99) that the correct city has been identified. |
|
State Confidence Factor |
The confidence factor (1-99) that the correct state has been identified. |
|
Country Confidence Factor |
The confidence factor (1-99) that the correct country has been identified. |
6.12.2 Location Details: Groups Tab
The Groups tab shows a listing of the geolocation groups the location belongs to.
Table 6-27, "Location Details: Group Filters" lists the filter parameters available for group searches.
Table 6-27 Location Details: Group Filters
| Filters | Description |
|---|---|
|
Group Name |
Name of the group. You can enter the complete name or part of a group name. For example, if you enter new, any group with new in any part of its name is displayed. |
|
Group Description |
This filter maps to the User Group: description field |
|
Cache Type |
Groups offer two Cache Type options: Full Cache or None. For information, refer to Cache Policy. |
The group tab shows a listing of the groups which the location is associated to.
If the location belongs to multiple groups, all the groups are listed. Click the Group Name link to open the Group Details page. Click the IP Address link to view IP Address Details.
6.12.3 Location Details: Users Tab
This tab lists all the users who used the location during the time frame mentioned in the search criteria
Table 6-28, "Location Details: Users Tab" lists filter parameters available for user searches.
Table 6-28 Location Details: Users Tab
| Filter | Description |
|---|---|
|
User Name |
Login name given by user to login. |
|
Organization ID |
Identifies the organization to which the user belongs. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
The last date the location was used to log in. |
The search results display the User Name, Authentication Status, Last Used On, Login Failures, Login Successes, Challenge Failures, and Challenge Successes for each user.
By default, the results are displayed are sorted by User Name in ascending order. Only one row is displayed for each User Name. The login and challenge success and failure counts correspond to the aggregate counts for the time frame.
The user can open the User Details page by clicking the User Name link.
6.12.4 Location Details: Devices Tab
This tab lists all the devices used from the location during the time frame mentioned in the search criteria
Table 6-29, "Location Details: Device Tab" lists the filter parameters available for device searches.
Table 6-29 Location Details: Device Tab
| Field | Description |
|---|---|
|
Device ID |
Uniquely identifies each device and is autogenerated by the application. No results are shown if you provide an invalid Device ID. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. By default, the Authentication status is set to "all." You can select multiple authentication status values. |
|
Date Range |
Get all the devices which were used by the user to login during the given time duration. No results are shown if you provide an invalid date range. |
The search results display the Device ID, Authentication Status, Last Used On, Login Failures, Login Successes, Challenge Failures, and Challenge Successes for each user.
By default, the results are displayed are sorted by Device ID in ascending order. Only one row is displayed for each Device ID. The login and challenge success and failure counts correspond to the aggregate counts for the time frame.
A device details page can be opened by clicking the Device ID link.
6.12.5 Location Details: Alerts Tab
This tab lists all the alerts that have been triggered from the location during the date range provided. The information shown is based on alert templates and not alert instances. Alert templates are displayed with the current details (level/type).
The tab contains the following filter parameters.
Table 6-30 Location Details: Alert Filters
| Filters | Description |
|---|---|
|
Alert Message |
Display name describing the alert. |
|
Alert ID |
ID of an alert. |
|
Alert Type |
Type of the alert whether fraud, investigation, information, or other types. Multiple alert types can be selected. |
|
Alert Level |
Severity of the alert whether high, medium, low. Multiple alert levels can be selected. |
|
Rule Name |
Rule that generated the alert. Multiple rules can be selected. |
|
Date Triggered |
Get all the alerts triggered during the given time duration for the user. |
The results display all the alert sources with the current details (level/type) for each alert message along with their count (total number of times the alert has been triggered).
Clicking the Session ID in the search results opens the Sessions search page with pre-filled search parameters (Alert Level, Alert Message, Alert Type, Date, and so on).
6.12.6 Location Details: Sessions Tab
This tab lists login sessions for a location for a given time frame. It contains the following filter parameters:
| Filter | Description |
|---|---|
|
Session ID |
The unique identifier for a session. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Client Type |
Virtual Authentication Devices. Device or application used for authentication or fingerprinting. For example: TextPad, KeyPad, Question Pad, login page, flash tracker. auth.client.type.enum is the enum used. |
|
Alert Level |
Severity of the alert whether high, medium, low. |
|
Device ID |
Uniquely identifies each device and is autogenerated by the application. |
|
User Name |
Login name given by user to login. |
|
Organization ID |
Identifies the organization to which the user belongs. |
|
Session Date |
The date the login or transaction occurred. |
By default the results are sorted by Session ID, which is unique. Clicking the Device ID, IP address, User Name, or alerts link opens the corresponding details page.
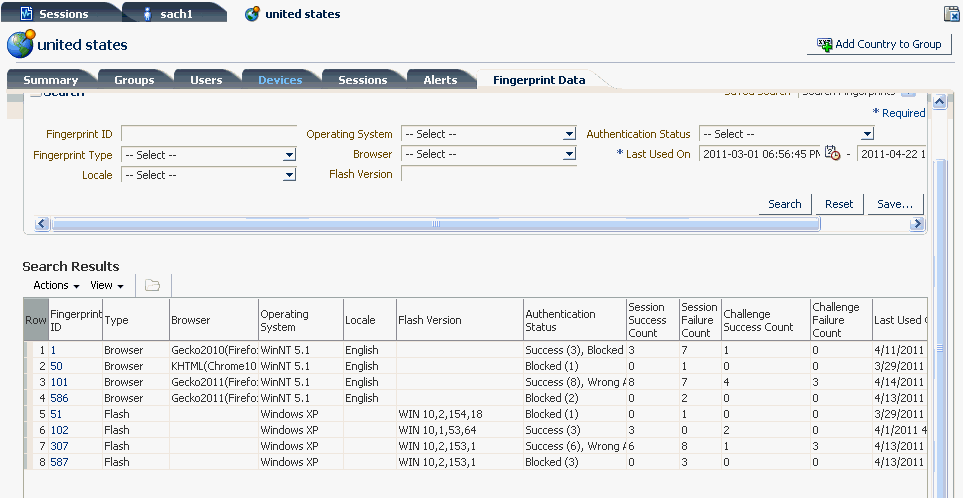
6.12.7 Location Details: Fingerprints Tab
This tab lists fingerprints created for the location during login.
The tab contains the following filter parameters:
| Filters | Description |
|---|---|
|
Fingerprint ID |
Unique ID generated for fingerprint by the application |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Browser Type |
The type of browser a user is viewing pages with |
|
OS Type |
Type of operating system |
|
Locale |
A set of parameters that defines the user's language, country and any special variant preferences that the user wants to see in their user interface |
|
Last Date Used |
Get all the fingerprints created for the given time duration |
By default, the results are sorted by browser Fingerprint ID. The browser/flash fingerprint combination is unique and hence each combination has only one row in the results table. The Fingerprint ID has a link and opens the corresponding Fingerprint Details page.
6.12.8 Location (Country, State, City, or IP) Details Tasks
This section describes how to obtain information through the use of the Location Details pages.
6.12.8.1 View general information about the location
To view general information about a location:
-
From the results of a session search, click the country, state, city, or IP link.
The Location Details page for that country, state, city, or IP is displayed.
-
View the Summary tab.
On the Summary tab, additional information is displayed about the country and state depending on the item selected.
