B Configuring Attribute Retrievers
As discussed in Section 1.3, "Overview of the Oracle Entitlements Server Architecture," the Policy Information Point (PIP) is a system entity that acts as a source for attribute values. Oracle Entitlements Server relies on an attribute retriever plug-in to get attribute values from one or more of these information stores. These attribute retrievers allow policies to be data-driven in that the value of the attribute can impact the access decision. For example, if access to transfer money from a bank account is based on how much money is currently in the account, an attribute retriever can be used to get a value for the current balance.
Predefined attribute retrievers are shipped with Oracle Entitlements Server. This chapter documents these predefined attribute retrievers and related configuration requirements and the configuration of custom attribute retrievers. It contains the following sections.
-
Section B.1, "Understanding Predefined Attribute Retrievers"
-
Section B.2, "Configuring the Attribute Retrievers Using SMConfig UI"
-
Section B.3, "Configuring the Predefined Attribute Retrievers Manually"
-
Section B.4, "Configuring the Custom Attribute Retrievers Manually"
Note:
For more information, see "Working With Attribute Retrievers" in Oracle Fusion Middleware Developer's Guide for Oracle Entitlements Server.B.1 Understanding Predefined Attribute Retrievers
Oracle Entitlements Server contains predefined attribute retrievers that are used to connect to, and retrieve attribute values from, Lightweight Directory Access Protocol (LDAP) data stores and relational database management systems (RDBMS). These predefined attribute retrievers can handle one or more attributes defined in the system without additional programming. They also contain a caching feature and failover.
B.2 Configuring the Attribute Retrievers Using SMConfig UI
The SMConfig UI enables you to create the following attribute retrievers:
-
LDAP attribute retriever
-
RDBMS attribute retriever
-
Custom attribute retriever
B.2.1 Prerequisites
Prerequisites for configuring an attribute retriever using the SMConfig UI are:
-
the OES Client is installed
-
a Security Module is installed or a
jps-config.xmlfile exists
B.2.2 Running the SMConfig UI to Edit the jps-config.xml File
To edit the jps-config.xml file:
-
Navigate to the
oesclient/oessm/enroll/bindirectory. -
Run the command:
./oessmconfig.sh -jpsconfig[path]/jps-config.xml.
To edit the SM instance jps-config.xml file:
-
Navigate to the
oesclient/oes_sm_instances/[SM Name]/bindirectory. -
Run the command
./oessmconfig.sh.A screen similar to the following appears.
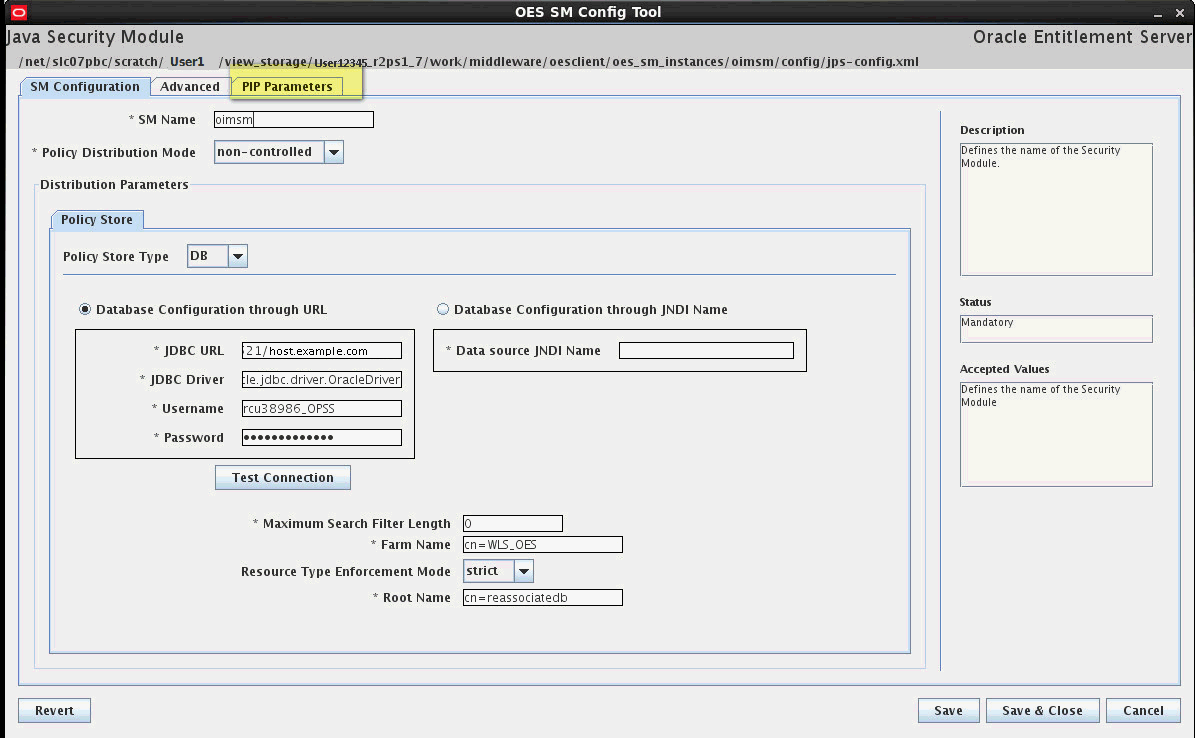
Description of the illustration pip1.gif
B.2.3 Adding, Editing, or Deleting Attribute Retrievers
To add, edit, delete an attribute retriever:
-
In the SMConfig UI, click the PIP Parameters tab.
The PIP configuration screen is displayed.
