| Oracle® Fusion Middleware Security and Administrator's Guide for Web Services 11g Release 1 (11.1.1.6) Part Number B32511-07 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware Security and Administrator's Guide for Web Services 11g Release 1 (11.1.1.6) Part Number B32511-07 |
|
|
PDF · Mobi · ePub |
This appendix provides the XML schema for reference when creating a WS-Policy file that contains Web service assertions. Sections include:
The following graphic describes the element hierarchy of the assertions in the WS-Policy file.
Figure D-1 Element Hierarchy of an Assertion
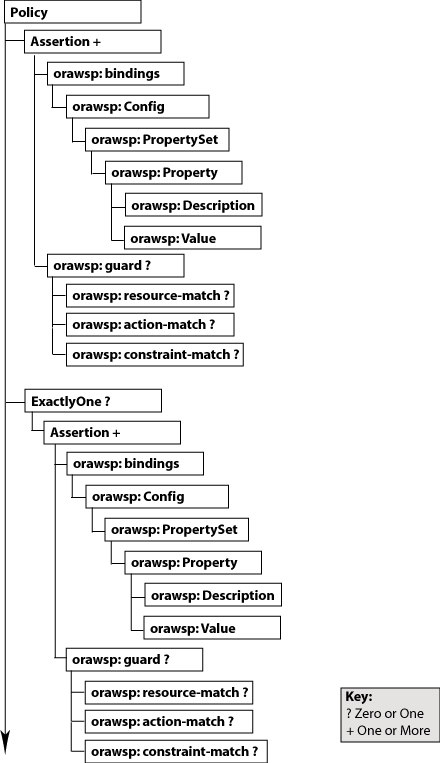
The following sections describe each element and their subelements in detail:
The following sections describe the elements in the assertion in more detail. The main elements are described up front. The subelements are described following the main elements and are organized in alphabetical order.
Groups nested policy assertions.
The following table summarizes the WS-Policy attributes, including the Oracle extensions.
Table D-1 Oracle Extensions to WS-Policy Attributes
| Attribute | Description |
|---|---|
|
Name |
Name of the policy. |
|
attachTo |
Policy subjects to which the policy can be attached. Valid values include:binding.client, binding.server, binding.any. |
|
category |
Category of the policy. Valid values include: security, mtom, wsrm, addressing, and management. |
|
description |
Description of the policy. |
|
displayName |
Name displayed in the user interface. |
|
localOptimization |
Flag that specifies whether local optimization is enabled. Oracle WSM supports a SOA local optimization feature for composite-to-composite invocations in which the reference of one composite specifies a Web service binding to a second composite. Valid values include:
|
|
status |
Status of the policy reference. Valid values include: enabled and disabled. |
|
smartDigest |
Smart Digest. |
|
oraSmartDigest |
Smart Digest. |
|
subjectCount |
Number of subjects to which the policy is attached currently. |
|
versionCreator |
Author of the current version. |
|
versionNumber |
Number of the current version. |
|
versionTime |
Time the current version was creatd. |
|
id |
Policy ID. |
<wsp:Policy xmlns:wsp="http://schemas.xmlsoap.org/ws/2004/09/policy" xmlns="http://schemas.xmlsoap.org/ws/2004/09/policy" xmlns:oralgp="http://schemas.oracle.com/ws/2006/01/loggingpolicy" xmlns:orasp="http://schemas.oracle.com/ws/2006/01/securitypolicy" xmlns:orawsp="http://schemas.oracle.com/ws/2006/01/policy" xmlns:wsu="http://docs.oasis-open.org/wss/2004/01/oasis-200401-wss-wssecurity-utility-1.0.xsd" Name="oracle/wss11_x509_token_with_message_protection_client_policy" orawsp:attachTo="binding.client" orawsp:category="security" orawsp:description="i18n:oracle.wsm.resources.policydescription.PolicyDescription Bundle_oracle/wss11_x509_token_with_message_protection_client_policy_PolyDescKey" orawsp:displayName="i18n:oracle.wsm.resources.policydescription.PolicyDescription Bundle_oracle/wss11_x509_token_with_message_protection_client_policy_PolyDispNameKey" orawsp:local-optimization="check-identity" orawsp:oraSmartDigest="935231872" orawsp:smartDigest="201244603" orawsp:status="enabled" orawsp:versionCreator="mdsInternal" orawsp:versionNumber="1" orawsp:versionTime="1238006529607" wsu:Id="wss11_x509_token_with_message_protection_client_policy"> ... </wsp:Policy>
Optional element that defines an OR group. For more information about OR groups, see "Defining Multiple Policy Alternatives (OR Groups)".
<wsp:ExactlyOne orawsp:name="Or"> <orasp:wss11-saml-with-certificates orawsp:Enforced="true" orawsp:Silent="false" orawsp:category="security/msg-protection, security/authentication" orawsp:name="WS-Security 1.1 Saml with certificates"> <orasp:saml-token orasp:confirmation-type="sender-vouches" orasp:is-encrypted="false" orasp:is-signed="true" orasp:version="1.1"/> <orasp:x509-token orasp:enc-key-ref-mech="thumbprint" orasp:is-encrypted="false" orasp:is-signed="true" orasp:sign-key-ref-mech="direct"/> <orasp:msg-security orasp:algorithm-suite="Basic128" orasp:confirm-signature="true" orasp:encrypt-signature="false" orasp:include-timestamp="true" orasp:sign-then-encrypt="true" orasp:use-derived-keys="false"> ... <orasp:wss11-username-with-certificates orawsp:Enforced="true" orawsp:Silent="false" orawsp:category="security/authentication, security/msg-protection" orawsp:name="WS-Security 1.1 username with certificates"> <orasp:username-token orasp:add-created="false" orasp:add-nonce="false" orasp:is-encrypted="true" orasp:is-signed="true" orasp:password-type="plaintext"/> <orasp:x509-token orasp:enc-key-ref-mech="thumbprint" orasp:is-encrypted="false" orasp:is-signed="true" orasp:sign-key-ref-mech="thumbprint"/> <orasp:msg-security orasp:algorithm-suite="Basic128" orasp:confirm-signature="true" orasp:encrypt-signature="false" orasp:include-timestamp="true" orasp:sign-then-encrypt="true" orasp:use-derived-keys="false"> ... </wsp:ExactlyOne>
Main element of the assertion. Valid assertion elements include:
The following table summarizes the attributes of the <orasp:Assertion> element.
Table D-3 Attributes of <orasp:Assertion> Element
| Attribute | Description |
|---|---|
|
Optional |
Flag that specifies whether the assertion is optional or required. |
|
Silent |
Flag that specifies whether the assertion is advertised. If set to true, the assertion is not advertised. |
|
Enforced |
Flag that specifies whether the assertion is currently enabled. Valid values are true or false. |
|
name |
Name of the assertion. |
|
description |
Description of the assertion. |
|
category |
Category to which the assertion applies. Valid values include: security/authentication, security/msg-protection, security/authorization, security/logging, mtom, wsrm, addressing, and management. |
The <oraswsp:bindings> element defines the bindings in the assertion. This element contains the following subelement:
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss11SamlWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
The <oraswsp:Config> element defines the configuration for the assertion. This element can contain the following subelement:
The following table summarizes the attributes of the <orawsp:Config> element.