For example, if you select a city called "San Jose," the Summary tab displays the state and country names for that city. If you select the state "California," only the country information is listed.
For details on the information displayed on the Summary tab, refer to Section 6.12.1, "Location Details: Summary Tab."
6.12.8.2 Search and view the different location groups to which a location is associated or belongs
To search and view the different location groups that a location is associated with or belongs to:
-
From the results of a session search, click the country, state, city, or IP link.
The Location Details page for that country, state, city, or IP is displayed.
-
Click the Groups tab.
-
Search and view the different location groups to which a location is associated or belongs by using the following filters:
Table 6-33 Location Details: Group Filters
Filters Description Group Name
Name of the group. You can enter the complete name or part of a group name. For example, if you enter new, any group with new in any part of its name is displayed. Group Name is not case sensitive.
No records are shown if you enter an invalid Group Name.
Cache Type
Groups offer two Cache Type options: Full Cache or None.
By default, the Cache Type should be set to "all."
For information, refer to Cache Policy.
Group Description
The description for the group.
Group Description is case insensitive. You can enter part of the group description.
No results are shown if you enter special characters or a description that is too long.
The group tab shows a listing of the geolocation groups the location belongs to. If the location belongs to multiple groups, all the groups are listed. You can open the Group Details page by clicking the Group ID link.
6.12.8.3 Add location to existing location group
Only Security Administrators, System Administrators, and Investigators have access to the Add to Group command. CSRs do not have access to the Add to Group command. The Add to Group button is available in the Sessions search and other details pages.
Locations can be added to geolocation group types. A location can be added to only one location group at a time.
To add a location to a location group:
-
In the Sessions search or other details page, click the location link.
The Location Details page is displayed.
-
Click the Add Location to Group button at the upper right corner.
The Add to Group dialog is displayed.
-
Search for the group you want to add the location to by the group name.
Only those groups that the location is not a member of are displayed.
If you do not find the country, state, or city group you need, you can create a new group. Information for doing so is provided later.
-
Select the group to add the location to and the Open this Group's details tab when done option.
-
Click the Add button.
The group's details tab is displayed with the location added.
6.12.8.4 Create a location group and add location to it
To create a location group and add the location to it:
-
In the Sessions search or other details page, click the location link.
The Location Details page is displayed.
-
Click the Add Location to Group button at the upper right corner.
The Add to Group dialog is displayed.
-
Click Create New Group button and specify the details for the new group.
-
Select the Open this Group's details tab when done option.
-
Click the Add button.
The group's details tab is displayed with the location added.
6.12.8.5 Search and view the different users that logged in from the location get additional information like the number of times a user logged in from the location and the successful and unsuccessful login attempts from the location by each user
To search and view the different users that logged in from the location get additional information like the number of times a user logged in from the location and the successful and unsuccessful login attempts from the location by each user:
-
From the results of a session search, click the country, state, city, or IP link.
The Location Details page for that country, state, city, or IP is displayed.
-
Click the Users tab.
-
To see additional information such as the number of times a user logged in from the location, search by User Name. The Login Successes column displays the number of times a user logged in.
-
To see the number of successful and unsuccessful login attempts from the location by each user, select Blocked and Success as the Authentication Status.
Login failures and successes are displayed for each user.
-
6.12.8.6 Search and view the different devices that logged in from the location get additional information like the number of times a device logged in from the location and the successful and unsuccessful login attempts from the location by each device
To search and view the different devices that logged in from the location get additional information like the number of times a device logged in from the location and the successful and unsuccessful login attempts from the location by each device:
-
From the results of a session search, click the country, state, city, or IP link.
The Location Details page for that country, state, city, or IP is displayed.
-
Click the Devices tab.
-
To see additional information such as the number of times a device was used to log in from the location, search by Device ID. The Login Successes column displays the number of times a device was used to log in.
-
To see the number of successful and unsuccessful login attempts from the location by each device, select Blocked and Success as the Authentication Status.
Login failures and successes are displayed for each device.
-
6.12.8.7 Search and view all the alerts triggered and generated for the location
To search and view all the alerts triggered and generated for the location. The alerts are shown with different color codes to indicate the alert levels whether it is high, medium or low
-
From the results of a session search, click the country, state, city, or IP link.
The Location Details page for that country, state, city, or IP is displayed.
-
Click the Alerts tab and view the results table for the alert levels.
6.12.8.8 Search and view all the login sessions or search login sessions for a particular period for the location
To search and view all the login sessions or search login sessions for a particular period for the location:
-
From the results of a session search, click the country, state, city, or IP link.
The Location Details page for that country, state, city, or IP is displayed.
-
Click the Sessions tab.
-
Enter session dates to get sessions for that period for the location.
6.12.8.9 Search and view the fingerprints created for the location
To search and view the fingerprints created for the location:
-
From the results of a session search, click the country, state, city, or IP link.
The Location Details page for that country, state, city, or IP is displayed.
-
Click the Fingerprint Data tab.
-
Search by OS, locale, browser, Fingerprint ID, and so on.
6.12.8.10 Navigate to other details pages for groups, alerts, devices, users, sessions and fingerprints
You can click the links in tabs to open the corresponding details page:
-
From the Summary tab: click the IP Address link to view IP Address Details.
-
From the Groups tab: click the Group Name link to open the Group Details page.
-
From the Devices tab: click the Device ID link to open the Device Details page.
-
From the Users tab: click the User Name link to open the User Details page.
-
From the Alerts tab: click the Session ID to open the Sessions search page with pre-filled search parameters (Alert Level, Alert Message, Alert Type, Date, and so on
-
From the Fingerprint tab: click the Fingerprint ID to open the corresponding Fingerprint Details page.
On the Sessions tab, links are provided for the following pages
-
For the Session Details - Links are provided for session ID
-
For IP Details - Links are provided for Country, State and City
-
For Country Details - Links are provided for IP, State and City
-
For State Details - Links are provided for IP, Country and City
-
For City Details - Links are provided for IP, Country and State
6.13 Device Details Page
The Device Details page displays details about a device including cross reference on other data types such as user, location, alerts, browser, sessions, full list of fingerprint data, and so on. You can open the Device Details page by clicking any Device ID link from the Sessions search, Session Details, or other listing pages.
