| Oracle® Fusion Middleware 2 Day Administration Guide 11g Release 1 (11.1.1) Part Number E10064-03 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware 2 Day Administration Guide 11g Release 1 (11.1.1) Part Number E10064-03 |
|
|
PDF · Mobi · ePub |
Oracle Fusion Middleware provides many security features, including accounts specifically for administrative purposes. This chapter describes how to create additional administrative accounts, create application roles, change passwords for those accounts, and configure SSL.
This chapter contains the following topics:
During the Oracle Fusion Middleware installation and configuration, you must specify an administrative user and a password for the user. By default, the user name is weblogic. You can use this administrative account to log in to Fusion Middleware Control and the Oracle WebLogic Server Administration Console.
You can create additional administrative users using the Oracle WebLogic Server Administration Console.
To create a new administrative user with full privileges:
Navigate to the Oracle WebLogic Server Administration Console. (For example, from the home page of the domain in Fusion Middleware Control, select To configure and managed this WebLogic Domain, use the Oracle WebLogic Server Administration Console.)
From the navigation pane, select Security Realms.
The Summary of Security Realms page is displayed.
Select a realm, such as myrealm.
The Settings for the realm page is displayed.
Select the Users and Groups tab, then the Users tab. Click New.
The Create a New User page is displayed.
For Name, enter the new user name. In this case, enter admin2.
Optionally, add a description for the account.
For Provider Authenticator, use the default, DefaultAuthenticator.
For Password, enter a password for the account. Then, for Confirm Password, reenter the password.
If you selected DefaultAuthenticator, any passwords you assign to Oracle Fusion Middleware users:
Must contain at least eight characters.
At least one of the characters must be a number or special character, such as US dollar sign ($), number sign (#), or underscore (_).
Click OK.
Select the newly created user in the Users table.
The Settings for user page is displayed.
Select the Groups tab.
From the Available groups, select the group. In this case, to give the new user full privileges, select Administrators and move it to the Chosen list, as shown in the following figure:
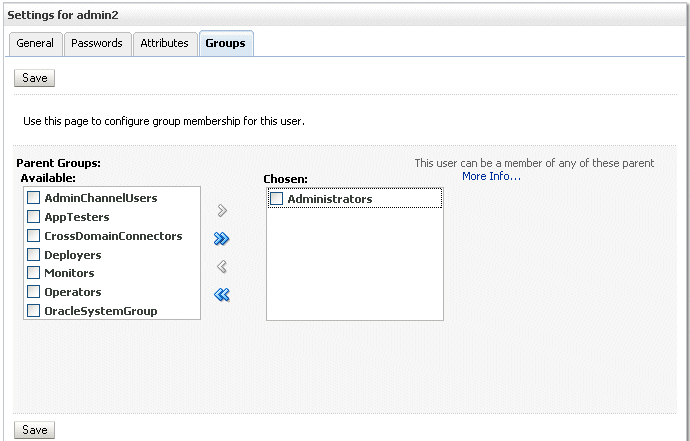
Click Save.
You now have a user named admin2 that has the Administrator role for the Oracle WebLogic Server domain.
You may want to give only minimal privileges to another user, allowing the user to only monitor Oracle Fusion Middleware, not to change any of the configuration. You can create additional users and give them limited access. For example, you can create a user with privileges to deploy applications.
To create an additional user who can deploy applications:
Navigate to the Oracle WebLogic Server Administration Console. (For example, from the home page of the domain in Fusion Middleware Control, select To configure and managed this WebLogic Domain, use the Oracle WebLogic Server Administration Console.)
From the navigation pane, select Security Realms.
The Summary of Security Realms page is displayed.
Select a realm, such as myrealm.
The Settings for the realm page is displayed.
Select the Users and Groups tab, then the Users tab. Click New.
The Create a New User page is displayed.
For Name, enter the new user name. In this case, enter app_deployer.
Optionally, add a description for the account.
For Password, enter a password for the account. Then, for Confirm Password, reenter the password.
If you selected DefaultAuthenticator, any passwords you assign to Oracle Fusion Middleware users:
Must contain at least eight characters.
At least one of the characters must be a number or special character, such as US dollar sign ($), number sign (#), or underscore (_).
Click OK.
Select the newly created user in the Users table.
The Settings for user page is displayed.
Select the Groups tab.
From the Available groups, select the group. In this case, to give the new user privileges only to deploy applications, select Deployers and move it to the Chosen list.
Click Save.
