| Oracle® Fusion Middleware Application Security Guide 11g Release 1 (11.1.1) Part Number E10043-12 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware Application Security Guide 11g Release 1 (11.1.1) Part Number E10043-12 |
|
|
PDF · Mobi · ePub |
The chapter outlines a set of recommended single sign-on solutions for Oracle Fusion Middleware. This chapter includes the following major sections:
Oracle Platform Security Services comprise Oracle WebLogic Server's internal security framework. A WebLogic domain uses a separate software component called an Authentication Provider to store, transport, and provide access to security data. Authentication Providers can use different types of systems to store security data. The Authentication Provider that WebLogic Server installs uses an embedded LDAP server.
Oracle Fusion Middleware 11g supports new single sign-on solutions that applications can use to establish and enforce perimeter authentication:
Customers must carefully choose the solution appropriate to their needs. Selecting the right SSO solution requires careful consideration and depends upon your requirements. This section outlines some general information and guidelines to help you choose the best solution for your needs.
Note:
Oracle recommends that you consider upgrading to Oracle Access Manager 11g Single Sign on solution to take advantage of additional functionality and architecture.
See Also:
Development or Small Stand-Alone Environment: Oracle recommends a light-weight SSO solution when deployed applications are not integrated into an enterprise-level single sign-on framework.
In such cases, a SAML-based solution that uses the Oracle WebLogic Server SAML Credential Mapping Provider is best. The embedded LDAP server is used as the default user repository. Alternatively, an LDAP Authenticator can be configured to leverage an external LDAP server as a user repository.
See Also:
"Configuring Single Sign-On with Web Browsers and HTTP Clients" in Oracle Fusion Middleware Securing Oracle WebLogic Server
Enterprise-Level SSO with Oracle Fusion Middleware 11g: Oracle Access Manager supports:
A wide variety of LDAP vendors as the user and group repository and also works with Oracle Virtual Directory
Integration with non-Oracle application server vendors and Web Tier components on a large variety of OS platforms to provide a flexible solution.
Oracle Access Manager 11g supports out-of-the-box integration with Oracle Fusion Middleware applications
Oracle Access Manager 11g (Release 1): Oracle recommends Oracle Access Manager 11g whether:
You are new to Oracle Fusion Middleware
You are considering a migration from OSSO
You are considering an enterprise-level SSO solution
You want to implement Identity Propagation with the OAM Token, as described in the Oracle Fusion Middleware Administrator's Guide for Oracle Access Manager with Oracle Security Token Service
Oracle Access Manager 10g (10.1.4.3): You can continue using this when you have:
Existing Oracle Access Manager 10g implementations
An enterprise-level SSO solution
Selecting the right Oracle Access Manager solution (11g versus 10g (10.1.4.3)) as your enterprise-level Single-Sign-on solution depends upon your requirements. Refer to product documentation in this chapter and in the respective administration guides to evaluate the release that best meets your overall requirements.
Existing OSSO 10g Customers: Oracle Single Sign-On is part of the 10g Oracle Application Server suite. OSSO is an enterprise-level single sign-on solution that works with the OC4J application server in conjunction with Oracle Internet Directory and Oracle HTTP Server 11g.
If OSSO is already in place as the enterprise solution for your existing Oracle deployment, Oracle Fusion Middleware continues to support the existing OSSO as a solution. However, Oracle recommends that you consider upgrading to Oracle Access Manager 11g Single Sign on solution, which is a strategic Oracle SSO solution. For more information when planning your upgrade, check the Lifetime Support Middleware Policy for the OSSO end of support dates at: http://www.oracle.com/support/lifetime-support-policy.html
See Also:
"Introduction: OAM Authentication Provider for WebLogic Server"
Oracle Fusion Middleware Upgrade Guide for Oracle Identity Management—For information about the types of Java EE environments available in 10g and instructions for upgrading those environments to Oracle Fusion Middleware 11g
Portal, Forms, Reports, and Discoverer 11g: Oracle Access Manager 11g is certified with Oracle Portal, Forms, Reports, and Discover 11g. With Oracle classic components, Oracle Delegated Administration Services 10g is a required and important feature of the Oracle Identity Management infrastructure.
