Client certificate authentication implements two levels of security; Oracle HTTP Server establishes two-way trust between client and server, and Shared Services security verifies user identities based on client certificate. The illustrated concept:
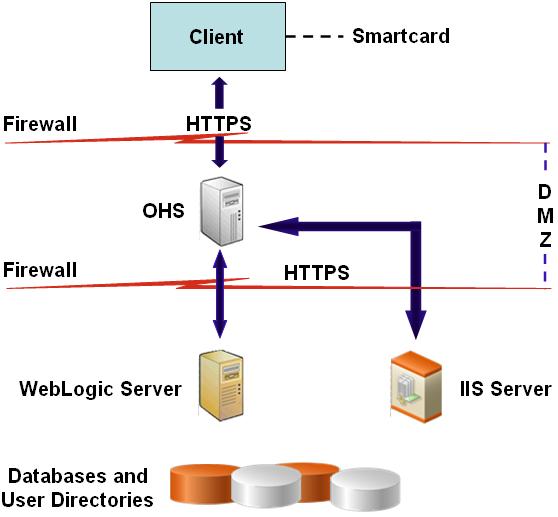
Note: | Oracle HTTP Server uses mod_wl_ohs for redirection to WebLogic Server and mod_proxy for redirection to IIS. |
The simplest implementation of client certificate authentication is when it is used for external communication (between the client and the web server or offloader) only. You can, however, enable two-way SSL among underlying EPM System components as well.
In a client certificate authentication implementation, a personal certificate (x509) issued to an EPM System user is used to authenticate the user. The personal certificate can be installed on a client machine or a smart card. Users are not prompted for a password.
Trust between components is established using the root certificate of the CA that the signed the component's certificate. You must ensure that the root CA certificate of a component is installed on each components with which it communicates. For example, to ensure SSL communication between Oracle HTTP Server and Foundation Services deployed on WebLogic Server, the root certificate of the CA that signed the WebLogic Server certificate must be installed on Oracle HTTP Server, and the root certificate of the CA that signed the Oracle HTTP Server certificate must be installed on WebLogic Server.
Note: | If you are not using a trusted third-party CA, to simplify the deployment process, Oracle recommends that you use the same CA to sign all server certificates. Self-signed certificates cannot be used to support client certificate authentication. |
Implementing client certificate authentication involves completing manual steps. See Configuring Client Certificate Authentication in EPM System.