| Oracle® Fusion Middleware Administrator's Guide for Oracle SOA Suite and Oracle Business Process Management Suite 11g Release 1 (11.1.1.6.3) Part Number E10226-16 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware Administrator's Guide for Oracle SOA Suite and Oracle Business Process Management Suite 11g Release 1 (11.1.1.6.3) Part Number E10226-16 |
|
|
PDF · Mobi · ePub |
This chapter describes how to start and stop Oracle Business Activity Monitoring (Oracle BAM) components, create users and groups, grant Oracle BAM application permissions using application-level roles, and set up data access permissions on data objects and folders, and reports.
This chapter includes the following topics:
Use Oracle Enterprise Manager Fusion Middleware Control to manage Oracle BAM availability. For more information, see Section 25.2, "Managing Oracle BAM Availability."
Oracle BAM users and groups are created in Oracle WebLogic Server Administration Console (or in a security provider configured for your Oracle WebLogic Server); application-level roles are administered and new groups/roles and policies/grants can be created in Fusion Middleware Control (in Application Policies); and the users' Oracle BAM objects are managed in Oracle BAM Administrator. For more information, see Section 25.3, "Managing Oracle BAM Users."
Oracle BAM Server and web applications can be started and stopped using Fusion Middleware Control, or, as a convenience, the entire Oracle BAM application (or the Oracle WebLogic Server to which it is deployed) can be restarted in the Oracle WebLogic Server Administration Console.
Note:
On all UNIX installations of Oracle BAM, due to a behavior of the Java AWT APIs that Oracle BAM uses, Oracle BAM Server must be started with the DISPLAY environment variable unset.
$ unsetenv DISPLAY
Restarting is required for any configuration changes made in the Fusion Middleware Control properties pages for Oracle BAM or its configuration files.
To start or stop Oracle BAM components in Fusion Middleware Control:
In Fusion Middleware Control locate the OracleBamServer or OracleBamWeb node in the navigation tree.

Right-click the node to open the shortcut menu, and select Control.
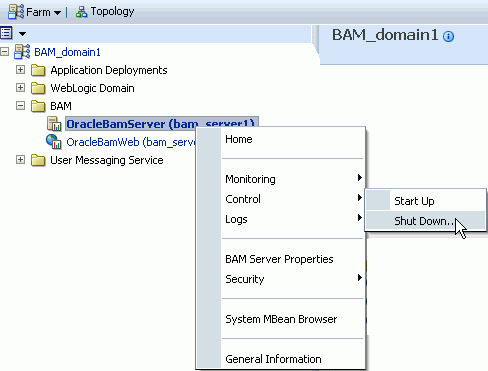
Start Up starts the component.
Shut Down shuts down the component.
Note:
Do not use Start Up alone to restart the component. To restart the component, you must stop the component using Shut Down before using Start Up to start the component or an error occurs.
These are the main steps for managing Oracle BAM users:
1. Configure the Security Provider
Users, groups, or both, to be used with Oracle BAM users must be present in a security provider configured for your Oracle WebLogic Server. For the main steps and links to detailed information about configuring security for Oracle WebLogic Server, see the Oracle Fusion Middleware Securing Oracle WebLogic Server.
Note:
You can use Oracle WebLogic Server to configure the Active Directory Authentication provider for authenticating Oracle BAM users instead of using the default embedded LDAP (also known as the default authenticator). To use Active Directory, you must also do some additional steps to change the OracleSystemUser default user. For more information, see "Changing the OracleSystemUser Default User" in the Oracle Fusion Middleware Security and Administrator's Guide for Web Services.
2. Create Users and Groups
Users and groups are defined in the configured security provider (for example, in the Oracle WebLogic Server embedded LDAP server). Refer to your specific security provider documentation for details on defining users and groups. For more information, see Section 25.3.1, "Defining Users and Groups" and Section 25.3.2, "Using Previously Seeded Group Members."
For example instructions about using Oracle WebLogic Server Administration Console to create users and groups, see Section 25.3.5, "Configuring Oracle WebLogic Server Embedded LDAP Server."
3. Assign Users and Groups to Application Roles
In turn, these users, groups, or both, are assigned to Oracle BAM application-level roles that grant those users, groups, or both, specific permissions for using Oracle BAM applications. Users and groups are granted Oracle BAM application permissions based on their Oracle BAM role membership.