See the Oracle Identity Management Guide to Delegated Administration in the Oracle Identity Management 10g (10.1.4.0.1) Online Documentation Library at:
http://www.oracle.com/technology/documentation/oim1014.html
See the Oracle Fusion Middleware Supported System Configurations page for more details:
http://www.oracle.com/technology/software/products/ias/files/fusion_certification.html
See Also:
The following topics and other 11g manuals:
"Introduction: OAM Authentication Provider for WebLogic Server"
Chapter 18, "Configuring Single Sign-On using OracleAS SSO 10g"
Oracle Fusion Middleware Administrator's Guide for Oracle Portal
Oracle Fusion Middleware Publishing Reports to the Web with Oracle Reports Services
Oracle Fusion Middleware Administrator's Guide for Oracle Business Intelligence Discoverer
Oracle Access Manager Integration with OSSO: Oracle recommends Oracle Access Manager 11g as the recommended enterprise-wide solution. If applications (Oracle Portal for example) are deployed that previously required OracleAS Single Sign-On, you can delegate the authentication (from OSSO 10g) to Oracle Access Manager 11g. Oracle Internet Directory is needed for applications that require integrating Oracle Access Manager and OSSO.
See Also:
"Introduction: OAM Authentication Provider for WebLogic Server"
Oracle Fusion Middleware Administrator's Guide for Oracle Access Manager for details about registering OSSO (mod_osso) Agents with Oracle Access Manager 11g to delegate authentication and for details about co-existence with Oracle Access Manager 11g during the OSSO 10g upgrade.
Oracle Fusion Middleware Upgrade Guide for Java EE—For information about the types of Java EE environments available in 10g and instructions for upgrading those environments to Oracle Fusion Middleware 11g
"Integrating with Oracle Application Servers" in the 10g (10.1.4.3) Oracle Access Manager Integration Guide.
Windows Native Authentication for Microsoft Clients: OSSO and Oracle Access Manager 11g both support this integration. Oracle WebLogic Server can be configured to use the Simple and Protected Negotiate (SPNEGO) mechanism for authentication to provide Windows Native Authentication support.
See Also:
The chapter on configuring Oracle Access Manager 11g to use Windows Native Authentication for Microsoft Clients in the Oracle Fusion Middleware Integration Guide for Oracle Access Manager
"Configuring Single Sign-On with Microsoft Clients" in Oracle Fusion Middleware Securing Oracle WebLogic Server
Unless explicitly stated, information here applies equally to both Oracle Access Manager 11g and 10g deployments.
The Oracle Access Manager Authentication Provider is one of several Providers that operate with Oracle WebLogic Server. The Oracle Access Manager Authentication Provider does not require the entire Oracle WebLogic Suite nor Oracle Java Required Files (JRF) to operate with Oracle Access Manager 11g or 10g.
In a WebLogic Server domain where JRF is installed, the JRF template is present as part of the domain in an Oracle Fusion Middleware product. In this case, the OAM Identity Asserter and OAM Authentication Provider are automatically available for configuration. If JRF is not installed in your WebLogic domain, you must add the OAMAuthnProvider.jar to a specific location in your domain as described later.
Note:
The JRF template is present as part of the domain in an Oracle Fusion Middleware product.
You can use the OAM Authentication Provider for WebLogic Server when you have:
Applications that are (or will be) deployed in a WebLogic container outside the Identity Management domain
WebGate is (or will be) deployed in front of the Authentication Provider
The Authentication Provider can be configured to provide either (or both) of the following functions for WebLogic users:
Identity Asserter for Single Sign-on Function
When the application is protected using a perimeter Webgate, the identity of the authenticated user that is communicated to the WebLogic Server is made available to container security layers using the Oracle Access Manager identity asserter. The Identity Asserter only asserts the incoming identity and then passes control to the configured Authentication Providers to continue with the rest of the authentication process (populating the subject with the right principals).
Note:
A Web-only applications implementation handles nearly all SSO use cases. The exception is when you have Oracle Web Services Manager protected Web services. In this case, there is no trusted WebGate. Instead the AccessGate provided with the Identity Asserter is contacted and interacts with your OAM 10g Access Server or 11g OAM Server; all other processing is essentially the same.
Oracle provides the following mechanisms, each with slightly different characteristics and requirements:
Trusted Header Assertion: This newest mechanism, for use with Oracle Access Manager 11.1.1.5.2 or later (and either a 10g or 11g Webgate), is triggered for the OAM_IDENTITY_ASSERTION token present for applications protected by 11g or 10g WebGate. This provides maximum security and is easy to configure.
Clear Text Header: This default mechanism is triggered for the OAM_REMOTE_USER token present for applications protected by 10g or 11g WebGate.