You can change the password of users using the Oracle WebLogic Server Administration Console.
To change the password of an administrative user:
Navigate to the Oracle WebLogic Server Administration Console. (For example, from the home page of the domain in Fusion Middleware Control, select To configure and managed this WebLogic Domain, use the Oracle WebLogic Server Administration Console.)
From the navigation pane, select Security Realms.
The Summary of Security Realms page is displayed.
Select a realm, such as myrealm.
The Settings for the realm page is displayed.
Select the Users and Groups tab, then the Users tab. Select the user.
The Settings for user page is displayed.
Select the Passwords tab.
Enter the new password, then enter it again to confirm it.
Click Save.
SSL secures communication by providing message encryption, integrity, and authentication. The SSL standard allows the involved components (such as browsers and HTTP servers) to negotiate which encryption, authentication, and integrity mechanisms to use.
Encryption provides confidentiality by allowing only the intended recipient to read the message. SSL can use different encryption algorithms to encrypt messages. During the SSL handshake that occurs at the start of each SSL session, the client and the server negotiate which algorithm to use. Examples of encryption algorithms supported by SSL include AES, RC4, and 3DES.
Integrity ensures that a message sent by a client is received intact by the server, untampered. To ensure message integrity, the client hashes the message into a digest using a hash function and sends this message digest to the server. The server also hashes the message into a digest and compares the digests. Because SSL uses hash functions that make it computationally infeasible to produce the same digest from two different messages, the server can tell that if the digests do not match, then someone had tampered with the message. An example of a hash function supported by SSL is SHA1.
Authentication enables the server and client to check that the other party is who it claims to be. When a client initiates an SSL session, the server typically sends its certificate to the client. Certificates are digital identities that are issued by trusted certificate authorities, such as Verisign.
The client verifies that the server is authentic and not an imposter by validating the certificate chain in the server certificate. The server certificate is guaranteed by the certificate authority (CA) who signed the server certificate.
The server can also require the client to have a certificate, if the server needs to authenticate the identity of the client.
This section describes the following topics:
In Oracle Fusion Middleware, all Java components and applications use the JKS keystore. Thus all Java components and applications running on Oracle WebLogic Server use the JKS-based KeyStore and TrustStore.
The Oracle Virtual Directory system component uses a JKS keystore to store keys and certificates. Configuring SSL for Oracle Virtual Directory thus requires setting up and using JKS keystores.
Other components use the Oracle wallet as their storage mechanism. An Oracle wallet is a container that stores your credentials, such as certificates, trusted certificates, certificate requests, and private keys. You can store Oracle wallets on the file system or in LDAP directories such as Oracle Internet Directory. Oracle wallets can be auto-login or password-protected wallets.
The following components use Oracle wallet:
Oracle HTTP Server
Oracle Web Cache
Oracle Internet Directory
You can enable SSL on the communication path between a client browser and a Web server. In this case, you configure the virtual host for Oracle HTTP Server to listen in SSL mode, as described in the following topics:
Enabling SSL for Inbound Traffic to Oracle HTTP Server Virtual Hosts
Enabling SSL for Outbound Traffic from Oracle HTTP Server Virtual Hosts
To enable SSL for inbound traffic to Oracle HTTP Server virtual hosts:
In the navigation pane, expand the farm, then Web Tier. Select an Oracle HTTP Server instance.
From the Oracle HTTP Server menu, choose Security, then Wallets.
The Wallets page is displayed.
Click Create.
The Create Wallet page is displayed, as shown in the following figure:
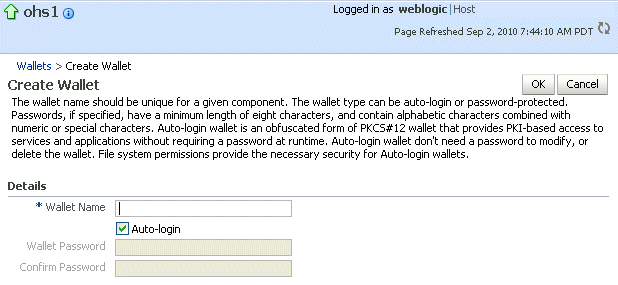
For Wallet Name, enter a descriptive wallet name.
Check or uncheck Autologin, depending on whether your wallet is an auto-login wallet. The default is an auto-login wallet. If you do not check Autologin, for Wallet Password, enter a password, then enter the same password in Confirm Password.
Click OK to create the wallet.
A confirmation box is displayed.
