1 Introducing Oracle Access Management
This book provides information on Oracle Access Management, the enterprise-level security platform, and how to administer and configure it. Oracle Access Management includes Oracle Access Management Access Manager (Access Manager) and its incorporated services: Identity Federation, Mobile and Social, Security Token Service, Identity Context and Access Portal.
This chapter provides a high-level overview of the Oracle Access Management architecture and these services.
1.1 Understanding Oracle Access Management Services
Oracle Access Management is a Java, Enterprise Edition (Java EE)-based enterprise-level security application that provides a full range of Web-perimeter security functions and Web single sign-on services including identity context, authentication and authorization; policy administration; testing; logging; auditing; and more. It leverages shared platform services including session management, Identity Context, risk analytics, and auditing, and provides restricted access to confidential information. Many existing access technologies in the Oracle Identity Management stack converge in the Oracle Access Management stack as illustrated in Figure 1-1.
Figure 1-1 Oracle Access Management Overview
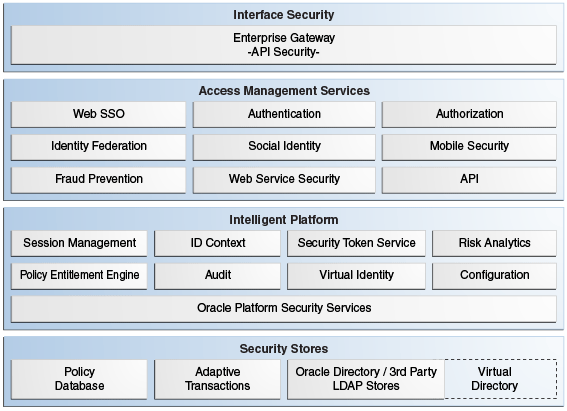
Description of "Figure 1-1 Oracle Access Management Overview"
Starting with release 11.1.2, Oracle Access Management includes these services.
-
Oracle Access Management Access Manager (Access Manager) is described in "Using Oracle Access Management Access Manager" and the following parts of this guide.
-
Oracle Access Management Identity Federation (Identity Federation) provides cross-domain single sign-on support using open federation protocol standards such as SAML and OpenID. Beginning with release 11.1.2, Identity Federation is tightly integrated with Oracle Access Management out of the box. This new Oracle Access Management service includes a streamlined user interface and administration experience. For more information, see the chapters listed in Part I, "Managing Oracle Access Management Identity Federation."
-
Oracle Access Management Security Token Service (Security Token Service) provides token validation and generation to facilitate access to services across security domains and beyond organizational boundaries. Essentially the service acts as a trust-broker that receives and validates client requests and generates appropriate tokens for a requested resource. For more information, see the chapters listed in Part I, "Managing Oracle Access Management Security Token Service."
-
Oracle Access Management Mobile and Social (Mobile and Social) acts as an intermediary between a user seeking access to protected resources, and the back-end Identity and Access Management services that protect the resources. Mobile and Social extends security and compliance to mobile platforms and simplifies integration with Social Identity services including Facebook and Google. Mobile and Social RESTful enables Identity and Access Management infrastructure and includes platform-specific developer kits for leading mobile platforms that enables developers to easily access security services and enable single sign-on across native and mobile browser-based applications. For more information, see the chapters listed in Part I, "Managing Oracle Access Management Mobile and Social."
-
Identity Context provides context-aware security policy management that enables Administrators to control the level of security imposed in an application delivery environment through security frameworks provided by Oracle Identity Management. For more information, see the chapters listed in Part I, "Using Identity Context".
OpenSSO 8.0 and Sun Access Manager 7.1 have also converged into Oracle Access Management 11.1.2. For more information, see:
-
Chapter 23, "Registering and Managing Legacy OpenSSO Agents"
-
Oracle Fusion Middleware Upgrade Guide for Oracle Identity and Access Management
With the 11.1.2.2 release, Oracle Access Management has integrated Oracle Access Portal, a hosted single sign-on proxy service that enables Web applications with Oracle's form-fill single sign-on technology. For more information, see Part I, "Managing Oracle Access Management Oracle Access Portal."