For a detailed description of the Oracle BAM application roles and their associated Oracle BAM application permissions, see Section 25.3.3, "Adding Members to Application Roles."
Membership in Oracle BAM application roles is administered from the Application Roles page for Oracle BAM provided by Fusion Middleware Control. This page allows users and groups to be added as members to the various Oracle BAM application roles and allows creation of new application roles. For more information, see Section 25.3.4, "Introduction to Oracle BAM Application Roles."
Note:
Oracle BAM does not support assigning Oracle BAM application permissions directly to users and groups. Oracle BAM application permissions can only be granted to Oracle BAM application roles.
The only way to grant Oracle BAM application permissions to users and groups is to make those users and groups members of an Oracle BAM application role associated with the desired Oracle BAM application permissions.
With the exception of the Administrator role, membership in an Oracle BAM application role does not imply any Oracle BAM data access permissions. The Oracle BAM application roles only grant the user access to the associated Oracle BAM user interface as described in Section 25.3.4, "Introduction to Oracle BAM Application Roles."
When the user logs on to the Oracle BAM start page, there is a button for each of the Oracle BAM applications. Whether these buttons are enabled or not is based on the user's Oracle BAM application role membership.
Note:
Changes to a user's group and role membership could take as long as 5 minutes to propagate throughout the system.
4. Populate Users In Oracle BAM Applications
Users are not visible from Oracle BAM Administrator until they have logged into Oracle BAM for the first time. Oracle BAM also provides a utility that you can run to populate the users in Oracle BAM Administrator. For more information, see Section 25.3.6, "Populating Users in Oracle BAM Administrator."
5. Set Up Data Access Permissions on Oracle BAM
Specific data access permissions can be granted to users and groups using Oracle BAM Architect and Oracle BAM Active Studio. Users and groups can be granted read, update, and delete operation permissions on specific data objects and folders. For more information, see "Creating Permissions on Data Objects" and "Using Data Object Folders" in the Oracle Fusion Middleware Developer's Guide for Oracle SOA Suite.
Data access permissions can also be granted to users and groups at the row level for data objects. For information about row-level data security, see "Creating Security Filters" in the Oracle Fusion Middleware Developer's Guide for Oracle SOA Suite.
Individual report authors can control which Oracle BAM users have access to reports. For more information, see "Setting Folder Permissions" in the Oracle Fusion Middleware User's Guide for Oracle Business Activity Monitoring.
6. Manage Oracle BAM Object Ownership
When Oracle BAM users are removed from the security provider, the user accounts still appear in Oracle BAM Administrator because they may own Oracle BAM objects that must be transferred to other users before the user is completely removed from Oracle BAM. Object ownership is managed using Oracle BAM Administrator (see Section 25.3.7, "Managing Oracle BAM Object Ownership").
7. Remove Users From Oracle BAM
The administrator must also remove users from Oracle BAM Administrator after they are deactivated in the security provider (see Section 25.3.8, "Removing Invalid Users from Oracle BAM Administrator").
OracleSystemUser is the default owner of all Oracle BAM objects. It is required by Oracle BAM Server and must not be deleted.
Users are defined in the configured security provider's identity store (for example, Oracle WebLogic Server embedded LDAP server).
Groups, also referred to as enterprise-level roles, are also defined in this identity store. Groups are referred to as enterprise-level roles to distinguish them from application-level roles.
The enterprise-level roles are global to Oracle WebLogic Server, and they are applicable to all applications running on that server, including Oracle BAM. The application-level roles are specific to each application.
For example instructions about using Oracle WebLogic Server Administration Console to create users and groups, see Section 25.3.5, "Configuring Oracle WebLogic Server Embedded LDAP Server."
Note:
When you delete a user you cannot reuse that user name until you resolve the old instance with Oracle BAM. Oracle BAM marks the deleted user inactive when you delete the user in Oracle WebLogic Server.
If you attempt to reuse the same user name for a new account, Oracle BAM does not consider the newly added user to be the same user as the one previously deleted. You must delete the original user from Oracle BAM using Oracle BAM Administrator (and optionally transfer the user's Oracle BAM objects to another valid user). Once the inactive user is removed from Oracle BAM you can reuse the user name.
