| Oracle® Fusion Middleware Enterprise Single Sign-On Suite Administrator's Guide 11g Release 2 (11.1.2.2) Part Number E37692-06 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware Enterprise Single Sign-On Suite Administrator's Guide 11g Release 2 (11.1.2.2) Part Number E37692-06 |
|
|
PDF · Mobi · ePub |
This section contains solutions to the most common problems encountered when installing, configuring, and deploying Oracle Enterprise Single Sign-On Suite. For in-depth discussion and best practices for administering the suite, see Oracle Enterprise Single Sign-On Suite Installation Guide, Deploying Logon Manager with a Directory-Based Repository, and Configuring and Diagnosing Logon Manager Application Templates.
Following are solutions to the most common installation scenario problems.
An authenticator is not installed when selected
By default, the installer does not install authenticators that will not work on the system. For example, if the Entrust Entelligence client is not installed, then the authenticator for the Entrust PKI will not be installed (Entrust Entelligence is available with Authentication Manager only).
The Microsoft Active Directory extension is not installed when selected
By default, the installer does not install synchronizer extensions that will not work on the system. For example, if the Microsoft Active Directory client is not installed, then the synchronizer extension for the Microsoft Active Directory Server will not be installed.
User credentials remain after uninstall
Only the current user's credentials can be removed by the standard uninstall. A simple batch file can handle removing other credentials. For Windows XP, for example:
CD /D %UsersProfile%
CD .
For /D %Z in (*.*) do Del /F/S/Q "%Z\Application Data\SSO"
You will need to manually delete registry entries for other users. This can be done in RegEdit or RegEdit32 (RegEdt32.exe), or you can push the following *.reg file to each user:
Windows Registry Editor Version 5.00
HKey_Current_User\Software\Passlogix]
The Agent responds slowly, applications are slowed, or specific functions within applications are slowed, when the Agent is running.
Some antiviral software programs check Agent modules too aggressively. To resolve this, disable checks of ssoshell.exe and/or of the %ProgramFiles%\Passlogix\v-GO SSO directory tree.
Some antiviral software programs check *.ini files too aggressively. The Agent stores user credentials in *.ini files. To resolve this, disable checks of *.ini files, of the file %UserName% aml.ini, and/or of files in the %AppData%\Passlogix directory.
Following are solutions to problems associated specifically with authentication.
User logs onto a computer with different domain/workgroup accounts but sees the same credentials.
The problem is that the local computer's Windows account provides the user's Registry Hive (HKCU), not the domain/workgroup account. There are two workarounds: use the CleanupOnShutdown feature or use a different Windows account for each domain/workgroup logon.
Users are never asked to reauthenticate.
Make sure Extensions\AccessManager:AutoLogin is set to the desired value. The value is in milliseconds; a value of 900000 (default for client-side installations) is 15 minutes.
Users have to reauthenticate too frequently.
Make sure Extensions\AccessManager:AutoLogin is set to the desired value. The value is in milliseconds; a value of 900000 (default for client-side installations) is 15 minutes.
Make sure other force-reauth settings are set appropriately. These settings include:
Overriding settings: Extensions\AccessManager:ReauthOnReveal.
Application configuration settings: ForceReauth.
Following are solutions to problems associated specifically with configuring Logon Manager's templates for any application.
The Agent does not recognize pre-existing logon credentials after an upgrade
After an upgrade of the Agent, users report that applications for which they have previously provided credentials no longer function. Instead, a message box appears, advising that the credentials do not correspond to configured logons. The applications appear in Logon Manager in gray, italicized text.
Create a Bulk Add list to update the user's entlist.ini. Also note that in Logon Manager, preconfigured logons for Windows and Web applications are included in the Administrative Console templates, rather than in the Agent's applist.ini. Create the required application logons, using templates, then create the Bulk Add list to update the user's entlist.ini.
An application is not available in the list of predefined applications when you add credentials
Shut down the Agent making sure that no ssoshell.exe processes are running, and restart the Agent.
