Specifying Row and Column Level Security
This topic provides an overview of role and user-based security and discusses how to:
Define security roles.
Grant dimension and metric access to security roles.
Assign users to security roles.
View summary for security roles.
Grant dimension and metric access to a user.
View summary for a secured user.
Request security processing
Pages Used to Establish Role and User-Based Security
|
Page Name |
Definition Name |
Navigation |
Usage |
|---|---|---|---|
|
Define EPM Security Roles |
PF_SY_ROLE_DEFN |
EPM Foundation, EPM Security, Security By Role, Define EPM Security Roles |
Define security roles. |
|
Access To Metric |
PF_SY_ROLE_METR |
EPM Foundation, EPM Security, Security By Role, Role Metric Access, Access To Metric |
Assign a metric to a security role. |
|
Role Dimension Access |
PF_SY_ROLE_ALL_MDW |
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Role Dimension Access |
Assign a dimension table to a security role and specify high-level access privileges. The object name of this page changes depending on whether an OWE or MDW dimension is selected. |
|
Individual Selection |
PF_SY_ROLE_LIST |
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Individual Selection |
Specify row-level access to the dimension based on SetID and dimension key fields. |
|
Constraint-based Selection |
PF_SY_ROLE_CONS |
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Constraint-based Selection |
Specify row-level access to the dimension based on constraint. |
|
Select Security Column |
PF_SY_COLUMN_PG |
Automatically accessed when you select a constraint on the Constraint-based Selection page that contains two or more columns and the system cannot distinguish the column you want to include in your security parameters |
Select one column to include in your constraint. |
|
Tree-based Selection |
PF_SY_ROLE_TREE |
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Tree-based Selection |
Specify row-level access to the dimension based on an existing tree hierarchy that is defined for the dimension. You can use the tree to grant a user access to specific nodes, leaves, or details in the tree. Used with OWE dimensions only. |
|
User Role Access |
PF_SY_USER_ROLES |
EPM Foundation, EPM Security, Security By User, User Role Access |
Assign a user to a security role. |
|
Role Security Summary |
PF_SY_ROL_SUMMARY |
EPM Foundation, EPM Security, Security By Role, Role Security Summary |
Review access privileges and other information for a security role. |
|
Review Role Dimension Access |
PF_SY_ROLE_DETAIL |
Click the Details link on the Role Security Summary page. |
Review additional details about a dimension that is associated with the selected security role |
|
Access To Metric |
PF_SY_ROLE_METR |
EPM Foundation, EPM Security, Security By User, User Metric Access, Access To Metric |
Assign a metric to a user. |
|
User Dimension Access |
PF_SY_ROLE_ALL |
EPM Foundation, EPM Security, Security By User, User Dimension Access, User Dimension Access |
Assign a dimension table to a user and specify high-level access privileges. |
|
Individual Selection |
PF_SY_ROLE_LIST |
EPM Foundation, EPM Security, Security By User, User Dimension Access, Individual Selection |
Specify row-level access to the dimension based on SetID and dimension key fields. |
|
Constraint-based Selection |
PF_SY_ROLE_CONS |
EPM Foundation, EPM Security, Security By User, User Dimension Access, Constraint-based Selection |
Specify row-level access to the dimension based on constraint. |
|
Select Security Column |
PF_SY_COLUMN_PG |
Automatically accessed when you select a constraint on the Constraint-based Selection page that contains two or more columns and the system cannot distinguish the column you want to include in your security parameters. |
Select one column to include in your constraint. |
|
Tree-based Selection |
PF_SY_ROLE_TREE |
EPM Foundation, EPM Security, Security By User, User Dimension Access, Tree-based Selection |
Specify row-level access to the dimension based on an existing tree hierarchy that is defined for the dimension. You can use the tree to grant a user access to specific nodes, leaves, or details in the tree. Used with OWE dimensions only. |
|
User Security Summary |
PF_SY_SUMMARY |
EPM Foundation, EPM Security, Security By User, User Security Summary |
Review access privileges and other information for a user. |
|
Review User Dimension Access |
PF_SY_USER_DETAIL |
Click the Details link on the User Security Summary page. |
Review additional details about a dimension that is associated with the selected user. |
|
Request Security Processing |
RUN_PF_SECURITY |
EPM Foundation, EPM Security, Advanced, Request Security Processing |
Apply security parameters for security roles and users by running the request security processing (PF_SECURITY) process. |
Defining Dimension and Metric Security
Because EPM is delivered with no security restrictions, dimensions and metrics (also known as fact-columns) are also delivered unsecured. Before you can grant a user access to a dimension or metric, you must first indicate to the system that a particular dimension or metric requires securing. The pages used to define dimension and metric security are discussed in the security topic of this documentation.