For information about removing users from Oracle BAM, see Section 25.3.8, "Removing Invalid Users from Oracle BAM Administrator."
The following Oracle WebLogic Server groups have been previously seeded in the Oracle BAM application policy:
BamAdministrators: Member of application role Administrator.
BamReportArchitects: Member of application role Report Architect.
BamReportCreators: Member of application role Report Creator.
BamReportViewers: Member of application role Report Viewer.
These members are a convenience. If you define these groups in your configured security provider, you can then assign Oracle BAM application-level roles to specific users and groups by placing them into these groups. All of this can be done from your security provider and does not require any Oracle BAM application policy modifications.
You must create these groups manually in the security provider because Oracle BAM does not automatically seed users or groups in the configured security provider.
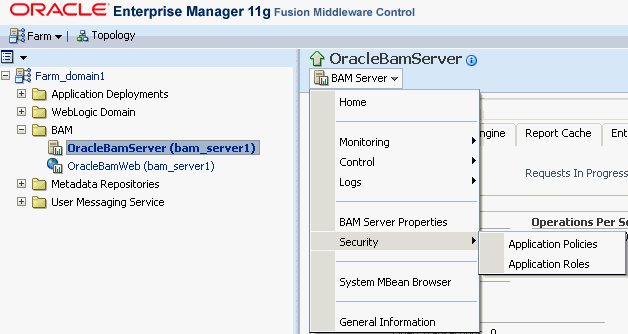
The Oracle BAM application policy defines the Oracle BAM application-level roles described in Section 25.3.4, "Introduction to Oracle BAM Application Roles" including role membership. The Oracle BAM application policy is managed in Fusion Middleware Control. The default policy store provider is the XML file-based policy store.
To add members to the Oracle BAM application-level roles, you must add entries to the membership list of the desired role using Fusion Middleware Control.
Shown here is the navigation required to open the Oracle BAM Application Roles page in Fusion Middleware Control:
Select a role in the Role Name list:
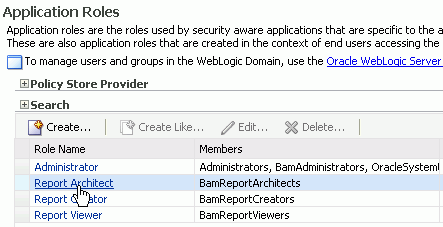
Add a member to the role:
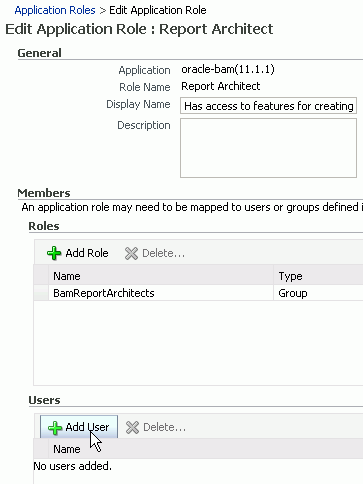
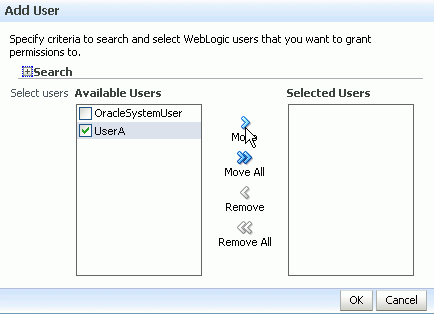
Select an available user and move it to the Selected Users list:
Oracle BAM defines the following application-level roles:
Administrator: Has access to all features.
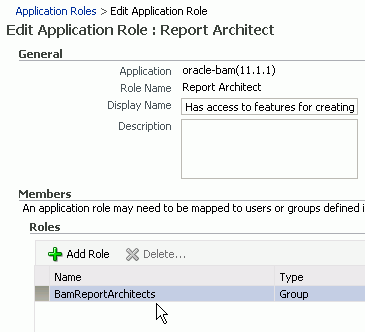
Report Architect: Has access to features for creating data objects and reports.
Report Creator: Has access to features for creating reports.
Report Viewer: Has access to features for viewing reports.
The application roles determine the permissions granted to specific users or groups. If a user or group is a member of one of these Oracle BAM application roles, then they are granted the associated Oracle BAM permissions.