The Agent can be started and Logon Manager can be opened without the user authenticating
Shut down the Agent, kill any running ssoshell.exe or SSObho.exe processes, and restart the Agent.
The Agent does not recognize a password change window –OR– The Agent does not respond to an application's configured password-change dialog
This can be remedied by adding the password-change form's window title to the main logon form's window-title matching list.
In the Administrative Console, select the application in the left pane and click the General tab. Double-click the Password Change form for the application to open the form configuration dialog. Note the Window Titles of the form, then click Cancel. Double-click the Logon form for the application and, under Window Titles, click Add. Enter the window title of the Password Change form, click OK, then click OK to close the form configuration dialog.
Double-Logon or Wrong Window
The Agent responds twice to an application or responds to a previously-invisible window or to the wrong window
Use one or more (additional) Match sections and Field keys to specify more precise matching criteria.
Specify the window class that should be ignored in Ignore this Window Class in the Miscellaneous tab on the application configuration.
The Agent does not respond to any Windows application
Shut down the Agent, kill any running ssoshell.exe or SSObho.exe processes, and restart the Agent.
The Agent does not respond to a specific Windows application
Use fewer matching criteria.
Check that the application configuration values that are numbers are in decimal, not hexadecimal.
Check that the application configuration values that are strings are the exact ones in the application dialoges.
If using multiple sections, try a test with just one section.
The Agent provides credentials but does not submit
Verify that Auto Submit is set in the Miscellaneous tab of the application configuration and AutoOK is set in the specific set of credentials.
Note:
In order for Logon Manager to respond correctly to ActiveX-based logon forms, you must configure these forms as Windows applications, with the template targeting the Web browser window.Refer to Configuring and Diagnosing Logon Manager Application Templates for complete instructions.
The Agent does not detect or respond to a specific Web page
Check that the page has a password field (Field Type of Password). Without it, the Agent will ignore the page.
Check that SSObho.exe is running.
Try disabling Java, JavaScript, and/or ActiveX support.
The Agent responds slowly to a specific Web page
Check that the page has finished loading. The Agent does not respond to a page until the page finishes loading completely.
Try turning off images.
Try disabling Java, JavaScript, and/or ActiveX support.
The Agent doesn't respond to a loaded Web Application
Start the Agent, then trigger the Agent from the Title Bar Button.
Log On using Logon Manager.
Refresh the browser page.
The Agent doesn't respond to a selected logon using Logon Manager
There is a known issue in the Agent where it does not respond to Web Applications in this way. The Agent still responds via the other triggers.
Note:
If the browser is embedded within another application, the Agent might respond as if the browser is a Windows Application.SSObho.exe does not run
If the Agent does not recognize web pages properly, make sure that SSObho.exe is running. If it is not, the Agent may think the user is in a Terminal Services session. To correct this:
Shut down the Agent. (Verify no SSO* tasks are running in Task Manager.)
Uninstall the Agent.
Make sure the following files are not present on the user's computer:
SSOwts.exe
SSOwts.exe
SSOwts.exe
Search using RegEdit in the system hives of the registry (for example, NOT in HKEY_CURRENT_USER or HKEY_USERS) for references to SSO, vGO, and Passlogix. Delete all inappropriate references, especially:
HKEY_LOCAL_MACHINE\SOFTWARE\Passlogix and its children
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{04EB19CE-B3B3-11D2-8A09-006008C7059E} and its children
HKEY_CLASSES_ROOT\CLSID\{04EB19CE-B3B3-11D2-8A09-006008C7059E} and its children
HKEY_CLASSES_ROOT\AppID\SSO WTS.EXE and its children
HKEY_CLASSES_ROOT\AppID\{6B9E3EFF-C54A-472C-821B-6FC464B58235} and its children
HKEY_CLASSES_ROOT\SSObho.HelperObject and its children
HKEY_CLASSES_ROOT\SSObho.HelperObject.1 and its children
Reinstall the Agent.
The Agent provides credentials but does not submit
If a Submit field is of type Image, make sure that the URL is exact, including the protocol.
If a Submit field is not present, add one.
