1 Introduction to Oracle Key Vault
Before you begin to use Oracle Key Vault, you should understand its purpose, benefits, user audience, major features, interfaces, and general steps for using Key Vault.
Topics:
About Oracle Key Vault and Key Management
Oracle Key Vault enables you to quickly deploy encryption and other security solutions by centrally managing encryption keys, Oracle wallets, Java keystores (JKS), Java Cryptography Extension keystores (JCEKS), and credential files.
Oracle Key Vault is optimized for managing Oracle Advanced Security Transparent Data Encryption (TDE) master keys. The full-stack, security-hardened Oracle Key Vault software appliance uses Oracle Linux and Oracle Database technology for security, availability, and scalability. This centralized approach addresses challenges that are caused by the increased use of keys, wallets, and keystores, and prevents their accidental loss, while enabling long-term retention and restoration of encrypted data.
In addition to supporting Oracle database and application servers, Oracle Key Vault follows the industry standard OASIS Key Management Interoperability Protocol (KMIP) for compatibility with KMIP-based clients.
See Also:
-
"Support for OASIS Key Management Interoperability Protocol (KMIP)"
-
Oracle Database Advanced Security Guide for a complete discussion of Transparent Data Encryption (TDE)
Benefits of Using Oracle Key Vault
Oracle Key Vault addresses the rising need to use encryption in data centers by providing a secure key management platform that quickly and efficiently deploys encryption across your enterprise.
Oracle Key Vault provides the following benefits:
-
A centralized platform to securely store and manage encryption keys, credential files, Oracle wallets, and Java keystores. This centralized platform enables you to achieve the following:
-
Manage the key lifecycle, including creation, rotation, and removal, for all endpoints. This includes the ability to share access to security objects among multiple endpoints. Endpoints can be databases, middleware, and other data sources that contain the keys that you want to manage with Oracle Key Vault.
-
Prevent the loss of keys and wallets due to forgotten passwords or accidentally deleted wallets and keystores.
-
-
Easy enrollment and provisioning of endpoints, that is; configuring the connections between Oracle Key Vault and endpoints. Endpoint provisioning uses a single package that contains all the necessary software binaries and configuration files as well as the endpoint certificates needed for mutually authenticated connections with Oracle Key Vault.
-
The ability to work with other Oracle products: in addition to TDE, Oracle Key Vault works with Oracle Real Application Clusters (Oracle RAC), Oracle Active Data Guard, and Oracle GoldenGate. Oracle Key Vault facilitates the movement of encrypted data using Oracle Data Pump and the transportable tablespaces feature of Oracle Database.
Figure 1-1 illustrates the Oracle Key Vault environment.
Figure 1-1 How Oracle Key Vault Manages Keys, Secrets, and Wallets for Endpoints
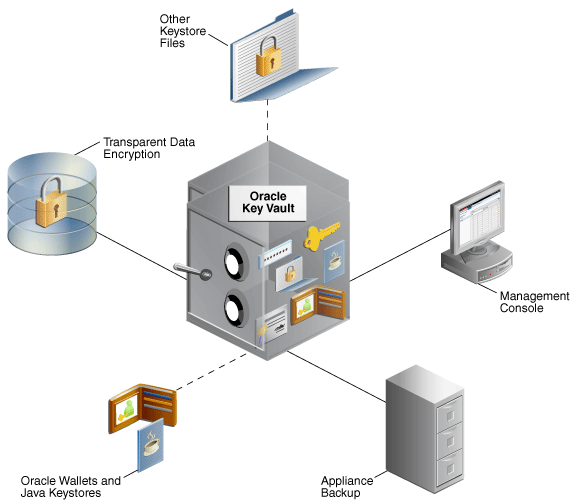
Description of ''Figure 1-1 How Oracle Key Vault Manages Keys, Secrets, and Wallets for Endpoints''
In Figure 1-1, Oracle Key Vault, in the center, stores and manages the security objects and backup devices. It works with the following components:
-
Transparent Data Encryption refers to Oracle databases that have tables and tablespaces configured to use TDE.
