| Oracle® Fusion Middleware Enterprise Single Sign-On Suite Installation Guide 11g Release 2 (11.1.2.2) Part Number E37691-05 |
|
|
PDF · Mobi · ePub |
| Oracle® Fusion Middleware Enterprise Single Sign-On Suite Installation Guide 11g Release 2 (11.1.2.2) Part Number E37691-05 |
|
|
PDF · Mobi · ePub |
This section describes the steps necessary for installing Password Reset. It covers the following topics:
Configuring IIS for Password Reset on Windows Server 2008/2008 R2
Completing the Installation of the Password Reset Server-Side Component
Before you install Password Reset, ensure the prerequisites listed in this section have been satisfied.
Note:
Please refer to the latest release notes to find out about last-minute requirements or changes that might affect your installation.
Note:
When installing on Windows XP, you must install the latest root certificate update from Microsoft, otherwise the installation will fail.
For details and instructions, see the following Microsoft Knowledge Base article:
Because the Password Reset Client relies on the Password Reset Server to function, you must install the Password Reset Server first before you will be able to install and successfully configure the Password Reset Client component.
If you are installing Password Reset Client and Logon Manager on the same Windows XP workstation, you cannot use the Logon Manager Network Provider logon method.
Installing the Password Reset Client on Windows XP disables the Fast User Switching feature, which allows multiple users to be logged on to a computer at the same time and to switch among logons by pressing Win+L. This feature is unavailable because Password Reset utilizes a custom GINA (Graphical Identification and Authentication) component that replaces the Microsoft default GINA dynamic link library (Msgina.dll). To change logons on a Windows XP computer, a user must log off to allow the next user to log on. To do this, open Task Manager (CTRL+ALT+DELETE), and click Log off.
If you want to use Password Reset on a workstation where Kiosk Manager is installed, refer to the Oracle Enterprise Single Sign-On Suite Administrator's Guide for configuration information.
The optional registry settings, AutomaticEnroll and ForceEnrollment, control whether a workstation user is asked or required to enroll in the password reset service on next logon. These values can be set by modifying the installer package; they are not added by the install wizard on the client. See the Enterprise Single Sign-On Suite Administrator's Guide for the locations and values of those settings.
When you install the Password Reset Server, take note of the URLs for the Password Reset Web resources listed in the table below; you will enter those URLs during the installation of the Password Reset Client. Those resources, served by the Password Reset Server, provide the client with the enrollment and reset capability.
|
Enroll URL |
Enter the URL of the Enrollment service default page: http://host/vgoselfservicereset/enrollmentclient/EnrollUser.aspx |
|
Reset URL |
Enter the URL of the reset service default page: http://host /vgoselfservicereset/resetclient/default.aspx |
|
Check Enroll URL |
Enter the URL of the Enrollment check service (checks if user is enrolled): http://host/vgoselfservicereset/resetclient/checkenrollment.aspx |
|
Check Force Enroll URL |
Enter the URL of the force enrollment check service (checks if user is forced to enroll): http://host /vgoselfservicereset/resetclient/checkforceenrollment.aspx |
|
Check Status URL |
Enter the URL of the status check service (checks for Password Reset service availability): http://host /vgoselfservicereset/resetclient/checkstatus.aspx |
Review the hardware and software requirements in the Oracle Enterprise Single Sign-On Suite Release Notes thoroughly and verify that your environment meets all requirements.
You must use matching versions of the Oracle Enterprise Single Sign-On Administrative Console and the Password Reset server component; otherwise, unpredictable behavior may result.
You must not install the Password Reset server-side components on a domain controller. Use a member server instead.
Ensure that DNS is configured and working properly, including correct enumeration of forward and reverse lookup zones.
Verify that your servers and workstations have the latest service packs and Windows updates installed on them.
Install the IIS Web Server first as described in Configuring IIS for Password Reset on Windows Server 2008/2008 R2 or Configuring IIS for Password Reset on Windows Server 2012.
By default, members of the "Domain Administrators" group in Active Directory are automatically added to the local "Administrators" group on the member server. If you are not a member of the "Domain Administrators" group, add yourself to the local "Administrators" group on the member server. For simplicity, the instructions in this guide assume that an "Administrator" account, which is a member of the "Schema Administrators" group is used to install and set up Password Reset Server.
For the creation of service accounts, consider using long, complex passwords and set the accounts to lock out after a specific number of bad password attempts. These actions will prevent a hacker from successfully launching a dictionary attack on service accounts.
Note:
Microsoft recommends that IIS servers be installed on member servers. For a full discussion of this matter, visit the Microsoft Web site.
In order to successfully install Password Reset in unattended ("silent") mode, the Windows Management Instrumentation (WMI) service must be running before the installer is executed.
To check whether the WMI service is running, and start it if necessary, do the following on each target machine:
Open the System Management Console.
Open the Services snap-in.
Navigate to the Windows Management Instrumentation service and check its status and startup mode.
Depending on the status, do one of the following:
If the status is Started, the WMI service is running; proceed to the next section.
