To set up Single Sign-on using CSS Token for external user directories (LDAP\MSAD), perform the following:
To set up Single Sign-on using CSS Token for external user directories (LDAP\MSAD), perform the following:
Oracle BI EE and Shared Services must be connected to the same LDAP or MSAD store.
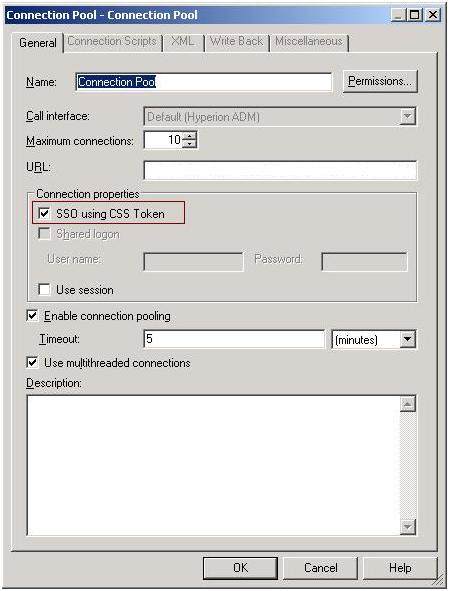
Open online rpd and go to HFM-Connection pool. Select the SSO using CSS Token and restart BI server.
Run the following command from Oracle BI EE installation path to set the CSS backward compatibility tag to true in OBIEE 11.1.1.5
For example: C:\OBIEE\instances\instance1\config\foundation\11.1.2.0> epmsys_registry.bat updateproperty SHARED_SERVICES_PRODUCT/@COMPATIBILITY 11120
Note:
If you are using EPM 11.1.2.x, then the compatibility setting is NOT required.
Download the regSyncUtil_OBIEE-TO-EPM.zip From details in bug 11725145. Unzip the utility and follow the instructions in the readme to run the utility.
Note:
This syncing of keys in the registry is only required when using EPM 11.1.2.x
You need to perform the following additional steps, if you are using the external user directory as MSAD:
IdentityAssertion Permission needs to be granted to css.jar, steps for which are
Confirm that BI Domain, mainly Admin Server is up and running
run wlst.sh or wlst.cmd available at $MW_HOME/oracle_common/common/bin
execute WLST connect command as shown below:
connect("<WLS_ADMIN_USERNAME>","<WLS_ADMIN_PASSWORD>","t3://<HOSTNAME>:<ADMIN_PORT>").
For example: wls:/offline> connect("Administrator","Admin123","t3://localhost:7001")
execute WLST runtime command as shown below:
runtime().
For example: wls:/bifoundation_domain/serverConfig> runtime()
execute WLST grantPermission command as shown below:
grantPermission(codeBaseURL="file:${hyperion.home}/common/CSS/11.1.2.0/lib/css.jar",permClass="oracle.security.jps.JpsPermission",permTarget="IdentityAssertion").
For example: wls:/bifoundation_domain/runtime>grantPermission(codeBaseURL="file:${hyperion.home}/common/CSS/11.1.2.0/lib/css.jar",permClass="oracle.security.jps.JpsPermission",permTarget="IdentityAssertion")
After successfully executing the grantPermission() command, the following information is displayed: Location changed to domainRuntime tree. This is a read-only tree with DomainMBean as the root. For more help, use help(domainRuntime).
If the IdentityAssertion Permission has already been granted to css.jar, after executing the above commands, the confirmation message is displayed.
Shutdown BI Domain including Admin Server and Managed Server(s) and any dependent OPMN Processes.
Download 13059356.zip from bug 13059356 and extract the zipped file to the following location: %BI_ORACLE_HOME%/OPatch/
Make sure %BI_ORACLE_HOME% has oraInst.Loc file. If it does not, browse to %BI_ORACLE_HOME%\bifoundation\provision\scripts\bidomain\inst and copy the oraInst-template.Loc to the %BI_ORACLE_HOME% location and rename it to oraInst.Loc
Invoke command prompt and change directory to %BI_ORACLE_HOME%/OPatch folder. Apply OPatch using following opatch command: opatch apply 13059356 -oh %BI_ORACLE_HOME% -jdk %BI_ORACLE_HOME%/jdk -invPtrLoc %BI_ORACLE_HOME%/oraInst.loc
A message displays the patch is applied successfully.
In case the above command does not work, and if any errors is displayed with the following message: The response file for OCM configuration does not exist (or) is not readable. Please provide a valid response file. Please perform the following:
Run the following command: %ORACLE_HOME%\ccr\bin\emocmrsp.bat -no_banner -output c:\out.rsp and then run the opatch command: opatch apply 13059356 -oh "c:\obiee\oracle_bi1" -ocmrf c:\out.rsp -jdk "c:\obiee\oracle_bi1\jdk" -invPtrLoc "c:\obiee\oracle_bi1\oraInst.loc"
Note:
The opatch must be applied successfully.
Note:
If the external directory is used as MSAD, then the above steps are additional requirements.
While configuring external user directory in OBIEE, if the “virtualize” property is set to true in the jps-config.xml file (<BI_DOMAIN_HOME>/config/fmwconfig/jps-config.xml), then perform the following:
Edit the setDomainEnv.cmd. From the following path: <BI_DOMAIN_HOME>/bin/ and add the following command lines:
Set EXTRA_JAVA_PROPERTIES=-Dcommon.components.home=%COMMON_COMPONENTS_HOME% -Didstore.identityAttribute=objectguid %EXTRA_JAVA_PROPERTIES% export EXTRA_JAVA_PROPERTIES
Based on the type of External user directory configured, the value of Didstore.identityAttribute needs to be set differently as shown below:
Microsoft Active Directory = objectguid
Oracle Internet Directory | Oracle Virtual Directory = orclguid
Novell EDirectory = guid
Sun One Directory = nsuniqueid
Open Ldap = entryuuid
If while configuring external user directory in OBIEE, if the “virtualize” property is set to false in the jps-config.xml file (<BI_DOMAIN_HOME>/config/fmwconfig/jps-config.xml ), then perform the following:
If only one External User directory is configured with default Unique Identity Attribute, as Authentication Provider in WLS Security Realm and ordered it as First provider in the stack, NO further action is required. In this case following DIRECTORY_TYPE=IDENTITY_ATTRIBUTE is used
Microsoft Active Directory = objectguid
Oracle Internet Directory | Oracle Virtual Directory = orclguid
Novell EDirectory = guid
Sun One Directory = nsuniqueid
Open Ldap = entryuuid
If External LDAP User Directory Authentication Provider in WLS Security Realm is configured to use Unique Identity Attribute different from above defaults, it should pass the Java System Property, idstore.identityAttribute, in BI Domain's setDomainEnv.sh file available at <BI_DOMAIN_HOME>/bin/
For example: set EXTRA_JAVA_PROPERTIES= -Dcommon.components.home=%COMMON_COMPONENTS_HOME% -Didstore.identityAttribute=customguid %EXTRA_JAVA_PROPERTIES% export EXTRA_JAVA_PROPERTIES
Restart BI Domain including Admin Server and Managed Server(s).
Restart OPMN Processes dependent on Admin or Managed Server(s).
Login using the external directory user credential to Oracle Financial Management Analytics and the user can view the dashboards.