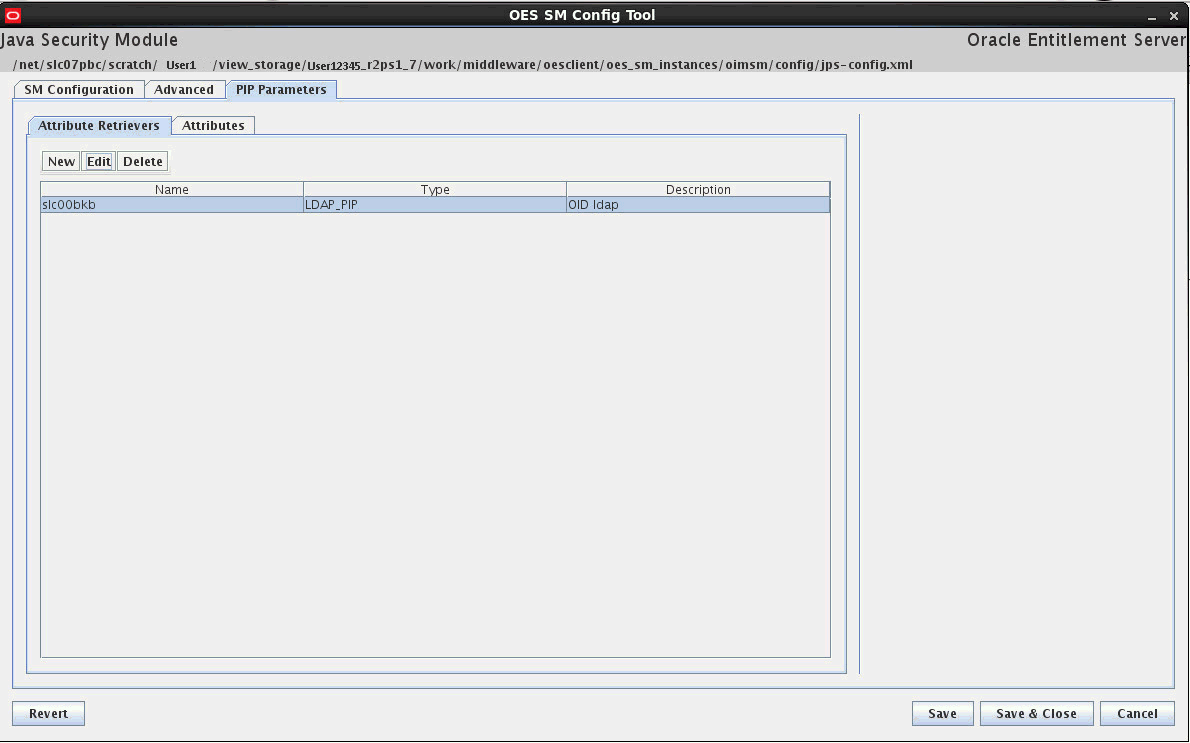
Description of the illustration pip2.gif
-
Click the Attribute Retrievers tab.
-
To create a new attribute retriever:
-
Click the New button to add a new attribute retriever.
The Create New Attribute Retriever screen is displayed.
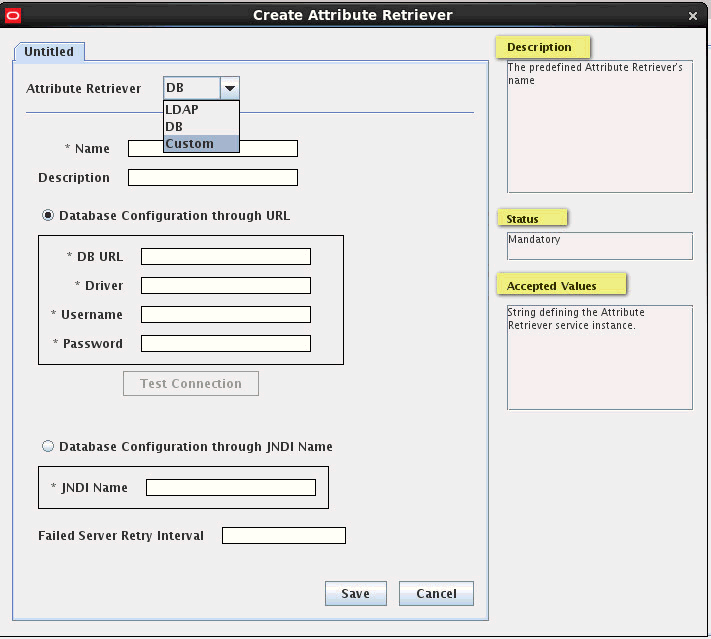
Description of the illustration pip3.gif
-
In the Create Attribute Retriever screen, provide information as documented in Table 8-6, "Java Security Module PIP Parameters (Attribute Retrievers)" in Chapter 8, "Managing Security Module Configurations."
-
Click Save to save the new attribute retriever.
Note:
The screen displays the field description, status, and accepted values.
-
-
To edit an attribute retriever:
-
Select an existing attribute retriever that is listed in the Attribute Retrievers tab.
-
Click the Edit button to edit the attribute retriever.
-
In the attribute retriever dialog that appears, update the value.
-
Click the Save button to save the changes.
-
-
To delete an attribute retriever:
-
Select an existing attribute retriever that is listed in the Attribute Retrievers tab.
-
Click the Delete button to delete the attribute retriever.
-
Click Yes in the confirmation dialog.
-
B.2.4 Adding, Editing, or Deleting Attributes in Attribute Retriever Configuration
To add, edit, or delete an attribute in the attribute retriever:
Note:
There must be 1 attribute retriever at least to perform any of the following tasks.-
In the SMConfig UI, click the PIP Parameters tab.
-
Click the Attributes tab.
-
To create a new attribute in the attribute retriever:
-
Click the New button.
The Create Attribute screen appears.