Table D-4 Attributes of <orawsp:Config> Element
| Attribute | Description |
|---|---|
|
name |
Name of the configuration. |
|
type |
Category to which the configuration applies. |
|
configType |
Configuration type. Valid values include: declarative and programmatic.
|
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss11SamlWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
The <oraswsp:PropertySet> element groups nested properties. This element contains the following subelement:
The <oraswsp:Property> element defines a single property. The following summarize valid properties used by the predefined assertions.
The <orawsp:Property> element can contain the following subelements:
The following table summarizes the attributes of the <orawsp:Property> element.
Table D-6 Attributes of <orawsp:Property> Element
| Attribute | Description |
|---|---|
|
name |
Name of the property. See Table D-7 for a list of property values used by the predefined assertions. |
|
type |
Type of the property. For example, string. |
|
contentType |
Specifies whether the property is required and can be overridden. Valid values include:
For information about overriding policies, see "Attaching Client Policies Permitting Overrides". |
The following table summarizes the properties used by the predefined assertions.
Table D-7 Properties Used by the Predefined Assertions
| Property | Description |
|---|---|
|
action |
Action or Web service operation for which authorization checks are performed. This value can be a comma-separated list of values. This field accepts wildcards. For example, |
|
attesting.mapping.attribute |
The mapping attribute used to represent the attesting entity. Only the DN is currently supported. This attribute is applicable only to sender vouches and then only to message protection use cases. It is not applicable to SAML over SSL policies. |
|
BaseRetransmissionInterval |
Interval, in milliseconds, that the source endpoint waits after transmitting a message and before it retransmits the message. If the source endpoint does not receive an acknowledgement for a given message within the interval specified by this element, the source endpoint retransmits the message. The source endpoint can modify this retransmission interval at any point during the lifetime of the sequence of messages. This assertion does not alter the formulation of messages as transmitted, only the timing of their transmission. This value defaults to 3000. |
|
csf-key |
Credential Store Key that maps to a username and password in the Oracle Platform Security Services identity store. The default value is |
|
DeliveryAssurance |
Delivery assurance. Valid values include:
|
|
jdbc-connection-name |
JNDI reference to a JDBC data store. Valid when the StoreType is set to JDBC. This value defaults to jdbc/MessagesStore. |
|
InactivityTimeout |
Period of inactivity (in milliseconds) for a sequence of messages. A sequence of messages is defined as a set of messages, identified by a unique sequence number, for which a particular delivery assurance applies; typically a sequence originates from a single source endpoint. If, during the duration specified by this element, a destination endpoint has received no messages from the source endpoint, the destination endpoint may consider the sequence to have been terminated due to inactivity. The same applies to the source endpoint. This value defaults to 600000. |
|
keystore.enc.csf.key |
If you set this value you then can override keystore.enc.csf.key, as described in "Attaching Web Service Policies Permitting Overrides". |
|
keystore.recipient.alias |
Keystore alias associated with the peer certificate. The security run time uses this alias to extract the peer certificate from the configured keystore and to encrypt messages to the peer. Can be superseded by "Using Service Identity Certification Extension". |
|
on.behalf.of |
Override this property to indicate whether the request is on behalf of an another entity. The default value for this flag is false. |
|
permission-class |
Class used for the permission-based checking. For example, |
|
realm |
HTTP realm. This value defaults to owsm. |
|
resource |
Name of the resource for which authorization checks are performed. This field accepts wildcards. For example, if the namespace of the Web service is |
|
role |
SOAP role. This value defaults to ultimateReceiver. |
|
saml.assertion.filename |
File containing SAML assertions. This value defaults to temp. |
|
saml.audience.uri |
Represents the relying party, as a comma-separated URI. This field accepts wildcards. |
|
saml.issuer.name |
Name of the issuer of the SAML token. This value defaults to www.oracle.com. |
|
saml.trusted.issuers |
A comma-separated list of SAML token trusted issuers for an application that will override trusted issuers at domain level. |
|
service.principal.name |
Kerberos principal name that identifies the service. |
|
StoreName |
Name of the message store. This value defaults to oracle. |
|
StoreType |
Type of message store. Valid values include:
|
|
sts.auth.caller.principal.name |
Client's principal name as generated using the |
|
sts.auth.keytab.location |
Location of the client's keytab file. |
|
sts.auth.on.behalf.of.csf.key |
Use to configure "on behalf of" entity. If present, it will be given preference over Subject (if it exists). |
|
sts.auth.service.principal.name |
Principal name for the Web service that needs to be protected. It is of the format |
|
sts.auth.user.csf.key |
Use to configure username/password to authenticate to the STS. If |
|
sts.auth.x509.csf.key |
Use to configure X509 certificate for authenticating to the STS. If |
|
sts.keystore.recipient.alias |
The alias of the STS certificate you added to the keystore. The default alias name is sts-csf-key. |
|
subject.precedence |
Set subject.precedence to false to allow for the use of a client-specified username rather than the authenticated subject. If subject.precedence is true, the user name to create the SAML assertion is obtained only from the Subject. Similarly, if subject.precedence is false, the user name to create the SAML assertion is obtained only from the csf-key username property. |
|
user.attributes |
Specify the attributes to be included as a comma-separated list. For example, attrib1,attrib2. The attribute names you specify must exactly match valid attributes in the configured identity store. The Oracle WSM run time reads the values for these attributes from the configured identity store, and then includes the attributes and their values in the SAML assertion. |
|
user.roles.include |
SOAP roles to be included. This value defaults to false. |
The <orawsp:guard> element defines the resource, action, and constraint match values.
<orawsp:guard>
<orawsp:resource-match>
http://project11/CreditValidation
</orawsp:resource-match>
<orawsp:action-match>validate,amountAvailable</orawsp:action-match>
</orawsp:guard>
<orawsp:guard>
<orawsp:resource-match>*</orawsp:resource-match>
<orawsp:action-match>validate,amountAvailable</orawsp:action-match>
</orawsp:guard>
<orawsp:guard>
<orawsp:constraint-match>${!(messageContext.authenticationMethod =='SAML_SV'
|| messageContext.requestOrigin == 'internal')}
</orawsp:constraint-match>
</orawsp:guard>
The <orawsp:resource-match> element specifies the name of the resource for which authorization checks are performed. This field accepts wildcards.
For example, if the namespace of the Web service is http://project11 and the service name is CreditValidation, the resource name is http://project11/CreditValidation.
<orawsp:guard>
<orawsp:resource-match>
http://project11/CreditValidation
</orawsp:resource-match>
<orawsp:action-match>validate,amountAvailable</orawsp:action-match>
</orawsp:guard>
<orawsp:guard> <orawsp:resource-match>*</orawsp:resource-match> <orawsp:action-match>validate,amountAvailable</orawsp:action-match> </orawsp:guard>
The <orawsp:resource-match> element specifies the action or Web service operation for which authorization checks are performed. This value can be a comma-separated list of values. This field accepts wildcards.
<orawsp:guard>
<orawsp:resource-match>
http://project11/CreditValidation
</orawsp:resource-match>
<orawsp:action-match>validate,amountAvailable</orawsp:action-match>
</orawsp:guard>
<orawsp:guard> <orawsp:resource-match>*</orawsp:resource-match> <orawsp:action-match>validate,amountAvailable</orawsp:action-match> </orawsp:guard>
The <orawsp:constraint-match> element specifies the constraints against which authorization checks are performed. The value is an expression specified using the following two messageContext properties:
messageContext.authenticationMethod—Determines the authentication method used to authenticate the user. Valid value is SAML_SV.
messageContext.requestOrigin—Determines whether the request originated from an internal or external network. This property is valid only when using Oracle HTTP Server and the Oracle HTTP server administrator has added a custom VIRTUAL_HOST_TYPE header to the request.