Session Token: This mechanism is available for use with only perimeter 10g Webgates and either the 10g Access Server or 11g OAM Server.
Table 15-1 lists the benefits and requirements for each.
Table 15-1 Summary: Identity Assertion Mechanisms for Oracle Access Manager
| Mechanism | Benefits | Requirements |
|---|---|---|
|
Trusted Header Assertion OAM_IDENTITY_ASSERTION |
Maximum security Easy configuration |
Oracle Access Manager 11.1.1.5.2 or later 10g or 11g Webgate |
|
Clear Text Header OAM_REMOTE_USER |
Maximum performance Default Mechanism |
Oracle Access Manager 11.1.1.5.0 10g or 11g Webgate |
|
Session Token (ObSSOCookie) To be deprecated |
10g Webgate with either OAM 10g or 11g Server |
Oracle Access Manager 11.1.1.3.0 Oracle Access Manager 10.1.4.3 10g Webgate |
Authenticator Function
The Authenticator function does not provide single sign-on. The Authenticator requests credentials from the user based on the authentication method specified in the application configuration file, web.xml, not according to the Oracle Access Manager authentication scheme. However, an Oracle Access Manager authentication scheme is required for the application domain.
Note:
You can skip this topic if you are using the Identity Asserter function.
For more information, see the following topics:
About Using the Identity Asserter Function with Oracle Access Manager
About Using the Authenticator Function with Oracle Access Manager
Choosing Applications for Oracle Access Manager SSO Scenarios and Solutions
This topic describes and illustrates the use of the Identity Asserter function with Oracle Access Manager 11g and 10g WebGates. Processing is similar, with few exceptions, whether you have OAM 11g with 11g (or 10g) WebGates or OAM 10g with 10g WebGates). For instance, with Oracle Access Manager 11g, the Access Server is known as the OAM Server.
All requests are first routed to a reverse proxy Web server and requests are intercepted by WebGate. The user is challenged for credentials based on the authentication scheme that is configured within Oracle Access Manager. Oracle recommends Form (form-based login) as the authentication scheme.
The Identity Asserter function relies on perimeter authentication performed by WebGate on the Web Tier. Triggering the Identity Asserter function requires the appropriate chosen Active Type for your WebGate release.
After triggering the Identity Asserter function, configured Authentication Providers (Login Modules) for constructing the Subject and populating it with the appropriate Principals are invoked.
Note:
The only difference between using the Identity Asserter function with 11g WebGates versus 10g WebGates is the provider's chosen Active Type.
Chosen Active Types
The Identity Asserter function's Active Type configuration parameter lists supported values under the Available UI section. One of the following must be selected as the "Chosen" type to trigger the Identity Asserter function:
Identity Assertion: Triggers Identity Assertion based on the trusted header OAM_IDENTITY_ASSERTION.
OAM_REMOTE_USER: Triggers Identity Assertion based on OAM_REMOTE_USER header.
ObSSOCookie: Triggers Identity Assertion based on the obSSOCookie.
OAM_REMOTE_USER header includes the uid of the logged in user. Configuring OAM_REMOTE_USER as the chosen Active Type for the Identity Asserter requires Oracle Access Manager policies that set OAM_REMOTE_USER as part of the authorization success response headers.
Authentication Processing and the Identity Assertion Function
Unless explicitly stated, information here applies equally to Oracle Access Manager 11g and Oracle Access Manager 10g.
WebGate, using the configured authentication scheme, authenticates the user, and then:
WebGate:
11g WebGate sets the OAMAuthnCookie and triggers the token (either OAM_IDENTITY_ASSERTION or OAM_REMOTE_USER).
10g WebGate triggers assertion based on the obSSOCookie or OAM_REMOTE_USER or OAM_IDENTITY_ASSERTION are possible
The OHS Web server mod_weblogic module forwards the request to Oracle WebLogic Server
Note:
mod_weblogic is the generic name of the WebLogic Server plug-in for Apache. For Oracle HTTP Server 11g, the name of this plug-in is mod_wl_ohs; the actual binary name is mod_wl_ohs.so.
The Identity Asserter is invoked when the configured Active token type is present in the request coming into the container: OAM_REMOTE_USER (default), obSSOCookie, OAM_IDENTITY_ASSERTION.