The Device Details page is divided into the following tabs:
Table 6-34 Device Details Tabs
| Device Details Tabs | Descriptions |
|---|---|
|
Summary |
The Summary tab provides general device information. |
|
Groups |
The Groups tab list groups with which the device is associated. For example Restricted Devices Group. |
|
Users |
The Users tab lists successful and unsuccessful login attempts from all users using the device. This report helps to find out which users and how many times a user used the device for login. |
|
Locations |
The Locations tab lists successful and unsuccessful login attempts from all devices' locations. This report helps to find out which locations and how many times a device logged in from a particular location. |
|
Sessions |
The Sessions tab lists login sessions for a device for a particular period. |
|
Alerts |
The Alerts tab lists alerts that are triggered and generated for a device by OAAM Admin during transaction process. The information shown is based on alert templates and not alert instances. Alert templates are displayed with the current details (level/type). |
|
Fingerprint Data |
The Fingerprint tab shows browser and flash fingerprint information for the device. |
|
Fingerprint Details |
The Fingerprint Details tab lists fingerprints created for the device during login. |
6.13.1 Device Details: Summary Tab
The Summary tab provides general device information. The following information is provided:
Table 6-35 Device Details Basic Information
| Device Details Summary Tab | Description |
|---|---|
|
Device ID |
Uniquely identifies each device and is autogenerated by the application. |
|
Operating System |
Device OS. The information is fetched from the fingerprint data associated with the device |
|
Browser |
Device Browser type. The information is fetched from the fingerprint data associated with the device |
|
Create Date |
Date on which the user has first used the device for authentication. Also, this refers to the first login date of the device. |
|
Last Used On |
This date refers to the most recent login time from the device. |
Table 6-36 Device Details Fingerprint Information
| Device Details Fingerprint Tab | Description |
|---|---|
|
Browser Fingerprint Data |
This field shows information such OS type, browser type, and so on. |
|
Flash Fingerprint Data |
This field shows information such as OS type, browser type, Player Type, Has audio, Has mp3, Supports streaming audio, and so on. |
6.13.2 Device Details: Groups Tab
This tab lists groups to which the device is associated. For example, Restricted Devices. The tab contains the following filter parameters:
Table 6-37 Device Details: Group Filters
| Filters | Description |
|---|---|
|
Group Name |
Name of the group. You can enter the complete name or part of a group name. For example, if you enter new, any group with new in any part of its name is displayed. |
|
Description |
This filter maps to the User Group: description field |
|
Cache Type |
Groups offer two Cache Type options: Full Cache or None. For information, refer to Cache Policy. |
You can open the Group Details page by clicking the Group ID link.
6.13.3 Device Details: Users Tab
This tab lists successful and unsuccessful login attempts from all users using the device. The tab contains the following filter parameters.
Table 6-38 Device Details: User tab
| Filter | Description |
|---|---|
|
User Name |
Login name given by user to login. |
|
Organization ID |
Identifies the organization to which the user belongs. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
Get all the users who used the device to login during the given time duration. |
The results are sorted by User Name and in ascending order. Each user is displayed only once in the results. You can open the User Details by clicking the User ID link
6.13.4 Device Details: Locations Tabs
This tab lists successful and unsuccessful login attempts from all locations. The tab contains the following filter parameters.
Table 6-39 Device Details: Location Tab
| Filters | Description |
|---|---|
|
Location |
Country ID, State ID, City ID |
|
IP Address |
Address mapped to a location usually, although some addresses are unknown or private |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
Get all the locations from which the user logged in during the given time duration |
The Locations are displayed multiple times, if the IP is different for the same device used to log in from the same location. Location is sorted by name and in ascending order. The login/challenge success and failure counts correspond to the aggregate counts for the time frame.
You can open the IP Details page by clicking the IP address link.
6.13.5 Device Details: Alerts Tab
This tab lists alerts that are generated for a device during transaction process. The information shown is based on alert templates and not alert instances. Alert templates are displayed with the current details (level/type).
The tab contains the following filter parameters.
Table 6-40 Device Details: Alert Filters
| Filters | Description |
|---|---|
|
Checkpoint |
Decision and enforcement point when the policies were called to run their rules |
|
Policy Name |
The name of the policy. The policy list is dynamically populated in respect to what has been selected for the checkpoint. |
|
Rule Name |
Rule that generated the alert. |
|
Alert Message |
Display name describing the alert. |
|
Alert ID |
ID of an alert. |
|
Alert Level |
Severity of the alert whether high, medium, low. |
|
Alert Type |
Type of the alert whether fraud, investigation, information, or other types. |
|
Session ID |
The ID of the session |
|
Date Triggered |
Given time when the alerts triggered for the user. |
The results displays all the alert sources for each alert message along with their count (total number of times it has been triggered).
By default the results are sorted by alert messages in ascending order.
Clicking the Session ID opens the Sessions search page with pre-filled search parameters (Alert Level, Alert Message, Alert Type and Date).
6.13.6 Device Details: Sessions Tab
This tab lists login sessions for a device for a particular period. The tab contains the following filter parameters.
| Filter | Description |
|---|---|
|
Session ID |
The unique identifier for the session. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Client Type |
Virtual Authentication Devices. Device or application used for authentication or fingerprinting. For example: TextPad, KeyPad, Question Pad, login page, flash tracker. auth.client.type.enum is the enum used |
|
Alert Level |
Severity of the alert whether high, medium, low. |
|
User Name |
Login name given by user to login. |
|
Organization ID |
Identifies the organization to which the user belongs. |
|
IP Address |
Address mapped to a location usually, although some addresses are unknown or private |
|
Location |
The geolocation. |
|
Session Date |
Get all the sessions during which the device logged in for the given time duration. |
By default, the results are sorted by Session ID in descending order.
Session ID is usually unique unless the IP or device has changed while the session is in progress.
6.13.7 Device Details: Fingerprint Data Tab
This tab lists fingerprints created for the device during login.
The tab contains the following filter parameters.
Table 6-42 Device Details: Fingerprint Data
| Filters | Description |
|---|---|
|
Fingerprint ID |
Unique ID generated for fingerprint by the application |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Browser Type |
The type of browser a user is viewing pages with |
|
OS Type |
Type of operating system |
|
Locale |
A set of parameters that defines the user's language, country and any special variant preferences that the user wants to see in their user interface |
|
Last Date Used |
Get all the fingerprints created for the given time duration |
6.13.8 Device Details Tasks
This section describes how to obtain information through the use of the Device Details pages.
6.13.8.1 View general information about the device
To view general information about the device:
-
Click the Device ID link in the Session search page or other pages.
The Device Details page is opened and shows additional details.
-
View the Summary tab.
The following general data is displayed:
-
Device ID
-
OS
-
Browser
-
Created Date
-
Last Used On
-
6.13.8.2 View flash and browser fingerprint information created for the device
To view general information about the device:
-
Click the Device ID link in the Session search page or other pages.
The Device Details page is opened and shows additional details.
-
View the Fingerprint Data tab.
Flash and Browser Fingerprint data is shown.
6.13.8.3 Search and view the different device groups to which a device is associated or belongs
To search and view the different device groups to which a device is associated or belongs:
-
Click the Device ID link in the Session search page or other pages.
The Device Details page is opened and shows additional details.
-
View the Groups tab.
-
Search groups using the following filters:
Filters Description Group Name
Name of the group. You can enter the complete name or part of a group name. For example, if you enter new, any group with new in any part of its name is displayed.
Group Type
Category to which the group belongs.
Cache Type
Groups offer two Cache Type options: Full Cache or None.
For information, refer to Cache Policy.
Group Description
This filter maps to the User Group: description field
6.13.8.4 Add/Remove Device from a Device Group
To add a device to a device group:
-
In the Sessions search or other details page, click the Device ID link.
The Device Details page is displayed.
-
Click the Add Device to Group button at the upper right corner.
The Add to Group dialog is displayed.
-
Search for the group you want to add the device to by the group name and device group type.
Only those groups that the device is not a member of are displayed.
If you do not find the device group you need, you can create a new group. Information for doing so is provided later.
-
Select the group to add the device to and the Open this Group's details tab when done option.
-
Click the Add button.
The group's details tab is displayed with the device added.
To remove a device from a device group:
-
Click the Device ID link in the Session search page.
The Device Details page is opened and shows additional details.
-
View the Groups tab.
The Groups tab shows a listing of the groups. The device is a member of all these device groups.
-
Click the Device Group that contains the device.
-
In the details page of the group, click the Devices tab.