See Defining Dimension and Metric Security.
Note: Dimensions and metrics that are not secured are classified as public, or unsecured. All EPM users can view public objects.
Understanding Role and User Based Security for Dimensions and Metrics
After you designate dimensions and metrics that require securing, you must grant users access to those objects. You can grant security access to an individual user or to a specific security role.
EPM security enables you to create security roles. A security role is a set of data access privileges that are assigned to one or more users. A user who is assigned to a specific role inherits all access privileges that are associated with that role. A user can belong to multiple roles. In this case, the user would inherit the combined privileges that are defined for all roles.
To set up security roles, define the role, assign dimension and metric access privileges to the role, and then assign users to the role.
Image: Process flow - security role setup
The following diagram depicts this process.
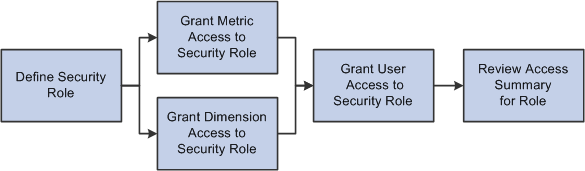
If you have established security roles for your PeopleTools security, you can import the roles into the EPM database using the Run Security Processing page.
See Request Security Processing Page.
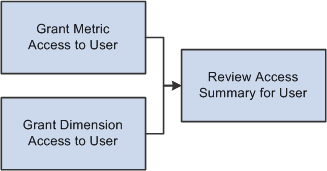
EPM security also enables you to define access privileges for individual users. To set up user access privileges, assign dimension and metric access privileges to a specific user.
Image: Process flow - user security setup
This example illustrates the Process flow - user security setup. .
Dimension Security and Individual, Constraint, and Tree Based Selections
EPM security provides three methods to specify row-level security for your dimension:
Individual-based definition: Enables you to specify row-level security using the SetID and dimension key fields.
Constraint-based definition: Enables you to specify row-level security by associating a constraint with a dimension table.
The constraint limits access to a dimension by acting as the WHERE clause in a SQL statement—for example, SELECT Account ID FROM Account Dimension WHERE Account ID = Northwest.
Set ID and Constraint ID are used to specify constraint access.
Tree-based definition: Enables you to specify row-level security using existing tree hierarchies that are defined for a dimension.
You can use the tree to grant a user access to specific nodes, leaves, or details in the tree. Tree hierarchy use is limited to OWE tables only.
Processing Role and User Based Security Parameters
After the security rules have been set up, the EPM security application engine (PF_SECURITY) process must be run. This processes the access as defined in the Role Dimension access pages and flattens the data to the individual dimension members and populates the security join tables specified in dimension metadata.
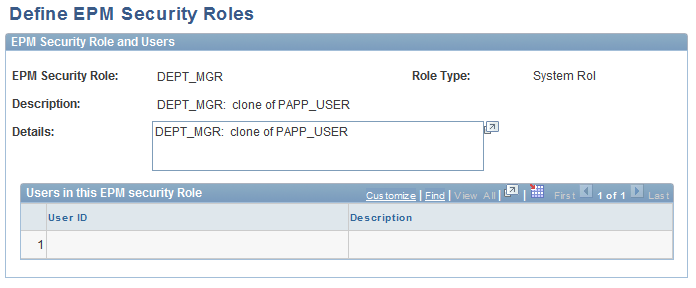
Define EPM Security Roles Page
Use the Define EPM Security Roles page (PF_SY_ROLE_DEFN) to define security roles.