Instead of submitting the page, the Agent triggers a link to another page or some other action (for example, cancel/clear)
Add a Submit field to the application configuration.
The Web page uses more than three fields (for example, a Social Security # as three fields and a password)
Break the logon up into two (or more) logons. Then the user will select (via the Logon Chooser) first the credential lacking the password (with Auto Submit disabled) and then the credential with the password.
The Agent provides credentials but does not submit
Keep the system focus on the window that is requesting the credentials; if you switch to another window, the Agent will supply the credentials but not tell the page to submit.
Instead of submitting the page, the Agent triggers a link to another page or some other action (for example, cancel/clear)
Turn off Auto Submit for that credential, and manually trigger page submission.
Predefine the page, specifying the Submit field.
When adding credentials, the window title is stored instead of the URL
Check that SSObho.exe is running. (See above.)
Following are solutions to problems particular to Logon Manager's response to Host/Mainframe applications.
The Agent does not respond to any Host application
Shut down the Agent, kill any running ssoshell.exe or SSObho.exe processes, and restart the Agent.
Check that HLLAPI is properly enabled in the host emulator.
Check that MFEnable=1.
Check that the coordinates are relative to the top-left corner, where the top-left corner is (1,1) (row 1, column 1).
The Agent does not respond at all to any Telnet application
Check that the Host emulator supports Telnet through HLLAPI or through a scripting language.
Note:
The Agent supports Telnet through HLLAPI only for ScanPak Aviva and NetManage Rumba.One or more credential fields are not inserted, or are partially inserted
Check that the coordinates are relative to the top-left corner, where the top-left corner is (1,1) (row 1, column 1).
Check that application configuration coordinates are for the exact place where credentials are inserted; usually, there is a space after the field prompts (for example, "Username:Space"), and the credential field needs to be inserted after the space.
If a special character sequence is used between fields, check that the sequence is valid, that Delay Field is set to a sufficiently high value.
The Agent does not respond at all to a specific Host application
Check that the coordinates are relative to the top-left corner, where the top-left corner is (1,1) (row 1, column 1).
Use fewer matching criteria.
The Agent does not respond at all to a specific Telnet application
Check that the coordinates for all fields are set to (1,1).
Following are solutions to problems associated with Event Logging with any extension.
No events are recorded
The Filter setting is not set. For testing purposes, set to 0xFFFFFFFF (to log all events) and restart the Agent.
The Agent has not reached the Retry setting (default: 30 minutes). To change the value from the default, set Extensions\EventManager:Retry or Extensions\EventManager\%Extension%:Retry to a lower value. To verify that the Event Logging is occurring, open the user's %UserName% AML.ini file, look in the SSOSection column for entries with the name starting with CacheItem (for example, CacheItem1). These items are the events, cached until the retry time is reached. At the retry time, the cached events will be sent to the extension(s).
The wrong events are recorded
The Filter setting is set improperly. Review the Event Logging Filter, note the precise bit order and conversion from binary to hexadecimal/decimal.
Credentials do not arrive at the server
The server name is not properly set. Do not use leading "\\" characters. Specify the proper NetBIOS name (not the TCP/IP name).
Credentials on the server are missing data; category and event labels are only numbers and the Description is similar to "The description for Event ID ( ### ) in Source (Logon Manager) cannot be found
The local computer may not have the necessary registry information or message DLL files to display messages from a remote computer. The following information is part of the event:"
The server is not properly configured. See Section 2.17.11.1, "Configuring the Windows Event Logging Server" extension for instructions on configuring the server.
Credential Sharing Groups are not working
Make sure Extensions\AccessManager:PWSEnable=1.
A Password Change within an application in the Domain or LDAP groups does not notify the authenticator of the change
Make sure AUI:ShareToAuth=1.
Following are solutions to problems experienced when synchronizing to any type of directory.
Cannot connect via SSL
Make sure the directory connection works without SSL.
A user cannot create an object on the directory
Make sure the user is connecting to the directory.
Make sure UserPaths points to a valid location.
An SSOlocator object for the user does not exist, either specifically for the user or as a default object. Put a default object in the location UserPaths points to; if this works, you can move the default object up the tree or put a user-specific object on the tree.
