C Troubleshooting Enterprise User Security
This appendix describes common situations that you might encounter when integrating Oracle Unified Directory with Enterprise User Security and explains the steps for addressing them. It contains the following topics:
-
Section C.1, "Net Configuration Assistant (NetCA) Tool Problems and Solutions"
-
Section C.2, "Database Configuration Assistant (DBCA) Problems and Solutions"
C.1 Net Configuration Assistant (NetCA) Tool Problems and Solutions
The following error may appear when you run the NetCA tool:
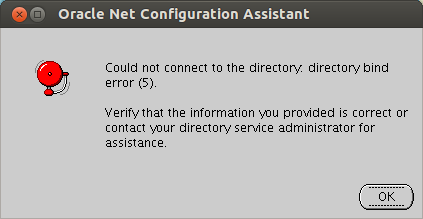
C.1.1 LDAP Server Connection Error
If the NetCA fails to connect to the directory then the Oracle Net Configuration Assistant screen displays the following error message:
To resolve this error, verify that the host name and port numbers are correct by running the following command on the command line:
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $PORT -b "" -s base "(objectclass=*)" dn: objectClass: top objectClass: ds-root-dse $ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $LDAPSPORT -Z -X -b "" -s base "(objectclass=*)" dn: objectClass: top objectClass: ds-root-dse
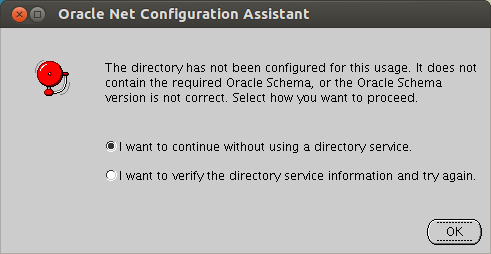
C.1.2 Schema Error
If the required schema is not available or the version number is incorrect then the Oracle Net Configuration Assistant screen displays the following error message:
To resolve this error, ensure that you can access Oracle Unified Directory anonymously and contains the cn=subschemasubentry entry:
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $LDAPSPORT -Z -X -b cn=subschemasubentry -s base "(objectclass=*)" dn: cn=subschema subentry objectClass: top objectClass: ldapSubentry objectClass: subschema
If the Oracle Unified Directory is not enabled for Enterprise User Security then the cn=subschemasubentry entry will not be available. To enable Enterprise User Security, see "Setting up the Directory Server by Using the GUI" in the Installing Oracle Unified Directory.
If the cn=subschemasubentry is not accessible anonymously then ensure that the following ACI is defined in the Oracle Unified Directory as a global ACIs:
(target="ldap:///cn=subschemasubentry")(targetscope="base")(targetattr="objectClass||attributeTypes||dITContentRules||dITStructureRules||ldapSyntaxes||matchingRules||matchingRuleUse||nameForms||objectClasses")(version 3.0; acl "User-Visible SubSchemaSubentry Operational Attributes"; allow (read,search,compare) userdn="ldap:///anyone";)
For more information, see Section 25.1, "Managing Global ACIs With dsconfig".
C.1.3 Naming Context Error
If the cn=OracleContext and cn=OracleContext,<your baseDN> naming contexts are not available, then the Oracle Net Configuration Assistant screen displays the following error message:
To resolve this error, complete the following:
-
Verify if the baseDN is available, by running the following command on the command line:
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $LDAPSPORT -Z -X -b "" -s base "(objectclass=*)" namingContexts dn: namingContexts: cn=OracleContext namingContexts: cn=OracleSchemaVersion namingContexts: dc=eusovd,dc=com
As shown above, ensure that there are three available naming context. If the base DN is missing then you must enable Enterprise User Security, as described in "Setting up the Directory Server by Using the GUI" in the Installing Oracle Unified Directory.
