11g Release 6 (11.1.6)
Part Number E16689-06
Home
Contents
Book
List
Contact
Us
|
Oracle® Fusion
Applications Security Guide 11g Release 6 (11.1.6) Part Number E16689-06 |
Home |
Contents |
Book List |
Contact Us |
|
Previous |
Next |
Security Tasks and Oracle Fusion Applications: How They Fit Together
Security Setup Tasks: How They Fit Together
Getting Started with an Implementation: Overview
Initial Security Administration: Critical Choices
Initial Security Administration: Worked Example
Defining Security After Enterprise Setup: Points to Consider
Defining Data Security After Enterprise Setup: Points to Consider
Defining Trading Partner Security After Enterprise Setup: Points to Consider
Security Tasks After Enterprise Changes: Points To Consider
Security tasks include the following.
Security setup
Security implementation and administration
Note
Security setup and administration tasks typically use integrated user interface pages that are provided by the following products.
Oracle Identity Manager (OIM)
Oracle Authorization Policy Manager (APM)
Oracle Fusion Human Capital Management (HCM) products
Oracle Application Access Control Governor (AACG) in Governance, Risk, and Compliance Controls (GRCC)
Security setup and administrative tasks performed by product administrators and implementation consultants, such as managing HCM security profiles, are presented in the documentation for those products.
Provision the IT Security Manager job role with roles for user and role management.
Sign into Oracle Fusion Applications for the first time with the Installation Super User account to synchronize LDAP users with HCM user management and create an IT security manager user account and provision it with the IT Security Manager role.
Establish at least one implementation user and provision that user with sufficient access to set up the enterprise for all integrated Oracle Fusion Middleware and all application pillars or partitions.
Once initial security administration is complete and your enterprise is set up with structures such as business units, additional security administration tasks are optional and based on modifying and expanding the predefined security reference implementation to fit your enterprise. See points to consider for defining security, data security and trading partner security after enterprise setup.
The major security tasks and their order within the context of an overall Oracle Fusion Applications implementation extend from security setup through production deployment audits.
The Oracle Fusion business process model (BPM) provides a sequence of security implementation tasks that includes the following.
Security setup (Define Common Applications Configuration activity)
Define Implementation Users task group (optional)
Create Implementation Users task
Create Data Role for Implementation Users task
Provision Roles to Implementation Users task
Define security - tasks vary depending on deployed Oracle Fusion product family
Revoke Data Role from Implementation Users task
Import Worker Users task
Import Partner Users task
Manage Duties task
Manage Job Roles task
Manage Application Access Controls task
Define Automated Governance, Risk, and Performance Controls activity
Manage Application Access Controls task (AACG settings)
Manage Application Preventive Controls task
Manage Application Transaction Controls task
Manage Application Configuration Controls task
User and role provisioning tasks
Implement Role Request and Provisioning Controls activity
Import Worker Users task
Import Partner Users task
Self Request User Roles task
Approve User and Role Provisioning Requests task
Assign User Roles task
Manage Supplier User Roles and User Role Usages task
Map and Synchronize User Account Details task
Tasks for viewing account details for self or others
Tasks for applying and managing various role provisioning rules
Tasks for running synchronization processes
Security implementation and ongoing maintenance after setup (Manage IT Security activity)
Implement Function Security Controls
Create Job Role task
Import Worker Users task
Import Partner Users task
Manage Duties task
Manage Job Roles task
Manage Users task
Implement Data Security Controls
Manage Data Security Policies task
Manage Role Templates task
Manage Encryption Keys task
Manage Segment Security task
Manage Data Access Sets task
Define Security Profiles task group
Auditing tasks
Manage Security Audit, Compliance and Reporting activity
Manage Application Access Controls task
Note
Go live deployment does not require lockdown or specific security tasks because security is enforced across the test to production information life cycle.
The Oracle Fusion Applications installation process sets up a single, super user provisioned with the following enterprise roles.
Application Implementation Consultant
IT Security Manager
Application Administrators for the provisioned products
Initial security administration includes provisioning the IT Security Manager role with Oracle Identity Management (OIM) roles that carry entitlement for user and role management.
Identity User Administrator
Role Administrator
Additionally, the Xellerate Users organization must be assigned to the IT Security Manager role.
Important
As a security guideline, provision a dedicated security professional with the IT Security Manager role at the beginning of an implementation, and revoke that role from users provisioned with the Application Implementation Consultant role.
Security tasks are supported by tools within both Oracle Fusion Applications and Oracle Fusion Middleware.
The figure lists the tasks associated with each of the integrated products and pillars of an Oracle Fusion Applications deployment.
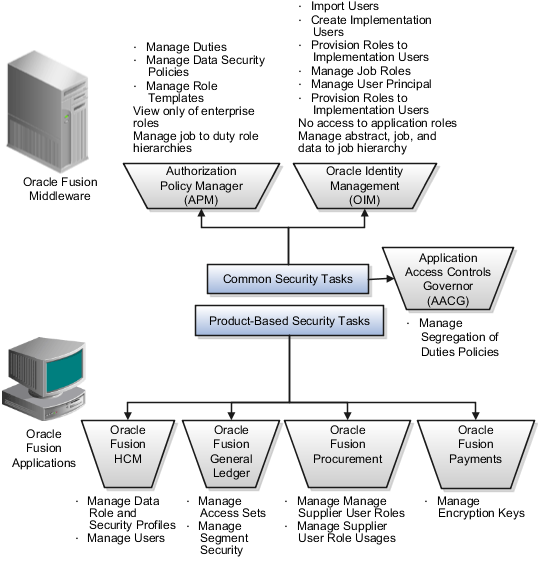
Set up security before and after setting up the enterprise with enterprise structures.