The properties and their values are case sensitive. The constraint expression uses the following standard supported operators: ==, !=, &&, || and !.
Note:
This element is supported with the binding-authorization element only. For other authorization assertion elements, this field is reserved for future use.The <orasp:Logging> element defines the logging policy.
The <orasp:Logging> element contains the following subelements:
<oralgp:Logging orawsp:Enforced="false" orawsp:Silent="true"
orawsp:category="security/logging" orawsp:name="Log Message1">
<oralgp:msg-log>
<oralgp:request>all</oralgp:request>
<oralgp:response>all</oralgp:response>
<oralgp:fault>all</oralgp:fault>
</oralgp:msg-log>
<orawsp:bindings>
<orawsp:Config orawsp:name="added-from-em"/>
</orawsp:bindings>
</oralgp:Logging>
The <orasp:binding-authorization> element defines a simple role-based authorization for the request based on the authenticated subject at the SOAP binding level.
The <orasp:binding-authorization> element contains the following subelements:
It also contains one of the following subelements:
<orasp:binding-authorization orawsp:Enforced="true" orawsp:Silent="true"
orawsp:category="security/authorization"
orawsp:name="J2EE services Authorization">
<orasp:denyAll/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative" orawsp:name="AuthzConfig"/>
</orawsp:bindings>
<orawsp:guard/>
</orasp:binding-authorization>
The <orasp:binding-permission-authorization> element defines simple permission-based authorization for the request based on the authenticated subject at the SOAP binding level.
The <orasp:binding-permission-authorization> element contains the following subelements:
<orasp:binding-permission-authorization orawsp:Enforced="true"
orawsp:Silent="true" orawsp:category="security/authorization"
orawsp:name="J2EE Permission Based Authorization">
<orasp:check-permission/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="BindingPermissionAuthzConfig">
<orawsp:PropertySet orawsp:name="perms-authz-properties">
<orawsp:Property orawsp:contentType="optional" orawsp:name="resource"
orawsp:type="string">
<orawsp:DefaultValue>*</orawsp:DefaultValue>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional" orawsp:name="action"
orawsp:type="string">
<orawsp:DefaultValue>*</orawsp:DefaultValue>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional"
orawsp:name="permission-class" orawsp:type="string">
<orawsp:DefaultValue>oracle.wsm.security.WSFunctionPermission
</orawsp:DefaultValue>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
<orawsp:guard>
<orawsp:resource-match>*</orawsp:resource-match>
<orawsp:action-match>*</orawsp:action-match>
</orawsp:guard>
</orasp:binding-permission-authorization>
The <orasp:coreid-security> element uses the credentials in the WS-Security header's binary security token to authenticate users against the Oracle Access Manager identity store.
It contains the following subelements:
<orasp:coreid-security orawsp:Enforced="true" orawsp:Silent="true"
orawsp:category="security/authentication, security/authorization"
orawsp:name="OAM Security">
<orasp:coreid-token orasp:is-encrypted="false" orasp:is-signed="false"/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative" orawsp:name="CoreIdConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:coreid-security>
The <orasp:http-security> element uses the credentials in the HTTP header to authenticate users against the Oracle Platform Security Services identity store.
It contains the following subelements:
<orasp:http-security orawsp:Enforced="true" orawsp:Silent="true"
orawsp:category="security/authentication, security/msg-protection"
orawsp:name="Http over SSL Security">
<orasp:auth-header orasp:mechanism="basic"/>
<orasp:require-tls orasp:include-timestamp="true" orasp:mutual-auth="false"/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative" orawsp:name="HttpConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="realm"
orawsp:type="string">
<orawsp:Value>owsm</orawsp:Value>
</orawsp:Property>
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:http-security>
The <orasp:kerberos-security> element enforces in accordance with the WS-Security Kerberos Token Profile v1.1 standard.
It contains the following subelements:
<orasp:kerberos-security orawsp:Enforced="true" orawsp:Silent="false"
orawsp:category="security/authentication" orawsp:name="WSS Kerberos Token">
<orasp:kerberos-token orasp:is-encrypted="false" orasp:is-signed="false"
orasp:type="gss-apreq-v5"/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="KerberosSecurityConfig"/>
</orawsp:bindings>
</orasp:kerberos-security>
The <orasp:sca-component-authorization> element defines simple role-based authorization for the request based on the authenticated subject at the SOA component level.
The <orasp:sca-component-authorization> element contains the following subelement:
It also contains one of the following subelements:
<orasp:sca-component-authorization orawsp:Enforced="true" orawsp:Silent="true"
orawsp:category="security/authorization" orawsp:name="Fabric Component
Authorization">
<orasp:denyAll/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="FabricAuthzConfig"/>
</orawsp:bindings>
</orasp:sca-component-authorization>
The <orasp:sca-component-permission-authorization> element provides simple permission-based authorization for the request based on the authenticated subject at the SOA component level.
The <orasp:binding-permission-authorization> element contains the following subelements:
<orasp:sca-component-permission-authorization orawsp:Enforced="true"
orawsp:Silent="true" orawsp:category="security/authorization"
orawsp:name="Fabric Component Authorization">
<orasp:check-permission/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="FabricAuthzConfig">
<orawsp:PropertySet orawsp:name="perms-authz-properties">
<orawsp:Property orawsp:contentType="optional" orawsp:name="resource"
orawsp:type="string">
<orawsp:DefaultValue>*</orawsp:DefaultValue>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional" orawsp:name="action"
orawsp:type="string">
<orawsp:DefaultValue>*</orawsp:DefaultValue>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional"
orawsp:name="permission-class" orawsp:type="string">
<orawsp:DefaultValue>
oracle.wsm.security.WSFunctionPermission</orawsp:DefaultValue>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
<orawsp:guard>
<orawsp:resource-match>*</orawsp:resource-match>
<orawsp:action-match>*</orawsp:action-match>
</orawsp:guard>
</orasp:sca-component-permission-authorization>
The <orasp:sts-trust-config> element provides a mechanism to invoke the STS for token exchange.
It contains the following subelements:
The following table summarizes the attributes of the <orasp:sts-trust-config> element.