Image: Define EPM Security Roles page
This example illustrates the fields and controls on the Define EPM Security Roles page. You can find definitions for the fields and controls later on this page.
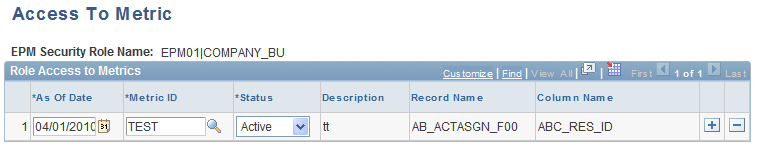
Access To Metric Page
Use the Access To Metric page (PF_SY_ROLE_METR) to assign a metric to a security role.
Image: Access To Metric page
This example illustrates the fields and controls on the Access To Metric page. You can find definitions for the fields and controls later on this page.
Role Dimension Access Page
Use the Role Dimension Access page (PF_SY_ROLE_ALL_MDW) to assign a dimension table to a security role and specify high-level access privileges.
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Role Dimension Access
Image: Role Dimension Access page
This example illustrates the fields and controls on the Role Dimension Access page. You can find definitions for the fields and controls later on this page.
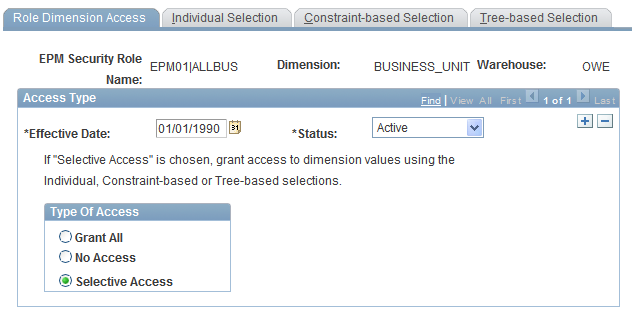
| Dimension |
Displays the dimension that you are associating with a particular security role. |
| Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
Type of Access
Individual Selection Page
Use the Individual Selection page (PF_SY_ROLE_LIST) to specify row-level access to the dimension based on SetID and dimension key fields.
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Individual Selection
Image: Individual Selection page
This example illustrates the fields and controls on the Individual Selection page. You can find definitions for the fields and controls later on this page.
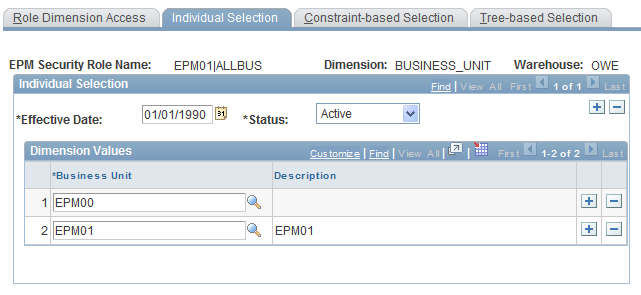
| Dimension |
Displays the dimension that you are associating with a particular security role. |
| Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
Dimension Values
Constraint-based Selection Page
Use the Constraint-based Selection page (PF_SY_ROLE_CONS) to specify row-level access to the dimension based on constraint.
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Constraint-based Selection
Image: Constraint-based Selection page
This example illustrates the fields and controls on the Constraint-based Selection page. You can find definitions for the fields and controls later on this page.