If the status is blank, check the service's startup type and start it as follows:
Double-click the service.
In the properties box that appears, set the startup type to Manual or Automatic, as dictated by your environment and click Apply.
Click Start. The status changes to Started.
Click OK to close the service properties dialog box.
This section provides information on upgrading an existing Password Reset installation to the latest version.
Upgrading to Password Reset 11.1.2.2.0 is supported from the following versions of Password Reset:
11.1.1.2.x
11.1.1.5.x
When upgrading a Password Reset Server installation, do the following:
Backup the server settings with an export of the HKEY_LOCAL_MACHINE\Software\Passlogix\SSPR registry key.
Follow the instructions in Installing the Password Reset Server Component. After completing the installation, you must restart Microsoft IIS and verify that the required service accounts are active within the system and that Password Reset is still configured to use them.
(Optional) If you are upgrading an instance of Password Reset that uses an Oracle database as its repository, you must add new indexes required by Password Reset 11.1.2 by running the following queries:
CREATE INDEX SSPR.UQ_USERID ON SSPR.USERQUESTIONS (USERSID);
CREATE INDEX SSPR.EI_USERID ON SSPR.ENROLLMENTINFORMATION (USERSID);
CREATE INDEX SSPR.RI_USERID ON SSPR.RESETINFORMATION (USERSID);
Prior to installing the Password Reset server, you must install Microsoft Internet Information Services as follows:
In the Windows Server Manager, select Roles>Add Roles.
In the Add Roles Wizard, select the Web Server (IIS) role.
In the popup window that appears, confirm that you want to add the required features.
Click Next.
In the "Role Services" window, select the following roles, if they are not already selected:
Application Development: ASP .NET and its required features
Common HTTP Features: Static Content, Default Content, Directory Browsing, HTTP Errors
Health and Diagnostics: HTTP Logging, Request Monitor
Security: Windows Authentication, Digest Authentication, IP and Domain Restrictions, Request Filtering
Performance: Static Content Compression
Management Tools: IIS Management Console, IIS Management Scripts and Tools, Management Service, IIS 6 Management Compatibility (with all sub-components)
Click Next.
In the confirmation window, verify your installation selections. Click Back if you want to change any of your selections. Click Install when you are ready to begin installation.
After the installation completes, continue to Installing the Password Reset Server Component.
Prior to installing the Password Reset server, you must install Microsoft Internet Information Services as follows:
In the Windows Server Manager, click Manage in the upper-right corner, and select Add Roles or Features. from the menu that appears.
In the Add Roles and Features Wizard, click Next.
In the "Select installation type" screen, select Role-based or feature-based installation and click Next.
In the "Select destination server" screen, select the Select a server from the server pool option, then select the target server from the list and click Next.
In the "Select server roles" screen, select Web Server (IIS); in the pop-up requesting to add features required by IIS, click Add Features; click Next.
In the "Web server role (IIS)" screen, click Next.
In the "Features" screen, click Next.
In the "Role services" screen, select the following and accept any prompts for installing features related to your selections:
Common HTTP Features: Default Document, Directory Browsing, HTTP Errors, Static Content, HTTP Redirection
Health and Diagnostics: HTTP Logging, Logging Tools, Request Monitor, Tracing
Performance: Static Content Compression
Security: Request Filtering, Digest Authentication, IP and Domain Restrictions, Windows Authentication
Application Development: .NET 3.5 Extensibility, .NET 4.5 Extensibility, ASP.NET 3.5, ASP.NET 4.5, ISAPI Extensions, ISAPI Filters
Management Tools: IIS Management Console, IIS 6 Management Compatibility (with all sub-components), IIS 6 Management Scripts and Tools
Click Next.
In the "Summary" screen, confirm your selections, click Install, and wait for the installation to complete.
After the installation completes, continue to Installing the Password Reset Server Component.
Note:
Make sure you have completed the steps in Configuring IIS for Password Reset on Windows Server 2008/2008 R2 or Configuring IIS for Password Reset on Windows Server 2012 before beginning this installation.
Close all programs.
Launch the ESSO-PR_Server.msi installer file.
In the "Welcome" panel, click Next.
Select Complete or Custom setup type and click Next.
Custom setup allows you to specify an alternate installation directory.
Click Install.
When the installation is complete, click Finish.
Perform the steps in this section to configure your host environment for Password Reset Server and configure your Password Reset Server installation for operation. You must do the following in order to start using Password Reset Server:
Configuring the Password Reset Authentication and Password Reset Services
Configuring Password Reset Server to Store Data in Active Directory
Limiting the Inherited Permissions for the SSPRRESET Account to the Required Minimum
Configuring the Password Reset Web Service's IIS Site as a Trusted Site in Active Directory
Complete the steps in this section to configure the necessary Password Reset services.
Create the following two accounts on your domain controller. These accounts should be ordinary users in the "Domain Users" group (default):
SSPRWEB. This account will be responsible for Password Reset IIS functions and will make changes, additions, and so forth, to the organizational unit (OU) that you will create later. When creating the OU, you must grant the SSPRWEB account permissions to read, write, modify, and delete all objects within the OU.