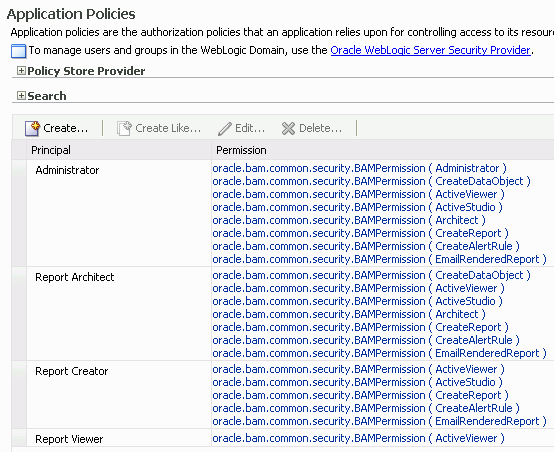
The Oracle BAM application roles are granted the following permissions:
Administrator Permissions
Administrator: Has full access to Oracle BAM Administrator application functionality.
CreateDataObject: Can create data objects in Oracle BAM Architect.
ActiveViewer: Has full access to Oracle BAM Active Viewer application functionality.
ActiveStudio: Has full access to Oracle BAM Active Studio application functionality.
Architect: Has full access to Oracle BAM Architect application functionality.
CreateReport: Can create reports in Oracle BAM Active Studio.
CreateAlertRule: Can create alerts in Oracle BAM Architect and Oracle BAM Active Studio.
EmailRenderedReport: Can email report attachments to Oracle BAM users.
Report Architect Permissions
CreateDataObject: Can create data objects in Oracle BAM Architect.
ActiveViewer: Has full access to Oracle BAM Active Viewer application functionality.
ActiveStudio: Has full access to Oracle BAM Active Studio application functionality.
Architect: Has full access to Oracle BAM Architect application functionality.
CreateReport: Can create reports in Oracle BAM Active Studio.
CreateAlertRule: Can create alerts in Oracle BAM Architect and Oracle BAM Active Studio.
EmailRenderedReport: Can email report attachments to Oracle BAM users.
Report Creator Permissions
ActiveViewer: Has full access to Oracle BAM Active Viewer application functionality.
ActiveStudio: Has full access to Oracle BAM Active Studio application functionality.
CreateReport: Can create reports in Oracle BAM Active Studio.
CreateAlertRule: Can create alerts in Oracle BAM Active Studio.
EmailRenderedReport: Can email report attachments to Oracle BAM users.
Report Viewer Permissions
ActiveViewer: Has full access to Oracle BAM Active Studio application functionality.
The Oracle WebLogic Server embedded LDAP server is the default security provider for Oracle WebLogic Server. This section describes the procedures for adding new users and groups to the Oracle WebLogic Server embedded LDAP server.
For information about configuring the embedded LDAP server, see "Managing the Embedded LDAP Server" in Oracle Fusion Middleware Securing Oracle WebLogic Server.
Oracle WebLogic Server administration is performed using the Oracle WebLogic Server Administration Console at
http://host_name:port_number/console
Oracle WebLogic Server must be running to access the administration console. This console requires the user to log in with Oracle WebLogic Server administrator credentials. After successfully logging in, the user is placed at the Oracle WebLogic Server Administration Console home page.
To add a group:
Go to Home > Security Realms > myrealm > Users and Groups in Oracle WebLogic Server Administration Console.
Select the Groups tab, and click New.
Enter the group name and description. Do not change the provider.
Click OK.
To add a user:
Go to Home > Security Realms > myrealm > Users and Groups in Oracle WebLogic Server Administration Console.
Select the Users tab, and click New.
Enter the user name, description, and login password. Do not change the provider.
Click OK.
To add a user to a group:
Go to Home > Security Realms > myrealm > Users and Groups in Oracle WebLogic Server Administration Console.
Select the Users tab, and select the user.
Select the Groups tab.
Move the groups from the Available list to the Chosen list. The Chosen list represents the list of groups of which the user is now a member.
Click Save.
Users are not automatically populated in Oracle BAM Administrator by the security provider. The system administrator must either run the registerusers utility, or have users log in to the Oracle BAM start page by using the provided credentials, before they can be managed in Oracle BAM Administrator.