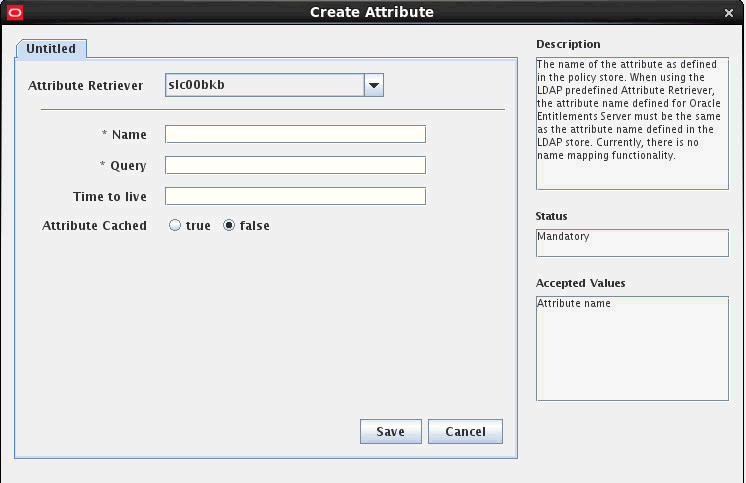
Description of the illustration pip4.gif
-
In the Create Attribute dialog, fill in the fields.
-
Click Save to Save the Attribute.
-
-
To edit an attribute in the attribute retriever:
-
Select an existing attribute listed in the Attributes tab.
-
Click the Edit button.
-
In the Attributes dialog, updated the attribute information.
-
Click Save to Save the Attribute changes.
-
-
To delete an attribute in the attribute retriever:
-
Select an existing Attribute in the Attributes tab.
-
Click the Delete button.
-
In the confirmation dialog, click Yes to delete the Attribute.
-
B.3 Configuring the Predefined Attribute Retrievers Manually
Configuration information for attribute retrievers is defined in the jps-config.xml configuration file (used by Java EE containers) located in the $DOMAIN_HOME/config/fmwconfig directory. To set up a predefined Attribute Retrieve manually, you must:
-
Configure individual attribute values including attribute name, name of attribute retriever used, search query to retrieve the value (for example, SQL query if the PIP is a relational database or LDAP query if it's a directory), and any attribute value caching information.
-
Configure information regarding the name of the class implementing the attribute retriever.
-
Configure information needed to connect to the data store as well as credential information.
-
Declare the attribute retriever reference
The following sections contain information on the configuration parameters for each type of attribute retriever.
B.3.1 Roadmap
The types of predefined attribute retriever are:
-
the LDAP attribute retriever
LDAP attribute retrievers retrieve attribute values from a LDAP database.
-
the RDBMS attribute retriever
RDBMS attribute retrievers retrieve attribute values from an RDBMS database.
Table B-1 contains a roadmap for configuring attribute retrievers.
Table B-1 Configuration Roadmap
| No. | Task | Information |
|---|---|---|
|
1. |
Configure individual attribute values by updating the propertySets section in the |
For more information, see Section B.3.2, "Configuring Individual Attribute Values." |
|
2. |
Declare the PIP service provider by updating the serviceProviders section in the |
For more information, see Section B.3.3, "Declaring the PIP Service Provider." |
|
3. |
Configure information needed to connect to the repository by updating the serviceInstances section in the |
For more information, see Section B.3.4, "Configuring Repository Connection." |
|
4. |
Declare the attribute retriever reference by updating the jpsContexts section in the |
For more information, see Section B.3.5, "Declaring the Predefined Attribute Retriever Reference in jpsContexts Section." |
B.3.2 Configuring Individual Attribute Values
Attribute query information is related to a particular attribute and includes its name, the name of the predefined attribute retriever used, the search query for retrieval (for example, a SQL query if the store is a relational database or an LDAP query if it is a directory), and any attribute caching information. Attribute query information is defined in the <propertySets> section of jps-config.xml.
Table B-2 documents the parameters to be defined for each attribute retrieved by the configured attribute retriever.
Table B-2 Configure Attributes to be Retrieved
| Name | Usage |
|---|---|
|
name |
Description: The name of the attribute as defined in the policy store. When using the LDAP predefined attribute retriever, the attribute name defined for Oracle Entitlements Server must be the same as the attribute name defined in the LDAP store. Currently, there is no name mapping functionality. Mandatory Accepted Value: Attribute name |
|
query |
Description: The database SQL command or LDAP filter used for the query. Users can use a built-in and custom attributes in the query string. For example, the built-in attribute Mandatory Accepted Value: SQL command or LDAP filter. |
|
ttl |
Description: The time-to-live in seconds of any cached attribute values when cached is enabled. Optional Accepted Value: Any integer; default value is 60 seconds if cache is enabled. |
|
cached |
Description: Enables the caching of attribute values. Optional Accepted Value: Default value is false. |
|
ootb.pip.attr.type |
Description: Should be set to OOTB_PIP_ATTRIBUTE. Mandatory Accepted Value: OOTB_PIP_ATTRIBUTE. |
|
ootb.pip.ref |
Description: Should be set to an OOTB PIP instance. Mandatory Accepted Value: The PIP service instance name defined in the |
Example B-1 shows an attribute defined for a LDAP retriever.
Example B-1 Attribute Query Information Defined for LDAP Attribute Retriever
<propertySet name="ootb.pip.attribute.age.based.on.myattr.ldap">
<property name="ootb.pip.attr.type" value="OOTB_PIP_ATTRIBUTE"/>
<property name="ootb.pip.ref" value="pip.service.ootb.ldap"/>
<property name="name" value="oespipage_myattr"/>
<property name="query" value="(cn=%MyAttr%)"/>
<property name="cached" value="true"/>
<property name="ttl" value="60"/>
</propertySet>
Example B-2 shows an attribute defined for a RDBMS retriever.
Example B-2 Attribute Query Information Defined for the RDBMS Attribute Retriever
<propertySet name="ootb.pip.attribute.age.based.on.myattr.rdbms">
<property name="ootb.pip.attr.type" value="OOTB_PIP_ATTRIBUTE"/>
<property name="ootb.pip.ref" value="pip.service.ootb.db"/>
<property name="name" value="oespipage_myattr"/>
<property name="query" value="select oespipage
as oespipage_myattr from pip_info_store where username=%MyAttr%"/>
<property name="cached" value="true"/>
<property name="ttl" value="60"/>
</propertySet>
B.3.3 Declaring the PIP Service Provider
Example B-3 illustrates how the serviceProvider element defines the use of a predefined attribute retriever by defining the internal Oracle Entitlements Server class.
