1 Introduction to Oracle Adaptive Access Manager
Oracle Adaptive Access Manager protects companies exposing Web applications and services, and their end users from online threats and insider fraud. It provides risk-aware authentication, real-time behavior profiling, and transaction and event risk analysis.
Functionality can be divided into two major areas as summarized in Table 1-1.
Table 1-1 Oracle Adaptive Access Manager Functionality
| Functionality | Description |
|---|---|
|
Real-time or offline risk analysis |
Oracle Adaptive Access Manager provides functionality to calculate the risk of an access request, an event or a transaction, and determine proper outcomes to prevent fraud and misuse. A portion of the risk evaluation is devoted to verifying a user's identity and determining if the activity is suspicious. Functionality that support risk analysis are:
|
|
End-user facing functionality to prevent fraud |
Oracle Adaptive Access Manager protects end users from phishing, pharming, and malware. The virtual authentication devices secure credential data at the entry point; this ensures maximum protection because the credential never resides on a user's computer or anywhere on the Internet where it can be vulnerable to theft. As well, Oracle Adaptive Access Manager provides interdiction methods including risk-based authentication, blocking and configurable actions to interdict in other systems. Functionality that supports end-user facing security are:
|
This chapter provides an overview of Oracle Adaptive Access Manager 11g and includes the following topics:
1.1 Benefits of Oracle Adaptive Access Manager
Oracle Adaptive Access Manager is a security solution to protect the enterprise and its end users of the Web applications and services it exposes.
Oracle Adaptive Access Manager provides:
-
Risk-aware authentication
-
Authentication security
-
Real-time and offline risk analytics
-
Flexible deployment options
-
Out-of-the-box integrations with single sign-on and identity management
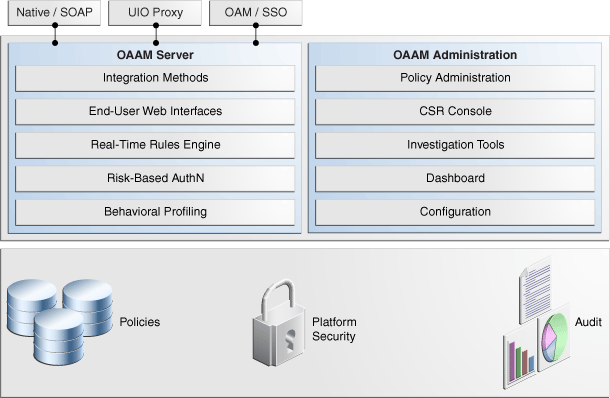
The following illustration shows the functionalities contained in OAAM Server and OAAM Admin.
1.2 Oracle Adaptive Access Manager Features
Adaptive access systems can provide the highest levels of security with context-sensitive online authentication and authorization. Thus, situations are evaluated and proactively acted upon based on various types of data.
This section outlines key components/features used for authentication and fraud monitoring and detection.
Oracle Adaptive Access Manager provides a number of rich features that strengthen existing web application login flows. Regardless of the type of authentication in place, Oracle Adaptive Access Manager can improve the level of security in a usable manner. Insider fraud, session hijacking, stolen credentials and other threats cannot be eliminated by strong, credential based authentication alone. Adding a risk-based challenge layer behind existing authentication can increase the level of security with minimal impact to the user experience – a critical factor for large deployments where desk calls can impact the bottom line. Oracle Adaptive Access Manager's suite of virtual authentication devices combats phishing personalized images and phrases known only to the server and the end user. Furthermore, through the use of KeyPad and PinPad, security of the user's credentials during entry can be assured by not capturing or transmitting the actual credential of the end user. This protects the credential from theft by malware and other similar threats. The virtual authentication devices are server driven; all features are provided without any client-side software or logic that can be compromised by key-loggers and other common malware. Additionally, Oracle Adaptive Access Manager performs device fingerprinting and behavioral profiling on every access to determine the likelihood that the authentication is being attempted by the valid user.
Oracle Adaptive Access Manager contains proprietary clientless technologies for fingerprinting and interrogating devices used during access requests and transactions. Device fingerprinting is a mechanism to recognize the devices a customer uses whether it is a desktop computer, laptop computer or other web-enabled device.
Each time the user accesses the system, information about the device is collected. OAAM generates a unique single-use fingerprint and marks a device for each user session. It is replaced upon each subsequent fingerprinting process with another unique fingerprint.
The fingerprinting process can be run any number of times during a user session to allow detection of changes mid-session that can indicate session hijacking. OAAM monitors a comprehensive list of device attributes. If any attributes are not available the device can still be fingerprinted. The single-use capabilities combined with server-side logic defends against the fingerprint being stolen and reused on another machine to commit fraud.