Oracle BAM is a monitoring and analytics application that in implementation can support requirements to secure data, not only at the user and permissions level, but also at the row level for specific analytic data. Because of this requirement, Oracle BAM users require some management in Oracle BAM Administrator that is not provided in the standard Oracle WebLogic Server user management tool set. In order to configure these additional security features for a specific user, that user must be defined in Oracle BAM Administrator.
See the following topics for more information:
The registerusers utility is a standalone Java application for registering users with Oracle BAM Server. Normally, Oracle BAM is not aware of a particular defined user until that user logs into Oracle BAM for the first time. On initial login, Oracle BAM looks up the user in the configured security provider, and synchronizes Oracle BAM's definition for that user with that of the configured security provider. This includes the user name, role membership, group membership, user properties (for example, email address), and so on.
Because Oracle BAM is not aware of defined users until they have logged in at least one time, it is not possible to perform certain Oracle BAM user configuration related to that user. For example, when defining data object permissions in Oracle BAM, the user is not present in the list of known users presented by the permission editor.
The registerusers utility allows a user with Oracle BAM administrator-level privileges to register a list of users with Oracle BAM. The result of this registration is that these users are fully defined in Oracle BAM and available for further Oracle BAM user configuration, such as defining data object permissions.
The users are only added to Oracle BAM if they are successfully authenticated with the security provider. The input to this utility is a simple list of white-space delimited user names.
The registerusers utility confirms the successful registration of each user to standard out, and the failed registration of any user to standard error. The following is sample output from the registerusers utility:
>registerusers -file cmd_file.txt Enter Password: Connecting to BAM server as user weblogic. Registering users... Registration Succeeded For User: james. Registration Failed For User: jane. Reason: BAM-00400: Authentication failed. Registration Succeeded For User: adam. Registration Failed For User: bob. Reason: BAM-00400: Authentication failed. Registration Succeeded For User: bill. Registration Succeeded For User: barbara. Registration Succeeded For User: lynn.
If the utility is executed without any arguments, then the command syntax is displayed to standard out.
The syntax of the command is:
registerusers -adminuser adminusername -host host -port port -protocol protocol [-file filename]... [username]...
where:
adminusername specifies the name of a user with Oracle BAM administrator privileges.
host specifies the hostname or IP address of the target Oracle BAM Server. Default: localhost
port specifies the port number of the target Oracle BAM server. Default: 7001
protocol specifies the communication protocol to be used. Can be t3 or t3s for SSL. Default: t3
filename specifies a file containing command line arguments. The -file option is replaced by the contents of the specified file.
username specifies the name of a user to be registered with Oracle BAM.
For example:
>registerusers -adminuser weblogic -host localhost -port 7001 -protocol t3 -file cmd_file.txt smith jones
If the -adminuser option is omitted, then it is prompted for from standard input. The password for the BAM Administrator specified by -adminuser is prompted for from standard input using a password prompt where typed characters are hidden.
The file represented by <filename> should contain white-space delimited command-line arguments. White space is defined as blanks, EOL characters, and commas. Both single- and double-quoted strings are supported.
The file can also contain double-slash and slash-asterisk comments for documentation purposes. These comments are ignored.
If a command-line argument must contain any white-space characters (including commas), forward slashes (/) (as in file paths), or asterisks (*), then it must be quoted. For example, "/dir1/dir2/file.txt".
The file can contain further -file options. The file should be in UTF-8 format to support extended character sets.
The following is a sample command file:
// Specify Oracle BAM administrator account to execute command. Password is not
// provided so that the user is securely prompted for the password.
-adminuser user_name
// Configure the target BAM server.
-host localhost -port 7001 -protocol t3
// Register the following users.
jones /* This is Mr. Jones. */
smith /* This is Ms. Smith. */
// Register users from another file.
-file "/dir1/dir2/user_list.txt"
Default values for -host, -port, and -protocol arguments are included in the UserRegisterConfig.xml file. These defaults are only used if the option is not specified on the command line. If these options are not specified on the command line, or in the UserRegisterConfig.xml configuration file, then the defaults are used. The command syntax output shows the default values that are in effect.
The defaults are:
-host localhost -port 7001 -protocol t3
The following is an example of a UserRegisterConfig.xml file.