-
Other Keystore Files can be JCEKS keystores that you upload to Oracle Key Vault from endpoints or download from Key Vault to endpoints.
-
Management Console refers to the Oracle Key Vault graphical user interface, in which you log in to manage objects that you upload to Key Vault.
-
Appliance Backup refers to a backup device for Oracle Key Vault data, which you configure for a high availability environment.
-
Oracle Wallets and Java Keystores refers to the wallets and keystores that you upload to Oracle Key Vault and download to endpoints.
Who Should Use Oracle Key Vault?
Users who are responsible for managing security objects should use Oracle Key Vault.
These users can be database administrators, IT personnel, system administrators, security administrators, and any information security personnel who are responsible for database servers, application servers, operating systems, and other systems that manage Oracle wallets, encryption keys, Java keystores, credential files, and certificates.
Other users can include personnel responsible for Oracle databases and servers that interact with Oracle databases, because Oracle Key Vault provides inherently tighter integration. These systems may have a need to simplify encryption key and wallet management.
Although Oracle Key Vault is designed for easy integration with Oracle Advanced Security TDE, it is compatible with endpoints that support OASIS KMIP.
Major Features of Oracle Key Vault
Oracle Key Vault provides a number of features designed to enhance the security of key management, such as centralized management of keys, wallets, keystores, and credential files.
Topics:
-
Centralization of TDE Master Keys, Oracle Wallets, Java Keystores, and Credential Files
-
Support for OASIS Key Management Interoperability Protocol (KMIP)
Centralization of TDE Master Keys, Oracle Wallets, Java Keystores, and Credential Files
Oracle Key Vault centralizes keys in a modern, secure, and robust key management platform. This enables you to secure, share, and manage the keys all in one place.
You can centrally manage the following types of security objects:
-
TDE master keys
For Oracle databases that use Transparent Data Encryption (TDE), Oracle Key Vault manages TDE master keys over a direct network connection as an alternative to using local wallet files. The keys stored in Oracle Key Vault can be shared across databases according to endpoint access control settings. This method of sharing keys without local wallet copies is useful when TDE is running on database clusters such as Oracle RAC, Oracle Active Data Guard, or Oracle GoldenGate. You can easily migrate master keys that are used for existing encrypted data in Oracle databases from Oracle wallets to Oracle Key Vault. Oracle Key Vault supports direct connections between TDE and Oracle Key Vault for Oracle Database 11g Release 2 and Oracle Database 12c.
-
Oracle wallets and Java keystores
Oracle wallets and Java keystores are often widely distributed across servers and server clusters, with backup and distribution of these files performed manually. Oracle Key Vault itemizes and stores contents of these files in a master repository yet allows server endpoints to continue operating while disconnected from Oracle Key Vault using their local copies. After you have archived wallets and keystores, you can recover them to their servers if their local copies are mistakenly deleted or their passwords are forgotten. Oracle Key Vault streamlines the sharing of wallets across database clusters such as Oracle RAC, Oracle Active Data Guard, and Oracle GoldenGate. Sharing of wallets also facilitates the movement of encrypted data using Oracle Data Pump and the transportable tablespaces feature of Oracle Database. You can use Oracle Key Vault with Oracle wallets from all supported releases of Oracle middleware products and Oracle Database.
-
Backup of credential files
Credential files that contain Secure Shell (SSH) keys, Kerberos keytabs, and similar keys are often widely distributed without appropriate protective mechanisms. Oracle Key Vault backs up credential files for long-term retention and recovery. Oracle Key Vault easily recovers these files when you need them, audits access to them, and shares them across trusted server endpoints.
Management of Key Lifecyle
The management of the key lifecycle entails activities such as reminding users to rotate passwords.
Most systems that create keys and passwords, including TDE, do not have a mechanism to remind customers of the key rotation requirements for staying in compliance, but Oracle Key Vault provides one. Oracle Key Vault enables you to create policies that track the lifecycle of keys (their creation, rotation, and expiration) and raise alerts when keys or passwords approach the end of their useful lives. You can use Oracle Key Vault reports to ensure that the keys have not expired (that is, that the keys are being rotated on a proper schedule).