After Assertion Processing: Authentication Providers configured in the security realm are invoked to populate the 'Subject' with Principals (Users and Groups)
Figure 15-1, and the overview that follows, describe processing between components when the Identity Asserter function is used with Web-only applications. This implementation handles nearly all SSO use cases. Exception: Oracle Web Services Manager protected Web services. In this case, there is no trusted WebGate. Instead the AccessGate provided with the Identity Asserter (dotted line in Figure 15-1) is contacted and interacts with the 11g OAM Server (or 10g OAM Access Server); all other processing is essentially the same.
For more information, see "Oracle Access Manager Authentication Provider Parameter List".
Figure 15-1 illustrates the processing overview using the Identity Asserter configuration with Oracle Access Manager 11g and
Assertion takes place based on which token type is configured in the authorization policy. Alone, the presence of token in the request is not sufficient to invoke the asserter. Simply configuring a particular active token type in WebLogic is not sufficient OAM_IDENTITY_ASSERTION will be set in the request if it is configured in the authorization policy.
Process overview: Identity Assertion with OAM 11g, 11g WebGate, and Web-only applications
A user attempts to access an Oracle Access Manager protected Web application that is deployed on the Oracle WebLogic Server.
WebGate on a reverse proxy Web server intercepts the request and queries the OAM Server to determine whether the requested resource is protected.
If the requested resource is protected, WebGate challenges the user for credentials based on the type of Oracle Access Manager authentication scheme configured for the resource (Oracle recommends Form Login). The user presents credentials such as user name and password.
WebGate forwards the authentication request to the OAM Server.
OAM 11g Server validates user credentials against the primary user identity store and returns the response to WebGate (OAM 10g Access Server validates user credentials against configured user directories). Upon:
Successful Authentication: Processing continues with Step 6.
Authentication Not Successful: The login form appears asking the user for credentials again; no error is reported.
OAM Server generates the session token and sends it to the WebGate:
11g WebGate: Sets and returns the OAMAuthn cookie and triggers the OAM_REMOTE_USER (or OAM_IDENTITY_ASSERTER) token when policies are configured for this.
10g WebGate: Sets and returns OAM_REMOTE_USER or OAM_IDENTITY_ASSERTION headers in the request when policies are configured for this.
The Web server forwards this request to the proxy, which in turn forwards the request to the Oracle WebLogic Server using the mod_weblogic plug-in.
mod_weblogic forwards requests as directed by its configuration.
Note:
mod_weblogic is the generic name of the WebLogic Server plug-in for Apache For Oracle HTTP Server 11g, the name of this plug-in is mod_wl_ohs.
WebLogic Server security service invokes the Oracle Access Manager Identity Asserter which is configured to accept tokens of type "OAM_REMOTE_USER" (or "OAM_IDENTITY_ASSERTER"). The Identity Asserter initializes a CallbackHandler with the header. In addition, the Identity Asserter sets up NameCallback with the username for downstream LoginModules.
Oracle WebLogic Security service authorizes the user and allows access to the requested resource.
A response is sent back to the reverse proxy Web server.
A response is sent back to the browser.
This topic describes and illustrates use of the Authenticator configured to protect access to Web and non-Web resources with Oracle Access Manager.
Note:
Unless explicitly stated, information applies equally to Oracle Access Manager 11g and Oracle Access Manager 10g.
The Authenticator function relies on Oracle Access Manager services to authenticate users who access applications deployed in WebLogic Server. Users are authenticated based on their credentials, such as a user name and password.
When a user attempts to access a protected resource, the Oracle WebLogic Server challenges the user for credentials according to the authentication method specified in the application's web.xml file. Oracle WebLogic Server then invokes the Authentication Provider, which passes the credentials to Oracle Access Manager Access Server for validation through the enterprise directory server.
Figure 15-2 illustrates the distribution of components and flow of information for Oracle Access Manager authentication for Web and non-Web resources. Details follow the figure. In this case, the Authenticator communicates with the 11g OAM Server (or the OAM 10g Access Server) through a custom AccessGate.
Figure 15-2 Authenticator for Web and non-Web Resources
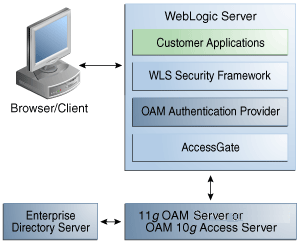
Process overview: Authenticator Function for Web and non-Web Resources
A user attempts to access a Java EE application (secured with the authentication mechanism in the application's web.xml file) that is deployed on the Oracle WebLogic Server.
Oracle WebLogic Server intercepts the request.
Oracle Access Manager Authentication Provider LoginModule is invoked by the Oracle WebLogic security service. The LoginModule uses the OAP library to communicate with the 11g OAM Server (or 10g Access Server) and validate the user credentials.