Answer Logic increases the usability of Knowledge Based Authentication (KBA) questions by accepting answers that are fundamentally correct but may contain a small typo, abbreviation or misspelling. For example, if abbreviation is enabled in Answer Logic a user is challenged with the question "What street did you live on in high school?" They may answer "1st St." which is fundamentally correct even though when they registered the answer six months ago they entered "First Street". By allowing a configurable variation in the form of correct answers, Answer Logic dramatically increases the usability of registered challenge questions making the balance between security and usability firmly in the control of the enterprise.
OTP Anywhere allows end users to authenticate themselves by entering a server generated one-time-password (OTP) which they can receive via SMS, email, instant message or voice channels. When the OTP is sent via SMS, the user's cell phone serves as a physical second factor that the user has in their possession. As well, the authentication is being sent out-of-band to increase the level of assurance that only the valid user has access to the one-time password. When authentication methods such as Answer Logic and OTP Anywhere are applied based on the level of risk it can dramatically increase web application access security in a cost-effective and usable manner.
The Oracle Adaptive Access Manager Dashboard is a unified display of integrated information from multiple components in a user interface that organizes and presents data in a way that is easy to read. The Oracle Adaptive Access Manager dashboard present monitor data versions of key metrics. Administrators can easily see up-to-the-minute data on application activity from a security perspective. The reports that are presented help users visualize and track general trends.
Oracle Adaptive Access Manager provides a framework and set of tools for investigators and customer service representatives.
The Case Management feature of Oracle Adaptive Access Manager is used in two ways.
-
Users of the enterprise using Oracle Adaptive Access Manager can call the enterprise asking for assistance with customer-facing features of Oracle Adaptive Access Manager such as images, phrases, or challenge questions, or any issues with their account. The CSR uses Case Management to create a case which records all the actions performed by the CSR to assist the user as well as various account activities of the user.
-
The Case Management feature is also used by Fraud Investigators to investigate potentially fraudulent activity performed on user accounts.
Knowledge-Based Authentication
Oracle Adaptive Access Manager provides out-of-the-box secondary authentication in the form of knowledge-based authentication (KBA) questions. The KBA infrastructure handles registration, answers, and the challenge of questions. Since KBA is a secondary authentication method, it is presented after successful primary authentication.
KBA is used to authenticate an individual based on knowledge of personal information, substantiated by a real-time interactive question and answer process. Oracle Adaptive Access Manager's Rules Engine and organizational policies are responsible for determining if it is appropriate to use challenge questions to authenticate the customer.
Policies and rules can be used by organizations to monitor and manage fraud or to evaluate business elements. The policy and rules are designed to handle patterns or practices, or specific activities that you may run across in the day-to-day operation of your business. Using Oracle Adaptive Access Manager, you can define when the collection of rules is to be executed, the criteria used to detect various scenarios, the group to evaluate, and the appropriate actions to take when the activity is detected.
Oracle Adaptive Access Manager integrates with Oracle Data Mining to provide statistical risk analysis in real-time. This form of risk analysis "trains" over time so it compliments the highly configurable rules and behavioral profiling which do not require training. The more training each model does, the more accurate the risk analysis becomes. The out of the box predictive models are trained in two ways:
-
The anomaly detection model trains automatically when fed historical access data.
-
The fraud classification model trains on the findings of human fraud investigators. Additional models can be configured as required to meet specific deployment use cases. This open approach to predictive risk analysis allows OAAM customers to clearly see on which decisions outcomes are based and allows augmentation as required.
This open approach to predictive risk analysis allows OAAM customers to clearly see on which decisions outcomes are based and allows augmentation as required.
Configurable actions are actions that are triggered based on the result action or risk scoring or both after a checkpoint execution. Java classes and action templates for certain configurable actions are provided out-of-the-box, but you have the option to create configurable actions based on business requirements.
A transaction is any process a user performs after successfully logging in. Examples of transactions are making a purchase, bill pay, money transfer, stock trade, address change, and others.
With each type of transaction, different types of details are involved. Before the client-specific transaction with its corresponding entities can be captured and used for enforcing authorization rules, fraud analysis, and so on, it must be defined and mapped. Oracle Adaptive Access Manager's Transactions feature allows administrators to perform this task. With the Transaction Definition feature, an administrator is able to create entity and data element definitions and map them to the client-specific data (source data).
Reporting is available through Oracle Adaptive Access Manager. A limited license of Oracle Business Intelligence Publisher is included for customizable reporting capabilities.
Oracle Identity Management BI Publisher Reports uses Oracle BI Publisher to query and report on information in Oracle Identity Management product databases. With minimal setup, Oracle Identity Management BI Publisher Reports provides a common method to create, manage, and deliver Oracle Identity Management reports.