Admin objects (vGOAdminOverride, vGOentlist, vGOftulist) cannot be altered
Existing objects cannot be overwritten. Instead, delete the old objects and then push new ones.
A user cannot create an object on the directory
Make sure the user can connect to the File System share directly (for example, in Explorer).
An error message appears when extending the Schema
In the Connect to Repository dialog, if OpenLDAP Directory Server is selected as the Repository Type and an Extend Schema Status error appears, the schema will have to be manually extended.
The Error message appears as follows:
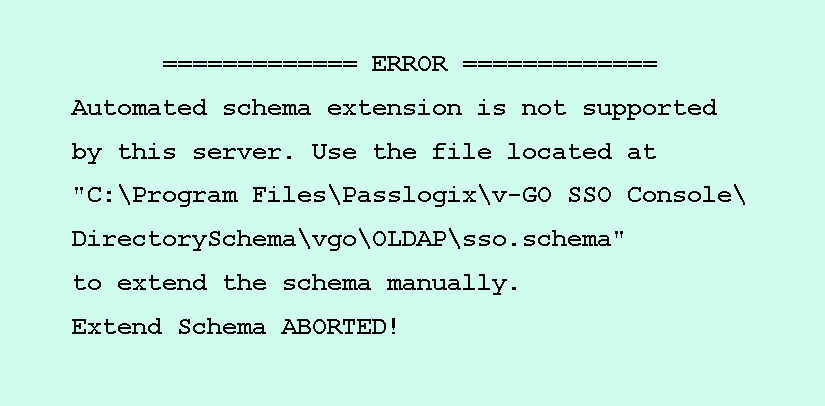
If you receive this error, follow these steps to extend the schema manually:
Copy the sso.schema file to the OpenLDAP server. The sso.schema file can be located in the following location: C:\Program Files\Passlogix\v-GO SSO Console\DirectorySchema\vgo\OLDAP\sso.schema
Place the sso.schema file in the following directory (or other schema directory for OpenLDAP configuration): /usr/local/etc/openldap/schema
The OpenLDAP configuration file must be modified to include the new schema file. Open the file, and add the following line: include <path>/sso.schema where <path> is the path specified in the previous step.
Note:
On UNIX machines, this file is calledslapd.conf.This section describes solutions to issues you may encounter when working with Universal Authentication Manager.
The Universal Authentication Manager service account is used by every Universal Authentication Manager instance on your network to securely access the repository to read and write data. If the service account is deleted or disabled, all instances will fail to synchronize with the repository and users may not be able to log on because the Universal Authentication Manager authentication service won't be able to start when the computer is restarted. If you cannot log on to perform the manual configuration steps, you will have to log on in Windows safe mode. It is important to ensure that this account is protected.
To prevent the Universal Authentication Manager service account from being compromised, set the password to never expire, use a strong password, and be sure no one deletes or changes it. If for some reason the service account is deleted or changed, use one of the following procedures to recover your system.
If the service account is deleted, re-create it with a different name, then follow the steps in Section 5.2.2.5, "Initializing Universal Authentication Manager Storage" to reconfigure Universal Authentication Manager to use the recreated account.
If you are working in Enterprise mode and your workstation has been configured so that the Universal Authentication Manager authentication service is logged on as the Universal Authentication Manager service account, you may see the following error message when you attempt to do a repair of the installation:
"Fatal error during installation."
The repair will not complete successfully.
To complete a repair:
Stop the Universal Authentication Manager authentication service. In the Control Panel, open Administrative Tools. Under Services, right-click the ESSO-UAM Authentication Service and click Stop.
Right-click the ESSO-UAM Authentication Service and click Properties. On the Log On tab, change the Log On As value from the Universal Authentication Manager service account user to the local system account.
Go to Add/Remove Programs or Programs and Features in Control Panel, run the Universal Authentication Manager installer and select the Repair option to repair the installation.