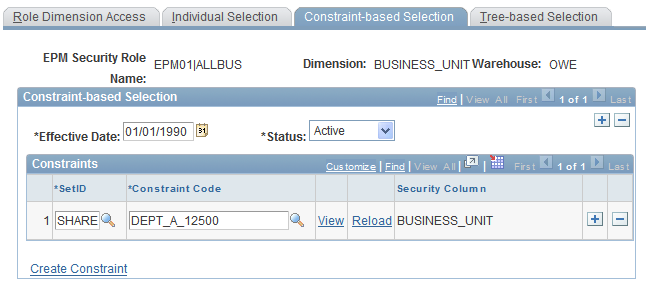
| Dimension |
Displays the dimension that you are associating with a particular security role. |
| Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
Constraint-based Selection
Select Security Column Page
Use the Select Security Column page (PF_SY_COLUMN_PG) to select one column to include in your constraint.
Automatically accessed when you select a constraint on the Constraint-based Selection page that contains two or more columns and the system cannot distinguish the column you want to include in your security parameters
When you select a constraint (on the Constraint-based Selection page) that contains two or more columns and the system cannot distinguish the column you want to include in your security parameters, the Select Security Column page is accessed automatically. The page displays the columns available to use in the constraint you selected. You must choose just one of the columns for the constraint. Select the column you want to include by clicking the column name in the Key ID field.
Tree-based Selection Pge
Use the Tree-based Selection page (PF_SY_ROLE_TREE) to specify row-level access to the dimension based on an existing tree hierarchy that is defined for the dimension.
You can use the tree to grant a user access to specific nodes, leaves, or details in the tree. Used with OWE dimensions only.
EPM Foundation, EPM Security, Security By Role, Role Dimension Access, Tree-based Selection
Image: Tree-based Selection page
This example illustrates the fields and controls on the Tree-based Selection page. You can find definitions for the fields and controls later on this page.
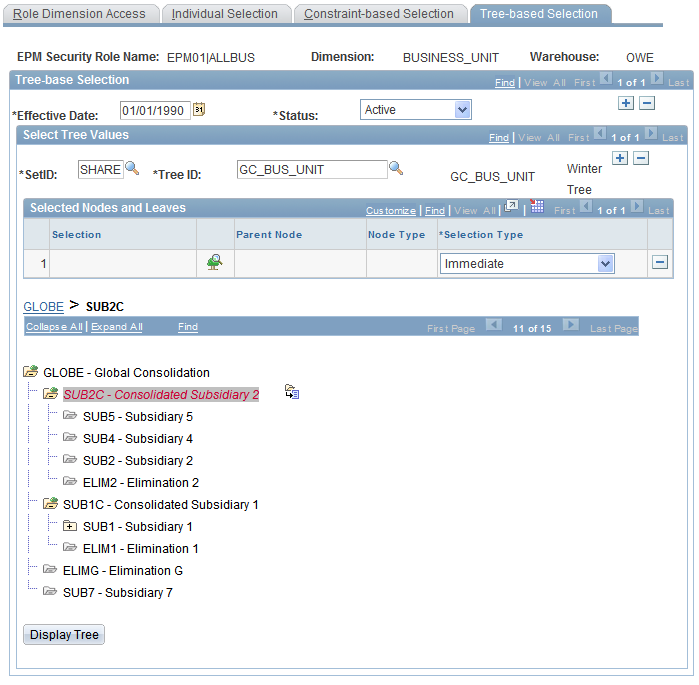
| Dimension |
Displays the dimension that you are associating with a particular security role. |
| Warehouse |
Displays the warehouse layer that is associated with the selected dimension. |
Select Tree Values
User Role Access Pge
Use the User Role Access page (PF_SY_USER_ROLES) to assign a user to a security role.
Image: User Role Access page
This example illustrates the fields and controls on the User Role Access page. You can find definitions for the fields and controls later on this page.