Security setup and administration tasks typically use integrated user interface pages that are provided by the following products.
Oracle Identity Manager (OIM)
Oracle Authorization Policy Manager (APM)
Oracle Fusion Human Capital Management (HCM) products
Oracle Application Access Control Governor (AACG) in Governance, Risk, and Compliance Controls (GRCC)
To define data security, administrators and implementation users additionally access integrated user interfaces provided by several products, including the following.
Oracle Fusion Global Human Resources
Oracle Fusion Middleware Extensions for Applications (FND)
Oracle Fusion General Ledger (GL)
Supplier Portal
Manage users and enterprise role hierarchies in OIM. Manage roles, including duty roles, in APM. Perform supplier role setup tasks for trading partner security in Supplier Portal. Application administrators perform user and role provisioning tasks within applications such as HCM, General Ledger, and Supplier Portal.
The following table shows initial security setup tasks in a likely order, as well as the conditions and purposes of the tasks and where in the user interface these tasks are performed.
|
Task |
Condition |
Purpose |
Performed In |
|---|---|---|---|
|
Create Implementation Users |
The predefined Oracle Fusion Applications super user is not the user who will be setting up your enterprise |
Create user accounts for implementation users. |
OIM |
|
Create Data Role for Implementation Users |
The predefined Application Implementation Consultant role access may be too broad |
Create a View All data role, such as a View All Financials Application Administrator data role. This data role is based on the Financials Application Administrator job role and combines the entitlements that have been granted to that role with unrestricted access to data on the secured objects that the role is authorized to access. |
HCM |
|
Provision Roles to Implementation Users |
An implementation user has been created with the Create Implementation Users task |
Provision implementation users with roles, such as Application Implementation Consultant, IT Security Manager, and product family Application Administrator job or data roles. |
OIM |
|
Revoke Data Role from Implementation Users |
None |
Revoke any View All data roles after setup is complete. |
OIM |
When setting up the enterprise with structures such as business units, data roles are automatically generated that inherit job roles based on data role templates. Data roles also can be generated based on HCM security profiles. Data role templates and HCM security profiles enable defining the instance sets specified in data security policies.
An HCM application administrator or application implementation consultant sets up enterprise structures, such as business units and ledgers, using Define Common Application Configuration activities. After the enterprise has been set up, you can proceed with the following security setup tasks.
The following table shows the tasks in a likely order, as well as the conditions and purposes of the tasks and where in the user interface these tasks are performed.
|
Task |
Condition |
Purpose |
Performed In |
|---|---|---|---|
|
Import Worker Users |
Users or workers are in legacy applications. |
If your enterprise has users in legacy applications, use a data load process to import user identities from legacy applications. If there are no legacy users, user accounts are created when workers are imported by performing the Import Workers task in HCM. |
OIM |
|
Import Partner Users |
|
If your enterprise has partner users in legacy applications, use a data load process to import partner identities from legacy applications. |
OIM |
|
Manage Job Roles |
None |
Manage job and abstract (enterprise) roles. |
OIM |
|
Manage Duties |
None |
Manage duty (application) roles and provision to job roles. |
APM |
|
Manage Application Access Controls |
None |
Manage segregation of duties policies. |
AACG |
|
Manage Data Access Sets |
GL is provisioned. |
Define access sets for ledgers and ledger sets. |
GL |
|
Manage Segment Security |
GL is provisioned. |
Manage accounting flexfield segment security rules. |
GL |
|
Manage Data Security Policies |
Product families other than HCM are provisioned. |
Manage data security grants to roles. |
APM |
|
Manage Role Templates |
None |
Manage templates to automatically create or update data roles based on a dimension such as business unit. |
APM |
|
Manage Encryption Keys |
Oracle Fusion Payments is provisioned. |
Create or edit encryption keys held in Oracle Wallet. Encryption keys are used to secure personally identifiable information (PII) attributes. |
Payments |
|
Manage Supplier User Roles |
Supplier Portal in Procurement is provisioned and requires trading partner security. |
Manage roles that can be provisioned to supplier users. |
Supplier Portal or Sourcing |
|
Manage Supplier User Role Usages |
Supplier Portal in Procurement is provisioned and requires trading partner security. |
Manage the supplier roles that can be provisioned by supplier users, and set default roles for Supplier Portal or Sourcing, based on the set of supplier roles that are defined by performing the Manage Supplier User Roles task. |
Supplier Portal or Sourcing |
To start an Oracle Fusion Applications implementation, you must setup one or more initial users using the super user that was created during installation and provisioning of the Oracle Fusion Applications environment. Because Oracle Fusion Applications is secure as delivered, the process of enabling the necessary setup access for initial users requires several specialized steps when getting started with an implementation.
The following high level steps are required for starting an implementation.
As the Oracle Identity Management Administration user, provision the IT Security Manager job role with roles for user and role management.