Change the Log On As value back to the Universal Authentication Manager Service Account user. In Control Panel, open Administrative Tools. Under Services, right-click the ESSO-UAM Authentication Service and click Properties. On the Log On tab, change the Log On As value from the local system account to the Universal Authentication Manager service account user.
Restart the Universal Authentication Manager authentication service. From the Control Panel, launch Administrative Tools. Under Services, right-click the ESSO-UAM Authentication Service and click Start.
If the AutoLogon condition is enabled but incorrectly configured, users logging on will see the Microsoft Logon dialog instead of the Universal Authentication Manager logon application. If the user then logs on to the workstation with a Windows password, they will not be prompted to enroll any logon methods. The user sees no PIN prompt or error message. However, users will see the Universal Authentication Manager logon dialog when unlocking the workstation, since AutoLogon pertains only to logon behavior, but not to unlocking a workstation. Users may see the Microsoft Logon dialog when they log off if ForceAutoLogon is not enforced.
For information on how to configure AutoLogon, visit Microsoft Support:
A dual-purpose card is a card that can act as both a smart card and a proximity card. A dual-purpose reader is a reader than can recognize both smart cards and proximity cards. Oracle does not recommend using dual-purpose cards together with dual-purpose readers, as the card will be simultaneously recognized by Universal Authentication Manager as both a smart card and a proximity card. In this case, Universal Authentication Manager will not be able to determine which technology the user intends to use for enrollment.
For example, if you use a dual-purpose device—such as a smart card that contains a proximity chip—with a dual purpose reader, the proximity function of the reader will read the proximity element of the card before you can fully insert the card into the reader for the smart card functionality. A better practice is to use a dual-purpose card with a single-purpose reader, or a single-purpose card with a dual-purpose reader.
Windows default domain policies are enforced by Universal Authentication Manager. Universal Authentication Manager extends your system's native Windows logon behavior. Microsoft Windows and Active Directory include numerous security policies and settings that affect the Windows log on and unlock flows; Universal Authentication Manager conforms to these policies. For example, if a user's password reaches the maximum password age, Universal Authentication Manager still requires the user to change the password before logon is allowed.
Universal Authentication Manager supports AutoLogon. For information on how to configure AutoLogon on an end-user workstation, visit Microsoft Support:
The Universal Authentication Manager Windows logon replicates all native Windows password logon and unlock flows.
The Universal Authentication Manager logon component conforms with Windows password authentication error scenarios and duplicates the flows of the Windows XP GINA. For example, if the user types an invalid password, the error flow is identical and the user receives the same error messages as with Windows XP.
Universal Authentication Manager integrates with and enhances the Windows Winlogon mechanism (based on GINA technology in Windows XP and Credential Provider technology in Windows 7 and later). Microsoft Windows and Active Directory include numerous security policies and settings that affect the Windows logon and unlock flows. Once installed, Universal Authentication Manager conforms to all Microsoft Active Directory security policies.
Note:
Ensure that security policies are not set to require smart cards for logon. This is because Universal Authentication Manager smart card authentication is not based on the PKI Kerberos authentication required by the Windows Group Policy for mandatory smart card logon. If this policy is enabled, Universal Authentication Manager Windows logon will fail.This group of policies is used to manage Active Directory password constraints and password aging, and drives the logic behind password change prompts and expiration. For example, if a user's password reaches the maximum password age as configured in Active Directory, the Universal Authentication Manager logon application requires the user to change the password before permitting a logon.
Universal Authentication Manager supports managing the number of invalid logon attempts that will cause a user's account to be temporarily or permanently disabled. If these policies are enabled to enforce account lockout, the Universal Authentication Manager logon application tracks and increments failed logon and unlock attempts for all supported methods. Accounts that exceed the account lockout threshold are locked by the operating system.
If, as an administrator, you change a user's password, and the user then tries to log on with a Universal Authentication Manager credential, an Incorrect Cached Password error dialog will be presented to the user. The user will be required to type in the new password; ensure that you have informed the user of the new password.
Note:
The incorrect cached password will count as one failed logon attempt, and may trigger the Windows account lockout threshold, depending on how your Windows password policies are configured.