If the IIS instance hosting the Password Reset Web service and the Active Directory or AD LDS (ADAM) repository are running on separate machines, this account must be in the same domain as (or in a trusted domain of) the Active Directory or AD LDS (ADAM) repository and must have read and write permissions to the Password Reset Web service's IIS site directories and subdirectories.
SSPRRESET. This account will run the actual reset service on the Password Reset member server with IIS. It will be responsible for resetting user passwords on the domain level.
Note:
Make these accounts members of the local "Administrators" group on the IIS host to avoid problems.
These accounts will be the service accounts that Password Reset uses to manage the container where user questions and enrollment information will be housed and to handle the actual password reset process. Because these are service accounts, you should use highly complex passwords and prudent practices in terms of user lockout after a certain number of bad attempts. Although this might result in some help desk calls from users who cannot reset their passwords, it will also alert you that someone has been trying to attack these service accounts. For information as to best practices for service accounts and security log monitoring, visit Microsoft's knowledge base.
Complete the steps below to assign the service account to the Password Reset system service:
Run: Control Panel > Administrative Tools > Services.
From the list in the right-hand pane, right-click Self Service Password Reset, and select Properties.
In the Self Service Password Reset Properties dialog box, select the Log On tab.
Select This account and enter the account name: Domain\SSPRRESET. Then enter and confirm (re-enter) the password for the account.
A dialog box displays to advise you that changes will apply after the service is restarted.
Restart the service as indicated. The SSPRRESET account setup is complete.
Note:
The SSPRRESET account runs the password reset service on the IIS server where the server-side components reside.
The SSPRWEB account runs the virtual Web site on the IIS server where the server-side components reside.
In order for Password Reset Server to function properly, it must be provided with the SSPRWEB account credentials. Complete the following steps to do so:
Add the credentials to the Web.config file:
Locate the following file on the Password Reset machine and open it in a text editor:
<PR_Install_Directory>\WebServices\Web.config
Locate the following line:
<identity impersonate="true">
Modify the line to look as follows and replace the example values of the userName and password parameters with the SSPRWEB account credentials. (Retain the quotation marks enclosing the values. The parameter names are case-sensitive.)
<identity impersonate="true" userName="domain\ssprweb" password="ssprweb_password" />
Save and close the file.
Encrypt the credentials:
On the Password Reset server machine, launch the command prompt with administrator privileges.
Change into the following directory:
%windir%\Microsoft.NET\Framework\v4.0.30319
Run the following command:
aspnet_regiis.exe -pe "system.web/identity" -app "/vgoselfservicereset/webservices"
Run the following command:
aspnet_regiis.exe -pa "NetFrameworkConfigurationKey" "IIS APPPOOL\SSPR AppPool"
The SSPRWEB account credentials will be encrypted and the Password Reset Web service will be able to decrypt and use them to run under the SSPRWEB account.
To manually decrypt the credentials, run the following command:
aspnet_regiis.exe -pd "system.web/identity" -app "/vgoselfservicereset/webservices"
You must configure access to the Password Reset Web service's IIS Web site contents (under the vgoSelfServiceReset virtual directory) as follows:
| Parameter | Value |
|---|---|
|
Virtual Directory |
EnrollmentClient |
|
Enable Anonymous Access |
NO |
|
Integrated Windows Authentication |
NO |
|
Digest Authentication |
YES |
|
Authentication and Access Control |
SSPRWEB |
|
Virtual Directory |
ManagementClient |
|
Enable Anonymous Access |
NO |
|
Integrated Windows Authentication |
YES |
|
Digest Authentication |
NO |
|
Authentication and Access Control |
SSPRWEB |
|
Virtual Directory |
ResetClient |
|
Enable Anonymous Access |
YES |
|
Integrated Windows Authentication |
YES |
|
Digest Authentication |
NO |
|
Authentication and Access Control |
SSPRWEB |
|
Virtual Directory |
WebServices |
|
Enable Anonymous Access |
NO |
|
Integrated Windows Authentication |
YES |
|
Digest Authentication |
NO |
|
Authentication and Access Control |
SSPRWEB |
Note:
The only virtual directory that permits anonymous access is the ResetClient directory.
In order for Password Reset to function properly, the SSPRWEB service account needs full permissions to the following registry key on the member server containing the Password Reset server side components:
On 32-bit systems: HKLM\SOFTWARE\Passlogix\SSPR
On 64-bit systems: HKLM\SOFTWARE\Wow6432Node\Passlogix\SSPR
Note:
After applying permissions to this key, drill down several levels to verify that permissions have been propagated throughout.
To avoid possible permissions problems during the configuration of the Password Reset server-side components, Oracle recommends that you make both the SSPRWEB and SSPRRESET accounts members of the local administrator's group on the IIS Member Server where you are installing the Password Reset server-side components.
After you have finished the installation and configuration of the Password Reset server-side components, you can remove these accounts from the local administrator's group on the member server.