This step enables the super user account, which is provisioned with the IT Security Manager job role, to create implementation users.
As the Oracle Fusion Applications installation super user, perform the following tasks once you have selected an offering to implement and generated the setup tasks needed to implement the offering.
Synchronize users and roles in the Lightweight Directory Access Protocol (LDAP) store with HCM user management by using the Run User and Roles Synchronization Process task.
Create an IT security manager user by using the Create Implementation Users task.
Provision the IT security manager with the IT Security Manager role by using the Provision Roles to Implementation Users task.
As the newly created IT security manager user, sign in to Oracle Fusion Applications and set up at least one implementation user for setting up enterprise structures.
Create an implementation user by using the Create Implementation Users task.
Provision the implementation user with the Application Implementation Manager job role or the Application Implementation Consultant job role by using the Provision Roles to Implementation Users task. The Application Implementation Consultant job role inherits from all product-specific application administrators and entitles the necessary View All access to all secured object.
Optionally, create a data role for an implementation user who needs only the limited access of a product-specific Application Administrator by using the Create Data Role for Implementation Users. Then assign the resulting data role to the implementation user by using the Provision Roles to Implementation Users task.
The figure shows the task flow from provisioning the IT Security Manager job role with the user and role management entitlement to creating and provisioning implementation users for enterprise setup.
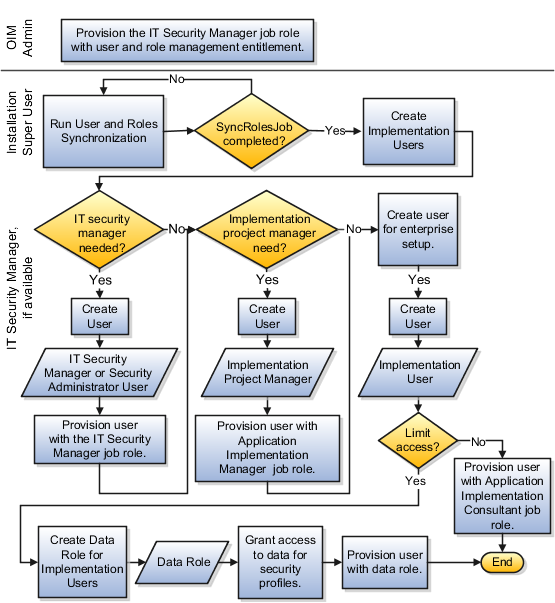
After installation and provisioning, and before setting up enterprise structures and implementing projects, you must establish required entitlement for the super user account and at least one implementation user to proceed with the implementation. Once initial enterprise structure setup is complete, additional users may be created through processes available in Human Capital Management (HCM).
Initial security administration consists of the following.
Preparing the IT Security Manager job role
Synchronizing users and roles from Lightweight Directory Access Protocol (LDAP) with HCM
Creating implementation users
Optionally creating data roles for implementation users
Provisioning implementation users with roles
Once the first implementation project begins and the enterprise work structure is set up, use standard user and security management processes such as the Manage Users task to create and manage additional users. Do not use the Create Implementation Users task after your enterprise has been set up.
Initially the super user is not provisioned to manage users and roles.
You must add the following Oracle Identity Management (OIM) roles to the IT Security Manager job role's role hierarchy to enable the super user to create one or more initial implementation users.
Identity User Administrators
Role Administrators
Additionally, you must assign the Xellerate Users organization to the IT Security Manager role.
After configuring an offering and setting up the task lists for implementation, the Run User and Roles Synchronization Process task is available to the super user for synchronizing users and roles in the LDAP store with Oracle Fusion Human Capital Management (HCM).
The super user is provisioned with roles that provide broad access to Oracle Fusion Middleware and Oracle Fusion Applications administration, and is not suitable as an implementation user in most enterprises. The super user should define at least one implementation user, which consists of creating the user account and provisioning it with at least the Application Implementation Consultant and Application Implementation Manager job roles.
As a security guideline, define an IT security manager user who in turn defines one or more implementation users to set up enterprise structures. The IT security manager users can provision the implementation user with the Application Implementation Consultant role, which entitles access to all enterprise structures. Or the IT security manager can create a data role that restricts access to enterprise structures of a specific product and provisioning that role.
Depending on the size of your implementation team, you may only need a single implementation user for security administration, implementation project management, enterprise structures setup, and application implementation. That single user must then be provisioned with all indicated roles, and therefore broad access.
The super user creates one or more implementation users by performing the Create Implementation Users task.
Note
This initial implementation user is a user account created in Oracle Identity Management only, specifically for setting up enterprise structures, and is not related to a real person or identity such as a user defined in HCM.
As an alternative to provisioning an implementation user with the Application Implementation Consultant role to access all enterprise structures, you may need implementation users with access restricted to enterprise structures for specific products. In this case, use the Create Data Roles for Implementation Users task to create a data role based on a job role with less broad access, such as the HCM Application Administrator job role.
After creating an implementation user, you must provision the user with one or more roles by performing the Provision Roles to Implementation Users task.
For example, assign a role to the implementation user that provides the access necessary for setting up the enterprise. Depending on need, provision to the implementation user the predefined Applications Implementation Consultant role or a product family-specific administrator data role, such as a data role based on the predefined Financials Applications Administrator.