Table D-8 Attributes of <orasp:sts-trust-config> Element
| Attribute | Description |
|---|---|
|
wsdl-uri |
The actual endpoint URI of the WSDL. |
|
port-uri |
The actual endpoint URI of the STS port. For example. |
|
port-endpoint |
The endpoint of the STS Web service. For a WSDL 2.0 STS, the format is specified as For a WSDL 1.1 STS, the format is specified as |
|
policy-reference-uri |
The client policy URI that will be used by the client to communicate with the STS. The policy you choose depends on the authentication requirements of the STS, as identified in its WSDL. |
|
soap-version |
SOAP version. |
|
sts-keystore-recipient-alias |
The alias of the STS certificate you added to the keystore. The default alias name is |
<orasp:sts-trust-config xmlns:orasp="http://schemas.oracle.com/ws/2006/01/securitypolicy" xmlns:orawsp="http://schemas.oracle.com/ws/2006/01/policy" orasp:policy-reference-uri="oracle/wss10_username_token_with_message_protection_ client_policy" orasp:port-endpoint="target-namespace#wsdl.endpoint(service-name/port-name)" orasp:port-uri="http://host:port/sts-service" orasp:soap-version="12" orasp:sts-keystore-recipient-alias="sts-csf-key" orasp:wsdl-uri="http://host:port/sts?wsdl" orawsp:Enforced="true" orawsp:Silent="true" orawsp:category="security/sts-config" orawsp:name="STS Trust Configuration"> <orawsp:bindings> <orawsp:Config orawsp:configType="declarative" orawsp:name="StsTrustConfig"> <orawsp:PropertySet orawsp:name="standard-security-properties"> <orawsp:Property orawsp:contentType="constant" orawsp:name="role" orawsp:type="string"> <orawsp:Value>ultimateReceiver</orawsp:Value> </orawsp:Property> </orawsp:PropertySet> </orawsp:Config> </orawsp:bindings> </orasp:sts-trust-config>
The <orasp:wss10-anonymous-with-certificates> element provides message protection (integrity and confidentiality) for outbound SOAP requests in accordance with the WS-Security 1.0 standard.
It contains the following subelements:
<orasp:wss10-anonymous-with-certificates orawsp:Enforced="true"
orawsp:Silent="false" orawsp:category="security/msg-protection"
orawsp:name="WS-Security 1.0 Anonymous with certificates">
<orasp:x509-token orasp:enc-key-ref-mech="direct" orasp:is-encrypted="false"
orasp:is-signed="true" orasp:rcpt-enc-key-ref-mech="direct"
orasp:rcpt-sign-key-ref-mech="direct" orasp:sign-key-ref-mech="direct"/>
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:encrypt-signature="false" orasp:include-timestamp="true"
orasp:sign-then-encrypt="true">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss10AnonWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss10-anonymous-with-certificates>
The <orasp:wss10-mutual-auth-with-certificates> element enforces message-level protection and certificate-based authentication for inbound SOAP requests in accordance with the WS-Security 1.1 standard.
It contains the following subelements:
<orasp:wss10-mutual-auth-with-certificates orawsp:Enforced="true"
orawsp:Silent="false" orawsp:category="security/authentication,
security/msg-protection" orawsp:name="WS-Security 1.0 Mutual Auth with
certificates">
<orasp:x509-token orasp:enc-key-ref-mech="direct" orasp:is-encrypted="false"
orasp:is-signed="true" orasp:rcpt-enc-key-ref-mech="direct"
orasp:rcpt-sign-key-ref-mech="direct" orasp:sign-key-ref-mech="direct"/>
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:encrypt-signature="false" orasp:include-timestamp="true"
orasp:sign-then-encrypt="true">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss10AnonWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss10-mutual-auth-with-certificates>
The <orasp:wss1-saml-hok-with-certificates> element provides message protection (integrity and confidentiality) and SAML holder of key based authentication for outbound SOAP messages in accordance with the WS-Security 1.0 standard.
It contains the following subelements:
<orasp:wss10-saml-hok-with-certificates orawsp:Enforced="true"
orawsp:Silent="false" orawsp:category="security/authentication,
security/msg-protection" orawsp:name="WS-Security 1.0 SAML Holder Of Key
with certificates">
<orasp:saml-token orasp:confirmation-type="holder-of-key"
orasp:is-encrypted="false" orasp:is-signed="true" orasp:version="1.1"/>
<orasp:x509-token orasp:enc-key-ref-mech="direct"
orasp:is-encrypted="false" orasp:is-signed="true"
orasp:rcpt-enc-key-ref-mech="direct" orasp:rcpt-sign-key-ref-mech="direct"
orasp:sign-key-ref-mech="ski"/>
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:encrypt-signature="false" orasp:include-timestamp="true"
orasp:sign-then-encrypt="true">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss10SamlHOKWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:name="keystore.recipient.alias"
orawsp:type="string">
<orawsp:Value>orakey</orawsp:Value>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional"
orawsp:name="saml.issuer.name" orawsp:type="string">
<orawsp:Value>www.oracle.com</orawsp:Value>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional"
orawsp:name="user.roles.include" orawsp:type="string">
<orawsp:Value>false</orawsp:Value>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional"
orawsp:name="saml.assertion.filename" orawsp:type="string">
<orawsp:Value>temp</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss10-saml-hok-with-certificates>
The <orasp:wss10-saml-token> element authenticates users using credentials provided in SAML tokens in the WS-Security SOAP header.
It contains the following subelements:
<orasp:wss10-saml-token orawsp:Enforced="true" orawsp:Silent="false"
orawsp:category="security/authentication" orawsp:name="WSSecurity SAML Token">
<orasp:saml-token orasp:confirmation-type="sender-vouches"
orasp:is-encrypted="false" orasp:is-signed="false" orasp:version="1.1"/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="WssSamlTokenConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss10-saml-token>
The <orasp:wss10-saml-with-certificates> element enforces message protection (integrity and confidentiality) and SAML-based authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
It contains the following subelements:
<orasp:wss10-saml-with-certificates orawsp:Enforced="true"
orawsp:Silent="false" orawsp:category="security/authentication,
security/msg-protection" orawsp:name="WS-Security 1.0 SAML with certificates">
<orasp:saml-token orasp:confirmation-type="sender-vouches"
orasp:is-encrypted="false" orasp:is-signed="true" orasp:version="1.1"/>
<orasp:x509-token orasp:enc-key-ref-mech="direct" orasp:is-encrypted="false"
orasp:is-signed="true" orasp:rcpt-enc-key-ref-mech="direct"
orasp:rcpt-sign-key-ref-mech="direct" orasp:sign-key-ref-mech="direct"/>
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:encrypt-signature="false" orasp:include-timestamp="true"
orasp:sign-then-encrypt="true">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss10SamlWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss10-saml-with-certificates>
The <orasp:wss10-username-with-certificates> element enforces message protection (integrity and confidentiality) and authentication for inbound SOAP requests in accordance with the WS-Security 1.0 standard.
It contains the following subelements:
<orasp:wss10-username-with-certificates orawsp:Enforced="true"
orawsp:Silent="false"
orawsp:category="security/authentication, security/msg-protection"
orawsp:name="WS-Security 1.0 username with certificates">
<orasp:username-token orasp:add-created="false" orasp:add-nonce="false"
orasp:is-encrypted="true" orasp:is-signed="true"
orasp:password-type="plaintext"/>
<orasp:x509-token orasp:enc-key-ref-mech="direct" orasp:is-encrypted="false"
orasp:is-signed="true" orasp:rcpt-enc-key-ref-mech="direct"
orasp:rcpt-sign-key-ref-mech="direct" orasp:sign-key-ref-mech="direct"/>
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:encrypt-signature="false" orasp:include-timestamp="true"
orasp:sign-then-encrypt="true">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss10UsernameWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss10-username-with-certificates>
The <orasp:wss11-anonymous-with-certificates> element provides message protection (integrity and confidentiality) for outbound SOAP requests in accordance with the WS-Security 1.1 standard.