B.3.4 Configuring Repository Connection
Repository connection information is used to connect to the data store and may include its location, JDBC driver and URL or LDAP URL (whichever is applicable) and the user/credential information. This connection information is related to a particular retriever instance. Repository connection information is defined in the <serviceInstances> section of jps-config.xml.
Note:
The instance must also be defined in the default<jpsContexts> section. See Example B-6, "Declaring the Predefined Attribute Retriever Reference in jpsContexts Section".Section B.3.4.1, "Configuring the LDAP Repository Attribute Retriever Parameters," Section B.3.4.2, "Configuring the Database Repository Attribute Retriever Parameters," and Section B.3.7, "Sample jps-config.xml File" contain information regarding a repository connection configuration.
Note:
These predefined attribute retrievers can be configured with Oracle Database 11gR1, Oracle Internet Directory 11gR1, and Oracle Virtual Directory 11gR1.B.3.4.1 Configuring the LDAP Repository Attribute Retriever Parameters
Table B-3 documents the parameters that must be defined when using the LDAP attribute retriever. See Example B-4, "Using the Predefined LDAP Attribute Retriever" and Example B-9, "Configuring LDAP Failover" for sample configuration code.
Table B-3 LDAP Attribute Retriever Parameters
| Name | Usage |
|---|---|
|
name |
Description: The predefined attribute retriever's name (PIP instance name) Mandatory Accepted Value: String defining the attribute retriever service instance. |
|
description |
Description: A description of the predefined attribute retriever (PIP instance description) Optional Accepted Value: string |
|
type |
Description: The predefined attribute retriever's type (The type of this PIP instance) Mandatory Accepted Value: LDAP_PIP |
|
failed.server.retry.interval |
Description: After communication with a primary repository has failed, this attribute defines the interval of time during which the backup repository is used before switching back to the primary repository. Optional Accepted Value: Takes a value equal to the number of seconds. Default value is 15. |
|
bootstrap.security.principal.key |
Description: Defines the principal key for the password credentials to access the LDAP policy store, stored in the CSF store. Valid in JEE and JSE applications. Applies to LDAP and database stores. See Section B.3.4.3, "Setting Up PIP Connection Credentials." Mandatory Accepted Value: key name of the credential; for example, |
|
bootstrap.security.principal.map |
Description: Defines the principal map for the password credentials to access the LDAP policy store, stored in the CSF store. Valid in JEE and JSE applications. Applies to LDAP and database stores. See Section B.3.4.3, "Setting Up PIP Connection Credentials." Mandatory Accepted Value: map name of the credential; for example, |
|
ldap.url |
Description: Defines the URL of the LDAP policy store. Valid in JEE and JSE applications and only applies to LDAP stores. Mandatory Accepted Value: URI of the LDAP policy store in the format |
|
search.base |
Description: The LDAP search base. Mandatory: For LDAP only. Accepted Value: The DN of the search base object. |
Example B-4 illustrates how to modify the serviceInstance element when using the predefined LDAP attribute retriever.
Example B-4 Using the Predefined LDAP Attribute Retriever
<serviceInstance name="pip.service.ootb.ldap" provider="pip.service.provider"> <property name="type" value="LDAP_PIP"/> <property name="ldap.url" value="ldap://dadvmg0065.domainexample.com:3080"/> <property name="bootstrap.security.principal.key" value="keyname"/> <property name="bootstrap.security.principal.map" value="mapname"/> <property name="failed.server.retry.interval" value="10"/> </serviceInstance>
B.3.4.2 Configuring the Database Repository Attribute Retriever Parameters
Table B-4 documents the parameters that must be defined when using the RDBMS attribute retriever. See Example B-5, "Using the Predefined RDBMS Attribute Retriever with JDBC" and Example B-6, "Using the Predefined RDBMS Attribute Retriever with Data Source" for sample configuration code.
Table B-4 RDBMS Attribute Retriever Parameters
| Name | Usage |
|---|---|
|
name |
Description: The predefined attribute retriever's name (PIP instance name) Mandatory Accepted Value: String defining the attribute retriever service instance. |
|
description |
Description: A description of the predefined attribute retriever (PIP instance description) Optional Accepted Value: string |
|
type |
Description: The predefined attribute retriever's type (The type of this PIP instance) Mandatory Accepted Value: RDBMS_PIP |
|
failed.server.retry.interval |
Description: After the primary repository has failed, this attribute identifies the interval of time during which the backup repository is used before switching back to the primary repository. Optional Accepted Value: Takes a value equal to the number of seconds. Default value is 15. |
|
bootstrap.security.principal.key |
Description: Defines the principal key for the password credentials to access the database, stored in the CSF store. Valid in JEE and JSE applications. See Section B.3.4.3, "Setting Up PIP Connection Credentials." Mandatory Accepted Value: key name of the credential; for example, |
|
bootstrap.security.principal.map |
Description: Defines the principal map for the password credentials to access the database, stored in the CSF store. Valid in JEE and JSE applications. See Section B.3.4.3, "Setting Up PIP Connection Credentials." Mandatory Accepted Value: map name of the credential; for example, |
|
jdbc.driver |
Description: Location of the driver when using Java Database Connectivity (JDBC) API to connect to a database. Mandatory: When using JDBC API to connect to database. Accepted Value: |
|
jdbc.url |
Description: Takes a URL that points to the database. Mandatory: When using JDBC API to connect to database. Accepted Value: A list of comma-delimited URLs. The first is treated as primary and so on. For example, |
|
datasource.jndi.name |
Description: Data source JNDI name if you want the PIP instance working through data source rather than directly through JDBC. The data source scenario is supported on WebLogic Server and WebSphere Application Server only. Mandatory: If you want the PIP instance working through data source rather than directly through JDBC. Accepted Value: JNDI name of pre-defined data source object |
The following two examples illustrate how to modify the serviceInstance element when using the predefined RDBMS attribute retriever.