-
Remove the device from a group by selecting the specific row and clicking the Delete selected members button on the toolbar.
-
Click Delete on the Confirmation dialog.
-
Click OK to dismiss the Information dialog.
The device is removed from the group selected.
6.13.8.5 Create a device group and add device to it
To create a device group and add the device to it:
-
In the Sessions search or other details page, click the Device ID link.
The Device Details page is displayed.
-
Click the Add Device to Group button at the upper right corner.
The Add to Group dialog is displayed.
-
Click Create New Group button and specify the details for the new group.
-
Select the Open this Group's details tab when done option.
-
Click the Add button.
The group's details tab is displayed with the device added.
6.13.8.6 Search and view the different users that used the device to login to get additional information like the number of times the device was used by a user and the successful and unsuccessful login attempts for the device by each user
To search and view the different users that used the device to login to get additional information like the number of times the device was used by a user and the successful and unsuccessful login attempts for the device by each user:
-
Click the Device ID link in the Session search page or other pages.
The Device Details page is opened and shows additional details.
-
Click the Users tab.
-
Search for the different users using the following filter parameters:
Filter Description User Name
Login name given by user to login.
Organization ID
Identifies the organization to which the user belongs.
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Last Used On
Get all the users who used the device to login during the given time duration.
-
In the search results, view the following:
-
Failure Counter (the login fail count)
-
Success Counter (the login success count)
-
6.13.8.7 Search and view the different locations from which the device was used for login to get additional information like the number of times the device was used from a location and the successful and unsuccessful login attempts for the device from each location
To search and view the different locations from which the device was used for login to get additional information like the number of times the device was used from a location and the successful and unsuccessful login attempts for the device from each location:
-
Click the Device ID link in the Session search page or other pages.
The Device Details page is opened and shows additional details.
-
Click the Locations tab.
-
Search for the different locations using the following filter parameters:
Filters Description Location
Country ID, State ID, City ID
IP Address
Address mapped to a location usually, although some addresses are unknown or private
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Last Used On
Get all the locations from which the user logged in during the given time duration
-
In the search results, view the following for the device from each location:
-
Failure Counter (the login fail count)
-
Success Counter (the login success count)
-
6.13.8.8 Search and view all the alerts triggered and generated for the device
To search and view all the alerts triggered and generated for the device. The alerts are shown with different color codes to indicate the alert levels whether it is high, medium or low:
-
Click the Device ID link in the Session search page or other pages.
The Device Details page is opened and shows additional details.
-
Click the Alerts tab.
This tab lists alerts that are triggered and generated for a device during transaction process.
-
Search for the different alerts using the following filter parameters:
Filters Description Alert Message
Display name describing the alert.
Alert ID
ID of an alert.
Alert Type
Type of the alert whether fraud, investigation, information, or other types.
Alert Level
Severity of the alert whether high, medium, low.
Rule Name
Rule that generated the alert.
Date Triggered
Given time when the alerts triggered for the user.
-
In the search results, view the alerts triggered and generated for the device:
The alerts are shown with different color codes to indicate the alert levels (whether is high, medium or low).
6.13.8.9 Search and view all the login sessions or search login sessions for a particular period for the device
To search and view all the alerts triggered and generated for the device. The alerts are shown with different color codes to indicate the alert levels whether it is high, medium or low:
-
Click the Device ID link in the Session search page or other pages.
The Device Details page is opened and shows additional details.
-
Click the Sessions tab.
This tab lists login sessions for a device for a particular period.
-
Search for the different sessions using the following filter parameters:
Filter Description Session ID
The unique identifier for a session.
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Client Type
Virtual Authentication Devices. Device or application used for authentication or fingerprinting. For example: TextPad, KeyPad, Question Pad, login page, flash tracker. auth.client.type.enum is the enum used
Alert Level
Severity of the alert whether high, medium, low.
User Name
Login name given by user to login.
Organization ID
Identifies the organization to which the user belongs.
IP Address
Address mapped to a location usually, although some addresses are unknown or private
Location
Place where login or transaction occurred
Session Date
Get all the sessions during which the device logged in for the given time duration.
6.13.8.10 Search and view the fingerprints created for the device
To search and view the fingerprints created for the device:
-
Click the Device ID link in the Session search page or other pages.
The Device Details page is opened and shows additional details.
-
Click the Fingerprint Data tab.
This tab lists the fingerprints created for the device during login.
6.13.8.11 Navigate to other details pages for groups, alerts, users, locations, sessions and fingerprints
You can click links on a tab in a details page to open other details pages:
-
From the Users tab: click the User Name link to open the User Details page.
-
From the Groups tab: click the Group Name link to open the Group Details page.
-
From the Locations tab, click the Location link to open the Location Details page.
-
From the Alerts tab: click the Alert Message to open the Alert Details page.
-
Links for User Name, IP address, session, and location are available on the Sessions tab.
6.14 Browser or Flash Fingerprint Details
You can drill down to the Fingerprint Details page from the Sessions search results by selecting a Browser or Flash Fingerprint ID.
There are two different kinds of Fingerprint Details pages:
-
Flash Fingerprint
-
Browser Fingerprint
6.14.1 Fingerprint Details: Summary Tab
The Fingerprint Details Summary page shows general fingerprint information and the data collected during device fingerprinting.
The basic information provided by this tab include:
Table 6-48 Fingerprint Details Tab
| Fingerprint Details | Description |
|---|---|
|
Fingerprint ID |
Unique ID generated for fingerprint by the application |
|
Fingerprint Type |
Type of fingerprint, whether the fingerprint is a flash or browser fingerprint. |
|
Created Date |
Date on which the fingerprint was created in the system |
Depending on the Fingerprint type, Fingerprint data provided by this tab may include browser, OS, locale information and digital information such as Player Type, Has audio, Has mp3, Supports streaming audio, and so on. Flash fingerprint information is available only if flash is installed on the user-client's machine.
6.14.2 Fingerprint Details: Users Tab
This tab lists all the users who used the fingerprint during the time frame specified. The Users tab of the Fingerprint Details page enables you to determine which users and how many times the fingerprint was used for each user during the login process.
The tab contains the following filter parameters:
Table 6-49 Fingerprint Details: Users tab
| Filter | Description |
|---|---|
|
User Name |
Login name given by user to login. (Not for Fingerprint) |
|
Organization ID |
Identifies the organization to which the user belongs. (Not for fingerprint) |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
Get all the users who used the device to login during the given time duration. (not for fingerprint) |
6.14.3 Fingerprint Details: Devices Tab
This tab lists all devices for which the fingerprint was used.
The Device tab of the Fingerprint Details page enables you to determine which devices and how many times the fingerprint was used for each device during login process.
The tab contains the following filter parameters.
Table 6-50 Fingerprint Details: Devices Tab
| Field | Description |
|---|---|
|
Device ID |
Uniquely identifies each device and is autogenerated by the application. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
Get all the devices which were used by the user to login during the given time duration. |
6.14.4 Fingerprint Details: Locations Tab
This tab lists all locations for which the fingerprint was used.
The Locations tab of the Fingerprint Details page enables you to determine which locations and how many times the fingerprint was used for each location during the login process.
The tab contains the following filter parameters.
Table 6-51 Fingerprint Details: Locations Tab
| Filters | Description |
|---|---|
|
Country |
Country ID |
|
State |
State ID |
|
City |
City ID |
|
IP Address |
Address mapped to a location usually, although some addresses are unknown or private |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
Get all the locations from which the user logged in during the given time duration |
6.14.5 Fingerprint Details: Sessions Tab
This tab lists of login sessions in which the fingerprint was generated for a particular period.