Password Reset stores user questions, answers, configuration, and enrollment information within an organizational unit in Active Directory. Select any name for the OU that will identify the unit easily.
Note:
Before you proceed, create this organizational unit at the root of your domain. If the OU does not exist when you try to enable storage, you might receive an error message indicating that no such object exists on the server.
The Connect As account performs the schema extension. As such, this account must be a member of the Schema Administrator's group and have permissions to create objects within the Password Reset OU.
To enable the storage of Password Reset data in Active Directory:
Launch the ESSO Suite Administrative Console.
Select the Password Reset tab, enter the administrative interface URL of the target Password Reset server instance and click Apply.
In the left-hand tree, select the System node, then select the Storage tab in the main pane.
From the Storage Type drop-down menu, select AD.
In the Servers field, click Add and do the following in the dialog that appears:
Enter the fully qualified host name or IP address of the target domain controller.
Enter the desired port number (see table below) of the target domain controller. By default, the SSL port is 636 and the non-SSL port is 389.
Click OK to save your changes.
The new entry appears in the Servers list.
In the Server timeout field, specify the number of seconds Password Reset should wait before deeming a connection attempt unsuccessful.
In the Storage Location (DN) field, enter the full path to the Password Reset OU. The SSPRWEB account must have permissions to read, write, modify, and delete all objects stored within this OU.
If your repository is using SSL for secure connections (recommended), select the Use SSL check box.
In the Initialize Storage field, do the following:
Select the Initialize Storage for ESSO-PR check box. This will cause Password Reset to extend the Active Directory schema and create the required objects.
In the Connect As (User) field, enter the name of the domain's schema administrator account. This account should also have permissions required to create objects within the Password Reset OU.
In the Password field, enter the password for the account.
Click Submit to save your changes.
Note:
To verify that the Password Reset OU is configured correctly, open a fresh instance of Active Directory Users and Computers on your targeted domain controller, using the Advanced view. You should see an OU named ESSOPR (or the name that you chose) and two subordinate OUs named SystemQuestions and Users. The existence of these two subordinate OUs indicates success.
You can now remove both the SSPRWEB and SSPRRESET accounts from the local administrator's group on the IIS member server where you installed the Password Reset server-side components.
The SSPRRESET account must be granted no privileges beyond those required to reset user passwords and unlock accounts with this account.
Note that the SSPRRESET account is simply a member of your domain users group. As a fail-safe built into Active Directory, this account cannot be used to change the password of a user that has greater rights (such as, an administrator account).
You can assign this right at the organizational unit level or group level. Assigning this right at the user level should not be a general practice and is not recommended.
The assignment of password reset permissions mandates careful consideration and planning to ensure that the desired accounts, and only the desired accounts, are granted this permission. Some practices and caveats that might help you fine-tune your strategy as you set up these accounts include:
Consider granting the password reset account granular permissions based on organizational units or specific groups. After applying permissions to either, test to make sure that you have the desired results.
Do not run the Delegation of Control Wizard at the root of your domain: if you do, you will give the password reset account rights that extend beyond users to objects such as computers and printers.
Because the password reset account is a member of the domain users group, its password reset permissions are applied to all the members of the domain users group, who are at the same level.
So, if you store all of your users in the default users container in AD and run the Delegation of Control Wizard at that level, it will not permit a domain user account to reset administrator account passwords. Active Directory does not permit users to have administrative rights over administrators.
In this scenario, the password reset service account will not be granted permission to reset the password of your administrators. Your administrators will be able to enroll in Password Reset and go through the entire password reset dialog. However, when they attempt to reset their passwords, they will receive an error message because the password reset service account is not designed to have permissions to reset the password for users in a higher security group.
Carefully consider whether you want members of your domain administrators group to be able to have their passwords reset by an ordinary user account. While you can grant this level of control to the password reset account, you might decide it is wiser not to do so.
Consider an OU structure in Active Directory where users are divided in the following manner:
OU = Users1
OU = Users2
OU = Users (the default user container created in Active Directory)
Assigning users to organizational units makes it possible to manage the SSPRRESET service account permissions of many users in a simple and uniform manner.
Go to Start>Administrative Tools> Active Directory Users and Computers.
Enable the Advanced Features option in the View menu if it's not already enabled.
Navigate to Active Directory Users and Computers > YourDomain > YourOU.
Right-click the OU that you want to control and select Properties.
In the Properties window, select the Security tab and click Advanced.
In the window that appears, click Add.
in the Enter the object name to select field, enter the name of your SSPRRESET account. (Use the Check names button to validate your entry.)
Click OK.
In the Object tab of the Permission Entry window, select User objects from the Apply onto: dropdown menu.
In the Permissions window, check the Reset Password box in the Allow column.
In the Permission Entry window, select the Properties tab.
From the Apply onto: dropdown menu, select User objects.
in the Permissions window, check the Allow box for the Write lockoutTime and Write pwdLastSet permissions.
Click OK.
Click OK two more times to close the windows. Your changes take effect immediately.