Caution
The Application Implementation Consultant has broad access. It is a very useful role for experimentation or setting up a pilot environment, but may not be suitable for implementation users in a full implementation project.
This example illustrates initial security administration after having installed and provisioned an Oracle Fusion Applications environment.
In Oracle Fusion Applications, you manage users and security through Oracle Fusion Human Capital Management (HCM) user management flows, which are included in each of the offering task lists. However, the HCM task flows require that enterprise structures have been set up, and yet to add users who can set up enterprise structures you need to have set up HCM. Therefore, you need to create one or more initial implementation users who are responsible for providing the following.
Users and their applications security management
Implementation project management
Initial enterprise structures management
The following table summarizes key decisions for this scenario.
|
Decision |
In this Example |
|---|---|
|
How to sign in to Oracle Fusion Applications for the first time |
Use the super user account that was created when installing and provisioning Oracle Fusion Applications (for example, FAADMIN). |
|
How to ensure that the roles and users in the Lightweight Directory Access Protocol (LDAP) store match what is available for selection when defining implementation users |
Perform the Run User and Roles Synchronization Process task. |
|
How to create a first implementation user |
Prepare the IT Security Manager job role for user and role management so the super user and any other user provisioned with the IT Security Manager job role can manage users and roles. |
|
How to establish security administration users |
Define an IT security manager user provisioned with the IT Security Manager job role. |
|
How to establish an implementation user with access to set up enterprise structures |
Define an implementation user provisioned with the Application Implementation Consultant job role. |
You create an initial implementation user by performing the following tasks.
The Oracle Identity Management System Administrator user provisions the IT Security Manager job role with roles for user and role management.
The Oracle Fusion Applications super user synchronizes LDAP users with HCM user management so that users can be provisioned with roles through HCM.
The Oracle Fusion Applications super user performs the Create Implementation Users task to create one or more IT security manager and administrator users provisioned with security administrative entitlement.
The IT Security Manager user signs in to Oracle Fusion Applications and performs the Create Implementation Users task to create implementation managers and users.
The IT Security Manager user provisions implementation users for enterprise structure setup.
Note
The following tasks assume that the super user has configured an offering and set up task lists. When not following a task flow within an activity, you can find tasks in Navigator > Tools > Setup and Maintenance > All Tasks. Search for the task and click its Go to Task icon in the search results.
The super user that was created when installing and provisioning Oracle Fusion Applications (for example, FAADMIN) has all necessary access for implementing Oracle Fusion Applications and administering security. This access is provided by the following roles:
Application Implementation Consultant
IT Security Manager
Neither of these roles provides access needed for creating and managing Oracle Fusion Applications users. Therefore, you must add the following two OIM roles to the IT Security Manager role:
Identity User Administrators
Role Administrators
The following procedure is prerequisite to an IT security manager or administrator creating an initial one or more implementation users.
This accesses the Welcome to Identity Manager Delegated Administration menu.
In the Search Results, click the role's Display Name.
Click the arrow icon to show the list of available roles. Select IT Security Manager and move it to the Roles to Add list. Click Save.
In the Welcome to Identity Manager Delegated Administration menu (see step 1, above), in the Organizations list of tasks, click Advanced Search - Organizations.
Search for the Xellerate Users organization by entering Xellerate Users in Display Name and clicking Search.
In the Search Results, click the organization's Display Name. The Xellerate Users page appears.
Click the Administrative Roles link in the row of links above the Xellerate Users.
In Filter By Role Name of the Details window, enter the following string:
*IT_SECURITY_MANAGER*
Click Find.
Enable Read, Write, Delete, and Assign.
Click Assign.
Click Confirm.
Lightweight Directory Access Protocol (LDAP) must be synchronized with HCM user management so that users can be provisioned with roles through HCM.
If you do not know the super user name and password, check with your system administrator or the person who installed Oracle Fusion Applications. For more information about account creation in Oracle Fusion Applications provisioning, see the Oracle Fusion Applications Installation Guide.
The SyncRolesJob process takes some time to complete the first time it is run.
The super user has broad access to Oracle Fusion Middleware and Oracle Fusion Applications administration. Due to this broad access, your enterprise needs users dedicated to managing users and applications security, such as an IT security manager user.
The Oracle Identity Manager appears.
For details, see the Creating Users section in the Oracle Fusion Middleware User's Guide for Oracle Identity Manager.
|
Attribute |
Value |
Example |
|---|---|---|
|
Last name |
<any valid string> |
Smith |
|
Organization |
Xellerate Users |
N/A |
|
User type |
Non Worker |
N/A |
|
User login |
<any valid string> |
IT_SECURITY_MANAGER |
|
Login password |
<any valid string> |
SeKur1TyPa$$w0Rd |
Note
In Oracle Fusion Applications, an implementation user is a user account created in OIM only, specifically for implementation tasks, and is not related to a real person or identity such as a user defined in HCM.
Application Implementation Manager
Application Implementation Consultant
Note
For an implementation to begin, at least one user must be provisioned with the Application Implementation Manager role, and another or the same user must be provisioned with the Application Implementation Consultant role. The Application Implementation Consultant has broad access too set up all enterprise structures.