The report templates included in Oracle Identity Management BI Publisher Reports are standard Oracle BI Publisher templates—though you can customize each template to change its look and feel. If schema definitions for an Oracle Identity Management product are available, you can use that information to modify and generate your own custom reports.
1.3 Oracle Adaptive Access Manager Architecture
Oracle Adaptive Access Manager is designed to provide a rich selection of capabilities with heterogeneous support for a variety of environments. Functionality is implemented to optimize resources and provide enterprise class scalability and redundancy.
1.3.1 High Availability
Oracle Adaptive Access Manager is built on a J2EE-based, multi-tier deployment architecture that separates the platform's presentation, business logic, and data tiers. Because of this separation of tiers, Oracle Adaptive Access Manager can rapidly scale with the performance needs of the customer. The architecture can leverage the most flexible and supported cross-platform J2EE services available: a combination of Java, XML and object technologies. This architecture makes Oracle Adaptive Access Manager a scalable, fault-tolerant solution.
The runtime components including the rules engine and end user interface flows are contained in one managed server while the administration console functionality is separated out into its own managed server. The administration console contains the customer service and security analyst case management functionality which must always be available to employees in potentially large call centers with high call volumes.
Depending on the deployment method used the topology changes slightly. Native application integration deployments embed the runtime components so the administration console is the only additional managed server added to the deployment. Oracle Adaptive Access Manager is also completely stateless and fully supports clustered deployments to meet high performance requirements. As well, all high availability features of the Oracle database are supported for use with Oracle Adaptive Access Manager.
1.4 Deployment Options
Oracle Adaptive Access Manager supports a number of deployment options to meet the specific needs of practically any deployment. The decision of which deployment type to employ is usually determined based on the use cases required and the applications being protected.
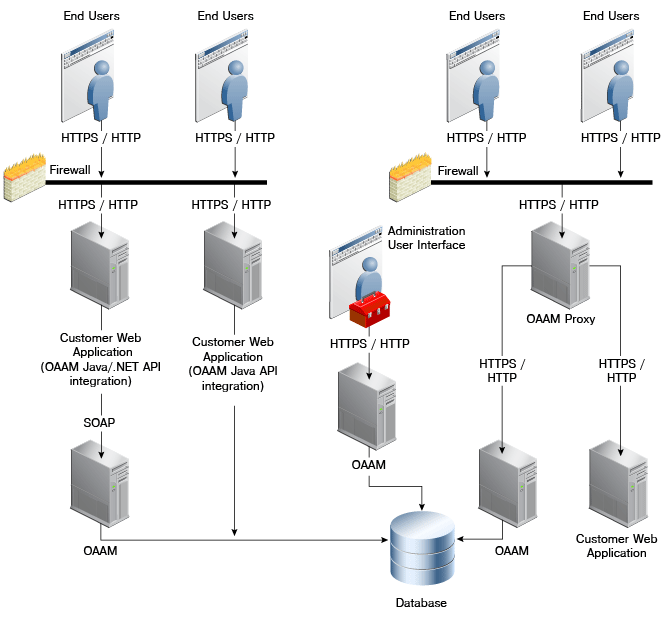
In the Oracle Adaptive Access Manager architecture shown in Figure 1-2, end users access customer web applications in various deployments.
1.4.1 Single Sign-On Integration
Oracle Adaptive Access Manager has an out of the box integration with Oracle Access Manager to provide advanced login security including the virtual devices, device fingerprinting, real-time risk analysis and risk-based challenge. New to 11g there are two versions of the OAAM and OAM integration, basic and advanced. The "basic" integration embeds OAAM into the OAM runtime server. It includes many of the login security use cases available from OAAM and reduces the footprint. To gain advanced features and extensibility customers can deploy using the "advanced" integration. Features such as OTP anywhere, challenge processor framework, shared library framework and secure self-service password management flows require the advanced integration option. Oracle Adaptive Access Manager can also be integrated with third party single sign-on products via systems integrators if required.
1.4.2 Universal Installation Option Reverse Proxy
Oracle Adaptive Access Manager can be deployed using an Apache module to intercept login requests and provide advanced login security. The flows available are the same as for the advanced single sign-on integration option.
The main benefit of the Oracle Universal Installation Option (UIO) deployment is that it requires little or no integration with protected applications and SSO is not required.
1.4.3 Native Application Integration
Oracle Adaptive Access Manager can be natively integrated with an application to provide extreme high performance and highly customizable security. A native integration embeds OAAM in-process inside the protected applications. The application invokes the Oracle Adaptive Access Manager APIs directly to access risk and challenge flows.