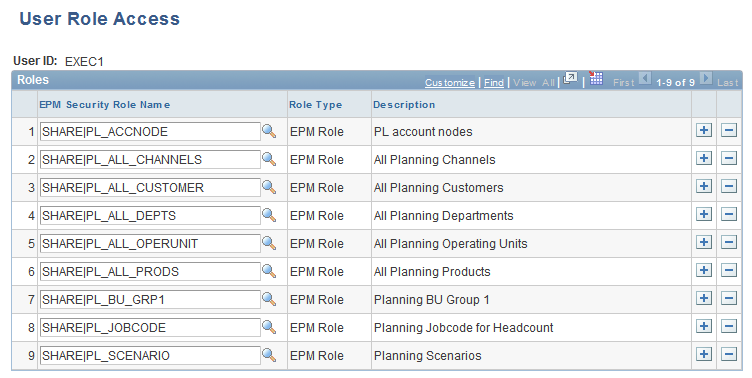
| User ID |
Displays the user for whom you are granting role access. |
| EPM Security Role Name |
Enter the security role that you want to associate with the selected user. |
Role Security Summary Page
Use the Role Security Summary page (PF_SY_ROL_SUMMARY) to review access privileges and other information for a security role.
Image: Role Security Summary page
This example illustrates the fields and controls on the Role Security Summary page. You can find definitions for the fields and controls later on this page.
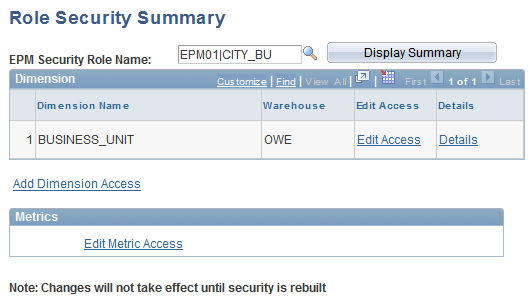
| EPM Security Role Name |
Enter the security role for which you want to see a summary of access privileges. |
| Display Summary |
Click to display the security role details and refresh the view. |
Dimension
Metrics
Click the Edit Metric Access link to access the Role Metric Access page and edit the security role's access to a metric.
Review Role Dimension Access Page
Use the Review Role Dimension Access page (PF_SY_ROLE_DETAIL) to .
Image: Review Role Dimension Access page
This example illustrates the fields and controls on the Review Role Dimension Access page. You can find definitions for the fields and controls later on this page.
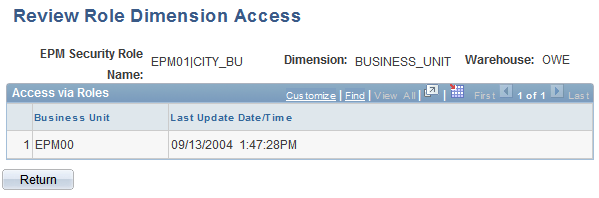
Use this page to review additional details about your dimension that is associated with a particular security role.
Access to Metric Page
Use the Access To Metric page (PF_SY_ROLE_METR) to assign a metric to a user.
The fields on this page are identical to the fields on the Access to Metric page for security roles. The only difference is that the fields on this page represent individual user access privileges and not a security role.
User Dimension Access Page
Use the User Dimension Access page (PF_SY_ROLE_ALL) to assign a dimension table to a user and specify high-level access privileges.
EPM Foundation, EPM Security, Security By User, User Dimension Access, User Dimension Access
The fields on this page are identical to the fields on the Role Dimension Access page. The only difference is that the fields on this page represent individual user access privileges and not a security role.
Individual Selection Page
Use the Individual Selection page (PF_SY_ROLE_LIST) to specify row-level access to the dimension based on SetID and dimension key fields.
EPM Foundation, EPM Security, Security By User, User Dimension Access, Individual Selection
The fields on this page are identical to the fields on the Individual Selection page for security roles. The only difference is that the fields on this page represent individual user access privileges and not a security role.
Constraint-Based Selection Page
Use the Constraint-based Selection page (PF_SY_ROLE_CONS) to specify row-level access to the dimension based on constraint.
EPM Foundation, EPM Security, Security By User, User Dimension Access, Constraint-based Selection
The fields on this page are identical to the fields on the Constraint-based Selection page for security roles. The only difference is that the fields on this page represent individual user access privileges and not a security role.
Tree-Based Selection Page (OWE Dimension Only)
Use the Tree-based Selection page (PF_SY_ROLE_TREE) to specify row-level access to the dimension based on an existing tree hierarchy that is defined for the dimension.
