11g Release 6 (11.1.6)
Part Number E16689-06
Home
Contents
Book
List
Contact
Us
|
Oracle® Fusion
Applications Security Guide 11g Release 6 (11.1.6) Part Number E16689-06 |
Home |
Contents |
Book List |
Contact Us |
|
Previous |
Next |
Database Resources and Data Security Policies: How They Work Together
Securing Data Access: Points to Consider
Data Role Templates: Explained
By default, users are denied access to all data.
Data security makes data available to users by the following means.
Policies that define grants available through provisioned roles
Policies defined in application code
You secure data by provisioning roles that provide the necessary access. Enterprise roles provide access to data through data security policies defined for the inherited application roles.
When setting up the enterprise with structures such as business units, data roles are automatically generated that inherit job roles based on data role templates. Data roles also can be generated based on HCM security profiles. Data role templates and HCM security profiles enable defining the instance sets specified in data security policies.
When you provision a job role to a user, the job role implicitly limits data access based on the data security policies of the inherited duty roles. When you provision a data role to a user, the data role explicitly limits the data access of the inherited job role to a dimension of data.
Data security consists of privileges conditionally granted to a role and used to control access to the data. A privilege is a single, real world action on a single business object. A data security policy is a grant of a set of privileges to a principal on an object or attribute group for a given condition. A grant authorizes a role, the grantee, to actions on a set of database resources. A database resource is an object, object instance, or object instance set. An entitlement is one or more allowable actions applied to a set of database resources.
Data is secured by the following means.
|
Data security feature |
Does what? |
|---|---|
|
Data security policy |
Grants access to roles by means of entitlement |
|
Role |
Applies data security policies with conditions to users through role provisioning. |
|
Data role template |
Defines the data roles generated based on enterprise setup of data dimensions such as business unit. |
|
HCM security profile |
Defines data security conditions on instances of object types such as person records, positions, and document types without requiring users to enter SQL code |
|
Masking |
Hides private data on non-production database instances |
|
Encryption |
Scrambles data to prevent users without decryption authorization from reading secured data |
The sets of data that a user can access via roles are defined in Oracle Fusion Data Security. Oracle Fusion Data Security integrates with Oracle Platform Security Services (OPSS) to entitle users or roles (which are stored externally) with access to data. Users are granted access through the entitlement assigned to the roles or role hierarchy with which the user is provisioned. Conditions are WHERE clauses that specify access within a particular dimension, such as by business unit to which the user is authorized.
Data security policies articulate the security requirement "Who can do What on Which set of data," where 'Which set of data' is an entire object or an object instance or object instance set and 'What' is the object entitlement.
For example, accounts payable managers can view AP disbursements for their business unit.
|
Who |
can do |
what |
on which set of data |
|---|---|---|---|
|
Accounts payable managers |
view |
AP disbursements |
for their business unit |
A data security policy is a statement in a natural language, such as English, that typically defines the grant by which a role secures business objects. The grant records the following.
Table or view
Entitlement (actions expressed by privileges)
Instance set (data identified by the condition)
For example, disbursement is a business object that an accounts payable manager can manage by payment function for any employee expenses in the payment process.
Note
Some data security policies are not defined as grants but directly in applications code. The security reference manuals for Oracle Fusion Applications offerings differentiate between data security policies that define a grant and data security policies defined in Oracle Fusion applications code.
A business object participating in a data security policy is the database resource of the policy.
Data security policies that use job or duty roles refer to data security entitlement.
For example, the data security policy for the Accounts Payable Manager job role refers to the view action on AP disbursements as the data security entitlement.
Important
The duty roles inherited by the job role can be moved and job roles reassembled without having to modify the data security.
As a security guideline, data security policies based on user session context should entitle a duty role. This keeps both function and data security policies at the duty role level, thus reducing errors.
For example, a Sales Party Management Duty can update Sales Party where the provisioned user is a member of the territory associated with the sales account. Or the Sales Party Management Duty can update Sales Party where the provisioned user is in the management chain of a resource who is on the sales account team with edit access. Or the Participant Interaction Management Duty can view an Interaction where the provisioned user is a participant of the Interaction.
For example, the Disbursement Process Management Duty role includes entitlement to build documents payable into payments. The Accounts Payable Manager job role inherits the Disbursement Process Management Duty role. Data security policies for the Disbursement Process Management Duty role authorize access to data associated with business objects such as AP disbursements within a business unit. As a result, the user provisioned with the Accounts Payable Manager job role is authorized to view AP disbursements within their business unit.
A data security policy identifies the entitlement (the actions that can be made on logical business objects or dashboards), the roles that can perform those actions, and the conditions that limit access. Conditions are readable WHERE clauses. The WHERE clause is defined in the data as an instance set and this is then referenced on a grant that also records the table name and required entitlement.
Data roles are implemented as job roles for a defined set of data.