The tab contains the following filter parameters.
Table 6-52 Fingerprint Details: Sessions tab
| Filter | Description |
|---|---|
|
Session ID |
ID of the session. |
|
Alert Message |
Display name describing the alert |
|
Alert Level |
Severity of the alert whether high, medium, low. |
|
Device ID |
Unique identifier of each device autogenerated by the application. |
|
User Name |
Login name given by user to login. |
|
Organization ID |
Identifier for the organization to which the user belongs. |
|
Country |
Country ID |
|
City |
City ID |
|
State |
State ID. |
|
IP Address |
Address mapped to a location usually, although some addresses are unknown or private |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Login Time |
Login time of the session. Field used to get all the sessions during which the device logged in for the given time duration. |
6.14.6 Fingerprint Details: Alerts Tab
This tab lists alerts that have been triggered for this device within the time frame specified in the search criteria.
The tab contains the following filter parameters.
Table 6-53 Fingerprint Details: Alerts Tab
| Filter | Description |
|---|---|
|
Checkpoint |
Decision and enforcement point when the policies were called to run their rules |
|
Policy Name |
Name of the policy. The policy list is dynamically populated in respect to what has been selected for the checkpoint. |
|
Rule Name |
Name of the rule that generated the alert. |
|
Alert Message |
Display name describing the alert |
|
Alert Level |
Severity of the alert whether high, medium, low. Multiple alert levels can be selected. |
|
Alert Type |
Type of the alert whether fraud, investigation, information, or other types. Multiple alert types can be selected. |
|
Session ID |
Unique identifier for a session |
|
Date Triggered |
Date the alert was triggered for this device. Required field. |
6.14.7 Fingerprint Details Tasks
This section describes how to obtain information through the use of the Fingerprint Details pages.
6.14.7.1 View flash fingerprint details
The flash fingerprint is only be available if the "flash" is installed on the client machines. To view flash fingerprint details, click the Flash Fingerprint ID link from the session details or listing page.
The Fingerprint Details page opens with additional details.
6.14.7.2 View browser fingerprint details
To view browser fingerprint details, click the Browser Fingerprint ID link from the session details or listing page.
The Fingerprint Details page opens with additional details.
6.14.7.3 Search and view the different users for which the fingerprint was used
To search and view the different users for which the fingerprint was used:
-
Click the Fingerprint ID link in the Session details or listing page.
The Fingerprint Details page is opened and shows additional details.
-
Click the Users tab.
This tab lists all the users who used the fingerprint during the time frame specified.
-
Search for the different users for which the fingerprint was used using the following filter parameters:
Table 6-54 Fingerprint Details: Users tab
Filter Description User Name
Login name given by user to login. (Not for Fingerprint)
Organization ID
Identifies the organization to which the user belongs. (Not for fingerprint)
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Last Used On
Get all the users who used the device to login during the given time duration. (not for fingerprint)
6.14.7.4 Search and view the different devices for which the fingerprint was used
To search and view the different devices for which the fingerprint was used:
-
Click the Fingerprint ID link in the Session details or listing page.
The Fingerprint Details page is opened and shows additional details.
-
Click the Devices tab.
This tab lists all devices for which the fingerprint was used.
-
Search for the different devices for which the fingerprint was used using the following filter parameters:
Table 6-55 Fingerprint Details: Users tab
Filter Description User Name
Login name given by user to login. (Not for Fingerprint)
Organization ID
Identifies the organization to which the user belongs. (Not for fingerprint)
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Last Used On
Get all the users who used the device to login during the given time duration. (not for fingerprint)
This report helps to find out which devices were used and how many times the fingerprint was used for each device during login process.
6.14.7.5 Search and view the different locations for which the fingerprint was used
To search and view the different locations for which the fingerprint was used:
-
Click the Fingerprint ID link in the Session details or listing page.
The Fingerprint Details page is opened and shows additional details.
-
Click the Locations tab.
This tab lists all locations for which the fingerprint was used.
-
Search for the different locations for which the fingerprint was used using the following filter parameters:
Table 6-56 Fingerprint Details: Locations Tab
Filters Description Location
Country ID, State ID, City ID
IP Address
Address mapped to location
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Last Used On
Get all the locations from which the user logged in during the given time duration
This report helps to find out which locations and how many times the fingerprint was used for each location during login process.
6.14.7.6 Search and view all the login sessions or search login sessions for a particular period for the fingerprint
To search and view all the login sessions or search login sessions for a particular period for the fingerprint:
-
Click the Fingerprint ID link in the Session details or listing page.
The Fingerprint Details page is opened and shows additional details.
-
Click the Sessions tab.
This tab lists of login sessions in which the fingerprint was generated for a particular period.
-
Search and view all the login sessions or search login sessions by the Session Date for the fingerprint.
Searching by Session Date gets all the sessions during which the device logged in for the given time duration.
6.14.7.7 Navigate to other details pages for users, devices, sessions and locations
You can access other details pages from a details page:
-
From the Users tab: click the User Name link to open the User Details page.
-
From the Locations tab, click the Location or IP link to open the Location Details page.
-
From the Devices tab: click the Device ID link to open the Device Details page.
-
Links for User Name, IP address, session, and location are available on the Sessions tab.
6.15 Alert Details Page
The Alert Details page provides information on the message, level, type of the message and cross references on other data types such as user, device, location, sessions, browser, operating system, locales, and others. Additionally, information is provided about the generation of the alert.
The Alert Details page allows you to quickly see the relationship between not just the users who have generated the alert but also other data relationships that would be useful like locales that have been used while generating the alert.
You can open the Alert Details page from Alert Message links in the Sessions search page, Session Details and other details pages, and Agent cases.
The Alert Details page presents general information and relationships details in the following tabs:
| Alert Details Tabs | Description |
|---|---|
|
Summary |
This is the general alert information |
|
Users |
List all users for which the alert was generated. This report helps to find out which users and how many times the alert was generated for each user during login process. |
|
Devices |
List all devices for which the alert was generated. This report helps to find out which devices and how many times the alert was generated for each device during login process. |
|
Locations |
List all locations for which the alert was generated. This report helps to find out which locations and how many times the alert was generated for each location during login process. |
|
Sessions |
List of login sessions in which the alert was generated for a particular period. |
|
Fingerprint Data |
List of fingerprints created in the login process during which the alert was generated. |
6.15.1 Alert Details: Summary Tab
This tab provides general information about the alert and the alert template with the current details (level/type).
Table 6-58 Alert Details: Summary Tab
| Alerts Summary | Description |
|---|---|
|
Alert Message |
Text message configured in the alert. |
|
Alert Type |
Type of alert template currently, whether it is for fraud, investigation, information, and so on. |
|
Alert Level |
Severity of the alert template currently, whether it is high, medium, low. |
|
Alert Group |
Group with which the alert template is linked/associated. |
6.15.2 Alert Details: Users Tab
This tab lists the users that have a session in which the alert was triggered.
The tab contains the following filter parameters.
