1 Contacts Server Security Overview
This chapter provides an overview of Oracle Communications Contacts Server security.
Basic Security Considerations
The following principles are fundamental to using any application securely:
-
Keep software up to date. This includes the latest product release and any patches that apply to it.
-
Limit privileges as much as possible. Users should be given only the access necessary to perform their work. User privileges should be reviewed periodically to determine relevance to current work requirements.
-
Monitor system activity. Establish who should access which system components, how often they should be accessed, and who should monitor those components.
-
Install software securely. For example, use firewalls, secure protocols (such as SSL), and secure passwords. See "Performing a Secure Contacts Server Installation" for more information.
-
Learn about and use Contacts Server security features. See "Implementing Contacts Server Security" for more information.
-
Use secure development practices. For example, take advantage of existing database security functionality instead of creating your own application security.
-
Keep up to date on security information. Oracle regularly issues security-related patch updates and security alerts. You must install all security patches as soon as possible. See "Critical Patch Updates and Security Alerts" on the Oracle website at:
http://www.oracle.com/technetwork/topics/security/alerts-086861.html
Understanding the Contacts Server Environment
When planning your Contacts Server implementation, consider the following:
-
Which resources must be protected?
For example:
-
Contacts Server front end
-
Contacts Server back end (MySQL Server or Oracle Database)
-
Document store (can be local, remote, or dbdocstore)
-
Dependent resources, such as the application server and Oracle Directory Server Enterprise Edition
-
-
From whom am I protecting the resources?
In general, resources must be protected from everyone on the Internet. But should the Contacts Server deployment be protected from employees on the intranet in your enterprise? Should your employees have access to all resources within the application server environment? Should the system administrators have access to all resources? Should the system administrators be able to access all data? You might consider giving access to highly confidential data or strategic resources to only a few well trusted system administrators. On the other hand, perhaps it would be best to allow no system administrators access to the data or resources.
-
What happens if protections on strategic resources fail?
In some cases, a fault in your security scheme is easily detected and considered nothing more than an inconvenience. In other cases, a fault might cause great damage to companies or individual clients that use Contacts Server. Understanding the security ramifications of each resource help you protect it properly.
Overview of Contacts Server Security
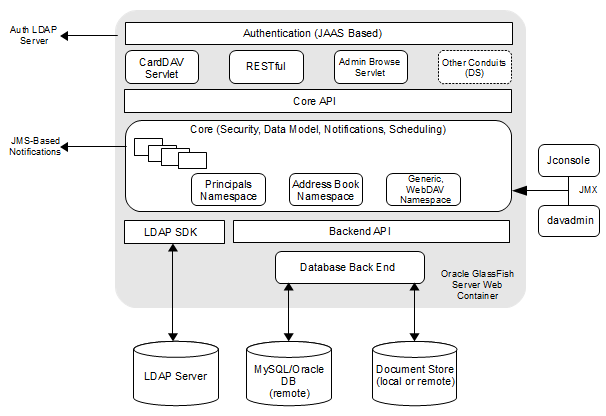
Figure 1-1 shows all the various components that can comprise Contacts Server, including the components to which it connects. Each installed or integrated component requires special steps and configurations to ensure system security.
Note:
The following figure includes Oracle GlassFish Server as an example for a container. However, this figure is also applicable for Oracle WebLogic Server as a container.Recommended Deployment Topologies
You can deploy Contacts Server on a single host or on multiple hosts, splitting up the components into multiple front-end hosts and multiple back-end hosts. You can also install the document stores onto separate hosts. For more information, see the topic on planning your installation in Contacts Server Installation and Configuration Guide.
The general architectural recommendation is to use the well-known and generally accepted Internet-Firewall-DMZ-Firewall-Intranet architecture. For more information on addressing network infrastructure concerns, see the topic on determining your Communications Suite network infrastructure needs in Communications Suite Deployment Planning Guide.
Operating System Security
This section lists Contacts Server-specific OS security configurations. This section applies to all supported OSs.
Firewall Port Configuration
Contacts Server communicates with various components on specific ports. Depending on your deployment and use of a firewall, you might need to ensure that the firewalls are configured to manage traffic for the following components:
-
MySQL Database port (the default value is 3306)
-
Oracle Database server port (the default value is 1521)
-
Contacts Server back-end remote document store port (the default value is 8008)
-
GlassFish Server administration server port (the default value is 4848)
-
Contacts Server access port (the default value is 443)
-
Notification mail server port (the default value is 25)
-
Oracle WebLogic Server Administration Server and Managed Server ports (the default values are 7002 and 7004)
Close all unused ports, especially non-SSL ports. Opt for SSL-enabled ports, instead of non-SSL ports, for all communications (for example: HTTPS, IIOPS, t3s).
For more information about securing your OS, see your OS documentation.
Database Security
For more information about securing Oracle Database, see Oracle Database Security Guide and Oracle Database Advanced Security Administrator's Guide: Oracle Database 19c Documentation.
For more information about securing MySQL Server, see Security in MySQL.
Secure Communications
Secure connections between applications connected over the World Wide Web can be obtained by using protocols such as Secure Socket Layer (SSL) or Transport Layer Security (TLS). SSL is often used to refer to either of these protocols or a combination of the two (SSL/TLS). Due to a security problem with SSLv3, Contacts Server recommends the use of only TLS. However, throughout this guide, secure communications may be referred to by the generic term SSL.
SSL enables secure communication between applications connected through the Web. In a Contacts Server deployment, you can configure SSL between the following components:
-
Application server and client connections
-
Contacts Server and Directory Server
-
Application server and the JMX port used by Contacts Server administration utility
-
Contacts Server and the back-end database
-
Contacts Server and the document store
See "Implementing Contacts Server Security" for more information.