Example B-5 is an example of when you want the RDBMS attribute retriever working via the Java Database Connectivity (JDBC) API.
Example B-5 Using the Predefined RDBMS Attribute Retriever with JDBC
<serviceInstance name="pip.service.ootb.db" provider="pip.service.provider">
<property name="type" value="RDBMS_PIP"/>
<property name="jdbc.url"
value="jdbc:oracle:thin:@scl58116.domainexample.com:1521:orcl"/>
<property name="jdbc.driver" value="oracle.jdbc.driver.OracleDriver"/>
<property name="bootstrap.security.principal.map" value="mapname"/>
<property name="bootstrap.security.principal.key" value="keyname"/>
<property name="failed.server.retry.interval" value="10"/>
</serviceInstance>
Example B-6 is an example of when you want the RDBMS attribute retriever working via a data source rather than directly with JDBC
Example B-6 Using the Predefined RDBMS Attribute Retriever with Data Source
<serviceInstance name="pip.service.ootb.db" provider="pip.service.provider">
<property name="type" value="RDBMS_PIP"/>
<property name="datasource.jndi.name" value="DB_RAC"/>
<property name="failed.server.retry.interval" value="10"/>
</serviceInstance>
B.3.4.3 Setting Up PIP Connection Credentials
As documented in Table B-3, "LDAP Attribute Retriever Parameters" and Table B-4, "RDBMS Attribute Retriever Parameters", the bootstrap.security.principal.key and bootstrap.security.principal.map parameters define the key and the map (respectively) to access the data store. Oracle Entitlements Server ships with oesPassword.sh which sets these LDAP and database connection credentials in the bootstrap credential store. The tool is located in the $OES_SM_INSTANCE_DIRECTORY/bin/ directory.
Note:
Set the following classes to the CLASSPATH before runningoesPassword.sh:
-
OES_ORACLE_HOME/modules/javax.security.jacc_1.0.0.0_1-1.jar -
OES_ORACLE_HOME/wlserver_10.3/server/lib/wseeclient.jar -
OES_ORACLE_HOME/wlserver_10.3/server/lib/wlthint3client.jar
To run the tool:
-
Add
Oracle_Home/wlserver_10.3/server/lib/*to theOES_CLASSPATHin thesetOesEnv.shfile. -
Enter the following command:
./oesPassword.sh -setpass
It prompts for the security principal key name, the security principal map name, the username and associated password.
B.3.4.4 Updating the Database Password
For security reasons, the passwords configured for databases are periodically changed; thus, the Oracle Entitlements Server components (Administration Server and Security Modules) will need to be updated with the new password. The following information documents how this can be done.
-
The Administration Server uses a WebLogic Server data source to provide database access and database connection management. To change the password, update the data source configuration with the new password using the WebLogic Server console. Items must be restarted for the changes to take effect. Run the WLST
modifyBootStrapCredentialcommand and then restart the server. -
Security Modules may connect to a particular database in either of the following ways:
-
The Security Module will connect to the database used as a Policy Store when distributing policies in either the controlled-pull, non-controlled or mixed distribution modes.
-
The Security Module can connect to any relational database management system (RDBMS) when retrieving attributes from an attribute repository using attribute retrievers. (This connection is not limited to the default Policy Store.)
Both cases can use either the WebLogic Server data source configuration or JDBC properties directly. In cases when connecting via the WLS data source configuration, update the data source configuration with the new password using the WebLogic Server console. No additional steps are required. In cases when connecting via the JDBC properties directly, use the oesPassword utility as discussed in Section B.3.4.3, "Setting Up PIP Connection Credentials." The map and key for the credential is defined in
jps-config.xml. -
B.3.5 Declaring the Predefined Attribute Retriever Reference in jpsContexts Section
Example B-7 illustrates how to declare the predefined attribute retriever reference in the jpsContext element. This sample defines a predefined RDBMS attribute retriever.
Example B-7 Declaring the Predefined Attribute Retriever in jpsContext
<jpsContext name="default">
<serviceInstanceRef ref="policystore.db"/>
<serviceInstanceRef ref="pdp.service"/>
<serviceInstanceRef ref="audit"/>
<serviceInstanceRef ref="idstore.xml"/>
<serviceInstanceRef ref="idstore.loginmodule"/>
<serviceInstanceRef ref="pip.service.ootb.db"/>
</jpsContext>
B.3.6 Configuring Cache and Failover
An in-memory cache mechanism is used to improve performance by reducing communications between Oracle Entitlements Server and the external repository. The cache holds up to 1000 entries and can be enabled for each individual attribute. The cache size is not configurable. If the limit is reached, cache items are removed randomly. Example B-1 illustrates the definition of an individual attribute with the cached and ttl properties.
Example B-8 illustrates how to configure the caching of a specific attribute value. Caching is enabled per attribute. In this example, the cache record is deleted after 60 seconds.
Example B-8 Enabling an Attribute's Cache
<propertySet name="ootb.pip.attribute.gender.ldap">
<property name="ootb.pip.attr.type" value="OOTB_PIP_ATTRIBUTE"/>
<property name="ootb.pip.ref" value="pip.service.ootb.ldap"/>
<property name="name" value="oespipgender"/>
<property name="query" value="(oespipage=%oespipage%)"/>
<property name="cached" value="true"/>
<property name="ttl" value="60"/>
</propertySet>
Repository failover can also be configured. When a call for an attribute is received, Oracle Entitlements Server checks whether the primary repository is active. If it is active, the value is retrieved. If the primary repository is not active, it has failed previously and the backup repository is active. In the latter case, Oracle Entitlements Server checks to see if it is time to switch back to the active repository (based on configuration). If it is time to switch back, the switch is made and the value is retrieved from the primary repository. If the configured time has not yet passed, the value is retrieved from the active backup repository.
Note:
If errors occur when retrieving values from the primary repository, Oracle Entitlements Server searches the backup repositories, trying them one by one until an active one is found.Example B-9 illustrates how to configure the failover behavior. In this example, the primary connection is ldap://dadvmg0065:3080 and the backup connection is ldap://scl58123:3060. The failed server retry interval is 10 seconds.