1.2 Using Oracle Access Management Access Manager
Oracle Access Management Access Manager (Access Manager) is the former (standalone) product named Oracle Access Manager. Access Manager provides the Oracle Fusion Middleware 11g single sign-on (SSO) solution. It operates independently (as described in this book) but can also operate with the Access Manager Authentication Provider as described in the Oracle Fusion Middleware Application Security Guide.
Note:
For information on the differences between Access Manager 11g, 10g and other software, see:Access Manager SSO allows users and groups to access multiple applications after authentication, eliminating the need for multiple sign-on requests. To enable SSO, a Web server, Application Server, or any third-party application must be protected by a WebGate (or mod_osso instance) that is registered as an agent with Access Manager. Administrators then define authentication and authorization policies to protect the resource. To enforce these authentication policies, the agent acts as a filter for HTTP requests.
Note:
WebGates are agents provided for various Web servers by Oracle as part of the product. Custom access clients, created using the Access Manager SDK, can be used with non-Web applications. Unless explicitly stated, information in this book applies equally to both.You can also integrate any Web applications currently using Oracle ADF Security and the OPSS SSO Framework with Access Manager. (See Appendix A, "Integrating Oracle ADF Applications with Access Manager SSO.") The following sections contain more details on Access Manager.
1.2.1 Architecting Access Manager
Access Manager 11g sits on an instance of Oracle WebLogic Server and is part of the Oracle Fusion Middleware Access Management architecture. While providing backward compatibility and co-existence with existing solutions, Access Manager 11g replaces and converges the earlier technologies Access Manager 10g and Oracle Application Server SSO (OSSO) 10g. Figure 1-2 illustrates the primary Access Manager 11g components and services. The Protocol Compatibility Framework interfaces with OAM WebGates, mod_osso agents, and custom Access Clients created using the Access Manager Software Developer Kit (SDK).
Figure 1-2 Access Manager 11g Components and Services
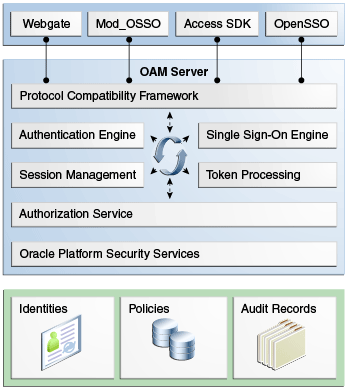
Description of "Figure 1-2 Access Manager 11g Components and Services"
Figure 1-3 illustrates the distribution of Access Manager components.
Figure 1-3 Access Manager 11g Component Distribution
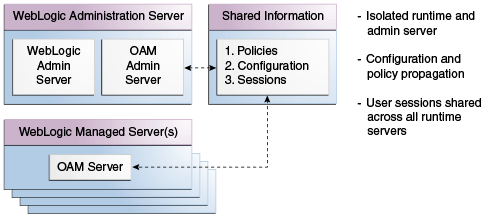
Description of "Figure 1-3 Access Manager 11g Component Distribution"
The Oracle Access Management Console resides on the Oracle WebLogic Administration Server (referred to as AdminServer). WebLogic Managed Servers hosting OAM runtime instances are known as OAM Servers. Information shared between the two includes:
-
Agent and server configuration data
-
Access Manager policies
-
Session data (shared among all OAM Servers)
1.2.2 Deploying Access Manager
Table 1-1 describes the types of deployments in which Access Manager might be installed by your enterprise.