It contains the following subelements:
<orasp:wss11-anonymous-with-certificates orawsp:Enforced="true"
orawsp:Silent="false" orawsp:category="security/msg-protection"
orawsp:name="WS-Security 1.0 Anonymous with certificates">
<orasp:x509-token orasp:enc-key-ref-mech="direct" orasp:is-encrypted="false"
orasp:is-signed="true" orasp:rcpt-enc-key-ref-mech="direct"
orasp:rcpt-sign-key-ref-mech="direct" orasp:sign-key-ref-mech="direct"/>
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:encrypt-signature="false" orasp:include-timestamp="true"
orasp:sign-then-encrypt="true">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss11AnonWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss11-anonymous-with-certificates>
The <orasp:wss11-mutual-auth-with-certificates> element enforces message-level protection and certificate-based authentication for inbound SOAP requests in accordance with the WS-Security 1.1 standard.
It contains the following subelements:
<orasp:wss11-mutual-auth-with-certificates orawsp:Enforced="true"
orawsp:Silent="false" orawsp:category="security/authentication,
security/msg-protection"
orawsp:name="WS-Security 1.1 Mutual Auth with certificates">
<orasp:x509-token orasp:enc-key-ref-mech="thumbprint"
orasp:is-encrypted="false" orasp:is-signed="true"
orasp:sign-key-ref-mech="direct"/>
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:confirm-signature="false" orasp:encrypt-signature="false"
orasp:include-timestamp="true" orasp:sign-then-encrypt="true"
orasp:use-derived-keys="false">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss10AnonWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:name="keystore.recipient.alias"
orawsp:type="string">
<orawsp:Value>orakey</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss11-mutual-auth-with-certificates>
The <orasp:wss11-saml-with-certificates> element enforces message protection (integrity and confidentiality) and SAML-based authentication for inbound SOAP requests in accordance with the WS-Security 1.1 standard.
It contains the following subelements:
<orasp:wss11-saml-with-certificates orawsp:Enforced="true"
orawsp:Silent="false" orawsp:category="security/authentication,
security/msg-protection" orawsp:name="WS-Security 1.1 SAML with certificates">
<orasp:saml-token orasp:confirmation-type="sender-vouches"
orasp:is-encrypted="false" orasp:is-signed="true" orasp:version="1.1"/>
<orasp:x509-token orasp:enc-key-ref-mech="direct" orasp:is-encrypted="false"
orasp:is-signed="true" orasp:rcpt-enc-key-ref-mech="direct"
orasp:rcpt-sign-key-ref-mech="direct" orasp:sign-key-ref-mech="direct"/>
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:encrypt-signature="false" orasp:include-timestamp="true"
orasp:sign-then-encrypt="true">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss11SamlWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss11-saml-with-certificates>
The <orasp:wss11-sts-issued-token-with-certificates> element enforces insertion of an assertion issued by a trusted STS. Messages are protected using proof key material provided by the STS, the client, or both.
It contains the following subelements:
The following table summarizes the attributes of the <orasp:wss11-sts-issued-token-with-certificates> element.
Table D-9 Attributes of <orasp:wss11-sts-issued-token-with-certificates> Element
| Attribute | Description |
|---|---|
|
trust-version |
WS-Trust version. |
|
require-client-entropy |
If a symmetric proof key is required by the Web service's security policy, this flag specifies whether the requestor can pass some key material (entropy) that can be included in the calculation of the proof key. The Web service policy can indicate whether client entropy, STS entropy, or both are required. |
|
require-server-entropy |
If a symmetric proof key is required by the Web service's security policy, this flag specifies whether the requestor can pass some key material (entropy) that can be included in the calculation of the proof key. The Web service policy can indicate whether client entropy, STS entropy, or both are required. |
|
require-applies-to |
Optional element in the RST. Flag that specifies whether Oracle WSM sends the endpoint address of the Web service for which the token is being requested. The default behavior is to always send the appliesTo element in the message from the client to the STS. |
<orasp:wss11-sts-issued-token-with-certificates xmlns:orasp="http://schemas.oracle.com/ws/2006/01/securitypolicy" xmlns:orawsp="http://schemas.oracle.com/ws/2006/01/policy" orasp:require-applies-to="true" orasp:require-client-entropy="true" orasp:require-server-entropy="true" orasp:trust-version="13" orawsp:Enforced="true" orawsp:Silent="false" orawsp:category="security/authentication, security/msg-protection" orawsp:name="WS-Security 1.1, issued token"> <orasp:issued-token orasp:require-external-reference="true" orasp:require-internal-reference="true" orasp:use-derived-keys="false"> <orasp:request-security-token-template orasp:algorithm-suite="Basic128" orasp:key-type="Symmetric" orasp:token-type="SAML11"/> </orasp:issued-token> <orasp:x509-token orasp:enc-key-ref-mech="thumbprint" orasp:is-encrypted="false" orasp:is-signed="true" orasp:sign-key-ref-mech="thumbprint"/> <orasp:msg-security orasp:algorithm-suite="Basic128" orasp:confirm-signature="true" orasp:encrypt-signature="false" orasp:include-timestamp="true" orasp:sign-then-encrypt="true" orasp:use-derived-keys="false"> <orasp:request> <orasp:signed-parts> <orasp:body/> <orasp:header orasp:namespace="http://www.w3.org/2005/08/addressing"/> <orasp:header orasp:namespace="http://schemas.xmlsoap.org/ws/2004/08/addressing"/> <orasp:header orasp:name="fmw-context" orasp:namespace="http://xmlns.oracle.com/fmw/context/1.0"/> </orasp:signed-parts> <orasp:encrypted-parts> <orasp:body/> <orasp:header orasp:name="fmw-context" orasp:namespace="http://xmlns.oracle.com/fmw/context/1.0"/> </orasp:encrypted-parts> </orasp:request> <orasp:response> <orasp:signed-parts> <orasp:body/> </orasp:signed-parts> <orasp:encrypted-parts> <orasp:body/> </orasp:encrypted-parts> </orasp:response> <orasp:fault/> </orasp:msg-security> <orawsp:bindings> <orawsp:Config orawsp:configType="declarative" orawsp:name="Wss11StsIssuedTokenWithCertsConfig"> <orawsp:PropertySet orawsp:name="standard-security-properties"> <orawsp:Property orawsp:contentType="optional" orawsp:name="sts.auth.user.csf.key" orawsp:type="string"> <orawsp:Value/> </orawsp:Property> <orawsp:Property orawsp:contentType="optional" orawsp:name="sts.auth.x509.csf.key" orawsp:type="string"> <orawsp:Value>enc-csf-key</orawsp:Value> </orawsp:Property> <orawsp:Property orawsp:name="on.behalf.of" orawsp:type="boolean"> <orawsp:Value>false</orawsp:Value> </orawsp:Property> <orawsp:Property orawsp:contentType="optional" orawsp:name="sts.auth.on.behalf.of.csf.key" orawsp:type="string"> <orawsp:Value/> </orawsp:Property> <orawsp:Property orawsp:name="keystore.recipient.alias" orawsp:type="string"> <orawsp:Value>orakey</orawsp:Value> </orawsp:Property> <orawsp:Property orawsp:contentType="optional" orawsp:name="keystore.enc.csf.key" orawsp:type="string"> <orawsp:Value/> </orawsp:Property> <orawsp:Property orawsp:contentType="optional" orawsp:name="sts.auth.service.principal.name" orawsp:type="string"> <orawsp:Value>HOST/localhost@EXAMPLE.COM</orawsp:Value> </orawsp:Property> <orawsp:Property orawsp:contentType="optional" orawsp:name="sts.auth.keytab.location" orawsp:type="string"> <orawsp:Value/> </orawsp:Property> <orawsp:Property orawsp:contentType="optional" orawsp:name="sts.auth.caller.principal.name" orawsp:type="string"> <orawsp:Value/> </orawsp:Property> </orawsp:PropertySet> </orawsp:Config> </orawsp:bindings> </orasp:wss11-sts-issued-token-with-certificates>
The <orasp:wss11-username-with-certificates> element enforces message protection (integrity and confidentiality) and authentication for inbound SOAP requests in accordance with the WS-Security 1.1 standard.