-
Verify if the baseDN contains the Oracle context by running the following command on the command line:
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $LDAPSPORT -Z -X -b "" "(objectclass=orclcontext)" dn: cn=OracleContext orclVersion: 90600 cn: OracleContext objectClass: orclContext objectClass: orclContextAux82 objectClass: top objectClass: orclRootContext dn: cn=OracleContext,dc=eusovd,dc=com orclVersion: 90600 cn: OracleContext objectClass: orclContext objectClass: orclContextAux82 objectClass: top
Note:
The NetCA performs the search anonymously. If the Oracle Unified Directory is configured to refuse anonymous searches or the ACIs restricts access tocn=OracleContext,<baseDN>then the NetCA will not able to find the Oracle Context. -
After the NetCA configuration is complete, it creates an
ldap.orafile in the$ORACLE_HOME/network/admindirectory (Unix) orORACLE_HOME\network\admin directory(Windows). Ensure that, it includes the following parameters:DIRECTORY_SERVERS= (sboy:1389:1636) DEFAULT_ADMIN_CONTEXT = "dc=eusovd,dc=com" DIRECTORY_SERVER_TYPE = OID
C.2 Database Configuration Assistant (DBCA) Problems and Solutions
The following error may appear when you run the DBCA tool:
-
Section C.2.1, "TNS-04409 error / TNS-04427: SSL access to the Directory Server"
-
Section C.2.2, "TNS-04409 error / TNS-04431: Required suffixes"
C.2.1 TNS-04409 error / TNS-04427: SSL access to the Directory Server
This error message appears if SSL is not enabled for Oracle Unified Directory.
To resolve this error, check if SSL is enabled for Oracle Unified Directory by running the following command on the command line:
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $LDAPSPORT -Z -X -b "" -s base "(objectclass=*)" dn: objectClass: top objectClass: ds-root-dse
For more information, see Chapter 23, "Configuring Security Between Clients and Servers".
C.2.2 TNS-04409 error / TNS-04431: Required suffixes
This error message appears if the suffixes are not available.
To resolve this error, ensure that the suffixes are created, as described in "Setting up the Directory Server by Using the GUI" in the Installing Oracle Unified Directory.
C.2.3 TNS-04411 error when registering the DB with a user different from cn=directory manager
This error message appears if you specify a different user name other then cn=directory manager during database registration.
To resolve this error, ensure that the user name has password reset privilege and any of the following the uniqueMember attribute:
-
cn=oraclecontextadmins,cn=groups,cn=oraclecontext,dc=eusovd,dc=com -
cn=oraclenetadmins,dc=oraclecontext,dc=eusovd,dc=comRun the following command on the command line:
$ OracleUnifiedDirectory/bin/ldapmodify -h $LDAPSERVER -p $LDAPPORT -D $DN -w $PWD dn: cn=newadmin,ou=people,dc=eusovd,dc=com changetype: modify add: ds-privilege-name ds-privilege-name: password-reset Processing MODIFY request for cn=newadmin,ou=people,dc=eusovd,dc=com MODIFY operation successful for DN cn=newadmin,ou=people,dc=eusovd,dc=com dn: cn=oraclenetadmins,cn=oraclecontext,dc=eusovd,dc=com changetype: modify add: uniquemember uniquemember: cn=newadmin,ou=people,dc=eusovd,dc=com Processing MODIFY request for cn=oraclenetadmins,cn=oraclecontext,dc=eusovd,dc=com MODIFY operation successful for DN cn=oraclenetadmins,cn=oraclecontext,dc=eusovd,dc=com dn: cn=oraclecontextadmins,cn=groups,cn=oraclecontext,dc=eusovd,dc=com changetype: modify add: uniquemember uniquemember: cn=newadmin,ou=people,dc=eusovd,dc=com Processing MODIFY request for cn=oraclecontextadmins,cn=groups,cn=oraclecontext,dc=eusovd,dc=com MODIFY operation successful for DN cn=oraclecontextadmins,cn=groups,cn=oraclecontext,dc=eusovd,dc=com
C.2.4 TNS-04409 error / TNS-04405
This error message appears if the Oracle Unified Directory password validator does not accept the password that DBCA creates for the database entry (For example, if it requires a password minimum length of 10 characters).
To resolve this error, you must complete the following:
-
Disable the password validator by running the following command on the command line:
$ OracleUnifiedDirectory/bin/dsconfig -h $LDAPSERVER -p $ADMINPORT -D $DN -j pwd.txt set-password-policy-prop --policy-name Default\ Password\ Policy --reset password-validator --trustAll --no-prompt
-
Run DBCA, as described in Section 28.3.3.2, "Registering Your Database with the Oracle Unified Directory".