<?xml version="1.0" encoding="UTF-8" standalone="yes"?> <UserRegister> <ServerName>localhost</ServerName> <ServerPort>7001</ServerPort> <Communication_Protocol>t3</Communication_Protocol> <ServerPlatform>weblogic</ServerPlatform> </UserRegister>
The -host default is picked up from the ServerName property, the -port default is picked up from the ServerPort property, and the -protocol default is picked up from the Communication_Protocol element. Information about these properties can be found in Table 23-3. ServerPlatform configuration is required for standalone applications. The value of this is weblogic or websphere, depending on the type of application server Oracle BAM Server is running on.
To populate users in Oracle BAM Administrator:
Have each Oracle BAM user open the Oracle BAM start page and log in using the credentials specified by the security provider.
The Oracle BAM start page can be found at:
http://host_name:port_number/OracleBAM/
The administrator opens the Oracle BAM start page, logs in, and selects Administrator.
Select User management from the list, if the User Management page is not displayed in Oracle BAM Administrator.
Figure 25-1 Oracle BAM Administrator Function List
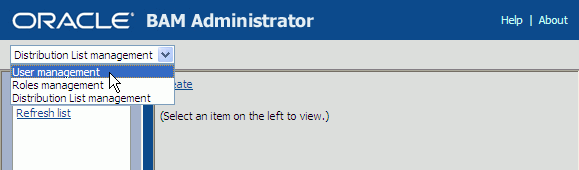
Verify that each Oracle BAM user appears in the Users list (use the Refresh list link to show the latest data).
When Oracle BAM users are removed from the security provider, the user accounts continue to appear in the Oracle BAM Administrator application with an exclamation mark (!) icon to indicate that they are not valid.
These users do not have access to Oracle BAM applications, but remain visible because they may own objects in Oracle BAM that must be transferred to other users before the user is completely removed from Oracle BAM.
Object ownership is managed using Oracle BAM Administrator.
To transfer object ownership:
Go to the Oracle BAM start page, log in, and select Administrator.
The Oracle BAM start page can be found at:
http://host_name:port_number/OracleBAM/
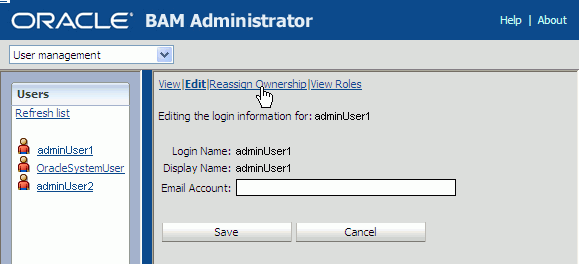
Select User management from the list (see Figure 25-1).
Select the user in the Users list that currently owns the objects you can reassign.
Click Reassign Ownership.
The Select Names dialog displays a list of users.
Select a user account in the list that becomes the new owner of the objects.
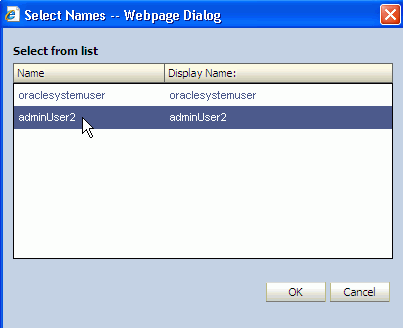
Click OK.
Reports are moved to a subfolder named after the selected user name.
Alerts are moved, and a zero (0) is appended to the alert name if the selected owner has an alert with the same name. If the alert needs an item updated or specified, an exclamation mark (!) is displayed on the alert icon in Oracle BAM Architect and Oracle BAM Active Studio Alerts pages.
Shared reports and folders change ownership but are not moved.
Invalid users are not automatically removed from Oracle BAM because they may own reports and alerts that must be transferred to active Oracle BAM users. After those objects are transferred, an invalid user may be deleted from Oracle BAM Administrator.
To remove invalid users:
Go to the Oracle BAM start page, log in, and select Administrator.
The Oracle BAM start page can be found at:
http://host_name:port_number/OracleBAM/
Select User management from the list (see Figure 25-1).
Select an invalid user in the Users list whose objects have been reassigned.
For information about reassigning objects, see Section 25.3.7, "Managing Oracle BAM Object Ownership."
An inactive user has an exclamation point (!) icon next to the user name.
Click Delete.