It contains the following subelements:
<orasp:wss11-username-with-certificates orawsp:Enforced="true"
orawsp:Silent="false"
orawsp:category="security/authentication, security/msg-protection"
orawsp:name="WS-Security 1.1 username with certificates">
<orasp:username-token orasp:add-created="false" orasp:add-nonce="false"
orasp:is-encrypted="true" orasp:is-signed="true"
orasp:password-type="plaintext"/>
<orasp:x509-token orasp:enc-key-ref-mech="direct" orasp:is-encrypted="false"
orasp:is-signed="true" orasp:rcpt-enc-key-ref-mech="direct"
orasp:rcpt-sign-key-ref-mech="direct" orasp:sign-key-ref-mech="direct"/>
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:encrypt-signature="false" orasp:include-timestamp="true"
orasp:sign-then-encrypt="true">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="Wss11UsernameWithCertsConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss11-username-with-certificates>
The <orasp:wss-saml-token-bearer-over-ssl> element authenticates users using credentials provided in SAML tokens with confirmation method 'Bearer' in the WS-Security SOAP header.
It contains the following subelements:
<orasp:wss-saml-token-bearer-over-ssl orawsp:Enforced="true"
orawsp:Silent="false"
orawsp:category="security/authentication, security/msg-protection"
orawsp:name="WSSecurity Saml Token With Confirmation method Bearer Over SSL ">
<orasp:saml-token orasp:confirmation-type="bearer" orasp:is-encrypted="false"
orasp:is-signed="false" orasp:version="1.1"/>
<orasp:require-tls orasp:include-timestamp="true" orasp:mutual-auth="false"/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="WssSamlTokenBearerOverSSLConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="optional"
orawsp:name="saml.issuer.name" orawsp:type="string">
<orawsp:Value>www.oracle.com</orawsp:Value>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional"
orawsp:name="user.roles.include" orawsp:type="string">
<orawsp:Value>false</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss-saml-token-bearer-over-ssl>
The <orasp:wss-saml-token-over-ssl> element enforces the authentication of credentials provided via a SAML token within WS-Security SOAP header using the sender-vouches confirmation type.
It contains the following subelements:
<orasp:wss-saml-token-over-ssl orawsp:Enforced="true" orawsp:Silent="false"
orawsp:category="security/authentication, security/msg-protection"
orawsp:name="WSSecurity SAML Token Over SSL">
<orasp:saml-token orasp:confirmation-type="sender-vouches"
orasp:is-encrypted="false" orasp:is-signed="true" orasp:version="1.1"/>
<orasp:require-tls orasp:include-timestamp="true" orasp:mutual-auth="true"/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="WssSamlTokenOverSSLConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="optional"
orawsp:name="saml.issuer.name" orawsp:type="string">
<orawsp:Value>www.oracle.com</orawsp:Value>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional"
orawsp:name="user.roles.include" orawsp:type="string">
<orawsp:Value>false</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss-saml-token-over-ssl>
The <orasp:wss-sts-issued-token-over-ssl> element enforces authentication of a SAML assertion issued by a trusted STS. Messages are protected using SSL
It contains the following subelements:
The following table summarizes the attributes of the <orasp:wss-sts-issued-token-over-ssl> element.
Table D-10 Attributes of <orasp:wss-sts-issued-token-over-ssl> Element
| Attribute | Description |
|---|---|
|
trust-version |
WS-Trust version. |
|
require-client-entropy |
If a symmetric proof key is required by the Web service's security policy, this flag specifies whether the requestor can pass some key material (entropy) that can be included in the calculation of the proof key. The Web service policy can indicate whether client entropy, STS entropy, or both are required. |
|
require-server-entropy |
If a symmetric proof key is required by the Web service's security policy, this flag specifies whether the requestor can pass some key material (entropy) that can be included in the calculation of the proof key. The Web service policy can indicate whether client entropy, STS entropy, or both are required. |
|
require-applies-to |
Optional element in the RST. Flag that specifies whether Oracle WSM sends the endpoint address of the Web service for which the token is being requested. The default behavior is to always send the appliesTo element in the message from the client to the STS. |
<orasp:wss-sts-issued-token-over-ssl xmlns:orasp="http://schemas.oracle.com/ws/2006/01/securitypolicy" xmlns:orawsp="http://schemas.oracle.com/ws/2006/01/policy" orasp:require-applies-to="true" orasp:require-client-entropy="true" orasp:require-server-entropy="true" orasp:trust-version="13" orawsp:Enforced="true" orawsp:Silent="false" orawsp:category="security/authentication, security/msg-protection" orawsp:name="WS-Security 1.1, issued token over ssl"> <orasp:issued-token orasp:require-external-reference="true" orasp:require-internal-reference="true" orasp:use-derived-keys="false"> <orasp:request-security-token-template orasp:key-type="Bearer" orasp:token-type="SAML11"/> </orasp:issued-token> <orasp:require-tls orasp:include-timestamp="true" orasp:mutual-auth="false"/> <orawsp:bindings> <orawsp:Config orawsp:configType="declarative" orawsp:name="WssStsIssuedTokenOverSSLConfig"> <orawsp:PropertySet orawsp:name="standard-security-properties"> <orawsp:Property orawsp:contentType="constant" orawsp:name="role" orawsp:type="string"> <orawsp:Value>ultimateReceiver</orawsp:Value> </orawsp:Property> </orawsp:PropertySet> </orawsp:Config> </orawsp:bindings> </orasp:wss-sts-issued-token-over-ssl>
The <orasp:wss-username-token> element enforces authentication with username and password credentials in the WS-Security UsernameToken SOAP header.
It contains the following subelements:
<orasp:wss-username-token orawsp:Enforced="true" orawsp:Silent="false"
orawsp:category="security/authentication"
orawsp:name="WSSecurity UserName Token">
<orasp:username-token orasp:add-created="false" orasp:add-nonce="false"
orasp:is-encrypted="true" orasp:is-signed="true"
orasp:password-type="plaintext"/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="WssUsernameTokenConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss-username-token>
The <orasp:wss-username-token-over-ssl> element uses the credentials in the UsernameToken WS-Security SOAP header to authenticate users against the Oracle Platform Security Services configured identity store.