Table 6-59 Alert Details: Users tab
| Filter | Description |
|---|---|
|
User Name |
Login name given by user to login. |
|
Organization ID |
Identifies the organization to which the user belongs. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Trigger Date |
Date the alert was triggered. |
The search results display the User Name, Alert Count, and Last Date Trigger for each user. Each user is listed only one time. The Alert Count displays the number of times, the alert was triggered for the user during a time frame. By default, the results are sorted by User Name.
You can open the User Details page by clicking the User Name link.
6.15.3 Alert Details: Devices Tab
This tab lists the devices that have been in a session in which the alert was triggered.
The page contains the following filter parameters.
Table 6-60 Alert Details: Device Tab
| Field | Description |
|---|---|
|
Device ID |
Uniquely identifies each device and is autogenerated by the application. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
Get all the devices which were used by the user to login during the given time duration. |
The search results display the Device ID, Alert Count, and Last Date Trigger for each device. By default, the results are sorted by Device ID in ascending order. Each Device ID is listed only one time. Alert Count displays the number of times, the alert was triggered for the device during a time frame.
You can open the Device Details page by clicking the Device ID link.
6.15.4 Alert Details: Locations Tab
This tab lists the locations (country, state and city) that have been in a session in which the alert was triggered.
The page contains the following filter parameters.
| Filters | Description |
|---|---|
|
Location |
Country ID, State ID, City ID |
|
IP Address |
Address mapped to a location usually, although some addresses are unknown or private |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Last Used On |
Get all the locations from which the user logged in during the given time duration |
The search results display the location, IP address, authentication status, last trigger date, user name, and alert count for each location. If the alert is generated from the same city but different IP then that city appears as many times as the unique IP. Alert Count displays the number of times, the alert was triggered from the location during a time frame.
You can open the Location Details page by clicking the Location link.
Clicking the User Name or IP address link opens the corresponding details page.
6.15.5 Alert Details: Sessions Tab
This tab lists sessions in which the alert was triggered.
The tab contains the following filter parameters.
| Filter | Description |
|---|---|
|
Session ID |
The unique identifier for a session. |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Client Type |
Virtual Authentication Devices. Device or application used for authentication or fingerprinting. For example: TextPad, KeyPad, Question Pad, login page, flash tracker. auth.client.type.enum is the enum used |
|
Device ID |
Uniquely identifies each device and is autogenerated by the application. |
|
User Name |
Login name given by user to login. |
|
IP Address |
Address mapped to a location usually, although some addresses are unknown or private |
|
Location |
Where the login occurred |
|
Trigger Date |
Generation date |
By default the results are sorted by Session ID, which is unique.
You can view the Session Details page by clicking the Session ID link.
Clicking the Device ID, IP address, user name, or location link opens the corresponding details page.
6.15.6 Alerts Details: Fingerprint Data
This tab displays the fingerprint information used when the alert was triggered during the time frame specified.
The tab contains the following filter parameters.
Table 6-63 User Details: Fingerprint Data Tab
| Filters | Description |
|---|---|
|
Fingerprint ID |
Unique ID generated for fingerprint by the application |
|
Authentication Status |
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status. |
|
Browser Type |
The type of browser a user is viewing pages with |
|
OS Type |
Type of operating system |
|
Locale |
A set of parameters that defines the user's language, country and any special variant preferences that the user wants to see in their user interface |
|
Last Date Used |
Get all the fingerprints created for the given time duration |
6.15.7 Alert Details Tasks
This section describes how to obtain information through the use of the Alert Details page.
6.15.7.1 View general information about the alert
To view general information about the alert, click the alert message links from the session details, other detail pages, or agent pages.
6.15.7.2 View alert groups with which an alert is associated
To view the alert group with which an alert is associated:
-
Navigate to the Sessions search page.
-
Click the yellow box next to the Alert in the Search Results table.
-
Click the alert message link.
The Alert group is displayed in the Summary tab.
6.15.7.3 Add alert from alert groups
To add an alert from alert groups:
-
Click the alert message links from the session details, other detail pages, or agent pages.
The Alert Details page is displayed.
-
Click Add Alert To Group at the upper right corner.
The Add Alert to Group dialog is displayed.
-
Search for the group you want to add the alert to by the group name.
Only those groups that the alert is not a member of are displayed.
-
Select the group to add the alert to and click the Add button.
6.15.7.4 Create an alert group and add an alert to it
To create an alert group and add the alert to it:
-
Click the alert message links from the session details, other detail pages, or agent pages.
The Alert Details page is displayed.
-
Click the Add Alert to Group button at the upper right corner.
The Add to Alert dialog is displayed.
-
Click Create New Group button and specify the details for the new group.
-
Select the Open this Group's details tab when done option.
-
Click the Add button.
The group's details tab is displayed with the alert added.
6.15.7.5 Search and view the different users for which the alert was generated
To search and view the different users for which the alert was generated:
-
Click the alert message links from the session details, other detail pages, or agent pages.
The Alert Details page is displayed.
-
Click the Users tab.
This tab lists the users that have a session in which the alert was triggered.
-
Search for the different users for which the alert was generated using the following filter parameters:
Table 6-64 Alert Details: Users tab
Filter Description User Name
Login name given by user to login.
Organization ID
Identifies the organization to which the user belongs.
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Last Trigger Date
Date the alert was triggered.
6.15.7.6 Search and view the different devices for which the alert was generated
To search and view the different devices for which the alert was generated:
-
Click the alert message links from the session details, other detail pages, or agent pages.
The Alert Details page is displayed.
-
Click the Devices tab.
This tab lists the devices that have been in a session in which the alert was triggered.
-
Search for the different devices for which the alert was generated using the following filter parameters:
Field Description Device ID
Uniquely identifies each device and is autogenerated by the application.
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Last Used On
Get all the devices which were used by the user to login during the given time duration.
6.15.7.7 Search and view the different locations for which the alert was generated
To search and view the different locations for which the alert was generated:
-
Click the alert message links from the session details, other detail pages, or agent pages.
The Alert Details page is displayed.
-
Click the Locations tab.
This tab lists the locations (country, state and city) that have been in a session in which the alert was triggered.
-
Search for the different locations for which the alert was generated using the following filter parameters:
Filters Description Location
Country ID, State ID, City ID
IP Address
Address mapped to a location usually, although some addresses are unknown or private
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Last Used On
Get all the locations from which the user logged in during the given time duration
6.15.7.8 Search and view all the login sessions or search login sessions for a particular period for the alert
To search and view all the login sessions or search login sessions for a particular period for the alert:
-
Click the alert message links from the session details, other detail pages, or agent pages.
The Alert Details page is displayed.
-
Click the Sessions tab.
This tab lists sessions in which the alert was triggered.
-
Search and view all the login sessions or search login sessions for a particular period for the alert using Trigger Date.
6.15.7.9 Search and view the fingerprints created
To search and view the fingerprints created:
-
Click the alert message links from the session details, other detail pages, or agent pages.
The Alert Details page is displayed.
-
Click the Fingerprint Data tab.
This tab displays the fingerprint information used when the alert was triggered during the time frame specified.
-
Search and view the fingerprints created by using the following filters:
Table 6-67 User Details: Fingerprint Data Tab
Filters Description Fingerprint ID
Unique ID generated for fingerprint by the application
Authentication Status
Status of the session (each login/transaction attempt creates a new session). For information, refer to Authentication Status.