Table 1-1 Access Manager Deployment Types
| Deployment Type | Description |
|---|---|
|
Development Deployment |
Ideally a sandbox-type setting where the dependency on the overall deployment is minimal |
|
QA Deployment |
Typically a smaller shared deployment used for testing |
|
Pre-production Deployment |
Typically a shared deployment used for testing with a wider audience |
|
Fully shared and available within the enterprise on a daily basis |
During initial installation and configuration of Access Manager in your deployment, you create a new WebLogic Server domain (or extend an existing domain). Regardless of the deployment size or type, in a new WebLogic Server domain, the following components are installed using the Oracle Fusion Middleware Configuration Wizard.
-
WebLogic Administration Server
Note:
In an existing WebLogic Server domain, the WebLogic Administration Server is already installed and operational. -
Oracle Access Management Console deployed on the WebLogic Administration Server
-
A WebLogic Managed Server for Oracle Access Management services
-
Application deployed on the Managed Server
See Also:
"Understanding Oracle WebLogic Server Domains" in the Oracle Fusion Middleware Understanding Domain Configuration for Oracle WebLogic Server guide provides information about Oracle WebLogic Server administration domains.Once the domain is configured, additional details are defined for OAM Servers, Database Schemas, (optional) WebLogic Managed Servers and clusters, and the following store types:
-
Policy Store: The default policy store is file-based for development and demonstration purposes, and is not supported in production environments. All policy operations and configurations are performed directly on the database configured as the policy store in production environments.
-
Identity Store: The default Embedded LDAP data store is set as the primary user identity store for Access Manager.
See Also:
"Managing OAM Identity Stores" -
Keystore: A Java keystore is configured for certificates for Simple or Certificate-based communication between OAM Servers and WebGates during authorization. The keystore bootstrap also occurs on the initial AdminServer startup after running the Configuration Wizard.
1.3 Features of Access Manager 11.1.2
The following sections provide details on the features available (and not available) in Access Manager 11.1.2.
1.3.1 Features In Access Manager 11.1.2
Table 1-2 provides an overview of Access Manager 11.1.2. For a list of names that have changed with 11.1.2, see "Product and Component Name Changes with 11.1.2".
Table 1-2 Features in Access Manager 11.1.2
| Access Manager 11g | Description |
|---|---|
|
Oracle Identity Management Infrastructure |
Enables secure, central management of enterprise identities. |
|
Policy Enforcement Agents |
Resides with the relying parties and delegate authentication and authorization tasks to OAM Servers.
Notes: Nine Administrator languages are supported. Unless explicitly stated, the term "Webgate" refers to both an out of the box Webgate or a custom Access Client. See Chapter 15 for an introduction to agents. |
|
Server-side components |
|
|
Console |
Oracle Access Management Console provides access to all services and configuration details. See Chapter 2. |
|
Protocols for information exchange on the Internet |
Front channel protocols exchanged between Agent and Server: HTTP/HTTPS. Back channel protocols: Authenticated clients can perform session operations using enhancements in the Oracle Access Protocol (OAP). |
|
Proxy |
Provides support for legacy systems
See Also: About the Embedded Proxy Server and Backward Compatibility and the new Part I, "Managing Oracle Access Management Oracle Access Portal." |
|
Cryptographic keys |
Note: One key is generated and used per registered mod_osso or 11g Webgate. However, one single key is generated for all 10g Webgates.
|
|
Keys storage |
|
|
Encryption / Decryption (The process of converting encrypted data back into its original form) |
Introduces client-side cryptography and ensures that cryptography is performed at both the agent and server ends:
|
|
Policy Store |
Database in production environments; file-based in demonstration and development environments, as described in "Managing the Policy and Session Database". |
|
Applications |
An application that delegates authentication and authorization to Access Manager and accepts headers from a registered Agent. Note: External applications do not delegate authentication. Instead, these display HTML login forms that ask for application user names and passwords. For example, Yahoo! Mail is an external application that uses HTML login forms. |
|
SSO Engine |
Manages the session lifecycle, facilitates global logout across all relying parties in the valid session, and provides consistent service across multiple protocols. Uses Agents registered with Access Manager 11g:
See: Chapter 18 |
|
Session Management |
See Chapter 17. |
|
Policies |
Registered agents rely on Access Manager authentication, authorization, and token issuance policies to determine who gets access to protected applications (defined resources). See: Chapter 20 |
|
Client IP |
|
|
Response token replay prevention |
|
|
Multiple network domain support |
Access Manager 11g supports cross-network-domain single sign-on out of the box. Oracle recommends you use Oracle Federation for this situation. |
|
Cookies |
Host-based authentication cookie:
See Chapter 18. |
|
Centralized log-out |
See Chapter 22. |
1.3.2 Features Not In Access Manager 11.1.2
Table 1-3 lists several features provided in Access Manager 10g but not included in Access Manager 11.1.2.
