Security options comprise the global parameters applicable to all user directories included in the search order.
 To set security options:
To set security options:
Launch Shared Services Console. See Launching Shared Services Console.
In Security Options, set global parameters.
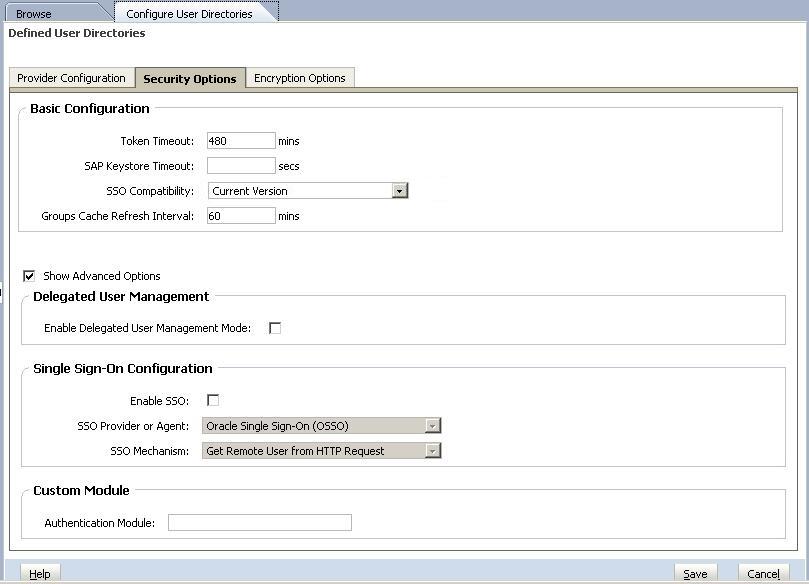
Table 7. Security Options for User Directories
Parameter Description Token Timeout Time (in minutes) after which the SSO token issued by EPM System products or the Web identity management solution expires. Users must log in again after this period. Token timeout is set based on the server's system clock. Note:
Token timeout is not the same as session timeout.
Example: 480
SAP Keystore Timeout The time limit (in seconds) for resolving the SAP keystore file. Default is 10. Example: 20
SSO Compatibility By default set to Current Version, which works for EPM System Release 11.1.2.1 components only. Select 11.1.2.0 and below if your deployment environment comprises components from previous EPM System releases. This setting supports backward compatibility of EPM System components.
Groups Cache Refresh Interval Interval (in minutes) for refreshing the Shared Services cache of groups to users relationship data. Default is 60 minutes. Shared Services caches information about new external user directory groups and new users added to existing groups only after the next cache refresh. Users provisioned through a newly created external user directory group do not get their provisioned roles until the cache is refreshed.
Example: 120
Show Advanced Options Option that allows you to display settings related to Delegated Administration and SSO configuration and custom authentication module class Enable Delegated User Management Mode Option enabling delegated user management of EPM System products to support the distributed management of provisioning activities. See Delegated User Management. Enable SSO Option enabling support for SSO from security agents such as Oracle Access Manager SSO Provider or Agent Select the Web identity management solution from which EPM System products should accept SSO. Select Other if your Web identity management solution; for example, Kerberos, is not listed. The preferred SSO method is automatically selected when you select the SSO provider. You can change the name of the HTTP header or custom login class, if required.
Note:
If you are using OSSO as the identity management solution, choose Other in SSO Provider or Agent, Custom HTTP Header in SSO Mechanism, and enter Proxy-Remote-User as the name of the custom HTTP header.
If you select Other as the SSO provider or agent, you must choose the SSO mechanism used by the agent. See “Supported SSO Methods” in the Oracle Hyperion Enterprise Performance Management System Security Administration Guide.
Custom HTTP Header: Set the name of the header that the agent passes to EPM System.
Custom Login Class: Specify the custom Java class that handles HTTP requests for authentication. See “Custom Login Class” in the Oracle Hyperion Enterprise Performance Management System Security Administration Guide.
Note:
This is not the same as custom authentication.
HTTP Authorization Header: The standard HTTP mechanism.
Get Remote User from HTTP Request: Select this option if the security agent populates the remote user in the HTTP request.
SSO Mechanism The method that the Web identity management solution uses to provide user's login name to EPM System products. For a description of acceptable SSO methods, see “Supported SSO Methods” in the Oracle Hyperion Enterprise Performance Management System Security Administration Guide. Authentication Module The fully qualified Java class name of the custom authentication module (for example, com.mycompany.epm.CustomAuthenticationImpl) that should be used to authenticate users on all user directories for which the custom authentication module is selected. The authentication module is used for a user directory only if the directory configuration has enabled (default) its use.
Foundation Services requires that the custom authentication JAR file be named CustomAuth.jar. CustomAuth.jar must be available in EPM_ORACLE_HOME/common/jlib/11.1.2.0. You can use any package structure and class name within the JAR file.For more information, see “Using a Custom Authentication Module” in the Oracle Hyperion Enterprise Performance Management System Security Administration Guide.