Browser Type
The type of browser a user is viewing pages with
OS Type
Type of operating system
Locale
A set of parameters that defines the user's language, country and any special variant preferences that the user wants to see in their user interface
Last Date Used
Get all the fingerprints created for the given time duration
6.15.7.10 Navigate to other details pages for groups, users, devices, locations, sessions and fingerprints
You can open details pages from other details pages:
-
From the Users tab: click the User Name link to open the User Details page.
-
From the Groups tab: click the Group Name link to open the Group Details page.
-
From the Locations tab, click the Location link to open the Location Details page.
-
From the Devices tab: click the Device ID link to open the Device Details page.
-
From the Fingerprint tab: click the Fingerprint ID to open the corresponding Fingerprint Details page.
-
Links for User Name, IP address, session, and location are available on the Sessions tab.
6.16 Uses Cases
This section describes example use cases for the Session Details page.
6.16.1 Use Case: Search Sessions
You are a member of the security team at Acme Corp. You work with Oracle Adaptive Access Manager on a regular basis, following up on escalated customer issues and security alerts. You perform a session search every couple hours throughout the day to identify any issues needing your attention and it is time to perform the next search. Directions: Search for sessions in the last 24 hours that have triggered high severity alerts and where access was blocked or locked.
To search sessions:
-
Log in to OAAM Admin as an Investigator.
-
In the Navigation tree, double-click Sessions.
The Sessions Search page is displayed.
-
Search through sessions in the last 24 hours with high alerts and a blocked or locked authentication status
-
For Authentication Status, select Blocked and Locked.
-
For Login Time, select the date and time, 24 hours ago, and the current date and time.
-
For Alert Level, select High.
-
Click Search.
-
6.16.2 Use Case: Session Details Page
You see a session with a Blocked authentication status. This may be a case of stolen authentication credentials so you want to look into it. You open the details page for this session to take a closer look at exactly what went on in this session. You see that the login had triggered a block. Phillip, the user, was dynamically added to a high risk users group because of this rule. Directions: Part A: Drill in on the policy that caused the block to see what rules triggered. Part B: You also want to see if this user has any CSR cases related to this lockout. Search the CSR cases and determine if Phillip called in for a temporary allow.
To view session details:
-
In the Sessions Search page, view the Search Results table.
You noticed that for Phillip, one of his sessions shows:
-
a "High alert" in the Alerts column. Clicking the information icon, you see a velocity alert.
-
a "Blocked" status in the Authentication Status column.
-
-
Click the Session ID in the Search Results table to open the Session Details page.
In Session Details panel, the Authentication Status shows Blocked.
-
View the final outcomes of each checkpoint.
-
Expand the checkpoints.
-
View the post-authentication checkpoints.
-
Expand the post-authentication policies.
-
Click the policy of interest to show details about the policy.
-
View the rules that are triggered.
-
View the final outcomes of the rules.
There are two final outcomes: the user is blocked and been added to a high risk group.
-
-
Because you want to see if Phillip has any CSR cases related to this lockout, search the CSR cases and determine if he called in to have his challenge questions reset.
-
In the Navigation tree, double-click Cases. The Cases Search page is displayed.
-
In Case Type, select CSR.
-
Enter Phillip's user name into User Name field.
-
In Search Results table, look for Temporary Allow in the Last Action Type column.
-
Click the Case ID for the case that has Temporary Allow in the Last Action Type column.
-
In the Log subtab of the Case Details page, view notes.
The notes said he was traveling overseas when his wife asked him to look at their account online.
-
6.16.3 Use Case: Checking for Fraudulent Devices and Adding Them to a Group
Login with user who has an Investigator or Investigation Manager role.
Checking for Fraudulent Devices and Adding Them to a Group
-
Search by action and alert to see recent blocked sessions.
For example, search for sessions that have been blocked in the last two hours.
You should see blocked sessions and the user who was blocked because of a device.
For example, you see a user jsmith who was blocked because he was logging in using device 123 that had been blocked more than three times in the last 24 hours.
-
View user details and check the Device tab to view the different devices the user used.
For example, you compare the blocked device with other devices jsmith has used in the past. You open the user details for jsmith and view devices for the last six months. Only three devices are shown (123, 511 and 333).
-
Compare the blocked device with other devices used using fingerprint details to see the OS, Browser, and Locale to get a general idea about the device.
-
Check to see if the blocked device looks different than the successful ones.
For example, you open the fingerprint details for the blocked device 123 and for device 333 that had been used recently by jsmith successfully and it showed a high number of successful uses. From the user interface, you can see that the blocked device 123 was a Linux machine with Opera running in Russian locale among other fingerprint data points.
The device 333 is a Windows XP machine with IE running in English locale which seems to be the one the user has used most of the time recently.
You open the fingerprint details for device 511 also and check the fingerprint data. You see it also is Windows XP machine with IE running in English locale but jsmith has not used it in a while. This makes you think device 123 was used by someone impersonating jsmith.
-
Search sessions by Device ID to check if the device has a lot of blocked sessions and if there are a lot of different users.
For example, you search for all the sessions device 123 has been involved in to see what other users may have been victims. There were ten sessions all in the last two weeks and many of them were blocked. As well each session was for a different user.
-
Add the device to the blacklist group from the Sessions search tab.
-
Export the blocked session to Excel to use as reference to contact the real users who need to reset their password.
You export table results to Excel. The Excel sheet should contain all the session details.
6.16.4 Use Case: Exporting the Sessions from the Last One Week
You can export sessions to use as reference or further study and investigation.
To export sessions:
-
Log in to the OAAM Admin.
-
In the Sessions search page, specify one week using the date editor and click Search.
-
Select the sessions from the Search Results table.
-
From Actions menu, select Export to Excel.
-
Click Save File or Open with and click OK.
File shows Row, Session ID, Alerts, Organization ID, User name, Device ID, IP Address, Location, Authentication Status, Login Time, Pre-Authentication Score, Pre-Authentication Action, Post-Authentication Score, Post-Authentication Action, Client Type, User ID, and Internal Session ID.
6.16.5 Use Case: User Details, Fingerprint Details
Tom, a fraud investigator, opens the OAAM Administration Console and searches for sessions that contain high-level alerts in the last 24 hours. This search returns a number of sessions. He orders the results by the User Name column and notices "jsmith" had several sessions with the "device with implausible velocity alert". Because "jsmith" has completed registration, every session was challenged.
-
Tom opens the user details for jsmith by clicking the link in the Session page. He searches for IPs jsmith has used in the last six months. A large list of IPs is returned. It appears the jsmith has been logging in from a random location every login session.
-
Tom finds only two devices used by jsmith in the last six months in device page for jsmith.
-
Tom searches for all of jsmith's sessions in the last three months. He finds almost every session has the same device velocity alert. Tom then filters all the sessions to see how many KBA locks occurred. He finds only one.
-
Tom navigates to fingerprint details and finds that jsmith has logged in from the same browser and the same OS every time and has used the same locale also. Tom determines jsmith must be a normal user whose IP is being changed in some way. He adds jsmith to the group of "traveling users" and excludes this group from the rule that is triggering for him.
6.16.6 Use Case: Device and Location Details
Tom opens the OAAM Administration Console and searches for sessions that contain high-level alerts in the last 6 hours. This search returns 5 sessions.
-
Tom orders the results by the username and notices none of them are from the same user.
-
Tom then orders on IP and sees there are different IPs used in each session.
-
He then orders by the device column and sees there is one device with 2 sessions and the other devices have one session each.