To verify that permissions were correctly assigned:
Right-click the OU to which you just assigned the new permissions.
Select Properties.
Select the Security tab.
The SSPRRESET account should be listed as having Special Permissions. The Advanced tab will indicate that this account has password reset permissions on the OU.
There are two virtual directories within Password Reset that do not permit anonymous access, but that are configured to use integrated Windows authentication (that is, if you are logged onto the domain with your Windows password, you should be able to get to that page).
Due to security policies for IIS running on Windows Server 2008, the first time a user attempts to enroll, he might encounter a popup screen requesting user name and password, as is customary with any Web site with such settings. You can avoid this behavior (which can lead to undesired help desk calls) by putting the fully qualified domain name of your Password Reset IIS server in your list of trusted sites for any user in your domain.
To designate your Password Reset server as a trusted intranet site:
For an individual computer, add the Password Reset IIS server's default Web site to your list of trusted intranet sites.
Within Active Directory, add this site to your list of trusted intranet sites through a group policy.
To accomplish this, you need:
Domain administrator rights
The ability to create or modify group policies at the OU or domain level.
In the following example, the Password Reset server site is designated as a trusted intranet site for the entire domain. As such, it is a trusted site to all domain users.
Note:
You might choose to create this policy for each OU that contains potential Password Reset users for more granular access control. Regardless of your approach, the end result is the inclusion of the Password Reset IIS server default Web site as a trusted site.
To add the Password Reset IIS server to the list of trusted sites in your organization, you must first create a policy for Windows clients that do not have the Internet Explorer Enhanced Security Configuration installed (by default, Windows XP does not have this feature installed):
Remove the Internet Explorer Enhanced Security Configuration settings (Control Panel > Add/Remove Programs > Add/Remove Windows Components).
De-select (remove) the Internet Explorer Enhanced Security Configuration.
Note:
You can install this enhanced security feature on your domain controller after having created this policy. Read the dialog box that pops up when you attempt to import the current zone within Group Policy Object Editor.
To create this policy, open Active Directory Users and Computers, right-click on the organizational units that contain users who will be enrolling in Password Reset (in this example, at the root level of the domain) and click the Group Policy tab.
Click New to create a policy. Name the policy SSPR TRUSTED INTRANET SERVER.
Click Edit.
In the left-hand tree, navigate to User Configuration > Windows Settings > Internet Explorer Maintenance > Security > Security Zones and Content Ratings.
Click Modify Settings.
Read the displayed message and proceed.
In the Internet Properties dialog box, click the Local intranet zone icon, then click the Sites button.
In the Local Intranet dialog box, click Advanced.
Enter the fully qualified domain name of your Password Reset IIS default website where indicated.
Click Close.
Click OK and Apply as needed to close out of the Group Policy Object Editor.
Depending on the replication speed within your network, it could take some time to replicate this policy throughout your Active Directory structure.
To confirm that this policy was applied at your desired level in AD:
Log on as a user who would be affected by this policy (having given AD group policy replication sufficient time).
In Internet Explorer, open Tools > Internet Options > Security > Local Intranet > Sites > Advanced.
Internet Explorer should list the site you added in its Trusted Sites window.
In order to avoid unauthorized users from accessing the Web-based Password Reset management console, perform the following steps:
Open Windows Explorer and navigate to:
On 32-bit systems: C:\Program Files\Passlogix\v-GO SSPR
On 64-bit systems: C:\Program Files (x86)\Passlogix\v-GO SSPR
Right-click the Management Client and select Properties from the shortcut menu.
In the Properties dialog box, click the Security tab.
Click Advanced.
Click Change Permissions.
Deselect the Include inheritable permissions from this object's parent check box.
In the warning dialog box that appears, click Add.
Click OK.
In the Security tab, remove the Users group (part of the default inheritance) as well as any other unauthorized users.
Click Add.
Click Advanced search and select the IIS_IUSRS group.
Click OK.
Note:
All permissions except Full should be checked under the Allow column. Additionally, the domain group containing the users who will be granted access to the console must also be added to the security ACL.
Before configuring Password Reset for SSL connectivity on Windows Server 2008/2008 R2 or Windows Server 2012, you must obtain an X.509 Certificate from a trusted certificate authority (CA). This trusted CA must be installed in the list of trusted Root CAs. The certificate must be valid for the current date and its subject must exactly match the network name (either its host name or fully qualified URL containing a host name and domain suffix) that Password Reset client instances will use when connecting to the Password Reset server instance. The instructions in this section assume that a valid certificate has been obtained and is ready to be installed.
Note:
The following articles from the Microsoft Web site can be referred to for information on installing certificates and setting up SSL:
· "How to: Obtain an X.509 Certificate" http://msdn2.microsoft.com/en-us/library/ms819929.aspx
· "How to: Set Up SSL on a Web Server" http://msdn2.microsoft.com/en-us/library/aa302411.aspx
If you use Microsoft Certificate Services to obtain the X.509 certificate, choose a Server Authentication Certificate. Also, enable the Mark keys as exportable and Use local machine store options under the Key Options section.