1.4 System Requirements and Certification
Refer to the system requirements and certification documentation on Oracle Technology Network (OTN) for information about hardware and software requirements, platforms, databases, and other information.
The system requirements document covers information such as hardware and software requirements, minimum disk space and memory requirements, and required system libraries, packages, or patches:
http://www.oracle.com/technetwork/middleware/ias/downloads/fusion-requirements-100147.html
The certification document covers supported installation types, platforms, operating systems, databases, JDKs, and third-party products:
http://www.oracle.com/technetwork/middleware/ias/downloads/fusion-certification-100350.html
1.5 Installing Oracle Access Management
The following sections contain information and links regarding Access Manager installation and post-installation tasks.
1.5.1 About Oracle Access Management Installation
The Oracle Fusion Middleware Supported System Configurations document provides certification information on supported installation types, platforms, operating systems, databases, JDKs, and third-party products related to Oracle Identity Management 11g. You can access the Oracle Fusion Middleware Supported System Configurations document by searching the Oracle Technology Network (OTN) Web site:
http://www.oracle.com/technology/software/products/ias/files/fusion_certification.html
Using the Oracle Fusion Middleware Configuration Wizard, the following components are deployed for a new domain:
-
WebLogic Administration Server
-
Oracle Access Management Console deployed on the WebLogic Administration Server (sometimes referred to as the OAM Administration Server, or simply AdminServer)
-
A Managed Server for Oracle Access Management
-
An application deployed on the Managed Server
OracleAS 10g SSO deployments can be upgraded to use Oracle Access Management 11g SSO. After upgrading and registering OSSO Agents, authentication is based on Access Manager 11g Authentication Policies. However, only OAM Agents (Webgates/Access Clients) use Access Manager 11g Authorization Policies. Over time, all mod_osso agents in the upgraded environment should be replaced with Webgates to enable use of 11g Authorization policies.
For details about co-existence after the upgrade, see Oracle Fusion Middleware Upgrade Guide for Oracle Identity and Access Management:
1.5.2 About Oracle Access Management Post-Installation Tasks
Each WebLogic Server domain is a logically related group of Oracle WebLogic Server resources. WebLogic administration domains include a special Oracle WebLogic Server instance called the Administration Server. Usually, the domain includes additional Oracle WebLogic Server instances called Managed Servers, where Web applications and Web Services are deployed.
During initial deployment, the WebLogic Administrator userID and password are set for use when signing in to both the Oracle Access Management and WebLogic Server Administration Console. A different Administrator can be assigned for Oracle Access Management, as described in "Specifying the Oracle Access Management Console Administrator". Administrators can log in and use the Oracle Access Management Console for the post-installation tasks documented in Table 1-4.
Table 1-4 Oracle Access Management Post-Installation Tasks
| Service | Requirements |
|---|---|
|
Access Manager |
Enable Access Manager Service. Register:
Configure:
Configure Access Manager Settings. |
|
Identity Federation |
Enable Identity Federation Service Configure Federation Settings Register Identity Provider and Service Provider partners |
|
Security Token Service |
Enable Security Token Service Service. Configure Security Token Service Settings. Register Endpoints Create Token Issuance and Validation Templates Register Partner Profiles and Partners |
|
Mobile and Social |
Enable Mobile and Social Service Configure Mobile and Social |