A data role defines a dimension of data within which a job is performed. The data role inherits the job role that describes the job. For example, a data role entitles a user to perform a job in a business unit.
The data role inherits abstract or job roles and is granted data security privileges. Data roles carry the function security privileges inherited from job roles and also the data security privilege granted on database objects and table rows.
For example, an accounts payables specialist in the US Business Unit may be assigned the data role Accounts Payables Specialist - US Business Unit. This data role inherits the job role Accounts Payables Specialist and grants access to transactions in the US Business Unit.
A data role may be granted entitlement over a set people.
For example, a Benefits Administrator A-E is allowed to administer benefits for all people that have a surname that begins with A-E.
Data roles are created using data role templates. You create and maintain data roles in the Authorization Policy Manager (APM). Use the Manage Data Roles and Security Profiles task to create and maintain HCM data roles in Oracle Fusion HCM.
HCM security profiles are used to secure HCM data, such as people and departments. You use HCM security profiles to generate grants for an enterprise role. The resulting data role with its role hierarchy and grants operates in the same way as any other data role.
For example, an HCM security profile identifies all employees in the Finance division.
Oracle Fusion Payroll uses HCM security profiles to secure project organizations. Applications outside of HCM can use the HCM Data Roles UI pages to give their roles access to HR people.
Oracle Fusion Applications uses masking to protect sensitive data from view by unauthorized users. Encryption APIs mask sensitive fields in applications user interfaces. Additionally, Oracle Data Masking is available for masking data in non-production instances and Oracle Transparent Data Encryption is available for protecting data in transit or in backups independent of managing encryption keys.
A data security policy applies a condition and allowable actions to a database resource for a role. When that role is provisioned to a user, the user has access to data defined by the policy. In the case of the predefined security reference implementation, this role is always a duty role. Data roles generated to inherit the job role based on data role templates limit access to database resources in a particular dimension, such as the US business unit.
The database resource defines and instance of a data object. The data object is a table, view, or flexfield.
The following figure shows the database resource definition as the means by which a data security policy secures a data object. The database resource names the data object. The data security policy grants to a role access to that database resource based on the policy's action and condition.
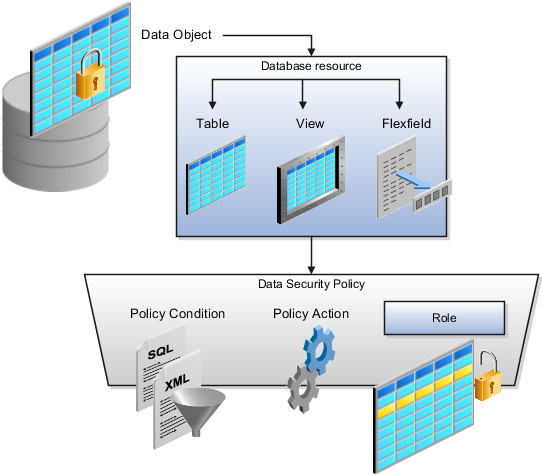
A database resource specifies access to a table, view, or flexfield that is secured by a data security policy.
Name providing a means of identifying the database resource
Data object to which the database resource points
Data security policies consist of actions and conditions for accessing all, some, or a single row of a database resource.
Condition identifying the instance set of values in the data object
Action specifying the type of access allowed on the available values
Note
If the data security policy needs to be less restrictive than any available database resource for a data object, define a new data security policy.
Actions correspond to privileges that entitle kinds of access to objects, such as view, edit, or delete. The actions allowed by a data security policy include all or a subset of the actions that exist for the database resource.
A condition is either a SQL predicate or an XML filter. A condition expresses the values in the data object by a search operator or a relationship in a tree hierarchy. A SQL predicate, unlike an XML filter, is entered in a text field in the data security user interface pages and supports more complex filtering than an XML filter, such as nesting of conditions or sub queries. An XML filter, unlike a SQL predicate, is assembled from choices in the UI pages as an AND statement.
Tip
An XML filter can be effective in downstream processes such as business intelligence metrics. A SQL predicate cannot be used in downstream metrics.
Oracle Fusion Applications supports securing data through role-based access control (RBAC) by the following methods.
|
Method of securing data |
Reason |
Example |
|---|---|---|
|
Data roles apply explicit data security policies on job and abstract roles |
Appropriate for job and abstract roles that should only access a subset of data, as defined by the data role template that generates the data role or by HCM security profiles. |
Accounts Payable Manager - US data role to provide an accounts payable manager in the US business unit with access to invoices in the US business unit. |
|
Data security policies |
Define data access for application roles and provide inheriting job and abstract roles with implicit data security |
Projects |
If a user has access to the same function through different roles that access different data sets, then the user has access to a union of those data sets.
