Setting Up Planning and Budgeting Security Groups and Secondary Security Groups
This section provides overviews of security groups, planning center version security, lists prerequisites, and discusses how to:
Define security groups.
Define secondary security groups.
Report secondary security user permissions.
Pages used to Define a Security Group
|
Page Name |
Definition Name |
Navigation |
Usage |
|---|---|---|---|
|
Security Group |
BP_SECURITY_GRP1 |
|
Assign user and role access to nodes on the planning center tree. |
|
Secondary Security Group |
BP_DIM_SECURITYGRP |
|
Create a secondary security group to associate a user with a particular dimension. |
|
Copy User Permissions |
BP_DIM_USRPRM_COPY |
Planning and Budgeting, System Administration, Administer User Security, Secondary Security Groups, and click Copy. |
Select from a list of target users to whom you want to copy permissions. |
|
Copy Secondary Security Group |
BP_DIM_SECGRP_COPY |
Planning and Budgeting, System Administration, Administer User Security, Secondary Security Groups, and click Copy Secondary Security Group. |
Specify the name and effective date of the secondary security group to which you want to copy. |
Understanding Security Groups
Use security groups to grant access to user roles at the planning center level. You define the elements of the security group on the Security Group page and they will be displayed on the User Roles pages. Only those planning centers assigned to a user and role here will show up on the User Planning Centers page. A security group can be used on multiple activity scenarios and planning models.
You create a secondary security group to associate users with a particular non-planning center dimension that you specify when you define the activity on the Activity page. You can grant both read and read-write access within the secondary security group.
Note: Planning and Budgeting does not support secondary dimension security for positions or assets.
Understanding Planning Center Version Security
A user who has read-only access to a secondary security group, will have only partial access to the planning center. For that reason the system draws a distinction between full and partial access:
Partial Access: User has access to only some of the line items within a planning center version. A user has partial access to a line item planning center version if and only if:
The security group authorizes him/her for the planning center, for example, BP01 has access to Department SALES; and
The secondary security group bars him/her from at least one line item within the planning center version, for example, BP01 has no access to Account SALARY; and
The line item combination (Department SALES, Account SALARY) does currently exist in the planning center version.
Full Access: User has access to all line items within a line item planning center version.
A planning center version is defined by a unique combination of these elements: business unit, planning model, activity, scenario, planning center, and version.
Users with partial access to a planning center version are not authorized to do the following:
Submit budgets.
See planning targets.
See user views that display a tree on any dimension.
Perform allocations.
See analysis reports.
Note: The system may still allow a user to see or derive secured data via a driver for the RELATE method, or a flexible formula source. Such read access should be restricted to trusted users.
Submit Status of Planning Centers
All line item planning center versions must have at least one full access user, that is, either read-only or read-write access to all line items in that planning center. Planning centers that do not have at least one such user are deemed nonsubmissible.
The system does not prevent you from creating a nonsubmissible planning center. However, during the staging process, the system generates a warning for each nonsubmissible planning center. The User Access to Line Items page shows the status (in the Submit Allowed? column) of each planning center version; this page is available only after staging.
Resolving Nonsubmissible Status of Planning Centers
The system provides tools so that the coordinator can ensure there is a full access user for every planning center version. Drilling down on a planning center version in the User Access to Line Items page takes you to the User Access to Line Items Detail page, that shows which users have access to each line item within the planning center version.
Prerequisites
To define a security group for your planning center dimension you must first define the following:
Planning center tree based on the dimension you will be using for your activity scenarios in your planning model.
User ID selected as a Planning and Budgeting user.
Security role linked to a delivered Planning and Budgeting role
Note: If you are using the optional secondary security, define the dimension used to secure on the Activity page.
Security Group Page
Use the Security Group page (BP_SECURITY_GRP1) to assign user and role access to nodes on the planning center tree.
Image: Security Groups page
This example illustrates the fields and controls on the Security Groups page. You can find definitions for the fields and controls later on this page.
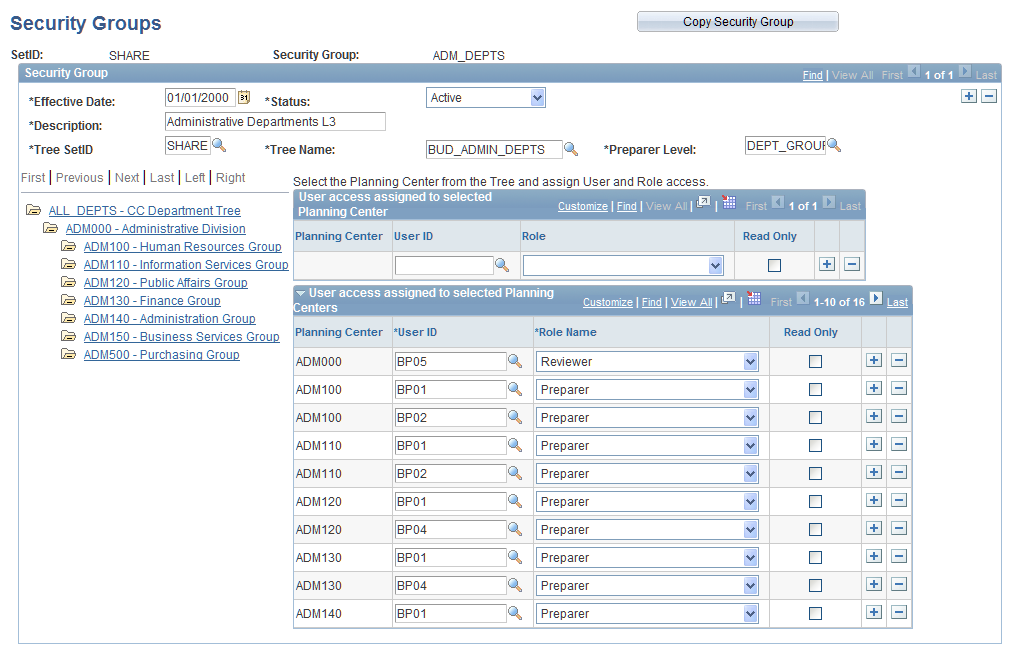
Security groups define the relationship between a planning center, a user and a role assigned to that user. This page allows you to add new combinations of the centers, users and roles. Click a node on the tree to get the planning center for the node into the first grid to the right, and then assign one or more user roles. To assign more nodes/planning centers to users and roles, click the next node and assign users and roles. When you click the next node, the system moves the data for the previously selected node from the first grid into the second grid on the right. When you click the save button the data in the first grid (if any) is moved into second grid and the system saves all the data in the second grid.