After the implementation user has set up the enterprise, further security administration depends on the requirements of your enterprise.
The Define Security activity within the Information Technology (IT) Management business process includes the following tasks.
Import Worker Users
Import Partner Users
Manage Job Roles
Manage Duties
Manage Application Access Controls
If no legacy users, user accounts, roles, and role memberships are available in the Lightweight Directory Access Protocol (LDAP) store, and no legacy workers are available in Human Resources (HR), the implementation user sets up new users and user accounts and provisions them with roles available in the Oracle Fusion Applications reference implementation.
If no legacy identities (workers, suppliers, customers) exist to represent people in your enterprise, implementation users can create new identities in Human Capital Management (HCM), Supplier Portal, and Customer Relationship Management (CRM) Self Service, respectively, and associate them with users.
Oracle Identity Management (OIM) handles importing users.
If legacy employees, contingent workers, and their assignments exist, the HCM Application Administrator imports these definitions by performing the Load Batch Data task. If user and role provisioning rules have been defined, the Load Batch Data process automatically creates user and role provisioning requests as the workers are created.
Once the enterprise is set up, performing the Load Batch Data task populates the enterprise with HR workers in records linked by global user ID (GUID) to corresponding user accounts in the LDAP store. If no user accounts exist in the LDAP store, the Load Batch Data task results in new user accounts being created. Worker email addresses as an alternate input for the Load Batch Data task triggers a search of the LDAP for user GUIDs, which may perform more slowly than entering user names.
In the security reference implementation, the HCM Application Administrator job role hierarchy includes the HCM Batch Data Loading Duty role, which is entitled to import worker identities. This entitlement provides the access necessary to perform the Load Batch Data task in HCM.
Note
The Import Person and Organization task in the Define Trading Community Import activity imports the following resources, creates users, and links the resources to users for use in CRM.
Internal employees
Contingent workers
External partner contacts
Partner companies
Legal entities
Customers
Consumers
If role provisioning rules have been defined, the Import Person and Organization task automatically provisions role requests as the users are created.
If legacy users (identities) and user accounts exist outside the LDAP store that is being used by the Oracle Fusion Applications installation, the IT security manager has the option to import these definitions to the LDAP store by performing the Import Worker Users and Import Partner Users tasks.
If no legacy users or user accounts can be imported or exist in an LDAP repository accessible to Oracle Identity Management (OIM), the IT security manager creates users manually in OIM or uses the Load Batch Data task to create users from imported HR workers.
Once users exist, their access to Oracle Fusion Applications is dependent on the roles provisioned to them in OIM or Human Capital Management. Use the Manage HCM Role Provisioning Rules task to define rules that determine what roles are provisioned to users.
Importing user identities from other applications, including other Oracle Applications product lines, is either a data migration or manual task. Migrating data from other Oracle Applications includes user data. For more information about importing users, see the Oracle Fusion Middleware Developer's Guide for Oracle Identity Manager.
In the security reference implementation, the IT Security Manager job role hierarchy includes the HCM Batch Data Loading Duty and the Partner Account Administration Duty. These duty roles provide entitlement to import or create users. The entitlement Load Batch Data provides the access necessary to perform the Import Worker Users task in OIM. The entitlement Import Partner entitlement provides the access necessary to perform the Import Partner Users task in OIM.
Job and abstract roles are managed in OIM. This task includes creating and modifying job and abstract roles, but not managing role hierarchies of duties for the jobs.
Note
Manage Job Roles does not include provisioning job roles to users. Provisioning users is done in OIM, HCM, CRM or Oracle Fusion Supplier Portal.
Roles control access to application functions and data. Various types of roles identify the functions performed by users.
The Oracle Fusion Applications security reference implementation provides predefined job and abstract roles. In some cases, the jobs defined in your enterprise may differ from the predefined job roles in the security reference implementation. The predefined roles and role hierarchies in Oracle Fusion may require changes or your enterprise may require you to create new roles. For example, you need a job role for a petty cash administrator, in addition to an accounts payable manager. The security reference implementation includes a predefined Accounts Payable Manager, and you can create a petty cash administrator role to extend the reference implementation.
In the security reference implementation, the IT Security Manager job role hierarchy includes the Enterprise Role Management Duty role, which is entitled to manage job and abstract roles (the entitlement is Manage Enterprise Role). This entitlement provides the access necessary to perform the Manage Job Roles task in OIM.
A person with a job role must be able to perform certain duties. In the Oracle Fusion Applications security reference implementation, enterprise roles inherit duties through a role hierarchy. Each duty corresponds to a duty role. Duty roles specify the duties performed within applications and define the function and data access granted to the enterprise roles that inherit the duty roles.
Managing duties includes assigning duties to job and abstract roles in a role hierarchy using Authorization Policy Manager (APM). If your enterprise needs users to perform some actions in applications coexistent with Oracle Fusion applications, you may wish to remove the duty roles that enable those actions. For details about which duty roles are specific to the products in an offering, see the Oracle Fusion Applications Security Reference Manual for each offering.
OIM stores the role hierarchy and the spanning of roles across multiple pillars or logical partitions of applications.
In cases where your enterprise needs to provide access to custom functions, it may be necessary to create or modify the duty roles of the reference implementation.