The confirmation box asks if you want to create a certificate request. Click Yes.
The Create Wallet: Add Certificate Request page is displayed.
For Common Name, enter a name for the certificate request.
Enter information about your organization.
For Key Size, select a size.
Click OK.
To get the certificate signed by a certificate authority (CA), you must export the certificate request out of the wallet and send it to your CA. After the issued certificate is returned, you must import it back into your wallet. Now your wallet is ready to use.
From the HTTP Server menu, choose Administration, then Virtual Hosts.
The Virtual Hosts page is displayed.
Select a virtual host and choose Configure, then SSL Configuration.
The SSL Configuration page is displayed, as shown in the following figure:
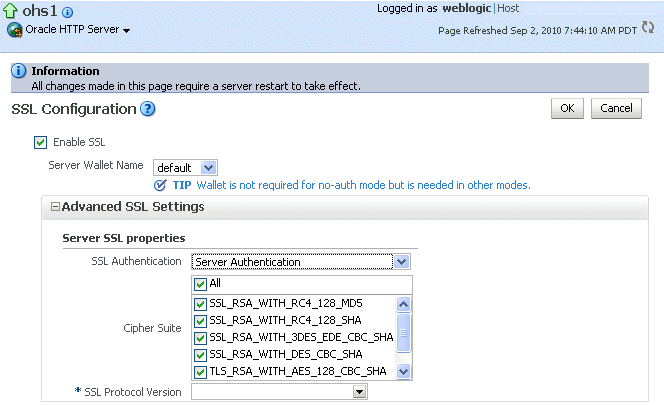
Select Enable SSL.
For Server Wallet Name, select the wallet.
From the Server SSL properties, select the SSL Authentication type, Cipher Suites to use, and the SSL protocol version.
Click OK.
Restart Oracle HTTP Server. (From the Oracle HTTP Server menu, choose Control, then Restart.)
Now, you can test this by visiting the Oracle HTTP Server page over SSL in a browser. Use a URL of the form https://host:port/, where you replace the host and port with values relevant to your own environment.
Outbound requests from Oracle HTTP Server are handled by configuring mod_wl_ohs.
To configure outbound requests for SSL:
Generate a custom keystore for Oracle WebLogic Server containing a certificate, using the Oracle WebLogic Server Administration Console:
In the left pane of the Console, expand Environment and select Servers.
Select Configuration, then Keystores.
Define the keystore. See the online help for information about each field.
Import the certificate used by Oracle WebLogic Server into the Oracle HTTP Server wallet as a trusted certificate. You can use any available utility such as WLST or Fusion Middleware Control for this task.
Edit the Oracle HTTP Server configuration file ORACLE_INSTANCE/config/OHS/ohs1/ssl.conf and add the following line to the SSL configuration under mod_weblogic:
WlSSLWallet "$(ORACLE_INSTANCE}/config/COMPONENT_TYPE/COMPONENT_NAME/default"
In the line, default is the name of the Oracle HTTP Server wallet in Step 2.
Here is an example of the configuration:
<IfModule mod_weblogic.c>
WebLogicHost myhost.example.com
WebLogicPort 7002
Debug ALL
WLLogFile /tmp/weblogic.log
MatchExpression *.jsp
SecureProxy On
WlSSLWallet "$(ORACLE_INSTANCE)/config/OHS/ohs1/keystores/default"
</IfModule>
Save the file and exit.
Restart Oracle HTTP Server to activate the changes.
Ensure that your Oracle WebLogic Server instance is configured to use the custom keystore generated in Step 1, and that the alias points to the alias value used in generating the certificate. Restart the Oracle WebLogic Server instance.
For more information about the topics covered in this chapter and other security topics, see:
Oracle Fusion Middleware Administrator's Guide for information about the following topics:
Secure Sockets Layer (SSL), which is an industry standard for securing communications. See "Configuring SSL."
Keystores, wallets, and certificates. See "Managing Keystores, Wallets, and Certificates."
Oracle Fusion Middleware Application Security Guide for information about the following topics:
Oracle Platform Security, which is a security framework that runs on Oracle WebLogic Server. It provides application developers, system integrators, security administrators, and independent software vendors with a portable, integrated, and comprehensive security platform framework for Java SE and Java EE applications.
Common Audit Framework, which provides a uniform system for administering audits across a range of components, flexible audit policies, and prebuilt compliance-reporting features.
Identity, Policy, and Credential stores, which provide secure storage and management of user and role information, policies, and credentials.