Note: You can directly add and delete user access from the grid on the right — 'User access assigned to selected planning centers' group box. It is not necessary to perform any security refresh process if access changes during the planning process, but if you add a new planning center node you will need to refresh Dimension members and worklists in the Update Data Stage Process.
Warning! You will receive the following error message if you attempt to modify or copy a security group that has a user flagged as inactivated:
Inactivated users exist in this security group. Some of the users removed from the Planning and Budgeting user list still exist in this security group. This error can be resolved either by including inactivated users in Planning and Budgeting user list or by deleting inactivated users from the security group.
Secondary Security Group Page
Use the Secondary Security Group page (BP_DIM_SECURITYGRP) to create a secondary security group to associate a user with a particular dimension.
Image: Secondary Security Groups page — Select Dimension Value by Value
This example illustrates the fields and controls on the Secondary Security Groups page — Select Dimension Value by Value. You can find definitions for the fields and controls later on this page.
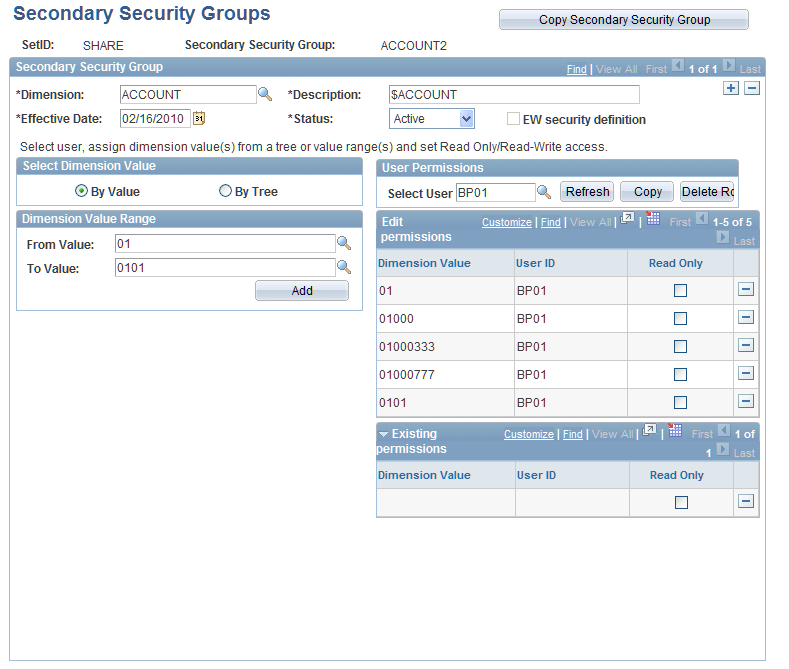
Image: Secondary Security Groups page — Select Dimension Value by Tree
This example illustrates the fields and controls on the Secondary Security Groups page — Select Dimension Value by Tree. You can find definitions for the fields and controls later on this page.
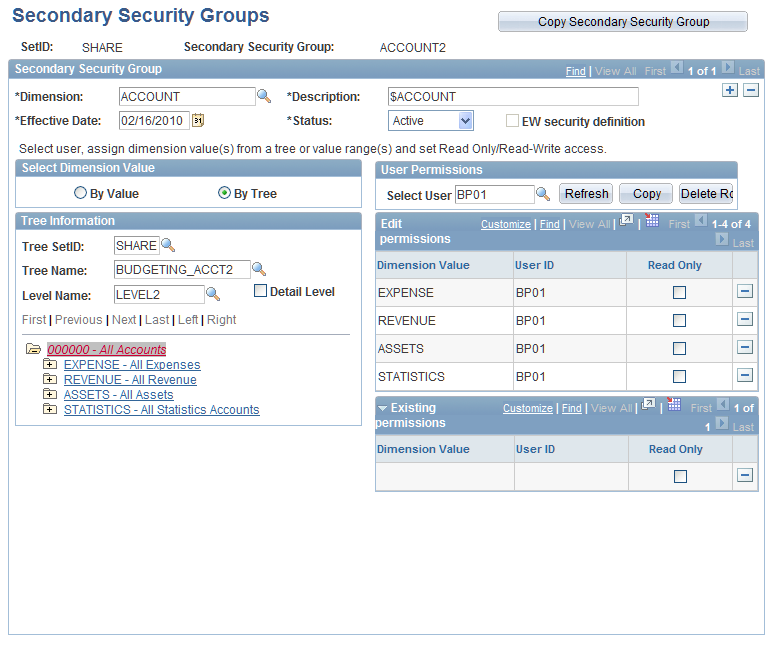
Create a secondary security group to associate users with a particular dimension that you specify when you define the line item activity on the Activity page. You can grant both read-only and read-write access permissions to the secondary security group.