The steps required to enforce SSL-only connections to Password Reset server are as follows:
Launch Microsoft IIS Manager.
In the Connections pane on the left, select the target server instance.
In the Home pane in the center, double-click the Server Certificates icon.
In the Actions pane on the right, click Complete Certificate Request....
In the Complete Certificate Request dialog that appears, do the following:
In the File name containing the certificate authority's response field, browse to or provide the full path and file name of the target X.509 certificate.
In the Friendly name field, enter a descriptive name for the certificate.
Click OK.
The certificate appears in the target machine's Server Certificates list.
Bind the installed certificate to the https protocol for the selected site. In the Connections pane on the left, expand the target machine node and drill down to and select the Default Web Site node.
In the Edit Site section in the Actions pane on the right, click Bindings.
In the "Site Bindings" dialog that appears, click Add.
In the "Add Site Binding" dialog that appears, do the following:
From the Type drop-down list, select https.
From the Certificate drop-down list, select the certificate you installed earlier in this procedure.
Leave the remaining settings at their defaults.
Click OK to save your changes and dismiss the Add Site Binding dialog.
Click Close to dismiss the Site Bindings dialog.
You must update the following configuration files to use the HTTP-over-SSL (HTTPS) protocol when calling the Password Reset Web pages:
%PROGRAMFILES%\Passlogix\v-GO SSPR\EnrollmentClient\web.config
%PROGRAMFILES%\Passlogix\v-GO SSPR\ManagementClient\web.config
%PROGRAMFILES%\Passlogix\v-GO SSPR\ResetClient\web.config
Modify the \EnrollmentClient\web.config file as follows:
Locate the <appSettings> section.
Modify the EnrollSvc.enrollment key value as follows:
Change http to https.
Replace localhost with the Issued To value from your X.509 certificate. (You recorded this value in the previous part of this procedure.)
(Optional) If you are using a custom port to connect to this service, append the port number at the end of the host name, separated by a semicolon.
For example: https://sssolabmem.ssolab.com:1880.
Save and close the file.

Modify the \ManagementClient\web.config file as follows:
Locate the <appSettings> section.
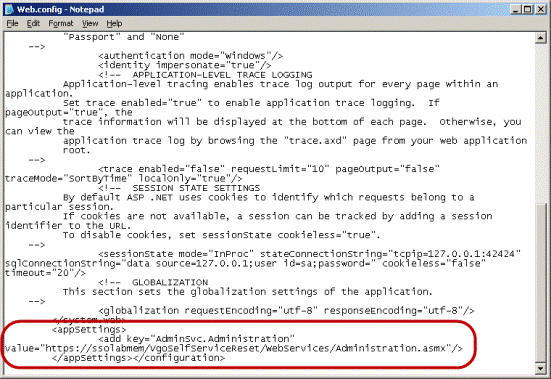
Modify the AdminSvc.administration key value as follows:
Change http to https.
Replace localhost with the Issued To value from your X.509 certificate. (You recorded this value in the previous part of this procedure.)
(Optional) If you are using a custom port to connect to this service, append the port number at the end of the host name, separated by a semicolon.
For example: https://sssolabmem.ssolab.com:1880.
Save and close the file.
Modify the \ResetClient\web.config file as follows:
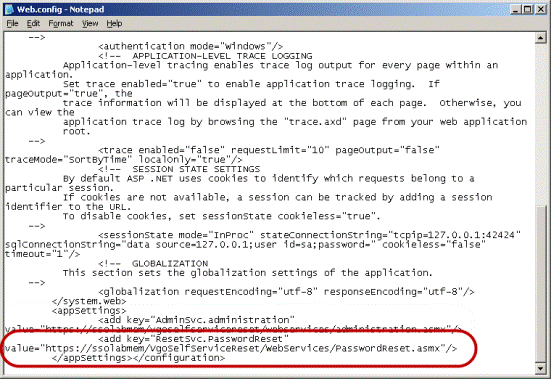
Locate the <appSettings> section.
Modify the ResetSvc.PasswordReset key value as follows:
Change http to https.
Replace localhost with the Issued To value from your X.509 certificate. (You recorded this value in the previous part of this procedure.)
(Optional) If you are using a custom port to connect to this service, append the port number at the end of the host name, separated by a semicolon.
For example: https://sssolabmem.ssolab.com:1880.
Save and close the file.
Launch Microsoft IIS Manager if it is not already open.
In the Connections pane on the left, expand the target machine node and drill down to and select the Sites > Default Web Site > WebServices node.
In the Default Web Site Home pane in the center, double-click the IP Address and Domain Restrictions icon.
In the Actions pane on the right, click Add Allow Entry... .
In the "Add Allow Restriction Rule" dialog that appears, do the following:
Select the Specific IP Address radio button.
Enter the IPv4 or IPv6 address of the target machine.
Click OK to save your changes and dismiss the dialog.
Launch Microsoft IIS Manager if it's not already open.
In the Connections pane on the left, select the target machine node.