-
Enable the password validator by running the following command on the command line:
$ OracleUnifiedDirectory/bin/dsconfig -h $LDAPSERVER -p $ADMINPORT -D $DN -j pwd.txt set-password-policy-prop --policy-name Default\ Password\ Policy --set password-validator:Length-Based\ Password\ Validator --trustAll --no-prompt
C.3 Oracle SQL Problems and Solutions
The following error may appear when you run the SQL tool:
-
Section C.3.1, "ORA-28030: Server encountered problems accessing LDAP directory service"
-
Section C.3.2, "ORA-01017: invalid username/password; logon denied"
-
Section C.3.3, "ORA-28274: No ORACLE password attribute corresponding to user nickname exists"
C.3.1 ORA-28030: Server encountered problems accessing LDAP directory service
This error message appears, if there is a problem with the connection between the database and the directory.
To resolve this issue, do the following:
-
Check that the database wallet has autologin enabled. Either use Oracle Wallet Manager or check that there is a
cwallet.ssofile in$ORACLE_HOME/admin/<ORACLE_SID>/wallet/. -
Check the DN and password of the user entry by running the following commands:
$ mkstore -wrl $ORACLE_BASE/admin/$ORACLE_SID/wallet -viewEntry ORACLE.SECURITY.DN Oracle Secret Store Tool : Version 11.2.0.2.0 - Production Copyright (c) 2004, 2010, Oracle and/or its affiliates. All rights reserved. Enter wallet password: ******** ORACLE.SECURITY.DN = cn=orcl11gr2,cn=OracleContext,dc=eusovd,dc=com $ mkstore -wrl $ORACLE_BASE/admin/$ORACLE_SID/wallet -viewEntry ORACLE.SECURITY.PASSWORD Oracle Secret Store Tool : Version 11.2.0.2.0 - Production Copyright (c) 2004, 2010, Oracle and/or its affiliates. All rights reserved. Enter wallet password: ******** ORACLE.SECURITY.PASSWORD = zQ7v4ek3
-
Check that the database is able to connect to the directory server using the following command:
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $LDAPSPORT -Z -X -D $DN -w $PWD -b $BASEDN -s base "(objectclass=*)" dn: dc=eusovd,dc=com orclversion: 90400 objectclass: domain objectclass: top orclsubscriberfullname: eusovd dc: eusovd
If the connection to the directory server fails, then you must do the following:
-
Ensure that the database entry exists in the Directory Server.
-
Ensure that the database entry contains a password in the
orclcommonrpwdattribute, by running the following command:$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $PORT -b cn=oraclecontext,$BASEDN -s one "(objectclass=orcldbserver)" orclcommonrpwdattribute dn: cn=orcl11gr2,cn=OracleContext,dc=eusovd,dc=com orclcommonrpwdattribute: {SASL-MD5}KvIVAyYahxnHWdlfN649Kw==
If the entry is missing or does not contain a password then you must DBCA, as described in Section 28.3.3.2, "Registering Your Database with the Oracle Unified Directory".
-
C.3.2 ORA-01017: invalid username/password; logon denied
This error message appears, if an invalid username or password is provided.
To resolve this error, specify the correct username and password.
-
Check the Enterprise User Security configuration by running the following command:
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $PORT -b cn=common,cn=products,cn=oraclecontext,$BASEDN "(objectclass=*)" orclcommonusersearchbase orclcommongroupsearchbase orclcommonnicknameattribute orclcommonnamingattribute dn: cn=Common,cn=Products,cn=OracleContext,dc=eusovd,dc=com orclcommonusersearchbase: ou=people,dc=eusovd,dc=com orclcommongroupsearchbase: ou=groups,dc=eusovd,dc=com orclcommonnicknameattribute: uid orclcommonnamingattribute: cn
After Oracle Unified Directory has been configured for EUS, the users and groups configurations are stored in the attributes
orclcommonusersearchbaseandorclusercommongroupsearchbase.The username provided to sqlplus must correspond to the value of
orclcommonnicknameattributein the user entry. For example, if you connect sqlplus using the values joe/password andorclcommonnicknameattribute=uid, then the database will look for an entry containing the attributeuid=joe.The user entry DN must start with
orclcommonnamingattribute. For example, iforclcommonnamingattribute=cn, the user entry must becn=joeuser,<orclcommonusersearchbase>. -
Ensure that there is a user entry in the user container that matches the username provided in sqlplus. The inetorgperson objectclass, containing the attribute defined in orclcommonnicknameattribute.