-
Tom opens the device details for the device with 2 sessions. He views sessions from that device in the last month. He sees there were five sessions from this device in the last 24 hours each for a different user. The most recent session was blocked.
-
Tom opens the blocked session details to see why it was blocked. He can see that the device with maximum users in a short time frame rule triggered.
-
Tom drills in on the policy containing this rule and sees the policy and rules. The rule blocks when a device has had more than four users and from more than three cities in a 12-hour period. He goes back to the device details screen and sees that the locale is Finnish, which seems strange.
-
Tom opens another session screen and searches for sessions in the last three months using the Finnish locale. There are 23 sessions, all in the last week.
-
Ordering by location, it seems the sessions were all from unique places within Washington State. Ordering by devices however he can see there were ten devices used. Finally, ordering by username Tom could see every session was for a different user. Feeling that this was not ordinary activity Tom puts together a call list of the affected users to verify if any of the activity was valid or not.
-
After calling 5 users Tom sees that none of them were in the locations these sessions seemed to come from. He decides to add the Finnish locale to a watch group that causes users in that locale to be challenged with an OTP via SMS every login. He also calls the rest of the users to confirm these sessions did not belong to them.
-
Once sure, he also selects all the devices used and adds them to a black list group.
6.16.7 Use Case: IP Details and Adding to Group
George is a Big Bank user. An impersonator of George gets blocked because he was logging in from a blocked IP.
-
The investigator, Tom, wants to compare the IP with other IPs George has used in the past. He opens the fingerprint details for the blocked IP and for another IP George has used many times successfully.
-
From the user interface Tom can see that the blocked IP was a Firefox browser running in Chinese locale. The IP George seems to use most of the time is a Windows XP machine with IE running at an private locale. As a result Tom adds the IP to Restricted IPs group directly from the Sessions IP screen.
6.16.8 Use Case: Viewing the Sessions from a Range of IPs
To view sessions coming in from a range of IPs:
-
Log in to the OAAM Admin Console.
-
Double-click Sessions in the Navigation tree.
-
Enter the IP range in the IP range fields and click Search.
Sessions in the IP range are displayed in the Search Results table.
6.16.9 Use Case: Checking If a User Failed to Login From a Particular Device or IP
To search and view the different devices that logged in from the location get additional information like the number of times a device logged in from the location and the successful and unsuccessful login attempts from the location by each device:
-
From the results of a session search, click the country, state, city, or IP link.
The Location Details page for that country, state, city, or IP is displayed.
-
Click the Devices tab.
-
To see additional information such as the number of times a device was used to log in from the location, search by Device ID. The Login Successes column displays the number of times a device was used to log in.
-
To see the number of successful and unsuccessful login attempts from the location by each device, select Blocked and Success as the Authentication Status.
Login failures and successes are displayed for each device.
-
6.16.10 Use Case: Checking If Users Logging In from This IP Used Spanish Browsers
To search and view the fingerprints created for the location:
-
From the results of a session search, click the country, state, city, or IP link.
The Location Details page for that country, state, city, or IP is displayed.
-
Click the Fingerprint Data tab.
-
In the Search Results table, check to see if Spanish is listed as the Locale for the Fingerprint.
6.16.11 Use Case: Adding Devices Used for Fraud from a Location To a Risky Group
An investigator is viewing a table of devices used from a location and decides two of them were used for fraud. He can select them and add them to a "high risk devices" group to be used in future risk evaluations. He should not lose the context of what he was doing in the process.
-
Open the OAAM Admin Console.
-
Search for sessions.
-
Open location details page.
-
Search for devices used from this location.
-
Select two devices and add them to a high risk group.
6.16.12 Use Case: Adding Suspicious Device to High Risk Device Group
George is a user who gets blocked because he was logging in using a device that had been blocked more than three times in the last 24 hours. Jeff, an investigator wants to compare the blocked device with other devices this user has used in the past. He opens the fingerprint details for the blocked device and for another device the user has used many times successfully. From the user interface Jeff can see that the blocked device was a Linux machine with Opera running in Russian locale. The device the user seems to use most of the time is a Windows XP machine with IE running in English locale. As a result Jeff adds the blocked device to a high risk devices group, and adds the IPs used by the device to a high risk IPs group directly from the search screen.
-
Open the OAAM Admin Console.
-
Search for sessions.
-
Open 2 device details pages.
-
View the full list of fingerprint data for both devices.
-
Select device and add it to a high risk group.
-
Select IP and add it to a high risk group.
6.16.13 Use Case: Mark Devices and IPs as High Risk
An investigator is searching for sessions with high alerts in the last hour. Out of the 30 sessions he thinks two were fraud so he wants to mark the devices and IPs used as high risk.
-
Open the OAAM Admin Console.
-
Search for sessions with high alerts in the last hour.
-
Select the two sessions and click the add to group button.
A dialog appears asking what data types from these sessions to add.
-
Select devices and IPs.
Message appears which asks the user to select a device group and an IPs group.
-
Select and add the high risk devices and high risk IPs.
A confirmation appears with message that the devices were added and that one IP was added and the other was already in the high risk IPs group.
6.16.14 Use Case: Search for Suspicious Sessions and Add Devices to High Risk Group
Login with user who has a Fraud Investigator or Fraud Investigation Manager role.
Search for Suspicious Sessions and Add Devices to High Risk Group
Garry is an investigator searching sessions looking for suspicious situations not found by the currently configured rules. He filters for all sessions in the last month with block actions from Mexico because of a recent incident. He selects all other sessions and in a single operation adds all the devices to a high risk device group.
-
Open the OAAM Admin Console.
-
Search sessions.
-
Add to group from search page.
6.16.15 Use Case: Search Sessions by Alert Message
An investigator is searching for sessions with high alerts with a message containing "speed". The search returns 20 sessions containing high alerts with the following messages: "Excessive speed navigation" and "User air speed."
-
Open the OAAM Admin Console.
-
Search for sessions with high level alerts and messages containing "speed."
6.16.16 Use Case: Search Sessions by Geography
An investigator is searching for sessions with an ID number that starts with 40 from Los Angeles, CA, USA in the last two hours.
-
Open the OAAM Admin Console.
-
Search for sessions with an ID number starting with 40 from Los Angeles in the last two hours.
6.16.17 Use Case: Search by Comma Separated Values
Jeff wants to see what activity has occurred recently from a list of high risk IPs he pulled from a portal. To gauge the value of the IP data he decides to view the activity from those IPs in the last six weeks and determine if any of the activity was suspicious. Jeff starts by searching sessions that have used this comma separated list of IPs and viewing the sessions that come back.
-
Open the OAAM Admin Console.
-
Search for sessions by pasting a comma separated list of IPs into the search field and filtering to the last two weeks.
Only sessions from the IPs in the list are shown.
6.16.18 Use Case: Export Search Sessions Results to Excel
An investigator is searching for sessions in the last two hours. He selects five rows and exports them to Excel format document that contains all columns.
-
Open OAAM Admin Console.
-
Search for sessions.
-
Select five sessions.
-
Export them to Excel.
6.16.19 Use Case: Export Search Sessions Results - Export Page to Excel
An investigator is searching for sessions in the last 2 hours. He selects the column heading to select all rows and exports them to Excel format document that contains all columns.
-
Open the OAAM Admin Console.
-
Search for sessions.
-
Click the heading to select all sessions on that page.
-
Export the rows to Excel document.