Under the target machine node, drill down to and select the Sites > Default Web Site node.
In the Default Web Site Home pane in the center, double-click the SSL Settings icon.
In the SSL Settings screen in the center pane, select the Require SSL check box and leave the Client certificates option at its default value.
In the Actions pane on the right, click Apply to save your changes.
Using a Web browser directly on the Password Reset server machine (do not perform this test from a remote machine), access each of the Password Reset interface services using the new SSL-enabled URLs (i.e., using the https protocol header in place of http). The URLs are as follows:
EnrollmentClient: https://<new_host_name>:<new_port>/vGOSelfServiceReset/ WebServices/Enrollment.asmx
ManagementClient: https://<new_host_name>:<new_port>/vGOSelfServiceReset/ WebServices/Administration.asmx
ResetClient: https://<new_host_name>:<new_port>/vGOSelfServiceReset/ WebServices/PasswordReset.asmx
If any of the URLs fails to load, or a certificate error is displayed, check your configuration, such as virtual directory permissions and certificate options, and correct it if necessary, then try again.
Note:
The Password Reset Client Installer provides the following functions:
Supplies the components needed to run Password Reset through the Windows interface
Sets the registry values that point the Password Reset client to the enrollment and reset service
Offers or obliges workstation users to enroll in the password reset service if so configured
To install and configure the Password Reset client-side software, make sure you have created a functioning installation of Password Reset server as described in Installing the Password Reset Server Component.
Note:
To perform an unattended ("silent") installation of the Password Reset client, see Installing the Password Reset Client-Side Software from the Command Line.
Then, follow the instructions in Installing the Logon Manager Client-Side Software and do the following when prompted by the installer:
When prompted to select between a Typical and Advanced installation, select Advanced.
In the Advanced Setup screen, click Password Reset Client and select This feature, and all subfeatures, will be installed on local hard drive. Make any other installation choices as desired, then click Next.
In the Setup Configuration Information screen, enter the Password Reset Server URLs.When you have finished, click Next.
Continue the installation process as prompted by the installer and described inInstalling the Logon Manager Client-Side Software.
In order to install additional language packs after initial installation:
In the Windows control panel, launch Add/Remove Programs.
Highlight Logon Manager and click the Change button.
Navigate through the install wizard and click the Modify button.
Select the additional language packs that you want to install.
Reboot as instructed and re-launch Add/Remove Programs to complete the additional language installation.
To revert to the original language pack after you've installed another one:
Launch Add/Remove Programs and modify the Logon Manager installation to set the appropriate language pack.
Reboot as instructed after the installation finishes.
Repair the installation.
Note:
You must repair the installation after modifying it. Failure to do so will cause improper functionality of the GINA button.
In order to install the various language packs, you must install Password Reset using command line switches as illustrated below; otherwise the GINA stub will not appear on localized operating systems. You install the desired language pack by adding the language name to the string that follows the ADDLOCAL switch.
Following is the minimum command line for the ADDLOCAL switch:
msiexec /i "Location of .msi" ADDLOCAL=Gina,VersionTracker,English, CheckEnrollment.x86_only,Release_Only
And following is an example of a command line to install silently (/q) with the German language pack added:
msiexec /i "Location of .msi" /q ADDLOCAL=Gina,vgo_sspr_client,English,German, CheckEnrollment.x86_only,Release_Only
| Switch | Action |
|---|---|
|
|
Install. |
|
|
Quiet installation. |
|
|
Follow with options to install (listed below) |
GINA:
Required for all operating systems prior to Windows 7 (Windows Vista is not supported)
Do not include for Windows 7
Required Items:
VersionTracker
CheckEnrollment.x86_only (32-bit operating systems only)
CheckEnrollment.x64_only (64-bit operating systems only)
Release_Only (32-bit operating systems only)
Release_Only.x64 (64-bit operating systems only)
Vista_Only (Windows 7 32-bit only)
Vista_Only.x64 (Windows 7 64-bit only)
Installable Language Packs (English is always installed): Brazilian Portuguese, Czech, Danish, Dutch, English, Finnish, French, German, Greek, Hungarian, Italian, Japanese, Korean, Norwegian, Polish, Portuguese, Romanian, Russian, Simplified Chinese, Slovak, Spanish, Swedish, Thai, Traditional Chinese, Turkish.
Note:
If you are upgrading the Client from an earlier version on the Microsoft Windows 7 32-bit operating system, you must uninstall the older version before performing the following procedure.
The Password Reset client can be installed via an msiexec command, using the following syntax:
msiexec /q /i c:\ESSO-LM_installer.msi ADDLOCAL="component1,component2,component3" programURLs [REBOOT=ReallySuppress]
For a list of a available component names and their functions, see the table below.
For a list of command-line switches for msiexec, refer to the Microsoft MSDN site at http://msdn.microsoft.com.
REBOOT=ReallySuppress - tells the Installer not to reboot under any circumstances.