Example B-9 Configuring LDAP Failover
<serviceInstance name="pip.service.ootb.ldap" provider="pip.service.provider">
<property name="type" value="LDAP_PIP"/>
<property name="ldap.url"
value="ldap://dadvmg0065:3080,ldap://scl58123:3060"/>
<property name="bootstrap.security.principal.key" value="keyname"/>
<property name="bootstrap.security.principal.map" value="mapname"/>
<property name="failed.server.retry.interval" value="10"/>
</serviceInstance>
B.3.7 Sample jps-config.xml File
To configure the predefined attribute retriever in jps-config.xml, modify the elements as described in each example in this section. Example B-10 is a sample jps-config.xml file. The examples following it illustrate the modifications that can be made.
Example B-10 Sample jps-config.xml File
<?xml version="1.0"?>
<jpsConfig xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:noNamespaceSchemaLocation="
http://xmlns.oracle.com/oracleas/schema/jps-config-11_0.xsd">
<property name="oracle.security.jps.jaas.mode" value="off"/>
<property name="oracle.security.jps.enterprise.user.class"
value="weblogic.security.principal.WLSUserImpl"/>
<property name="oracle.security.jps.enterprise.role.class"
value="weblogic.security.principal.WLSGroupImpl"/>
<propertySets>
<!-- These are the global authenticated role properties -->
<propertySet name="authenticated.role.properties">
<property name="authenticated.role.name" value="authenticated-role"/>
<property name="authenticated.role.uniquename" value="authenticated-role"/>
<property name="authenticated.role.description"
value="This is the authenticated role used by identity store
service instance."/>
</propertySet>
<!-- attribute defined for ldap retriever -->
<propertySet name="ootb.pip.attribute.age.ldap">
<property name="ootb.pip.attr.type" value="OOTB_PIP_ATTRIBUTE"/>
<property name="ootb.pip.ref" value="pip.service.ootb.ldap"/>
<property name="name" value="oespipage"/>
<property name="query" value="(cn=%SYS_USER%)"/>
<property name="cached" value="true"/>
<property name="ttl" value="60"/>
</propertySet>
<propertySet name="ootb.pip.attribute.age.based.on.myattr.ldap">
<property name="ootb.pip.attr.type" value="OOTB_PIP_ATTRIBUTE"/>
<property name="ootb.pip.ref" value="pip.service.ootb.ldap"/>
<property name="name" value="oespipage_myattr"/>
<property name="query" value="(cn=%MyAttr%)"/>
<property name="cached" value="true"/>
<property name="ttl" value="60"/>
</propertySet>
<propertySet name="ootb.pip.attribute.gender.ldap">
<property name="ootb.pip.attr.type" value="OOTB_PIP_ATTRIBUTE"/>
<property name="ootb.pip.ref" value="pip.service.ootb.ldap"/>
<property name="name" value="oespipgender"/>
<property name="query" value="(oespipage=%oespipage%)"/>
<property name="cached" value="true"/>
<property name="ttl" value="60"/>
</propertySet>
<!-- attribute defined for rdbms retriever -->
<propertySet name="ootb.pip.attribute.age.rdbms">
<property name="ootb.pip.attr.type" value="OOTB_PIP_ATTRIBUTE"/>
<property name="ootb.pip.ref" value="pip.service.ootb.db"/>
<property name="name" value="oespipage"/>
<property name="query" value="select oespipage
from pip_info_store where username=%SYS_USER%"/>
<property name="cached" value="true"/>
<property name="ttl" value="60"/>
</propertySet>
<propertySet name="ootb.pip.attribute.age.based.on.myattr.rdbms">
<property name="ootb.pip.attr.type" value="OOTB_PIP_ATTRIBUTE"/>
<property name="ootb.pip.ref" value="pip.service.ootb.db"/>
<property name="name" value="oespipage_myattr"/>
<property name="query" value="select oespipage
as oespipage_myattr from pip_info_store where username=%MyAttr%"/>
<property name="cached" value="true"/>
<property name="ttl" value="60"/>
</propertySet>
<propertySet name="ootb.pip.attribute.gender.rdbms">
<property name="ootb.pip.attr.type" value="OOTB_PIP_ATTRIBUTE"/>
<property name="ootb.pip.ref" value="pip.service.ootb.db"/>
<property name="name" value="oespipgender"/>
<property name="query" value="select oespipgender
from pip_info_store where oespipage=%oespipage%"/>
<property name="cached" value="true"/>
<property name="ttl" value="60"/>
</propertySet>
</propertySets>
<serviceProviders>
<serviceProvider type="CREDENTIAL_STORE" name="credstoressp"
class="oracle.security.jps.internal.credstore.ssp.
SspCredentialStoreProvider">
<description>SecretStore-based CSF Provider</description>
</serviceProvider>
<serviceProvider class="oracle.security.jps.az.
internal.runtime.provider.PIPServiceProvider"
name="pip.service.provider" type="PIP"/>
<serviceProvider type="POLICY_STORE" name="policy.rdbms"
class="oracle.security.jps.internal.policystore.