It contains the following subelements:
<orasp:wss-username-token-over-ssl orawsp:Enforced="true" orawsp:Silent="false"
orawsp:category="security/authentication, security/msg-protection"
orawsp:name="WSSecurity UserName Token Over SSL">
<orasp:username-token orasp:add-created="true" orasp:add-nonce="true"
orasp:is-encrypted="true" orasp:is-signed="true"
orasp:password-type="plaintext"/>
<orasp:require-tls orasp:include-timestamp="true" orasp:mutual-auth="false"/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative"
orawsp:name="WssUsernameTokenOverSSLConfig">
<orawsp:PropertySet orawsp:name="standard-security-properties">
<orawsp:Property orawsp:contentType="constant" orawsp:name="role"
orawsp:type="string">
<orawsp:Value>ultimateReceiver</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</orasp:wss-username-token-over-ssl>
The <rm:RMAssertion> element provides support for version 1.0 and version 1.1 of the Web Services Reliable Messaging protocol. The version supported depends on the XML schema namespace value used:
WS-ReliableMessaging 1.1: http://docs.oasis-open.org/ws-rx/wsrmp/200702
WS-ReliableMessaging 1.0: http://schemas.xmlsoap.org/ws/2005/02/rm/policy
This policy can be attached to any SOAP-based client or endpoint. Full support for this feature may require additional programming.
The <rm:RMAssertion> element contains the following subelement:
<rm:RMAssertion xmlns:rm="http://schemas.xmlsoap.org/ws/2005/02/rm/policy"
orawsp:Enforced="true" orawsp:Silent="false" orawsp:category="wsrm"
orawsp:description="i18n:oracle.wsm.resources.policydescription.PolicyDescriptionBundle_oracle/wsrm10_policy_RMAssertion_AssertionDescKey"
orawsp:name="RM 1.0">
<wsp:Policy/>
<orawsp:bindings>
<orawsp:Config orawsp:name="RMConfig">
<orawsp:PropertySet orawsp:name="standard-wsrm-properties">
<orawsp:Property orawsp:name="DeliveryAssurance" orawsp:type="string">
<orawsp:Description>Delivery Assurance. Possible values
(case-insensitive) are InOrder, AtLeastOnce, AtLeastOnceInOrder,
ExactlyOnce, ExactlyOnceInOrder, AtMostOnce,
AtMostOnceInOrder.</orawsp:Description>
<orawsp:Value>inorder</orawsp:Value>
<orawsp:DefaultValue>inorder</orawsp:DefaultValue>
</orawsp:Property>
<orawsp:Property orawsp:name="StoreType" orawsp:type="string">
<orawsp:Description>The type of message store used. Possible values
(case-insensitive) areInMemory, JDBC.</orawsp:Description>
<orawsp:Value>inmemory</orawsp:Value>
<orawsp:DefaultValue>inmemory</orawsp:DefaultValue>
</orawsp:Property>
<orawsp:Property orawsp:name="StoreName" orawsp:type="string">
<orawsp:Description>The name of the message store.
</orawsp:Description>
<orawsp:Value>oracle</orawsp:Value>
</orawsp:Property>
<orawsp:Property orawsp:contentType="optional"
orawsp:name="jdbc-connection-name" orawsp:type="string">
<orawsp:Description>The JNDI reference to a JDBC data source, when
the store type is JDBC.</orawsp:Description>
<orawsp:Value>jdbc/MessagesStore</orawsp:Value>
</orawsp:Property>
<orawsp:Property orawsp:name="InactivityTimeout" orawsp:type="int">
<orawsp:Description>The inactivity timeout duration, specified in
milliseconds.</orawsp:Description>
<orawsp:Value>600000</orawsp:Value>
</orawsp:Property>
<orawsp:Property orawsp:name="BaseRetransmissionInterval"
orawsp:type="int">
<orawsp:Description>The base retransmission interval, specified in
milliseconds.</orawsp:Description>
<orawsp:Value>3000</orawsp:Value>
</orawsp:Property>
</orawsp:PropertySet>
</orawsp:Config>
</orawsp:bindings>
</rm:RMAssertion>
The <wsaw:UsingAddressing> element causes the platform to check inbound messages for the presence of WS-Addressing headers conforming to the W3C 2005 Final WS-Addressing Policy standard. In addition, it causes the platform to include a WS-Addressing header in outbound SOAP messages.
The <wsaw:UsingAddressing> element contains the following subelement:
The <wsoma:OptimizedMimeSerialization> element rejects inbound messages that are not in MTOM format and verifies that outbound messages are in MTOM format. MTOM refers to specifications http://www.w3.org/TR/2005/REC-soap12-mtom-20050125 and http://www.w3.org/Submission/2006/SUBM-soap11mtom10-20060405 for SOAP 1.2 and SOAP 1.1 bindings, respectively.
The <wsoma:OptimizedMimeSerialization> element contains the following subelement:
<wsoma:OptimizedMimeSerialization
xmlns:wsoma=
"http://schemas.xmlsoap.org/ws/2004/09/policy/optimizedmimeserialization"
orawsp:Enforced="true" orawsp:Silent="false" orawsp:category="mtom"
orawsp:name="MTOM">
<orawsp:bindings>
<orawsp:Config orawsp:name="added-from-em"/>
</orawsp:bindings>
</wsoma:OptimizedMimeSerialization>
The <oralgp:fault> element configures logging for the fault message. Valid values include:
all—Log the entire SOAP message.
header—Log SOAP header information only.
soap_body—Log SOAP body information only.
soap_envelope—Log SOAP envelope information only.
The <oralgp:request> element configures logging for the request message. Valid values include:
all—Log the entire SOAP message.
header—Log SOAP header information only.
soap_body—Log SOAP body information only.
soap_envelope—Log SOAP envelope information only.
The <oralgp:response> element configures logging for the response message. Valid values include:
all—Log the entire SOAP message.
header—Log SOAP header information only.
soap_body—Log SOAP body information only.
soap_envelope—Log SOAP envelope information only.
The <oralgp:msg-log> element configures logging for the request, response, and fault messages. The <oralgp:msg-log> element contains the following subelements:
The <orasp:attachment> element defines the attachment information.
The <orasp:auth-header> element specifies the name of the authentication header.
The following table summarizes the attribute of the <orasp:auth-header> element.
Table D-12 Attributes of <orasp:auth-header> Element
| Attribute | Description |
|---|---|
|
mechanism |
Authentication mechanism. Valid values include:
|
The <orasp:body> element defines the message body elements that are signed and encrypted. To include the entire body, specify the body element as follows: <orasp:body/>.
The <orasp:check-permission> element specifies that permissions are to be checked.
The <orasp:coreid-token> element defines the OAM token.
The <orasp:denyAll> element denies all users with any roles.
<orasp:binding-authorization orawsp:Enforced="true" orawsp:Silent="true"
orawsp:category="security/authorization"
orawsp:name="J2EE services Authorization">
<orasp:denyAll/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative" orawsp:name="AuthzConfig"/>
</orawsp:bindings>
<orawsp:guard/>
</orasp:binding-authorization>
The <orasp:element> element defines a header or body element that is signed or encrypted.
The <orassp:encrypted-elements> element defines the message body elements that are signed. This element is valid if <orasp:encrypted-parts> is not set to <orasp:body/>
The <orassp:encrypted-parts> element contains the following subelement:
The <orasp:encrypted-parts> element defines the message parts that are encrypted.
The <orasp:encrypted-parts> element contains one or more of the following subelements:
The <orasp:fault> element defines the message body elements that are signed and encrypted in the fault message. The <orasp:fault> element contains the following subelements:
The <orasp:header> element defines a header element.
The following table summarizes the attributes of the <orasp:header> element.