Tip
As a security guideline, use only the predefined duty roles, unless you have added new applications functions. The predefined duty roles fully represent the functions and data that must be accessed by application users and contain all appropriate entitlement. The predefined duty roles are inherently without segregation of duty violations of the constraints used by the Application Access Controls Governor.
In the security reference implementation, the IT Security Manager job role hierarchy includes the Application Role Management Duty role, which is entitled to manage duty roles (the entitlement is Manage Application Role). This entitlement provides the access necessary to perform the Manage Duties task in APM.
Note
Product family administrators are not entitled to create role hierarchies or manage duty roles and must work with the IT security manager to make changes such as localizing a duty role to change a role hierarchy. Setup for localizations is documented in HCM documentation.
Prevent or limit the business activities that a single person may initiate or validate by managing segregation of duties policies in the Application Access Controls Governor (AACG) .
Note
In AACG, segregation of duties policies are called access controls or segregation of duties controls.
In the security reference implementation, the IT Security Manager job role hierarchy includes the Segregation of Duties Policy Management Duty role, which is entitled to manage segregation of duties policies (the entitlement is Manage Segregation of Duties Policy). This entitlement provides the access necessary to perform the Manage Application Access Controls task in AACG.
After the implementation user has set up the enterprise, further security administration depends on the requirements of your enterprise.
The Define Data Security activity within the Information Technology (IT) Management business process includes the following tasks.
Manage Data Access Sets
Manage Segment Security
Manage Role Templates
Manage Data Security Policies
Manage Encryption Keys
These tasks address data security administration. For information on using the user interface pages for setting up and managing data security, see the Oracle Fusion Middleware Administrator's Guide for Authorization Policy Manager (Oracle Fusion Applications edition).
Note
The Manage Data Role and Security Profiles task, and all other HCM security profile setup tasks are documented in Human Capital Management (HCM) documentation.
Data access sets define a set of access privileges to one or more ledgers or ledger sets.
The information on ledgers that are attached to data access sets are secured by function security. Users must have access to the segment values associated with the data access sets to access the corresponding GL account.
In the security reference implementation, the IT Security Manager job role hierarchy includes the Data Access Administration Duty role, which is entitled to manage data access sets (the entitlement is Define General Ledger Data Access Set). This entitlement provides the access necessary to perform the Manage Data Access Sets task in General Ledger.
Balancing or management segment values can secure data within a ledger.
Segment values are stored in GL_ACCESS_SET_ASSIGNMENTS and secured by restrictions, such as Exclude, on parameters that control the set of values that a user can use during data entry.
In the security reference implementation, the IT Security Manager job role hierarchy includes the Application Key Flexfield Administration Duty role, which is entitled to manage application key flexfields (the entitlement is Manage Application Key Flexfield). This entitlement provides the access necessary to perform the Manage Segment Security task in General Ledger.
Data role templates automatically create or update data roles based on dimensions such as business unit. As an enterprise expands, data role templates trigger replication of roles for added dimensions. For example, when creating a new business unit, a data role template generates a new Accounts Payables Manager data role based on the Financials Common Module Template for Business Unit Security data role template.
In the security reference implementation, the IT Security Manager job role hierarchy includes the Application Role Management Duty role, which is entitled to manage data role templates (the entitlement is Manage Role Template). This entitlement provides the access necessary to perform the Manage Role Templates task in APM.
Data security grants provisioned to roles are data security policies. The security reference implementation provides a comprehensive set of predefined data security policies and predetermined data security policies based on data role templates.
Data security policies are available for review in Authorization Policy Manager (APM). Data security policies are implemented by grants stored in Oracle Fusion Data Security (FND_GRANTS).
Data security policies secure the database resources of an enterprise. Database resources are predefined applications data objects and should not be changed. However, for cases where custom database resources must be secured objects, the IT security manager is entitled to manage database resources and create new data security policies.
Warning
Review but do not modify HCM data security policies in APM except as a custom implementation. Use the HCM Manage Data Role And Security Profiles task to generate the necessary data security policies and data roles.
In the security reference implementation, the IT Security Manager job role hierarchy includes the Application Role Management Duty role, which is entitled to manage data security policies (the entitlement is Manage Data Security Policy). This entitlement provides the access necessary to perform the Manage Data Security Policies task in APM.
Create or edit encryption keys held in Oracle Wallet to secure Personally Identifiable Information (PII) attributes This task is only available when Payments is implemented.
In the security reference implementation, the IT Security Manager job role hierarchy includes the Payments Data Security Administration Duty role, which is entitled to manage encryption keys that secure PII (the entitlement is Manage Wallet). This entitlement provides the access necessary to perform the Manage Encryptions Keys task in Payments.
Trading partner access can be secured with user roles and user role usages for suppliers.
Trading Partner Security tasks within the Information Technology (IT) Management business process are:
Manage Supplier User Roles
Manage Supplier User Role Usages
This task manages roles that the supplier administrator can provision to supplier users, and is only available when the Supplier Portal or Sourcing are implemented.
In the security reference implementation, the IT Security Manager job role hierarchy includes the User Management Duty role, which is entitled to create and manage users (the entitlement is Manage User Principal). This entitlement provides the access necessary to perform the Create Implementation Users task in OIM.