If the user identity is authenticated successfully, WLSUserImpl and WLSGroupImpl principals are populated in the Subject.
If Oracle Access Manager LoginModule fails to authenticate the identity of the user, it returns a LoginException (authentication failure) and the user is not allowed to access the Oracle WebLogic resource.
Oracle Access Manager Authenticator supports Oracle WebLogic Server UserNameAssertion.
Oracle Access Manager Authenticator can be used with any Identity Asserter. In this case, the Oracle Access Manager Authenticator performs user name resolution and gets the roles and groups associated with the user name.
This section introduces choosing applications to use Oracle Access Manager and the Authentication Provider according to current application setup. Details are similar whether you plan to use Oracle Access Manager 11g or 10g with the Authentication Provider:
If your application is to use Oracle Access Manager Authentication Provider for the first time, proceed based on the functionality that you want to use:
Identity Asserter for Single Sign-On: The Web-only applications implementation handles nearly all SSO use cases. See "Installing the Authentication Provider with Oracle Access Manager 11g".
Oracle Web Services Manager-Protected Web Services: This requires the AccessGate that is provided with the Identity Asserter to interact with the OAM Server. See "Configuring Identity Assertion for Oracle Web Services Manager and OAM 11g".
Authenticator: No single sign-on is provided. The Authenticator requests credentials from the user based on the authentication method specified in the application configuration file, web.xml. See "Configuring the Authenticator Function for Oracle Access Manager 11g".
If your application has been deployed on the old Oracle Application Server (OC4J), you can perform a few steps to make the application use the Authentication provider with Oracle WebLogic Server, proceed as follows:
Remove all OC4J-specific settings from the application configuration
Identity Asserter for Single Sign-On: The Web-only applications implementation handles nearly all SSO use cases. See the appropriate topic for your environment:
—OAM 11g: "Configuring Identity Assertion for SSO with Oracle Access Manager 11g"
—OAM 10g: "Configuring OAM Identity Assertion for SSO with Oracle Access Manager 10g"
Oracle Web Services Manager-Protected Web Services: Require the AccessGate provided with the Identity Asserter. See the appropriate topic for your environment:
—OAM 11g: "Configuring Identity Assertion for Oracle Web Services Manager and OAM 11g"
—OAM 10g: "Configuring Identity Assertion for Oracle Web Services Manager and OAM 10g"
Authenticator: No single sign-on is provided. The Authenticator requests credentials from the user based on the authentication method specified in the application configuration file, web.xml. See the appropriate topic for your environment:
—OAM 11g:"Configuring the Authenticator Function for Oracle Access Manager 11g"
—OAM 10g: "Configuring the Authenticator for Oracle Access Manager 10g"
The Oracle Access Manager Security Provider for WebLogic SSPI provides authentication, authorization, and single sign-on across Java EE applications that are deployed in the WebLogic platform. The Security Provider for WebLogic SSPI enables WebLogic administrators to use Oracle Access Manager to control user access to business applications.
Note:
Security Provider for WebLogic SSPI is also known as "Security Provider" in the 10g (10.1.4.3) Oracle Access Manager Integration Guide.
The Oracle Access Manager Security Provider for WebLogic SSPI provides authentication to Oracle WebLogic Portal resources and supports single sign-on between Oracle Access Manager and Oracle WebLogic Portal Web applications. Apart from this, the Security Provider for WebLogic SSPI also offers user and group management functions.
The Oracle Access Manager Authentication Provider is more easily installed and configured than the Security Provider for WebLogic SSPI. The Authentication Provider offers authentication and single sign-on (SSO) services, and also works with all platforms supported by Oracle WebLogic Server.
If your application has been using the Oracle Access Manager Security Provider for WebLogic SSPI for only authentication and SSO, the deployment is a good candidate for the latest Authentication Provider. However, if your application relies on features other than those offered by the latest Oracle Access Manager Authentication Provider, you can continue to use the Oracle Access Manager 10g Security Provider for WebLogic SSPI.
Note:
WebLogic SSPI connector can be used with Oracle Access Manager 10g but is not supported with Oracle Access Manager 11g
With a very few differences, implementing solutions is similar whether you are using OAM 11g or OAM 10g to protect for applications in a WebLogic container.
Table 15-2 outlines the differences when deploying the Authentication Provider with OAM 11g versus OAM 10g. Topic headings are highlighted.