You can use the tree to grant a user access to specific nodes, leaves, or details in the tree. Used with OWE dimensions only.
EPM Foundation, EPM Security, Security By User, User Dimension Access, Tree-based Selection
The fields on this page are identical to the fields on the Tree-based Selection page for security roles. The only difference is that the fields on this page represent individual user access privileges and not a security role.
User Security Summary Page
Use the User Security Summary page (PF_SY_SUMMARY) to review access privileges and other information for a user.
Image: User Security Summary page
This example illustrates the fields and controls on the User Security Summary page. You can find definitions for the fields and controls later on this page.
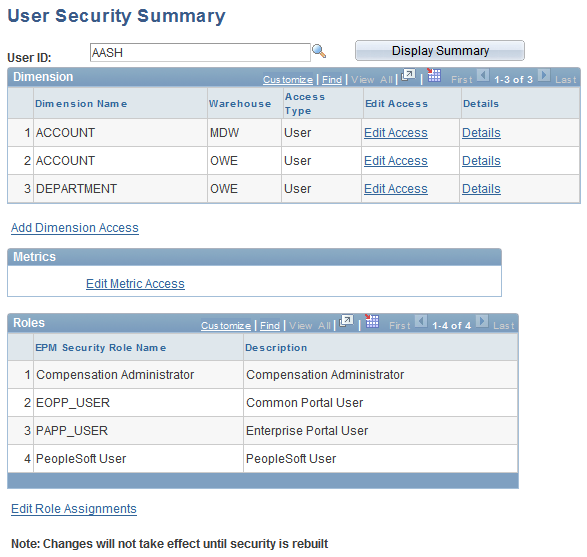
| User ID |
Enter the user for which you want to see a summary of access privileges. |
| Display Summary |
Click to display security details for the user and refresh the view. |
Dimension
Metrics
Click the Edit Metric Access link to access the User Metric Access page and edit the user's access to a metric.
Review User Dimension or User Metric Access Summary
Use the Review User Dimension Access page (PF_SY_USER_DETAIL) to review additional details about a dimension that is associated with the selected user.
The fields on this page are identical to the fields on the Review Role Dimension Access page. The only difference is that the fields on this page represent individual user access privileges and not a security role.
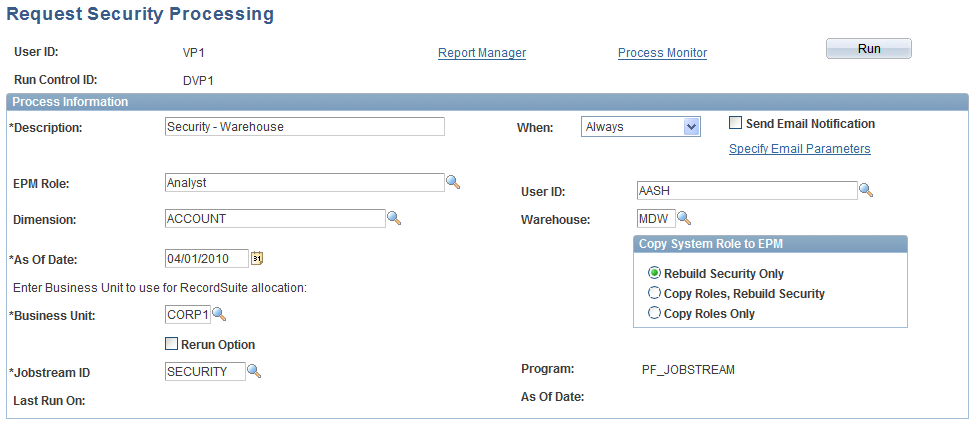
Request Security Processing Page
Use the Request Security Processing page (RUN_PF_SECURITY) to apply security parameters for security roles and users by running the request security processing (PF_SECURITY) process.
Image: Request Security Processing page
This example illustrates the fields and controls on the Request Security Processing page. You can find definitions for the fields and controls later on this page.
Copy System Role to EPM