When a runtime session is created, Oracle Platform Security Services (OPSS) propagates only the necessary user to role mapping based on Oracle Fusion Data Security grants. A grant can specify entitlement to the following.
Specific rows of data (data object) identified by primary key
Groups of data (instance set) based on a predicate that names a particular parameter
Data objects or instance sets based on runtime user session variables
Data is either identified by the primary key value of the row in the table where the data is stored. Or data is identified by a rule (SQL predicate) applied to the WHERE clause of a query against the table where the data is stored.
Oracle Fusion Data Security can be used to restrict the following.
Rows that are returned by a given query based on the intended business operation
Actions that are available for a given row
Grants control which data a user can access.
Note
Attribute level security using grants requires a data security policy to secure the attribute and the entitlement check enforces that policy.
A grant logically joins a user or role and an entitlement
with a static or parameterized object instance set. For example, REGION='WEST' is a static object instance set
and REGION=&GRANT_ALIAS.PARAMETER1 is a parameterized object instance set. In the context of a specific
object instance, grants specify the allowable actions on the set of
accessible object instances. In the database, grants are stored in
FND_GRANTS and object instance sets are stored in FND_OBJECT_INSTANCE_SETS.
Object access can be tested using the privilege check application
programming interface (API).
A business object is a logical entity that is typically implemented as a table or view, and corresponds to a physical database resource. The data security policies of the security reference implementation secure predefined database resources. Use the Manage Data Security Policies task to define and register other database resources.
Data security policies identify sets of data on the registered business object and the actions that may be performed on the business object by a role The grant can be made by data instance, instance set or at a global level..
Note
Use parameterized object instance sets whenever feasible to reduce the number of predicates the database parses and the number of administrative intervention required as static object instances sets become obsolete. In HCM, security profiles generate the instance sets.
You use data role templates to generate data roles. You generate such data roles, and create and maintain data role templates in the Authorization Policy Manager (APM).
Note
HCM data roles are generated using the Manage Data Roles and Security Profiles task, which uses HCM security profiles, not data role templates, to define the data security condition.
The following attributes define a data role template.
Template name
Template description
Template group ID
Base roles
Data dimension
Data role naming rule
Data security policies
The data role template specifies which base roles to combine with which dimension values for a set of data security policies. The base roles are the parent job or abstract roles of the data roles.
Note
Abstract, job, and data roles are enterprise roles in Oracle Fusion Applications. Oracle Fusion Middleware products such as Oracle Identity Manager (OIM) and Authorization Policy Manager (APM) refer to enterprise roles as external roles. Duty roles are implemented as application roles in APM and scoped to individual Oracle Fusion Applications.
The dimension expresses stripes of data, such as territorial or geographic information you use to partition enterprise data. For example, business units are a type of dimension, and the values picked up for that dimension by the data role template as it creates data roles are the business units defined for your enterprise. The data role template constrains the generated data roles with grants of entitlement to access specific data resources with particular actions. The data role provides provisioned users with access to a dimensional subset of the data granted by a data security policy.
An example of a dimension is a business unit. An example of a dimension value is a specific business unit defined in your enterprise, such as US. An example of a data security policy is a grant to access a business object such as an invoice with a view entitlement.
When you generate data roles, the template applies the values of the dimension and participant data security policies to the group of base roles.
The template generates the data roles using a naming convention specified by the template's naming rule. The generated data roles are stored in the Lightweight Directory Access Protocol (LDAP) store. Once a data role is generated, you provision it to users. A user provisioned with a data role is granted permission to access the data defined by the dimension and data security grant policies of the data role template.
For example, a data role template contains an Accounts Payable Specialist role and an Accounts Payable Manager role as its base roles, and region as its dimension, with the dimension values US and UK. The naming convention is [base-role-name]:[DIMENSION-CODE-NAME]. This data role template generates four data roles.
Accounts Payable Specialist - US (business unit)
Accounts Payable Specialist - UK (business unit)
Accounts Payable Manager - US (business unit)
Accounts Payable Manager - UK (business unit)
If you add a base role to an existing data role template, you can generate a new set of data roles. If the naming rule is unchanged, existing data roles are overwritten.
If you remove a base role from a data role template and regenerate data roles, a resulting invalid role list gives you the option to delete or disable the data roles that would be changed by that removal.
If you add a dimension value to your enterprise that is used by a data role template, you must regenerate roles from that data role template to create a data role for the new dimension. For example if you add a business unit to your enterprise, you must regenerate data roles from the data role templates that include business unit as a dimension.
If you add or remove a dimension value from your enterprise that is used to generate data roles, regenerating the set of data roles adds or removes the data roles for those dimension values. If your enterprise has scheduled regeneration as an Oracle Enterprise Scheduler Services process, the changes are made automatically.
For information on working with data role templates, see the Oracle Fusion Middleware Administrator's Guide for Authorization Policy Manager (Oracle Fusion Applications Edition).