Table 15-2 Differences in Authentication Provider Implementation Tasks for OAM 11g versus OAM 10g
The required components and files for implementing the Authentication Provider are nearly identical whether you have OAM 11g or OAM 10g as the SSO solution. The few exceptions are noted in the following list:
An enterprise directory server (Oracle Internet Directory or Oracle Sun One directory server) for Oracle Access Manager and Oracle WebLogic Server.
Oracle WebLogic Server 10.3.1+ to be configured to use the Oracle Access Manager Authentication Provider as described later in this chapter.
Optional: A Fusion Middleware product (Oracle Identity Manager, Oracle SOA Suite, or Oracle Web Center for example).
Authentication Provider: For applications deployed in a WebLogic container, Oracle Access Manager JAR are WAR files are available when you install an Oracle Fusion Middleware product (Oracle Identity Management, Oracle SOA Suite, or Oracle WebCenter).
Note:
With a stand-alone Oracle WebLogic Server (no Fusion Middleware), you must obtain the Authentication Provider JAR and WAR files from Oracle Technology Network as described in Step 1 of procedures later in this chapter.
oamAuthnProvider.jar: Includes files for both the Oracle Access Manager Identity Asserter for single sign-on and the Authenticator for Oracle WebLogic Server 10.3.1+. A custom Oracle Access Manager AccessGate is also provided to process requests for Web and non-Web resources (non-HTTP) from users or applications.
oamauthenticationprovider.war: Restricts the list of providers that you see in the Oracle WebLogic Server Console to only those needed for use with Oracle Access Manager.
When you deploy the extension, the WebLogic Administration Console creates an in-memory union of the files and directories in its WAR file with the files and directories in the extension WAR file. Once the extension is deployed, it is a full member of the WebLogic Administration Console: it is secured by the WebLogic Server security realm, it can navigate to other sections of the Administration Console, and when the extension modifies WebLogic Server resources, it participates in the change control process For more information, see the Oracle Fusion Middleware Extending the Administration Console for Oracle WebLogic Server.
Oracle Access Manager 11g: A remote registration command-line utility streamlines WebGate provisioning and creates a fresh application domain with security policies. Administrators can specify WebGate parameters and values using a template.
Oracle Access Manager 10g: The platform-agnostic OAMCfgTool and scripts (oamcfgtool.jar) automate creation of the Oracle Access Manager form-based authentication scheme, policy domain, access policies, and WebGate profile for the Identity Asserter for single sign-on. OAMCfgTool requires JRE 1.5 or 1.6. Internationalized login forms for Fusion Middleware applications are supported with the policies protecting those applications.
OHS 11g must be configured as a reverse proxy for the WebGate (required by the Oracle Access Manager Identity Asserter)
Oracle Access Manager:
OAM 11g: Deployed with initial configuration using the Oracle Fusion Middleware Configuration Wizard, as described in Oracle Fusion Middleware Installation Guide for Oracle Identity Management. See "Deploying the Oracle Access Manager 11g SSO Solution".
OAM 10g: Installed with initial setup as described in Oracle Access Manager Installation Guide. See "Deploying SSO Solutions with Oracle Access Manager 10g".
WebGate/AccessGate: Whether you need to provision a WebGate or an AccessGate with Oracle Access Manager depends on your use of the OAM Authentication Provider:
Identity Asserter for Single Sign-On: Requires a separate WebGate for each application to define perimeter authentication.
Authenticator (or Oracle Web Services Manager): Requires the custom 10g AccessGate that is available with the Authentication Provider.
The Authentication Providers use messages with verbose descriptions of low-level activity within the application when Debug mode issued. Ordinarily, you do not need this much information. However, if you must call Oracle Support, you might be advised to set up debugging. When set, Authentication Providers messages appear in the Oracle WebLogic Server default log location.
To set up debugging
Log into WebLogic Administration Console.
Go to Domain, Environment, Servers, yourserver.
Click the Debug tab.
Under Debug Settings for this Server, click to expand the following: weblogic, security, atn.
Click the option beside DebugSecurityAtn to enable it.
Save Changes.
Restart the Oracle WebLogic Server.
In the Oracle WebLogic Server default log location, search for SSOAssertionProvider. For example:
####<Apr 10, 2009 2:32:16 AM PDT> <Debug> <SecurityAtn> <sta00483> <AdminServer> <[ACTIVE] ExecuteThread: '0' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <> <1239355936490> <BEA-000000> <SSOAssertionProvider:Type = Proxy-Remote-User>