In the security reference implementation the IT Security Manager job role hierarchy includes the Supplier User Role Management Duty role, which is entitled to manage supplier user roles (the entitlement is Manage Supplier User Roles). This entitlement provides the access necessary to perform the Manage Supplier User Roles task in the Supplier Portal or Sourcing.
This task manages the set of roles and default roles that supplier users can provision based on the roles that are defined by the Manage Supplier User Roles task.
This task is only available when the Supplier Portal or Sourcing are implemented.
In the security reference implementation, the IT Security Manager job role hierarchy includes the Supplier Portal Configuration Management Duty role, which is entitled to manage supplier user roles (the entitlement is Manage Supplier User Role Usages). This entitlement provides the access necessary to perform the Manage Supplier User Roles Usages task in the Supplier Portal or Sourcing.
Various changes to your enterprise require security adjustments.
New enterprise roles
Reorganization
Note
Oracle Fusion Applications security does not require security adjustments after HCM changes, such as when a person changes to another job, because their provisioned roles are automatically revoked and recalculated based on role provisioning rules.
You may be adding new abstract or job roles or both, and the data role templates in your deployment may be generating new data roles as you set up new dimensions.
As a security guideline, adjust your role provisioning rules so these new roles are appropriately provisioned.
Tip
Review data role templates to identify newly generated data roles after enterprise setup changes. For example, the Financials Common Module Template for Business Unit generates new data roles after you create a new business unit. These data roles need to be provisioned.
You may create a new business unit or combine existing business units.
Securing the change may require security tasks including the following.
Changes to role provisioning rules for new or obsolete data roles.
The top security administration tasks for IT security managers and security administrators are the ones required or most likely necessary in setting up and implementing Oracle Fusion Applications security.
Top security tasks include the following.
Top initial security setup tasks
Top tasks for defining security implementation
Top security administration tasks
The top initial security setup tasks are as follows.
|
Security task |
Importance to managing risk |
Frequency |
Notes |
|---|---|---|---|
|
1. Import Worker Users |
Low |
Depends on need |
|
|
2. Create Implementation Users |
Low |
Required |
Task flow includes provisioning roles to a new implementation user |
|
3. Provision Roles to Implementation Users |
High |
Optional |
Used for provisioning additional roles, such as data roles |
After reviewing the security reference implementation, as presented in the Security Reference Manual for each offering, the top tasks for defining security implementation are as follows.
|
Security task |
Importance to managing risk |
Frequency |
Notes |
|---|---|---|---|
|
4. Implement predefined data security policies by generating data roles (if appropriate) and HCM security profiles. |
High |
Depends on need |
To understand what data roles are available, review the predefined data role templates and HCM security profiles. Once data roles are generated based on your implementation of data role templates and Human Capital Management (HCM) security profiles, modify or define role |
|
5. Manage Data Security Policies when customizing, such as when adding a database resource (table) |
High |
Initially or when new database resources needs to be secured |
To understand the data security provided by the Oracle Fusion Applications security reference implementation, it is important to review the predefined data security policies. |
|
6. Manage Duties |
High |
Initially or when new jobs are defined |
To understand the Oracle Fusion Applications security reference implementation and the job roles available for provisioning to users, it is important to understand the duty roles inherited by those job roles. As a security guideline, duty roles should not be changed, only their participation in role hierarchies. |
The top security administration tasks are as follows.
|
Security Task |
Importance to managing risk |
Frequency |
Notes |
|---|---|---|---|
|
7. Approve User and Role Provisioning Requests |
High |
Infrequent |
Provisioning requests are pre-approved in HCM. This task can be set up to be manual. Approvals are required when provisioning a role in HCM causes a segregation of duties (SOD) violation. |
|
8. Assign User Roles |
Low |
Never - this task is in Workforce Deployment and performed by HCM roles or when provisioning supplier users in Supplier Portal |
The Oracle Fusion Applications security reference implementation provides abstract, job, and data roles available for provisioning to user. Without provisioned roles, users are not authorized to access the portions of Oracle Fusion applications necessary to perform their duties. |
|
9. View segregation of duties (SOD) policy conflicts and violations |
High |
Infrequent |
Significant where reference security implementation changes |
Use the Manage Duties task to view the duties inherited by a role. To perform this task, you'll use the integrated Authorization Policy Manager.
Each logical partition or pillar contains a collection of application roles representing duties, and function and data security policies carried by those roles.
Use the Manage Duties task to view the entitlement carried by the duty roles in a role hierarchy, or policies carried by enterprise roles. To perform this task, you'll use the integrated Authorization Policy Manager.
The Lightweight Directory Access Protocol (LDAP) policy store stores application roles representing duties, and the identity store stores enterprise roles.
Use the Manage Job Roles task to create a hierarchy of enterprise roles. To perform this task, you'll use the integrated Oracle Identity Management UI pages.
Use the Manage Duties task to create a hierarchy of duty roles. To perform this task, you'll use the integrated Authorization Policy Manager.
The Lightweight Directory Access Protocol (LDAP) stores the role hierarchy and the spanning of roles across multiple pillars or logical partitions. The policy store stores duty roles. The identity store stores enterprise roles.
Use the Manage Job Roles task to create a hierarchy of enterprise roles. Use the integrated Oracle Identity Management UI pages to perform this task
User the Manage Duties task to create a hierarchy of applications roles. Use the integrated Authorization Policy Manager to perform this task.