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $PORT -D $DN -w $PWD -b ou=people,$BASEDN "(uid=joe)" dn: cn=joe,ou=people,dc=eusovd,dc=com userPassword: {SSHA}DdW5je5GCUnT2jVTeMdfPR9NWwkBt40FwWImpA== objectclass: person objectclass: organizationalPerson objectclass: inetorgperson objectclass: top uid: joe cn: joe sn: joe -
Ensure that you have created the user-schema mapping, as described in "Mapping Enterprise Users to the Shared Schema" in the Oracle Database Enterprise User Security Administrator's Guide.
C.3.3 ORA-28274: No ORACLE password attribute corresponding to user nickname exists
This error message appears, when the database finds a corresponding user but can not compare its password with the password supplied to SQL.
To resolve this issue, do the following:
-
Ensure that the database entry has the required ACI to read the entry
authpasswordandorclguid:$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $PORT -D $DN -w $PWD -b ou=people,$BASEDN "(uid=joe)" authpassword orclguid dn: cn=joe,ou=people,dc=eusovd,dc=com authpassword;orclcommonpwd: {SSHA}DdW5je5GCUnT2jVTeMdfPR9NWwkBt40FwWImpA== orclguid: 6458c6945c0a48be92ab35cf71859210 -
If the database cannot read the entry, check that the following ACIs are defined in your OUD server as global-acis (they are added automatically by oud-setup when EUS is selected):
(target="ldap:///dc=eusovd,dc=com")(targetattr!="userpassword||authpassword||aci")(version 3.0; acl "Anonymous read access to subtree";allow (read,search,compare) userdn="ldap:///anyone";) (target="ldap:///dc=eusovd,dc=com")(targetattr="authpassword||userpassword")(version 3.0; acl "EUS reads authpassword"; allow (read,search,compare) userdn="ldap:///??sub?(&(objectclass=orclservice)(objectclass=orcldbserver))";)
-
If the user entry does not contain authpassword, ensure that there is a user password:
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $PORT -D $DN -w $PWD -b ou=people,$BASEDN "(uid=joe)" userpassword dn: cn=joe,ou=people,dc=eusovd,dc=com userpassword: {SSHA}DdW5je5GCUnT2jVTeMdfPR9NWwkBt40FwWImpA== -
Ensure that the userpassword attribute is stored using a compatible scheme (SSHA-512 is not supported):
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p $PORT -D $DN -w $PWD -b ou=people,$BASEDN "(uid=joe)" userpassword dn: cn=joe,ou=people,dc=eusovd,dc=com userpassword: {SSHA}DdW5je5GCUnT2jVTeMdfPR9NWwkBt40FwWImpA==
C.3.4 ORA-28051: the account is locked
This error message appears, if you fail to authenticate properly after multiple attempts.
To resolve this issue, do the following:
-
Verify if Oracle Unified Directory is configured for account lockout, by running the following command on the command line:
$ OracleUnifiedDirectory/bin/ldapsearch -h $LDAPSERVER -p 4444 -X -Z -D cn=directory\ manager -w Admin123 -b "cn=Default Password Policy,cn=Password Policies,cn=config" "(objectclass=*)" ds-cfg-lockout-failure-count ds-cfg-lockout-duration ds-cfg-lockout-failure-expiration-interval dn: cn=Default Password Policy,cn=Password Policies,cn=config ds-cfg-lockout-failure-expiration-interval: 180 s ds-cfg-lockout-failure-count: 3 ds-cfg-lockout-duration: 180 s
If the
failure-countvalue is 0, then the account lockout is not enabled. For more information, see Chapter 27, "Managing Password Policies". -
Ensure that the following ACI is defined, when the Enterprise User Security is configured:
(target="ldap:///dc=eusovd,dc=com")(targetattr="orclaccountstatusevent")(version 3.0; acl "EUS write orclaccountstatusenabled"; allow (write) userdn="ldap:///??sub?(&(objectclass=orclservice)(objectclass=orcldbserver))";) (targetcontrol="2.16.840.1.113894.1.8.16")(version 3.0; acl "Anonymous control access"; allow(read) userdn="ldap:///anyone";) (targetcontrol="2.16.840.1.113894.1.8.2")(version 3.0; acl "Anonymous control access"; allow(read) userdn="ldap:///anyone";)