OPSSPolicyStoreProvider">
<property name="policystore.type" value="DB_ORACLE"/>
<description>DBMS based PolicyStore</description>
</serviceProvider>
<serviceProvider name="pdp.service.provider" type="PDP"
class="oracle.security.jps.az.internal.
runtime.provider.PDPServiceProvider">
<description>OPSS Runtime PDP Service Provider</description>
</serviceProvider>
<serviceProvider name="idstore.xml.provider" type="IDENTITY_STORE"
class="oracle.security.jps.internal.idstore.
xml.XmlIdentityStoreProvider">
<description>XML-based IdStore Provider</description>
</serviceProvider>
<serviceProvider name="jaas.login.provider" type="LOGIN"
class="oracle.security.jps.internal.
login.jaas.JaasLoginServiceProvider">
<description>This is Jaas Login Service Provider and is used
to configure login module service instances</description>
</serviceProvider>
<serviceProvider name="policy.xml" type="POLICY_STORE"
class="oracle.security.jps.internal.
policystore.xml.XmlPolicyStoreProvider">
<description>XML-based PolicyStore</description>
</serviceProvider>
<serviceProvider type="POLICY_STORE" name="policy.oid"
class="oracle.security.jps.internal.
policystore.ldap.LdapPolicyStoreProvider">
<description>LDAP-based PolicyStore</description>
<property name="policystore.type" value="OID"/>
<property name="connection.pool.maxsize" value="30"/>
<property name="connection.pool.provider.type" value="idmpool"/>
</serviceProvider>
<serviceProvider type="AUDIT" name="audit.provider"
class="oracle.security.jps.internal.audit.AuditProvider">
<description>Audit Service</description>
</serviceProvider>
</serviceProviders>
<serviceInstances>
<serviceInstance name="credstore" provider="credstoressp" location="./">
<description>File Based Credential Store Service Instance</description>
</serviceInstance>
<serviceInstance name="idstore.xml" provider="idstore.xml.provider">
<!-- Subscriber name must be defined for XML Identity Store -->
<property name="subscriber.name" value="jazn.com"/>
<!-- This is the location of XML Identity Store -->
<property name="location" value="./user-data.xml"/>
<!-- This property set defines the authenticated role -->
<propertySetRef ref="authenticated.role.properties"/>
</serviceInstance>
<serviceInstance name="idstore.loginmodule"
provider="jaas.login.provider">
<description>Identity Store Login Module</description>
<property name="loginModuleClassName" value="oracle.security.jps.internal.
jaas.module.idstore.IdStoreLoginModule"/>
<property name="jaas.login.controlFlag" value="REQUIRED"/>
<property name="debug" value="true"/>
<property name="addAllRoles" value="true"/>
</serviceInstance>
<serviceInstance name="policystore.rdbms" provider="policy.rdbms">
<property name="jdbc.url"
value="jdbc:oracle:thin:@scl58116.domainexample.com:1521:orcl"/>
<property name="jdbc.driver" value="oracle.jdbc.driver.OracleDriver"/>
<property name="bootstrap.security.principal.key" value="keyname"/>
<property name="bootstrap.security.principal.map" value="mapname"/>
<property name="oracle.security.jps.ldap.root.name"
value="cn=jpsTestNode"/>
<property name="oracle.security.jps.farm.name"
value="cn=wcai_view_jing.atzsrg"/>
</serviceInstance>
<serviceInstance name="policystore.rdbms.ds" provider="policy.rdbms">
<property name="oracle.security.jps.ldap.root.name"
value="cn=jpsTestNode"/>
<property name="oracle.security.jps.farm.name"
value="cn=wcai_view_jing.atzsrg"/>
<property value="atzsrgds" name="datasource.jndi.name"/>
</serviceInstance>
<serviceInstance name="pdp.service" provider="pdp.service.provider">
<property name="oracle.security.jps.runtime.pd.client.sm_name"
value="${atzsrg.pdp.configuration_id}"/>
<property name="oracle.security.jps.pdp.
AuthorizationDecisionCacheEnabled" value="true"/>
<property name="oracle.security.jps.pdp.
AuthorizationDecisionCacheEvictionCapacity" value="500"/>
<property name="oracle.security.jps.pdp.
AuthorizationDecisionCacheEvictionPercentage" value="10"/>
<property name="oracle.security.jps.pdp.
AuthorizationDecisionCacheTTL" value="60"/>
<property name="oracle.security.jps.ldap.
policystore.refresh.interval" value="30000"/>
<property name="oracle.security.jps.policystore.
refresh.purge.timeout" value="600000"/> <!-- 10 minutes -->
<property name="loading_attribute_backward_compatible" value="false"/>
<!-- Properties for controlled mode PD -->
<property name="oracle.security.jps.runtime.
pd.client.policyDistributionMode" value="non-controlled"/>
<property name="oracle.security.jps.runtime.
instance.name" value="${atzsrg.pdp.instance_name}"/>
</serviceInstance>
<serviceInstance name="policystore.oid" provider="policy.oid">
<property name="max.search.filter.length" value="4096"/>
<property name="bootstrap.security.principal.key" value="keyname"/>
<property name="bootstrap.security.principal.map" value="mapname"/>
<property name="ldap.url" value="ldap://scl58126.domainexample.com:3060"/>
<property name="oracle.security.jps.ldap.root.name"
value="cn=jpsTestNode"/>
<property name="oracle.security.jps.farm.name"
value="cn=wcai_view_jing.atzsrg"/>
<property name="oracle.security.jps.policystore.resourcetypeenforcementmode"
value="Lenient"/>
</serviceInstance>
<serviceInstance name="policystore.xml" provider="policy.xml"
location="./system-jazn-data.xml"/>
<serviceInstance name="user.authentication.loginmodule"
provider="jaas.login.provider">
<description>User Authentication Login Module</description>
<property name="loginModuleClassName"
value="oracle.security.jps.internal.
jaas.module.authentication.JpsUserAuthenticationLoginModule"/>
<property name="jaas.login.controlFlag" value="REQUIRED"/>
</serviceInstance>
<serviceInstance name="user.assertion.loginmodule"
provider="jaas.login.provider">
<description>User Assertion Login Module</description>
<property name="loginModuleClassName"
value="oracle.security.jps.internal.