Some duty roles may enable actions and their associated users interface features that your enterprise does not want users to perform in Oracle Fusion applications.
Use the following tasks to view the job, abstract, and data roles provisioned to a user.
Create Job Roles
Manage Job Roles
Use the integrated Oracle Identity Management UI pages to perform these tasks. The Lightweight Directory Access Protocol (LDAP) identity store stores enterprise roles.
Yes, but this should only be necessary if you have extended your Oracle Fusion Applications with new duties involving custom objects or functions that must be secured.
Use the Manage Duties task to create a duty role. To perform this task, you'll use the integrated Authorization Policy Manager.
Use the Manage Segregation of Duties Policies task to view segregation of duties policies. Use the integrated Application Access Controls Governor (AACG) in Governance, Risk, and Compliance Controls (GRCC) to perform this task.
The Oracle Fusion Applications security reference manual (SRM) for each offering documents the segregation of duties (SOD) policies respected within each job role.
Use the Manage Application Access Controls task to view segregation of duties policy violations carried by the duty roles inherited by a job role. Use the integrated Application Access Controls Governor (AACG) in Governance, Risk, and Compliance Controls (GRCC) to perform this task.
The Oracle Fusion Applications security reference manual (SRM) for each offering documents the segregation of duties (SOD) policies respected within each job role.
Use the Manage Data Security Policies task to view or change data security policies. To perform this task, you'll use the integrated Authorization Policy Manager or data security pages provided by Oracle Fusion Middleware Extensions for Applications (Applications Core).
Oracle Fusion Data Security stores data security policies in the policy store.
Use the Manage Role Templates task to define which data roles are generated. To perform this task, you'll use the integrated Authorization Policy Manager.
Use the Manage Data Roles and Security Profiles task to define which HCM data roles are generated. To perform this task, you'll use Oracle Fusion Human Capital Management (HCM).
These tasks may trigger the need for revised role provisioning rules to ensure that new data roles are appropriately provisioned to users.
Use the Manage Data Security Policies task to create new data security policies. Data security policies can also be created by generating data roles based on data role templates or HCM security profiles. To perform this task, you'll use the integrated Authorization Policy Manager or data security pages provided by Oracle Fusion Middleware Extensions for Applications (Applications Core).
Oracle Fusion Data Security stores data security policies in the policy store.
Use the Manage Role Templates task to view, create, or change data role templates. Use the integrated Authorization Policy Manager to perform the Manage Role Templates task.
Use the Manage Data Security Policies task to secure objects. To perform this task, you'll use the integrated Authorization Policy Manager or data security pages provided by Oracle Fusion Middleware Extensions for Applications (Applications Core).
Use the Manage Encryption Keys task, which is available in Oracle Fusion Payments.
Use the Manage Data Access Sets task, which is available in Oracle Fusion General Ledger.
Use the Manage Security Segments task, which is available in Oracle Fusion General Ledger.
If a user believes a necessary task is missing from their list of tasks, they may need to be provisioned with different or additional roles.
Access is provisioned to users based on their position or job, which consists of the duties performed in that job. Provisioned enterprise roles provide access by means of inherited duty roles.
The duty roles in a role hierarchy carry entitlement to access functions and data. Duty roles are not provisioned directly to users but granted to enterprise roles in a role hierarchy. As a security guideline, refrain from changing the privileges of the duty role's entitlement. If more or less entitlement is required by an enterprise role, change the role hierarchy that defines the enterprise role instead.
Users are generally provisioned with roles based on role provisioning rules. If a user requests being provisioned with a role to access a task, use the security considerations of your enterprise and the roles available in your security reference implementation to determine which roles are appropriate.
Use the following tasks to view the job, abstract, and data roles provisioned to a user.
Manage Users
Manage User Principal
Provision Roles to Implementation Users
Use Human Capital Management and integrated Oracle Identity Management UI pages to perform these tasks. Users, roles, and provisioning information are stored in Lightweight Directory Access Protocol (LDAP) stores.
Use the Manage Users task to create new users. Use Human Capital Management (HCM) pages to perform this task.
When you create a new worker, HCM creates a new user and identity.
The Hire Employee and Add Contingent Worker tasks also result in new user creation requests.
Creating a new user automatically triggers role provisioning requests based on role provisioning rules.
Note
If you are creating new implementation users for setting up your enterprise, use the Create Implementation Users task. Use the integrated Oracle Identity Management UI pages to perform this task.
Use the following tasks to provision roles to users.
Manage Users
Provision Roles to Implementation Users
The Manage Users task is available in Oracle Fusion Human Capital Management (HCM), Oracle Fusion Customer Relationship Management (CRM) and Oracle Fusion Suppliers.
Implementation users are provisioned through Oracle Identity Management (OIM) when HCM is not setup at the start of the implementation. The Provision Roles to Implementation Users is not needed once implementation is complete. Once HCM is setup, HCM is used to provision roles to non-implementation users by performing the Manage Users task. Human Resources (HR) transaction flows such as Hire and Promote also provision roles.
Use Oracle Enterprise Manager to view audit logs. Viewing audit logs is an Oracle Fusion Middleware function and not represented by an Oracle Fusion Applications business process model (BPM) task.