Lifecycle tracking is very important because standards such as the Payment Card Industry Data Security Standard (PCI DSS) have specific requirements for the maximum lifetime of encryption keys and passwords.
Reporting and Alerts
Oracle Key Vault provides report and alert capabilities.
-
Report capabilities
Oracle Key Vault provides both audit reports and management reports. Audit reports capture the actions that users perform and the results of those actions. Management reports capture information about wallet access, key deactivation or expiration, endpoint certificate expiration, and the user password expiration date.
See Also:
"About Oracle Key Vault Reports" -
Alert capabilities
You can configure alerts for key rotations, endpoint certificate expirations, user password expirations, disk space, system backups, and high availability events. You can choose to send alerts regarding the Oracle Key Vault server to syslog to allow for external monitoring.
See Also:
"Oracle Key Vault Alert Configuration"
Separation of Duties for Oracle Key Vault Users
For better security, Oracle Key Vault is designed to provide separation of duties for anyone who uses it.
Oracle Key Vault provides three roles for specific tasks: the Key Administrator role, the System Administrator role, and the Audit Manager role. The user who is responsible for uploading and downloading security objects between Oracle Key Vault and the endpoint is referred to as the endpoint administrator.
See Also:
"Overview of Administrative Roles"Support for a High Availability Environment
To ensure that Oracle Key Vault can access security objects in the event of a failure, Oracle Key Vault can be configured for a high availability environment.
You can deploy two Oracle Key Vault appliances in a two-node cluster for a high availability configuration. The primary appliance services the requests that come from endpoints. If the primary appliance fails, then the standby appliance takes over after a preset delay. The preset delay prevents the standby appliance from taking over prematurely if there is a transient communication problem between the nodes.
Oracle Key Vault uses Oracle Data Guard to synchronize data between the primary and standby nodes in a high availability deployment.
Backup and Restore Functionality for Security Objects
Oracle Key Vault enables you to back up all security objects including keys, certificates, and passwords. It encrypts the backups.
Oracle Key Vault can securely store backups at a remote destination. This enables backups to be restored to a new appliance if the original appliance encounters a irrecoverable error. Therefore, Oracle Key Vault can restore the previous state that is represented in the backup to the same Oracle Key Vault appliance or to a new one if the originating appliance must be replaced due to a catastrophic failure.
Oracle Key Vault can transfer backup files to any remote location that implements the secure copy protocol (SCP).
Users who have been granted the System Administrator role can perform the following backup and restore tasks in Oracle Key Vault:
-
Set up and modify remote backup locations. This task automatically transfers the encrypted backup media to a remote location on a preconfigured schedule.
-
Set up, modify, or disable the current backup schedule.
-
Initiate an immediate one-time backup.
-
Schedule a future one-time backup.
Oracle Key Vault performs the backup in hot backup mode, which ensures that the system is not interrupted while the backup is being created.
Compatibility and Deployment Support
You should be aware of Oracle Key Vault compatibility with earlier releases and platforms on which the deployment is certified.
-
Compatibility
Oracle Database 11g Release 2 and later can use Oracle Key Vault to store TDE master keys with no database patching required.
-
Deployment
You can deploy Oracle Key Vault on Oracle Linux x86-64 systems. Oracle Key Vault works with endpoints that are on Oracle Linux and Oracle Solaris systems.
Support for OASIS Key Management Interoperability Protocol (KMIP)
OASIS Key Management Interoperability Protocol (KMIP) standardizes key management operations between key management servers and endpoints provided by different vendors.
Oracle Key Vault implements the following OASIS KMIP Version 1.1 profiles:
-
Basic Discover Versions Server Profile: Provides the server version to endpoints.
-
Basic Baseline Server KMIP Profile: Provides core functionality to retrieve objects from the server.
-
Basic Secret Data Server KMIP Profile: Provides endpoints the ability to create, store, and retrieve secret data (typically passwords) on the server.