Table D-15 Attributes of <orasp:header> Element
| Attribute | Description |
|---|---|
|
name |
Name of the header element. The default header elements in the predefined namespace include: To, From, FaultTo, ReplyTo, MessageID, RelatesTo, and Action. |
|
namespace |
Namespace. The predefined namespace is as follows: http://www.w3.org/2005/08/addressing. |
The <orasp:issued-token> element enforces token characteristics.
The following table summarizes the attributes of the <orasp:issued-token> element.
Table D-16 Attributes of <orasp:issued-token> Element
| Attribute | Description |
|---|---|
|
use-derived-keys |
Flag that specifies whether derived keys are required. Possible values are True and False. |
|
require-internal-reference |
Flag that specifies whether internal reference to the token is required. Possible values are True and False. |
|
require-external-reference |
Flag that specifies whether external reference to the token is required. Possible values are True and False. |
The <orasp:kerberos-token> element defines the kerberos token.
The following table summarizes the attributes of the <orasp:kerberos-token> element.
Table D-17 Attributes of <orasp:kerberos-token> Element
| Attribute | Description |
|---|---|
|
is-encrypted |
Flag that specifies whether the assertion is encrypted. Valid values include true or false. |
|
is-signed |
Flag that specifies whether the assertion is signed. Valid values include true or false. |
|
type |
Type of Kerberos token. The only valid value is gss-apreq-v5 (Kerberos Version 5 GSS-API). |
The <orassp:msg-security> element defines message security for the policy. You define the body elements that are signed and encrypted for the request, response, and fault.
The <orasp:msg-security> element contains the following subelements:
The following table summarizes the attributes of the <orasp:msg-security> element.
Table D-18 Attributes of <orasp:msg-security> Element
| Attribute | Description |
|---|---|
|
algorithm-suite |
Defines the algorithm suite that is used for message protection. For example, Basic128. For more information, see "Supported Algorithm Suites". |
|
confirm-signature |
Flag that specifies whether to send a signature confirmation back to the client. Valid values inlcude true or false. |
|
encrypt-signature |
Flag that specifies whether to send a encryption confirmation back to the client. Valid values inlcude true or false. |
|
include-timestamp |
Flag that specifies whether to include a timestamp. A timestamp can be used to prevent replay attacks by identifying an expiration time after which the message is no longer valid. |
|
sign-then-encyrpt |
Flag that specifies whether to sign the message before encrypting the message. |
|
use-derived-keys |
Flag that specifies whether to use derived keys. |
<orasp:msg-security orasp:algorithm-suite="Basic128"
orasp:confirm-signature="false" orasp:encrypt-signature="false"
orasp:include-timestamp="true" orasp:sign-then-encrypt="true"
orasp:use-derived-keys="false">
<orasp:request>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:request>
<orasp:response>
<orasp:signed-parts>
<orasp:body/>
</orasp:signed-parts>
<orasp:encrypted-parts>
<orasp:body/>
</orasp:encrypted-parts>
</orasp:response>
<orasp:fault/>
</orasp:msg-security>
The <orasp:permitAll> element permits all users with any roles.
<orasp:binding-authorization orawsp:Enforced="true" orawsp:Silent="true"
orawsp:category="security/authorization"
orawsp:name="J2EE services Authorization">
<orasp:permitAll/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative" orawsp:name="AuthzConfig"/>
</orawsp:bindings>
</orasp:binding-authorization>
The <orasp:request> element defines the message body elements that are signed and encrypted in the request message. The <orasp:request> element contains the following subelements:
The <orasp:require-tls> element specifies whether two-way authentication is required.
The following table summarizes the attributes of the <orasp:require-tls> element.
Table D-19 Attributes of <orawsp:require-tls> Element
| Attribute | Description |
|---|---|
|
include-timestamp |
Flag that specifies whether to include a timestamp. A timestamp can be used to prevent replay attacks by identifying an expiration time after which the message is no longer valid. |
|
mutual-auth |
Flag that specifies whether two-way authentication is required. Valid values include true or false. |
The <orassp:response> element defines the message body elements that are signed and encrypted in the response message. The <oraswsp:response> element contains the following subelements:
The <orasp:role> element defines the roles that are permitted access.
<orasp:binding-authorization orawsp:Enforced="true" orawsp:Silent="true"
orawsp:category="security/authorization" orawsp:description=""
orawsp:name="J2EE services Authorization">
<orasp:role orasp:name="Monitors"/>
<orasp:role orasp:name="AdminChannelUsers"/>
<orawsp:bindings>
<orawsp:Config orawsp:configType="declarative" orawsp:name="AuthzConfig"/>
</orawsp:bindings>
</orasp:binding-authorization>
The <orasp:saml-token> element configures the SAML token.
The following table summarizes the attributes of the <orasp:saml-token> element.
Table D-21 Attributes of <orasp:saml-token> Element
| Attribute | Description |
|---|---|
|
confirmation-type |
Confirmation type. Valid values include: sender-vouches and holder-of-key.
|
|
is-encrypted |
Flag that specifies whether the assertion is encrypted. Valid values include true or false. |
|
is-signed |
Flag that specifies whether the assertion is signed. Valid values include true or false. |
|
version |
SAML version. Valid values include: 1.1 and 2.0. |
The <orassp:signed-elements> element defines the message body elements that are signed. This element is valid if <orasp:signed-parts> is not set to <orasp:body/>
The <orassp:signed-elements> element contains the following subelement:
The <orasp:signed-parts> element defines the message parts that are signed.
The <orasp:signed-parts> element contains one or more of the following subelements:
The <orasp:username-token> element configures the SAML token.
The following table summarizes the attributes of the <orasp:username-token> element.
Table D-22 Attributes of <orasp:username-token> Element
| Attribute | Description |
|---|---|
|
add-created |
Flag that specifies whether a time stamp for the creation of the username token is required. Note: If Password Type is set to digest, then this attribute must be set to true. Otherwise, the policy to which it is attached will not validate. |
|
add-nonce |
Flag that specifies whether a nonce must be included with the username to prevent replay attacks. Note: If Password Type is set to digest, then this attribute must be set to true. Otherwise, the policy to which it is attached will not validate. |
|
is-encrypted |
Flag that specifies whether the username is encrypted. Valid values include true or false. |
|
is-signed |
Flag that specifies whether the username is signed. Valid values include true or false. |
|
password-type |
Type of password required. Valid values are:
|
The <orasp:x509-token> element defines the x.509 digital certificate.
The following table summarizes the attributes of the <orasp:x509-token> element.
Table D-23 Attributes of <orasp:x509-token> Element
| Attribute | Description |
|---|---|
|
sign-key-ref-mech |
Mechanism used when signing the request. Valid values include:
|
|
enc-key-ref-mech |
Mechanism used when encrypting the request. Valid values are the same as for Sign Key Reference Mechanism above. |
|
rcpt-sign-key-ref-mech |
Mechanism used when signing the receipt. Valid values are the same as for Sign Key Reference Mechanism above. |
|
rcpt-enc-key-ref-mech |
Mechanism used when encrypting the receipt. Valid values are the same as for Sign Key Reference Mechanism above. |
|
is-encrypted |
Flag that specifies whether the assertion is encrypted. Valid values include true or false. |
|
is-signed |
Flag that specifies whether the assertion is signed. Valid values include true or false. |