Example:
Using the following command line, you can perform a silent installation without a reboot of the workstation. This command assumes that the user's Windows directory is Windows and the Logon Manager installer file is named ESSO-LM_installer.msi:
msiexec /q /i "ESSO-LM 07.004_121.x64.msi" ADDLOCAL="InternetExplorer.x64,JavaHelper.x64,Mozilla,Chrome.x64,MainframeEmulators,PR_Components.x64,Provisioning,Authenticators,MSauth,AD_Sync,English_Pack" REG_CHECKENROLLURL="http://host/vgoselfservicereset/resetclient/
checkenrollment.aspx" REG_CHECKFORCEENROLLURL="http://host/vgoselfservicereset/
resetclient/checkforceenrollment.aspx" REG_ENROLLURL=" http://host/vgoselfservicereset/enrollmentclient/enrolluser.aspx" REG_RESETURL="http://host/vgoselfservicereset/resetclient/default.aspx" REG_CHECKSTATUSURL="http://host/vgoselfservicereset/resetclient/checkstatus.aspx" REBOOT=ReallySuppress
Note:
You must type out the full path to the installer .msi, as in the example above. A single space must separate each REG_*="*.aspx"-not a line return.
| ProgramURLs (required) |
|---|
|
|
|
|
|
|
|
|
|
|
|
Where |
To install Password Reset only on an end-user workstation without installing Logon Manager, use the following command:
msiexec /i ""<lm_installer>.msi" TRANSFORMS="pr_client_only.mst"
Be sure to specify the full path and name to the installer file and the full path to the transform file.
Perform the steps in this section to complete the installation of Password Reset Client component.
The Password Reset client runs under the "Local System" account, which by default prevents it from displaying the password reset quiz on Windows Server 2008/2012 systems due to heightened security, namely a stricter "Trusted Sites" zone configuration. To work around this issue, you must add the fully qualified Password Reset server hostname to the affected client system's "Trusted Sites" zone.
For example, to add server.subdomain.domain.com to the "Trusted Sites" zone, create the following registry key:
[HKEY_USERS\S-1-5-18\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap\Domains\domain.com\server.subdomain]
Under that key, create a DWORD value named * and set it to 2.
The value name of * denotes that both the http and https protocols are allowed; the value setting of 2 denotes that the entry is a member of the "Trusted Sites" zone.
Note:
This feature is not available on Windows 7; it applies to Windows XP only.
You can download the aspnet_setreg.exe tool from the Microsoft Web site at:
The Password Reset client provides the ability to run the Reset client under a specified user account instead of the Local System account. This eliminates the possibility that the Reset client will have rights to access resources it should not.
To enable this feature, follow these steps:
Open a command prompt and run the following command:
aspnet_setreg -k:software\passlogix\sspr\windowsinterface -u:domain\username -p:password
Replace domain\username and password with real values.
Ensure that the key HKLM\Software\Passlogix\SSPR\WindowsInterface\ASPNET_SETREG exists. There should be two values in the key: password and userName.
Rename the ASPNET_SETREG key to RestrictedUser.
The Reset Client should launch under the configured user. The Enrollment Client will run under the logged on user.
To test this feature:
Open the Registry and browse to HKLM\Software\Passlogix\SSPR\WindowsInterface.
Copy the value of EnrollURL and set ResetURL to that value.
Change the authentication method for the EnrollmentClient Web application on the Password Reset server from Digest to Windows Authentication.
Note:
Modifying the IIS authentication method for the EnrollmentClient Web application is only required for the purpose of this test; you must revert it back to Digest after you have successfully completed the test.
Manually add your Password Reset server URL to the "Trusted Sites" zone of the machine.
Launch the Password Reset client. The Enrollment screen appears, listing the specified user.
You can disable the popup that indicates that Password Reset is redirecting the user to an external reset page.
To disable this popup, the Password Reset client will create the following setting before launching windowsinterface.exe, and then restore it after redirection: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings Value: WarnonZoneCrossing.
You can configure Password Reset so that the Password Reset GINA button displays as a banner at the top of any window you choose.
To specify the windows that display this banner, add them to the list in: HKLM\Software\Passlogix\SSPR\WindowsInterface\xx\GinaWindows
where xx is the two-letter language code of the currently installed Password Reset language pack.
Within this key, add a REG_SZ value for each window title that you want to have display the banner. The value name will be WindowTitleX, where X is a sequence number starting from 1, and the value data is the window title. For example:
WindowTitle1=Log On to Windows
WindowTitle2=Unlock Computer
Note:
The window title must match exactly, including any leading or trailing white space.
You can configure the Password Reset client in the absence of a Password Reset server installation.
Follow the instructions to install Password Reset on the client machine.
Set the ResetURL value to point to the custom reset Web application.
Set the StatusURL to a resource that will return the success response. This forces Password Reset to bypass the status check and display the ResetURL contents. See below for details.
The StatusURL setting should point to a resource (such as an HTML file) that contains the following content:
<HTML>
<HEAD>
<TITLE>CHECKSTATUS</TITLE>
</HEAD>
<BODY>
GOOD SSPR STATUS
</BODY>
</HTML>