jaas.module.assertion.JpsUserAssertionLoginModule"/>
<property name="jaas.login.controlFlag" value="REQUIRED"/>
</serviceInstance>
<serviceInstance name="pip.service.ootb.ldap" provider="pip.service.provider">
<property name="type" value="LDAP_PIP"/>
<property name="ldap.url"
value="ldap://scl58126.domainexample.com:3060"/>
<property name="bootstrap.security.principal.key" value="keyname"/>
<property name="bootstrap.security.principal.map" value="mapname"/>
<property name="search.base" value="cn=pip_info_store,
cn=wcai_view_jing.atzsrg,cn=JPSContext,cn=jpsTestNode"/>
<property name="failed.server.retry.interval" value="10"/>
</serviceInstance>
<!-- JPS Audit Service Instance-->
<serviceInstance name="audit" provider="audit.provider">
<property name="audit.filterPreset" value="None"/>
<property name="audit.maxDirSize" value ="0"/>
<property name="audit.maxFileSize" value ="104857600"/>
<property name="audit.loader.jndi" value="jdbc/AuditDB"/>
<property name="audit.loader.interval" value="15" />
<property name="audit.loader.repositoryType" value="File" />
</serviceInstance>
<serviceInstance name="pip.service.ootb.db" provider="pip.service.provider">
<property name="type" value="RDBMS_PIP"/>
<property name="jdbc.url"
value="jdbc:oracle:thin:@scl58116.domainexample.com:1521:orcl"/>
<property name="jdbc.driver" value="oracle.jdbc.driver.OracleDriver"/>
<property name="bootstrap.security.principal.key" value="keyname"/>
<property name="bootstrap.security.principal.map" value="mapname"/>
<property name="failed.server.retry.interval" value="10"/>
</serviceInstance>
<serviceInstance name="pip.service.ootb.db.ds" provider="pip.service.provider">
<property name="type" value="RDBMS_PIP"/>
<property value="atzsrgds" name="datasource.jndi.name"/>
<property name="failed.server.retry.interval" value="10"/>
</serviceInstance>
</serviceInstances>
<jpsContexts default="default">
<jpsContext name="default">
<serviceInstanceRef ref="policystore.oid"/>
<serviceInstanceRef ref="pdp.service"/>
<serviceInstanceRef ref="audit"/>
<serviceInstanceRef ref="idstore.xml"/>
<serviceInstanceRef ref="idstore.loginmodule"/>
<serviceInstanceRef ref="pip.service.ootb.ldap"/>
<serviceInstanceRef ref="pip.service.ootb.db"/>
</jpsContext>
<jpsContext name="smsec">
<serviceInstanceRef ref="credstore"/>
</jpsContext>
</jpsContexts>
</jpsConfig>
B.4 Configuring the Custom Attribute Retrievers Manually
To set up a custom attribute retriever manually, use the following section as an example.
Configuration information for attribute retrievers is defined in the jps-config.xml configuration file (used by Java EE containers) located in the $DOMAIN_HOME/config/fmwconfig directory. To set up custom attribute retrievers manually, use the following section as an example.
B.4.1 Configuring the jps-config.xml Configuration File
Review the following sections for examples on how to configure the jps-config.xml file for custom attribute retrievers.
Declaring the Custom Attribute Retriever Service Provider
Example B-11 illustrates how the serviceProvider element defines the use of a custom attribute retriever by defining the internal Oracle Entitlements Server class.
Example B-11 Declaring Custom Attribute Retriever Service Provider
<serviceProvider class="oracle.security.jps.az.internal.runtime.provider.PIPServiceProvider" name="pip.service.provider" type="PIP"/>
Specifying Custom Attribute Retriever Type and Classnames
Specify type as CUSTOM_PIP, and the classnames to the custom attribute retriever class full qualified name.
Example B-12 Specifying Custom Attribute Retriever Type and Classnames
<serviceInstance name="pip.service.MyAttributeRetriever" provider="pip.service.provider">
<property name="type" value="CUSTOM_PIP"/>
<property name="application" value="myapp"/>
<property name="description" value="custom pip"/>
<property name="classnames" value="com.mycompany.info.MyPip"/> </serviceInstance>
Declaring the Custom Attribute Retriever Reference in jpsContext
Example B-13 illustrates how to declare the custom attribute retriever reference in the jpsContext element.
Example B-13 Declaring Custom Attribute Retriever Reference in jpsContext
<jpsContext name="default">
<serviceInstanceRef ref="pip.service.MyAttributeRetriever"/>
<serviceInstanceRef ref="pdp.service"/>
<serviceInstanceRef ref="audit"/>
<serviceInstanceRef ref="idstore.xml"/>
<serviceInstanceRef ref="idstore.loginmodule"/>
<serviceInstanceRef ref="pip.service.MyAttributeRetriever"/>
</jpsContext>
B.4.2 Implementing Custom PIP Interface
The class of custom PIP should implement the following interface, and the class should be added to the classpath of the security module:
Example B-14 Implementing Custom PIP Interface
package com.bea.security.providers.authorization.asi;
import java.util.Map;
import javax.security.auth.Subject;
import com.bea.security.providers.authorization.asi.ARME.evaluator.RequestHandle;
import weblogic.security.service.ContextHandler;
import weblogic.security.spi.Resource;
/**Version 2 interface for performing attribute retrieval, an implementation of an <code>AttributeRetrieverV2</code> may be used to get embedded data from complex data objects. Multiple retrievers may be registered for the same attribute name, they will be called in order until one returns a non-null result. The difference between Version 1 and Version 2 interface: Version 2 interface introduces a RequestHandle parameter, from which the function is able to get ARME internal system attributes.
*/
public interface AttributeRetrieverV2 {
/**Returns the names of attributes handled by this object. An empty or
<code>null</code> value indicates that the retriever will be considered
capable of handling any attribute name.
@return the names associated with this object*/
String[] getHandledAttributeNames();
/**retrieve the value of the named attribute. Additional authorization
request data is made available to allow for more complex attribute
retrieval.
@param name the name of the needed attribute
@param requestHandle the attributes container associated with the request,
through which the function can get required attribute value.
@param subject the subject associated with the request
@param roles the role membership of the subject
key: role name.
value: role object
<code>null</code> if function is called during role mapping
@param resource the resource associated with the request
@param contextHandler the context associated with the request, may be
<code>null</code> if non-existant
@return the attributes value, or <code>null</code> if not found
*/
Object getAttributeValue(String name,
RequestHandle requestHandle,
Subject subject,
Map roles,
Resource resource,
ContextHandler contextHandler);
} //endof AttributeRetrieverV2