-
Basic Symmetric Key Store and Server KMIP Profile: Provides endpoints the ability to store and retrieve symmetric encryption keys on the server.
-
Basic Symmetric Key Foundry and Server KMIP Profile: Provides endpoints the ability to create new symmetric encryption keys on the server.
See Also:
http://docs.oasis-open.org/kmip/spec/v1.1/os/kmip-spec-v1.1-os.html for information about the OASIS KMIP specificationOracle Key Vault Interfaces
Oracle Key Vault provides two interfaces: a management console and an endpoint command-line utility for uploading and retrieving security objects.
-
Oracle Key Vault management console
The Oracle Key Vault management console, which is a browser-based graphical user interface, enables Oracle Key Vault administrators (depending on their role and access) to manage endpoints, wallets, users, and reports, and to configure high availability, backup, and recovery. The information that is viewable depends on the type of user (the role this user has or does not have) who is logged in.
-
Oracle Key Vault
okvutilendpoint utilityYou use the
okvutilcommand-line utility from an endpoint to upload and download security objects between Oracle Key Vault and endpoints. For example, you can upload an Oracle wallet from one endpoint to Oracle Key Vault, and then later on download this wallet to a different endpoint. Theokvutilutility communicates with Oracle Key Vault over a mutually authenticated secure connection.
Outline of Steps for Using Oracle Key Vault
Oracle recommends that you follow a general set of steps for using Oracle Key Vault.
-
Read Chapter 2, "Oracle Key Vault Concepts," which covers conceptual information for using Oracle Key Vault.
-
Install and configure Oracle Key Vault.
You install Oracle Key Vault onto its own dedicated server. The configuration process entails creating or providing the user accounts, setting the IP address and recovery passphrase, and optionally, configuring the system time and Domain Name Service (DNS) setup.
See Chapter 3, "Oracle Key Vault Installation and Configuration," for more information.
-
(Optional) Configure a high availability environment for your Oracle Key Vault endpoints. An Oracle Key Vault user with the System Administrator role performs this task.
Note:
You must have a separate license for each Oracle Key Vault server installation in a high availability environment.Oracle recommends that you deploy two Oracle Key Vault appliances, in primary and standby configurations, for a high availability environment.
See "Configuring High Availability for Oracle Key Vault" for more information.
-
Create users to manage the day-to-day tasks for Oracle Key Vault.
The installation process includes creating user accounts, but you may want to configure additional user accounts to handle Oracle Key Vault tasks, depending on the requirements of your site. The ability to manage specific security objects can be assigned to individual users as necessary.
See Chapter 5, "Managing Oracle Key Vault Users," for more information.
-
Add endpoints so that users can use Oracle Key Vault to store their security objects.
Endpoints are systems (such as Oracle databases) that use security objects for various cryptographic operations.
See Chapter 6, "Managing Oracle Key Vault Endpoints," for more information.
-
Manage the Oracle Key Vault virtual wallets.
Virtual wallets reside in Oracle Key Vault and are containers for security objects that you upload from endpoints.
See Chapter 7, "Managing Oracle Key Vault Virtual Wallets and Security Objects," for more information.
-
Enroll endpoints and then upload or download security objects between the endpoints and Oracle Key Vault.
In this step, you register the databases or other endpoints that contain the keys, credentials, and other secure data with Oracle Key Vault. Users who are responsible for the endpoint (endpoint administrators) upload and download security objects.
Chapter 8, "Using Oracle Key Vault Endpoints," describes how to enroll endpoints for more information.
-
Manage the endpoint data.
In this step, you upload and download data (Oracle wallets, Java keystores, credential files, and so on) between Oracle Key Vault and the endpoints.
See Chapter 9, "Oracle Key Vault Use Case Scenarios," for more information.
-
Perform periodic maintenance tasks.
Depending on the task, users who have the Key Administrator, System Administrator, or Audit Manager roles perform periodic maintenance tasks.
See Chapter 10, "General Oracle Key Vault Management," for more information.